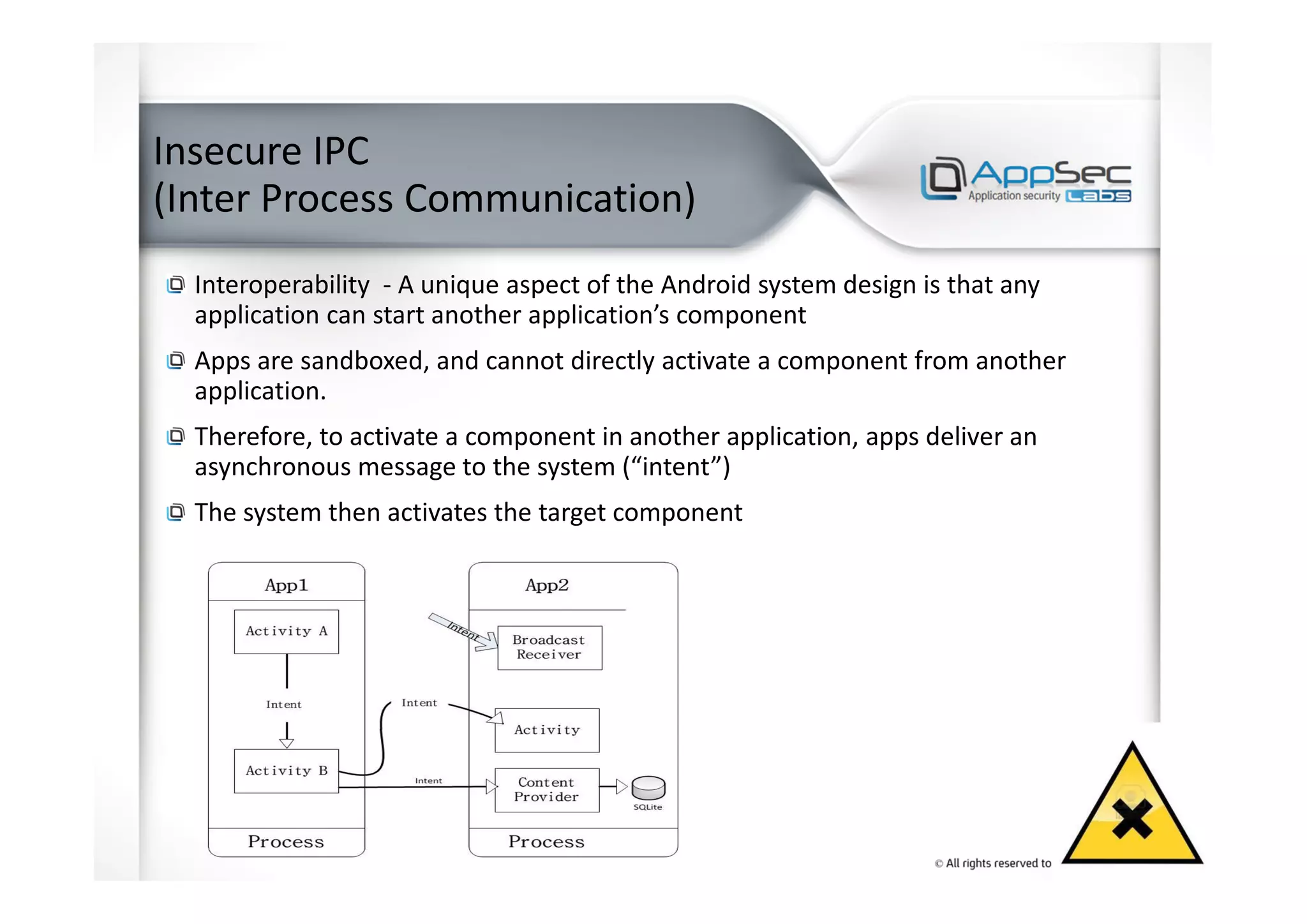
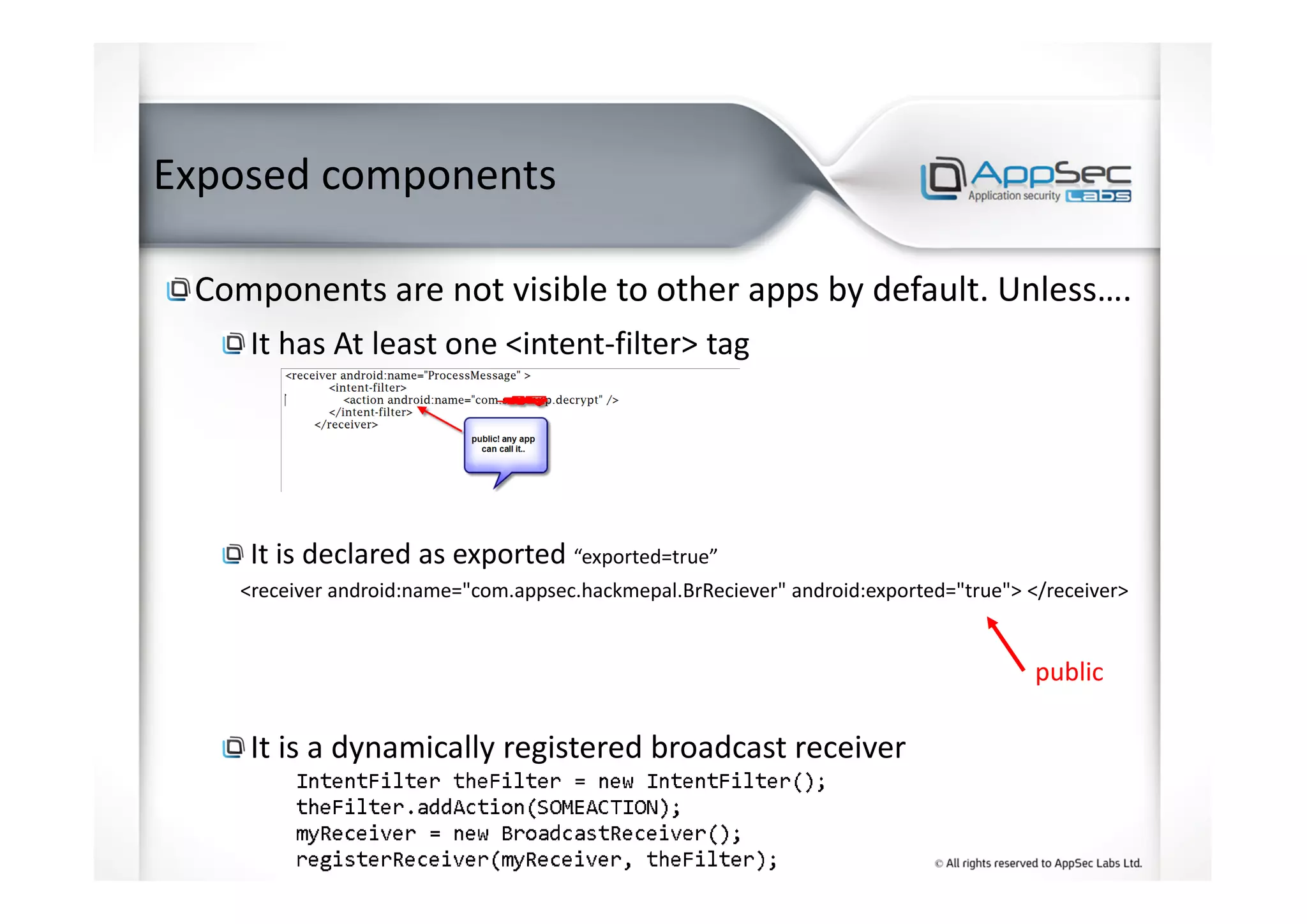
This document summarizes an expert presentation on hacking Android apps. It discusses the top 10 most common Android app vulnerabilities according to OWASP, including weak server-side controls, insecure data storage, lack of transport layer security, unintended data leakage, poor authorization and authentication, broken cryptography, client-side injections, making security decisions via untrusted inputs, improper session handling, and lack of binary protections. Specific attack examples for each vulnerability are provided.





![Another common Mistakes – no
cert validation
• usage of out of date/self signed SSL certificates
TrustManager[] trustAllCerts = new TrustManager[] { new X509TrustManager() {
public java.security.cert.X509Certificate[] getAcceptedIssuers() {
return new java.security.cert.X509Certificate[] {};
}
public void checkClientTrusted(X509Certificate[] chain, String authType)
throws CertificateException { }
public void checkServerTrusted(X509Certificate[] chain, String authType)
throws CertificateException { }
}};](https://image.slidesharecdn.com/androidapphacking-erezmetula-150618122600-lva1-app6891/75/Android-App-Hacking-Erez-Metula-AppSec-15-2048.jpg)