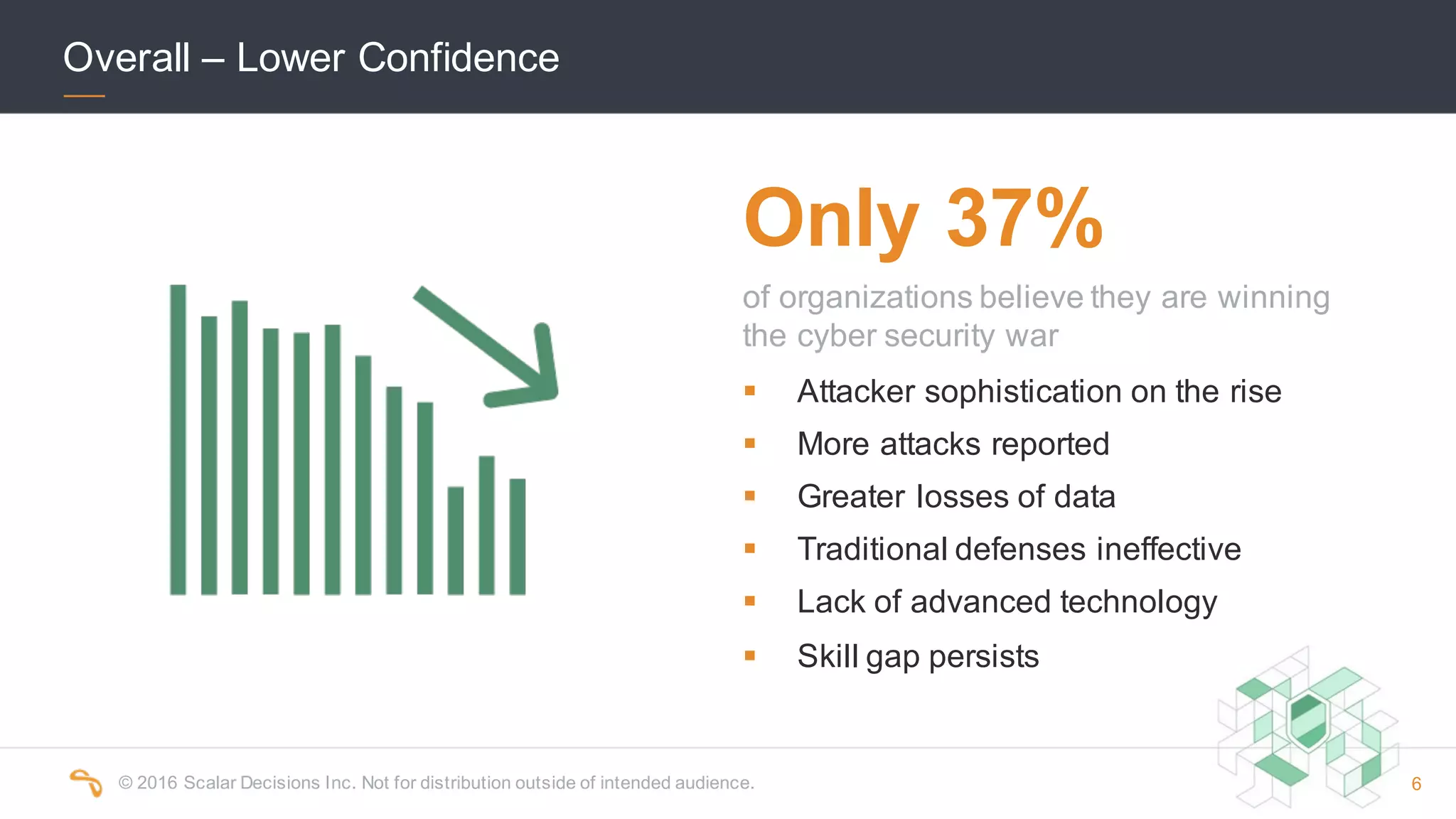
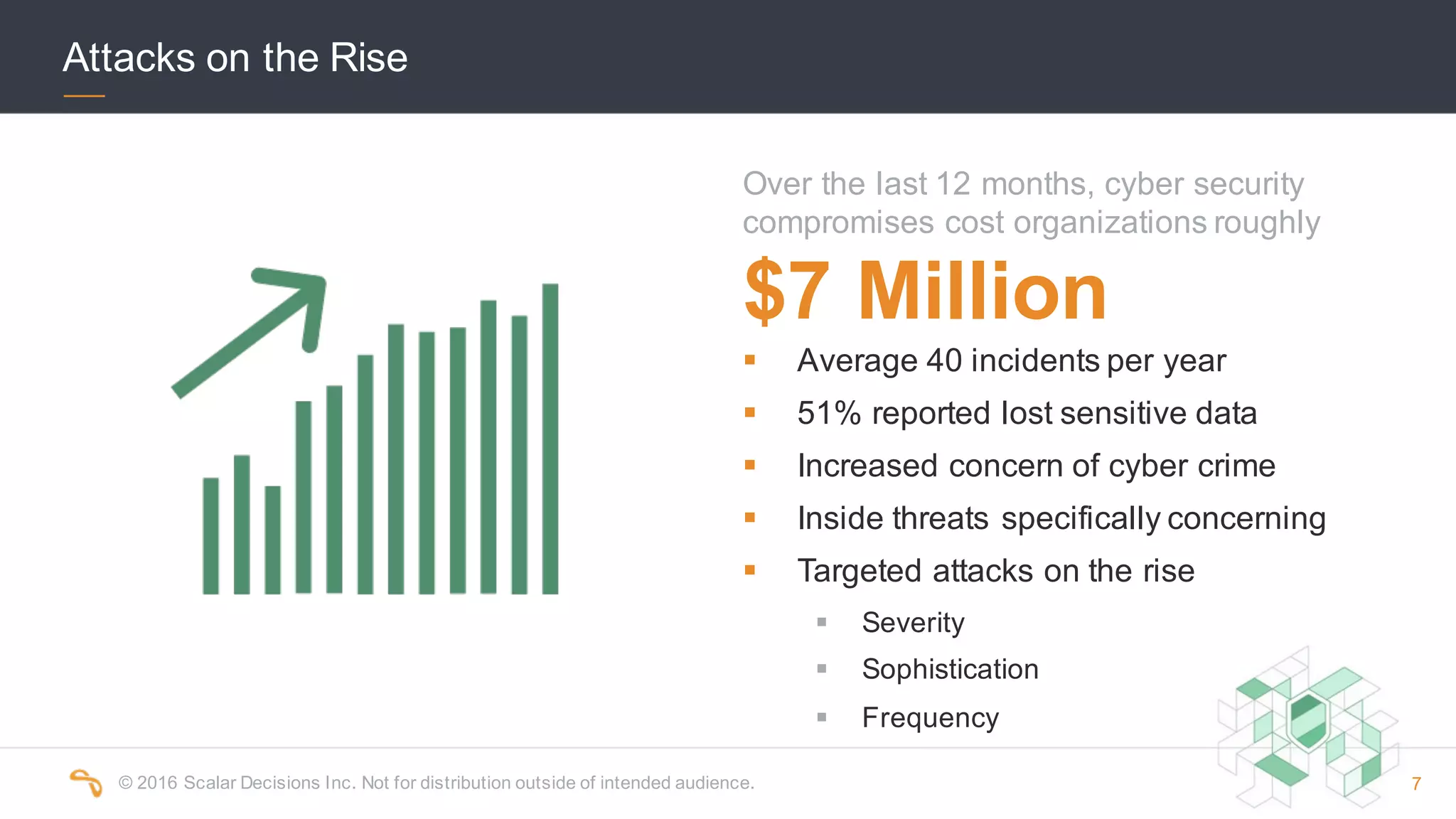
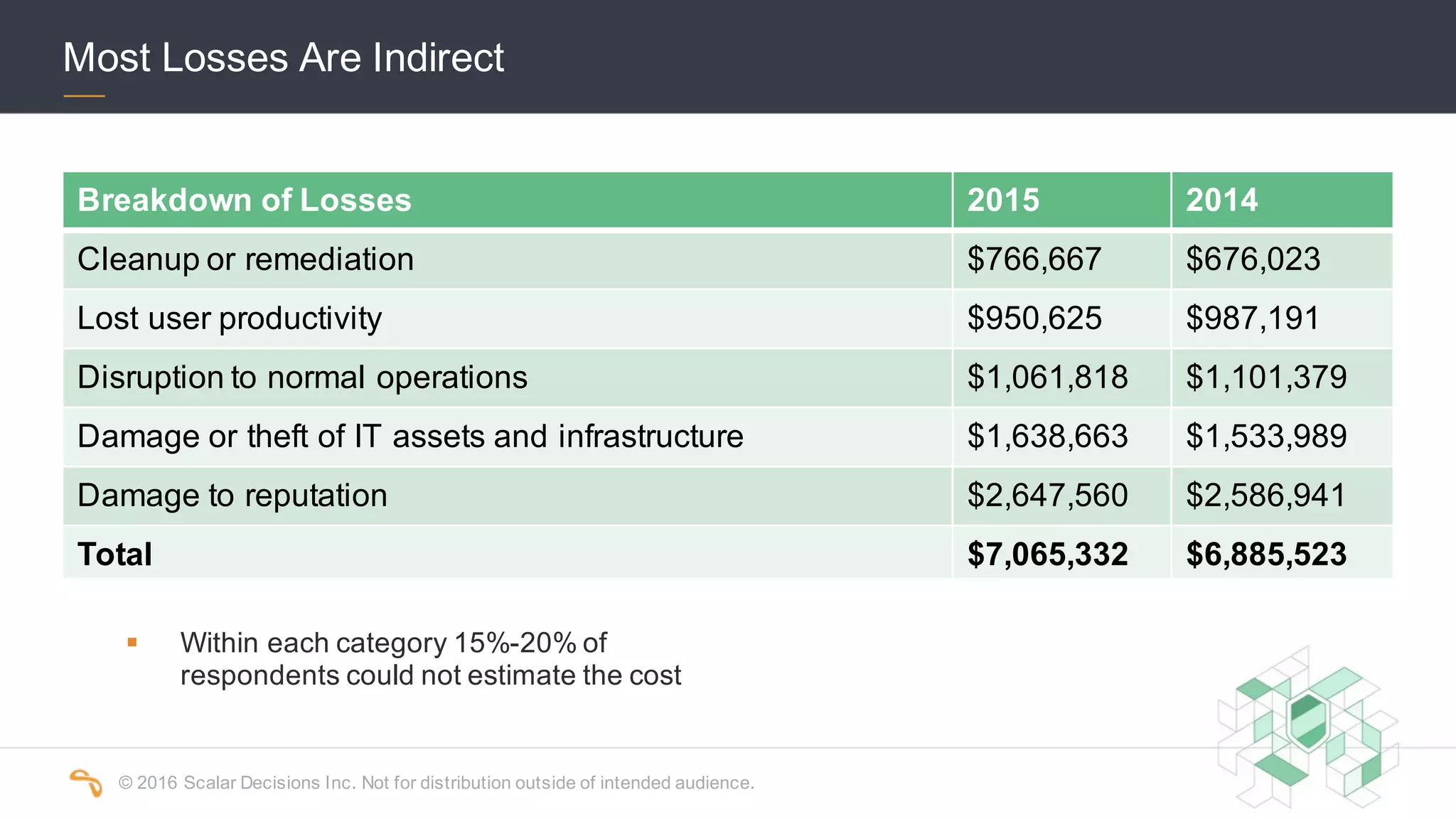
