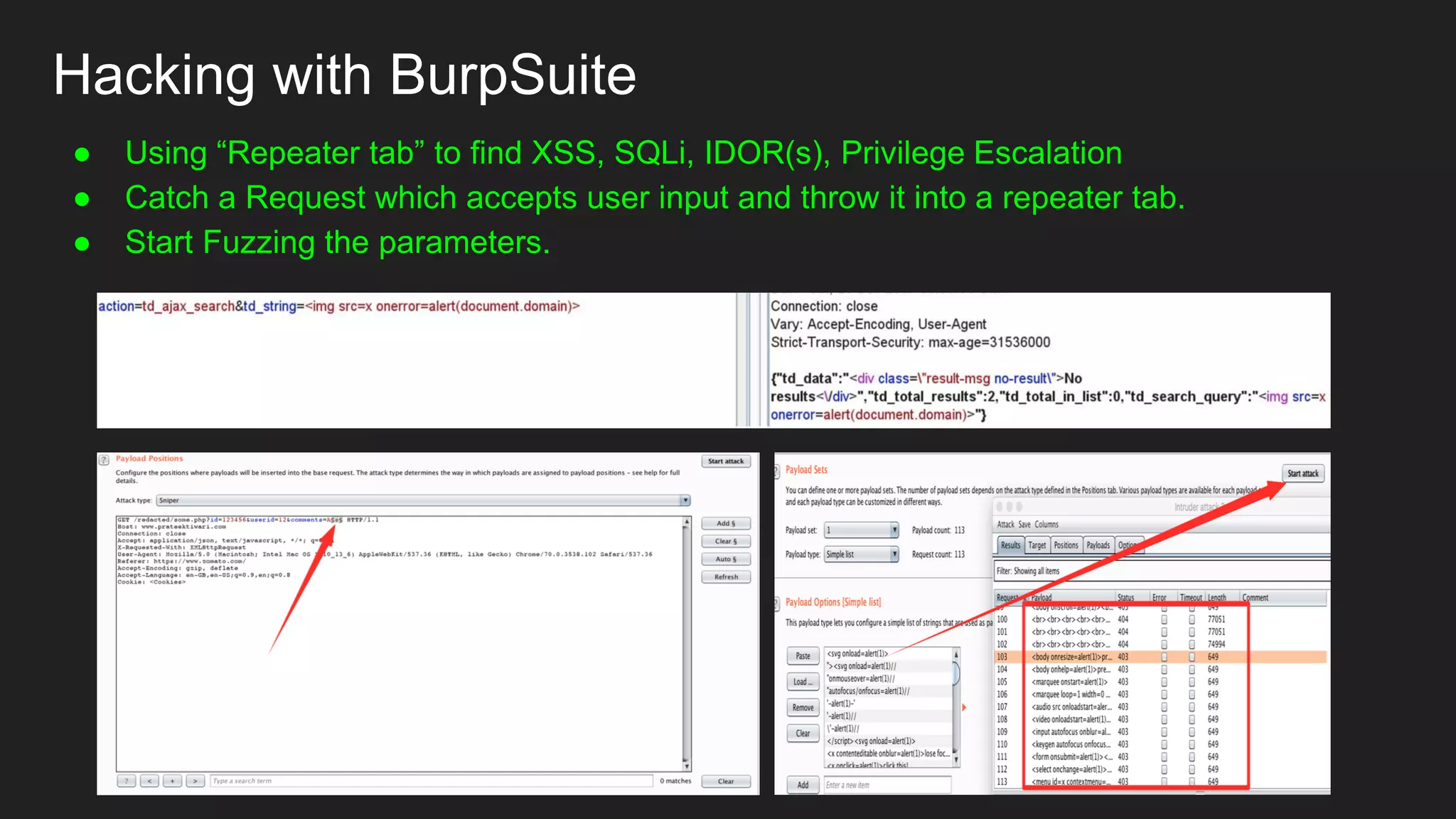
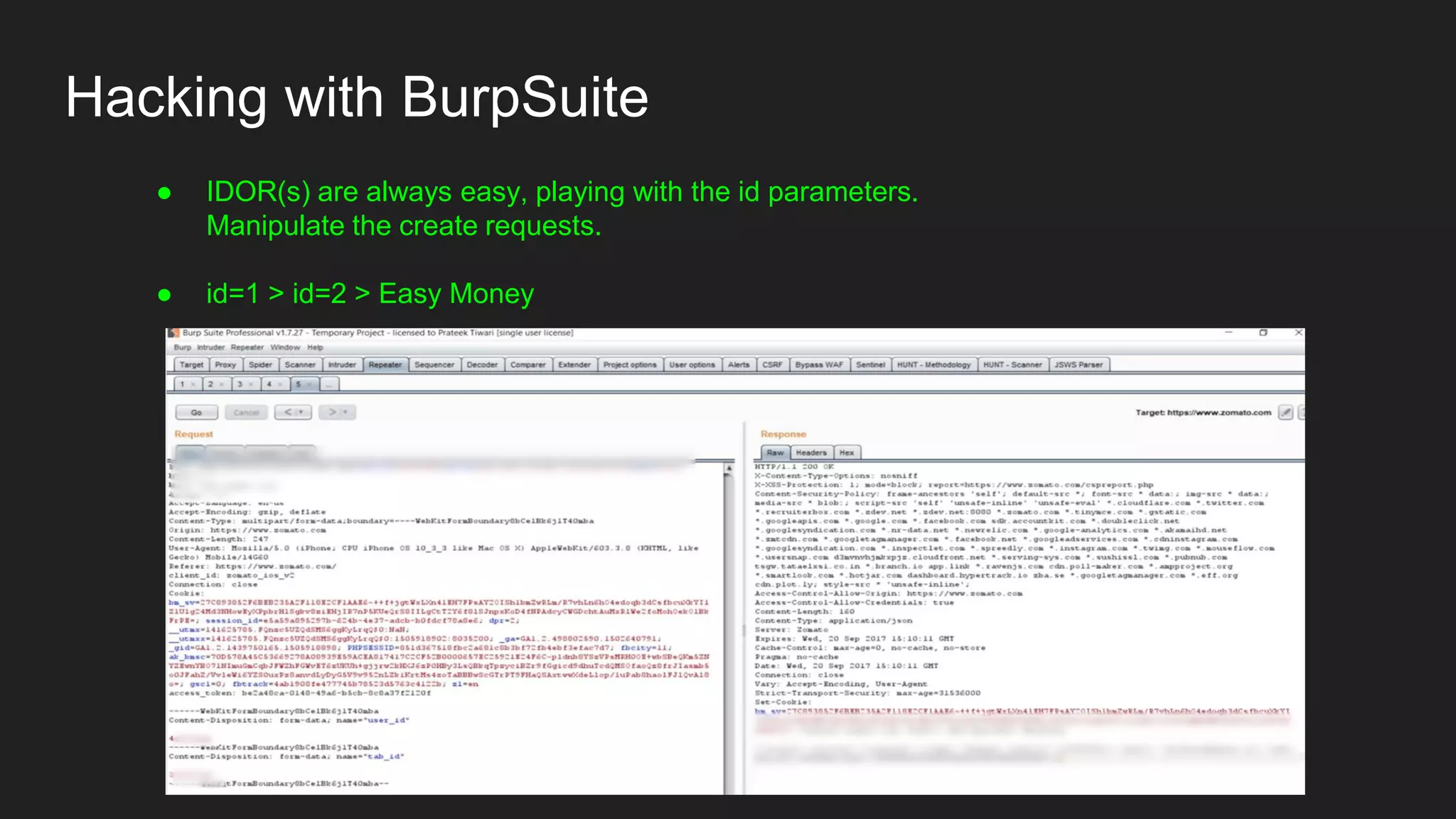
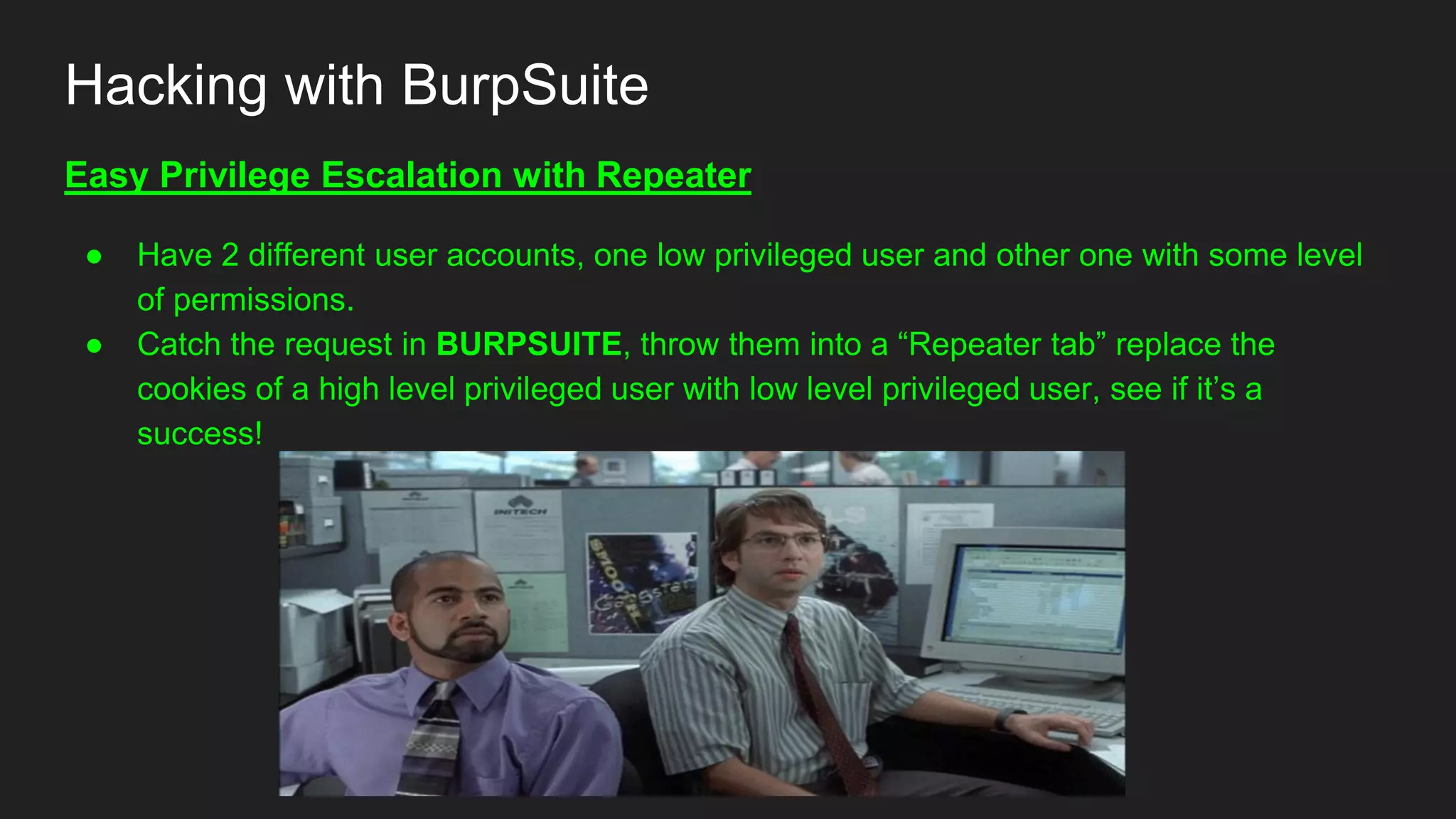
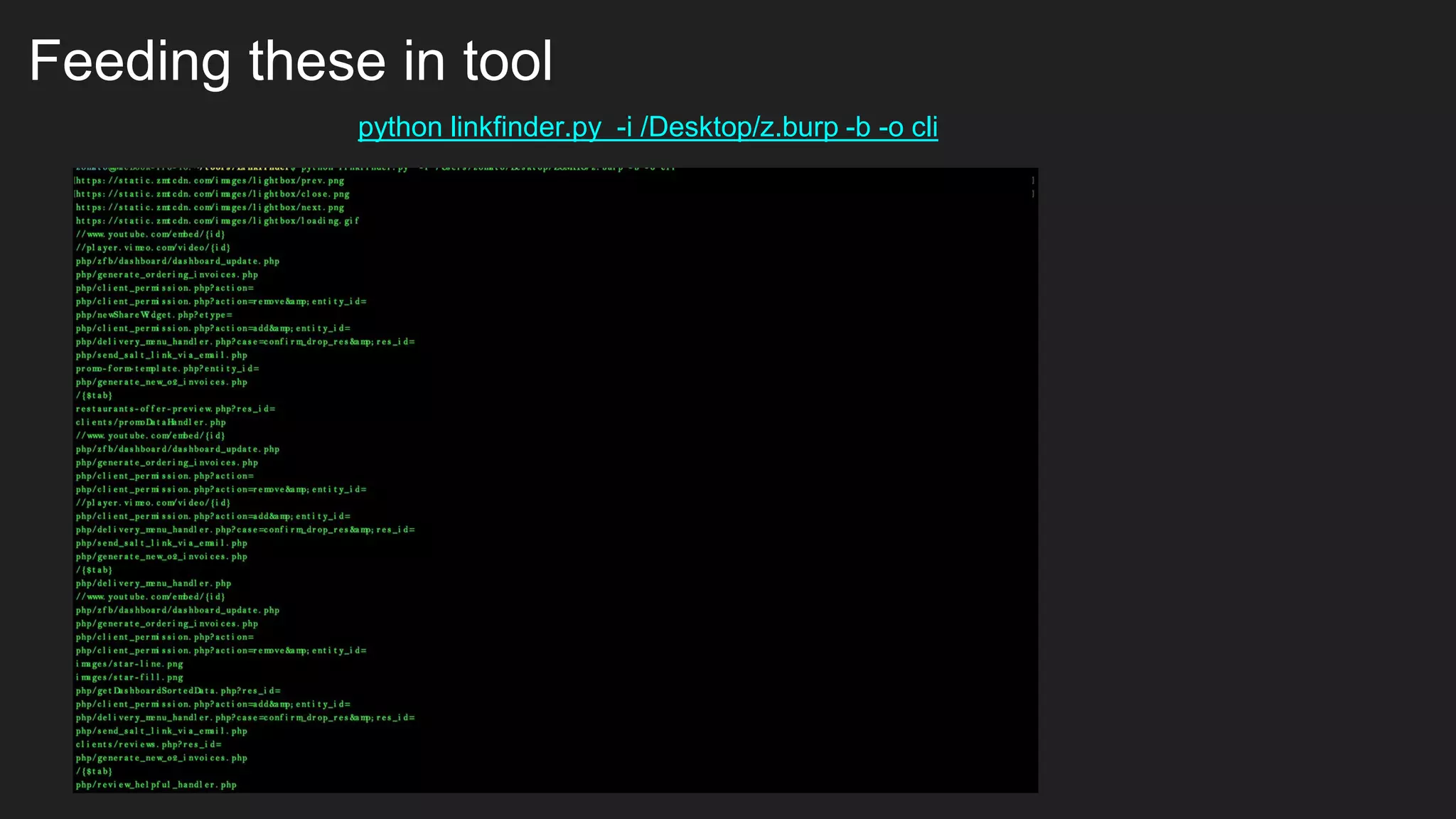
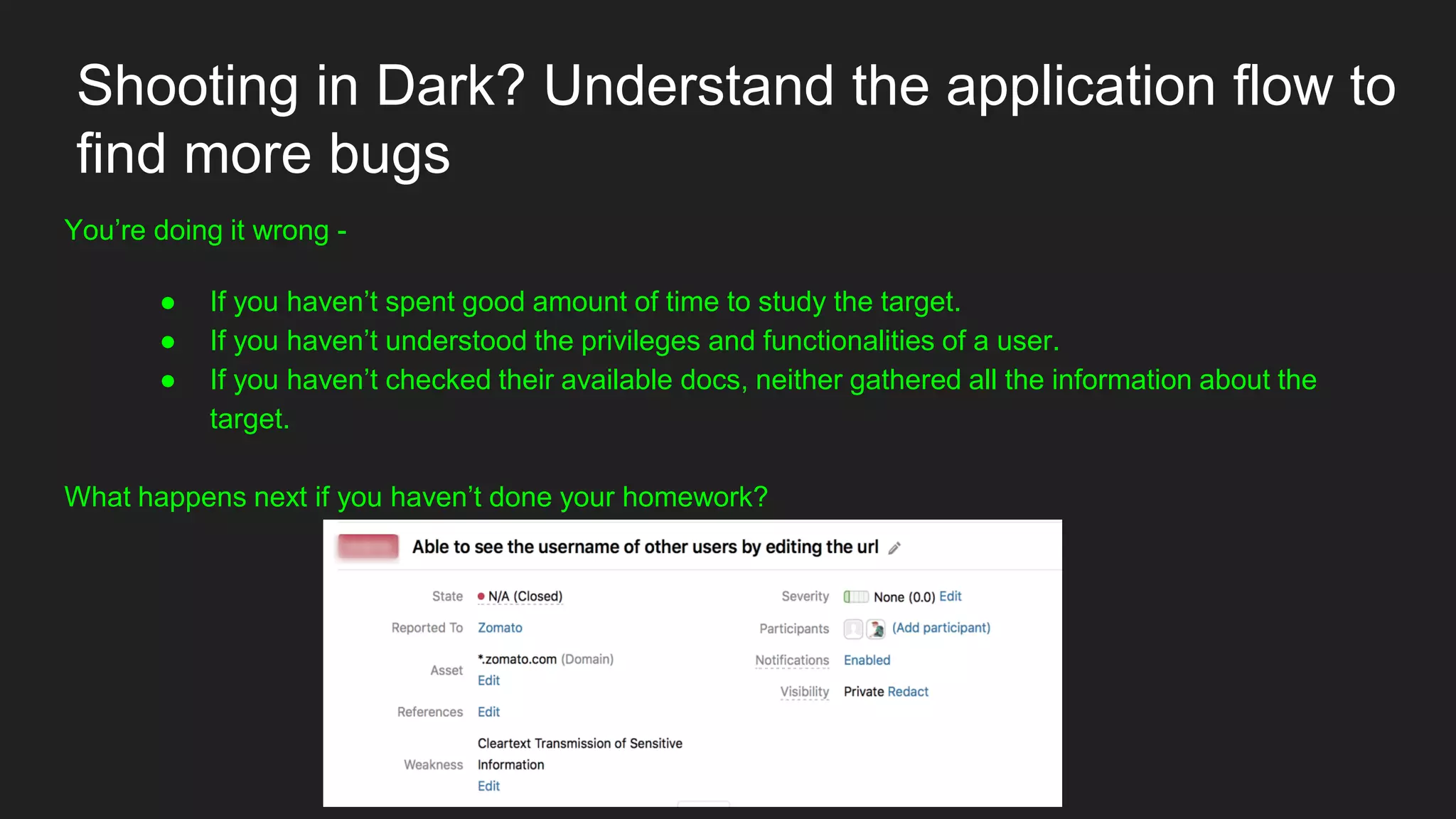
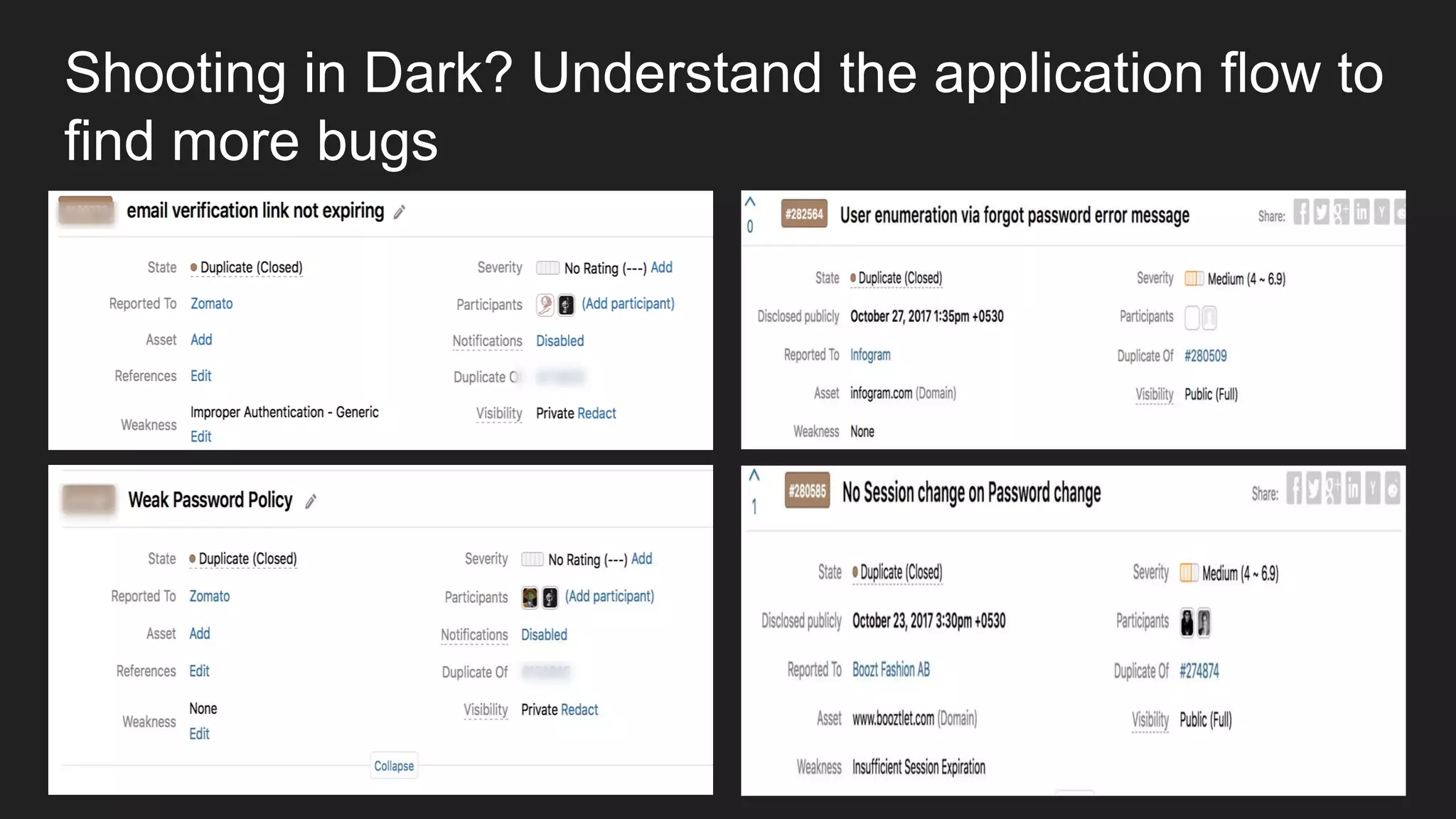
