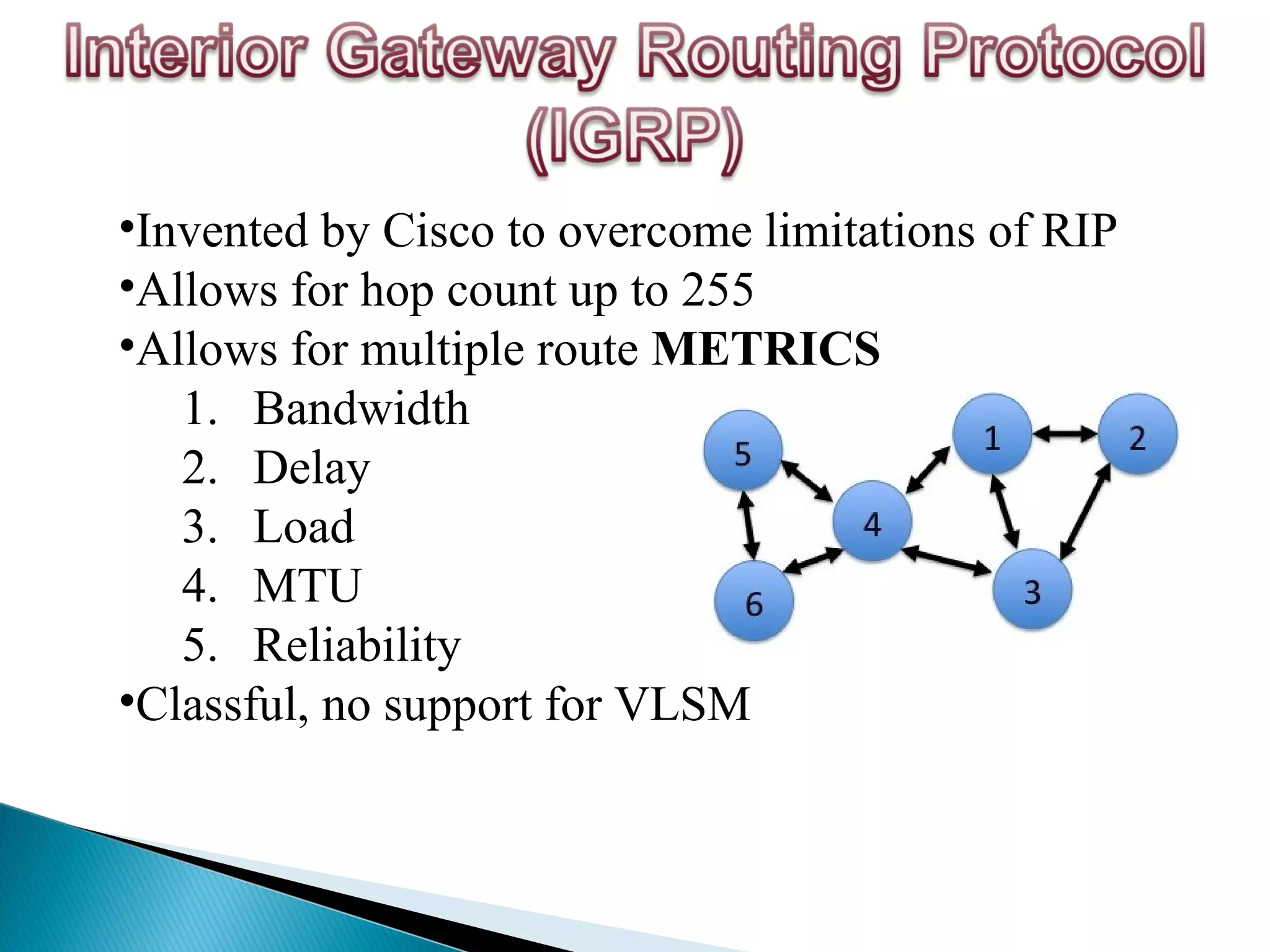
