0% found this document useful (0 votes)
6 views6 pagesInstalling and Configuring Mysql
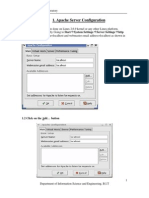
The document provides instructions for installing and configuring MySQL, including launching the MySQL Command-Line Client and troubleshooting installation issues. It also discusses IT security guidelines, privilege-granting guidelines, and the installation of Apache and PHP. Additionally, it covers log management for Apache, including error and access logs, and the basics of the php.ini configuration file.
Uploaded by
kamalakar76Copyright
© © All Rights Reserved
We take content rights seriously. If you suspect this is your content, claim it here.
Available Formats
Download as DOCX, PDF, TXT or read online on Scribd
0% found this document useful (0 votes)
6 views6 pagesInstalling and Configuring Mysql
The document provides instructions for installing and configuring MySQL, including launching the MySQL Command-Line Client and troubleshooting installation issues. It also discusses IT security guidelines, privilege-granting guidelines, and the installation of Apache and PHP. Additionally, it covers log management for Apache, including error and access logs, and the basics of the php.ini configuration file.
Uploaded by
kamalakar76Copyright
© © All Rights Reserved
We take content rights seriously. If you suspect this is your content, claim it here.
Available Formats
Download as DOCX, PDF, TXT or read online on Scribd
/ 6