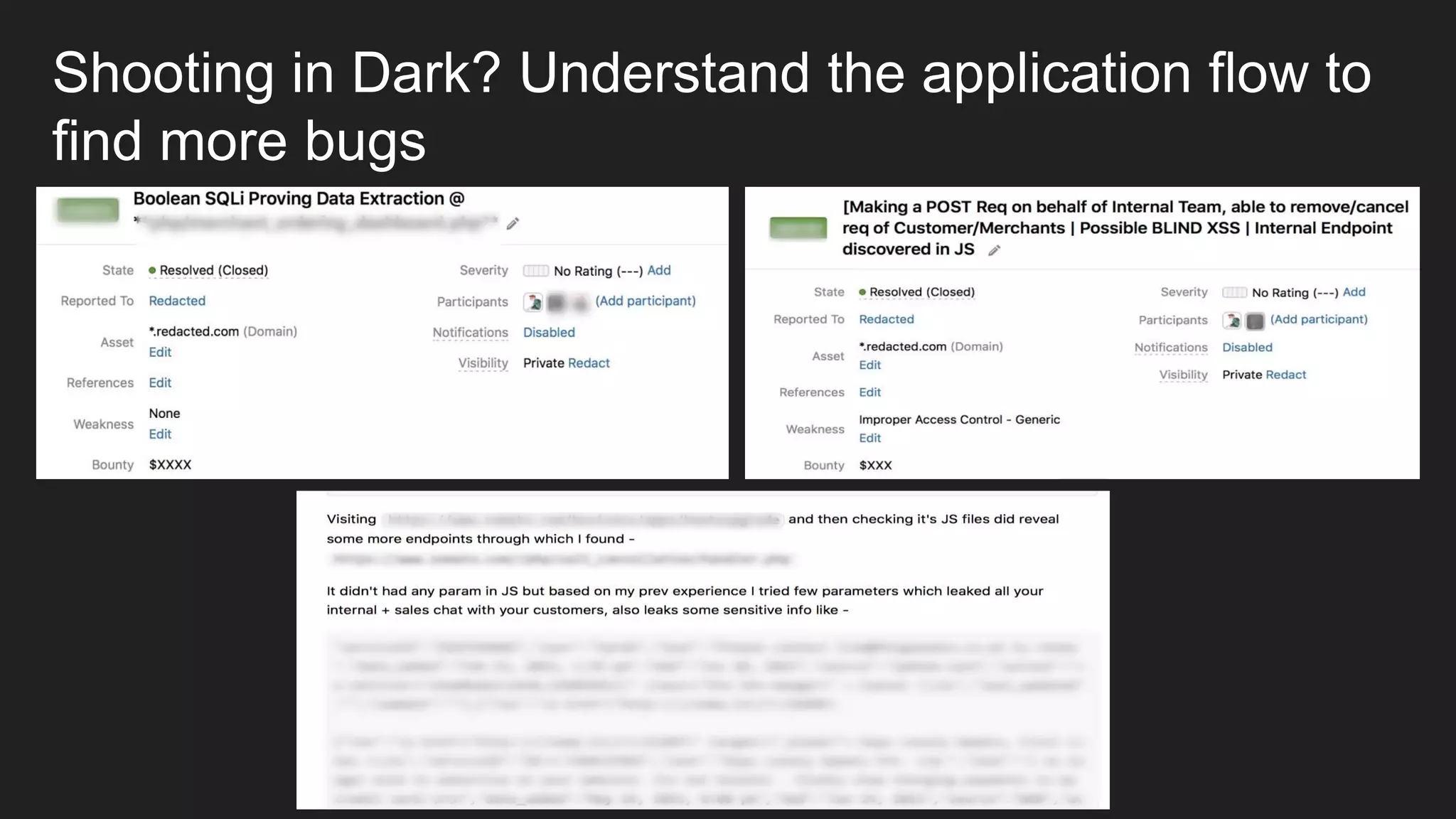
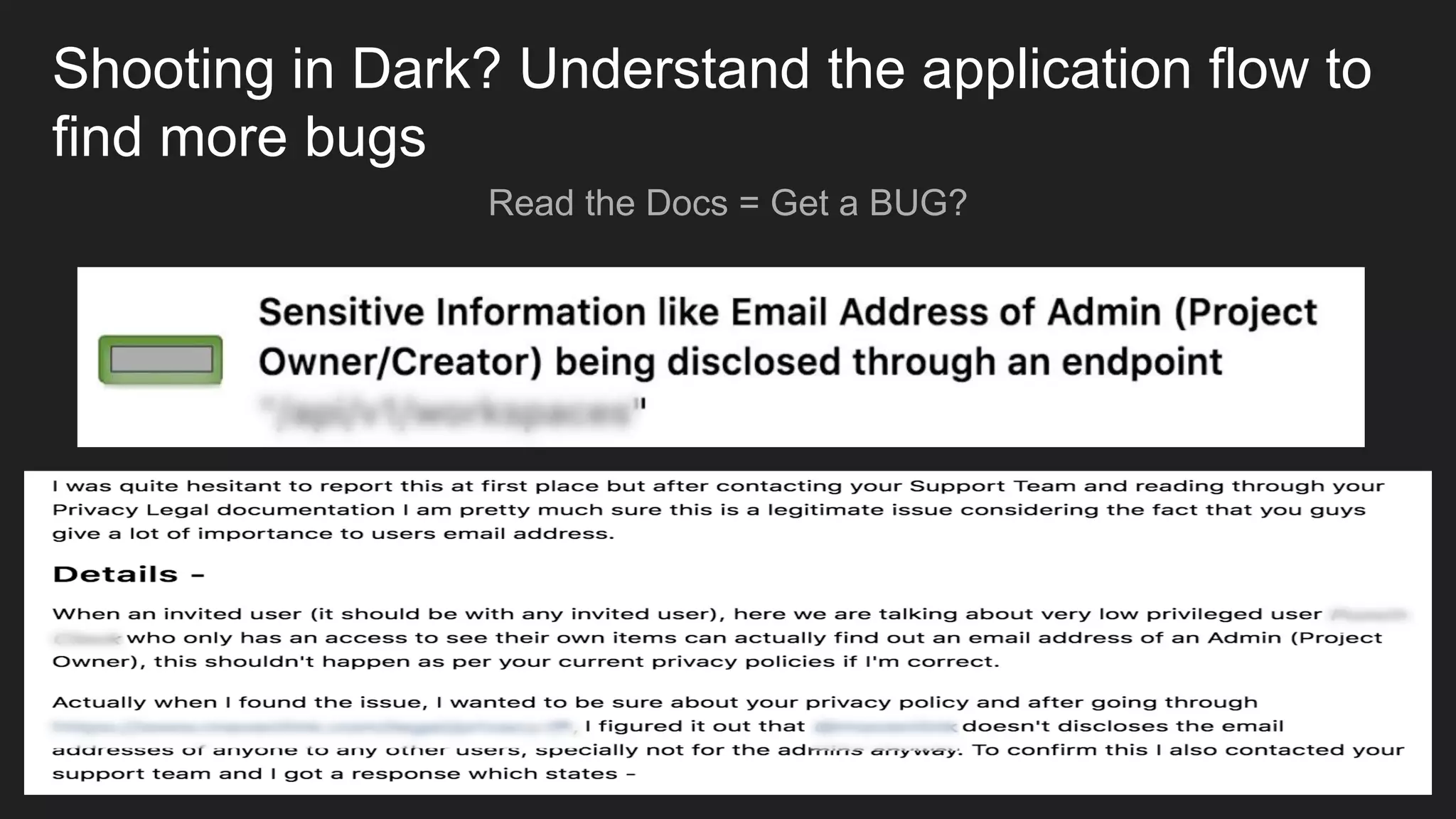
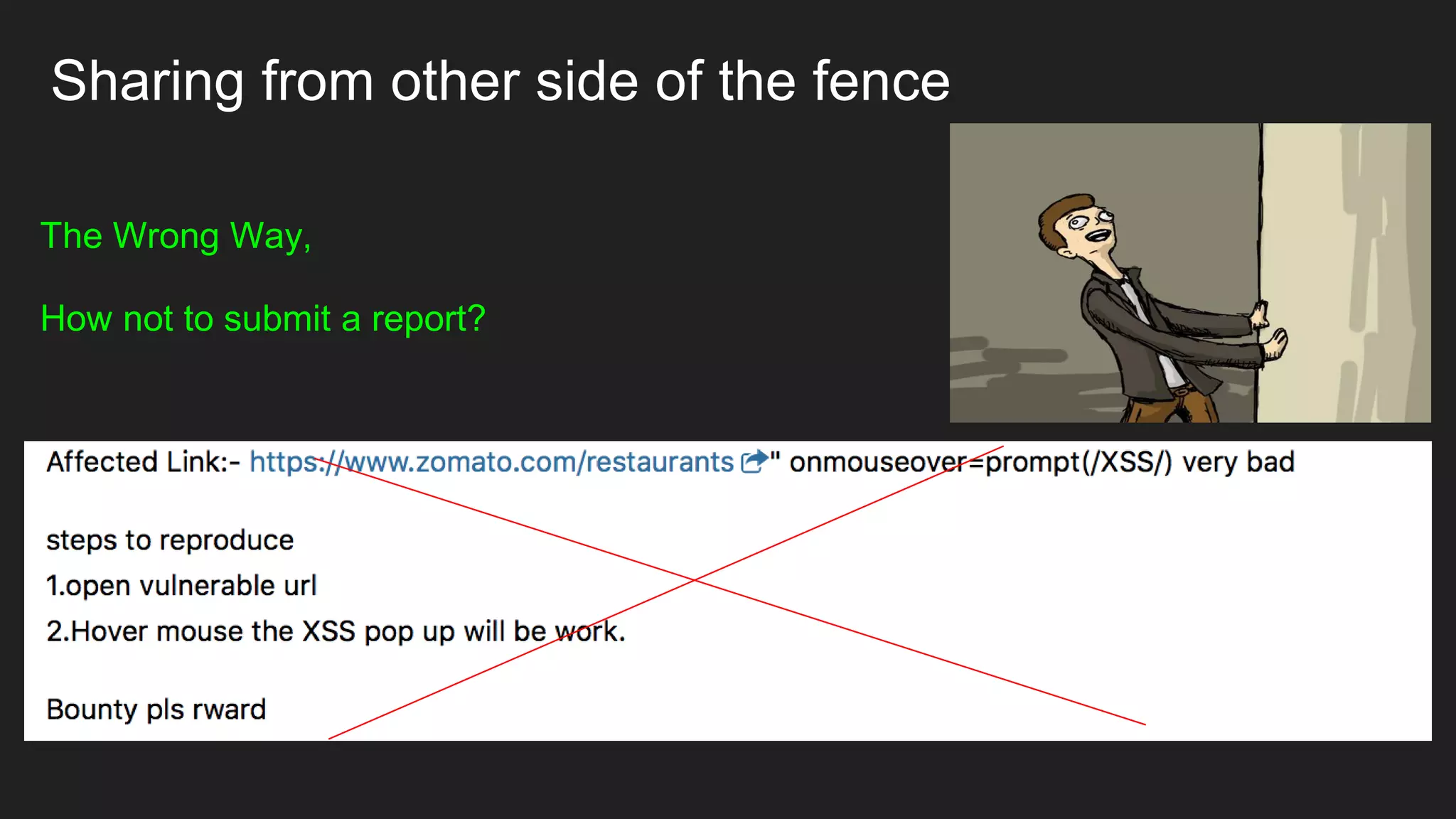
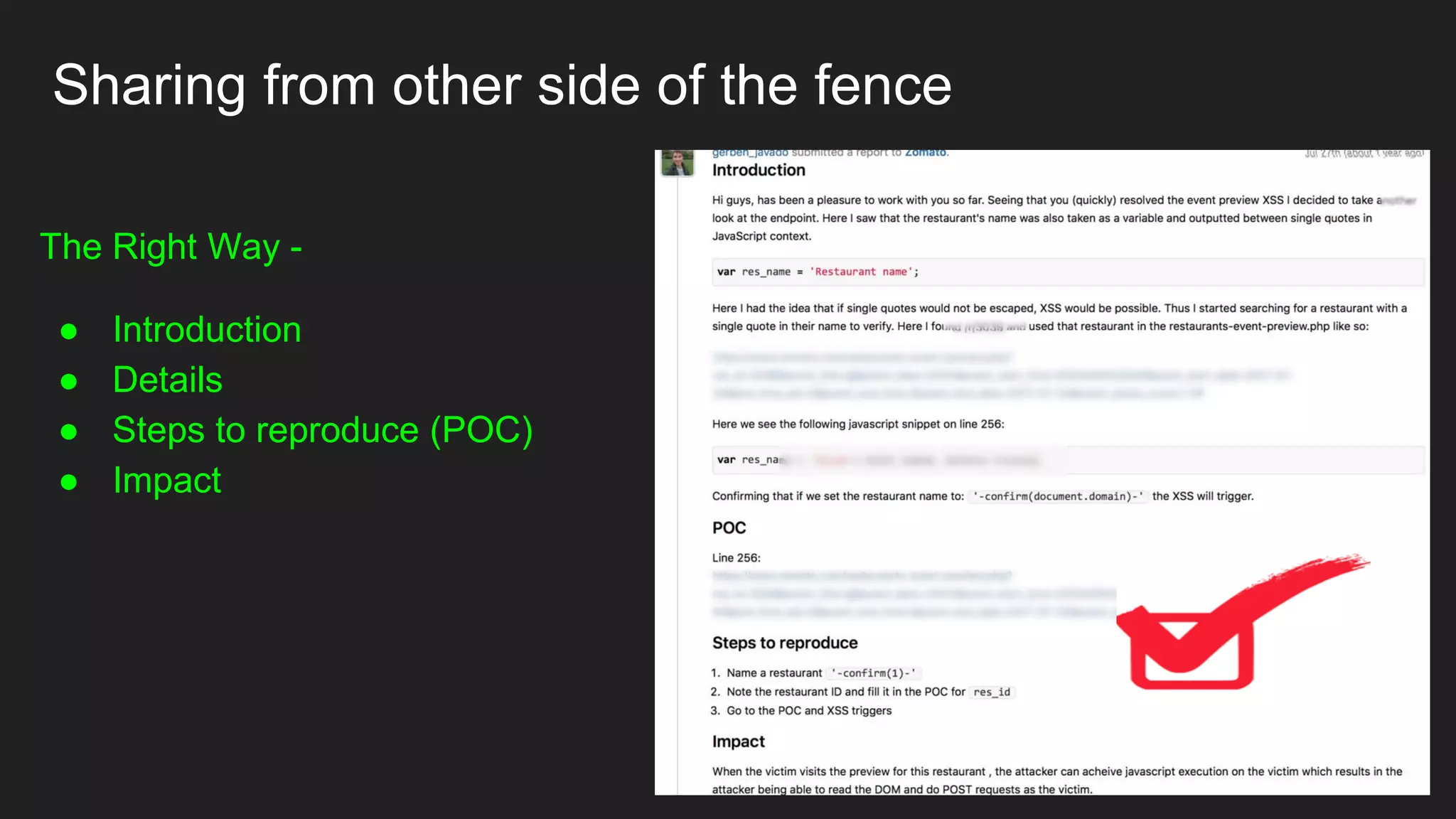
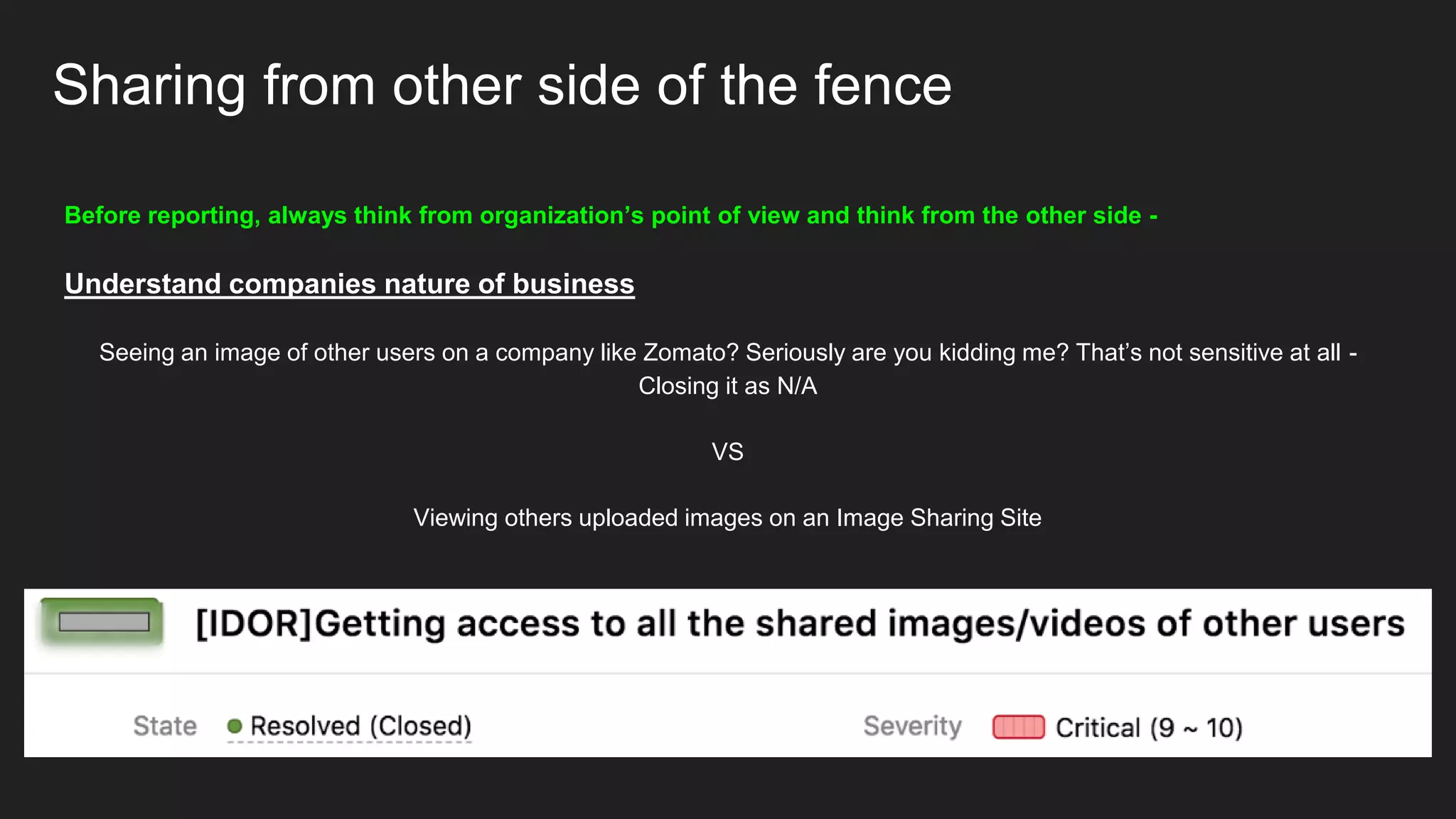
Bug bounty roadmap covers various techniques for finding vulnerabilities such as understanding the target application flow, using passive reconnaissance tools to discover assets, hacking with Burp Suite to find bugs like XSS and SQLi, and keeping up with new trends to improve bounty hunting. The presentation emphasizes thorough preparation and research to avoid duplicate reports and better understand the target before launching attacks. It also provides tips for writing high-quality bug reports to build good relationships with security teams.






