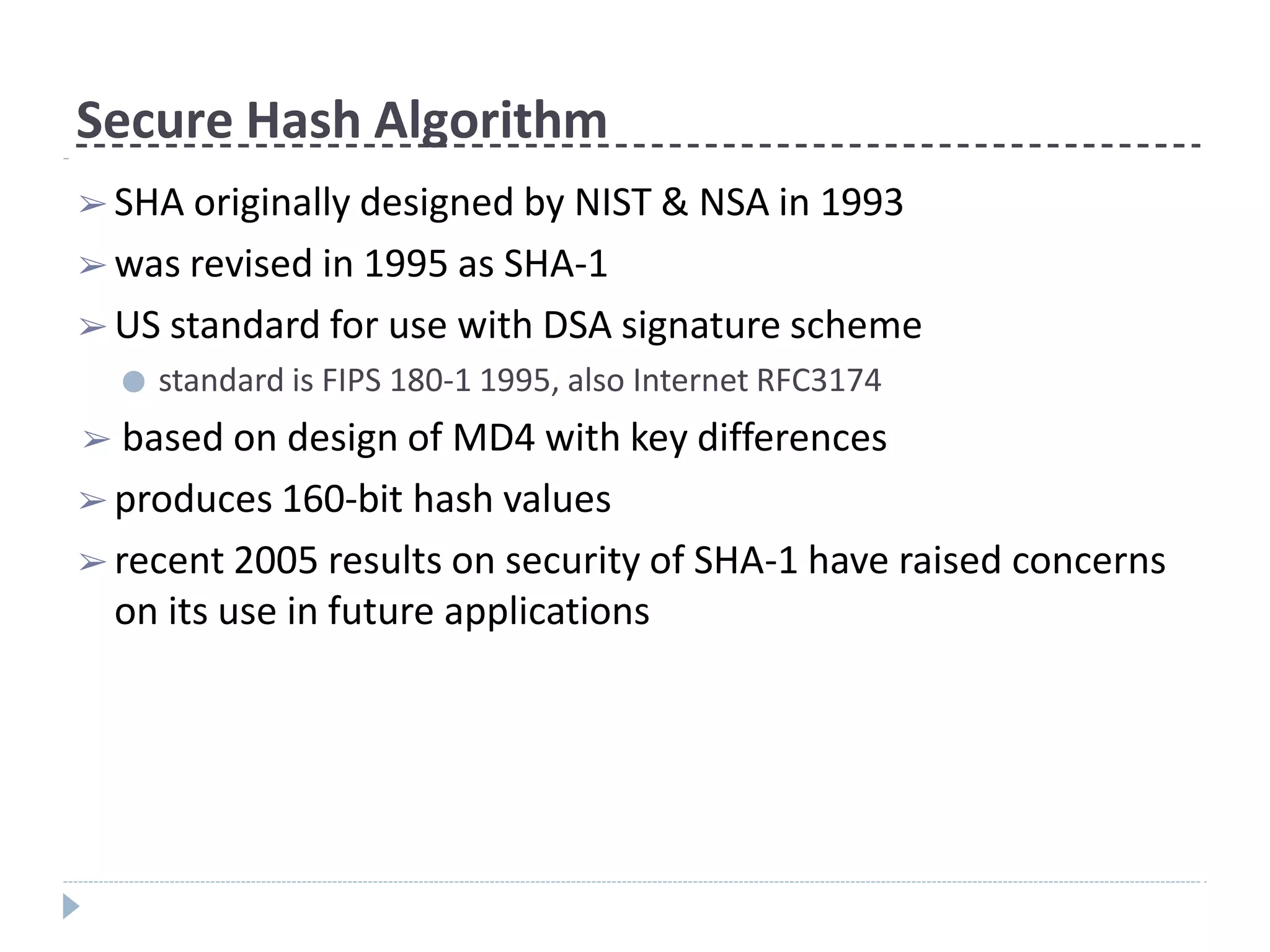
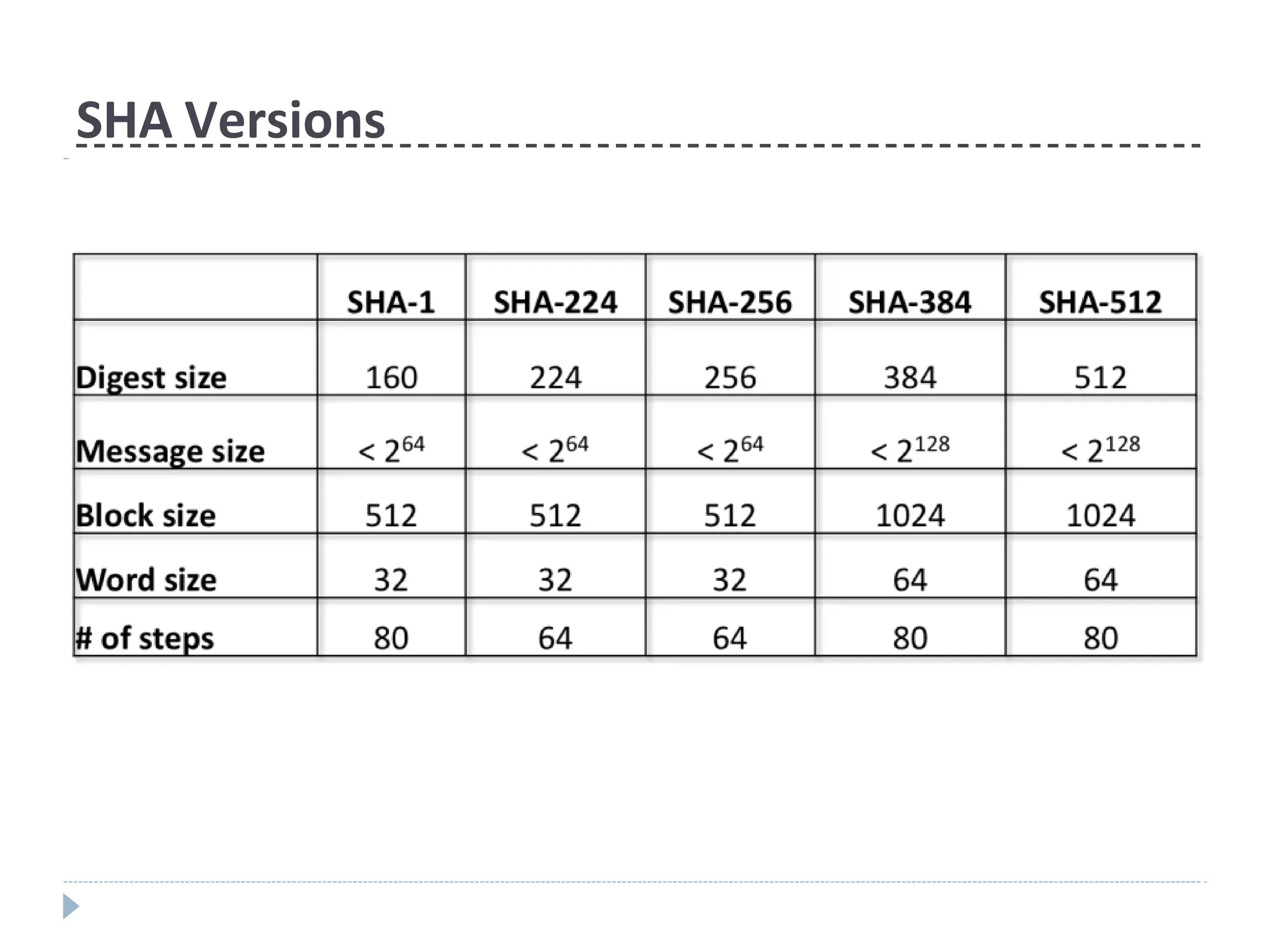
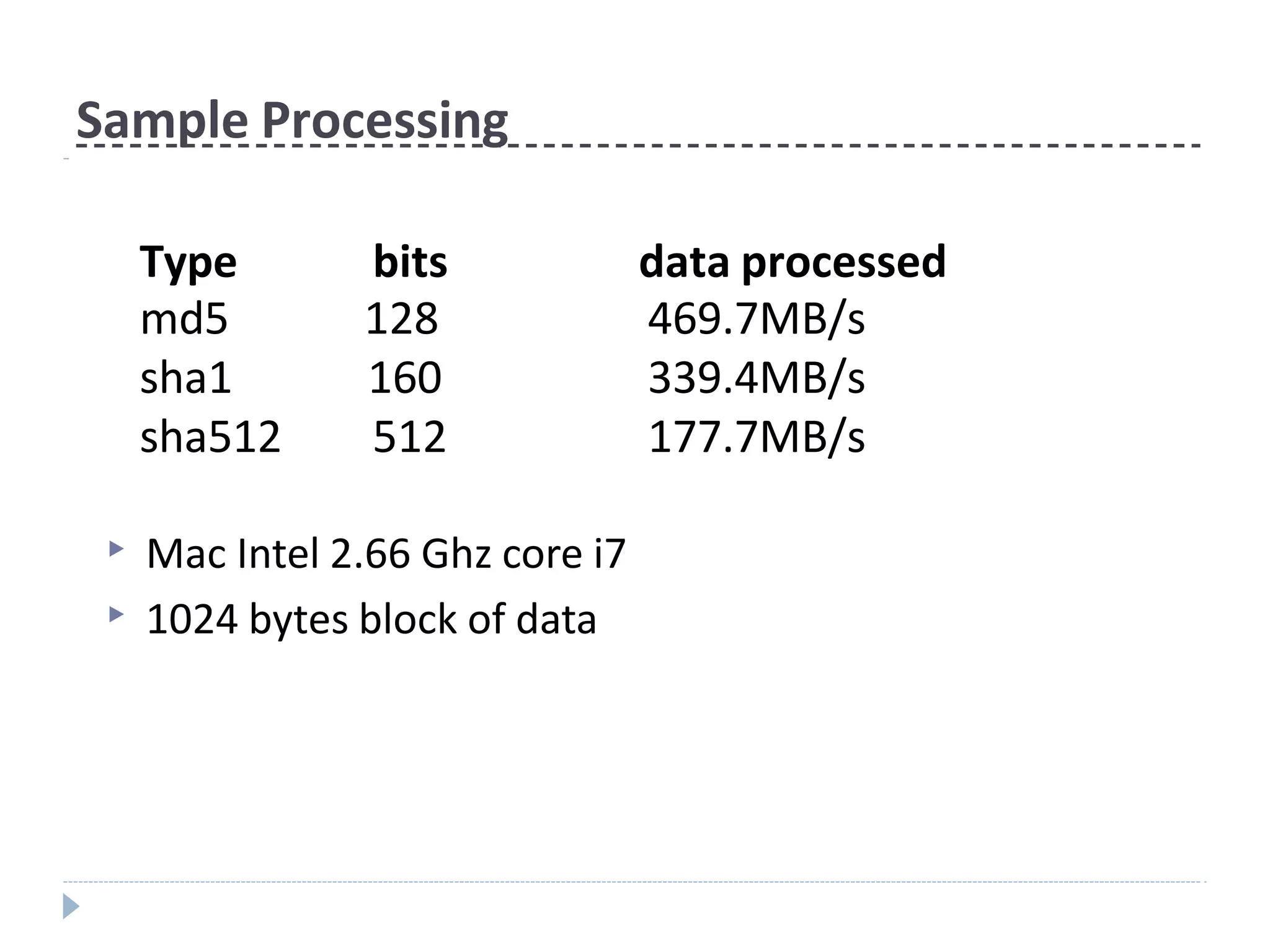
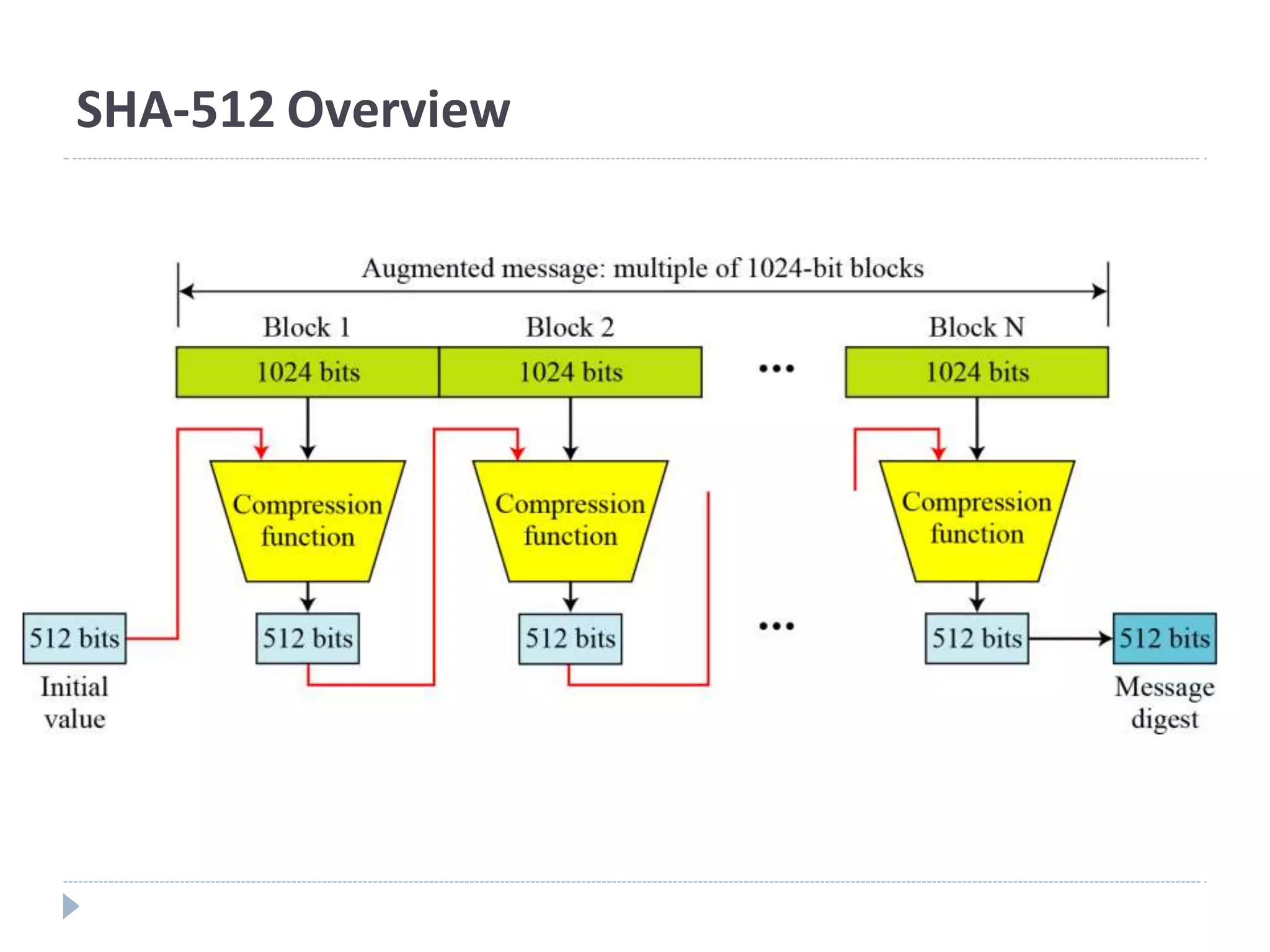
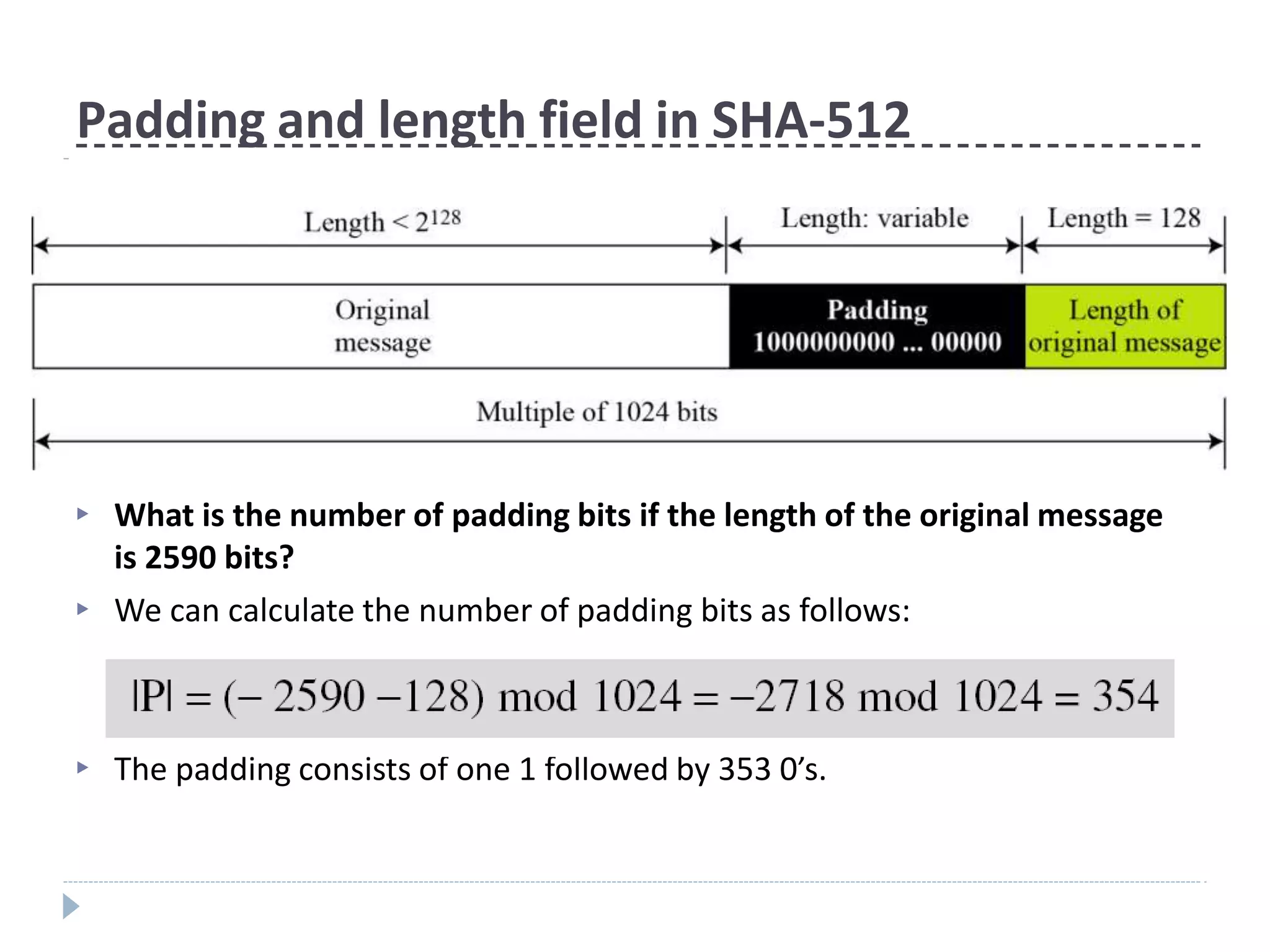
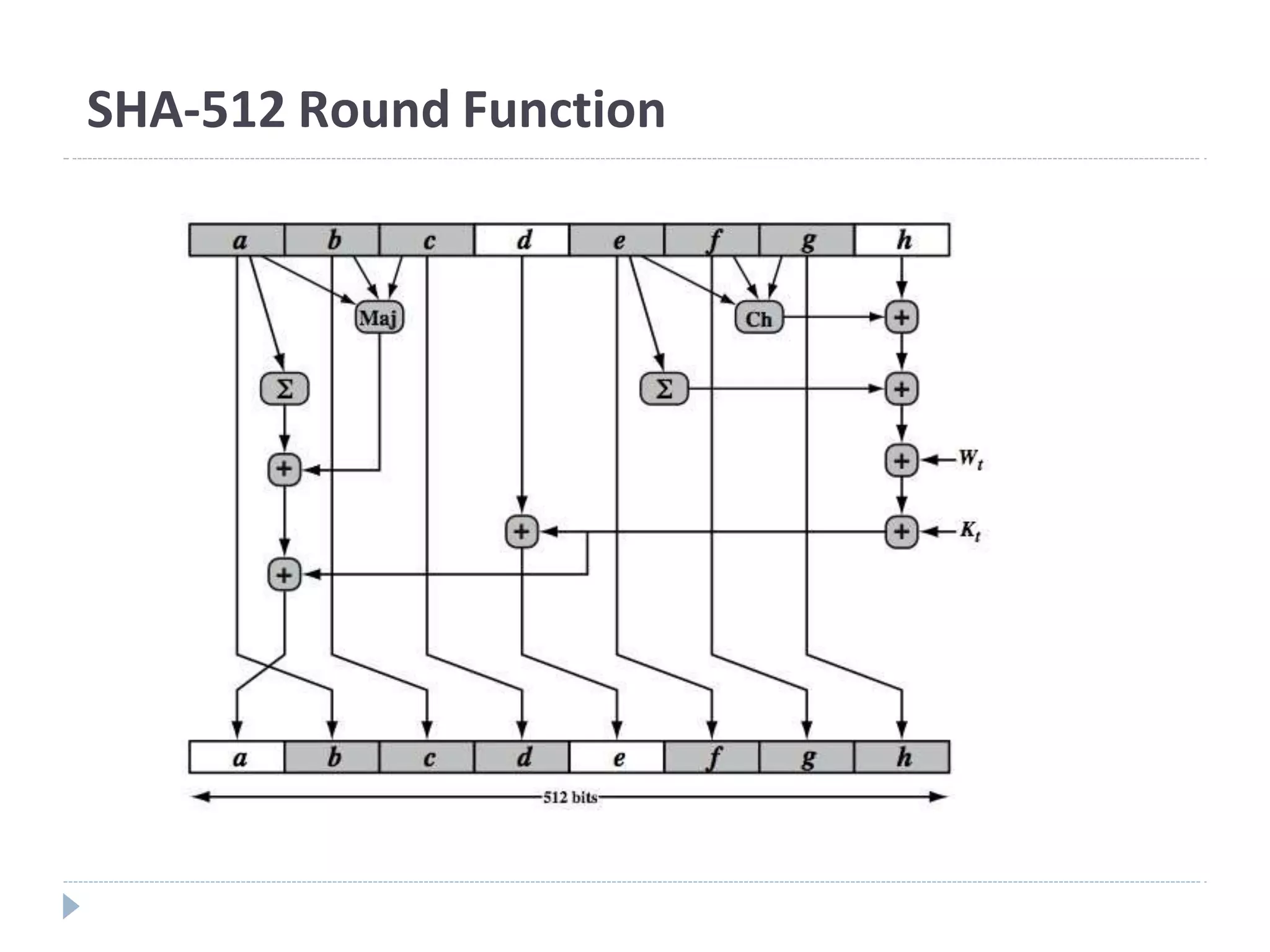
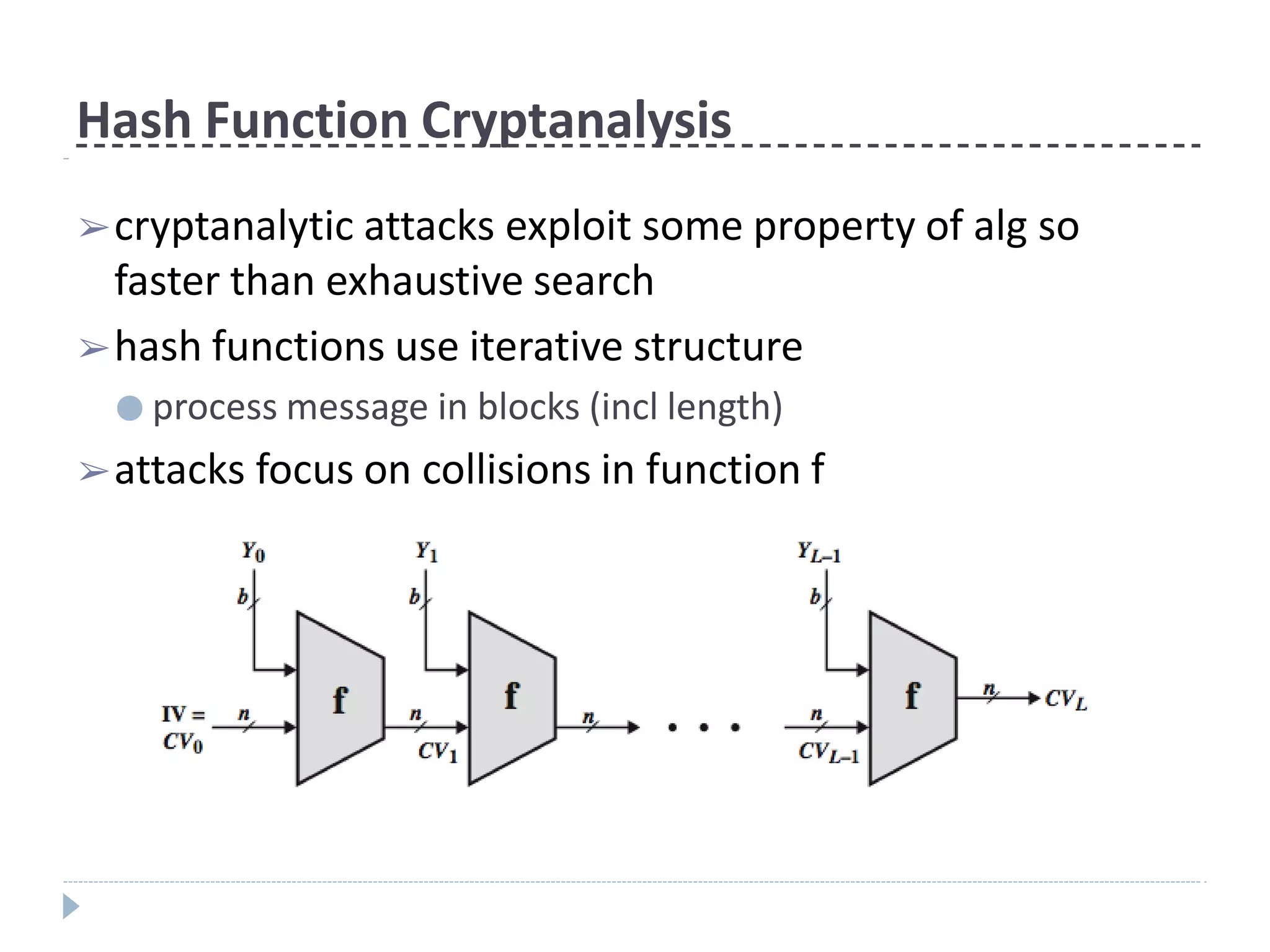
