0% found this document useful (0 votes)
10 views1 pageHTTP by Default
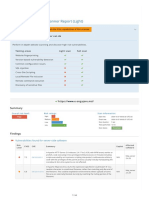
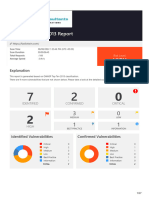
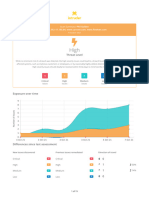
The website lacks a proper SSL certificate, making it vulnerable to Man-in-the-Middle attacks that can expose users' usernames and passwords. This risk is particularly high for users on public or shared networks. To mitigate this vulnerability, it is recommended to implement an SSL certificate to ensure secure HTTPS connections.
Uploaded by
piyushcyber9Copyright
© © All Rights Reserved
We take content rights seriously. If you suspect this is your content, claim it here.
Available Formats
Download as TXT, PDF, TXT or read online on Scribd
0% found this document useful (0 votes)
10 views1 pageHTTP by Default
The website lacks a proper SSL certificate, making it vulnerable to Man-in-the-Middle attacks that can expose users' usernames and passwords. This risk is particularly high for users on public or shared networks. To mitigate this vulnerability, it is recommended to implement an SSL certificate to ensure secure HTTPS connections.
Uploaded by
piyushcyber9Copyright
© © All Rights Reserved
We take content rights seriously. If you suspect this is your content, claim it here.
Available Formats
Download as TXT, PDF, TXT or read online on Scribd
/ 1