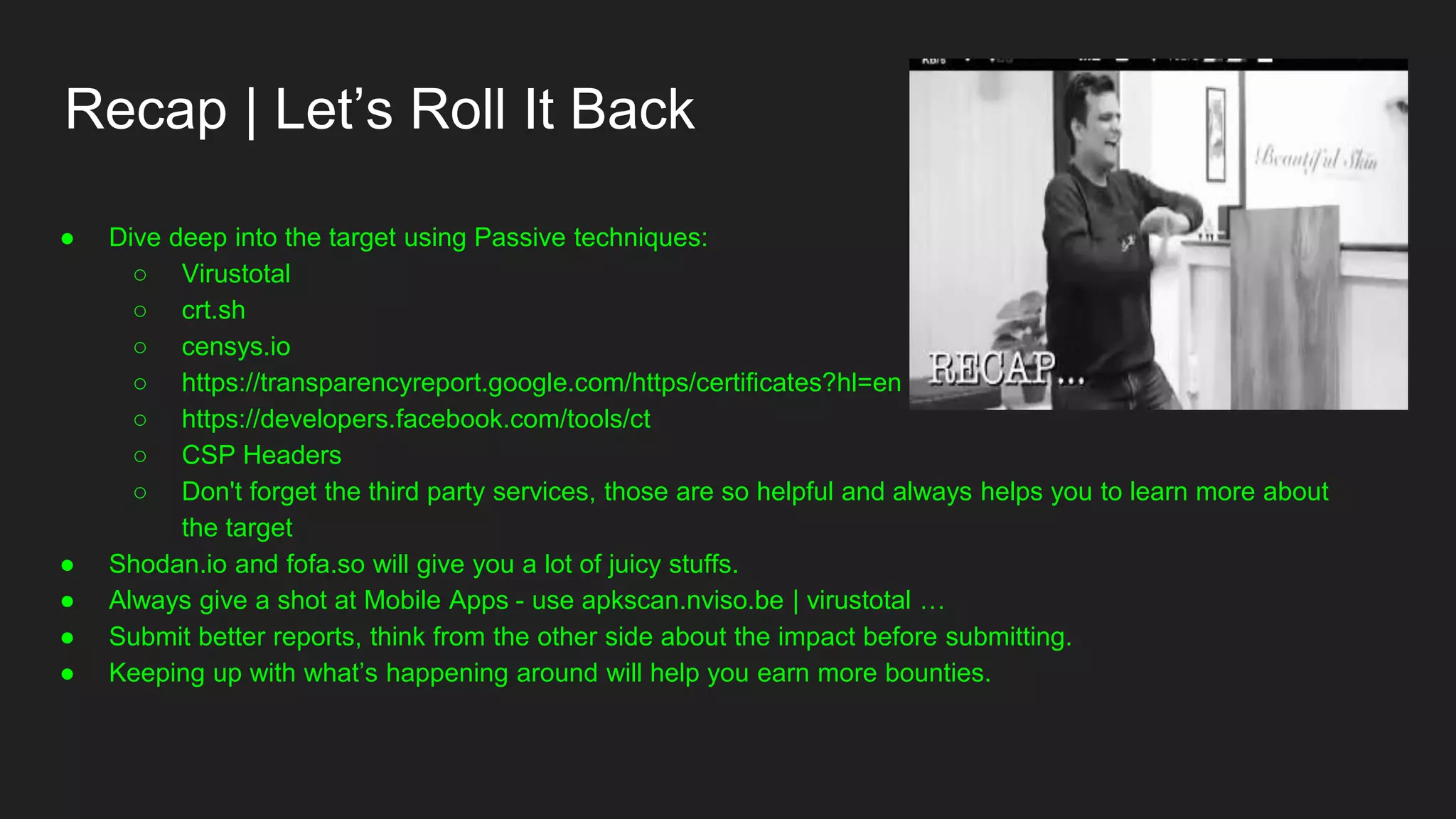
![Diving deep into the target using passive..sh Recon
Find all the **ASSETS** that belongs to that organisation. Assets?
○ Domains?
○ Subdomains?
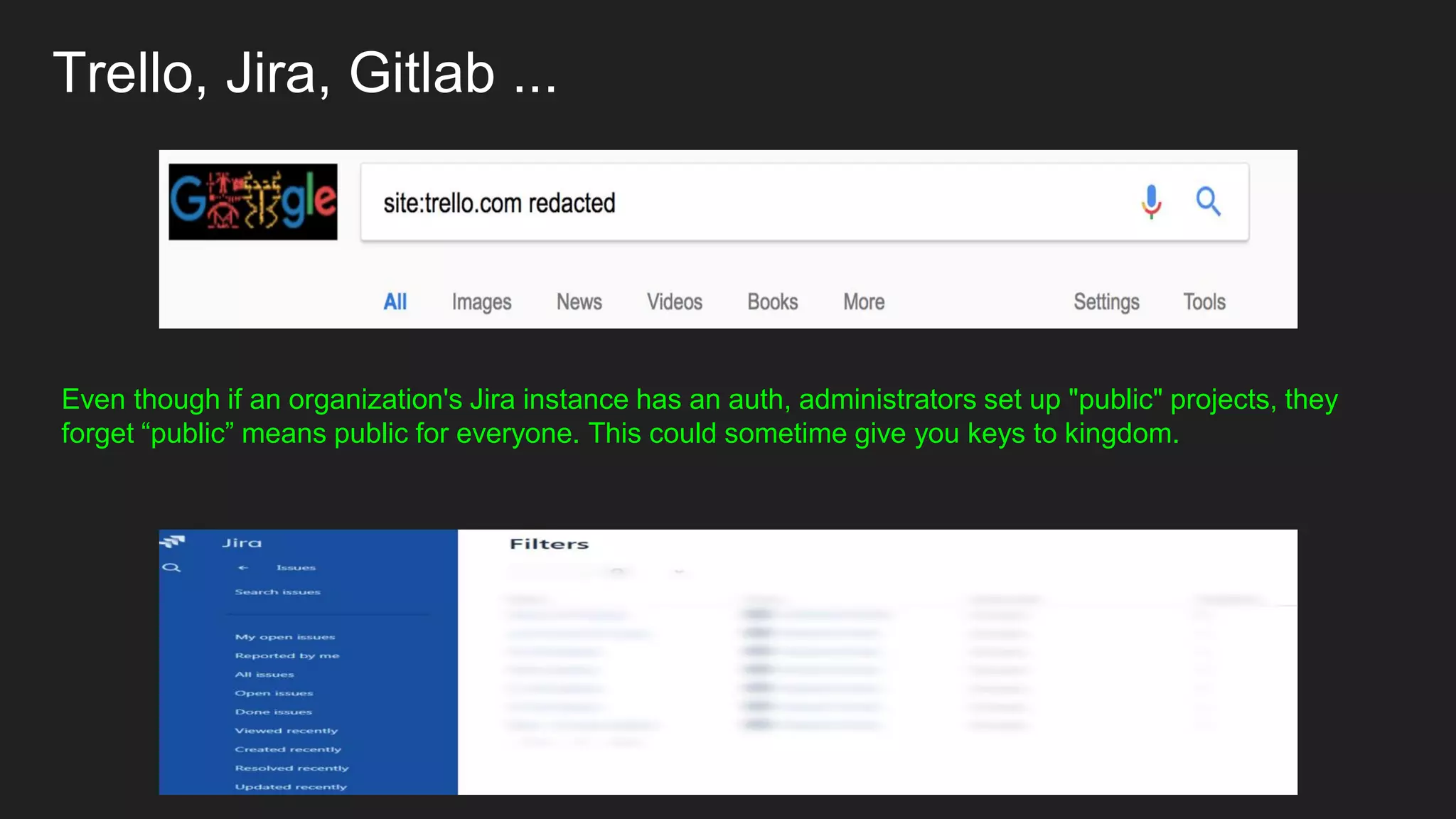
○ 3rd Party Services used by Organisation (GitHub, Jira, Trello, Jenkins, GitLab, etc...)
