0% found this document useful (0 votes)
8 views19 pagesAddress Resolution Protocol
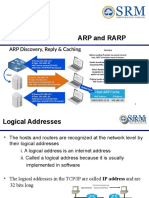
The Address Resolution Protocol (ARP) is essential for mapping IP addresses (L3) to MAC addresses (L2) in a network, facilitating packet delivery. The document discusses various ARP iterations, including Traditional ARP, Proxy ARP, and others, detailing their processes and use cases. It emphasizes the importance of ARP in enabling communication between devices on the same or different networks and addresses how ARP entries are maintained in an ARP Cache.
Uploaded by
rashmi mCopyright
© © All Rights Reserved
We take content rights seriously. If you suspect this is your content, claim it here.
Available Formats
Download as DOCX, PDF, TXT or read online on Scribd
0% found this document useful (0 votes)
8 views19 pagesAddress Resolution Protocol
The Address Resolution Protocol (ARP) is essential for mapping IP addresses (L3) to MAC addresses (L2) in a network, facilitating packet delivery. The document discusses various ARP iterations, including Traditional ARP, Proxy ARP, and others, detailing their processes and use cases. It emphasizes the importance of ARP in enabling communication between devices on the same or different networks and addresses how ARP entries are maintained in an ARP Cache.
Uploaded by
rashmi mCopyright
© © All Rights Reserved
We take content rights seriously. If you suspect this is your content, claim it here.
Available Formats
Download as DOCX, PDF, TXT or read online on Scribd
/ 19