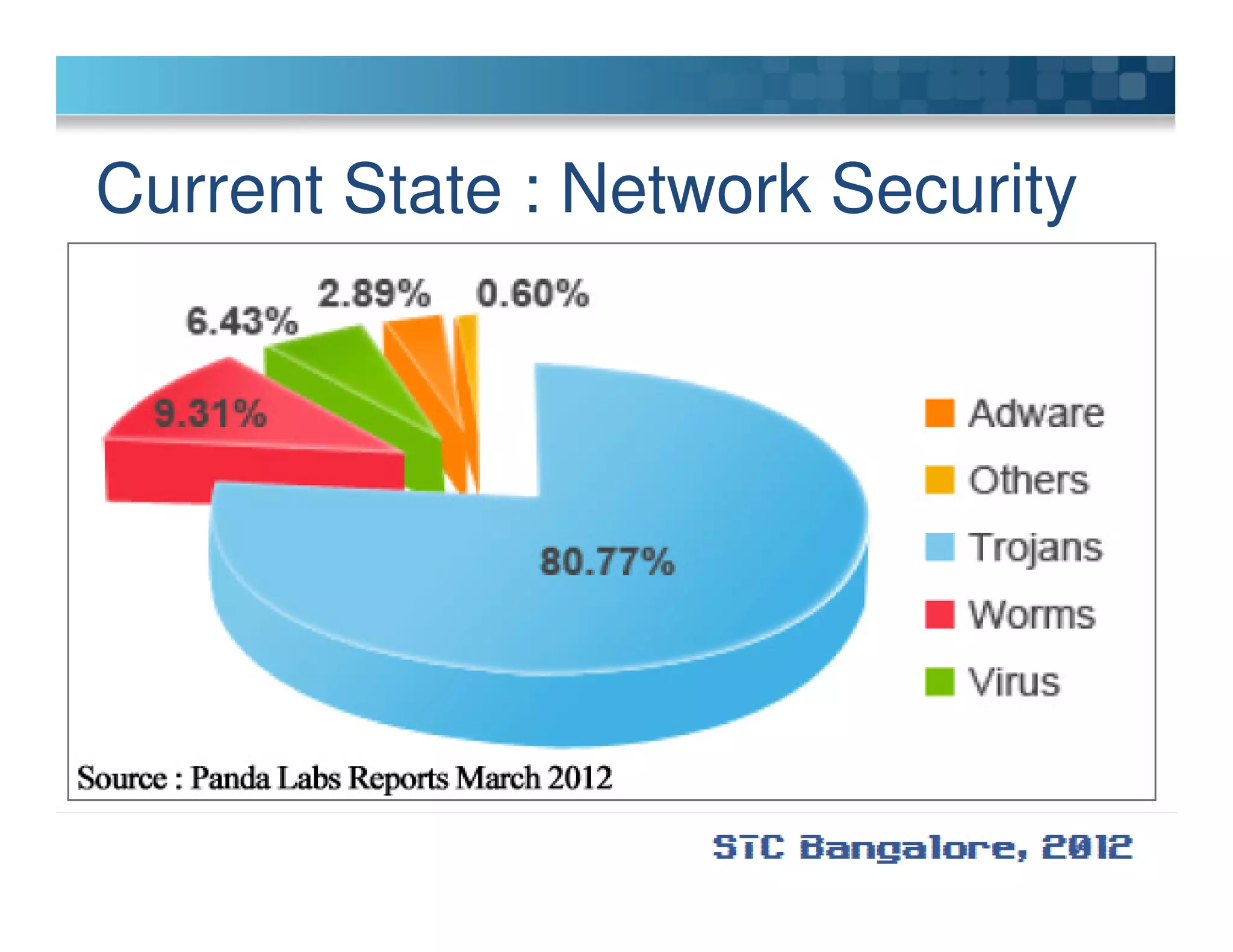
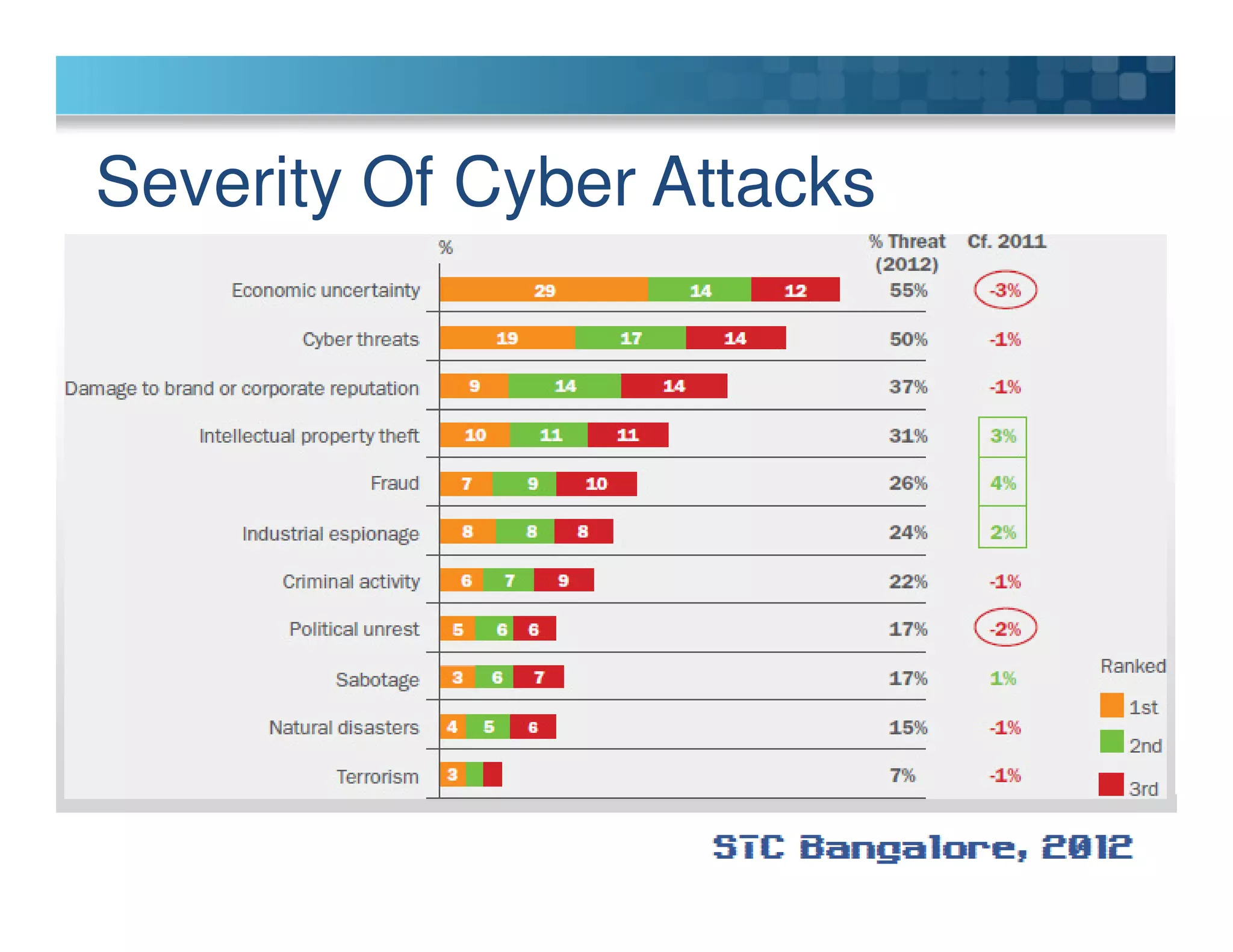
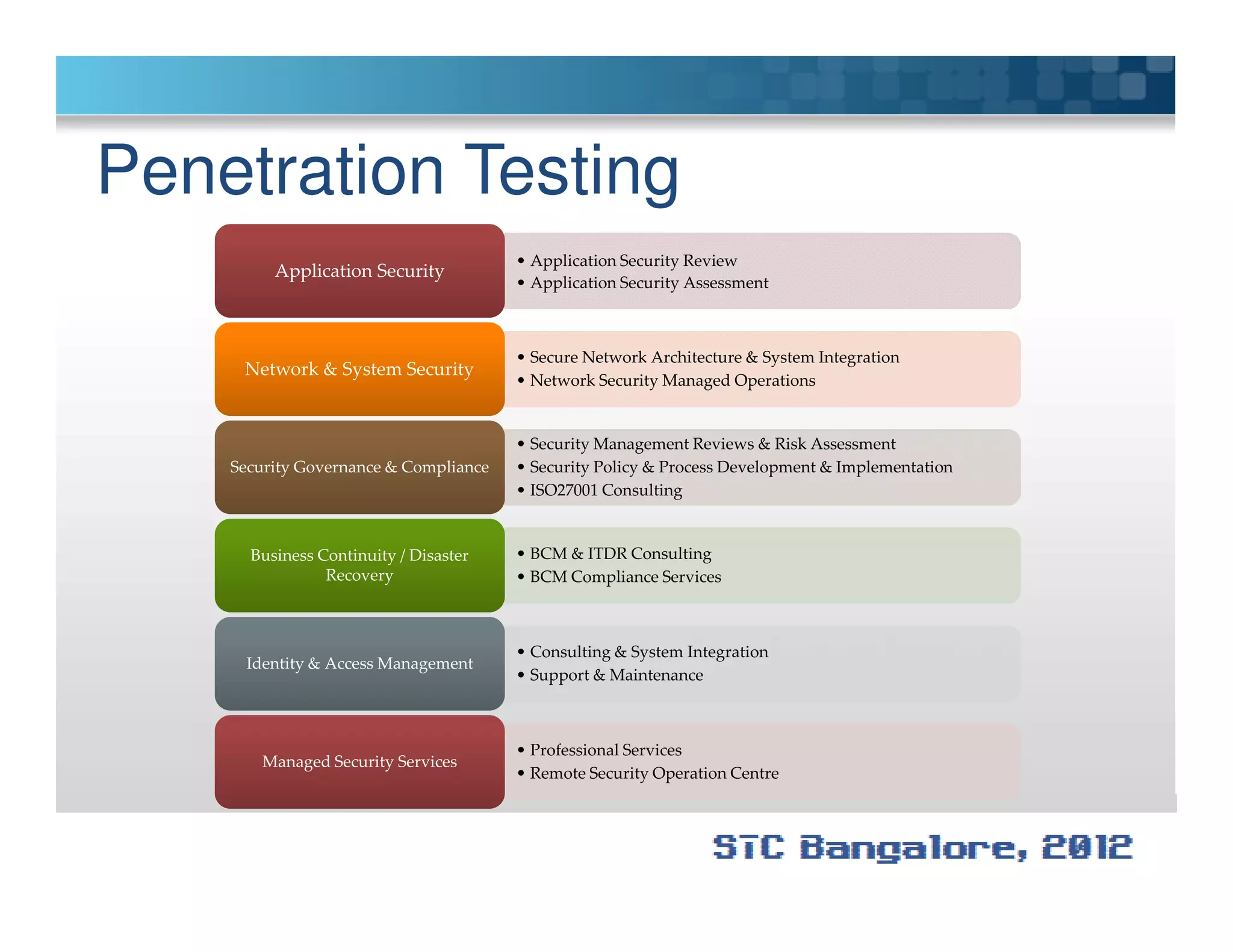