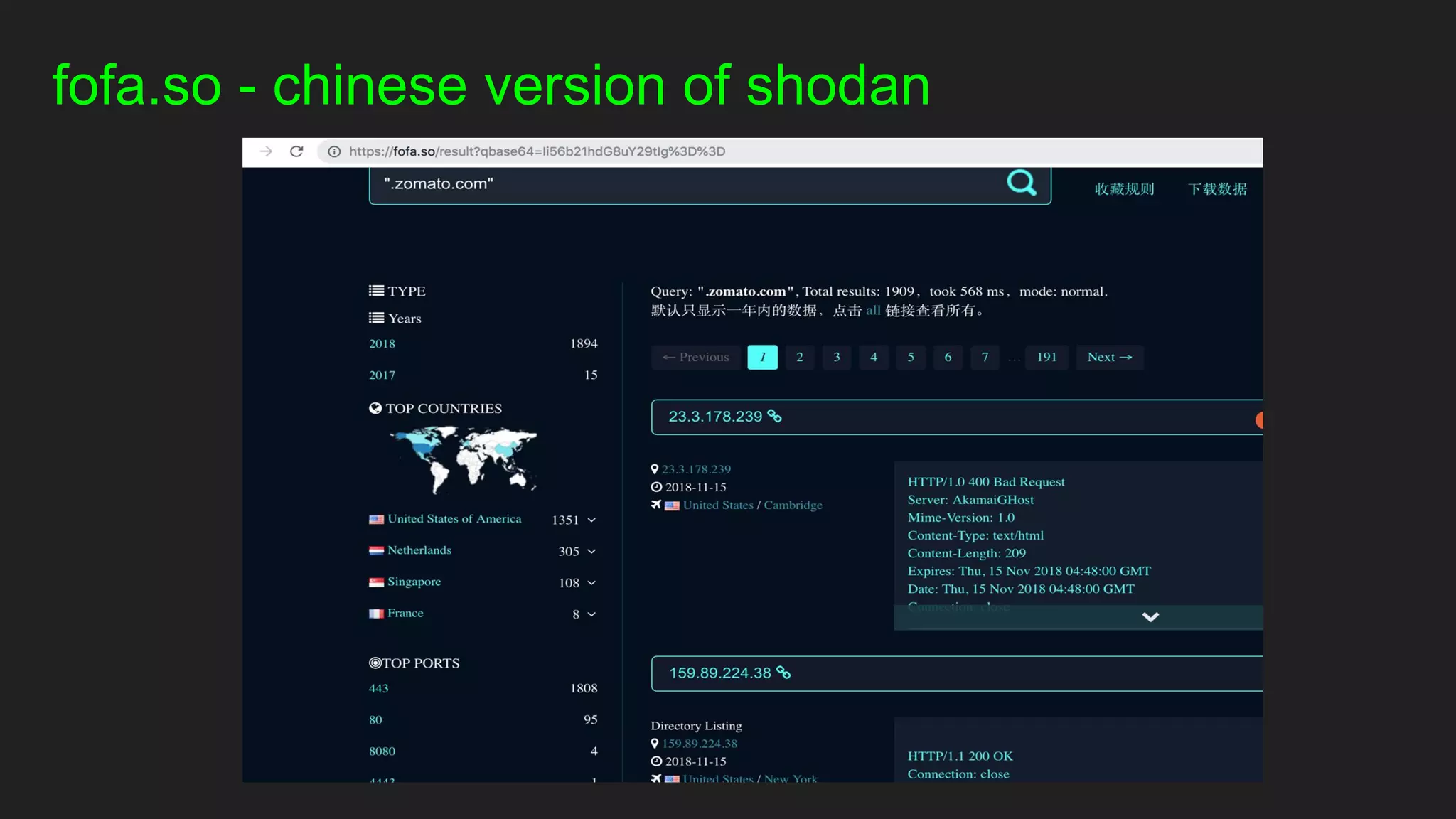
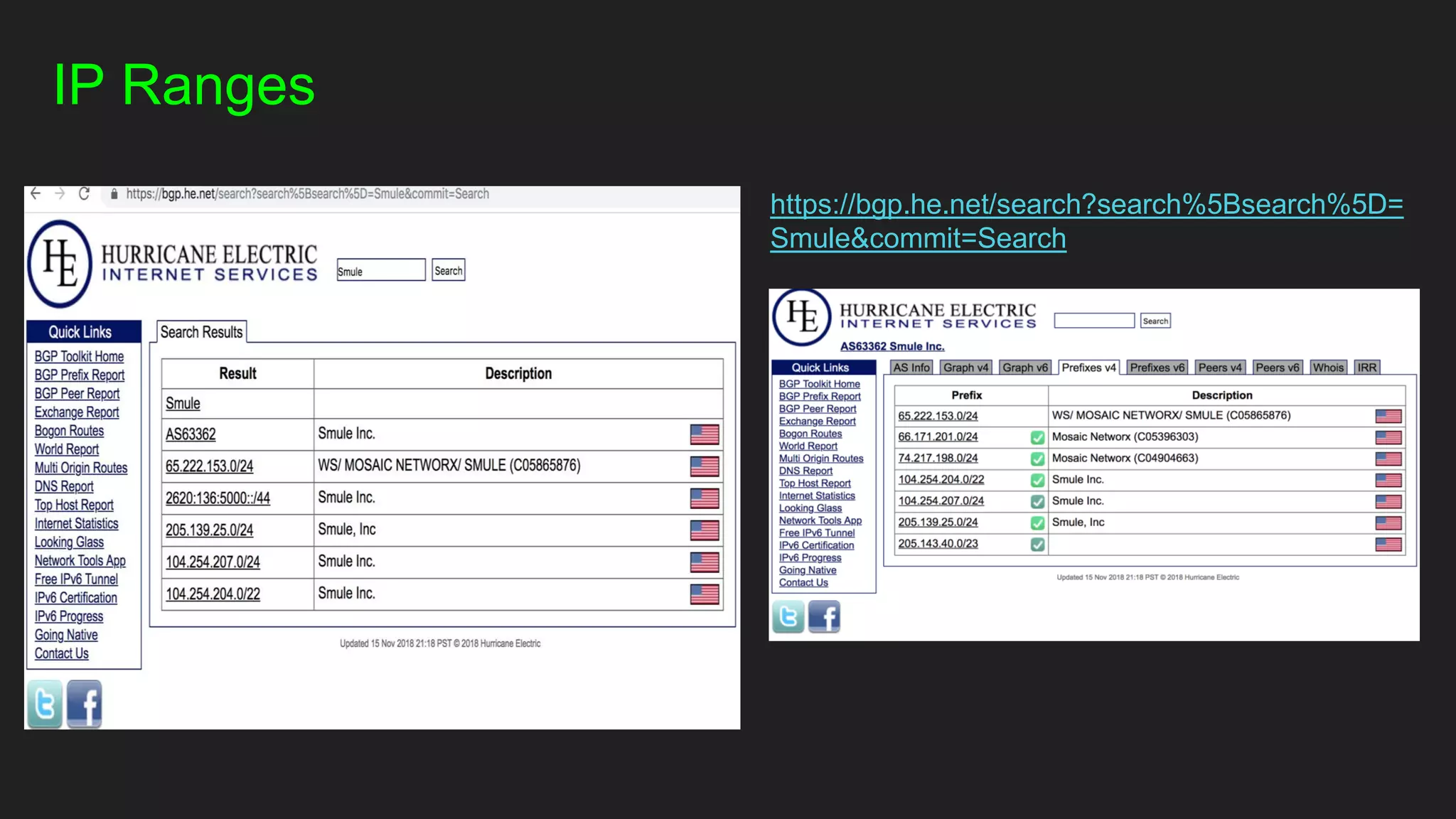
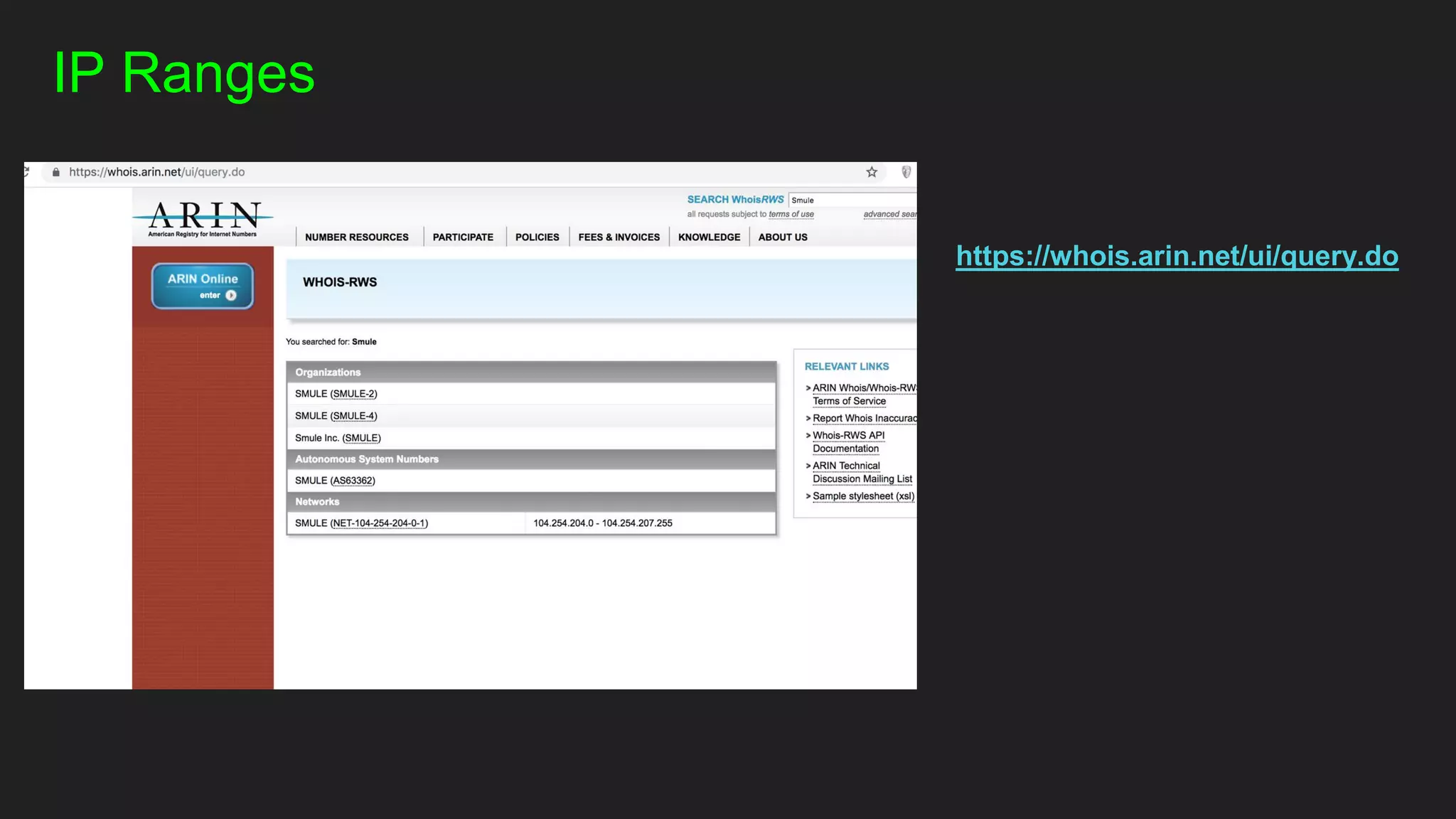
○ IP Ranges?
