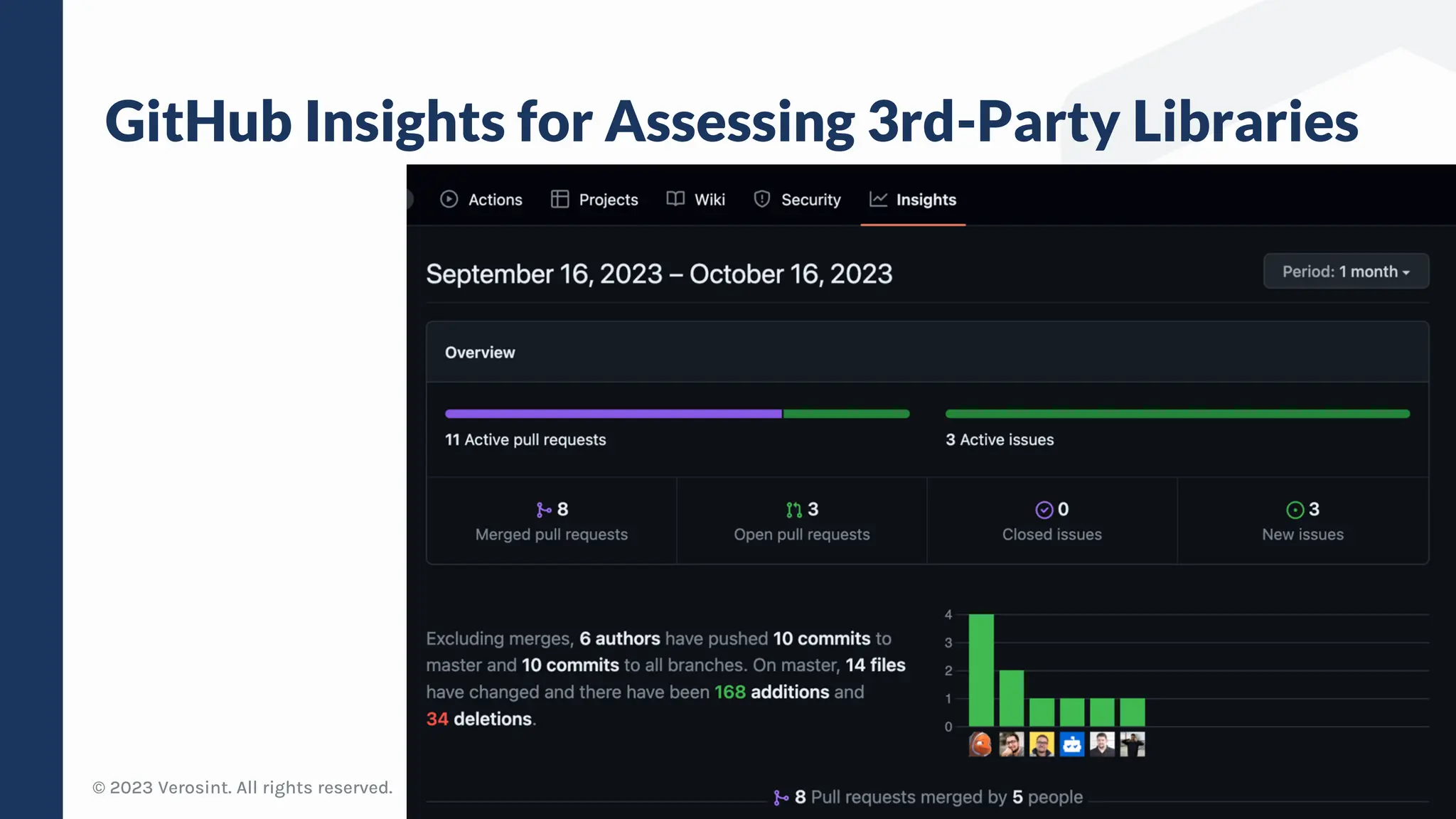
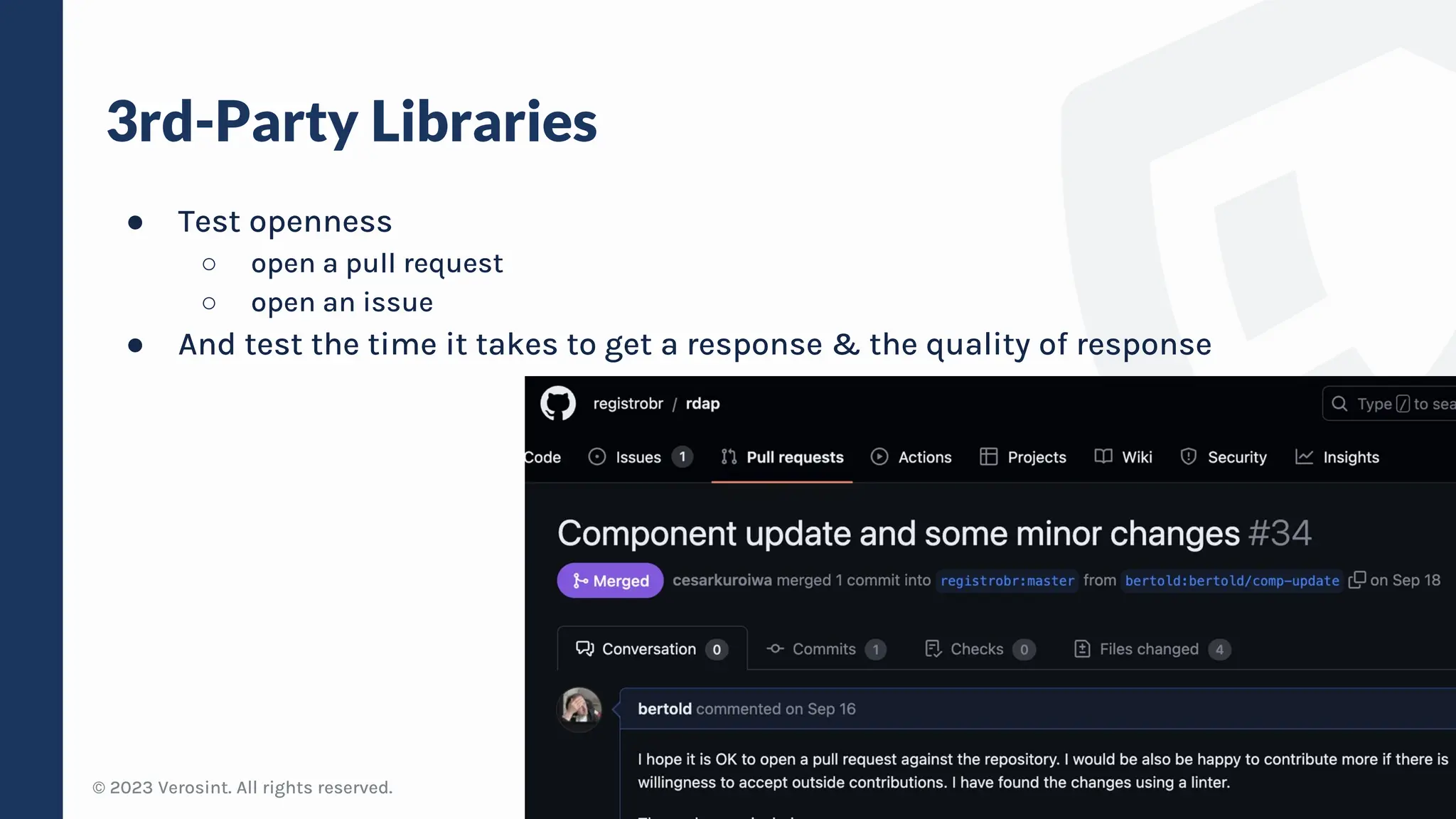
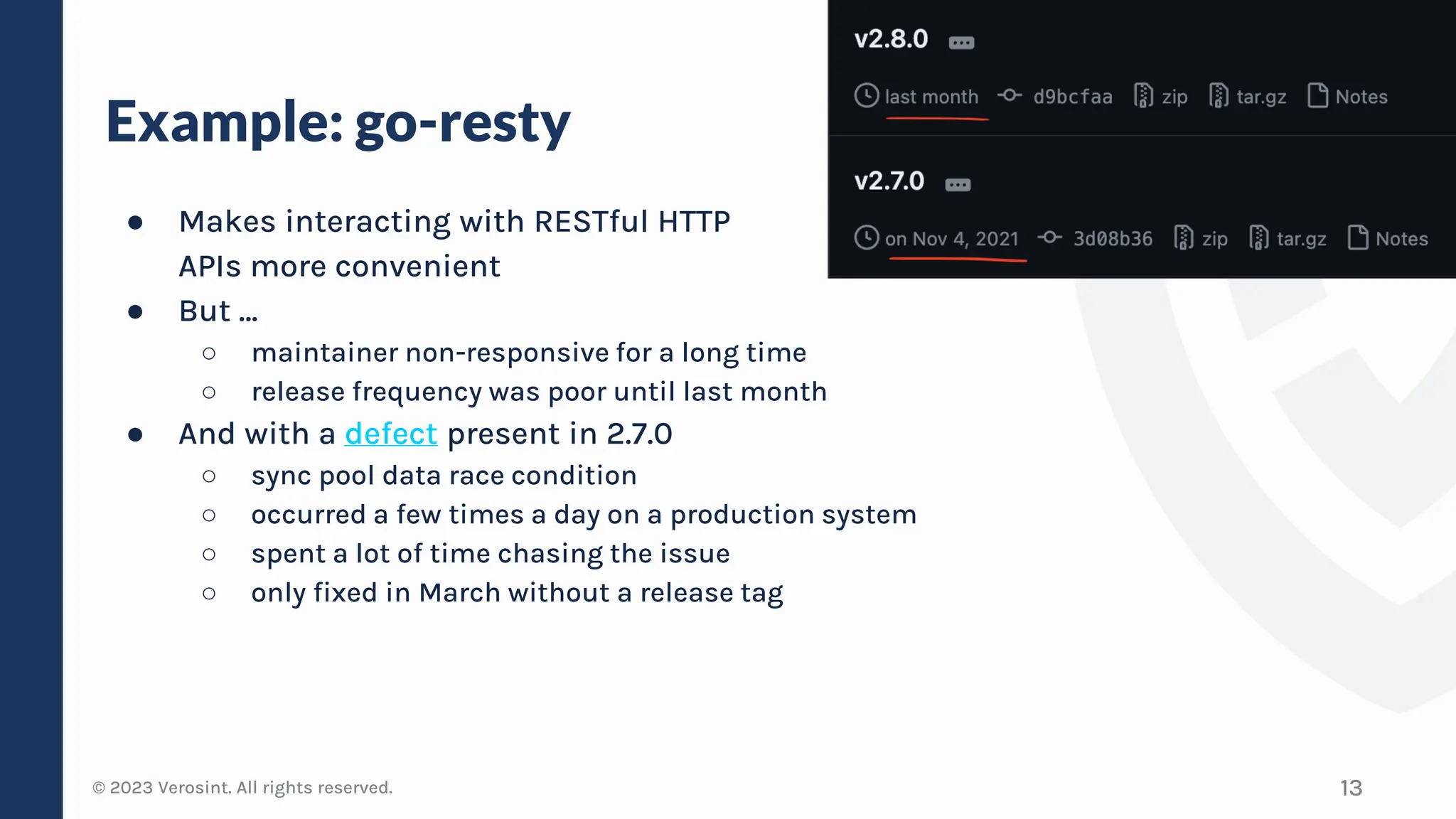