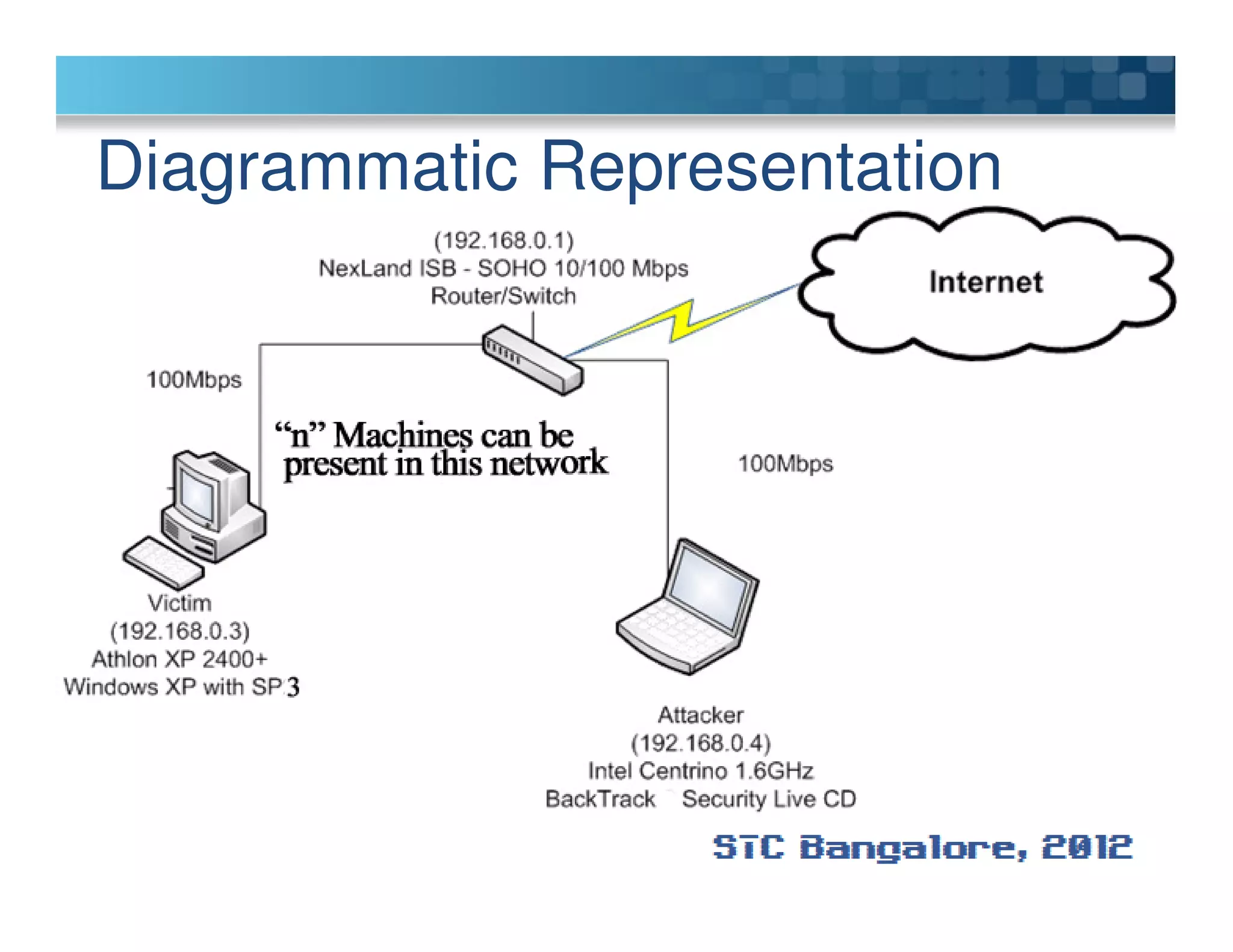
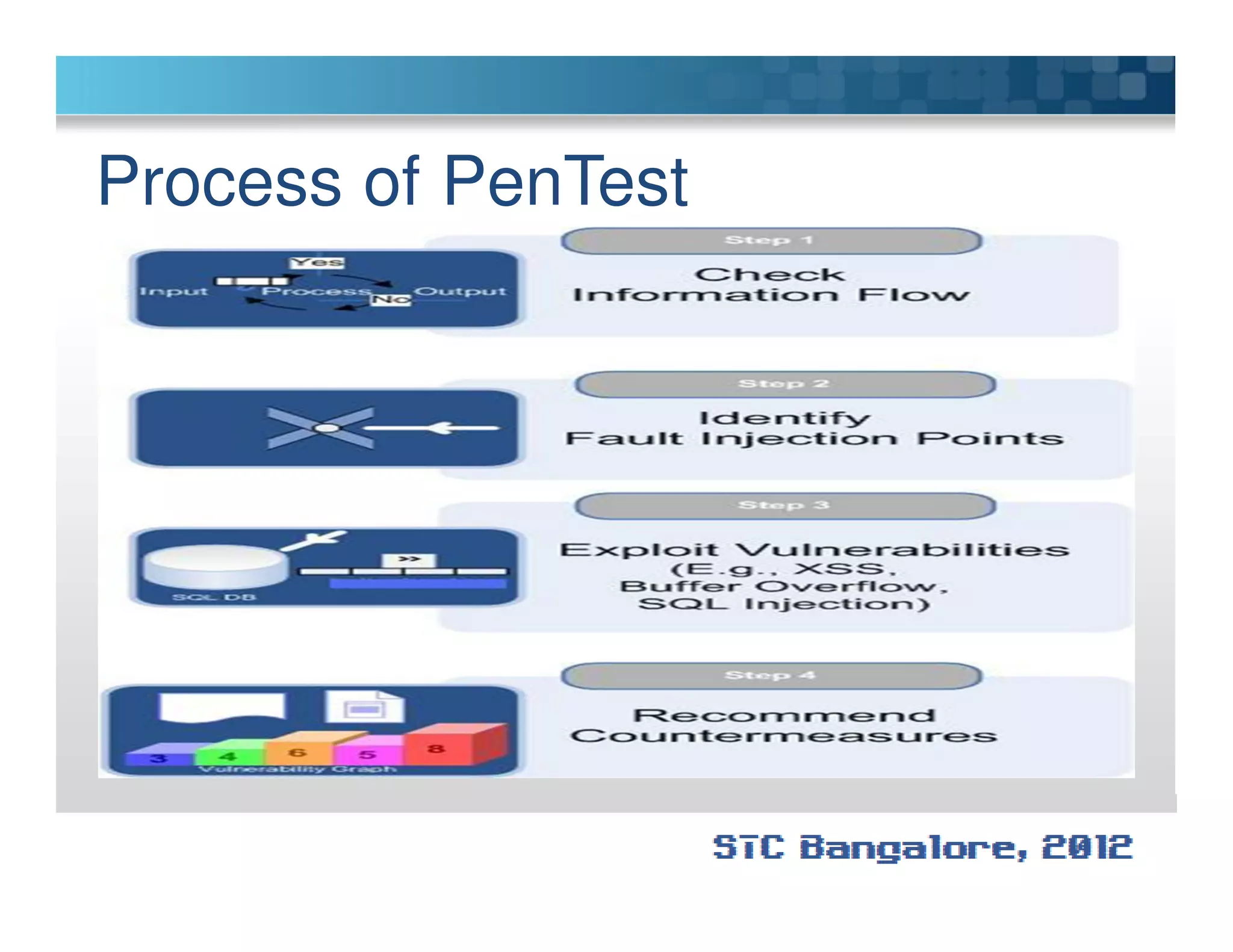
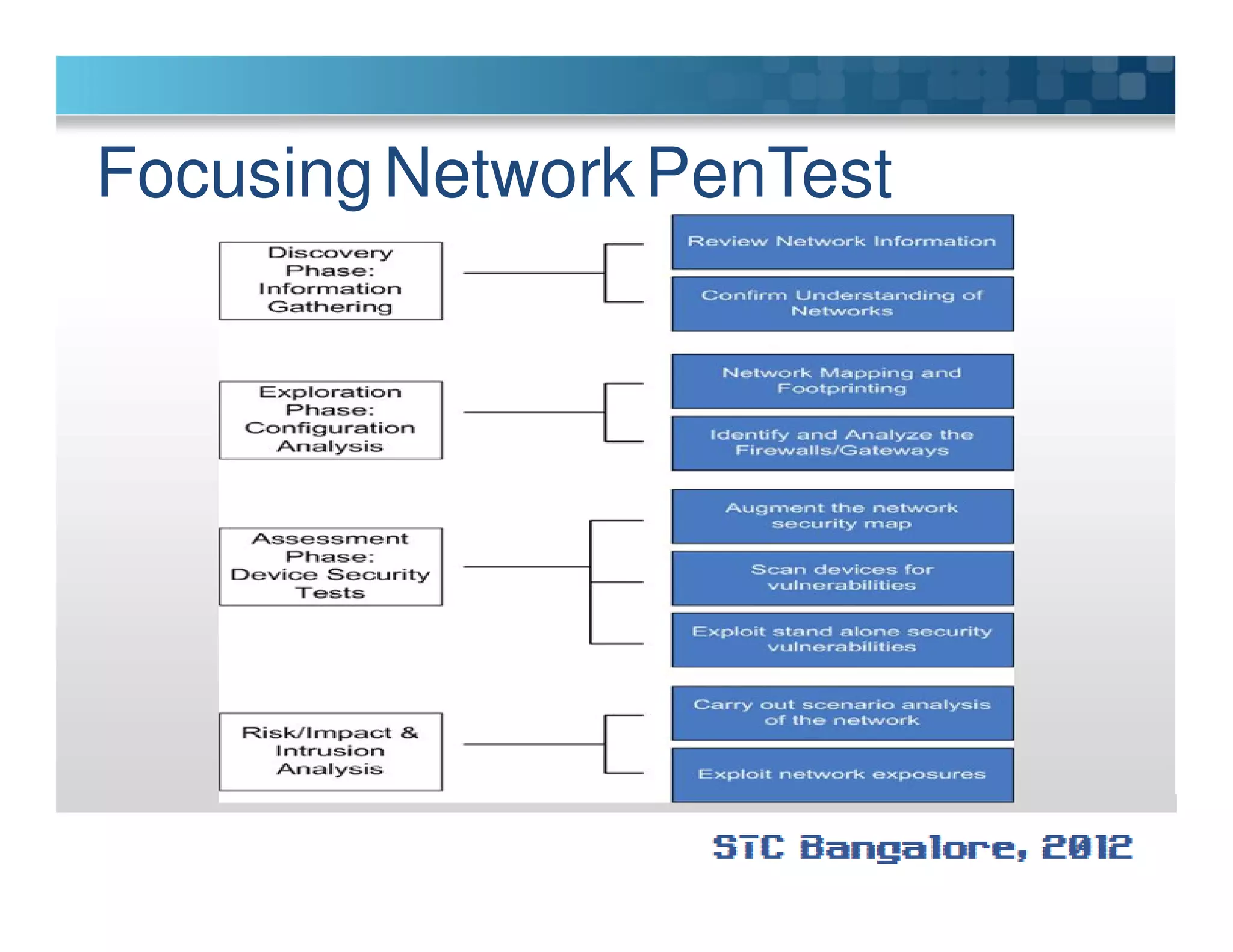
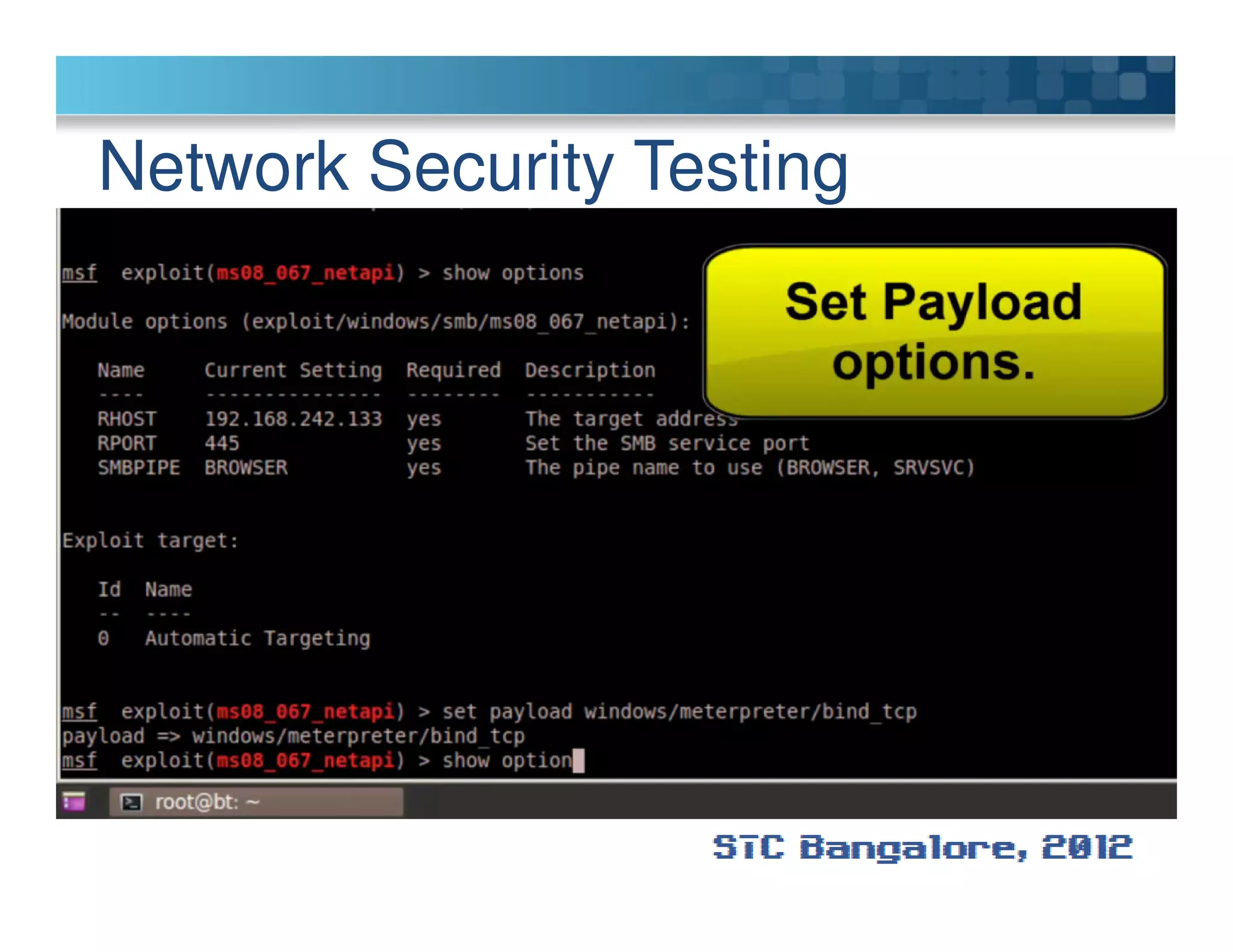
