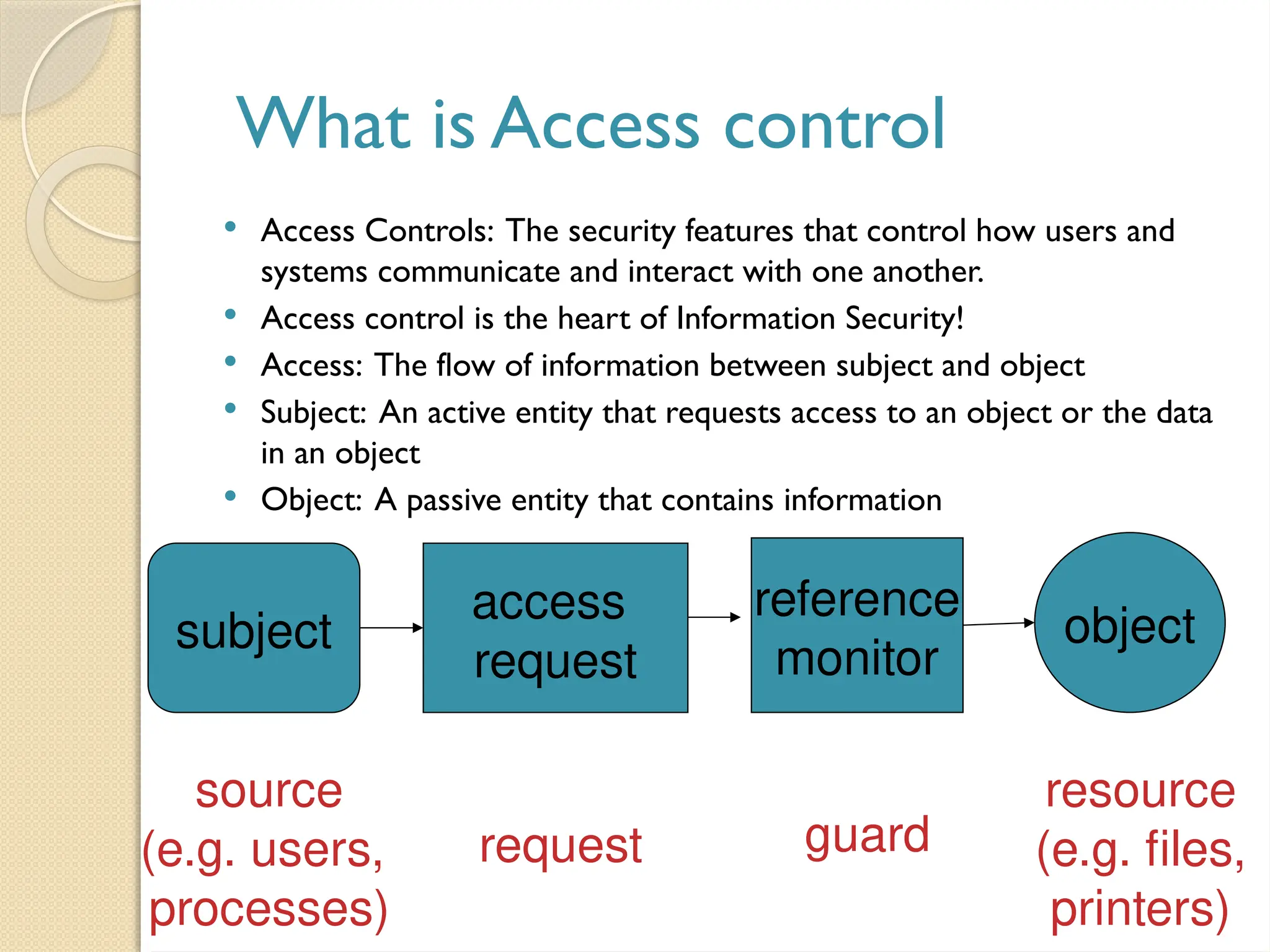
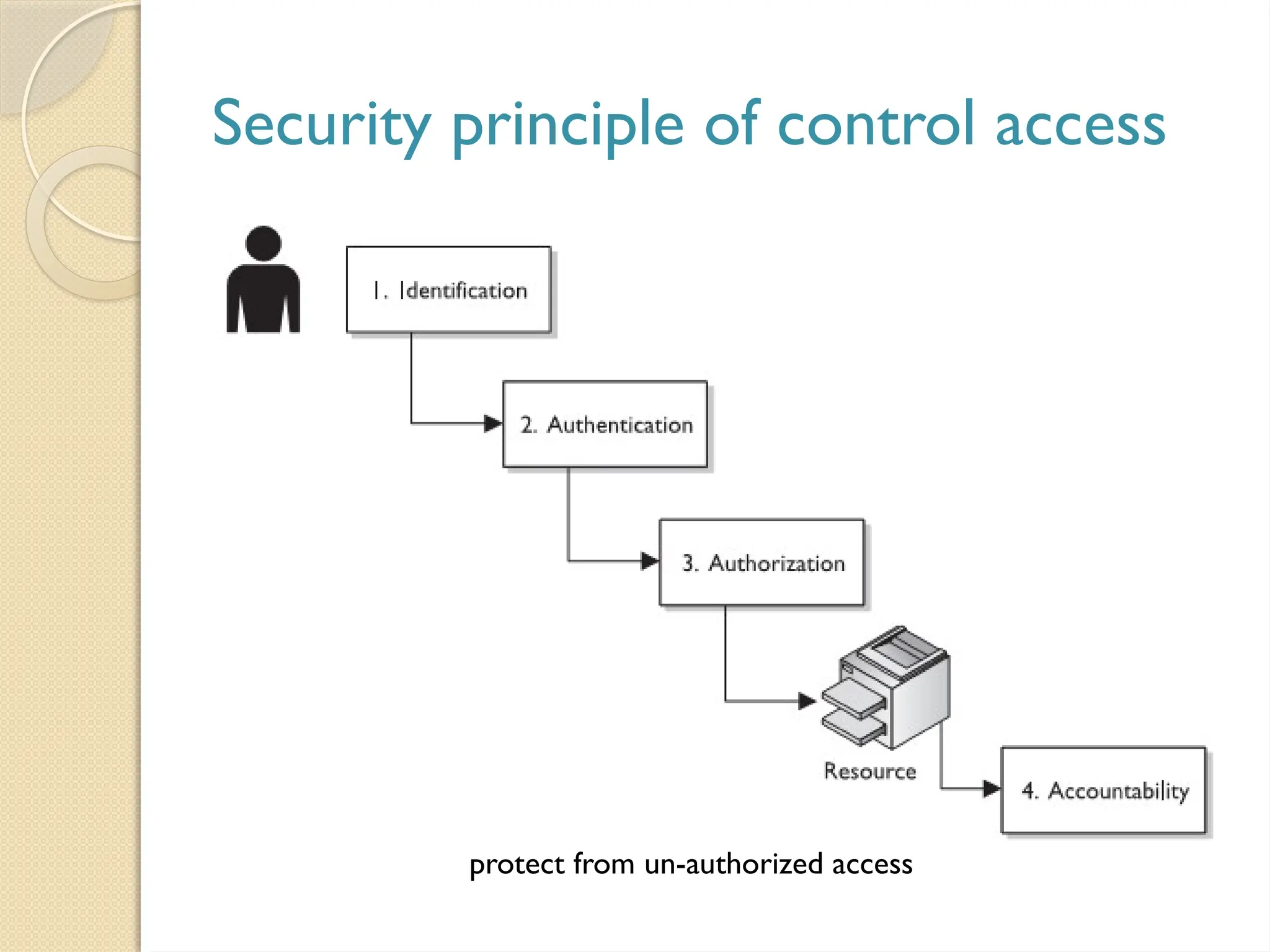
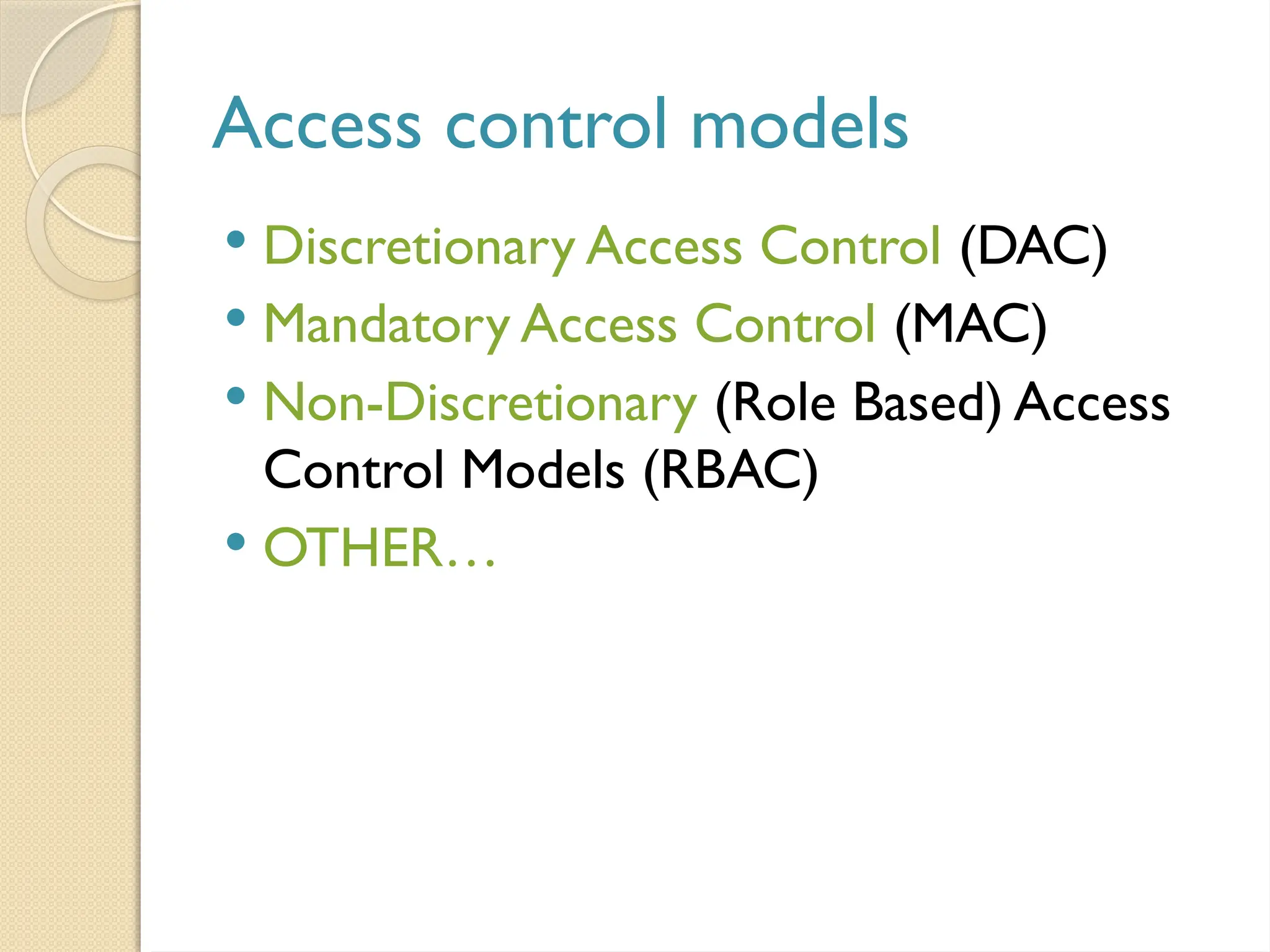
