28th Telecommunications forum TELFOR 2020 Serbia, Belgrade, November 24-25, 2020.
Overview of SQL Injection Defense
Mechanisms
Igor Tasevski, Faculty of Informatics, AUE-FON – Skopje, R.N. Macedonia;
Kire Jakimoski, IEEE Senior Member, Faculty of Informatics, AUE-FON – Skopje, R.N. Macedonia;
Access to databases is via website or APIs using a
Abstract — Today, in the era of rapidly changing and language called SQL (structured query language). Many of
evolving IT Technology, the Internet Network has become the websites are vulnerable to hacker attacks, that may
one of the main daily needs of mankind. However, web further launch backdoor attacks [3] as a result of bad
applications such as online banking, web-based emails, social
networking that are instant means of communication, are
coding practices that do not comply with coding standards.
targeted by attackers where their main goal is to get Hackers are sending huge amounts of bots that are meant
important information about users and use them for their to find websites that have vulnerabilities in the code. In
own purpose. One of the methods of targeting web some cases, specific websites can be targeted as a result of
applications and web-based information systems is using the the value that data itself has and hackers themselves want
SQL injection attacks. In this work main subject of the to reach. In both cases, however simply writing good code
research is analysis of the methods of SQL injection attacks
and creating an overview of the best defense mechanisms for is the first phase of protection in order to have healthy
detection and prevention of SQL injection attacks. basis for further system protection.
Furthermore, practical simulation of SQL injection attack is The main purpose of this paper will be to create an
done using Kali-Linux platform for sensing the real threat overview of the key defense mechanisms in order to
from this kind of cyber-attack. Analysis of the best practices protect users’ information from injecting SQL attacks.
for defense from this kind of attacks is presented after the
Analysis of the solutions and techniques for defending
practical simulation. Aim of this is users to be more aware
against this kind of cyber security attacks. against SQL attacks [4] is needed for minimizing the risks
Keywords — Cyber Security, SQL Injection Attack, for this kind of attacks. Also, for our needs virtual machine
Vulnerability, Web Application Attacks, Kali-Linux, with Kali-Linux [5] is used for simulation purpose of real
SQLMap Tool. SQL injection attack.
The remainder of this paper is organized as follows:
I. INTRODUCTION Section 2 gives overview of the types of SQL injection
S QL INJECTION in simple terms is the process of passing
SQL code into interactive web applications. They
accept user input such as form and then they include this
attacks in order to explain possible options for attacks.
Section 3 presents the simulation scenario results of SQL
Injection attack. Purpose of this section is users to rise
input in database requests, but in a way that was not their awareness for this kind of cyber-attacks. Section 4
intended. Main reason is to trick the database executing gives overview of the key defense mechanisms against
malicious code due to the poor design of the application SQL Injection attacks after deep analysis of the scientific
[1]. SQL injection attacks are known long time ago, but results. Purpose of this section is to analyze the most
they still pose a serious threat. Today we all live in what important defense mechanisms and present them to the
we call the information age, with no threat of being left users. Section 4 concludes the paper.
without information. There is general perception that we
are overloaded with data, with the ability to store, process,
analyze and secure the data becoming our primary concern II. TYPES OF SQL INJECTION ATTACKS
[2]. For large multinational organizations such as financial
industry, health care industry etc., the situation has become There are different ways to attack using SQL injection.
very complex and challenging. The question that arises Attackers could bypass authentication and access, modify
here is how we will store and process this data maintaining and delete data in databases. Using SQL injection attackers
their secrecy, availability and confidentiality. In many could even execute command on the operating systems. In
cases, large amount of data is stored in databases but this way attackers could perform more serious attacks
before that happens relations between them are created. inside the network behind the firewall. Hence, SQL
injection attacks could be classified in the following types
of attacks.
K. Jakimoski, I. Tasevski are with the Faculty of Informatics, AUE- Error-based SQL injection
FON, Bul. Kiro Gligorov 5, 1000 Skopje, R.N. Macedonia; (e-mail:
kire.jakimoski@fon.edu.mk; igor.tasevski@fon.mk). Error-based SQL injection is very common type of SQL
injection vulnerability. It is based on unexpected
978-1-6654-0499-0/20/$31.00 ©2020 IEEE
Authorized licensed use limited to: UNIVERSITY OF CONNECTICUT. Downloaded on May 23,2021 at 00:45:44 UTC from IEEE Xplore. Restrictions apply.
�commands or invalid input, through a user interface. As a complicated to exploit because there is information
result of this, database server replies with an error that may returned when the application is given SQL payloads.
contain information about the target like structure, version,
operating system or returns full query results. There are two types of blind SQL-injection: boolean-based
and time based.
Boolean-Based Blind SQL injection
In this type of SQL injection attack, a Boolean query
causes the application to give a different response for a
valid or invalid result in the database. It works by
enumerating the characters from the text that needs to be
extracted. The reply shows if the user ID is present in the
database or not.
Time-Based Blind SQL injection
In this type of SQL injection attack, SQL query is sent to
the database which forses it to wait for a specified amount
of time expressed in seconds before responding. Attacker
will know from the response time whether the result of the
query is true or false.
