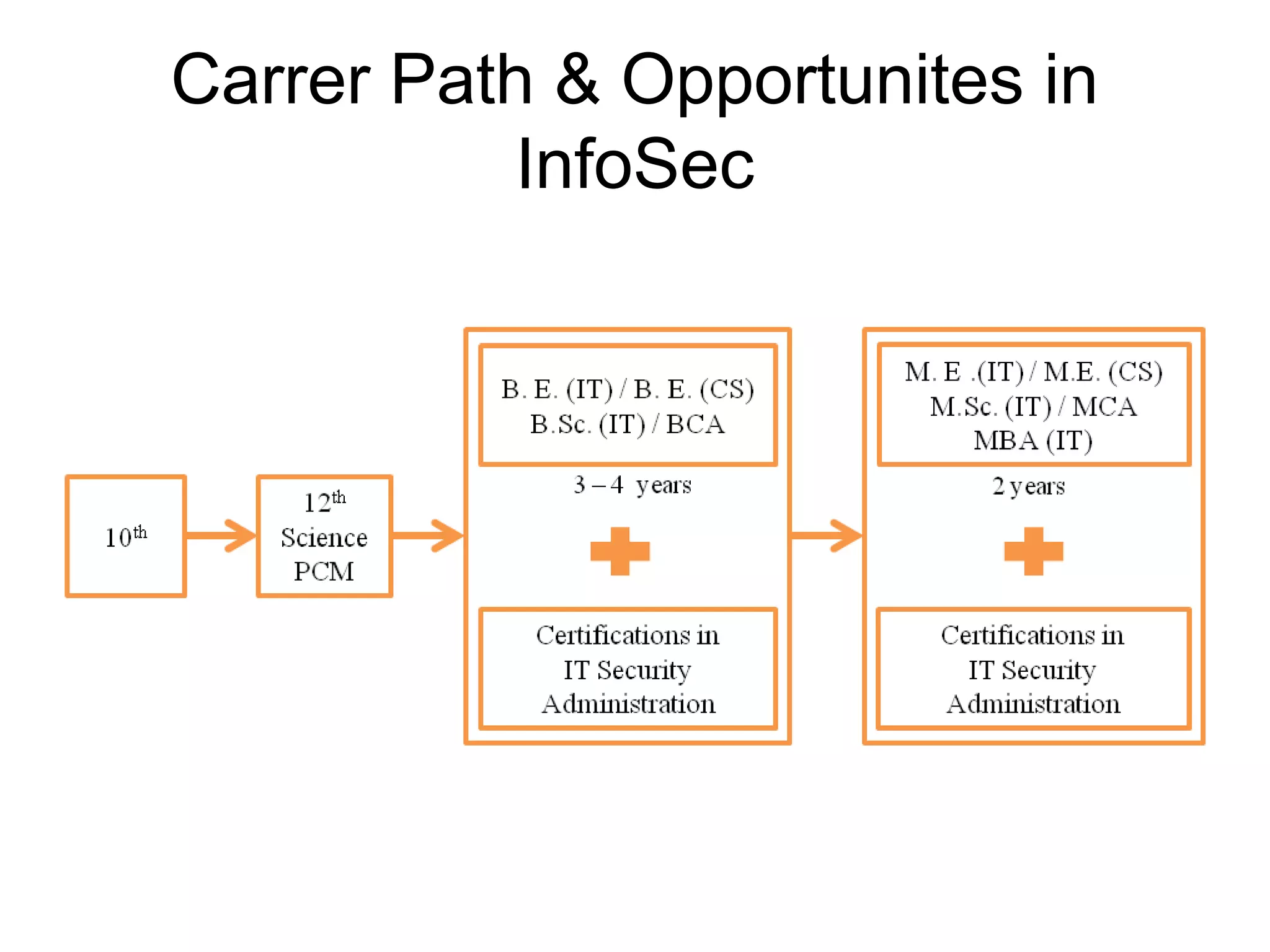
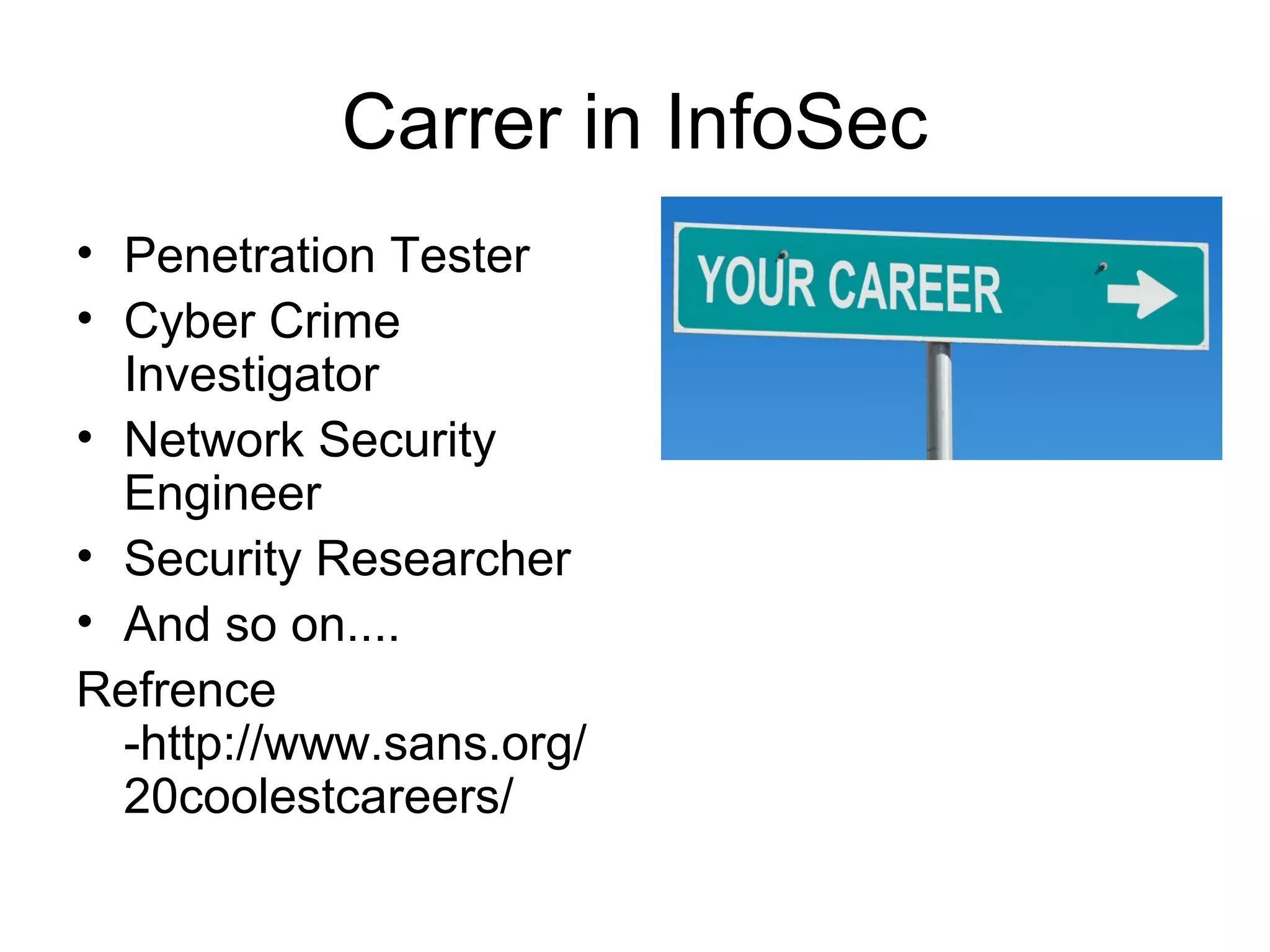
This document provides an introduction to information security topics such as penetration testing, hacking, and ethical hacking. It defines penetration testing as attacking a system to find security weaknesses and potential access. Hacking is exploiting vulnerabilities in computer systems, while ethical hacking does the same thing legally with permission. The document also discusses the differences between hackers and crackers, careers in information security such as penetration testing and cyber crime investigation, and provides references for further information security terms and resources.