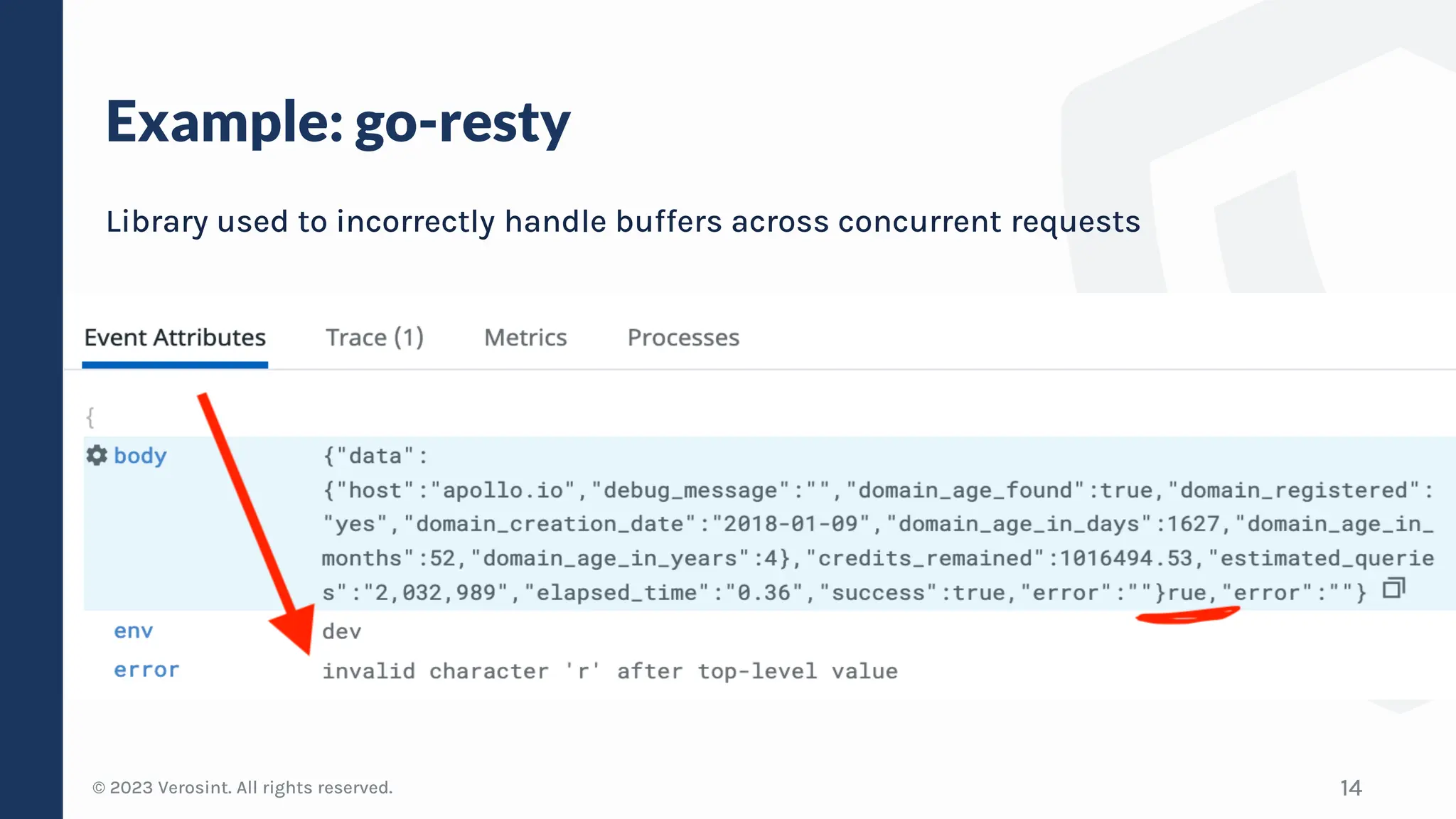
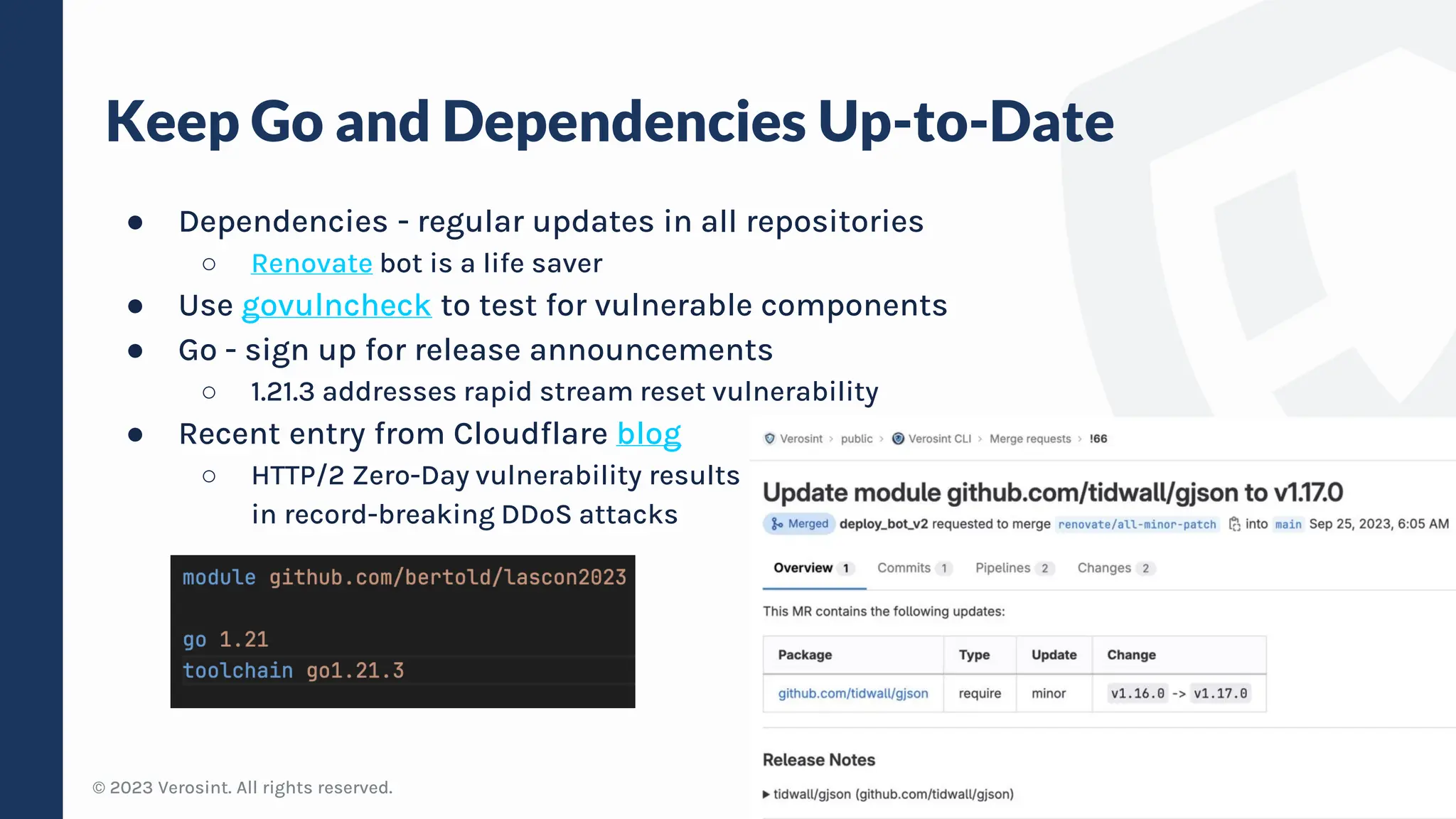
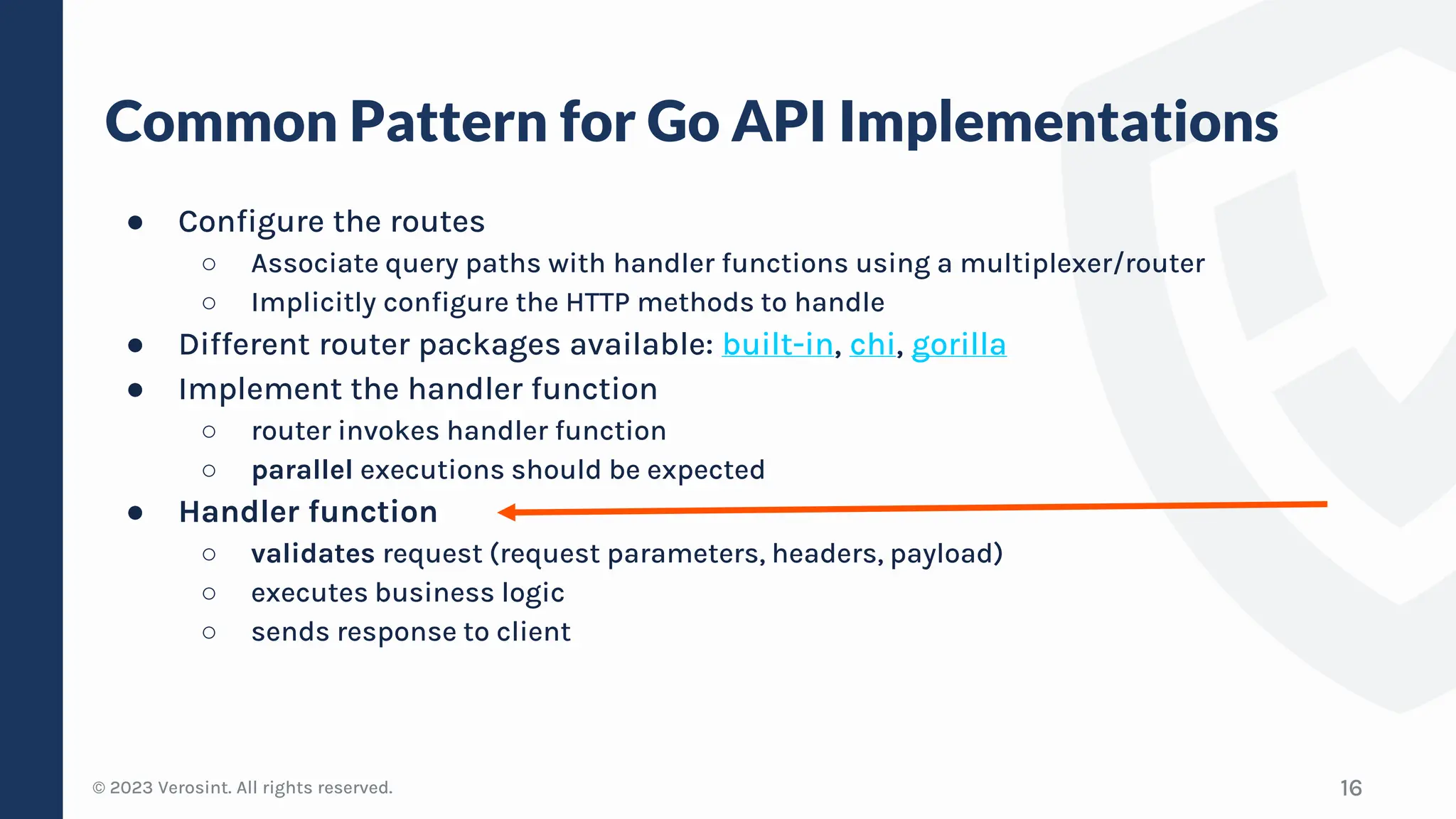