Fig. 1. SQL Injection Attack Scenario
Out-of-band SQL injection
Union-based SQL injection This is not very common type of SQL injection attack,
mostly because it depends on features being enabled on the
Results that are returned by the original query are extended database server. This type of attack occurs when the
by the Union operator. In this way users are enabled to run attacker cannot use the same channel to execute the attack
two or more statements if the structure is the same as the and gather results.
original one. For this purpose, let’s analyze this example
[6]:
Example: SELECT first_name, last_name FROM users
UNION SELECT username, password FROM login;
III. SQL INJECTION ATTACK SIMULATION SCENARIO
In this example SELECT command is used and the In order readers to have clearer picture of the nature of the
following conditions should be fulfilled in order exploit to real SQL injection attacks, in this section practical attack
work: on random web site is demonstrated using the VMware
virtual environment with Kali-Linux operation system and
-Each SELECT statement within union has the same SQLmap tool [7]. SQLmap tool offers many features, per
number of columns; example, support of different types of attack and support
- The columns must also have similar data types; for most database management systems.
-The columns in each SELECT statement are in the Simulation scenario was obtained using the Kali-Linux
same order. operation system on VMware. SQL Injection attack
scenario is presented in Fig. 1. First phase of the attack
In this example names of the columns in the table users are scenario was identifying the vulnerable parameter. All
first_name and last_name. Names of the columns in the testing is done on testphp.vulnweb.com free test and
table login are username and password. demonstration site for Acunetix Web Vulnerability
Scanner [8]. Next phase was to decide which SQL
The query is successful when it has the correct numbers of injection techniques could be used to exploit the
columns. vulnerable parameter and take control of the entire
database with all sensitive data like names, passwords,
tables, columns, hashes, privileges or roles.
Blind SQL injection
The vulnerable website shows warning message with
Blind SQL injection is type of SQL injection attack that errors: “You have an error in your SQL syntax: check the
does not show error message. Hence, it is more
Authorized licensed use limited to: UNIVERSITY OF CONNECTICUT. Downloaded on May 23,2021 at 00:45:44 UTC from IEEE Xplore. Restrictions apply.
�manual that corresponds to your MYSQL server version IV. OVERVIEW OF THE KEY DEFENSE MECHANISMS
for the right syntax to use near \ at line 1“. AGAINST SQL INJECTION ATTACKS
Although there is no such thing as a foolproof solution in
Attack is performed on the following website for pen network security, key defense mechanisms against SQL-
testing: injection attempts are the following:
http://testphp.vulnweb.com/listproducts.php?cat=1
Next phase was to list all databases using SQL Injection
attack. With further testing for vulnerabilities it was found
that the back-end database is MySQL, and the web
application technology is PHP. Further analysis has shown
that there are two available databases: acuart and
information_schema, presented in Fig. 2.
Information_shema is standard database, so our main focus
will be acuart database.
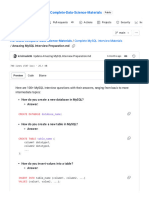
Fig. 2 Testing the vulnerabilities of the site
Fig. 3 Listing columns of Table users
Next what of the attack scenario was to check how many
tables this database has, and to collect information about
the name of the tables and other important data. For this
purpose, the following command is used:
root@Kali:~# sqlmap -u
http://testphp.vulnweb.com/listproducts.php?cat=1 D
acuart --tables
In this phase of the SQL injection attack, it was found that
this database has 8 tables. Our further interest was to get
more detailed information about the users and their Fig. 4 Retrieving user name login credentials
credentials. For this purpose we used the following
command:
root@Kali: #sqlmap -u - Filtering
“http://testphp.vulnweb.com/listproducts.php?cat=1” – D Everything should be sanitazed by filtering user
acuart -T users –columns data by context. For example, email addresses
should be filtered to allow only the characters
allowed in an e-mail address, phone numbers
After executing the above presented command we’ve got should be filtered to allow only the digits in a phone
the columns from Table users using the database acuart number and etc. Creating a list of approved
(Figure 3). characters is an efficient method to defend against
SQL injection attacks [9]. Once the whitelist is
Our final goal in this attack scenario was to get the ready, the application should disallow all requests
username login credentials in order to gain full access of containing characters that are not in it.
the database. After successful retrieving the victim’s login
credentials (Figure 4), we can further manipulate with the - Cloudflare Website Protection
data in our advantage. This is solid protection against all kind of
unauthorized attempts [10] of gaining access on the
target website, customer data, compromise and
abusive bots. This type of protection also includes
features like under attack mode [11], where the
client should be able to answer to the java script
challenge.
Authorized licensed use limited to: UNIVERSITY OF CONNECTICUT. Downloaded on May 23,2021 at 00:45:44 UTC from IEEE Xplore. Restrictions apply.