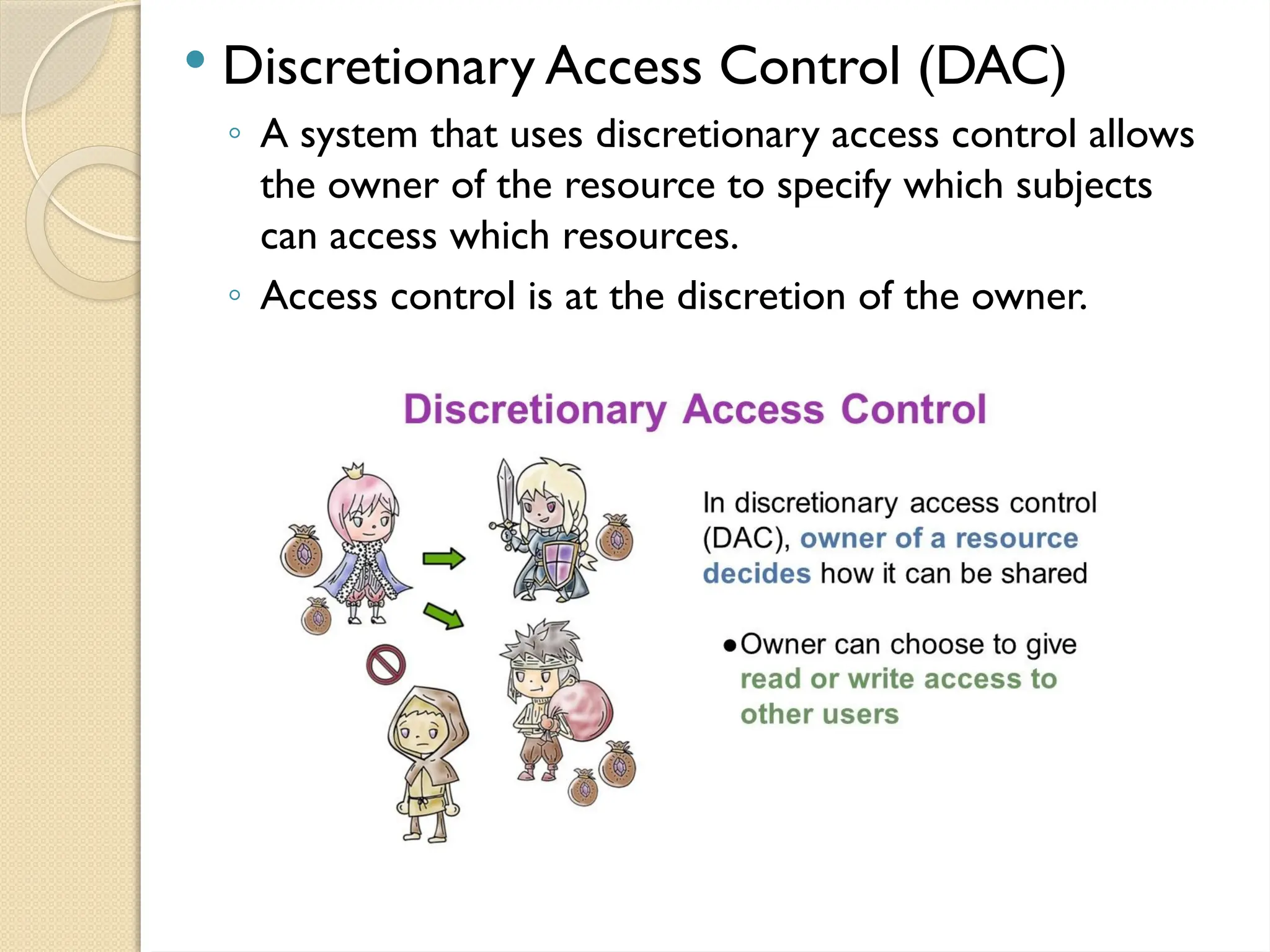
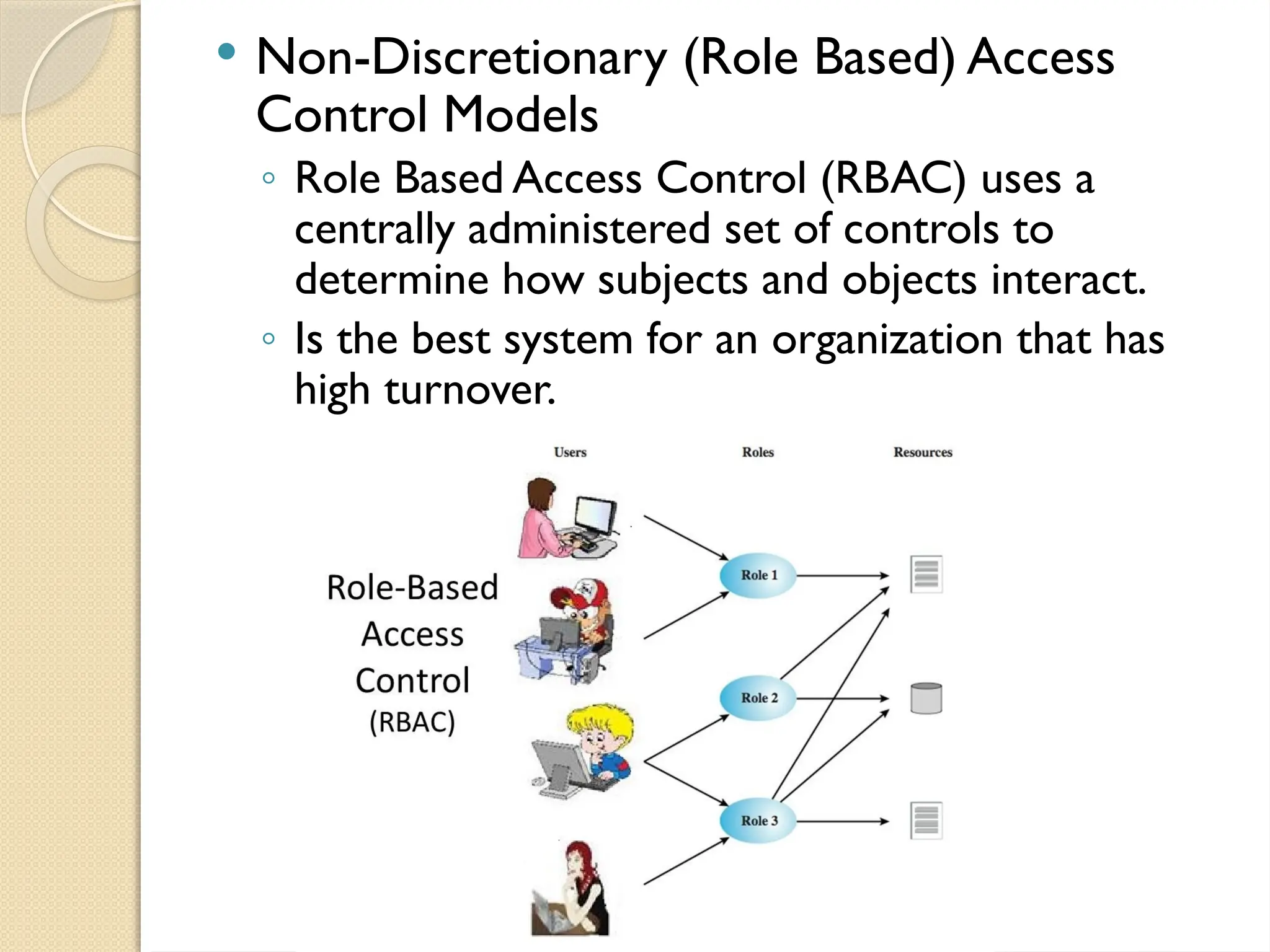