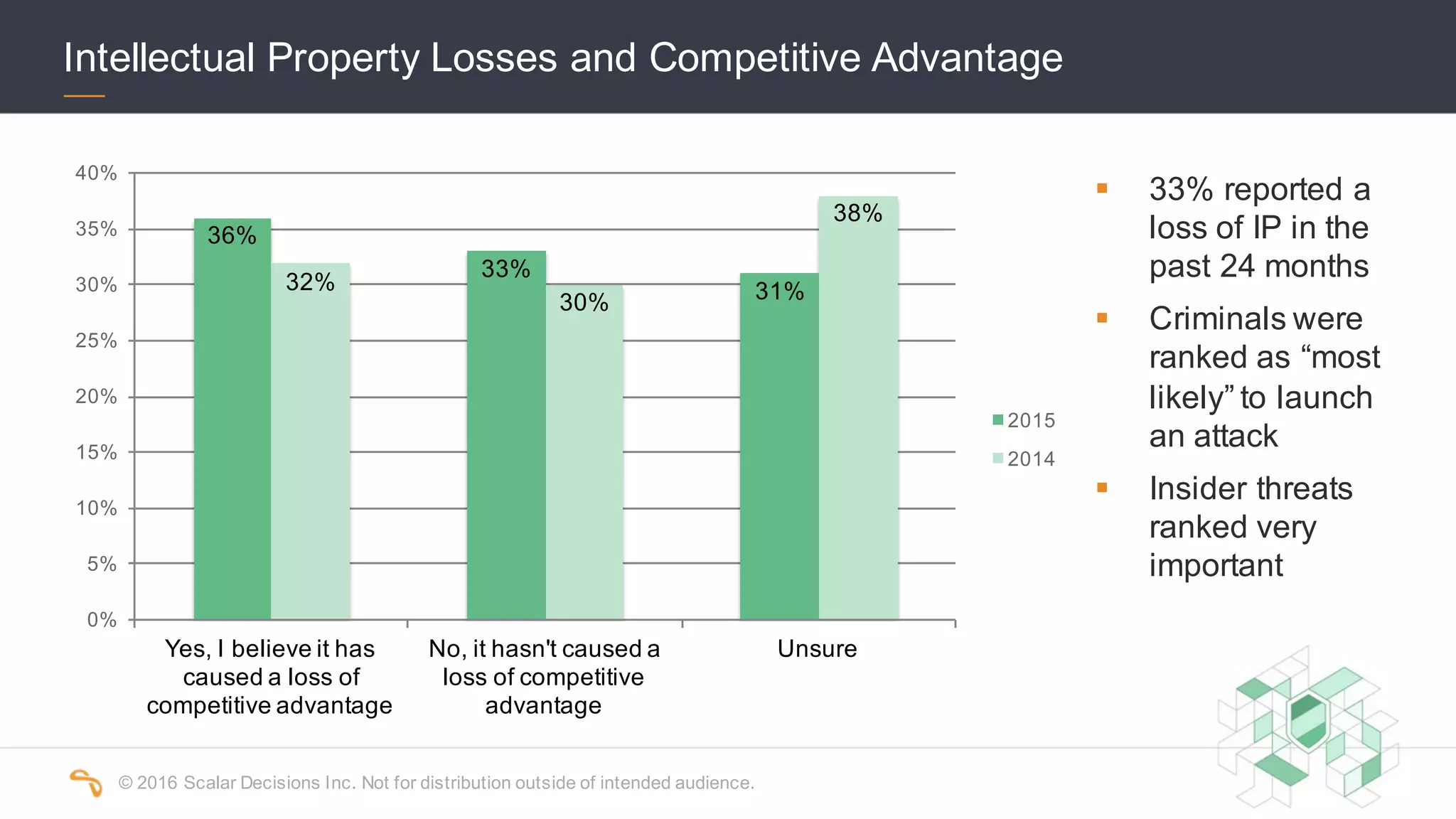
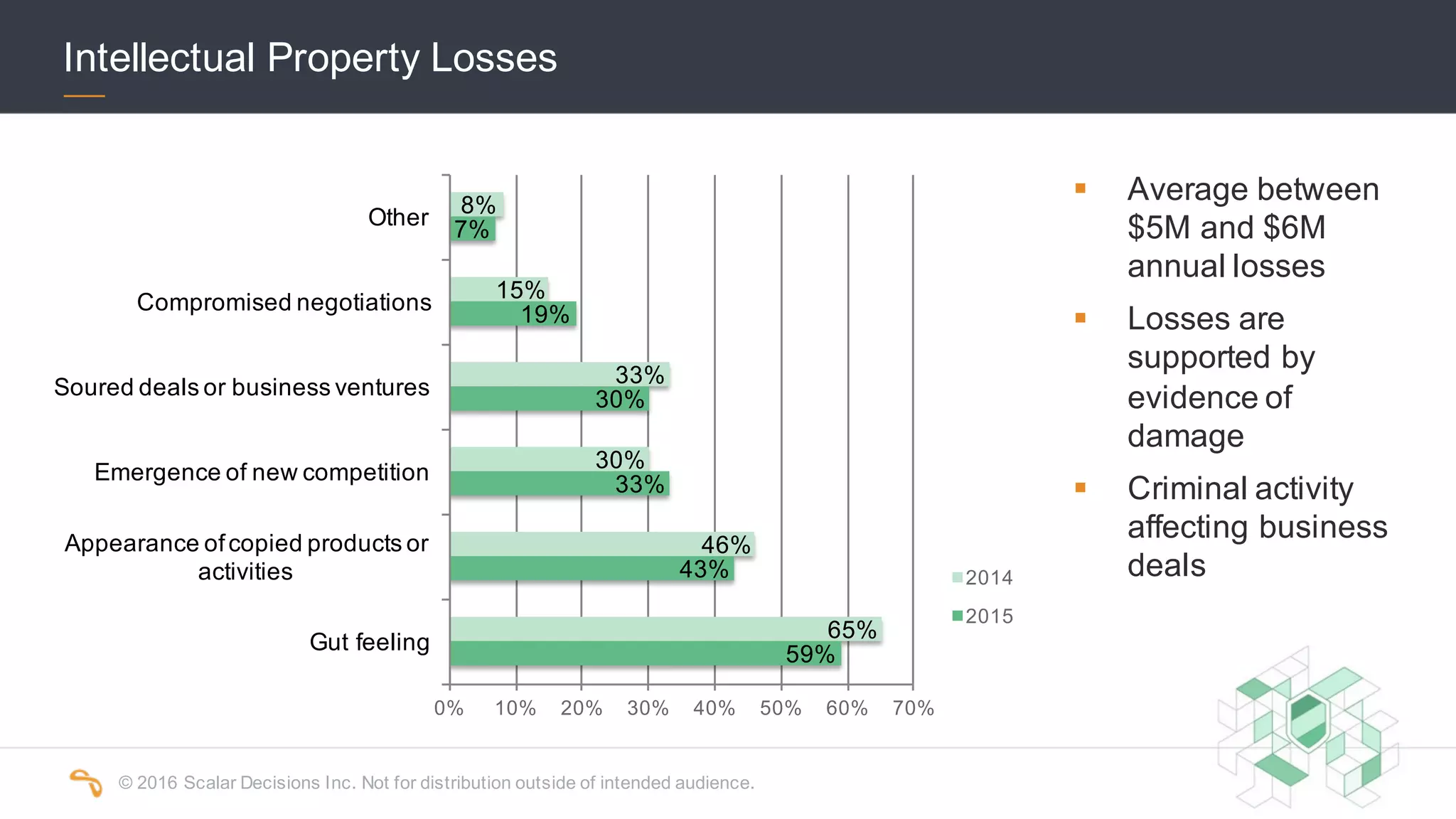