○ iOS / Android Apps?
○ Doesn’t ends [n number of assets] ..….](https://image.slidesharecdn.com/bugbountyroadmap-adam-200829071400/75/BugBounty-Roadmap-with-Mohammed-Adam-10-2048.jpg)
![Subdomains | Asset(s) Identification
● Subfinder [https://github.com/subfinder/subfinder]
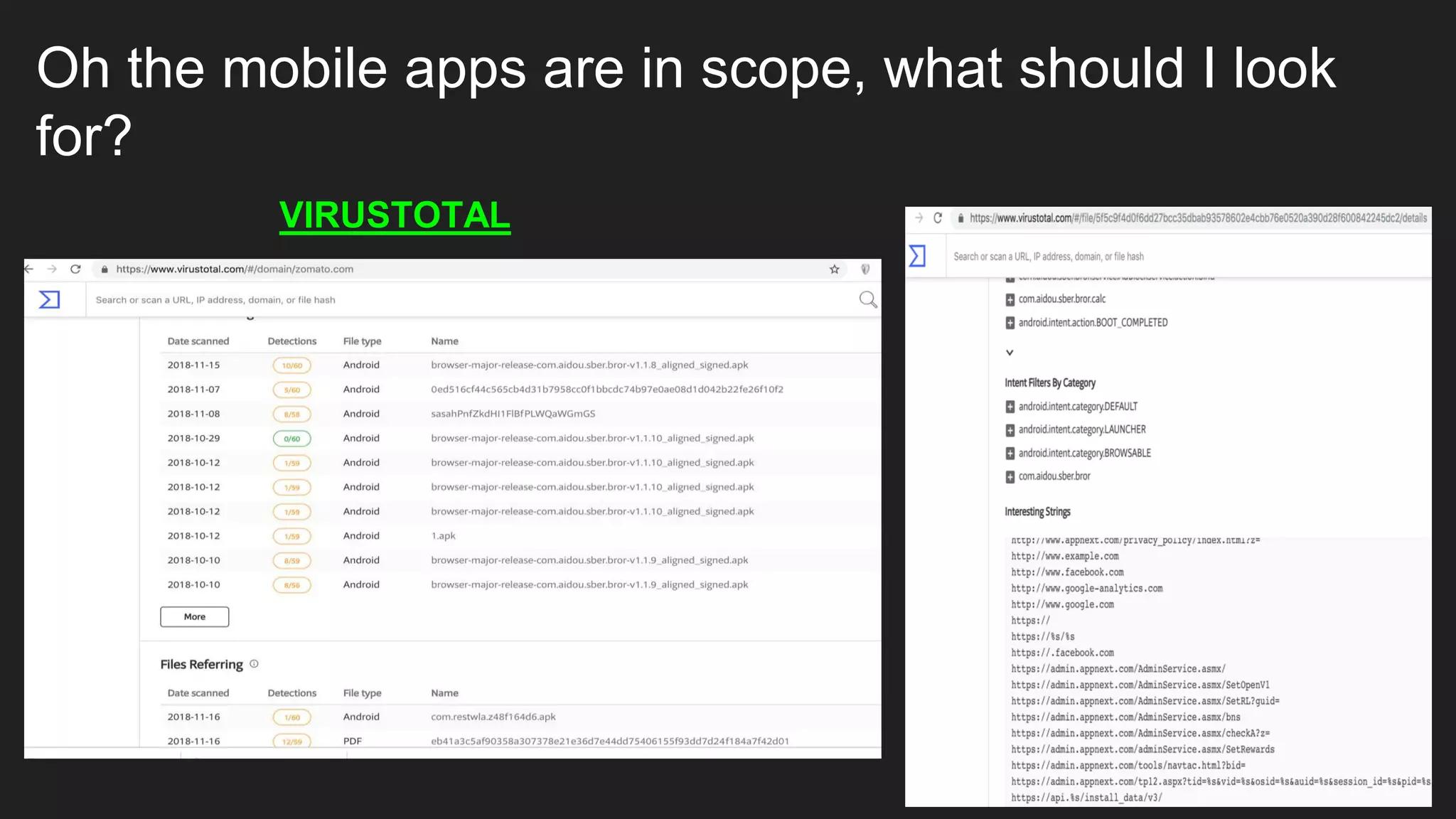
● VirusTotal [https://www.virustotal.com/#/domain/domain.com]
● Certificate Transparency [https://crt.sh/?q=%.domain.com]
● Censys [https://www.censys.io]
● Google - site:example.com -www [Other Search Engines - Bing, DuckDuckGo, Yahoo]
● Google Certificate Transparency
[https://transparencyreport.google.com/https/certificates?hl=en]