� on web application using SQLMap tool from Kali –Linux
- HTTPS usage is demonstrated. After this part, detailed explanation of
Websites should use HTTPS [12] which will enable methods for exploiting web site vulnerabilities is obtained
to have encrypted data while sending it over the in this work. Presented defense mechanisms reduce the
Internet. This is one of the key defense mechanisms risks for this kind of attacks to minimum level. One of the
for SQL Injection Attacks and is “must” for web main goals of this paper is to rise the awareness of the
applications. users of web applications by presenting real simulation
scenario of SQL injection attack. Furthermore, goal of this
paper is to present the key defence mechanisms for
- Don’t use dynamic SQL detection and prevention of SQL injection attacks. This is
Data sanitazion routines can be also flawed, so this especially important for website and computer network
means we can use prepared statements [13] or administrators.
stored procedures instead whenever possible. But,
also we must be aware that while stored procedures
prevent some types of SQL injection attacks, they
fail to protect against many others. Hence, we REFERENCES
shouldn’t rely exclusively on their usage in our [1] Cui Z, Xue F, Cai X, Cao Y, Wang GG, Chen J. Detection of
defense. malicious code variants based on deep learning. IEEE Transactions on
Industrial Informatics. 2018 Apr 3;14(7):3187-96.
[2] Salijeni G, Samsonova-Taddei A, Turley S. Big Data and changes in
- Update and Patch audit technology: contemplating a research agenda. Accounting and
It’s very vital to apply patches and updates because Business Research. 2019 Jan 2;49(1):95-119.
[3] Prasad R, Rohokale V. Cyber Threats and Attack Overview. InCyber
hackers can find them and expliot with SQL- Security: The Lifeline of Information and Communication Technology
injection attempts. 2020 (pp. 15-31). Springer, Cham.
[4] Nagpal B, Chauhan N, Singh N. A survey on the detection of SQL
- Encryption injection attacks and their countermeasures. JIPS (Journal of Information
Processing Systems). 2017;13(4):689-702.
Act accordingly by encypting or hashing passwords
[5] Hertzog R, O'Gorman J. Kali Linux Revealed: Mastering the
and other confidential data [14]. Penetration Testing Distribution. Offsec Press; 2017 Jun 5.
[6] Satyam Singh. Common SQL Injection Attacks. April 23, 2019.
- Monitor SQL Statements Avaliable: https://pentest-tools.com/blog/sql-injection-attacks/
This will help identify rogue SQL statements and [7] Gudipati VK, Venna T, Subburaj S, Abuzaghleh O. Advanced
automated SQL injection attacks and defensive mechanisms. In 2016
vulnerabilities [15]. Monitoring tools that utilize Annual Connecticut Conference on Industrial Electronics, Technology &
machine learning or behavioral analysis can be Automation (CT-IETA) 2016 Oct 14 (pp. 1-6). IEEE.
especially useful. [8] Erturk E, Rajan A. Web Vulnerability Scanners: A Case Study. arXiv
preprint arXiv:1706.08017. 2017 June 25.
[9] Mitropoulos D, Louridas P, Polychronakis M, Keromytis AD.
Defending against web application attacks: approaches, challenges and
In this work the pen-testing was done on test site which is implications. IEEE Transactions on Dependable and Secure Computing.
intentionaly vulnerable, so we can better understand and 2017 Mar 1;16(2):188-203.
also be aware how even the smallest mistakes and bad [10] Dewi, Estri JH, Umar Rusydi, and Riadi Imam. Implementation of
Cloudflare Hosting for Speeds and Protection on The Website. Diss.
configuration can lead someone to hack into our website. Universitas Ahmad Dahlan, 2019.
In this work only the personal data of the victim are [11] Wu C, Wu L, Liu J, Jiang ZP. Active defense-based resilient sliding
obtained – in this case the user password. But however, in mode control under denial-of-service attacks. IEEE Transactions on
real life situation the attacker will try to do much more and Information Forensics and Security. 2019, May 16; 15:237-49.
[12] Krombholz K, Busse K, Pfeffer K, Smith M, von Zezschwitz E. " If
cause even more damage. Before websites goes life, HTTPS Were Secure, I Wouldn't Need 2FA"-End User and
responsible website and computer network administrators Administrator Mental Models of HTTPS. In2019 IEEE Symposium on
should make all the necessary cheks mentioned above, in Security and Privacy (SP) 2019 May 19 (pp. 246-263). IEEE.
order to prevent any kind of unathorized access and reduse [13] Alwan ZS, Younis MF. Detection and prevention of SQL injection
attack: A survey. International Journal of Computer Science and Mobile
the risk of data breach. Computing. 2017 Aug;6(8):5-17.
[14] Varadarajan S, Lal R, Triplett J, inventors; Intel Corp, assignee.
Systems and methods for providing confidentiality and privacy of user
V. CONCLUSION data for web browsers. United States patent US 10,462,135. 2019 Oct
29.
In this paper, analysis of the key defense mechanisms [15] Pollack E. Protecting Against SQL Injection. InDynamic SQL 2019
against SQL injection attacks is done. For this purpose, (pp. 31-60). Apress, Berkeley, CA.
real attack scenario using SQL injection attack is obtained
in simulation envrionment. Practical SQL Injection attack
Authorized licensed use limited to: UNIVERSITY OF CONNECTICUT. Downloaded on May 23,2021 at 00:45:44 UTC from IEEE Xplore. Restrictions apply.