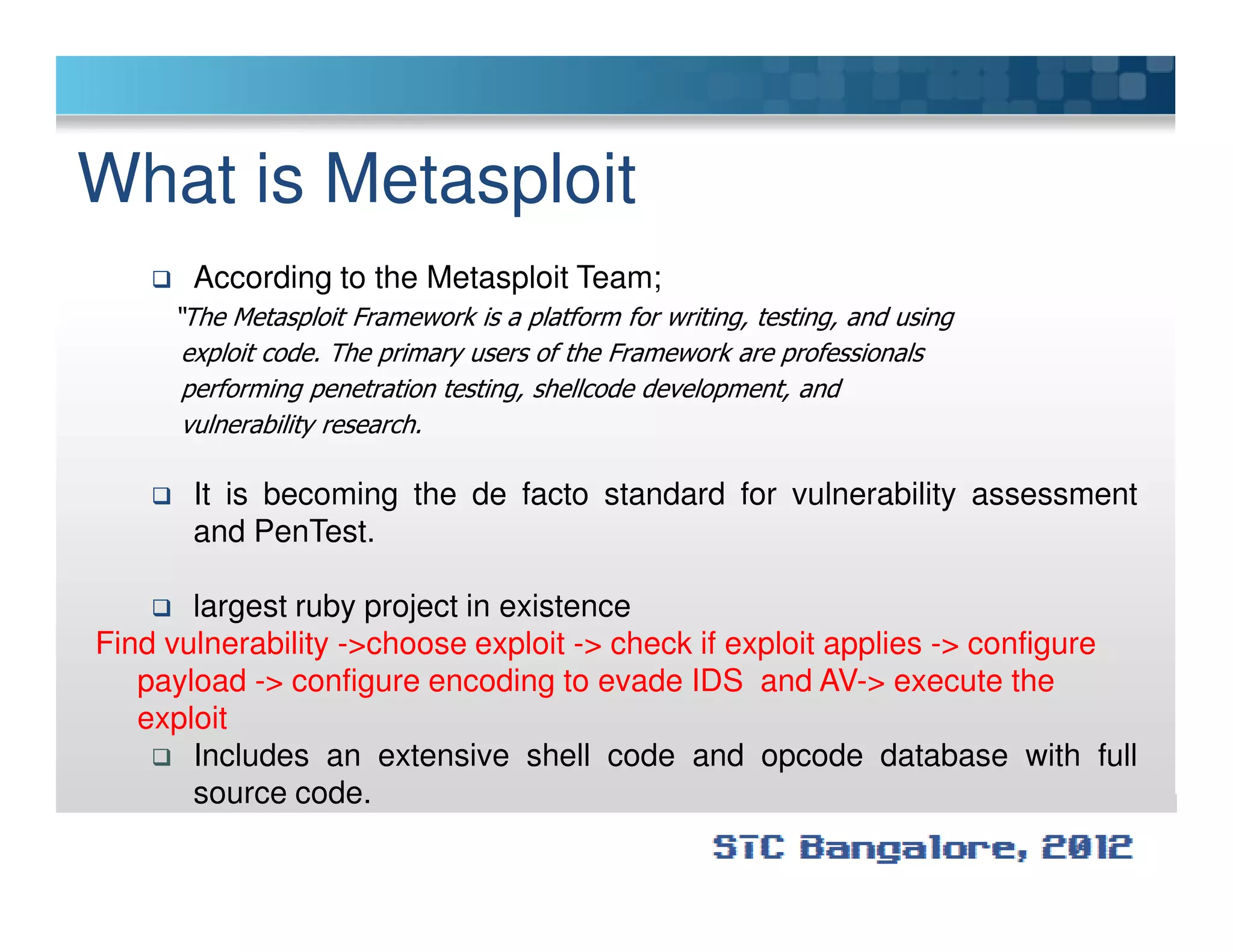
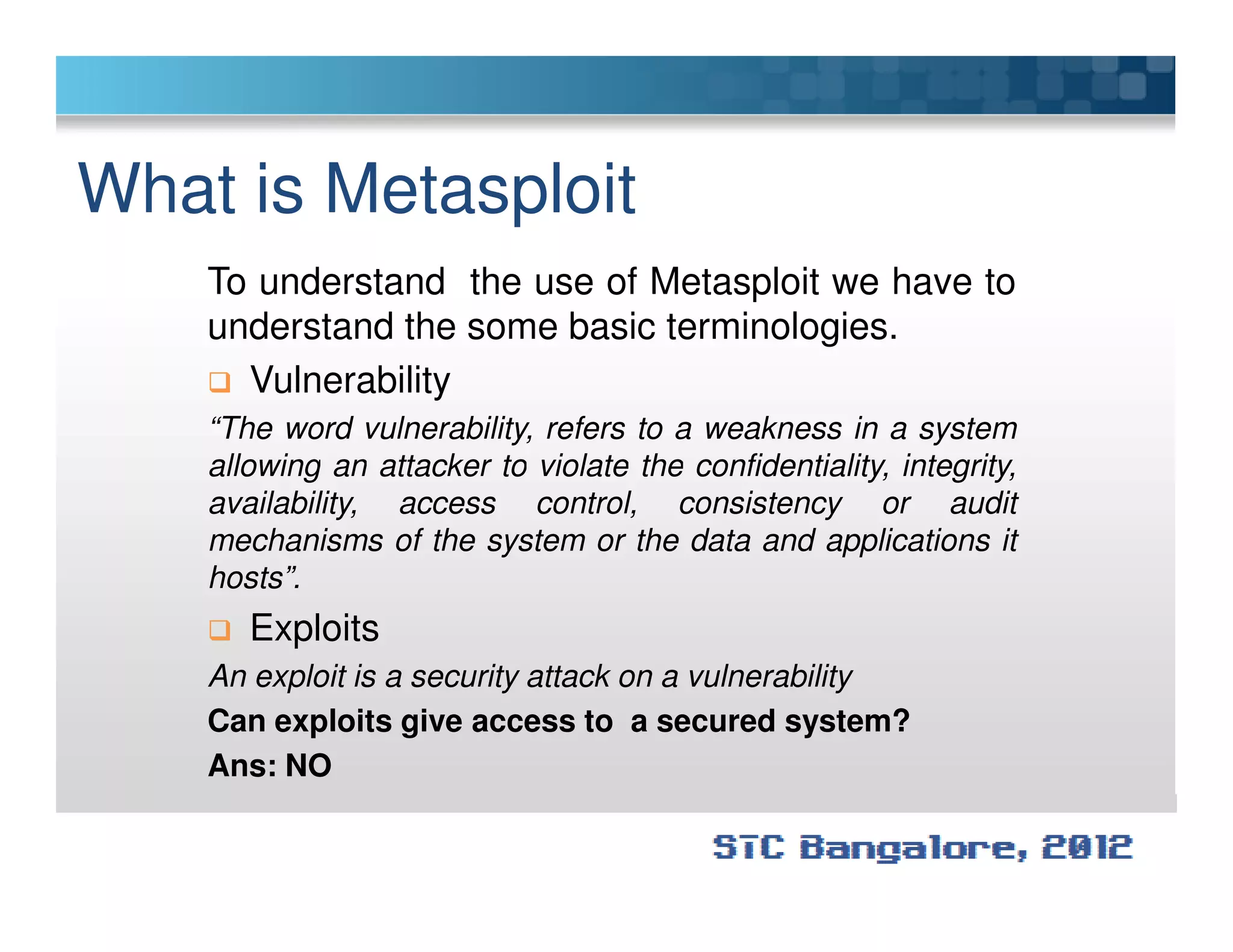
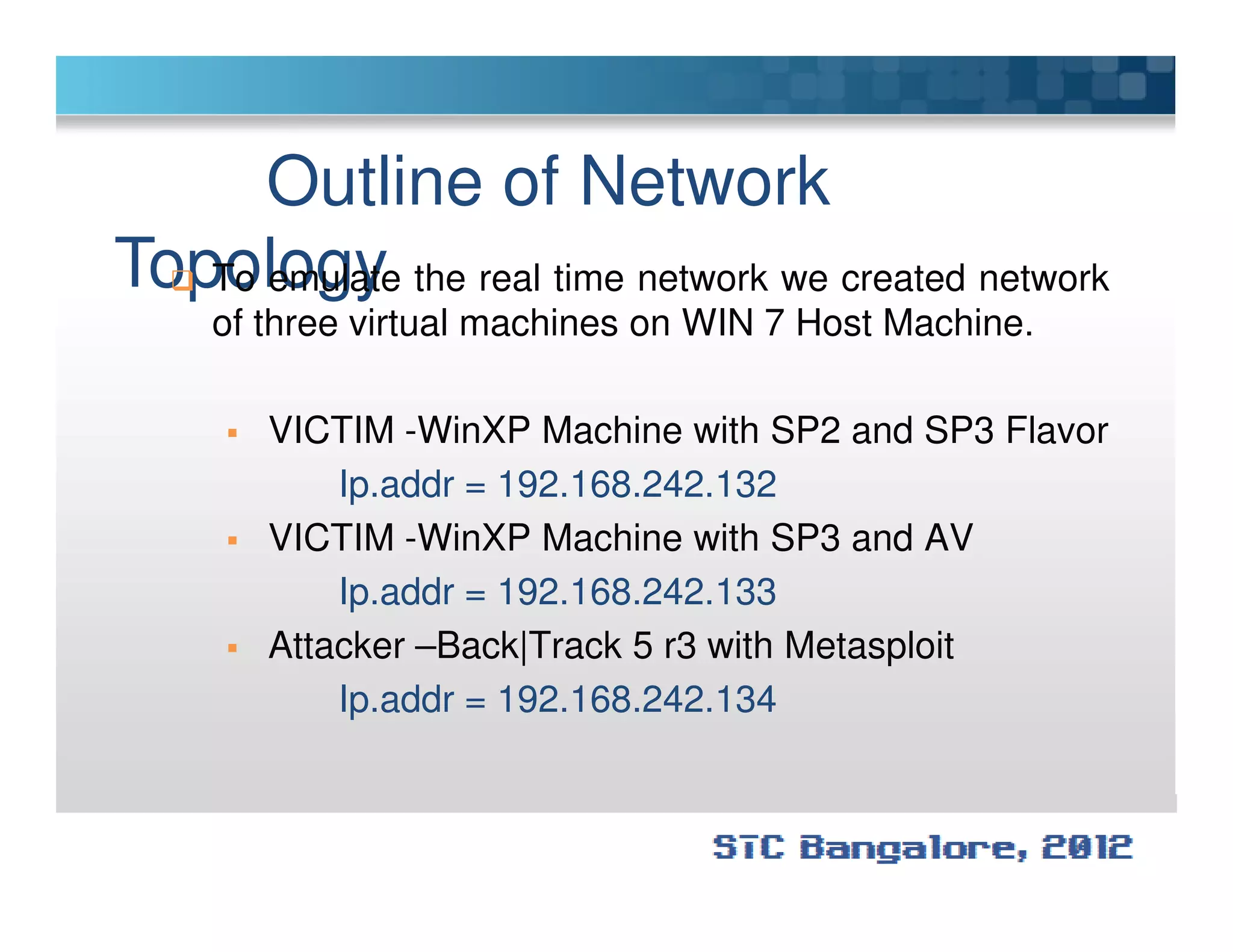
