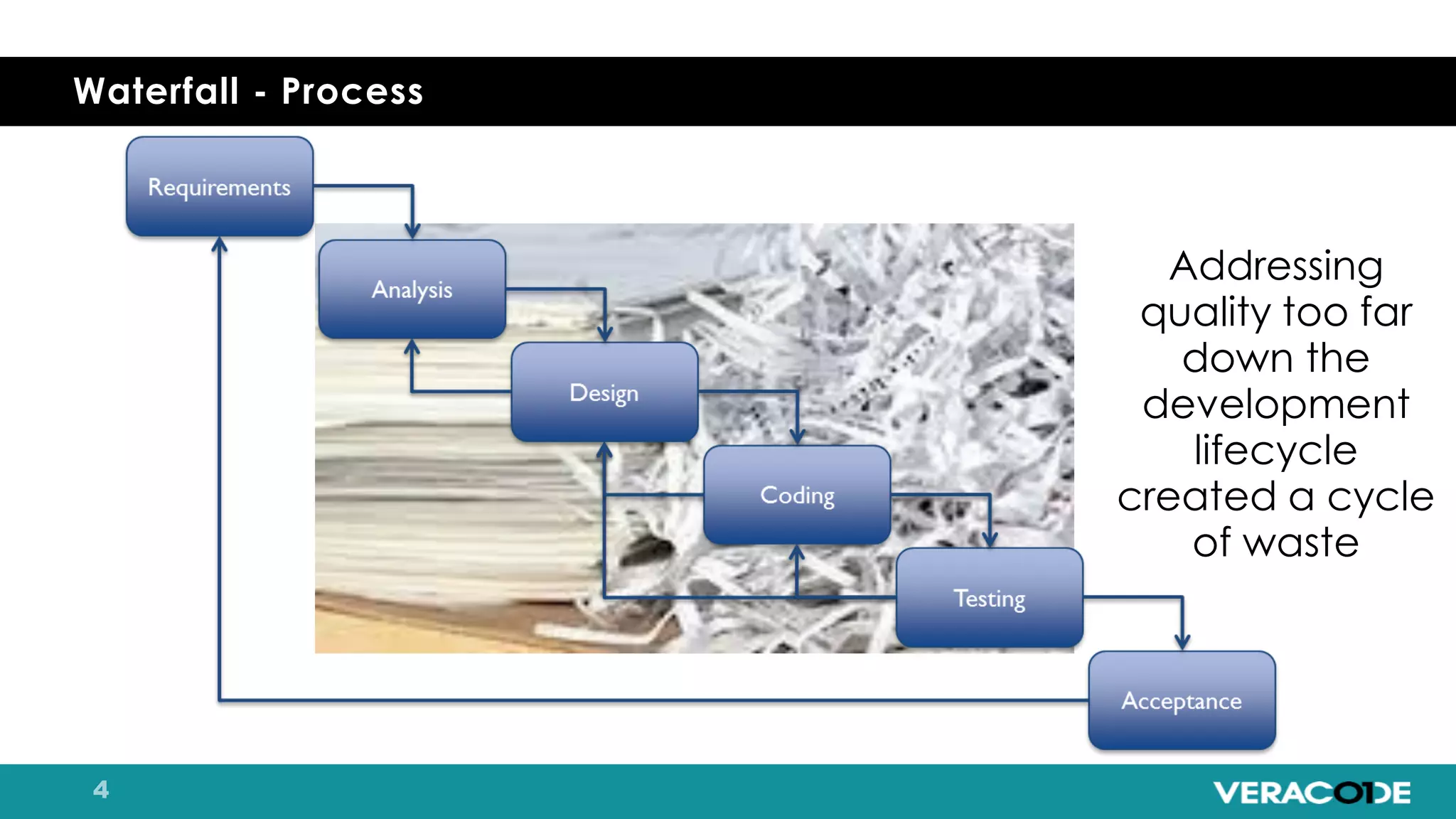
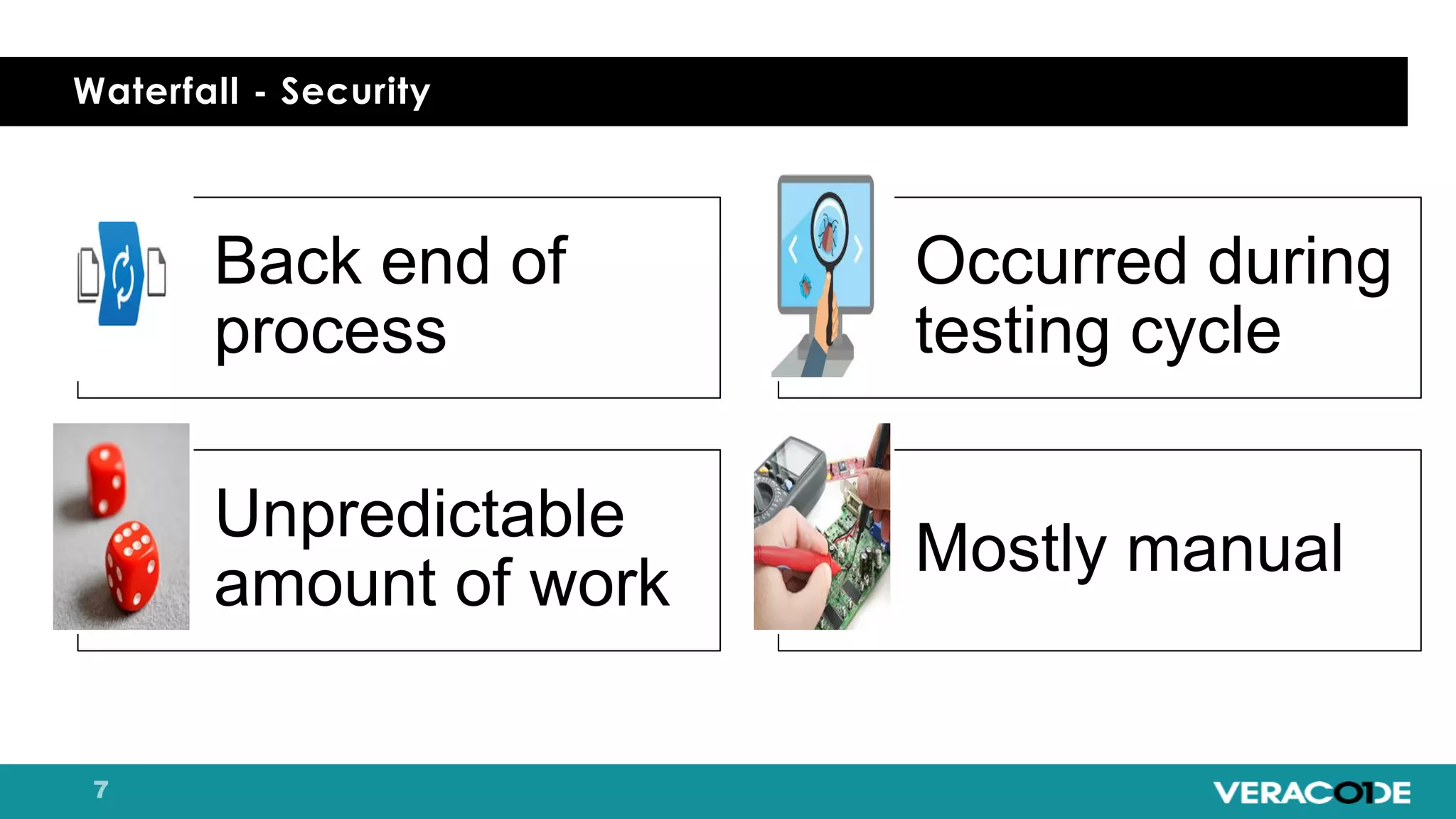
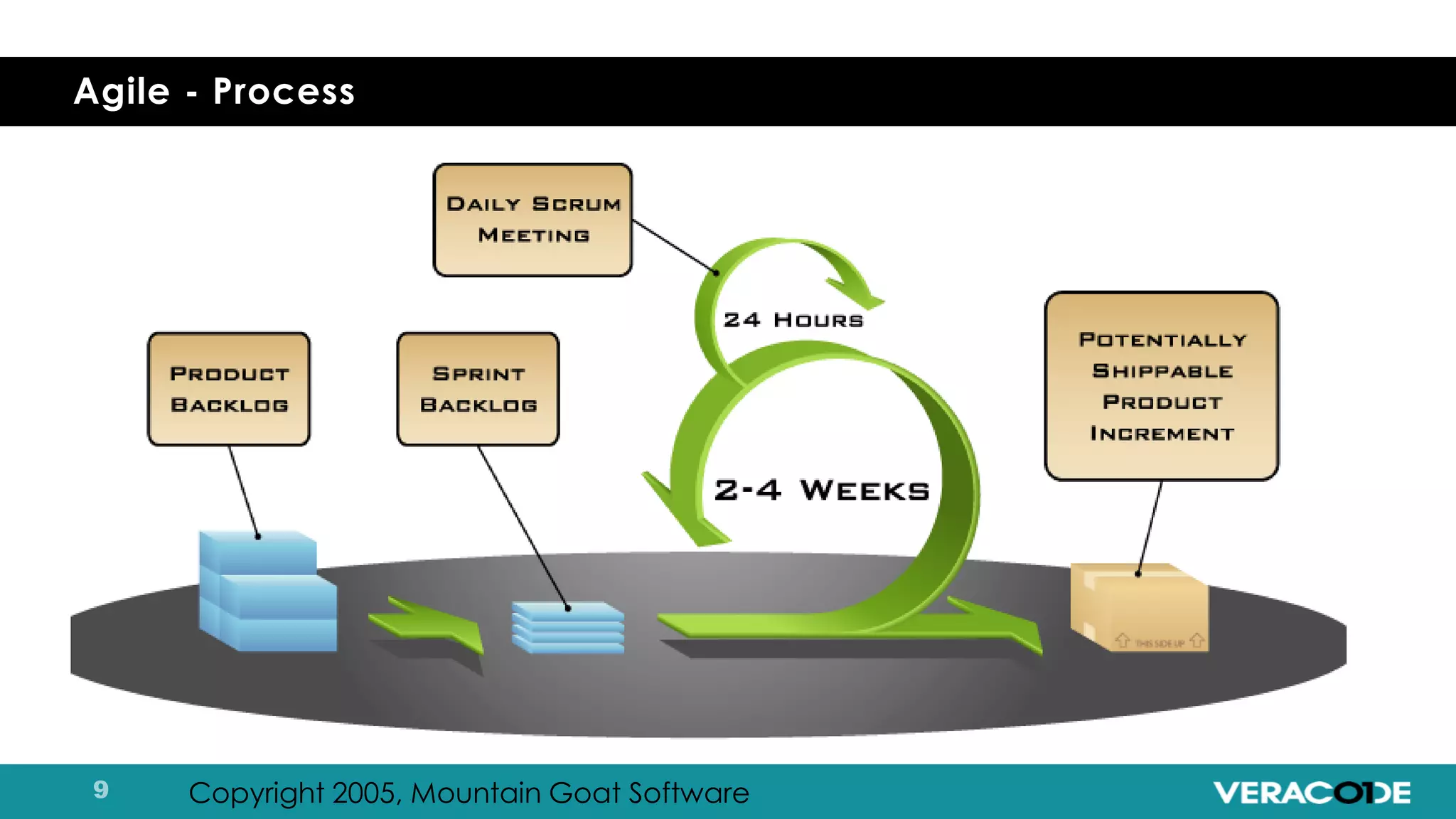
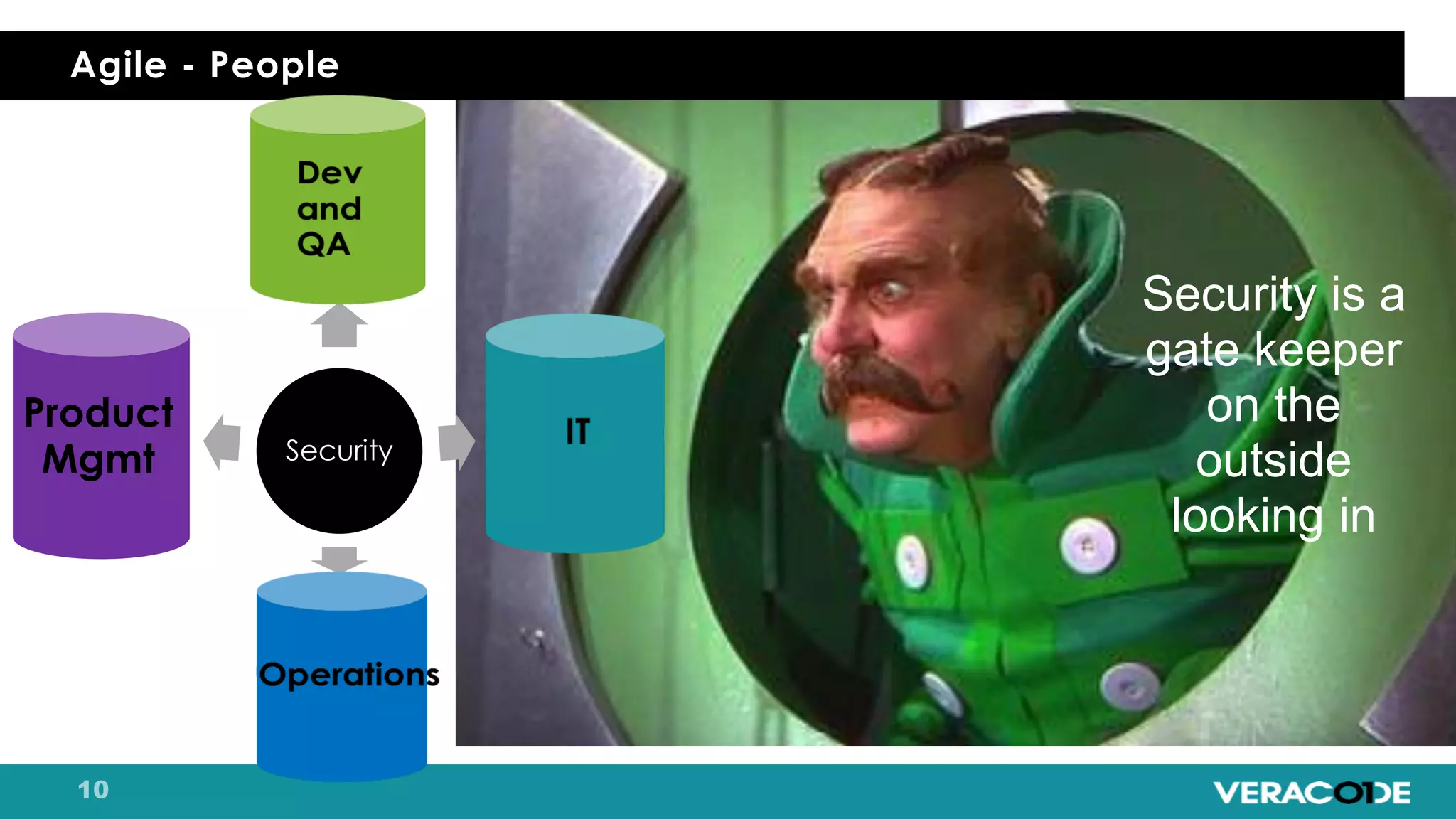