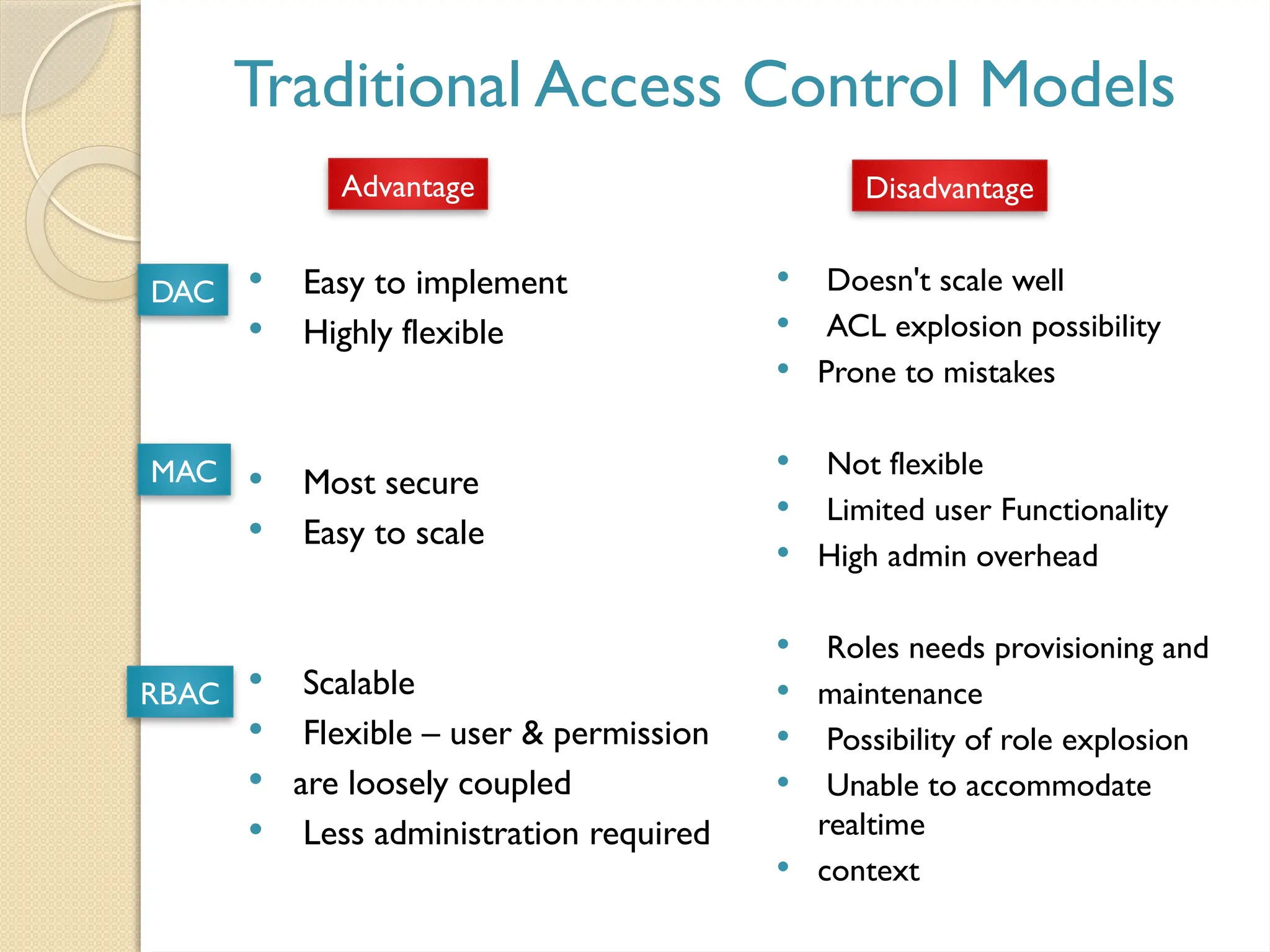
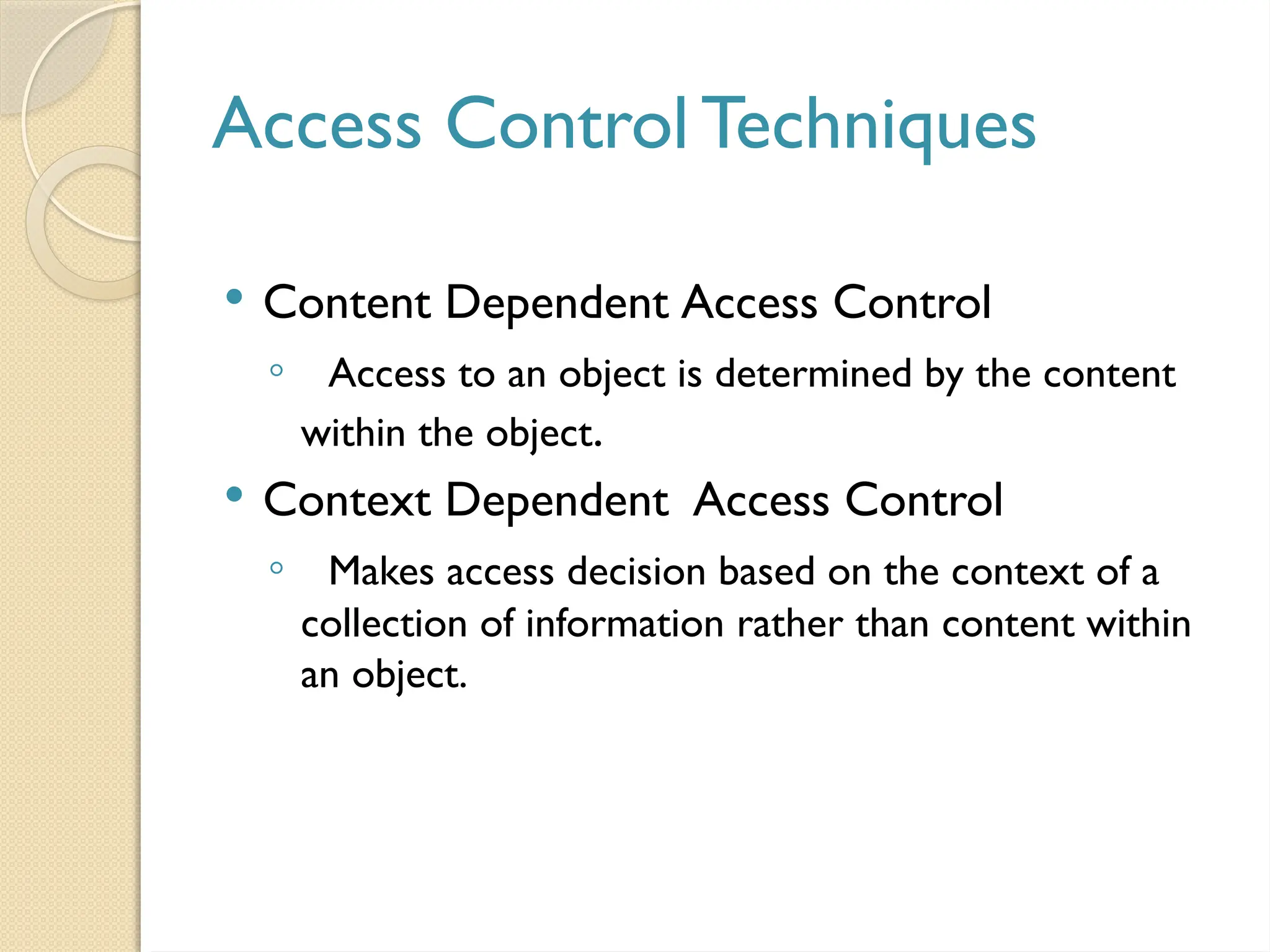
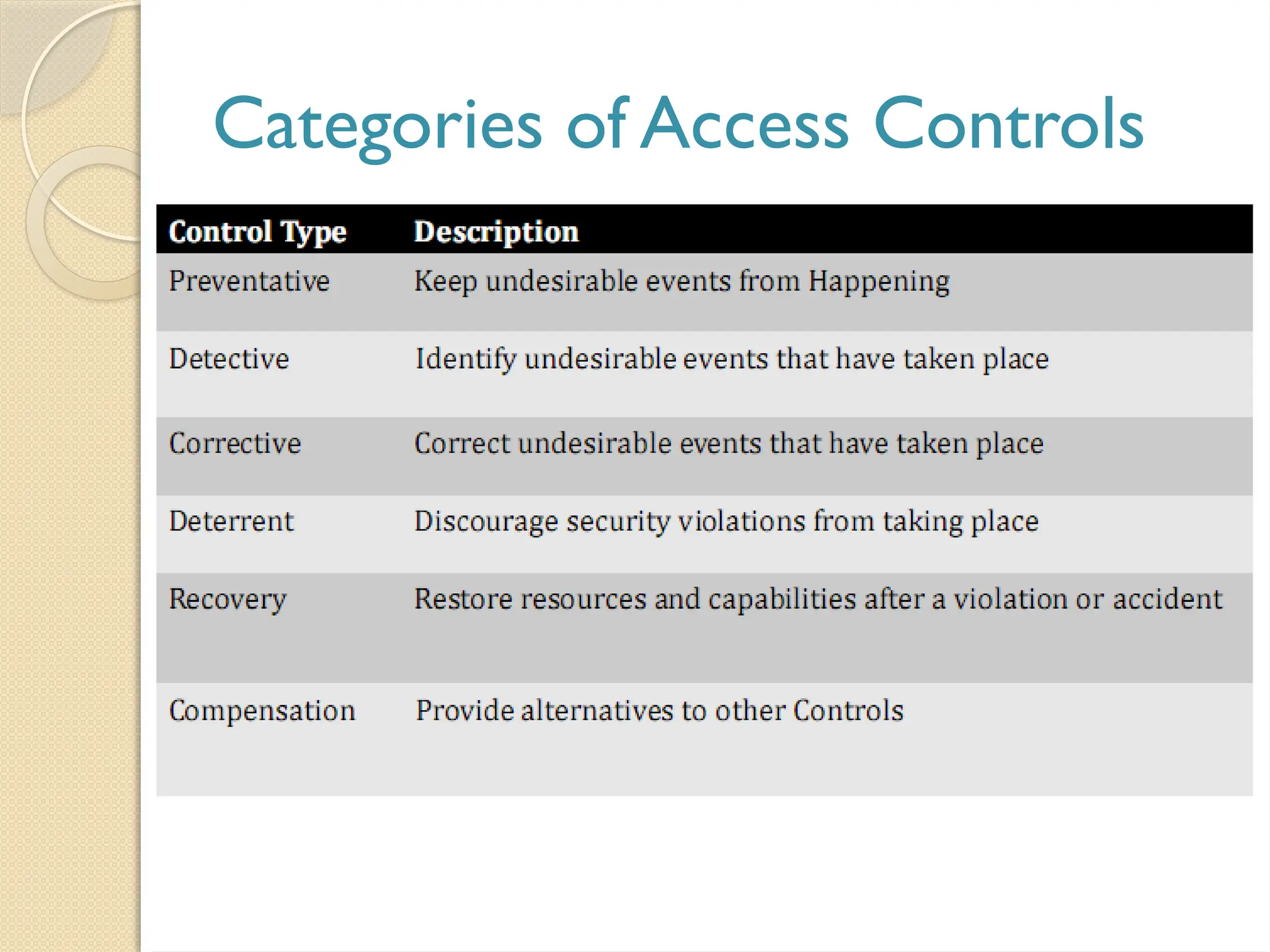
The document outlines the principles, models, types, techniques, and threats related to access control, which is fundamental to information security. It details security concepts such as identification, authentication, and authorization, as well as various access control models including discretionary, mandatory, and role-based access control. Additionally, it addresses access control techniques and the importance of administrative, technical, and physical controls in protecting information from unauthorized access.