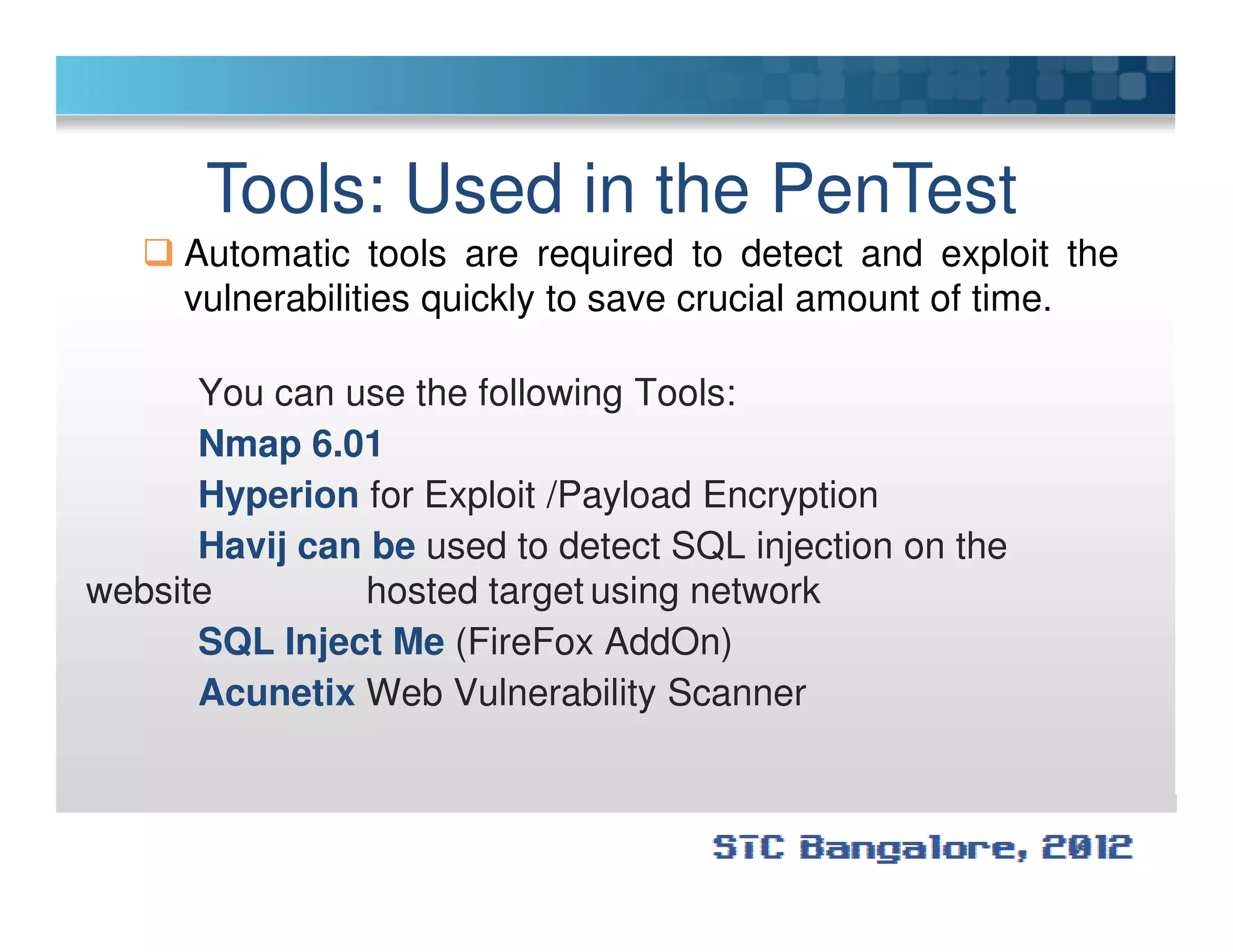
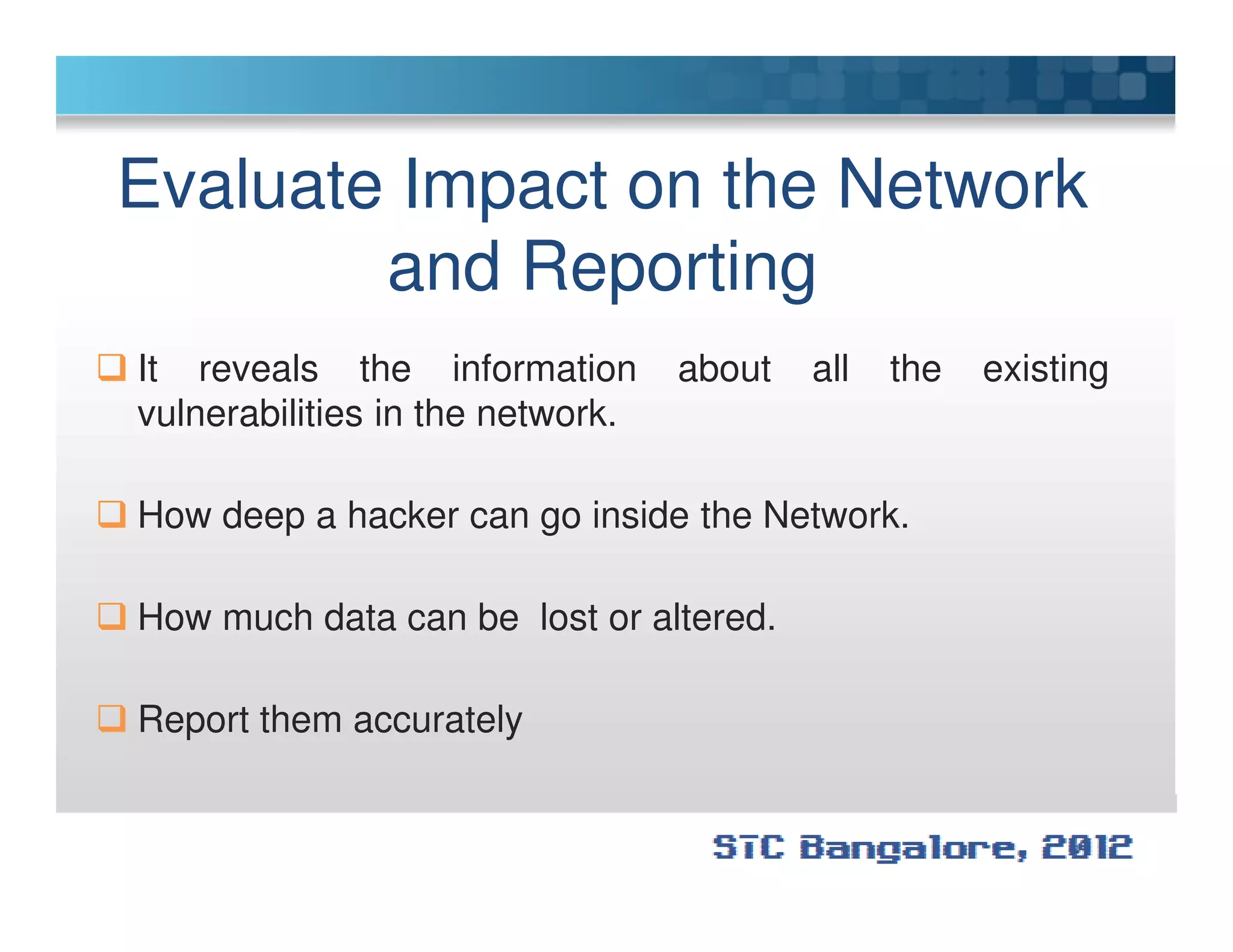
The document discusses penetration testing using Metasploit. It begins by defining penetration testing and why it is important for security. It then provides an overview of Metasploit, explaining what it is and some key terminology. The document demonstrates a sample penetration test against a virtual network, using Metasploit to exploit a Windows vulnerability. It evaluates the impact and recommends countermeasures like patching, code reviews, and periodic testing. The goal is to show how Metasploit can be used to test network security by simulating real-world attacks.