0% found this document useful (0 votes)
102 views7 pagesReport Network Hack
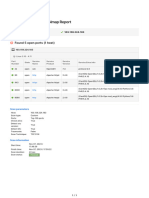
The document describes several failed SSH login attempts from IP addresses in China to a root username. Location lookups show one IP address is located in Shanghai, China and the other in Jiangsu, China. Blacklist checks show neither IP is listed on known blacklists.
Uploaded by
Edmar SamortinCopyright
© © All Rights Reserved
We take content rights seriously. If you suspect this is your content, claim it here.
Available Formats
Download as DOCX, PDF, TXT or read online on Scribd
0% found this document useful (0 votes)
102 views7 pagesReport Network Hack
The document describes several failed SSH login attempts from IP addresses in China to a root username. Location lookups show one IP address is located in Shanghai, China and the other in Jiangsu, China. Blacklist checks show neither IP is listed on known blacklists.
Uploaded by
Edmar SamortinCopyright
© © All Rights Reserved
We take content rights seriously. If you suspect this is your content, claim it here.
Available Formats
Download as DOCX, PDF, TXT or read online on Scribd
/ 7