0% found this document useful (0 votes)
5 views38 pagesPractical 1
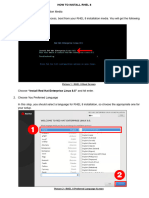
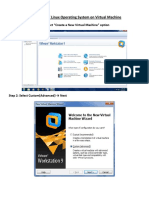
The document provides a comprehensive guide on installing Red Hat Enterprise Linux (RHEL) 6.x, detailing hardware requirements, pre-installation steps, and the installation process. It also covers user and group management, including commands for creating, modifying, and deleting users, as well as managing passwords and permissions. Key configuration files like /etc/passwd and /etc/shadow are explained, emphasizing their roles in user management and security.
Uploaded by
dubeysumit378Copyright
© © All Rights Reserved
We take content rights seriously. If you suspect this is your content, claim it here.
Available Formats
Download as PDF, TXT or read online on Scribd
0% found this document useful (0 votes)
5 views38 pagesPractical 1
The document provides a comprehensive guide on installing Red Hat Enterprise Linux (RHEL) 6.x, detailing hardware requirements, pre-installation steps, and the installation process. It also covers user and group management, including commands for creating, modifying, and deleting users, as well as managing passwords and permissions. Key configuration files like /etc/passwd and /etc/shadow are explained, emphasizing their roles in user management and security.
Uploaded by
dubeysumit378Copyright
© © All Rights Reserved
We take content rights seriously. If you suspect this is your content, claim it here.
Available Formats
Download as PDF, TXT or read online on Scribd
/ 38