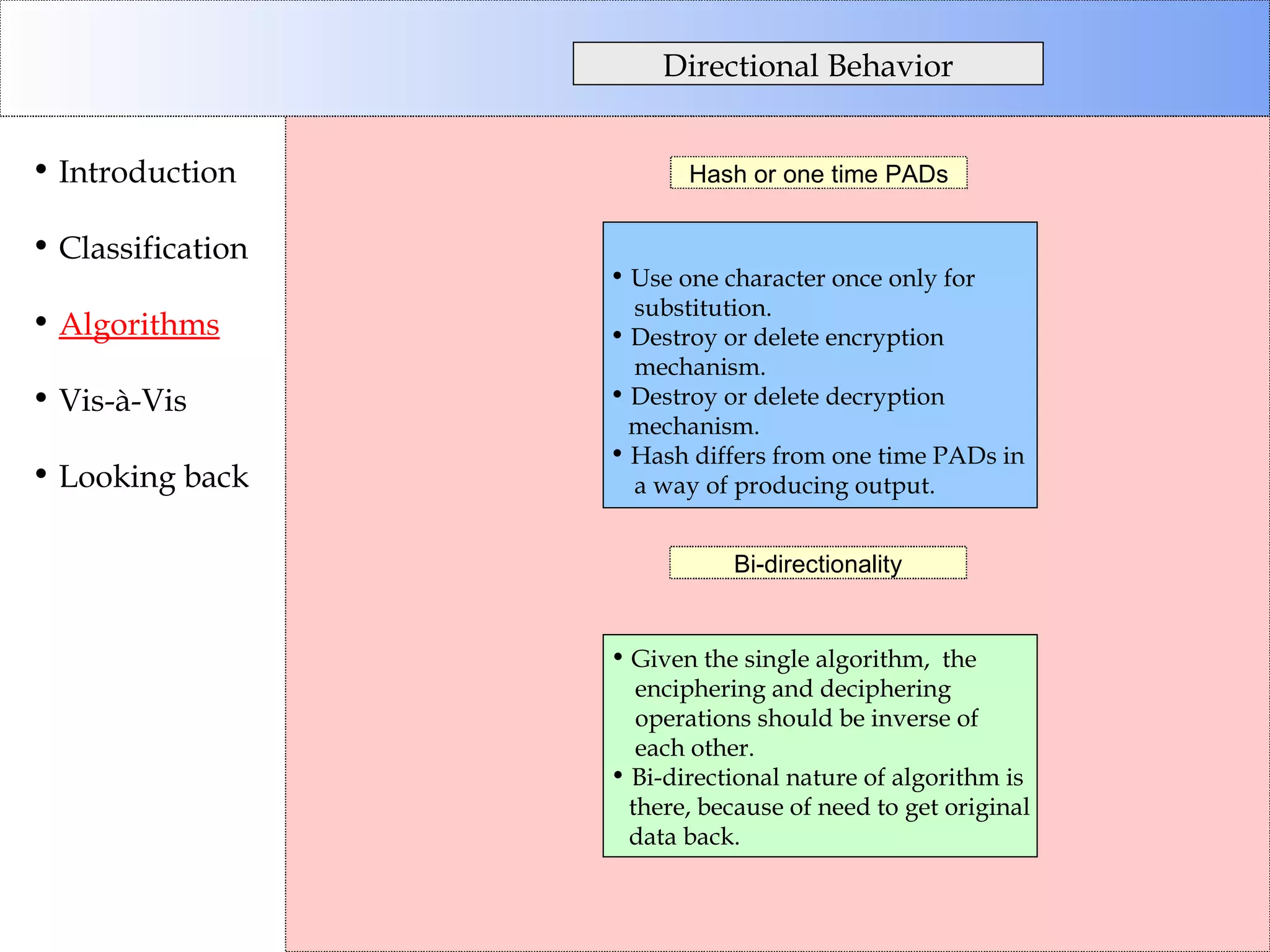
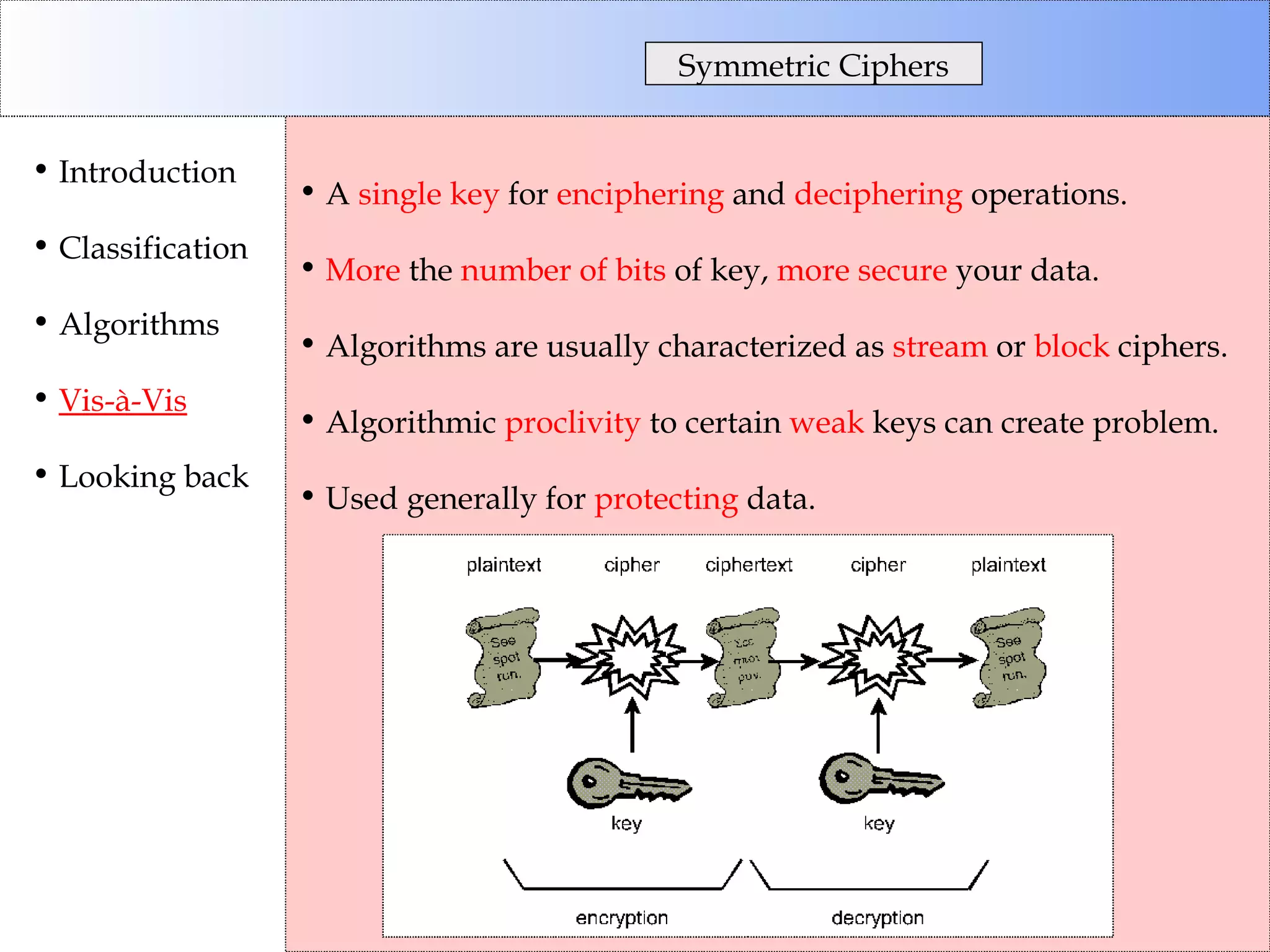
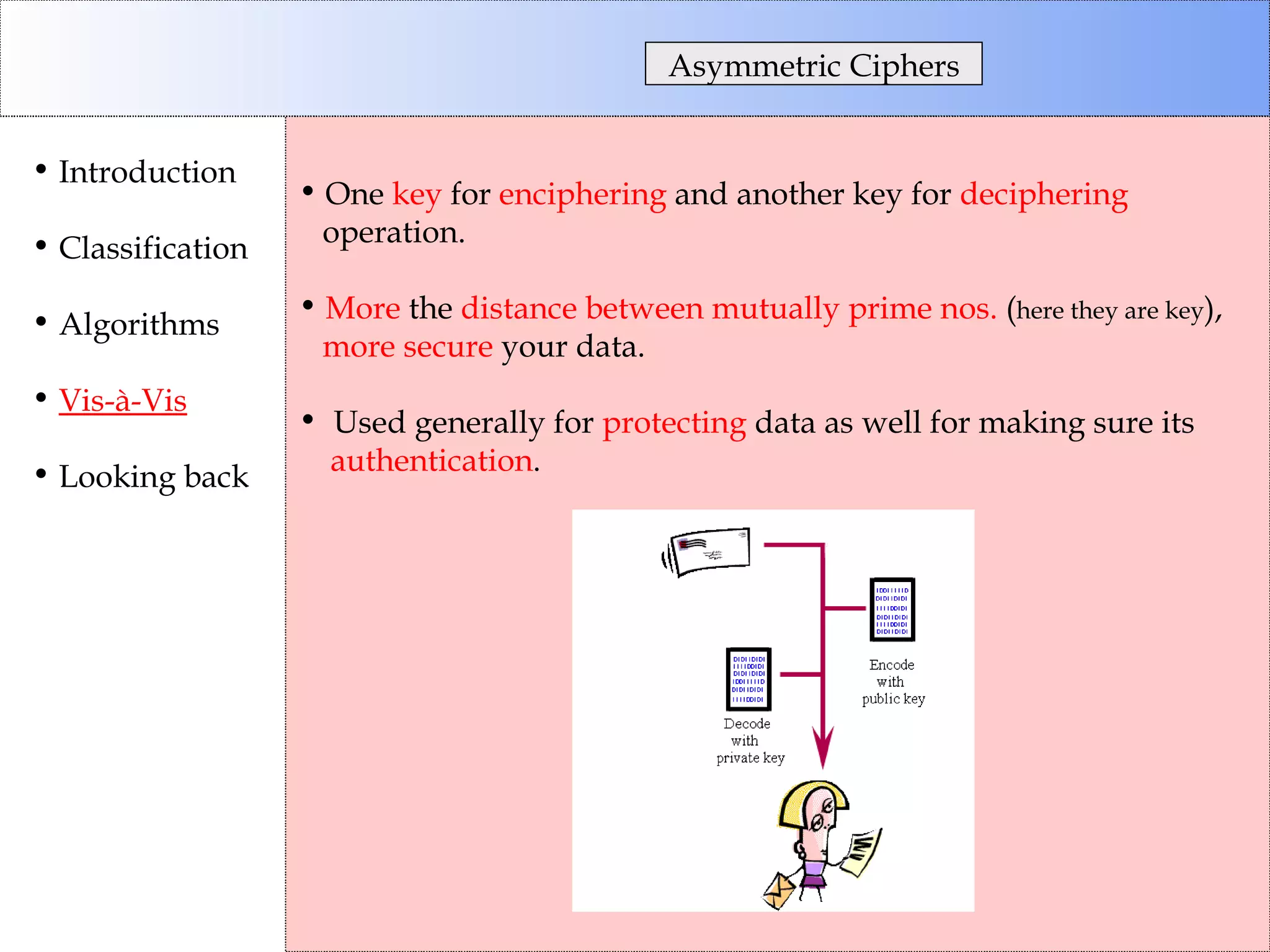
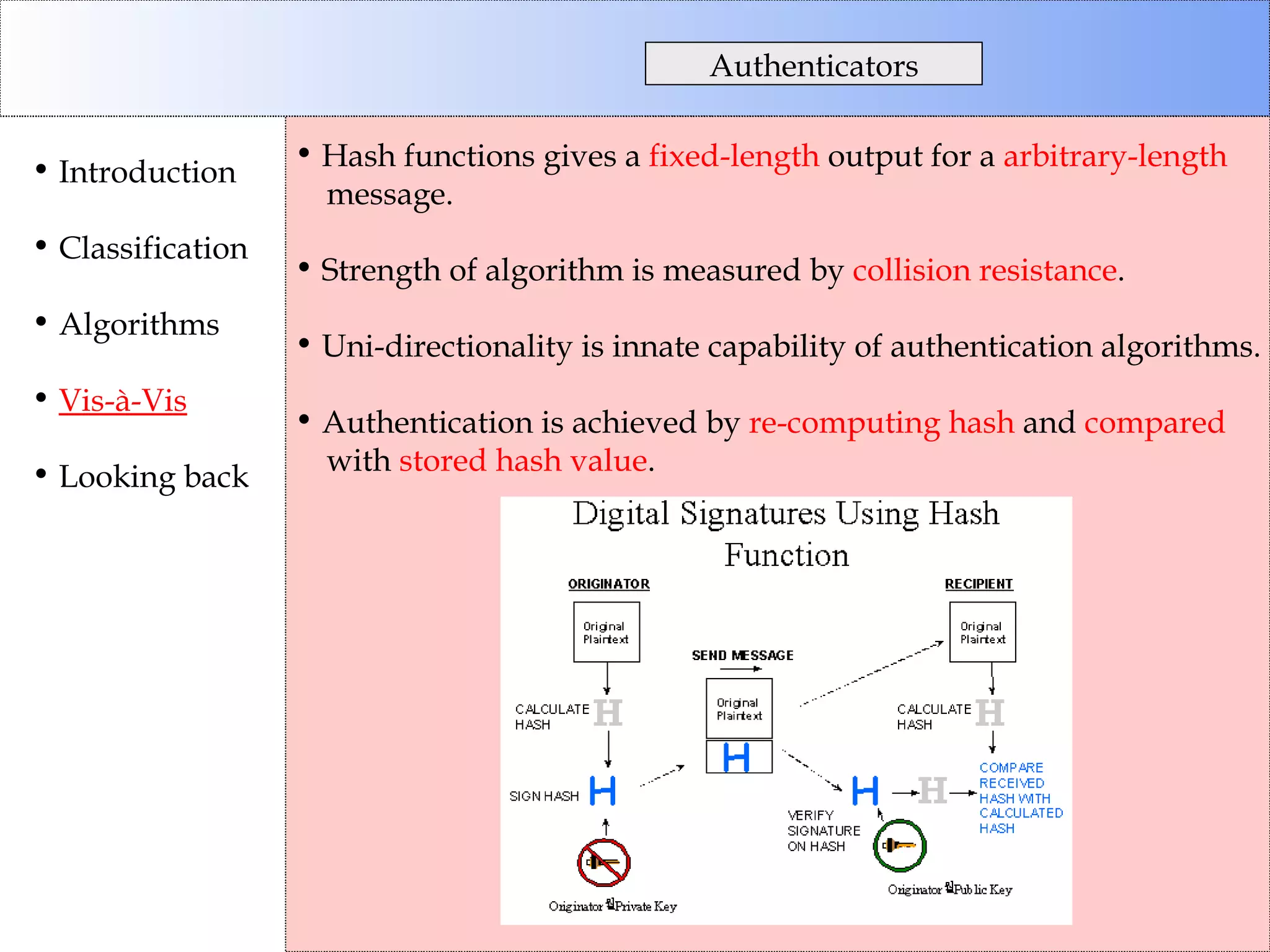
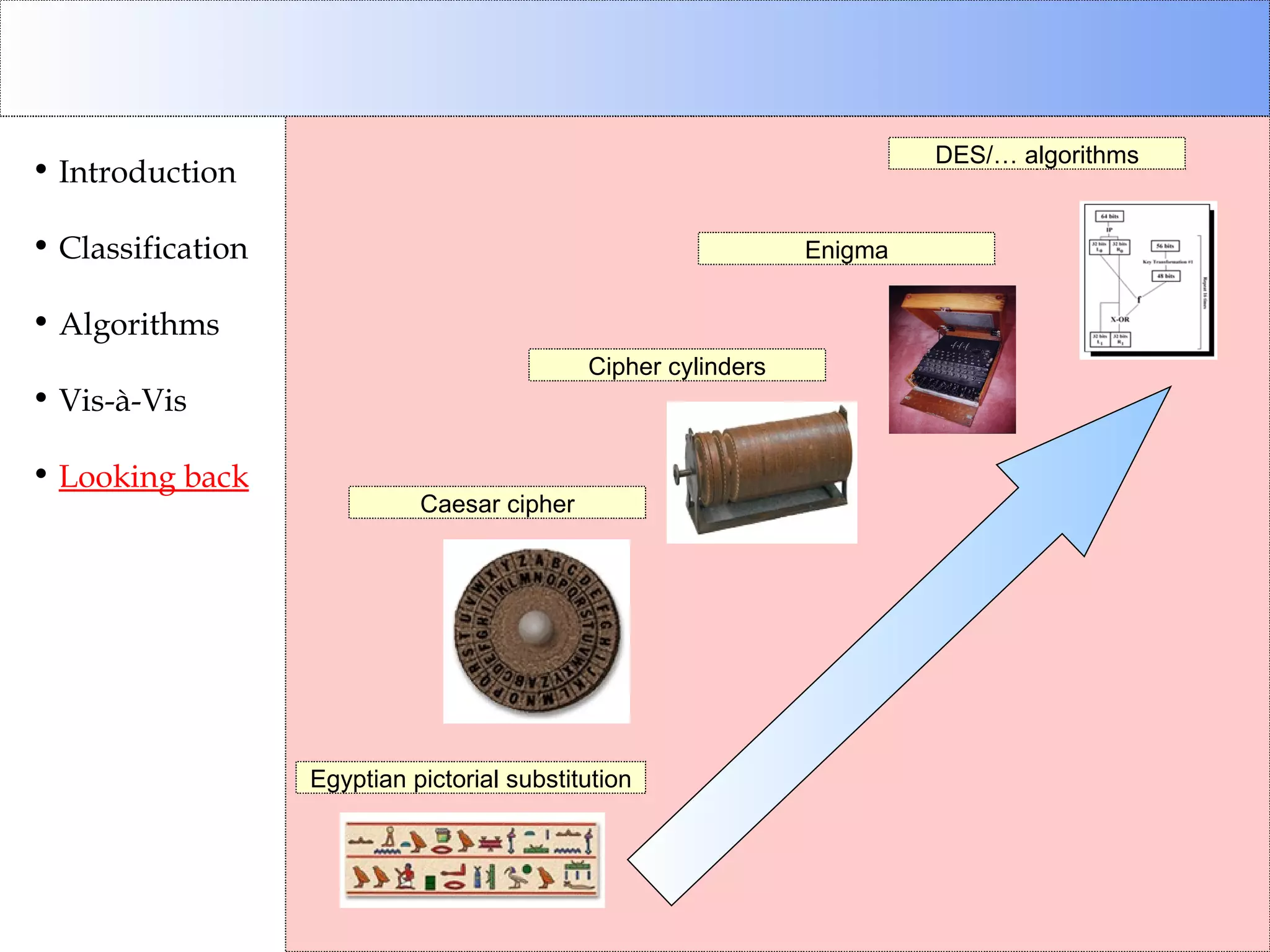
