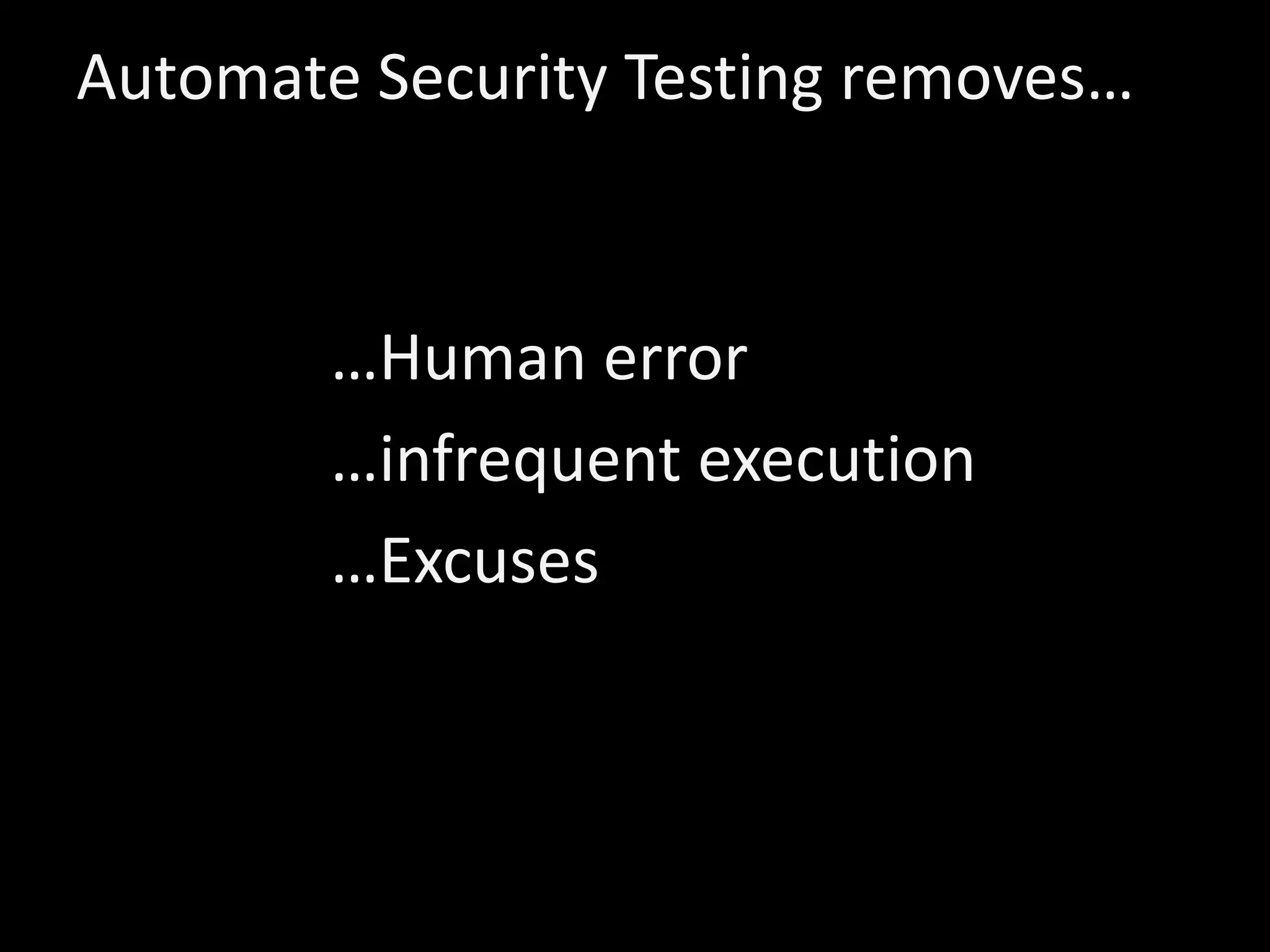
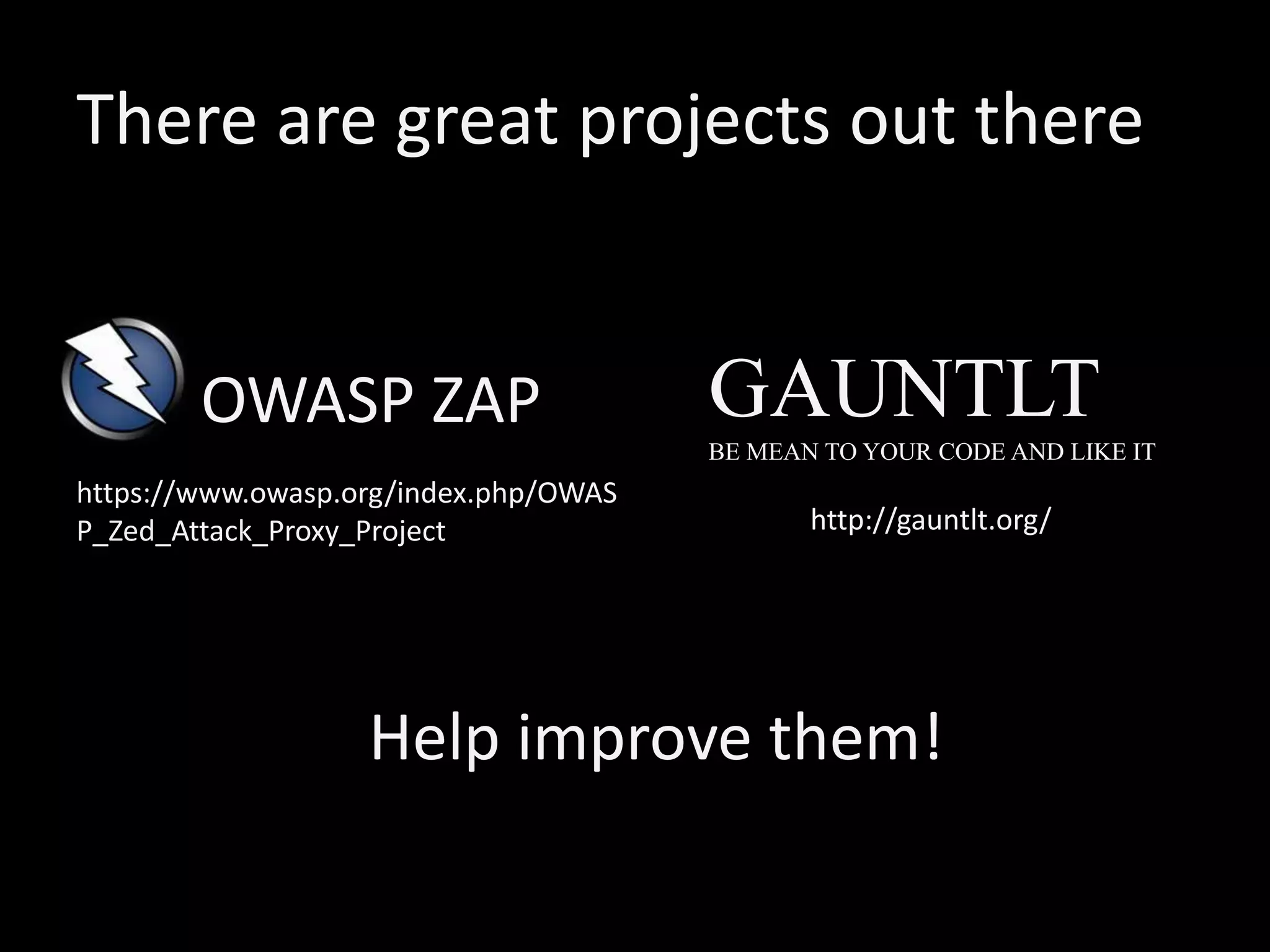
This document discusses various anti-patterns in DevOps security, highlighting how security testing often remains manual and emphasizing the need for automation to mitigate risks. It outlines several anti-patterns such as the 'Exceptions', 'Multiverse', 'Configurator', and others, each illustrating common pitfalls that can hinder security and reliability in software development. The author advocates for proactive failure management and continuous improvement in DevOps practices to ensure robust security measures are in place.