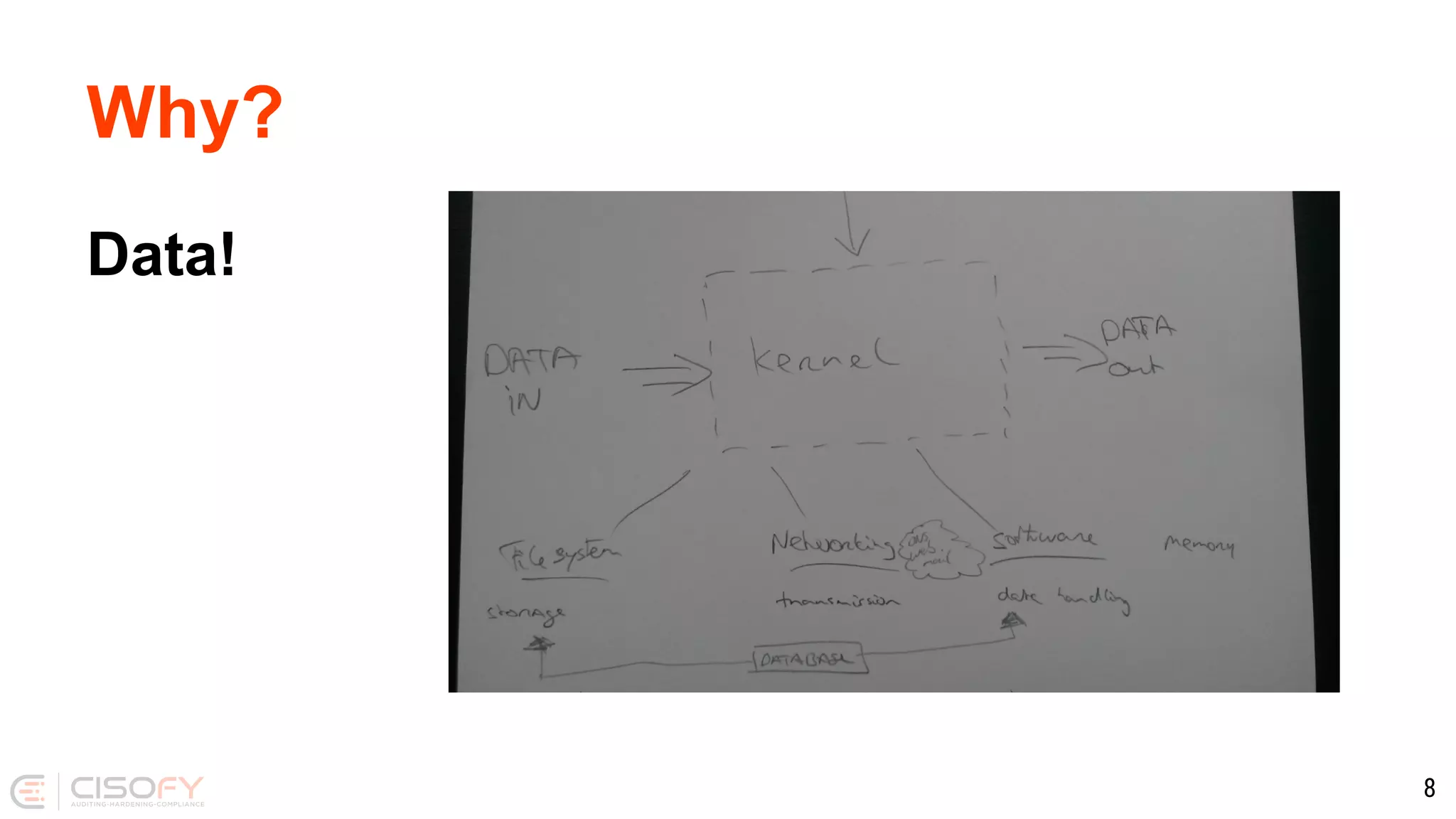
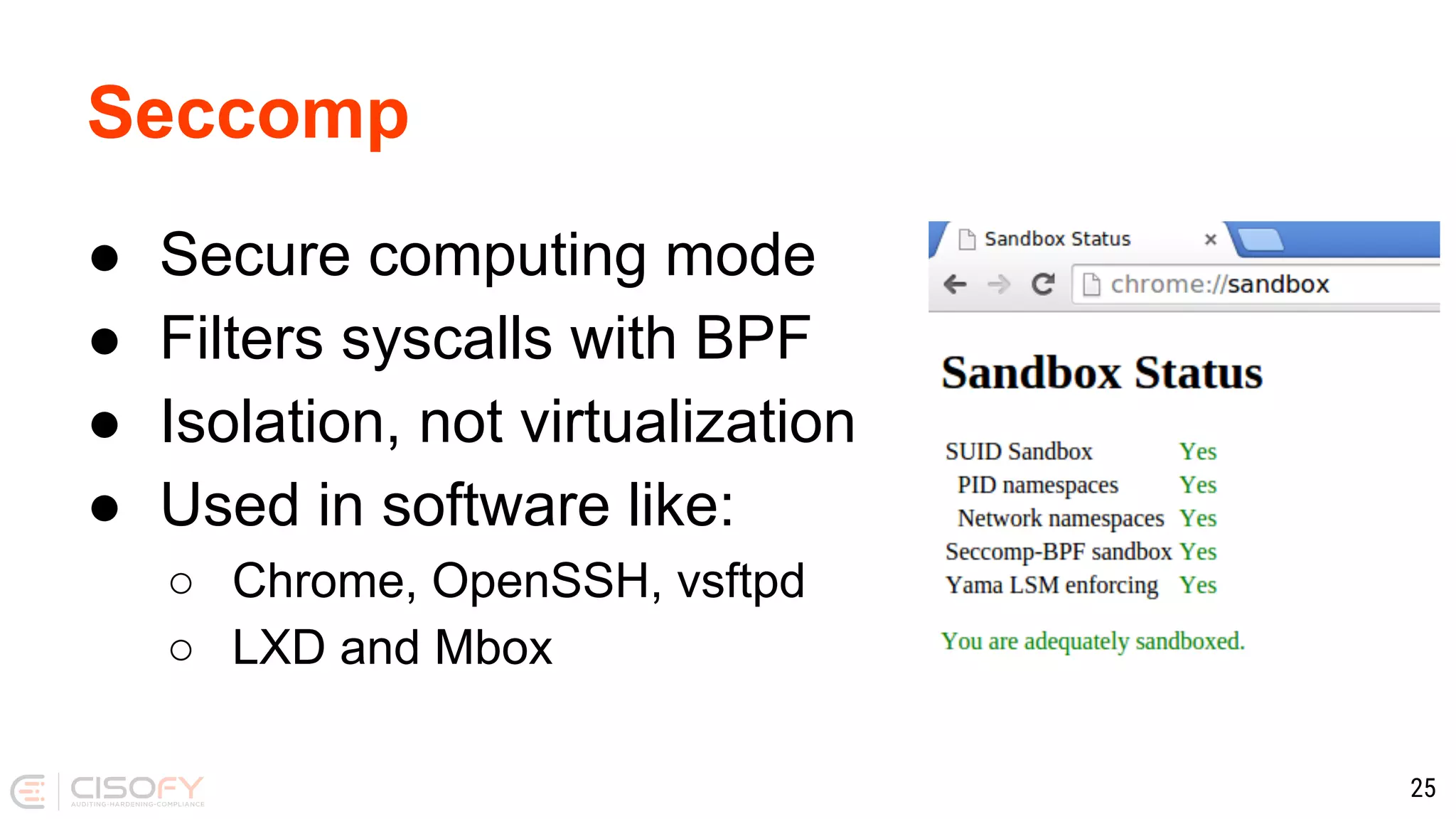
The document discusses Docker security, emphasizing the importance of securing container deployment on Linux. It outlines various risks associated with Docker, such as software vulnerabilities and knowledge gaps, and proposes best practices for enhancing security through tool usage, risk management, and container hardening techniques. The author also provides insights on Docker's benefits and the significance of data confidentiality in a containerized environment.