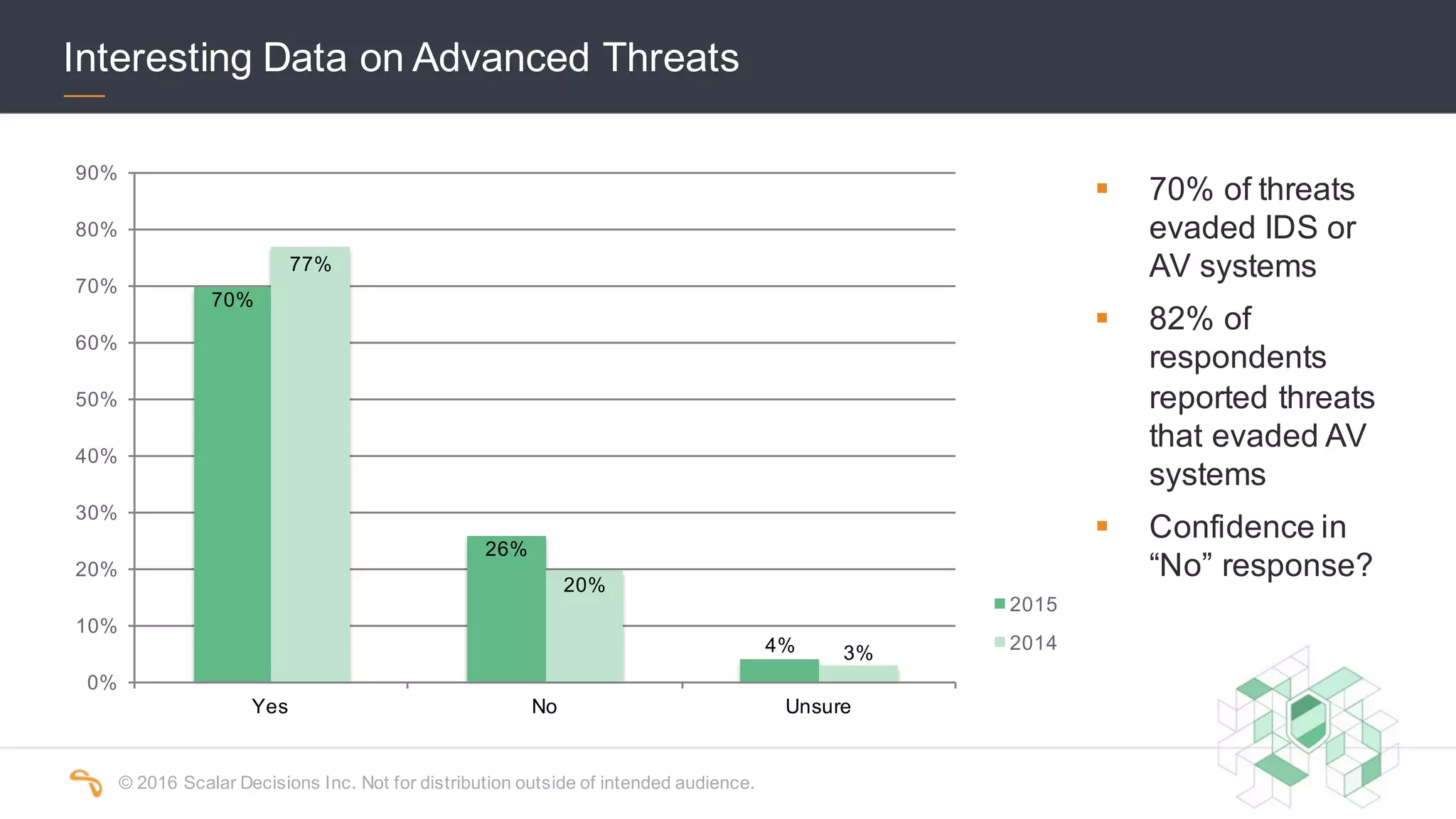
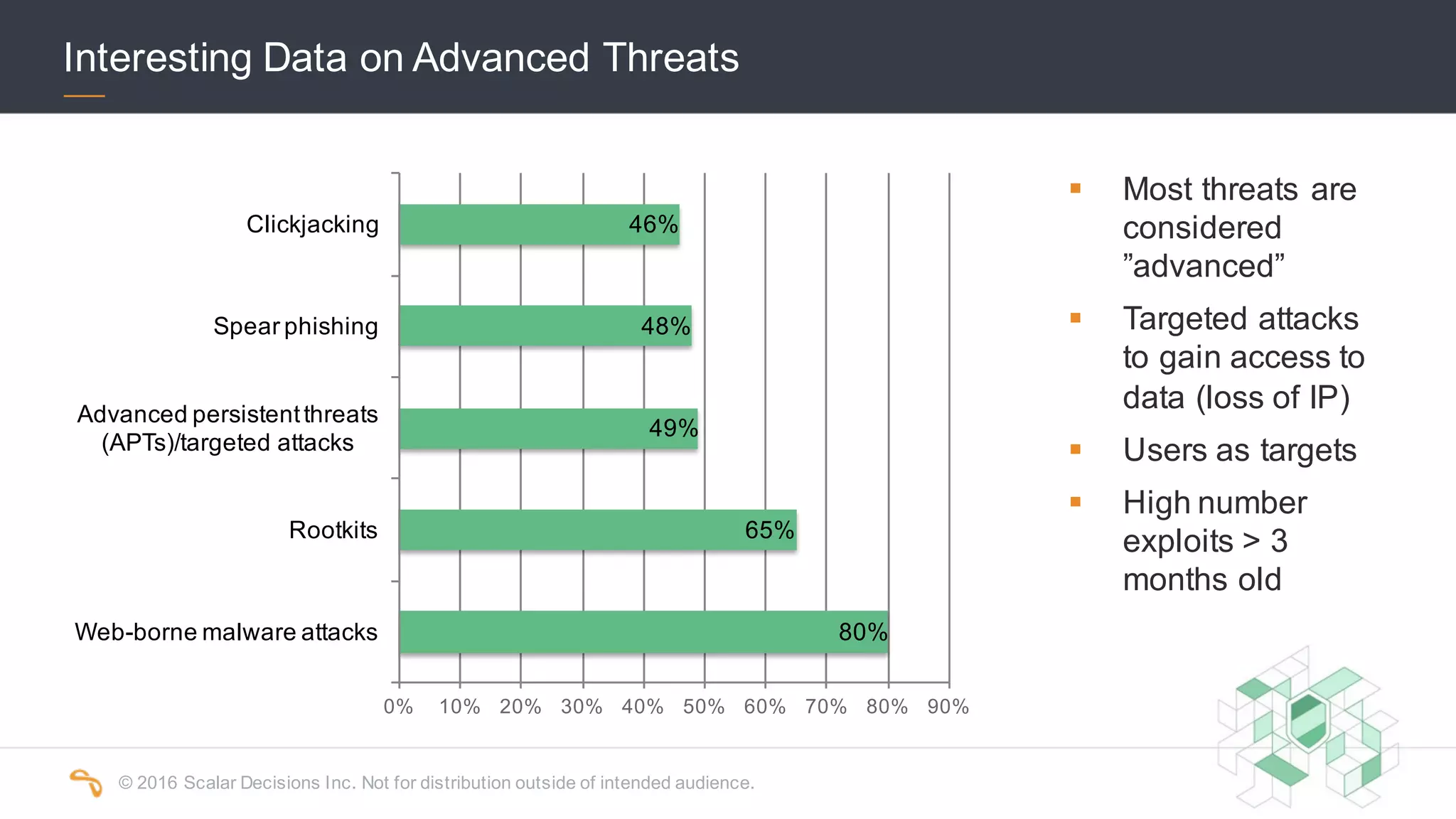
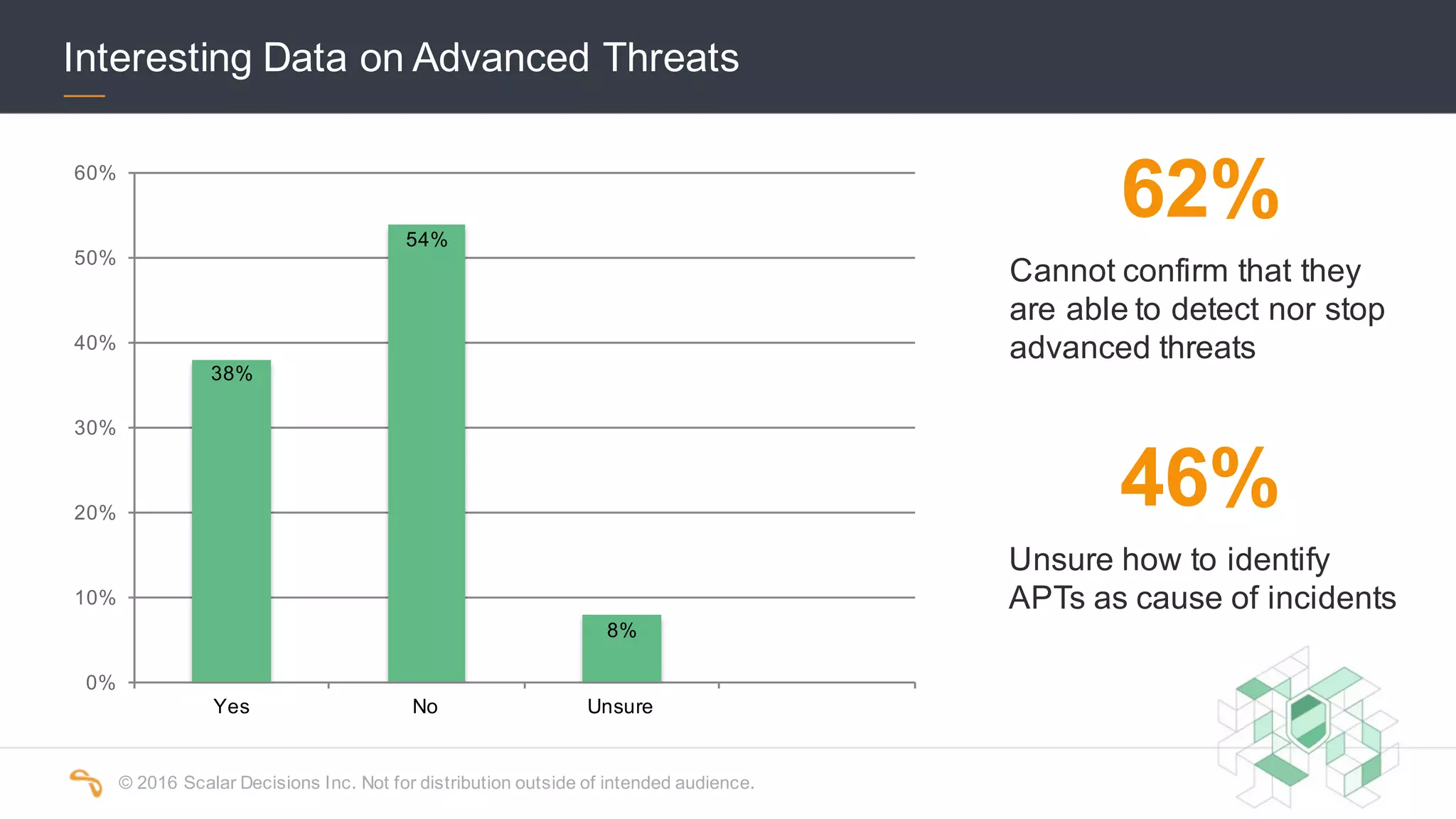
