Download as PDF, PPTX






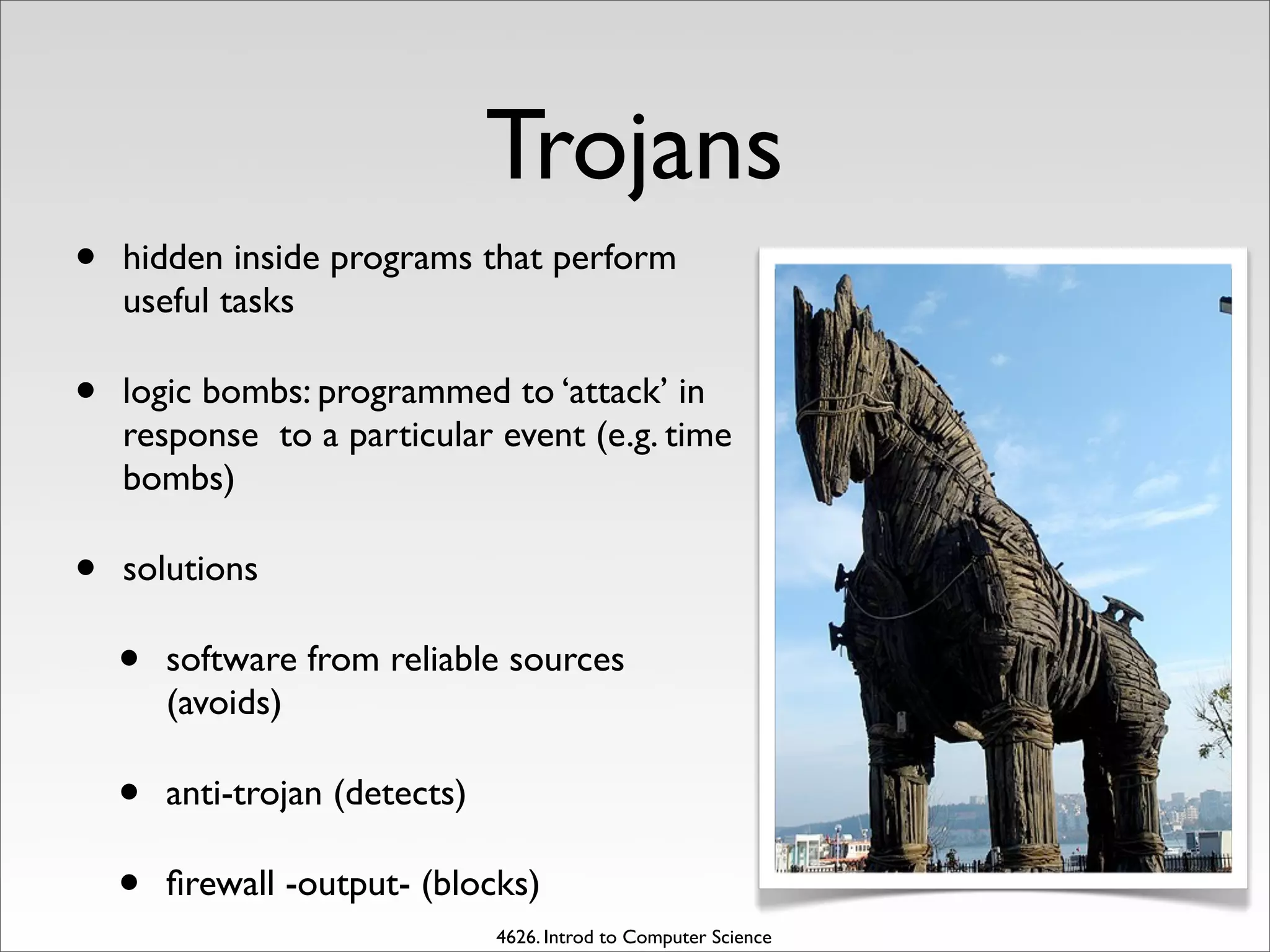

















This document discusses several types of computer security risks and methods to reduce risks. It describes common computer crimes like software piracy, hacking, and computer sabotage using malware. It also discusses how these risks affect personal privacy and intellectual property. Finally, it provides recommendations for protecting systems through physical access restrictions, passwords, firewalls, encryption, backups, and RAID technology to safeguard data integrity and availability.