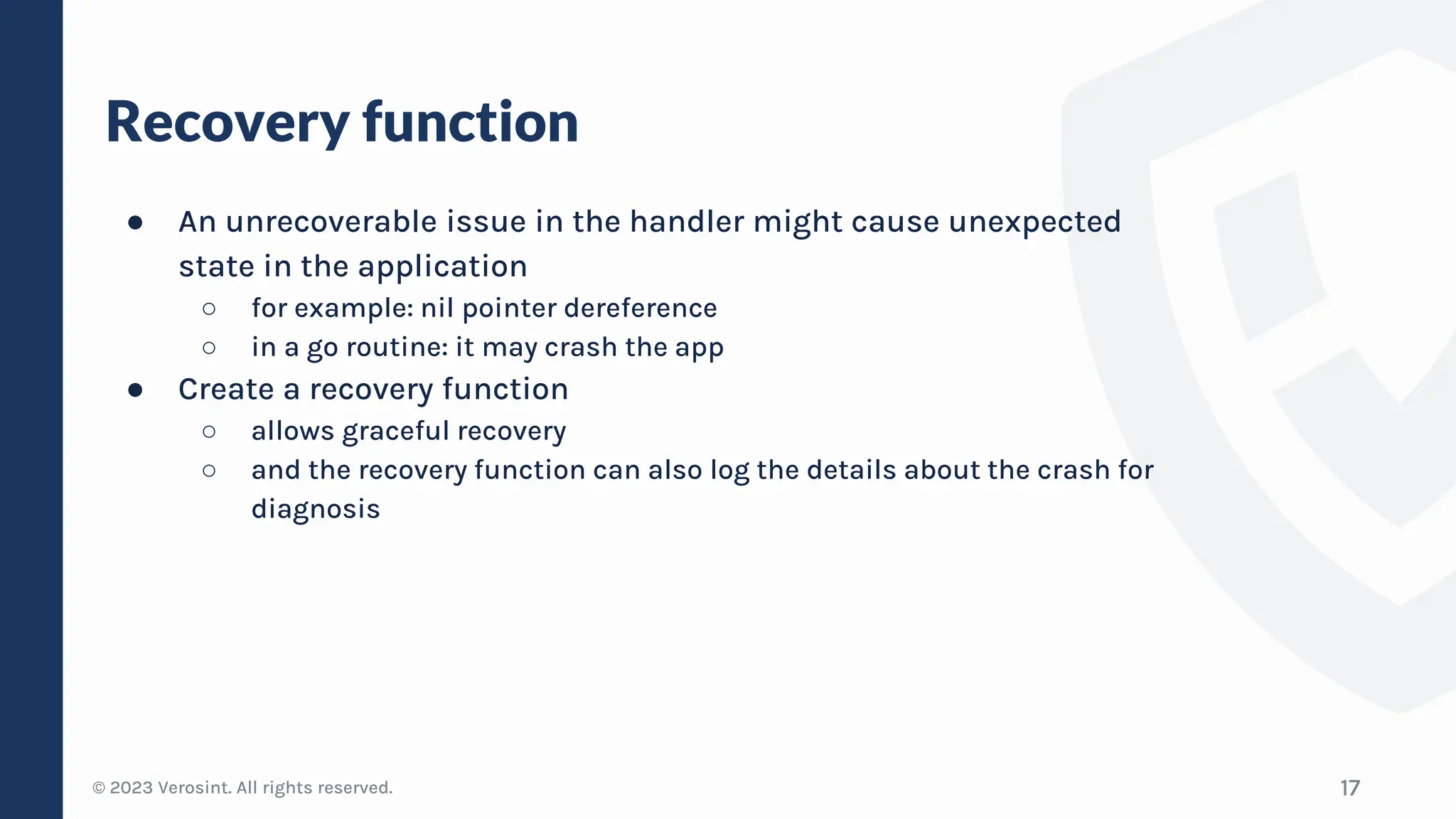
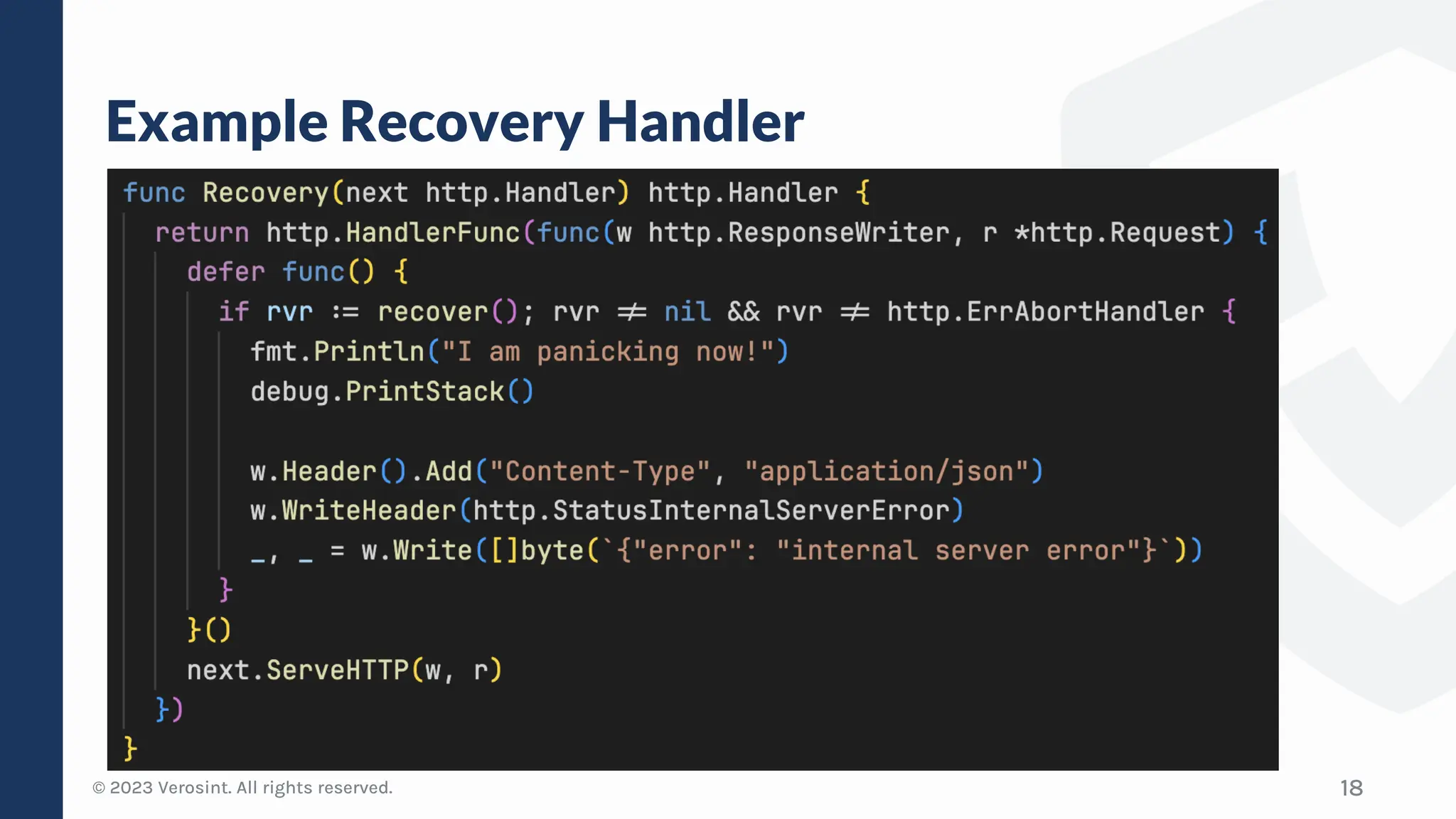
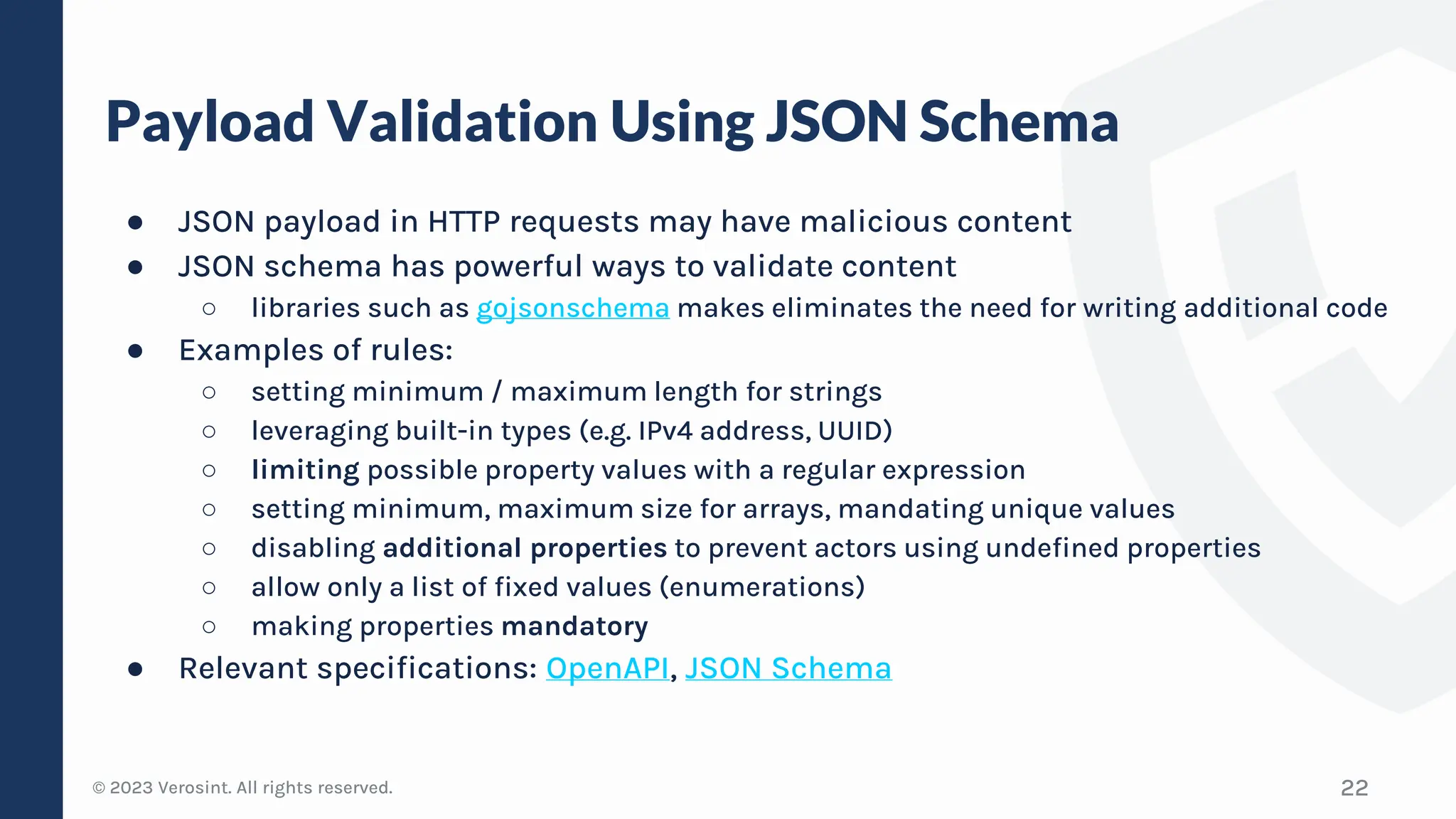