● Facebook Certificate Transparency Monitoring
[https://developers.facebook.com/tools/ct]
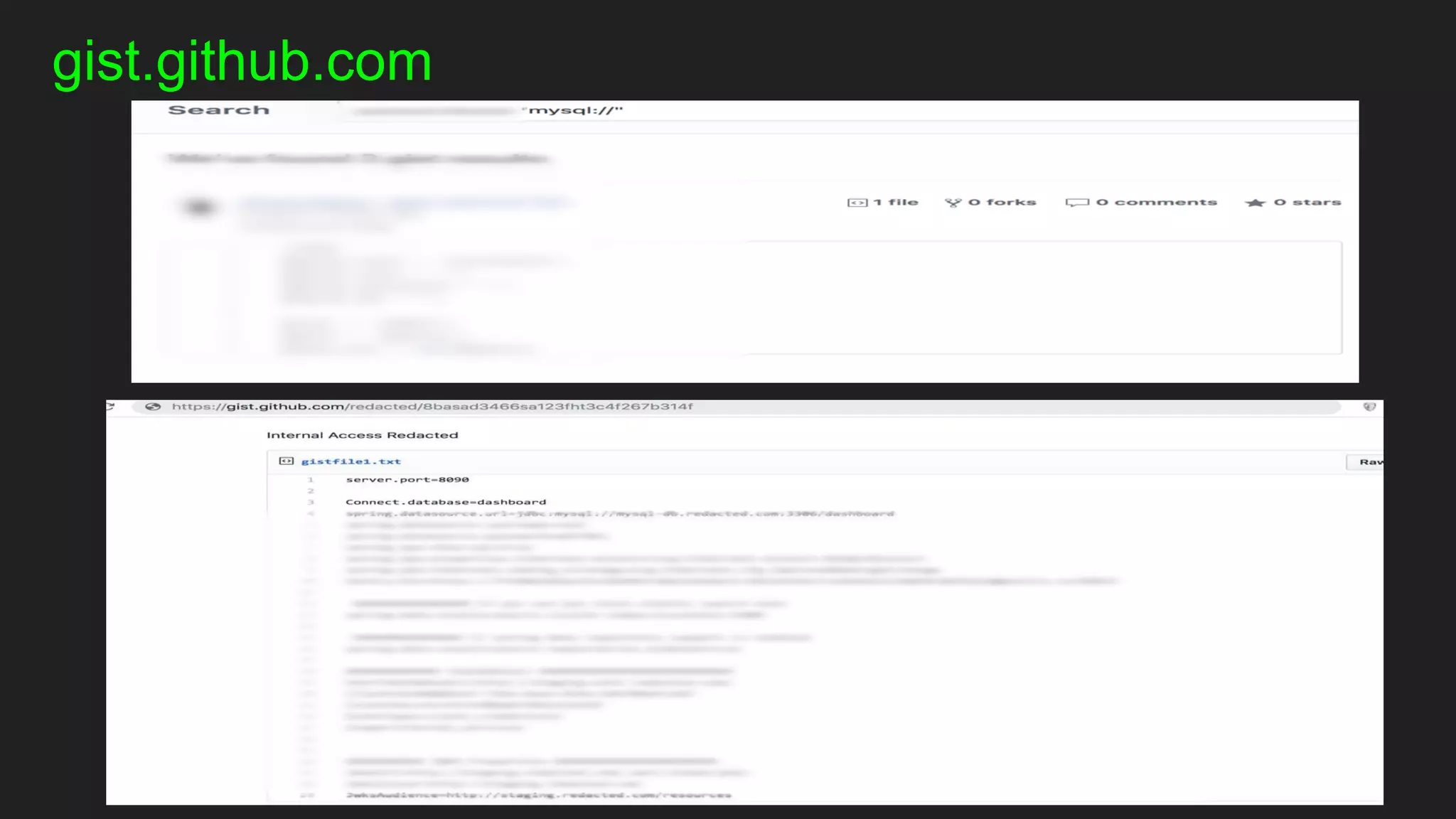
● GitHub, Gist, Gitlab, Trello, Jira, etc…](https://image.slidesharecdn.com/bugbountyroadmap-adam-200829071400/75/BugBounty-Roadmap-with-Mohammed-Adam-11-2048.jpg)




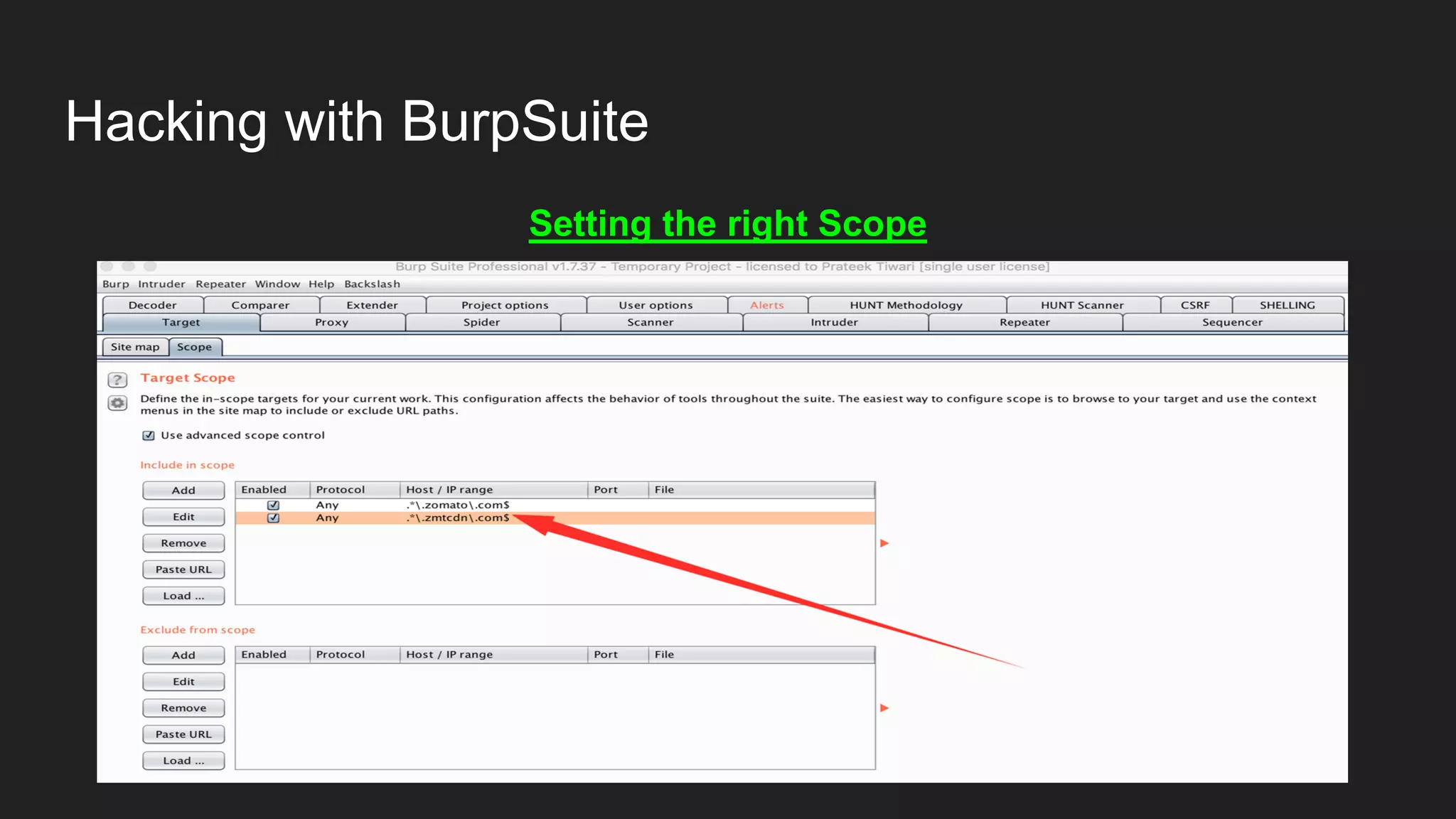
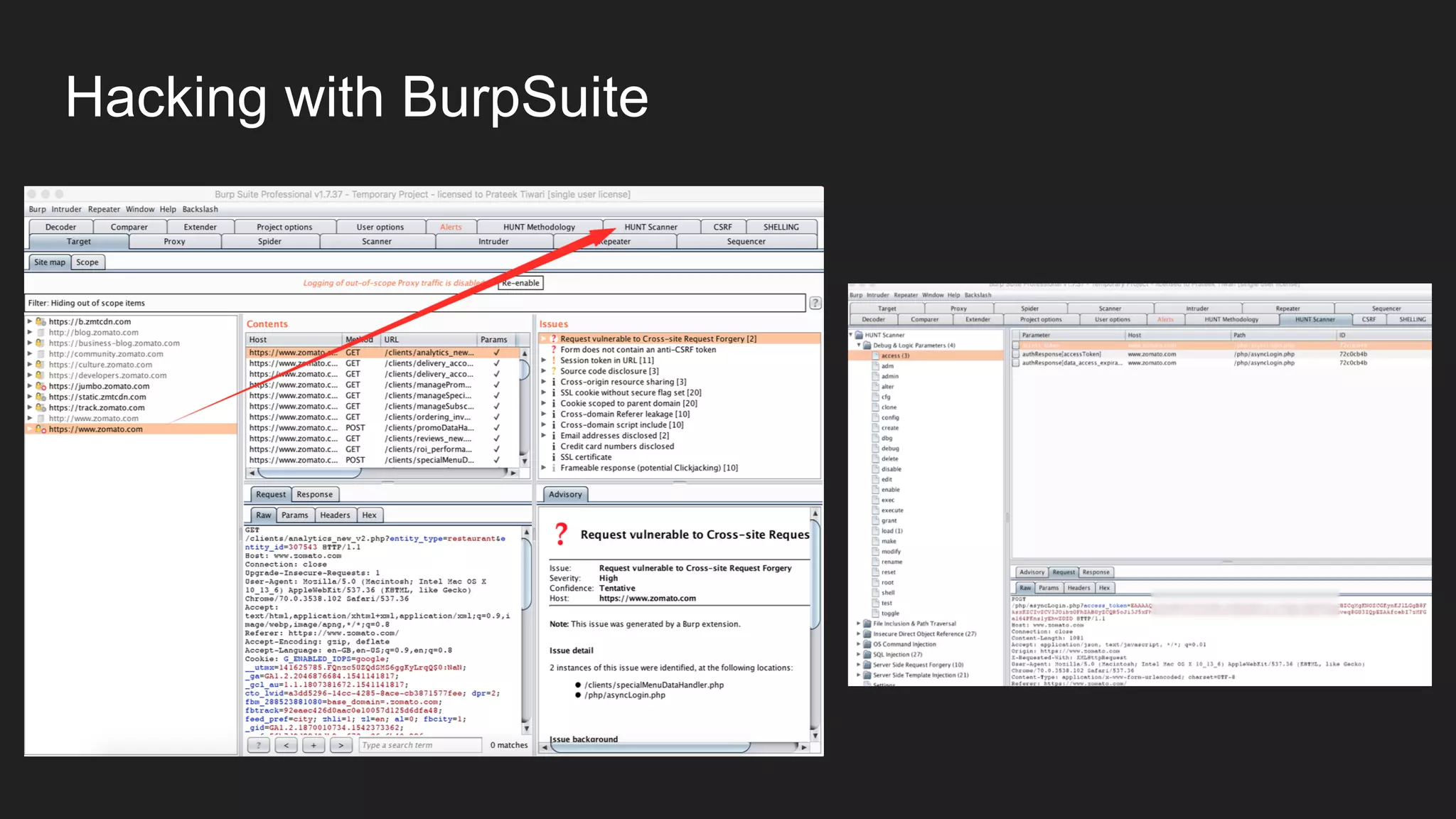


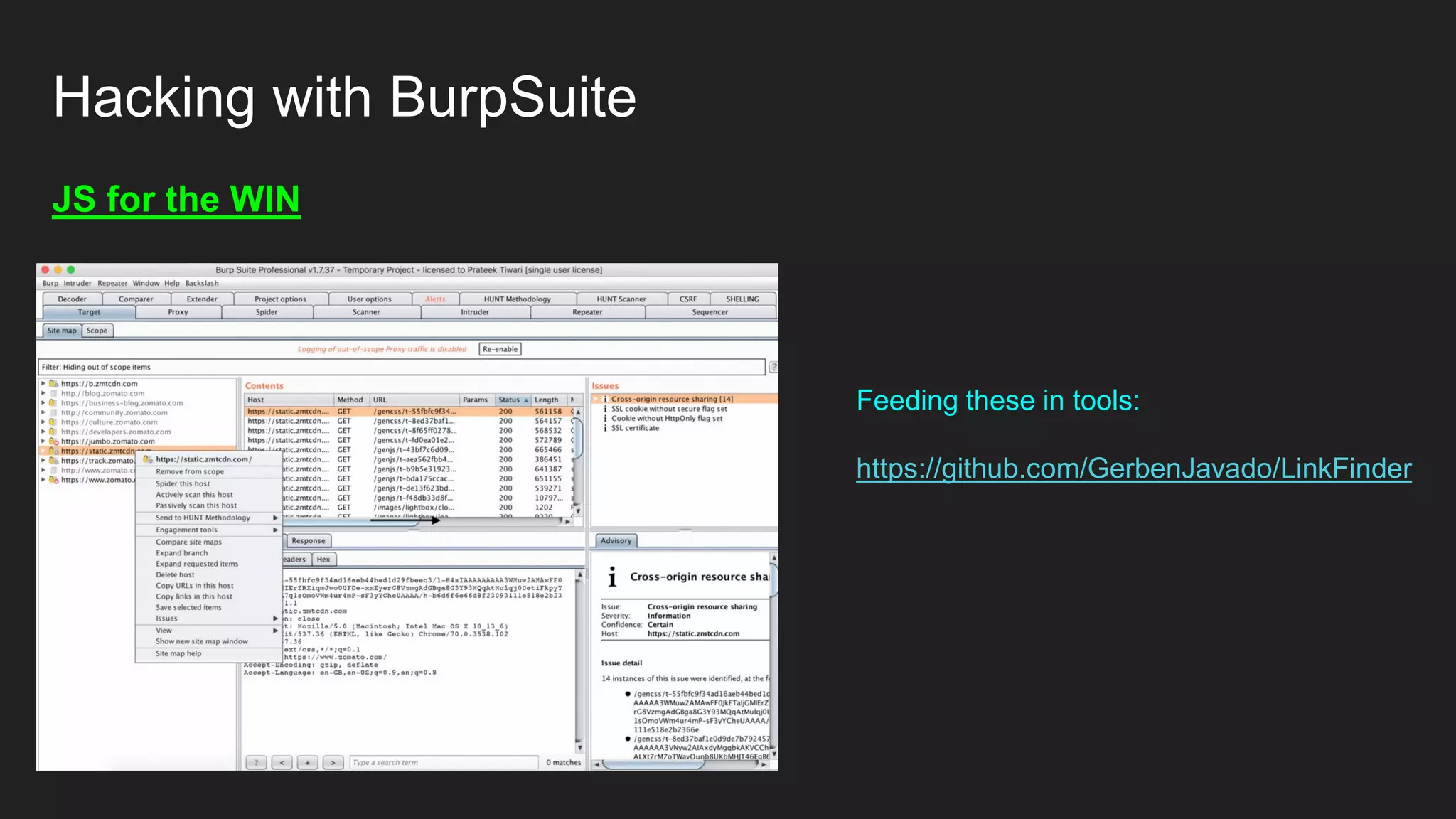
![Hacking with BurpSuite
Did you know? You don’t always need an automated Script to demonstrate the
impact of any data leak [PIIs].
Intruder for the win!](https://image.slidesharecdn.com/bugbountyroadmap-adam-200829071400/75/BugBounty-Roadmap-with-Mohammed-Adam-29-2048.jpg)