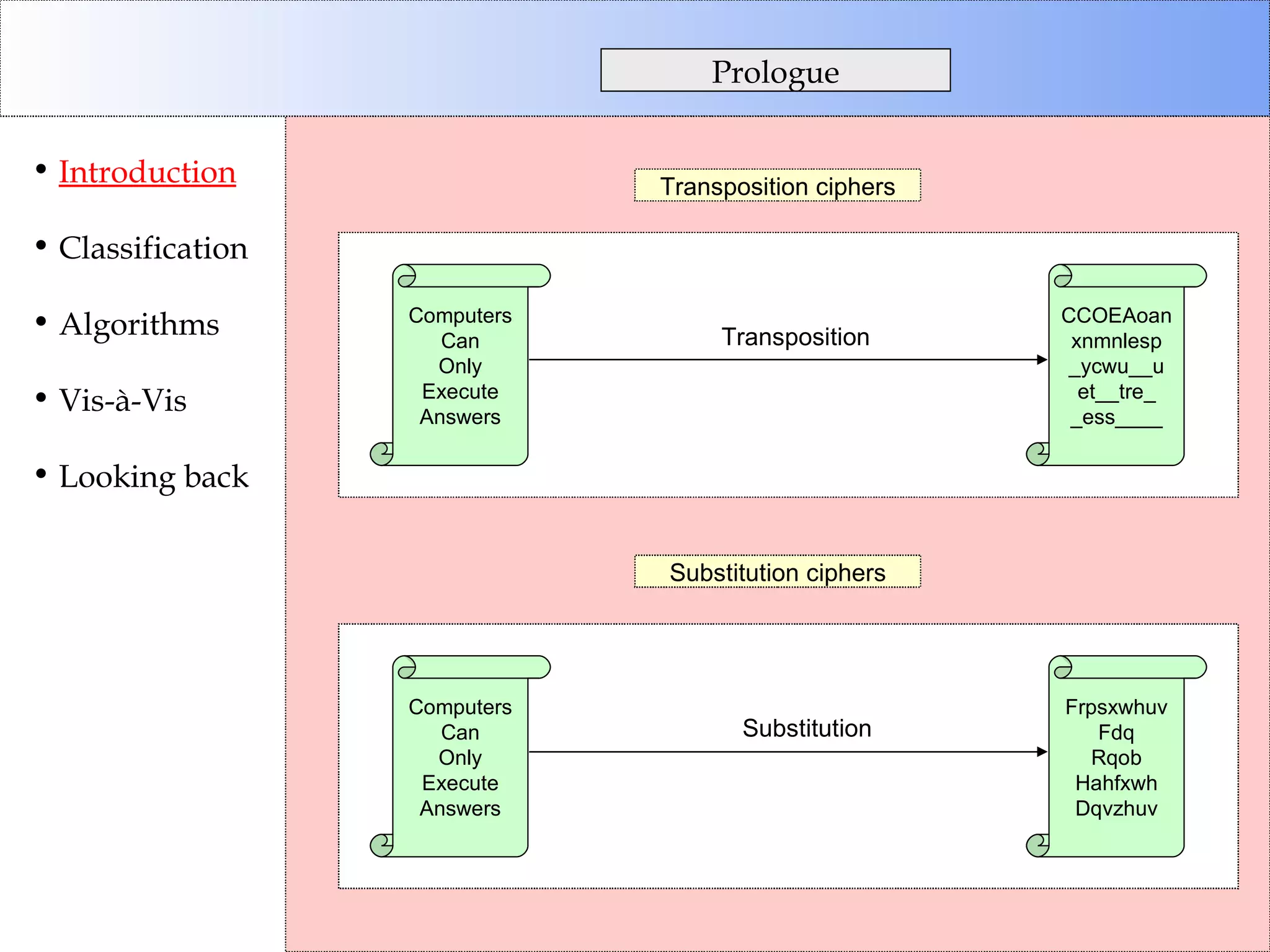
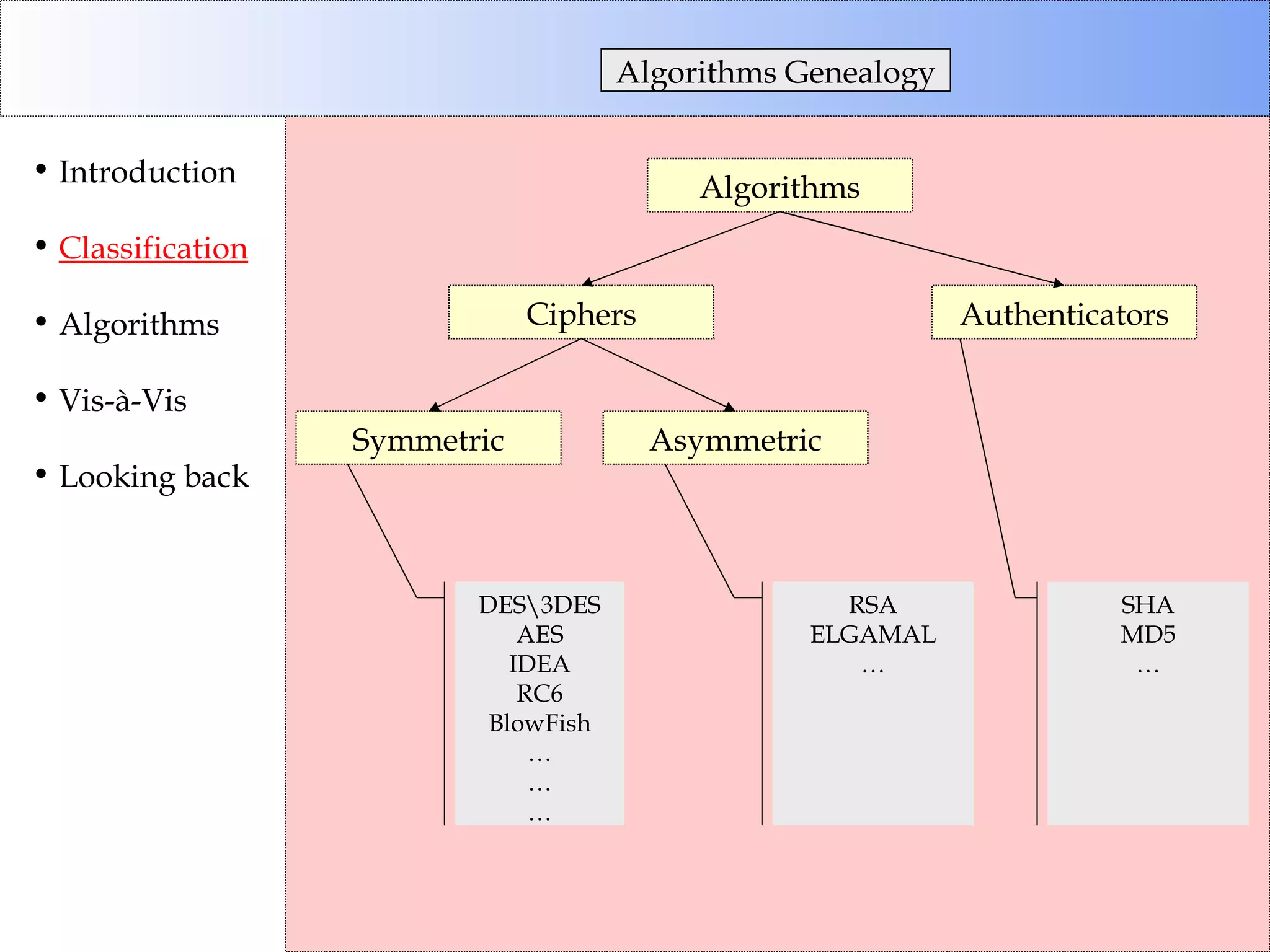
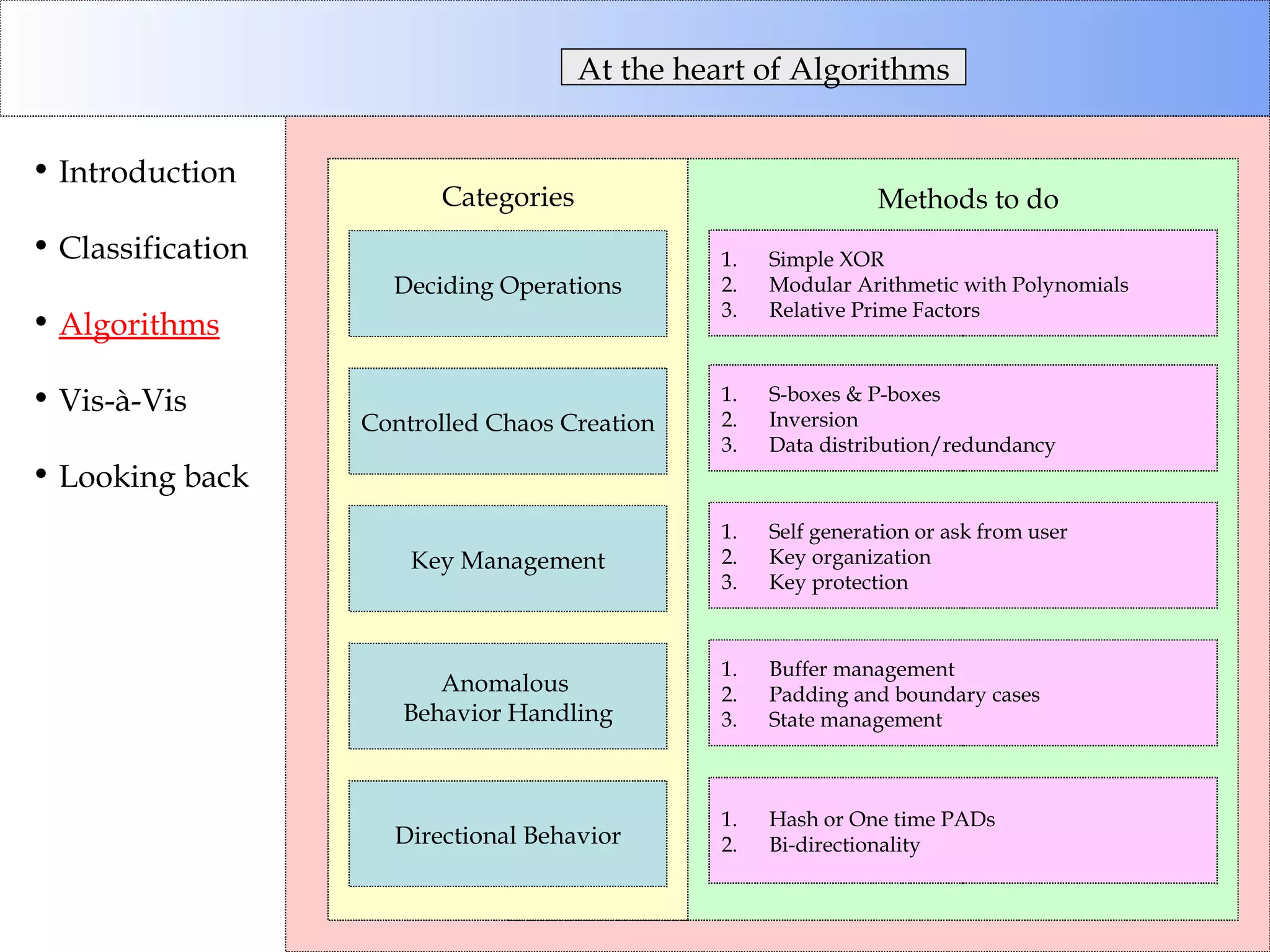
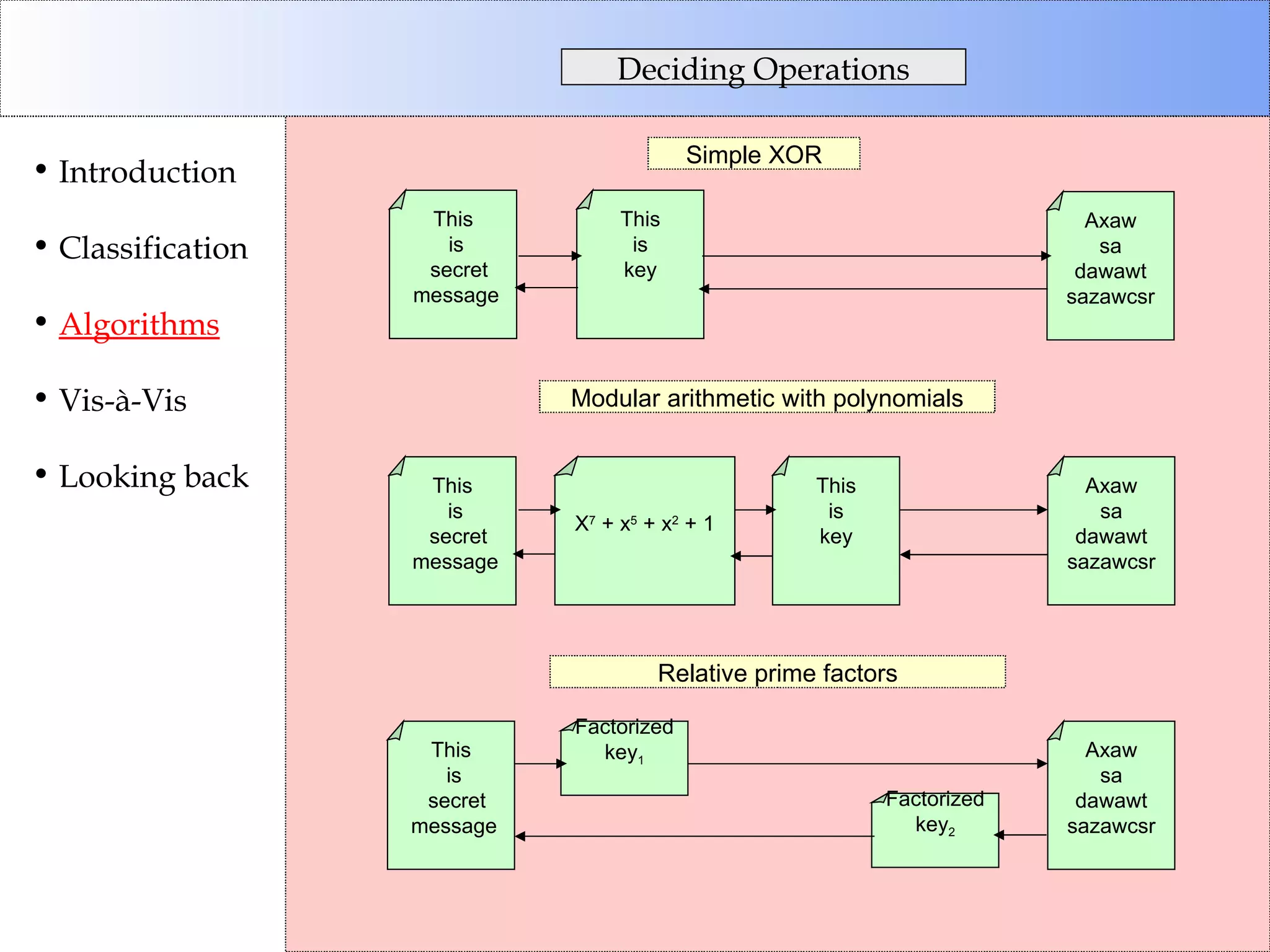
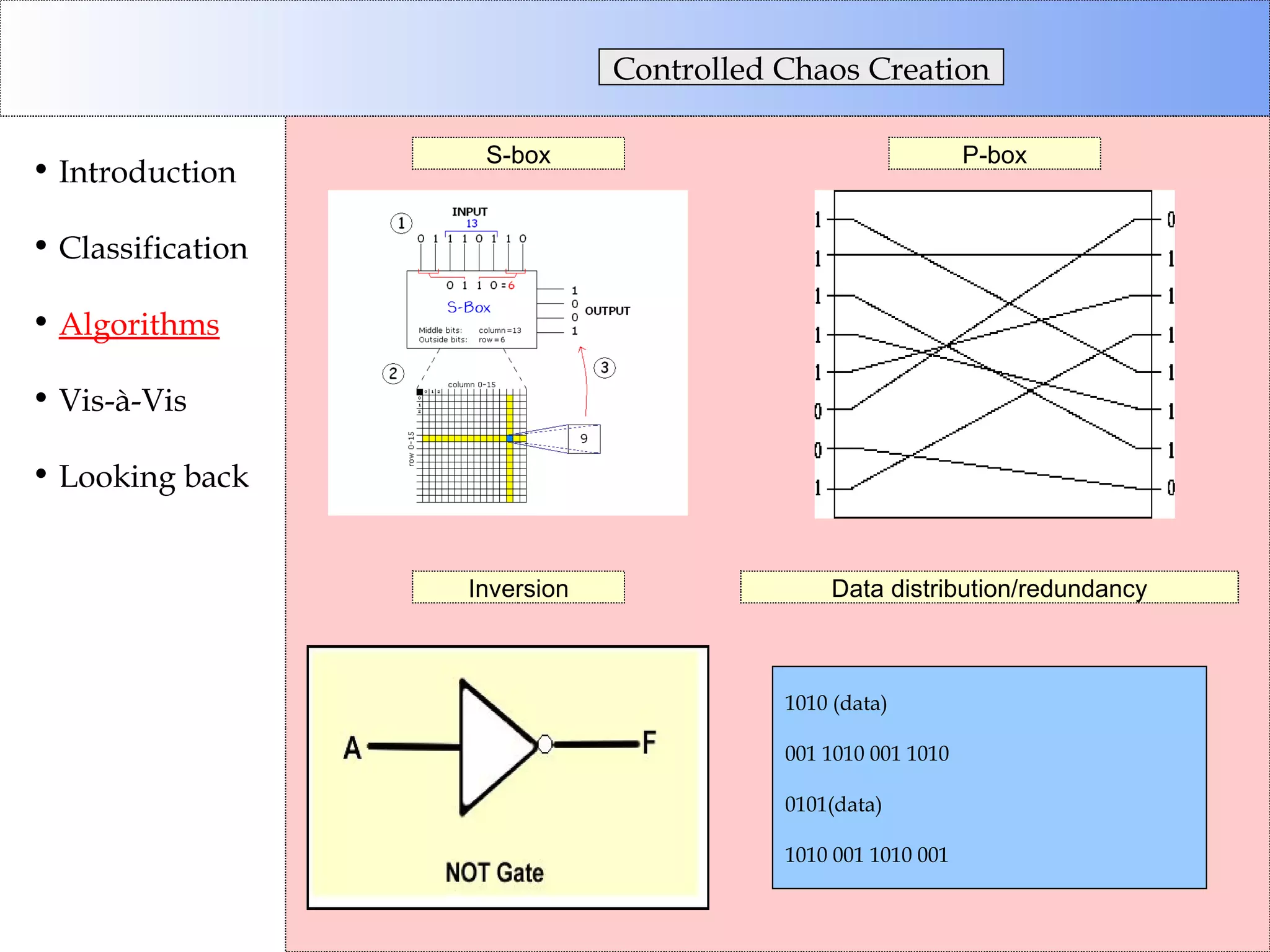
This document discusses cryptographic algorithms and their classification. It introduces different types of ciphers like transposition ciphers, substitution ciphers, symmetric ciphers, asymmetric ciphers, and authenticators. It also explains concepts like keys, padding, buffer management, and directional behavior in algorithms. Examples of specific algorithms discussed include DES, AES, RSA, Elgamal, SHA, and MD5.

![Anomalous Behavior Handling Introduction Classification Algorithms Vis-à-Vis Looking back Buffer management Padding Boundary cases State management 1010 1000 0010 1100 [+] 1000 1001 = Overflow Capture of 1010 1000 0010 1100 as plain-text from buffer on which algorithm operate If the input data or key are not exactly fulfilling the algorithm requirements, lets say required input is of multiple of 2 and > 512 bit, but user does not provide … ! U/SIGN-INT * U/SIGN-INT > 65536/32768 If the algorithm works in various stages, each stage signifying a state and regurgitating partially (weak) cipher-text and hence making possible ‘interleaving’… !](https://image.slidesharecdn.com/cryptographicalgorithms-111003021522-phpapp01/75/Cryptographicalgorithms-10-2048.jpg)