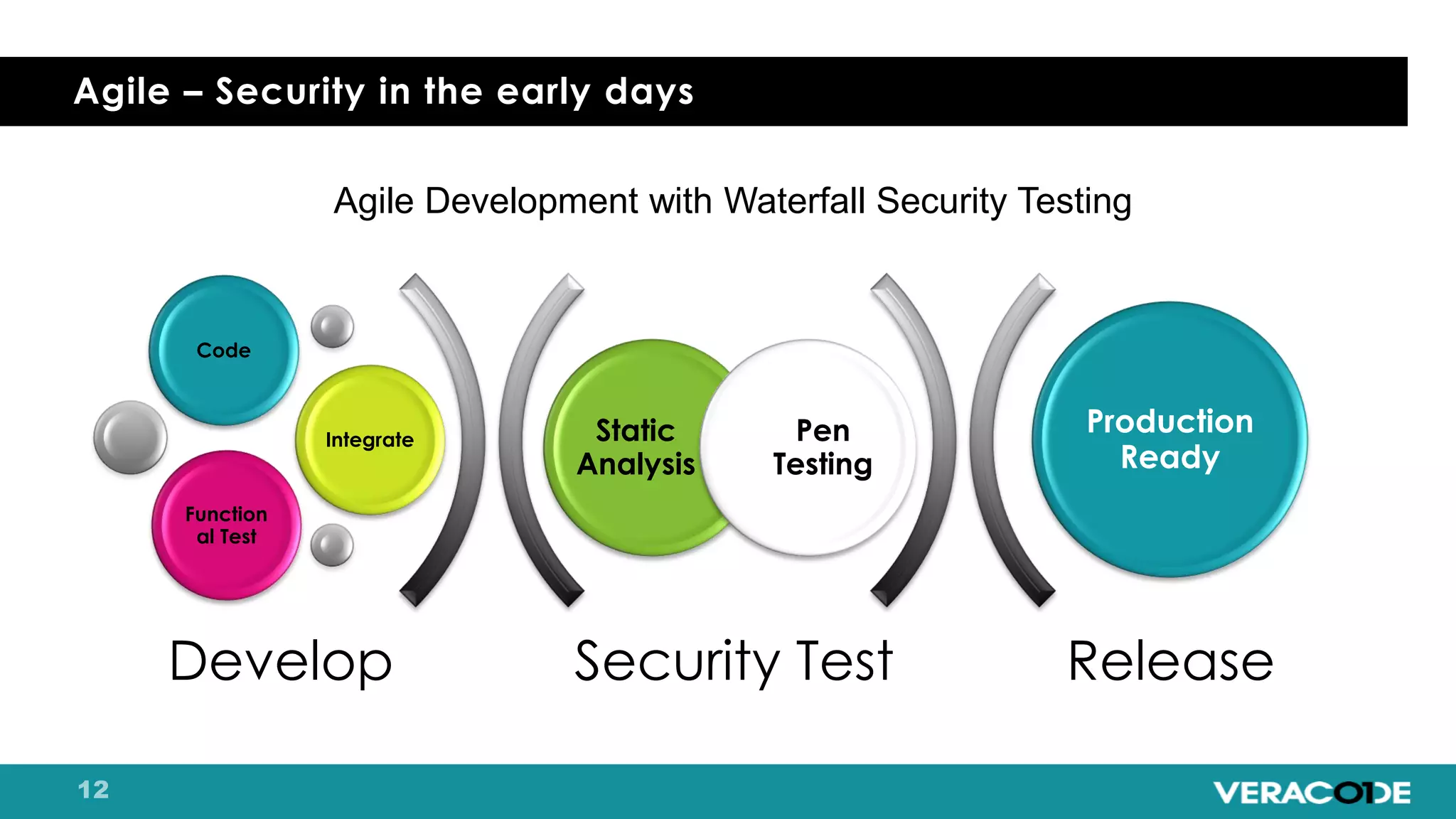
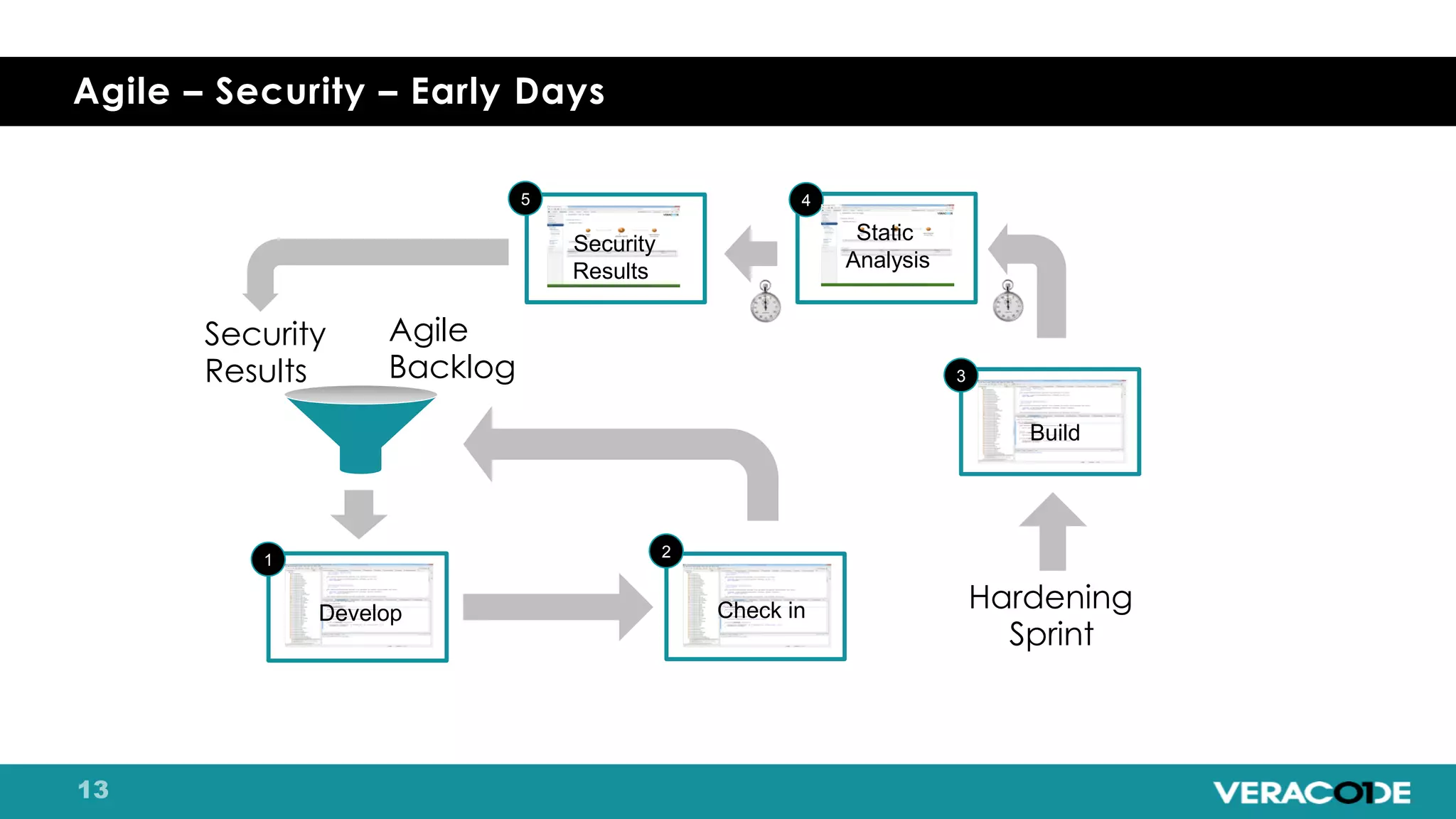
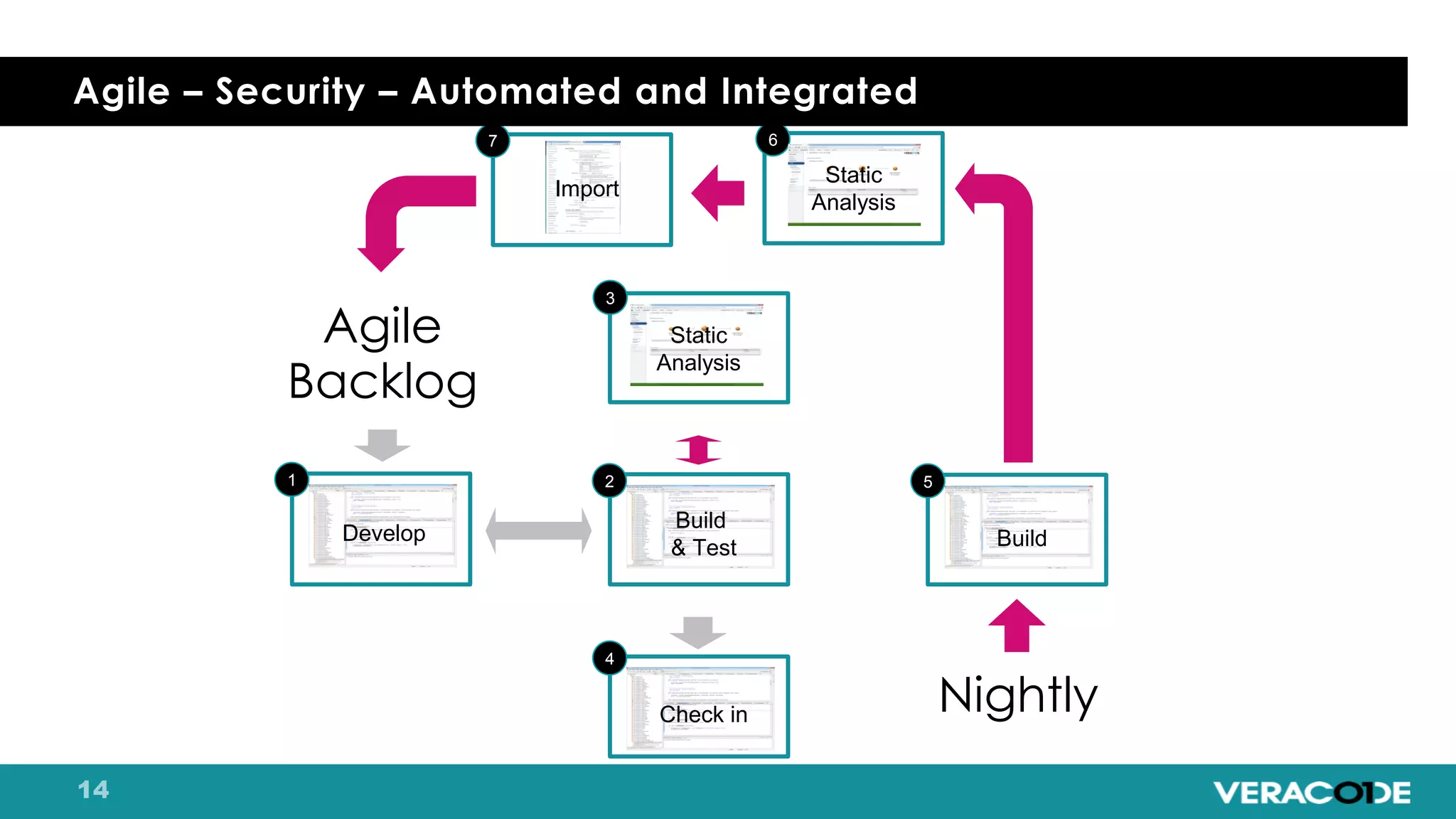