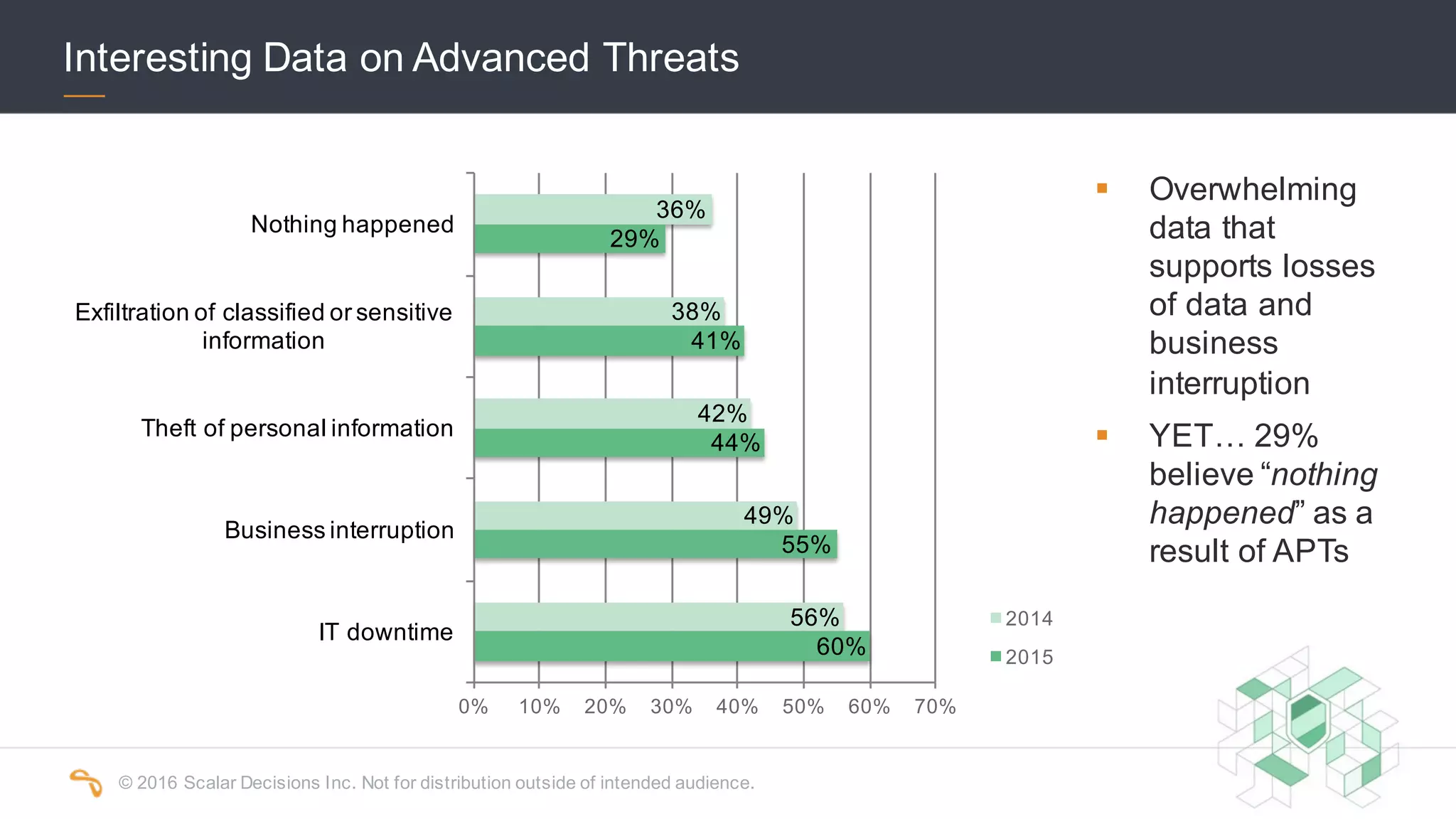
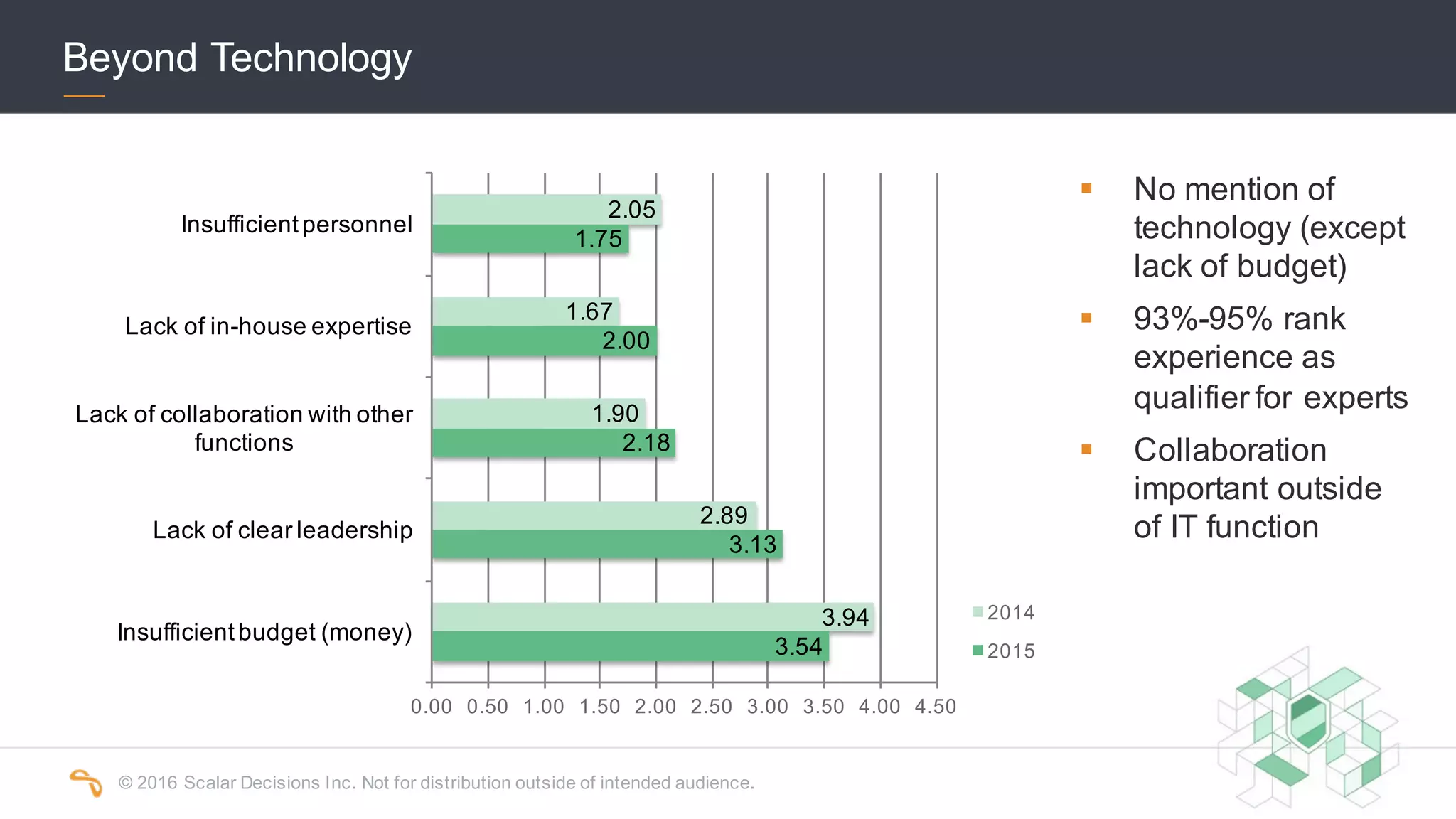
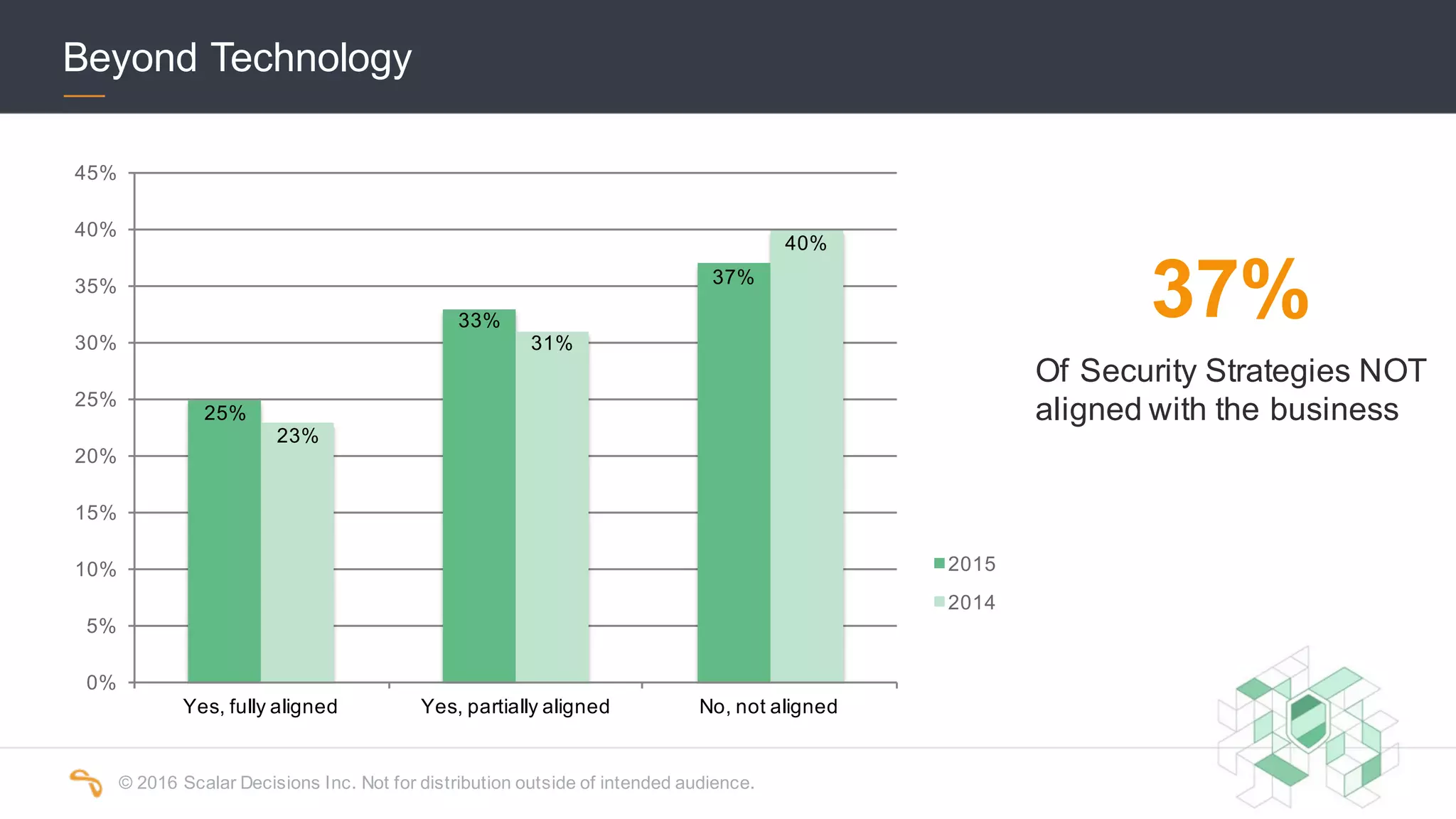
The 2016 Scalar Security Study reports that Canadian organizations face increasing challenges from cyber attacks, with only 37% feeling effective in their defenses. The study highlights significant costs from these attacks, averaging $7 million annually, and emphasizes the importance of aligning security strategies with business objectives. Recommendations include investing in advanced technology and expertise to enhance security measures.