0% found this document useful (0 votes)
170 views18 pagesStructured System Analysis and Design Method
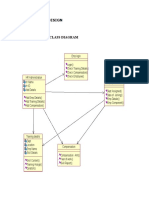
Structured system analysis and design method (SSADM) is a waterfall method for analyzing and designing information systems. It was developed in the UK in the 1980s. SSADM uses data flow diagrams, entity relationship diagrams, and other modeling techniques to document existing systems and design new systems. The goal is to provide a framework to enable the economic development of computer systems that meet user needs. SSADM involves rigorous documentation and contrasts with more agile methods.
Uploaded by
sudarakagamageCopyright
© Attribution Non-Commercial (BY-NC)
We take content rights seriously. If you suspect this is your content, claim it here.
Available Formats
Download as PDF, TXT or read online on Scribd
0% found this document useful (0 votes)
170 views18 pagesStructured System Analysis and Design Method
Structured system analysis and design method (SSADM) is a waterfall method for analyzing and designing information systems. It was developed in the UK in the 1980s. SSADM uses data flow diagrams, entity relationship diagrams, and other modeling techniques to document existing systems and design new systems. The goal is to provide a framework to enable the economic development of computer systems that meet user needs. SSADM involves rigorous documentation and contrasts with more agile methods.
Uploaded by
sudarakagamageCopyright
© Attribution Non-Commercial (BY-NC)
We take content rights seriously. If you suspect this is your content, claim it here.
Available Formats
Download as PDF, TXT or read online on Scribd
/ 18