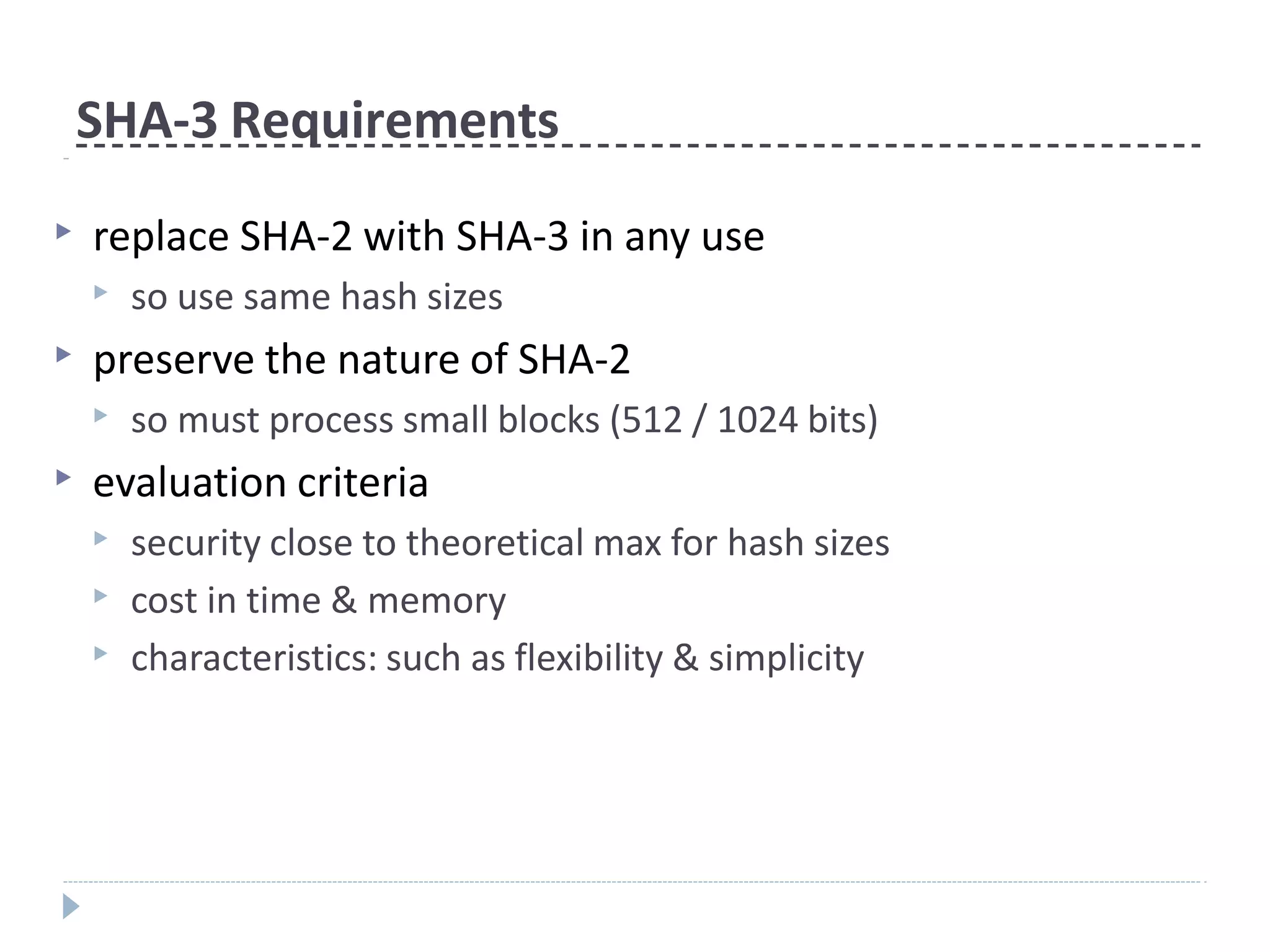
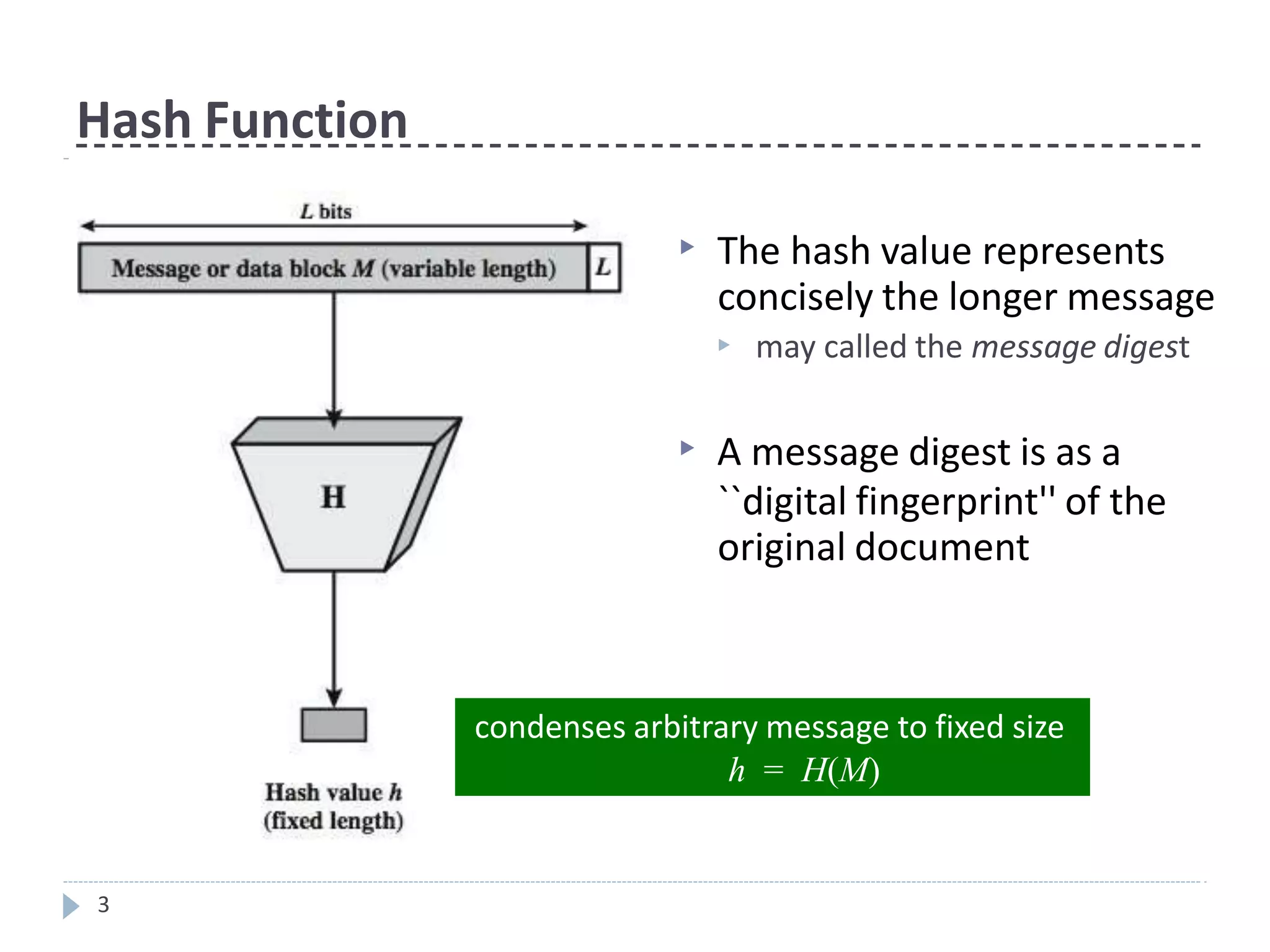
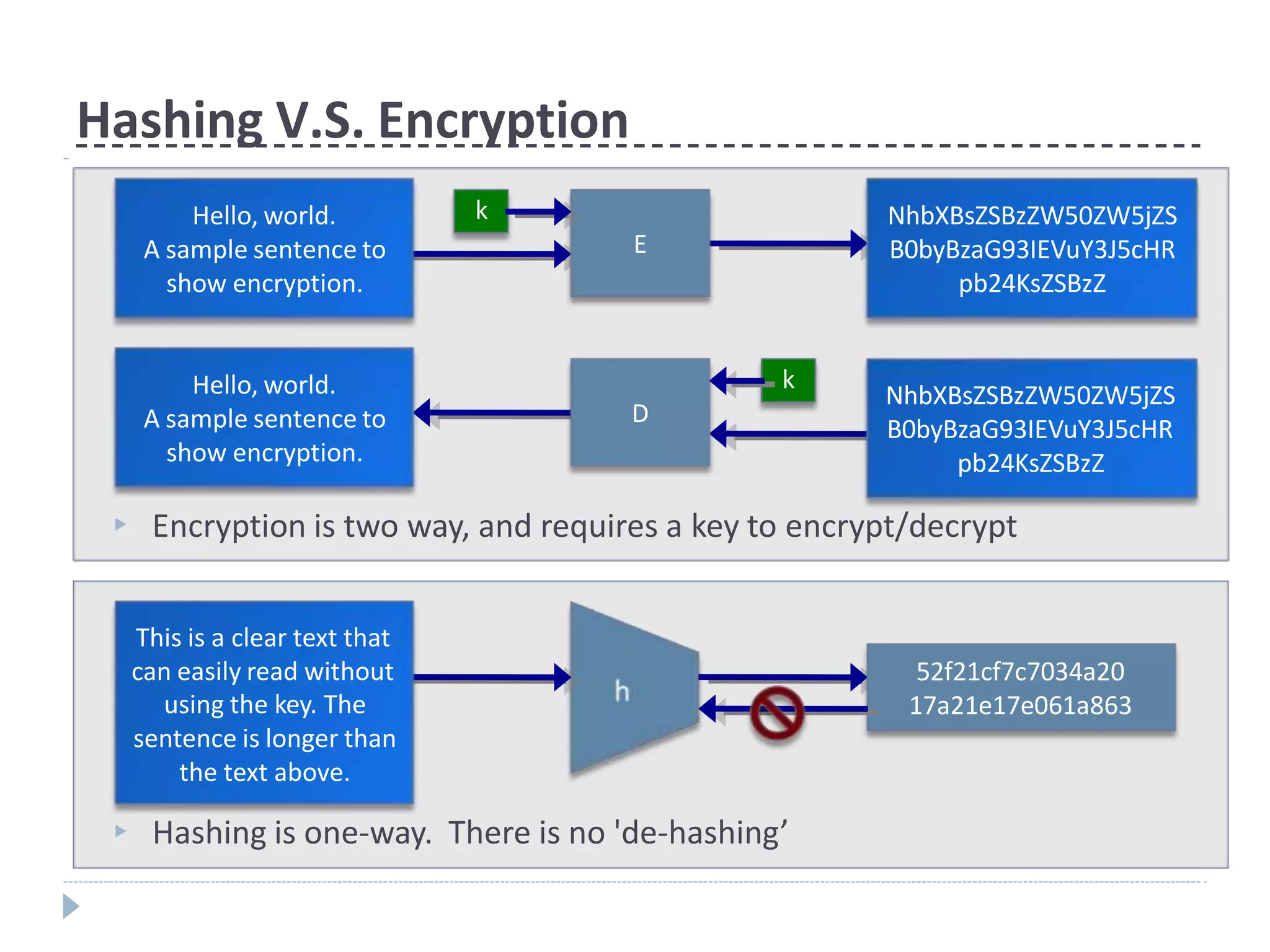
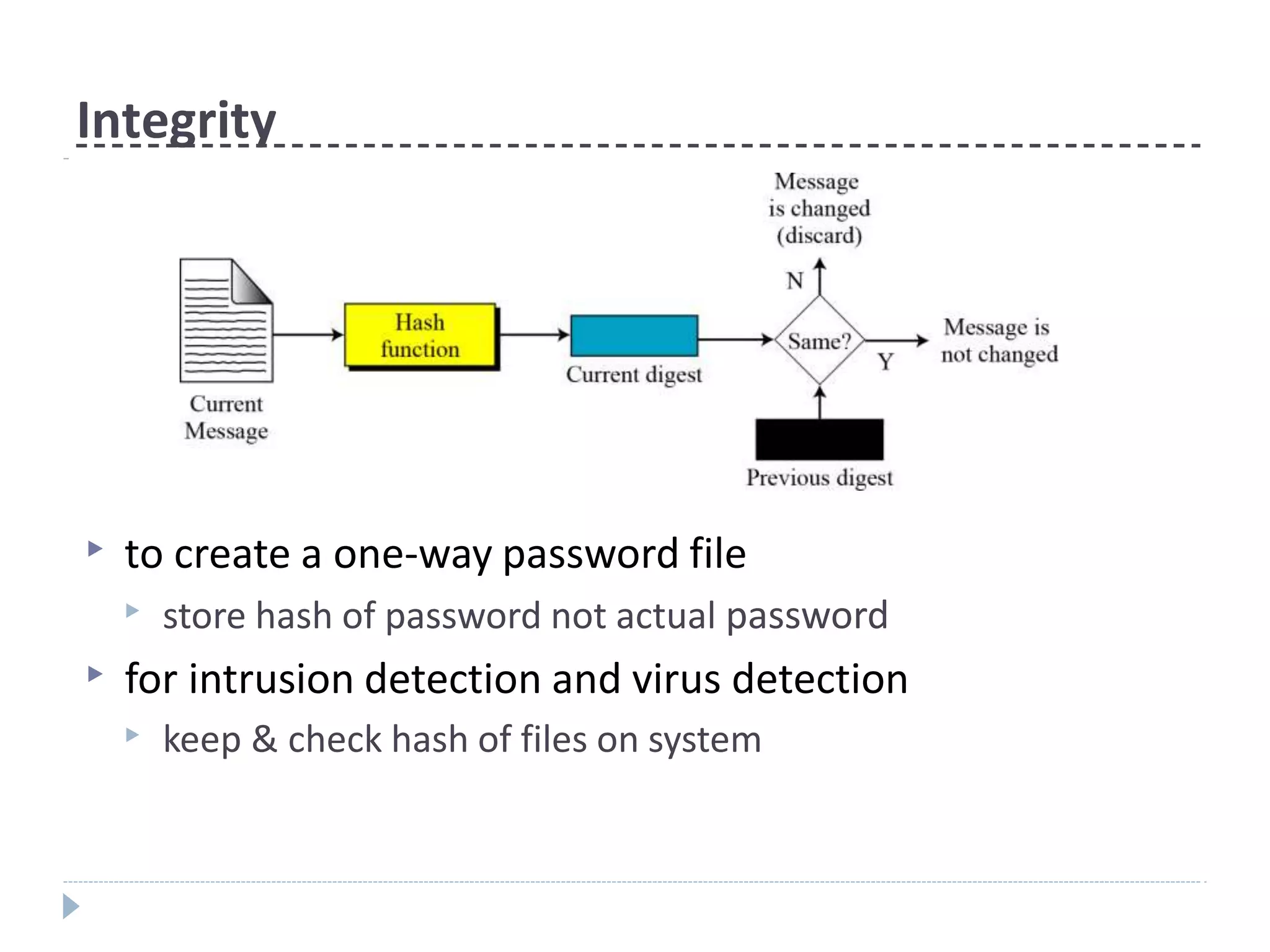
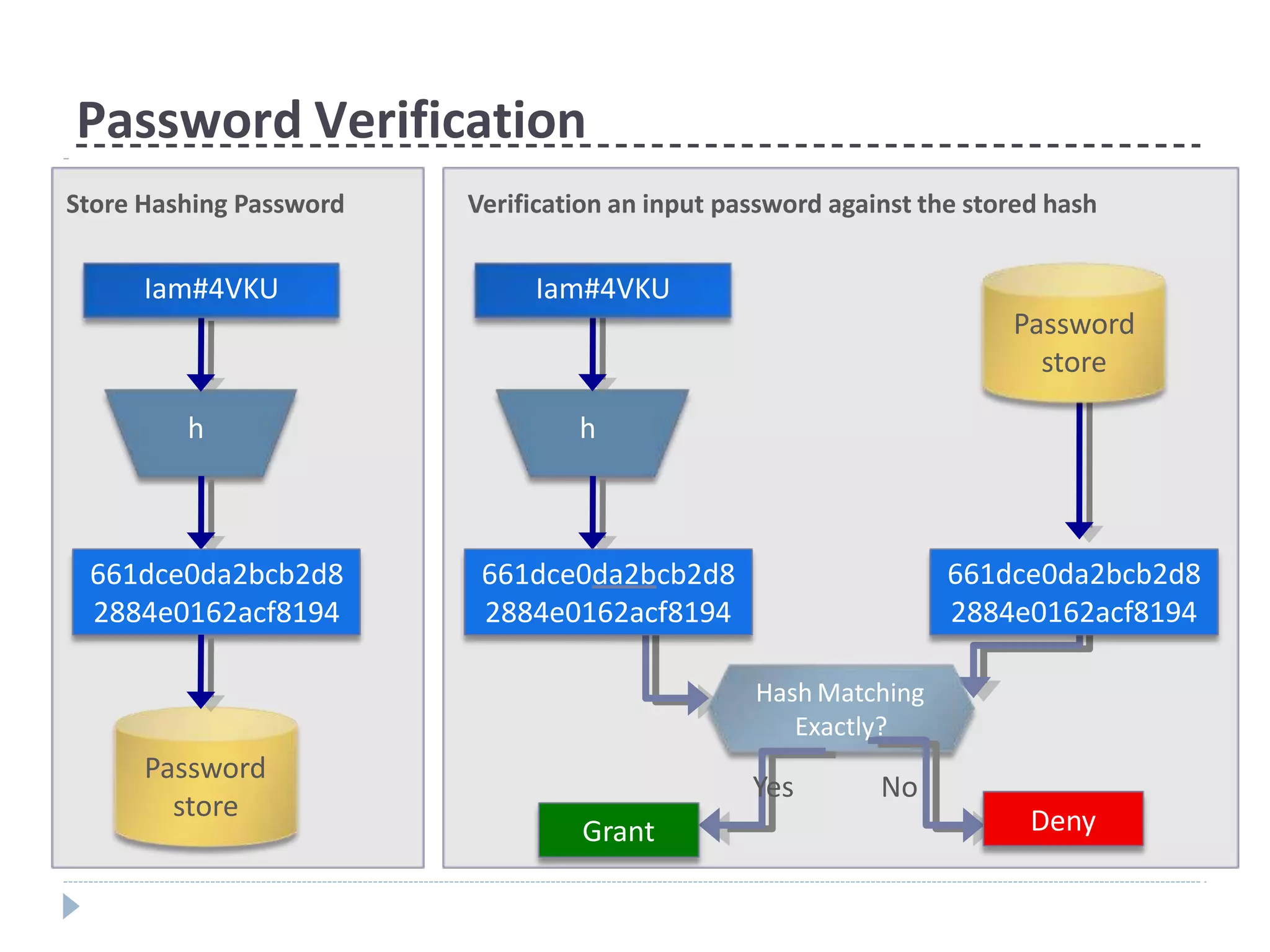
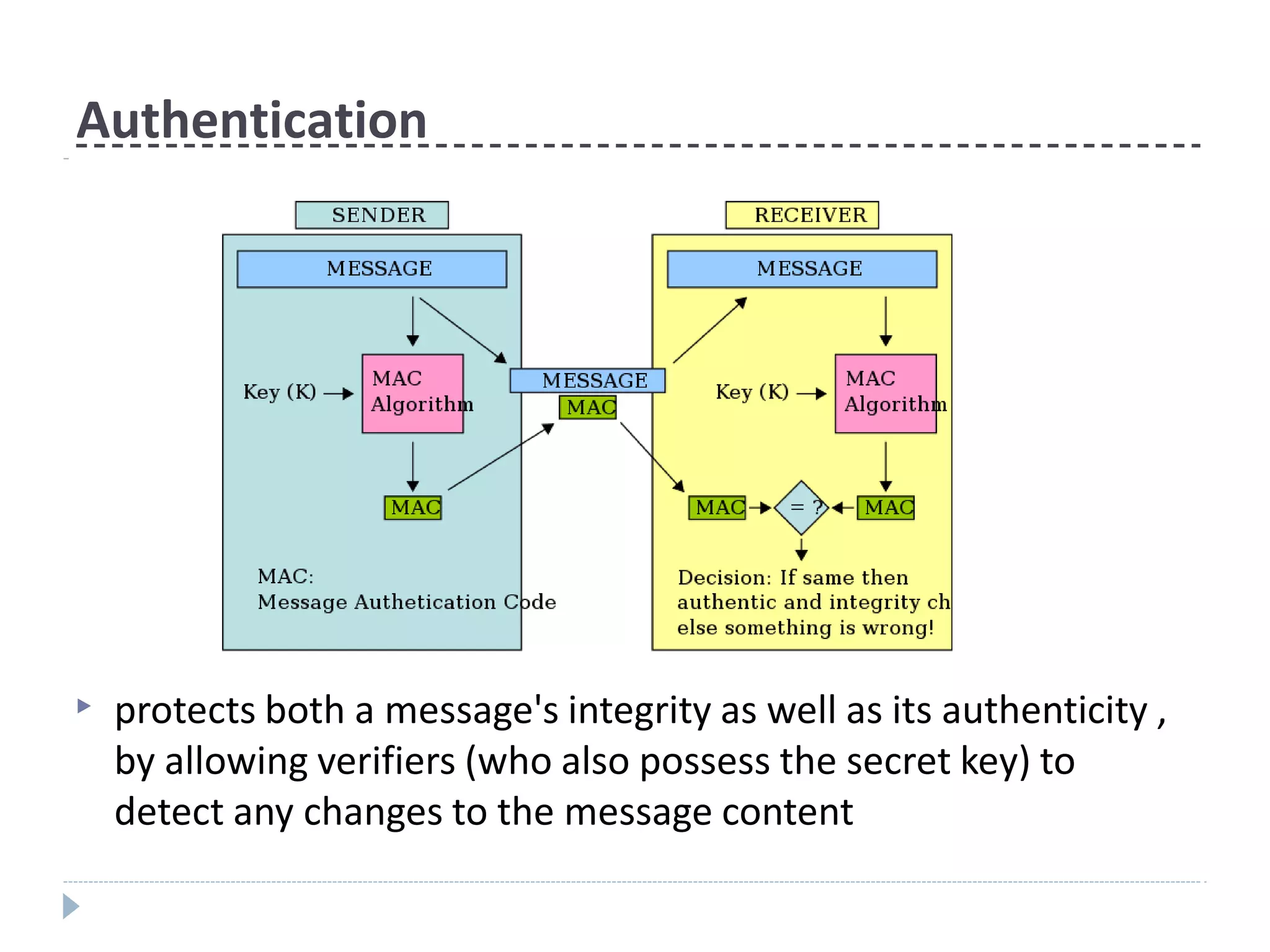