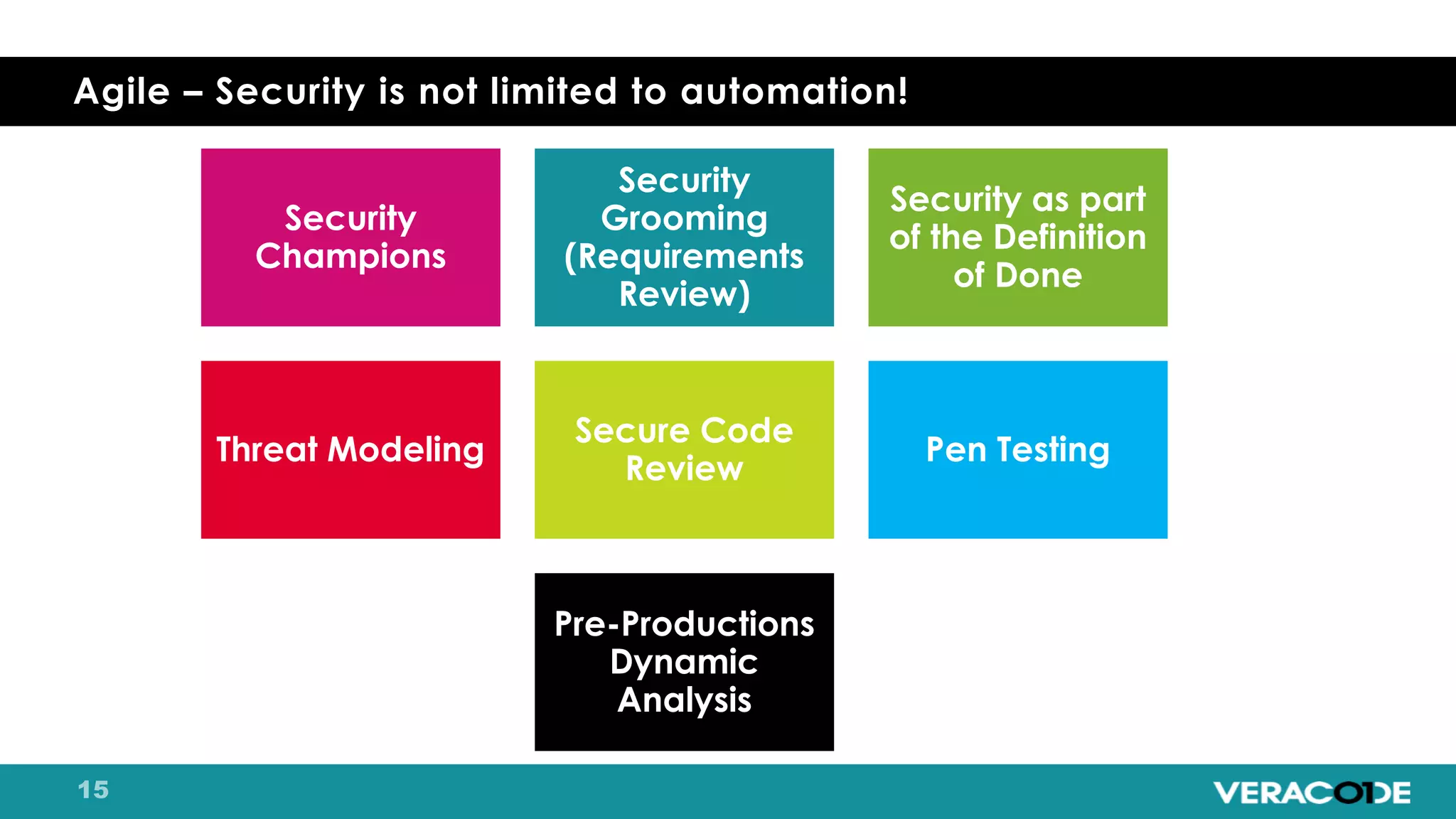
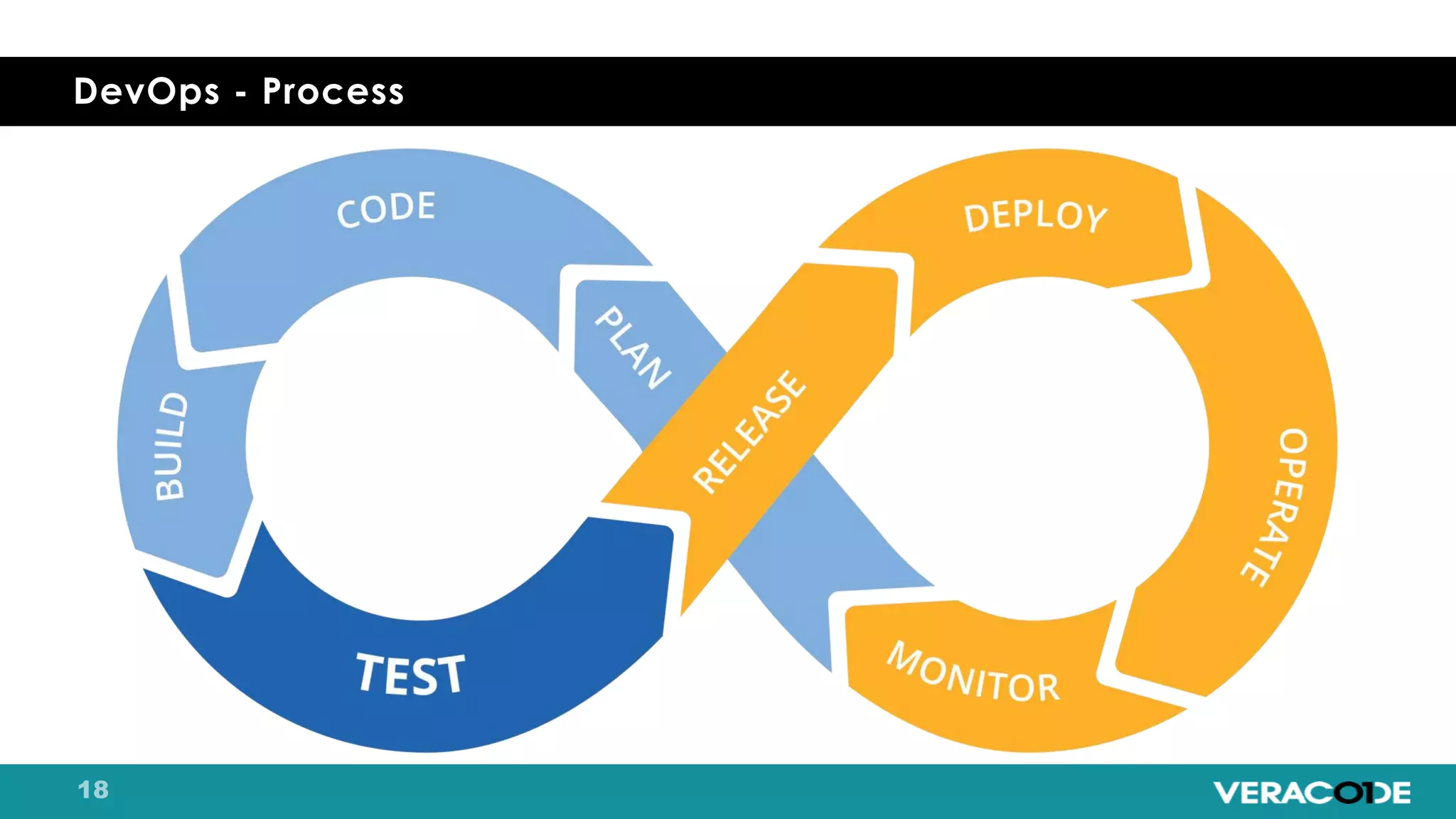
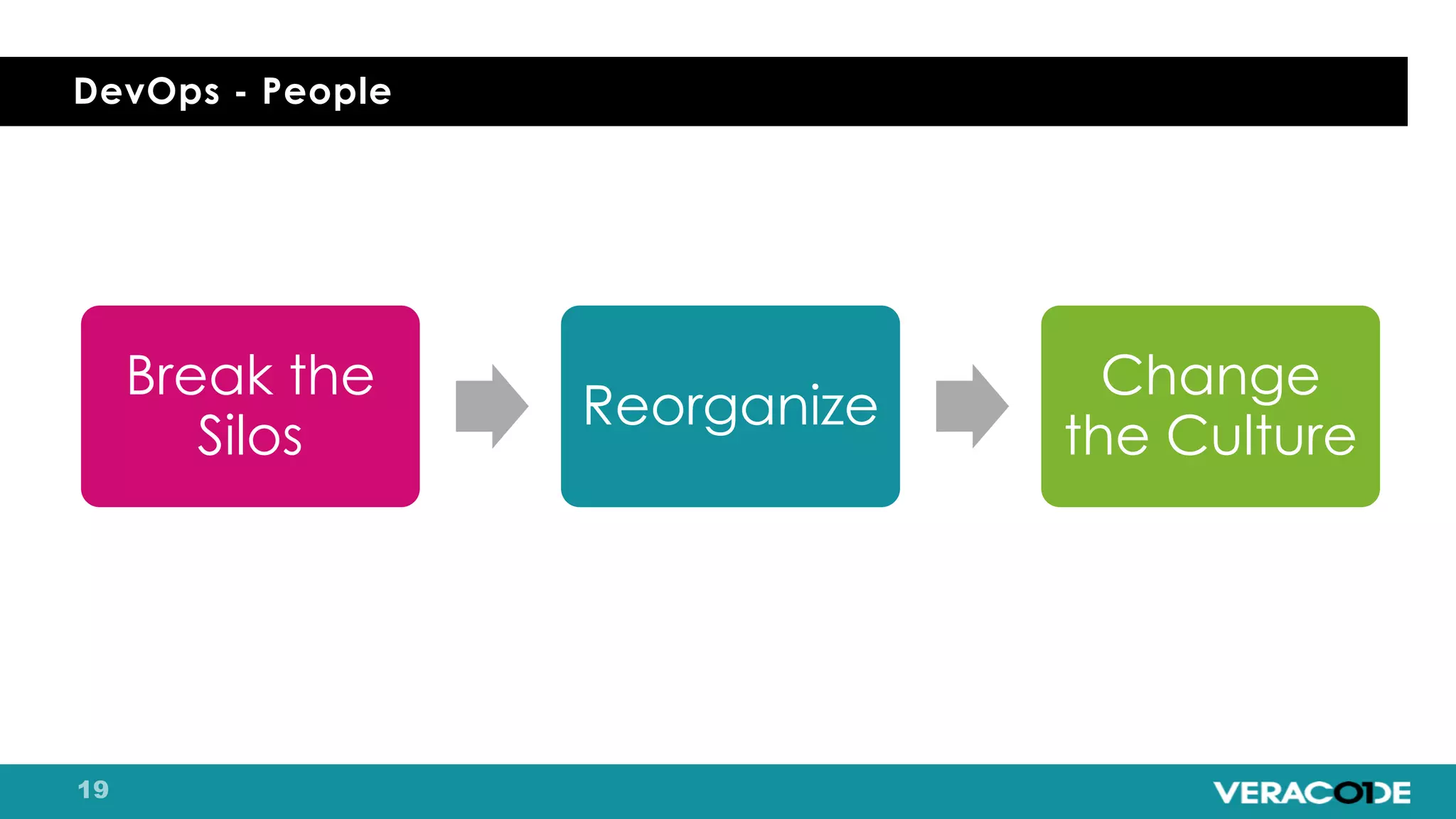
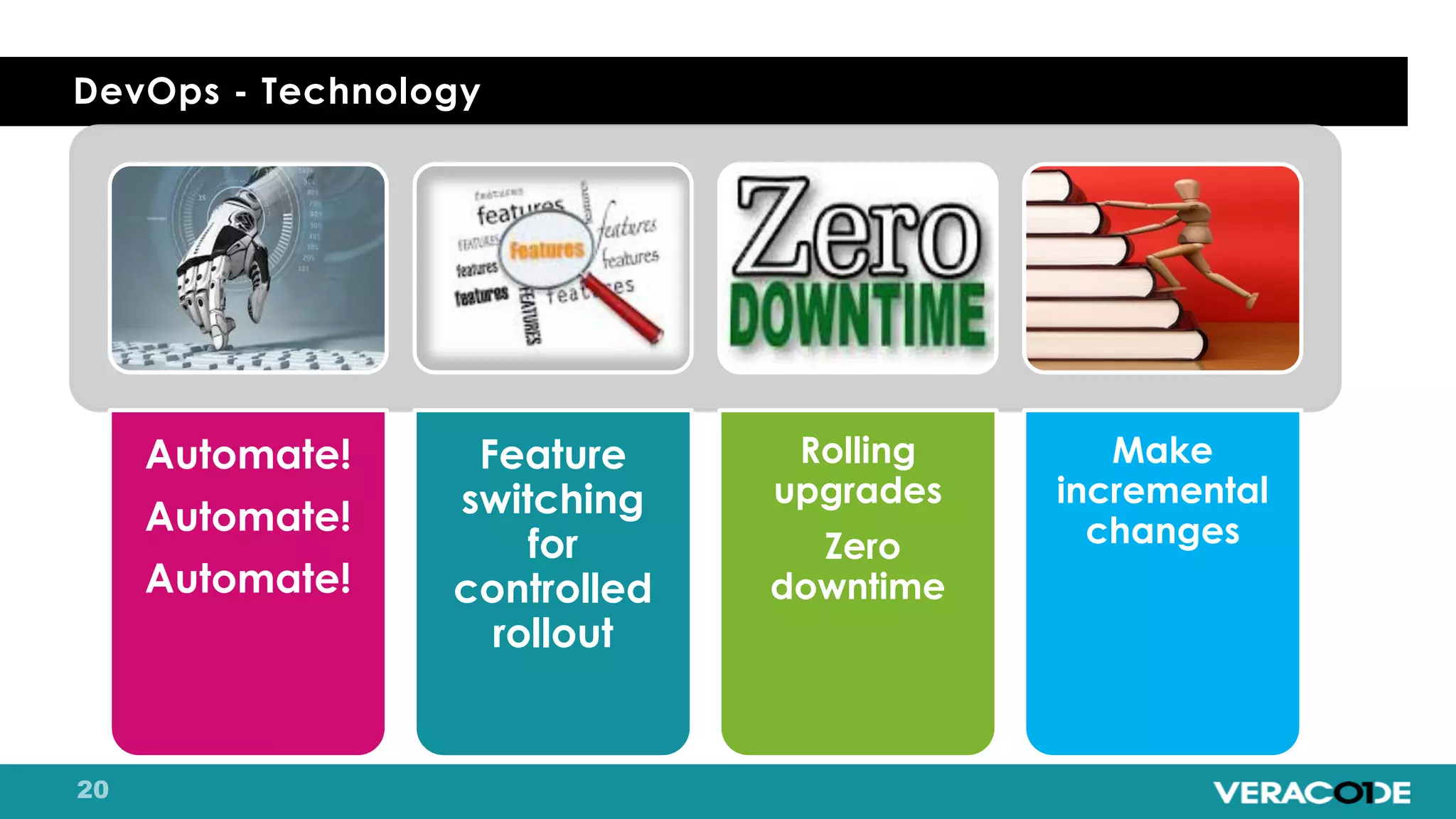