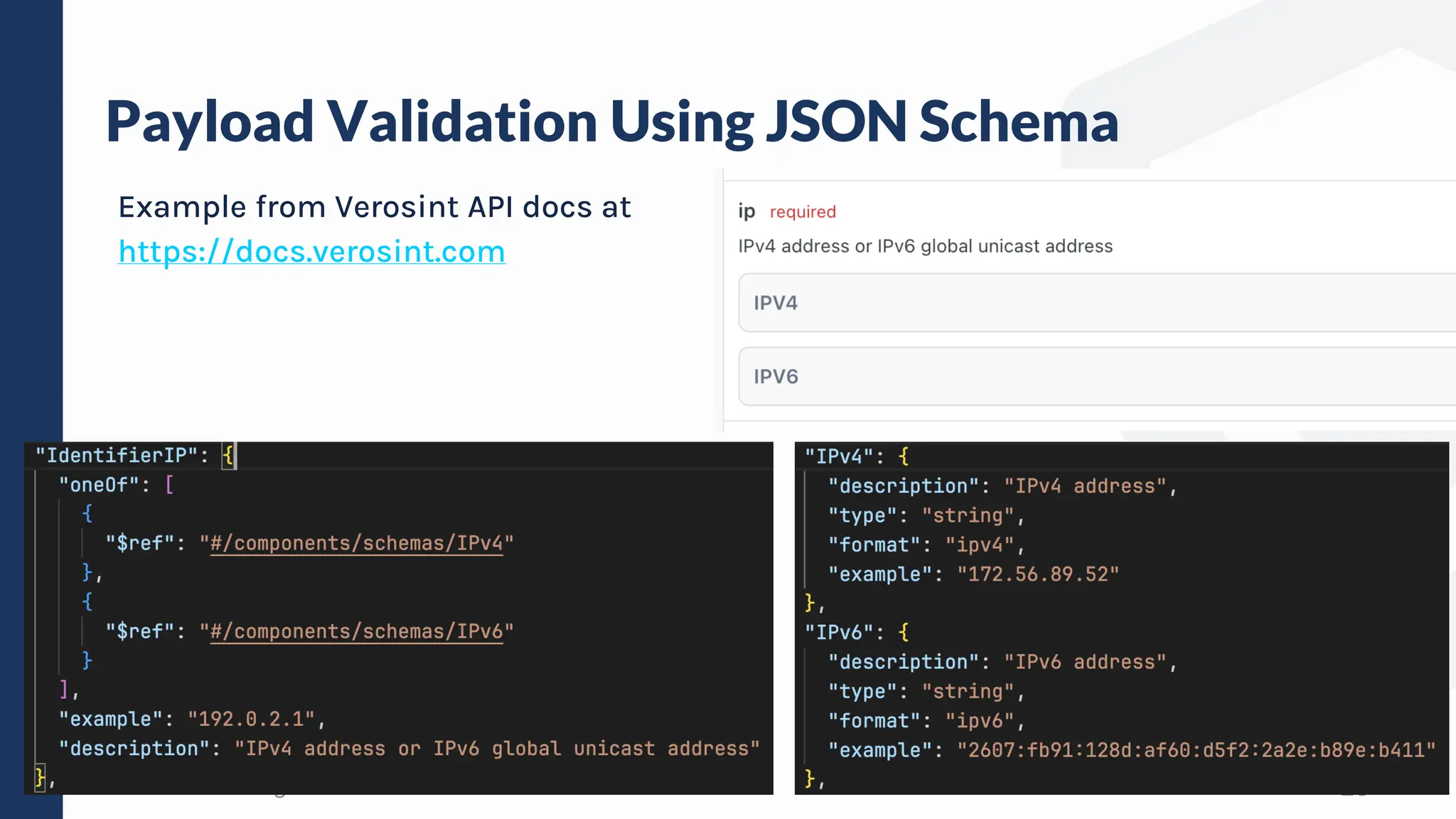
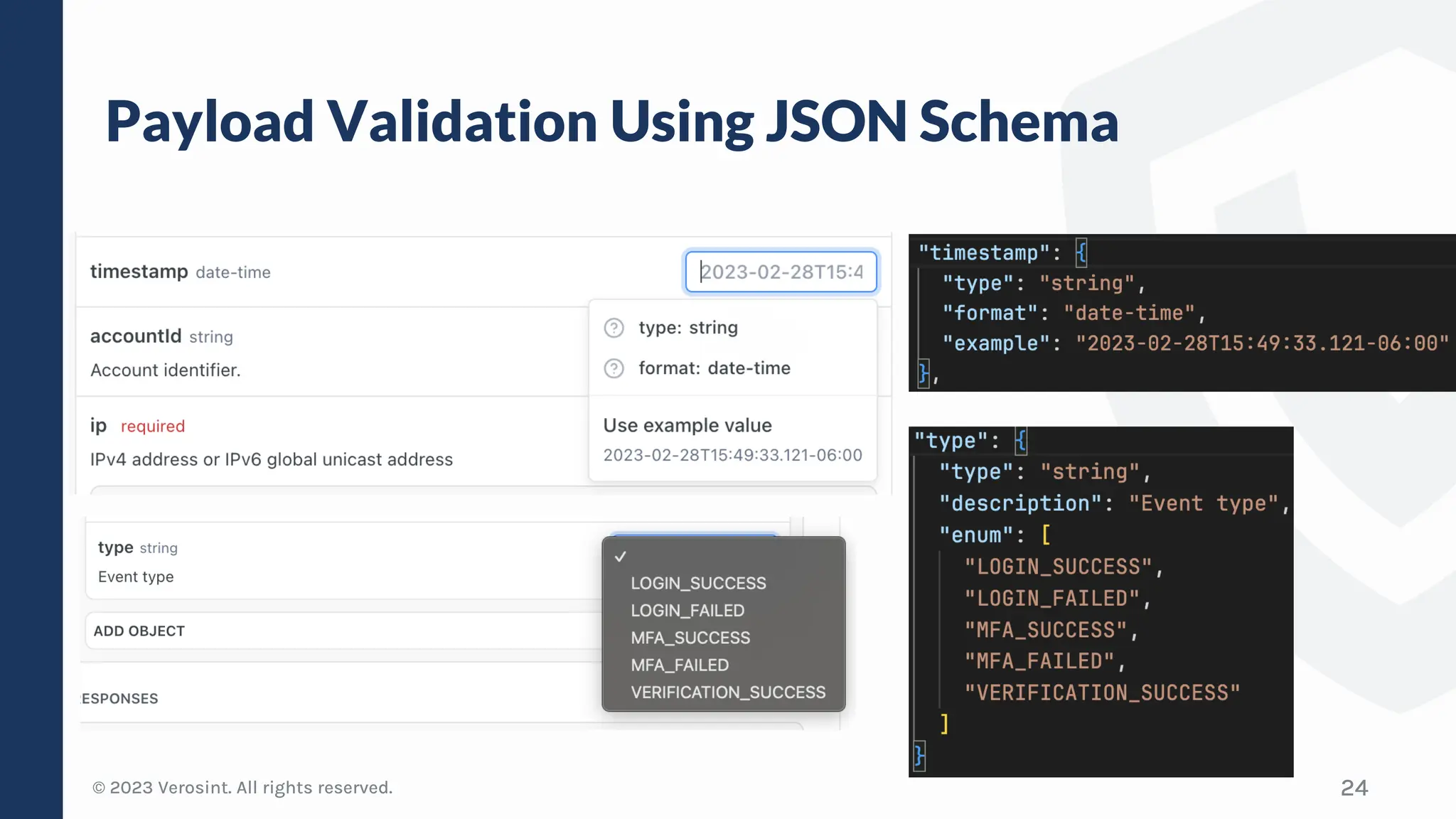
The document discusses defensive API development techniques for building HTTP APIs in Go. It covers choosing third-party libraries carefully, keeping dependencies up-to-date, implementing request validation, adding rate limiting and error handling, and testing APIs through fuzzing. The presentation provides code examples and recommendations for securing APIs, including validating payloads with JSON schema, emitting diagnostic logs, and leveraging features in Go like built-in rate limiting and fuzzing.