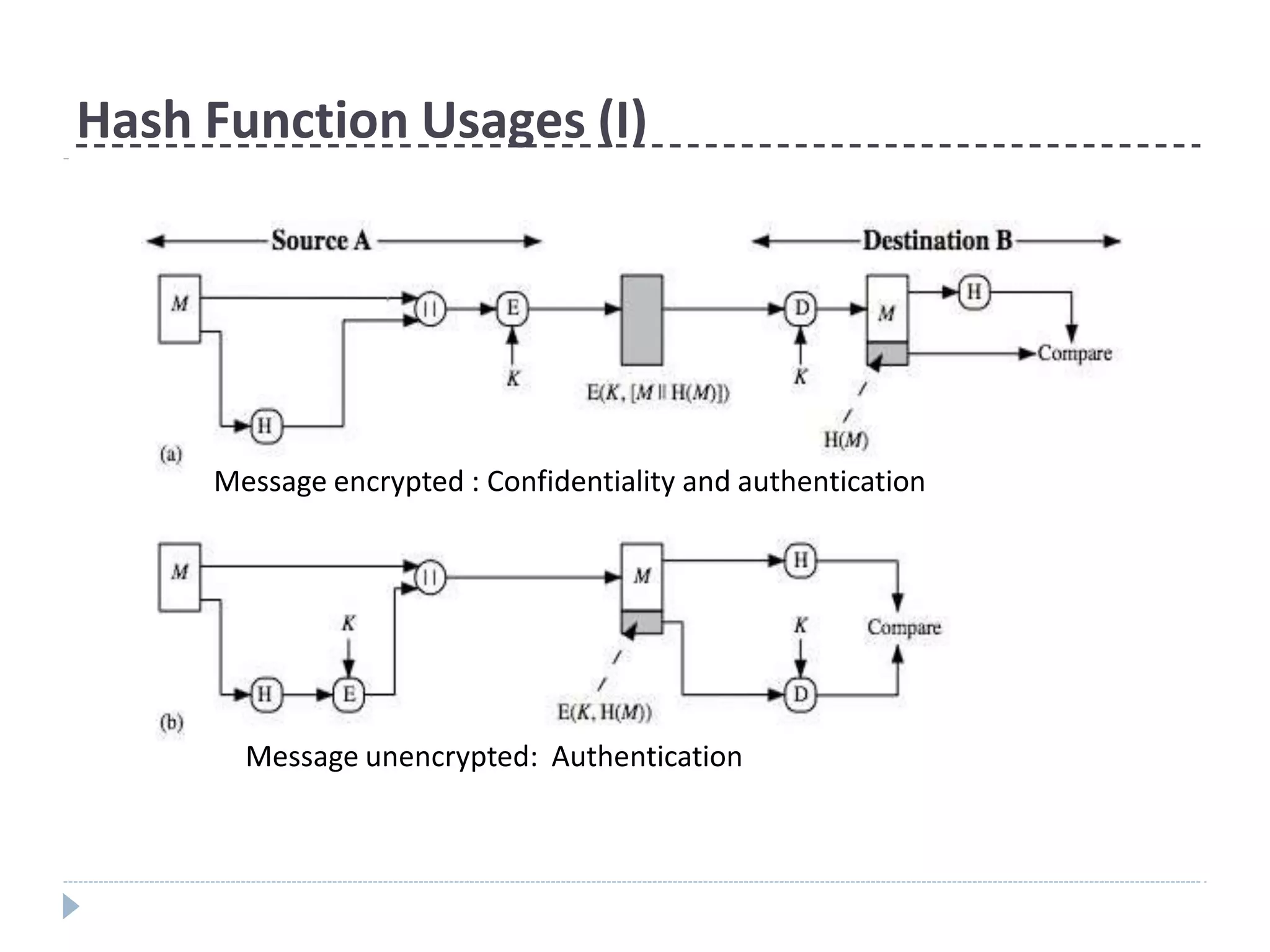
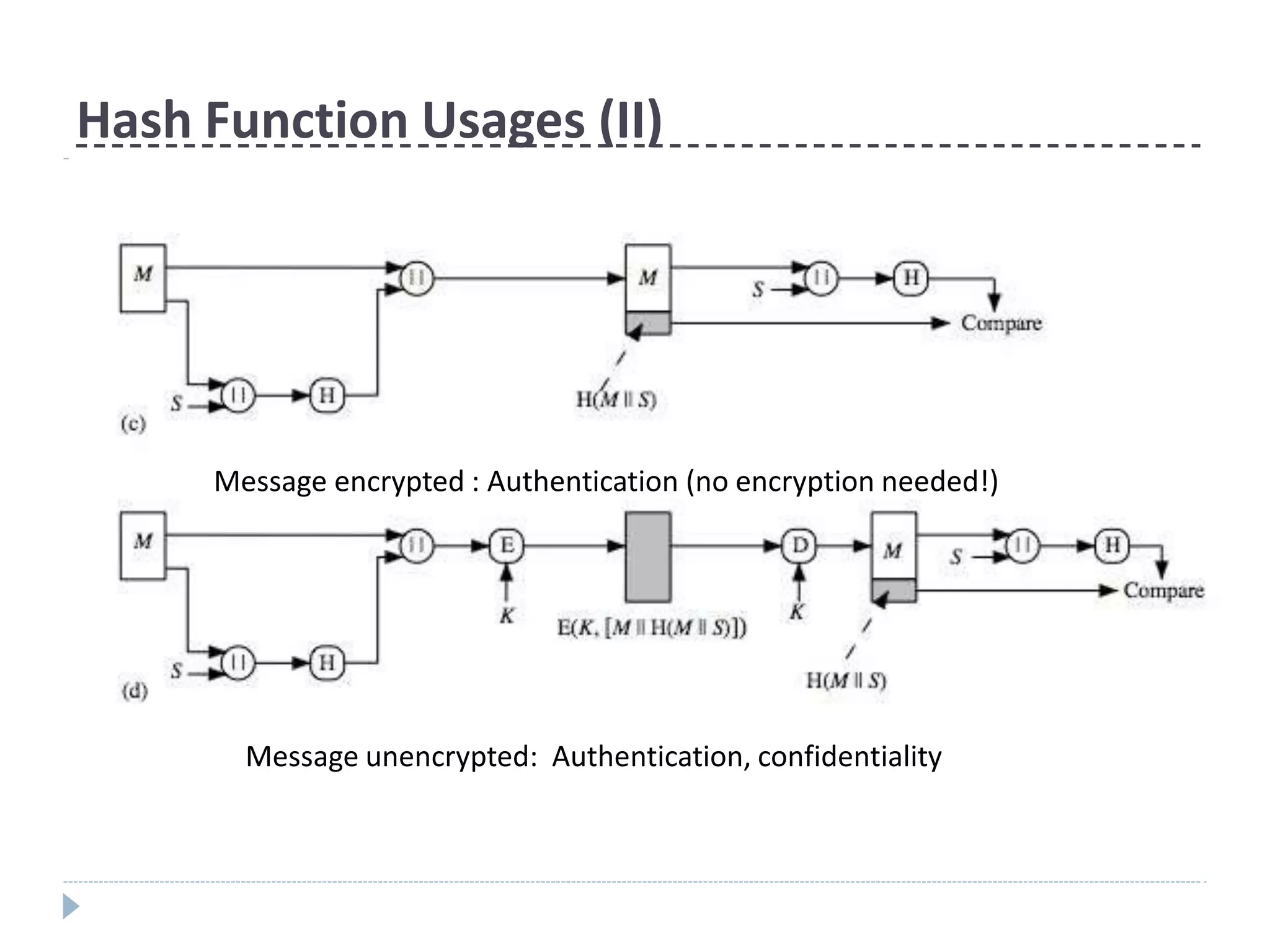
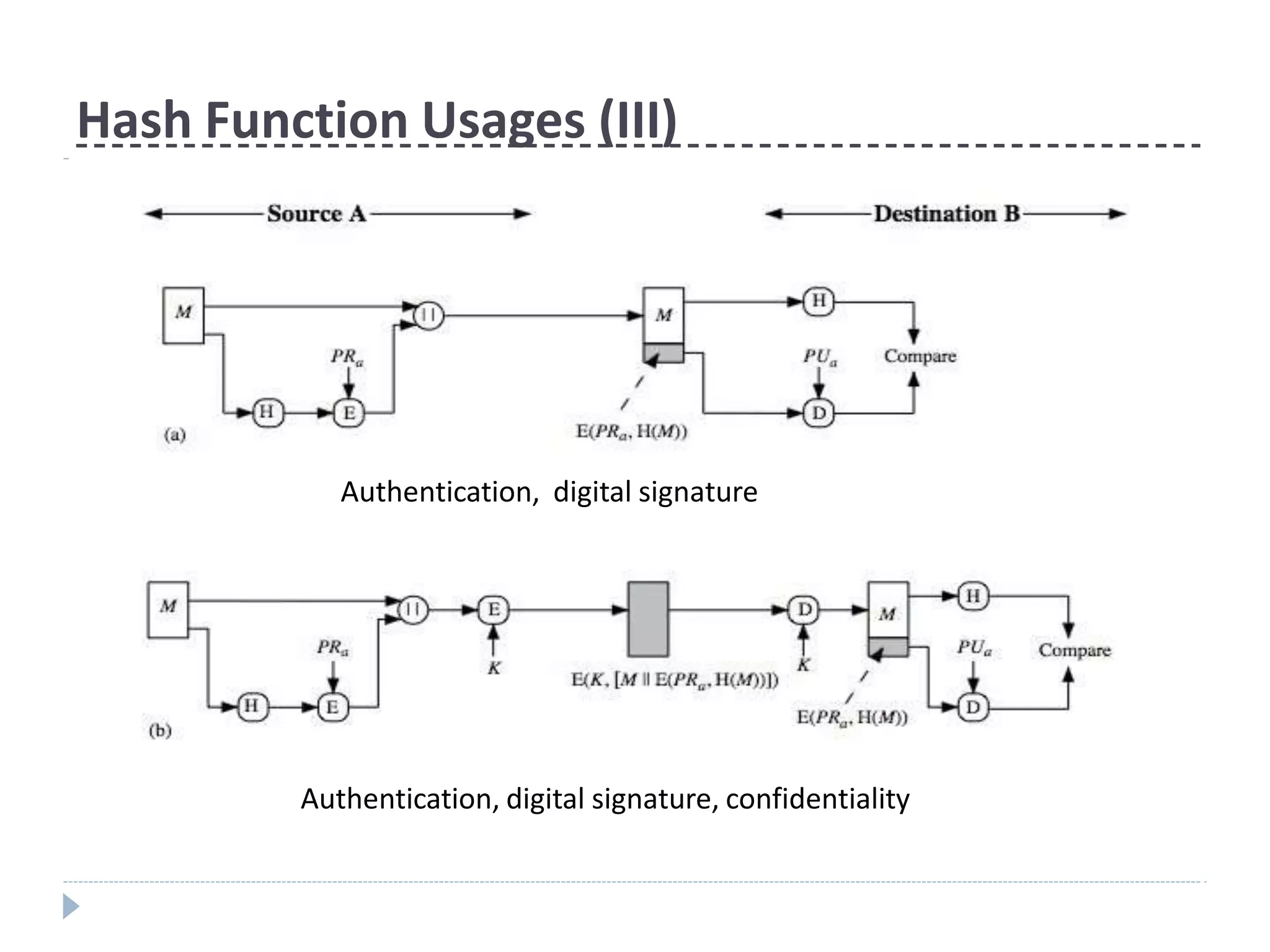
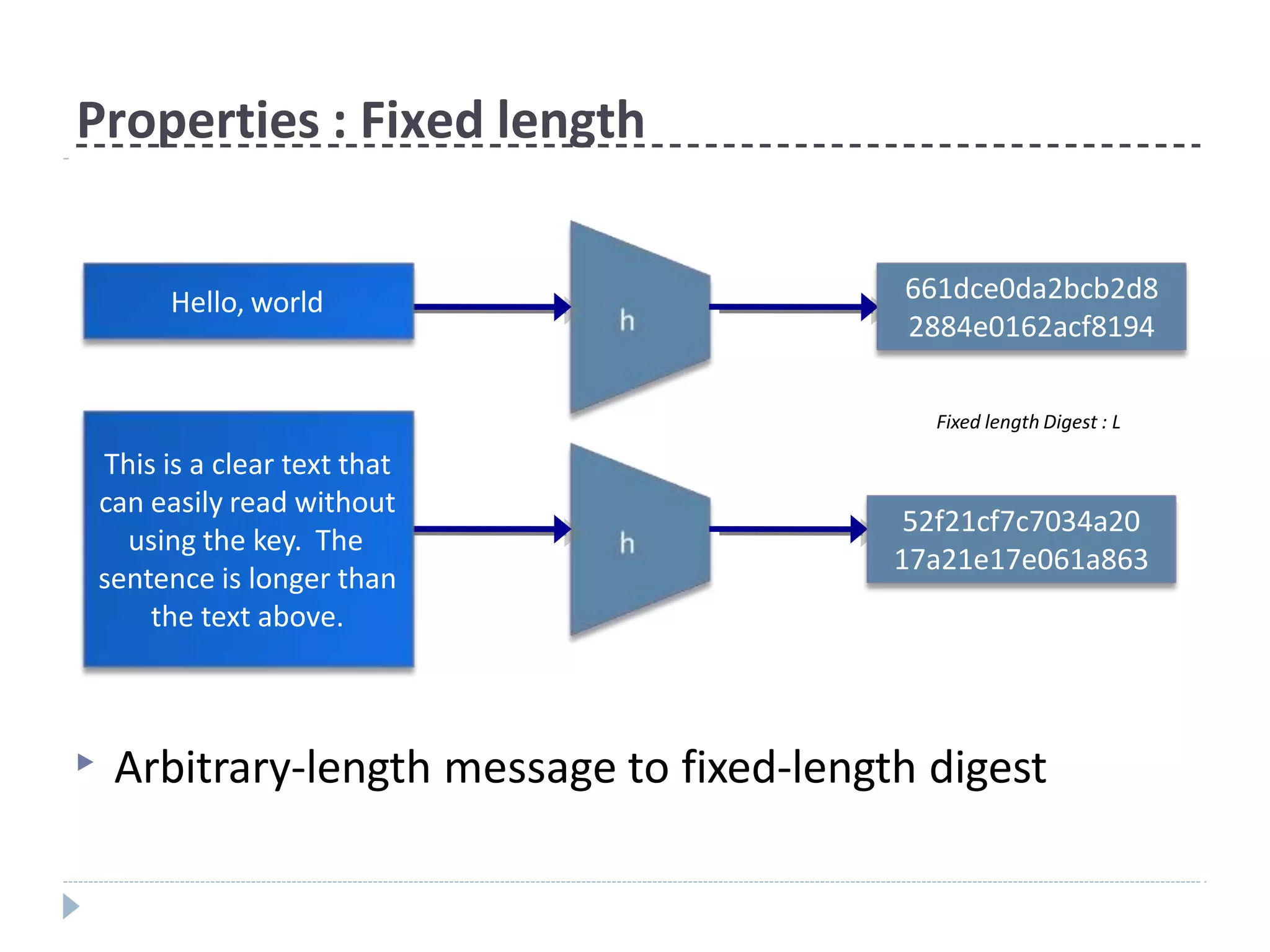
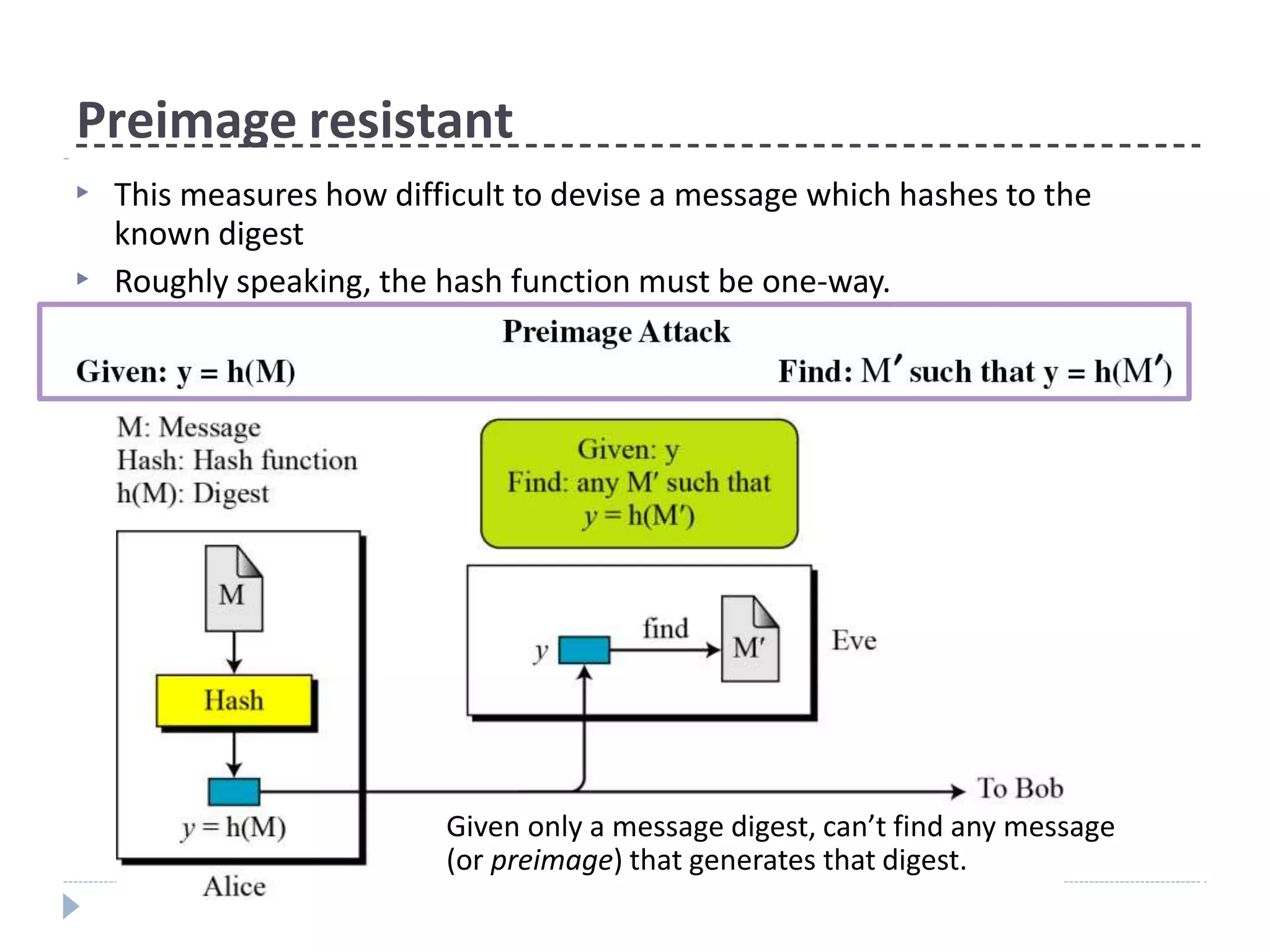
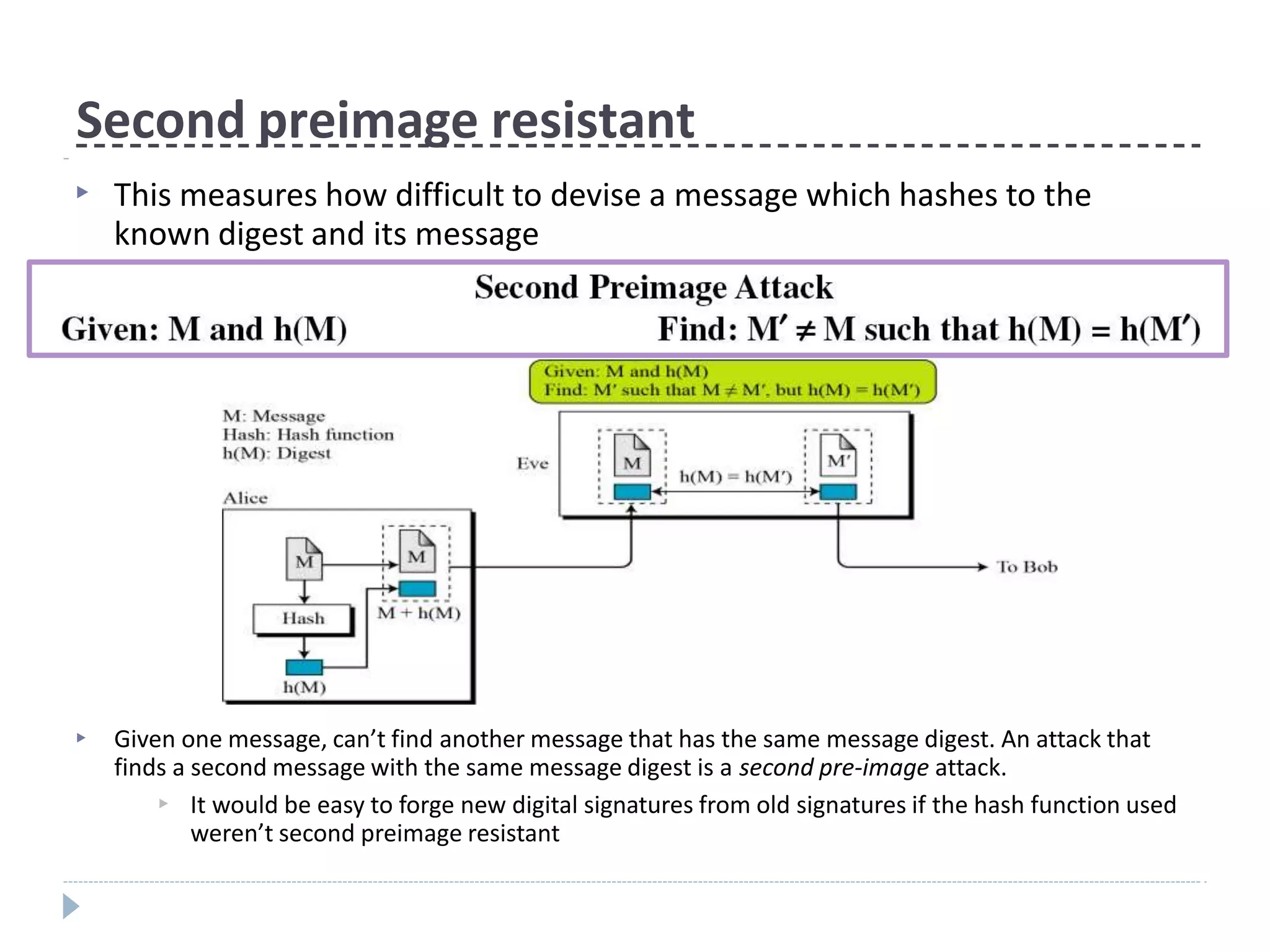
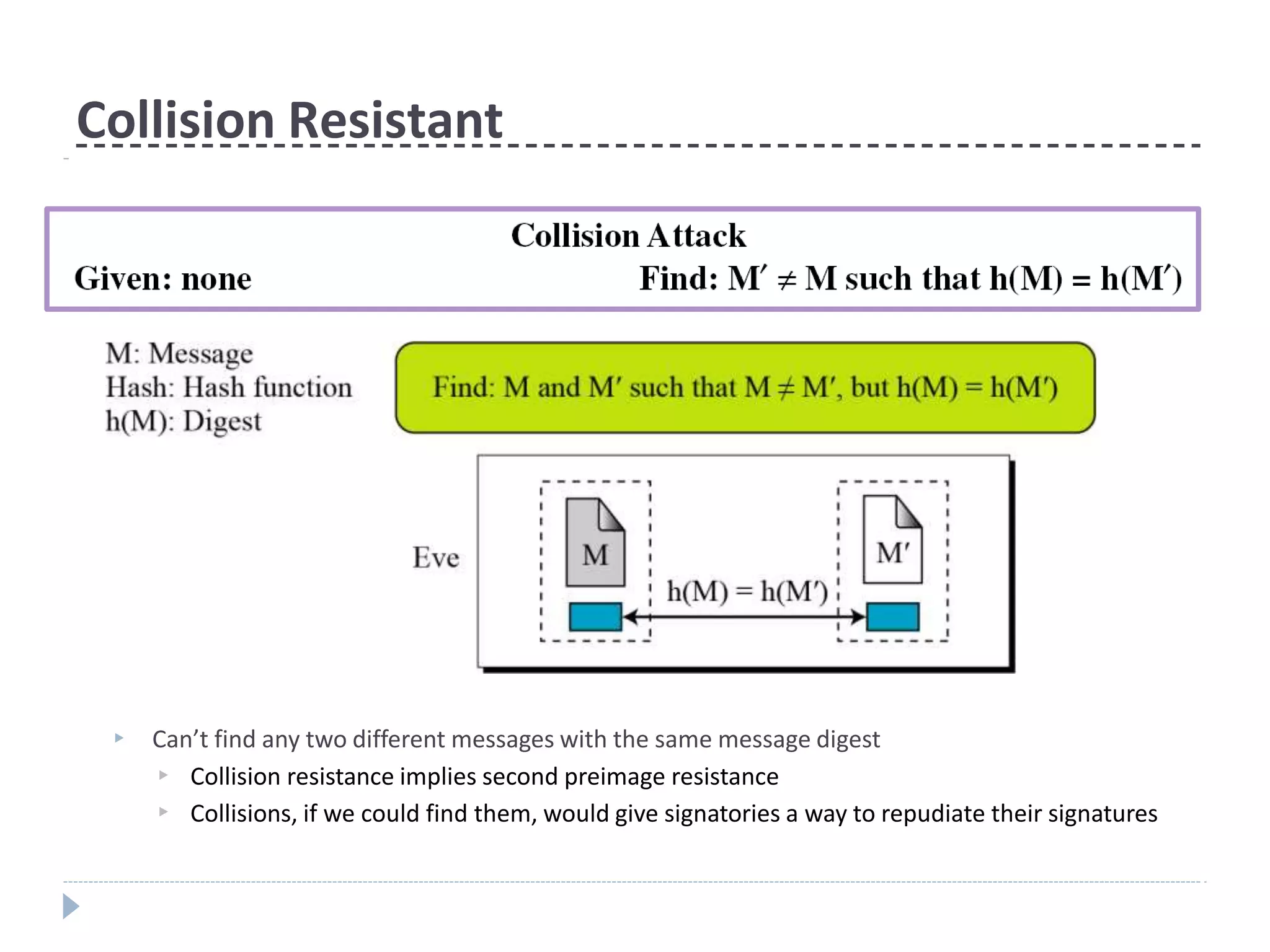
