0% found this document useful (0 votes)
4 views4 pagesTask 9
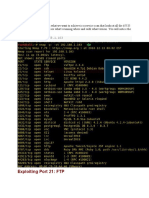
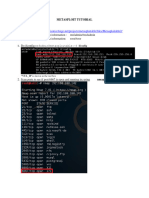
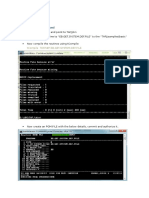
The document outlines a task involving the use of the Metasploit framework for penetration testing, specifically focusing on reconnaissance and exploitation of the Metasploitable 2 virtual machine. It details the installation process of Metasploitable 2 in VirtualBox, including network configuration and connectivity checks between Kali Linux and Metasploitable 2. The document also describes the exploitation of a vulnerability in the Metasploitable 2 machine using Metasploit commands to gain access through an identified weak point.
Uploaded by
prabhuaiCopyright
© © All Rights Reserved
We take content rights seriously. If you suspect this is your content, claim it here.
Available Formats
Download as DOCX, PDF, TXT or read online on Scribd
0% found this document useful (0 votes)
4 views4 pagesTask 9
The document outlines a task involving the use of the Metasploit framework for penetration testing, specifically focusing on reconnaissance and exploitation of the Metasploitable 2 virtual machine. It details the installation process of Metasploitable 2 in VirtualBox, including network configuration and connectivity checks between Kali Linux and Metasploitable 2. The document also describes the exploitation of a vulnerability in the Metasploitable 2 machine using Metasploit commands to gain access through an identified weak point.
Uploaded by
prabhuaiCopyright
© © All Rights Reserved
We take content rights seriously. If you suspect this is your content, claim it here.
Available Formats
Download as DOCX, PDF, TXT or read online on Scribd
/ 4