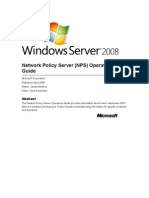
API Pentesting
Mindmap
{{Recon}}
V1
V2
API Version Discovery
V3
Import the API environment, etc
documentation and collections
Product / open source
Link BurpSuite proxy with Postman API Implementation Discovery
Custom API Implementation
Activate the API environment These two steps should handle every
function in the recon method together
RESTful [Most common]
Discovering authentication systems,
server's headers and requests Postman API Type Discovery SOAP [Very rare]
parameters body
GraphQL [Newcomer]
OTP
WADL for RESTful API
Identifying authentication's
login
endpoints. Local WSDL for SOAP API
etc
API Documentations etc
Analyzing JS code, like the JSON in
the Tests tab Any public documentation for API like the open
Public
source APIs
Importing WADL / WSDL file initially
or using the Application's URL GET
Analyze endpoint behaviors using POST
SoapUI
the endpoint explorer
HTTP Methods Discovery PATCH
Link BurpSuite proxy with Postman
PUT
Intercept and monitor every request
/ response DELETE
Run the content discovery on the WADL
API seeking for additional endpoints, Endpoints gathering through local
actions and objects WSDL
docs
Analyze request & response headers etc
and parameters
BurpSuite Reconnaissance
the endpoints which requires authentication and other
Manipulate the request headers and publicly accessible.
monitor the server's actions to the Weaponizing
manipulations Cookie based (non-standard)
Authentication / Authorization
methods
Run the JavaScript scans to analyze Header based (standard)
Authentication &
JavaScript files in order to Authorization
understand the API infrastructure JWT (JSON Web Token)
Endpoints Encrypted value
Objects Fuzzing points Arbitrary value to save the user's
Identification handlers
state
Methods / Actions
Encoded Serialized value
Link it with Burp in order to extend Fuzzing
FFUF
your sitemap range Encrypted Serialized value
BurpSuite Intruder Hashed user value e.g: hashed username, user ID
Tools
Link it with Burp in order to extend Compare the local & public API documentations seeking for hidden functions,
Comparing docs
your endpoints parameter range methods or endpoints.
(Vary from target to another)
Arjun Endpoints
Analyze the arjun output to check
for the possible vulnerable API Fuzzing Actions AKA Methods
parameter
Objects
SecLists
Mapping the API's request &
FuzzDB response body and headers.
Behavior mapping
Using wayback machine Wordlists Identify the job of every API method
[It's vary from API to another]
Using the API docs
Swagger API
e.g: JavaScript Source Code Reviewing Generating Custom Wordlist API Visualization tools / interfaces
Custom Implementations
discovery
Organization's github repository if
exists etc
The source code of API product
- if it was open source - Enumerate resources e.g: /api/{{products}}/122/edit
e.g: enumerate object identifiers:
RESTful API enumeration Enumerate objects
/api/users/{{1}}/edit
In this phase you should concentrate
more in the response headers,
response length and application's
behaviors
Could be found in
PayloadAllTheThings
Introspection query enumerating
Our aim of making this is to retrieve
every query that can be run in the
Enumeration
database and it's parameters
GraphQL API enumeration
GraphQL Voyager
Visual representation tools It will show us the visual
representation of GraphQL which
made use able to analyze the
GraphQL in a deep and accurate way
API scanner for endpoints and
Kiterunner
content discovery.
Tools
Extracting paths from URL lists, this
unfurl will help in generating custom
wordlists phase.