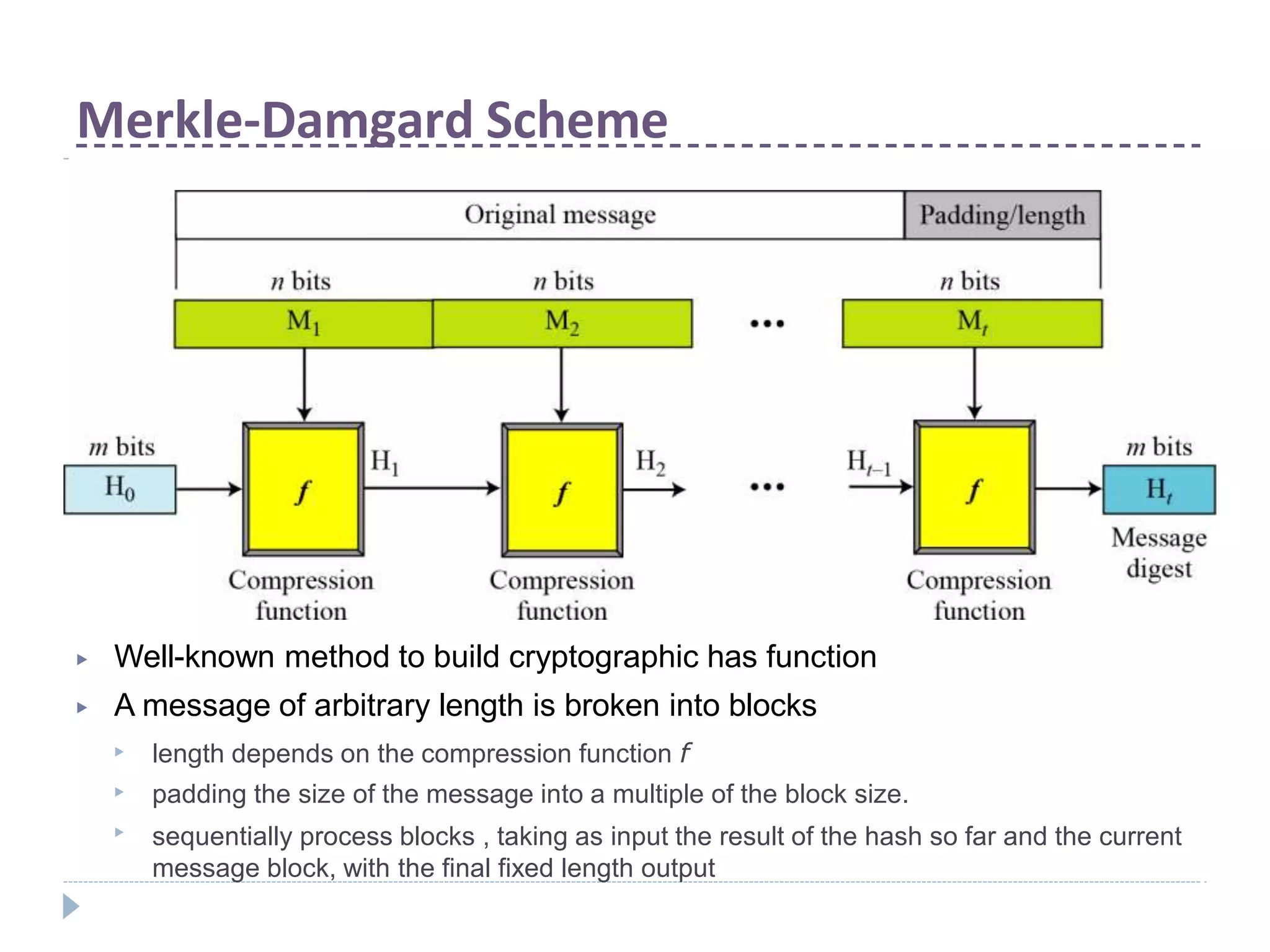
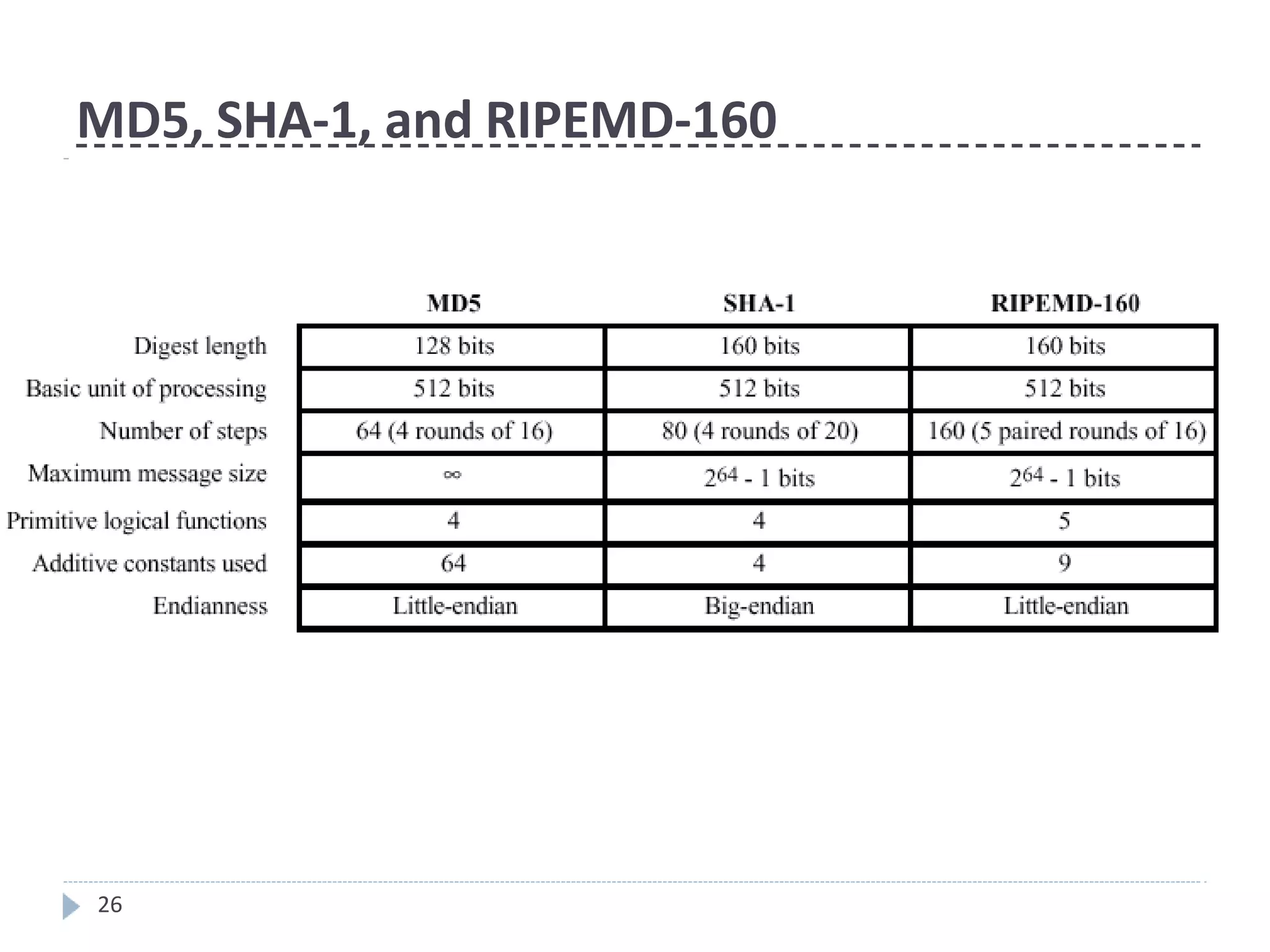
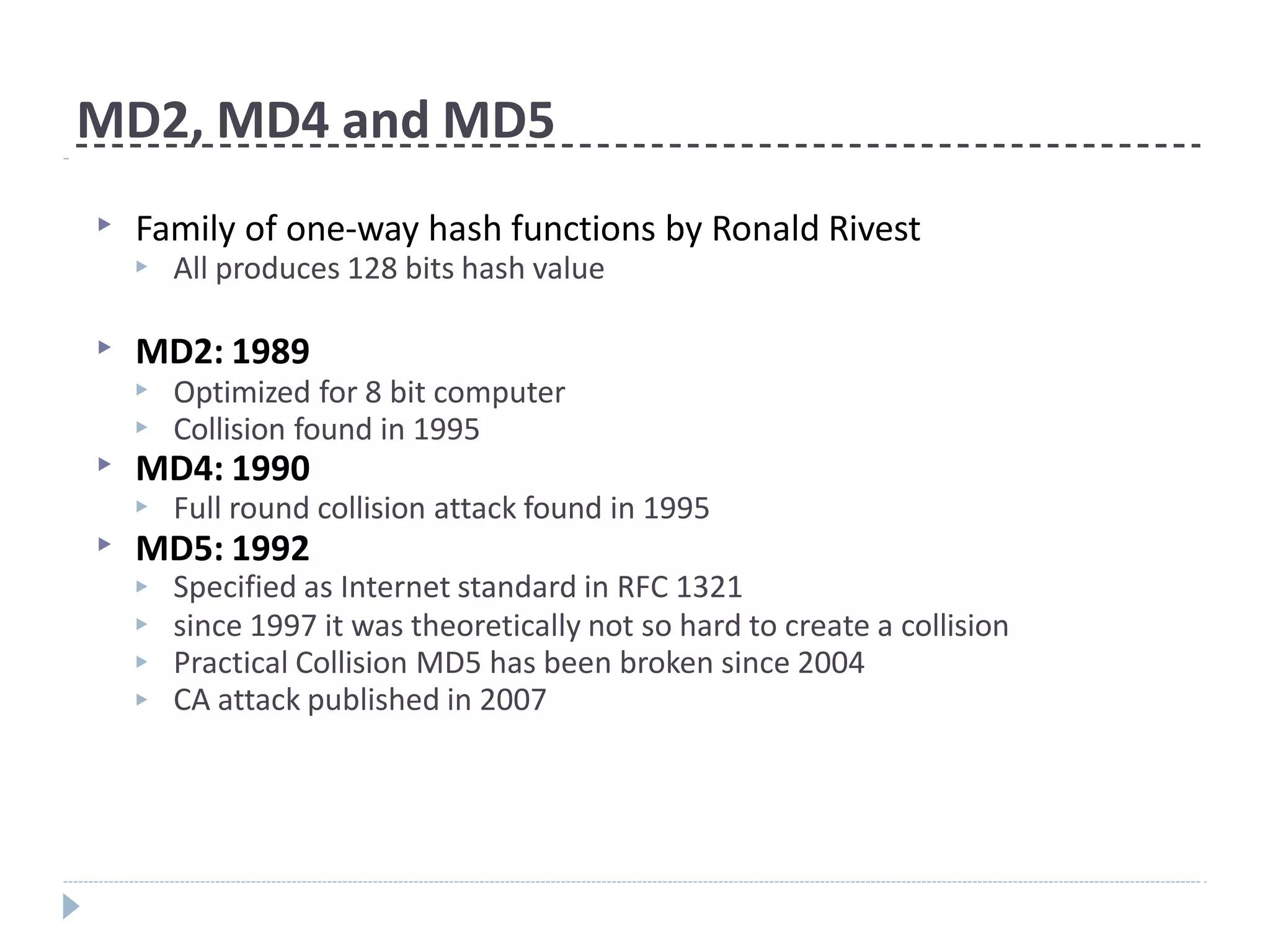
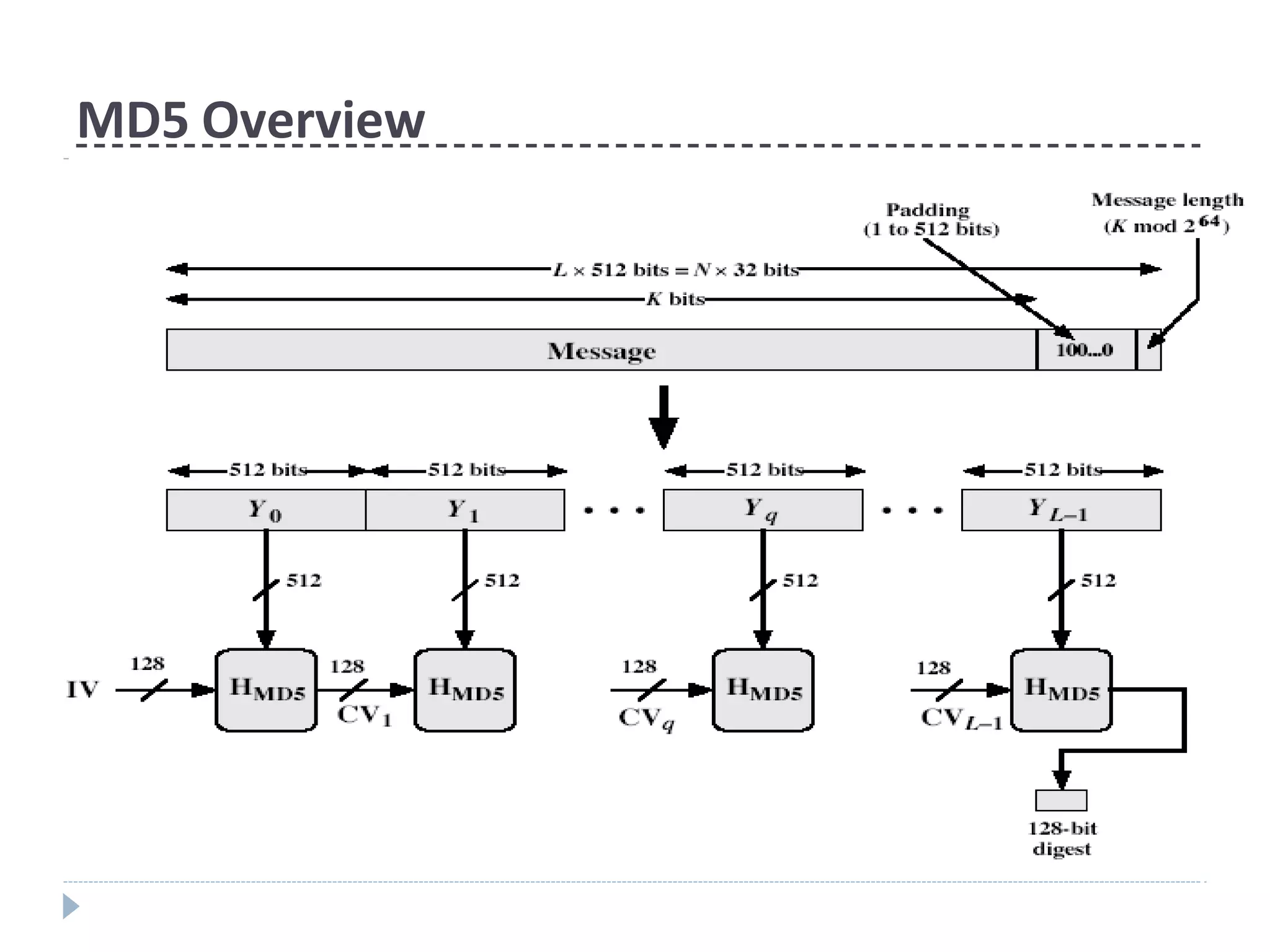
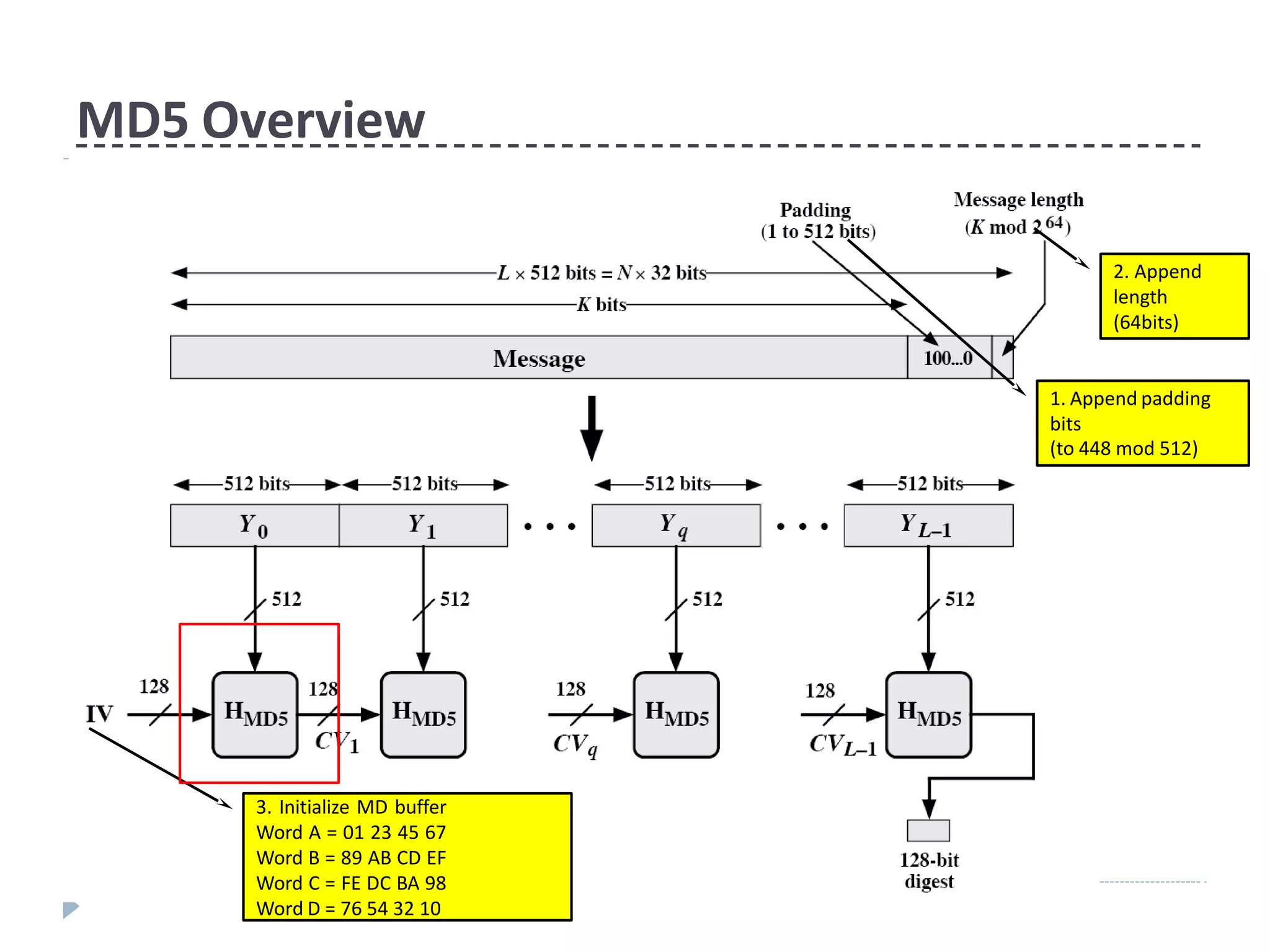
This document discusses cryptographic hash functions. It provides an overview of their usage, properties, structure, and attacks. Hash functions map messages of arbitrary length to fixed-length digests. They are used for applications like file integrity verification, password storage, and digital signatures. The document outlines the design of common hash functions like MD5 and SHA-1/2, and notes that MD5 is insecure while SHA-1 is becoming outdated. It discusses the need for a new secure hash standard, and the NIST SHA-3 competition to select standardized replacement functions.










![Hash Algorithm Design – MD5
16 steps
Constructed from sine function
X[k] = M [q*16+k] (32 bit)](https://image.slidesharecdn.com/cryptography-hash-functions-230308230538-8bbfb896/75/Cryptography-Hash-Functions-pptx-31-2048.jpg)
![The ith 32-bit word in matrix T, constructed from the sine function
M [q*16+k] = the kth 32-bit word from the qth 512-bit block of the msg
Single step](https://image.slidesharecdn.com/cryptography-hash-functions-230308230538-8bbfb896/75/Cryptography-Hash-Functions-pptx-32-2048.jpg)