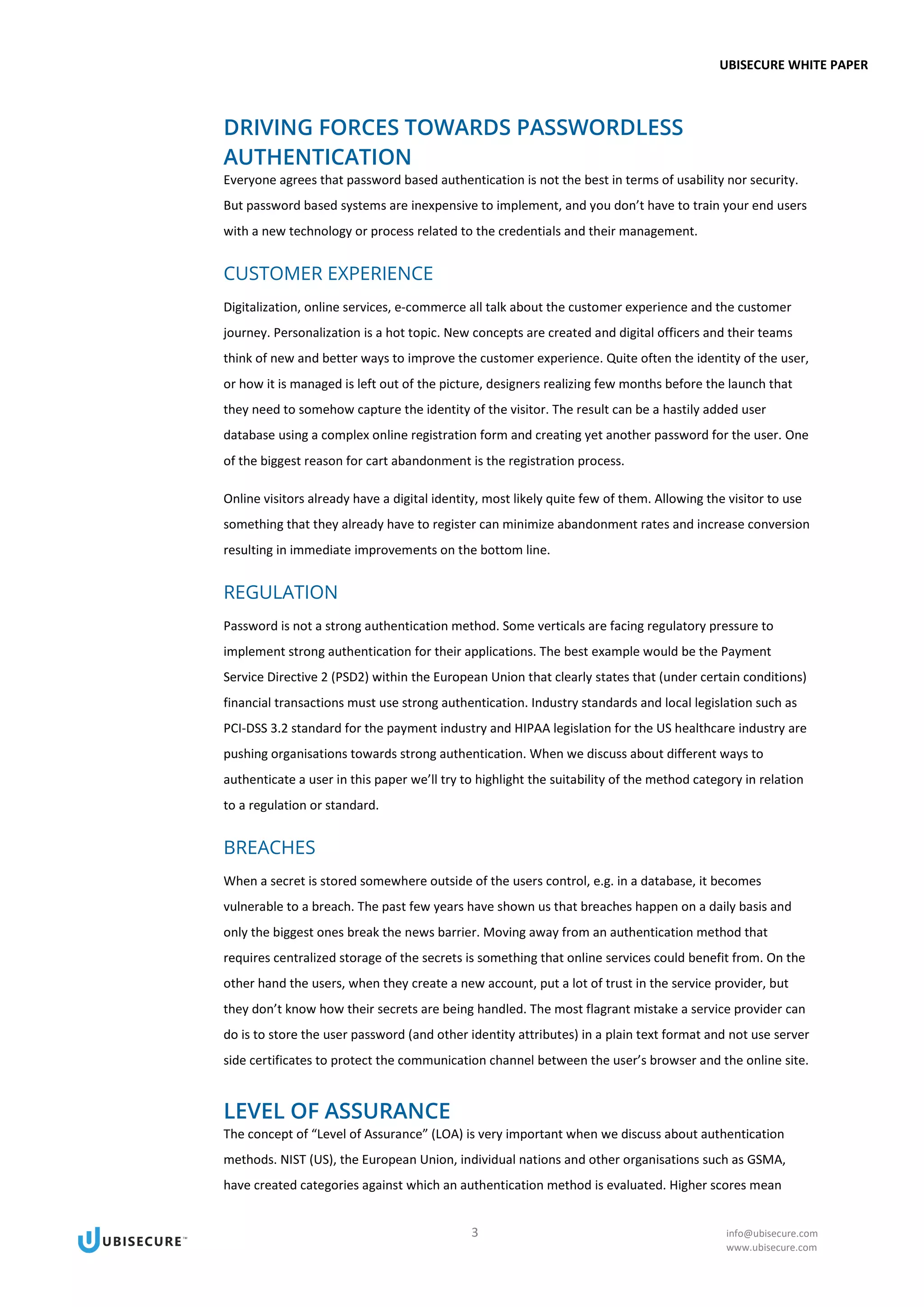
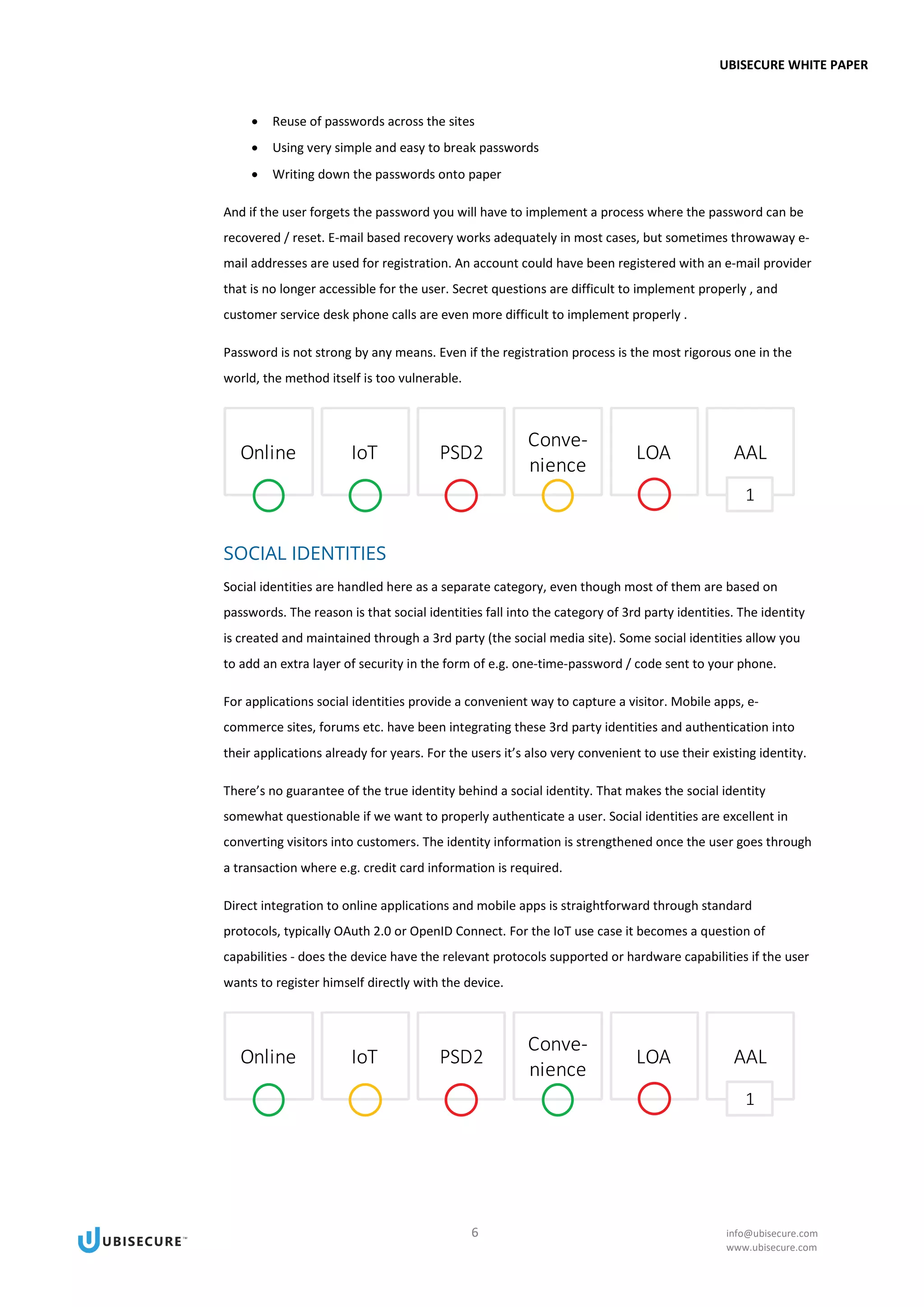
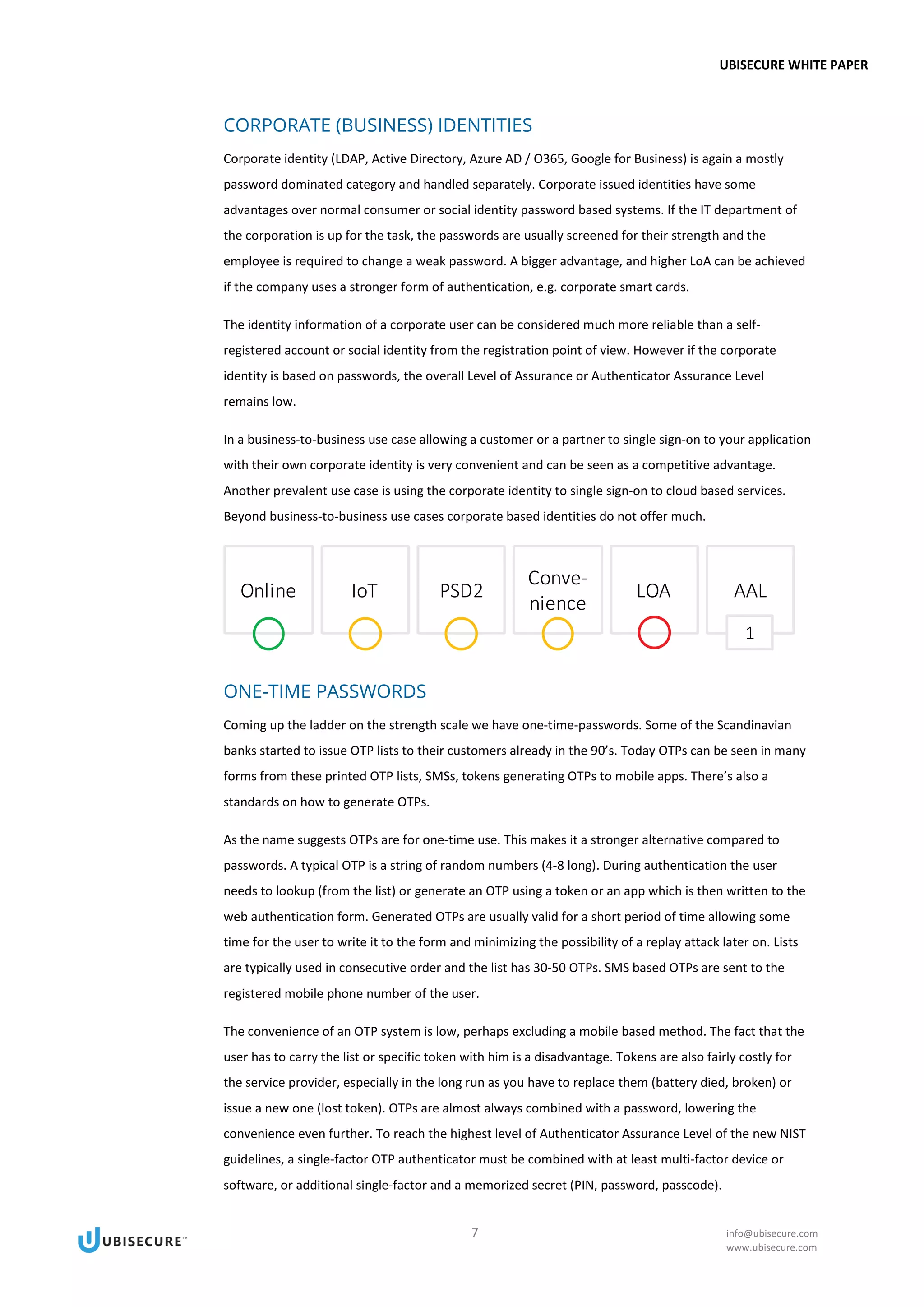
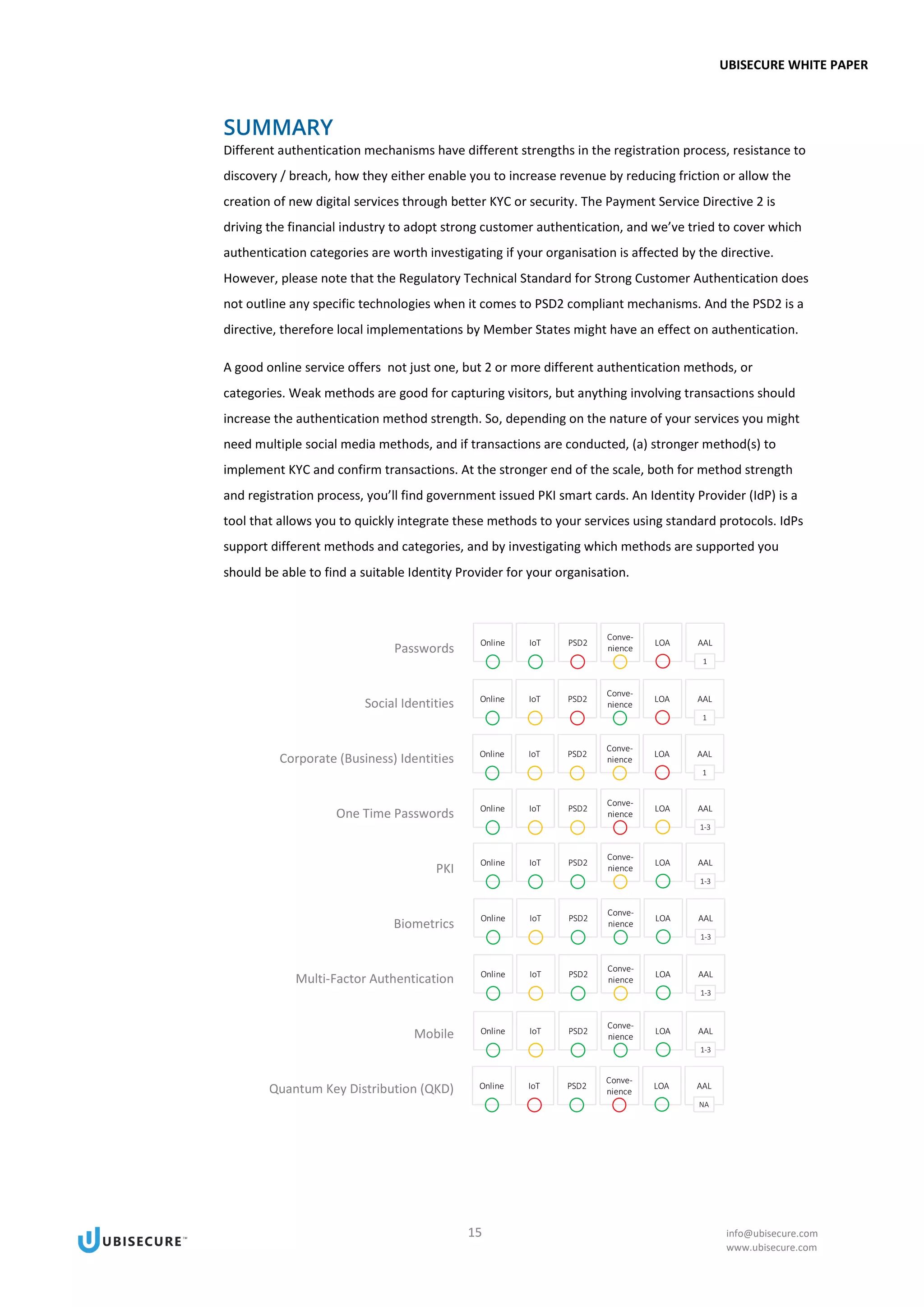
This document provides an introduction to various authentication methods for applications, including passwords, one-time passwords, social identities, corporate identities, and public key infrastructure (PKI). It discusses the driving forces towards passwordless authentication, including improving customer experience, regulatory pressures, data breaches, and authentication strength. The document evaluates each authentication method based on factors like usability, security, and their ability to meet a given level of assurance. It aims to help readers understand the tradeoffs of different authentication solutions.