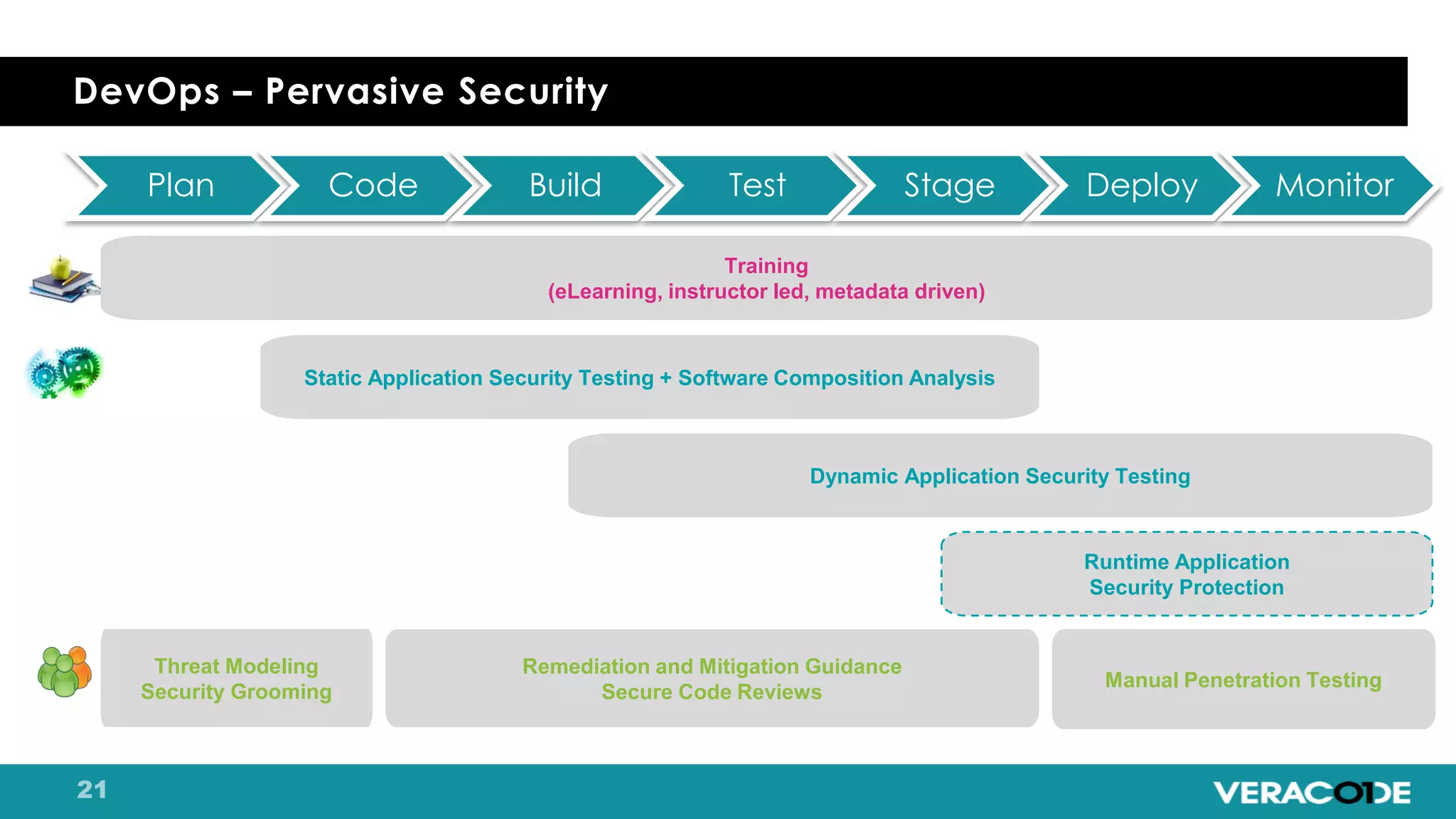
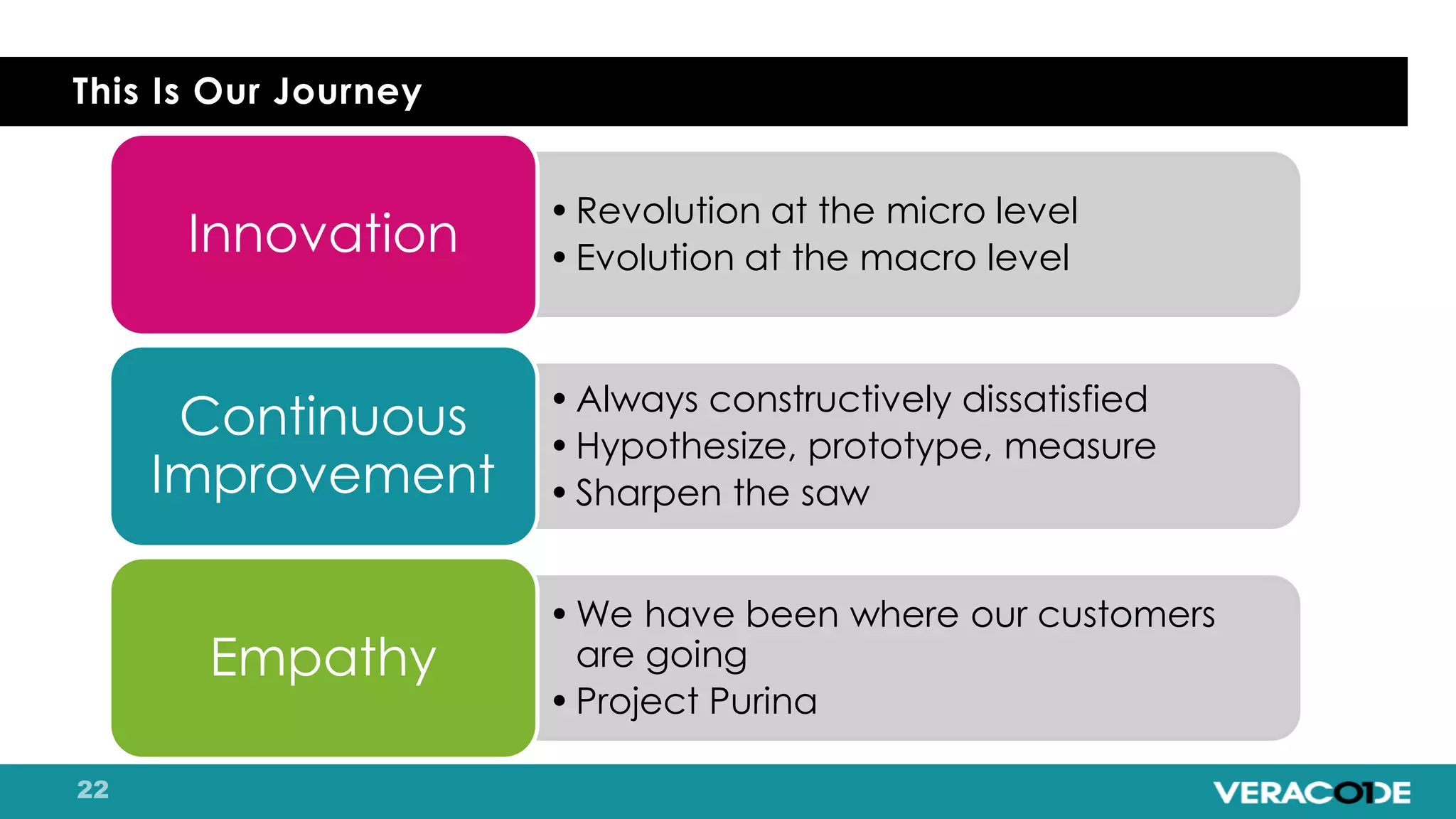
Pete Chestna has 25 years of experience in enterprise software development and has worked at Veracode for over 10 years. He discusses the evolution from waterfall to agile to DevOps approaches. With waterfall, quality tasks like security occurred late in the process and were unpredictable. Agile broke down silos but security initially remained separate. DevOps integrates security throughout by automating tasks, enabling zero downtime upgrades, and embedding security into definitions of done. The journey requires revolution at a micro level and evolution at a macro level through continuous improvement and empathy.