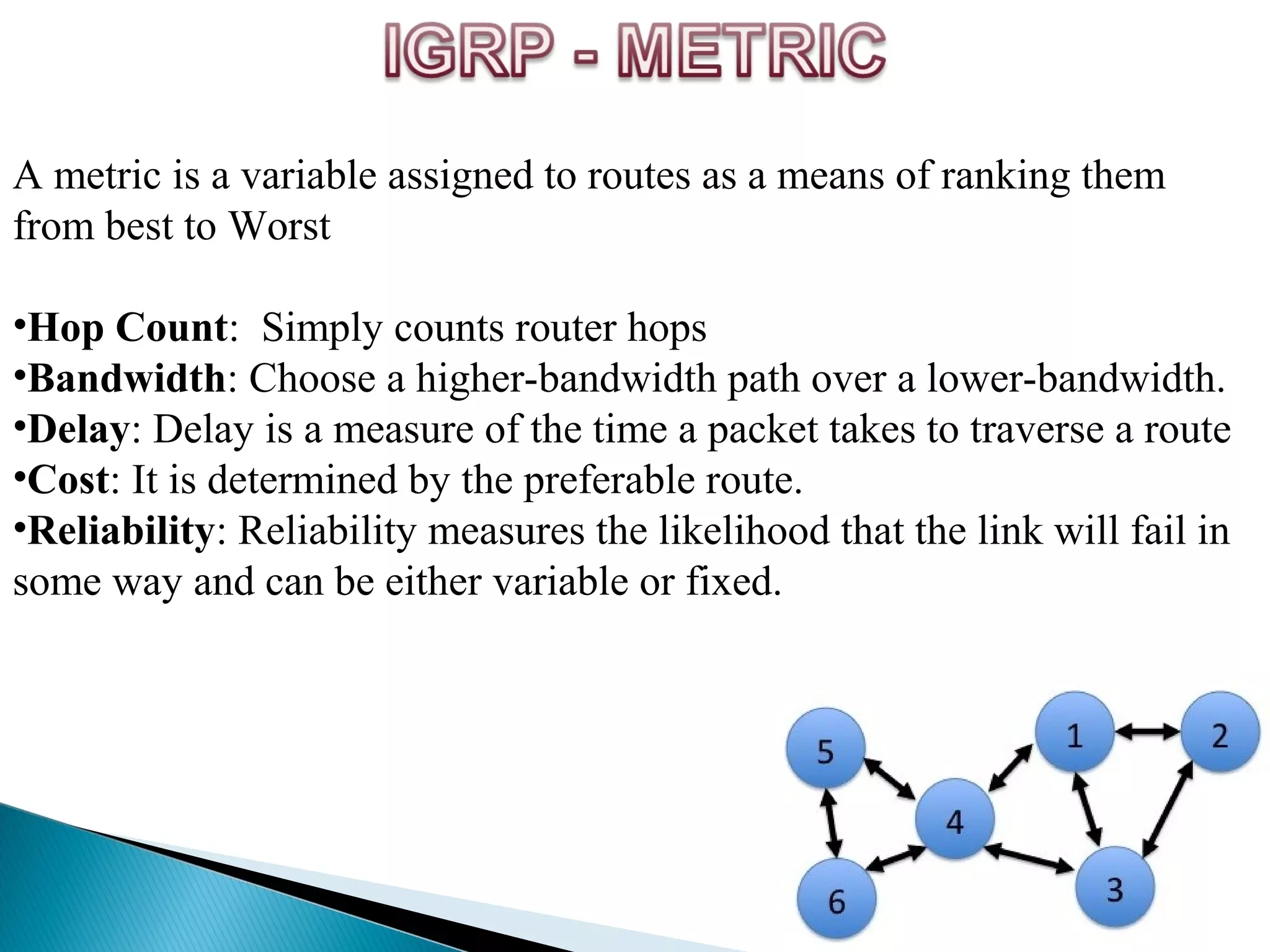
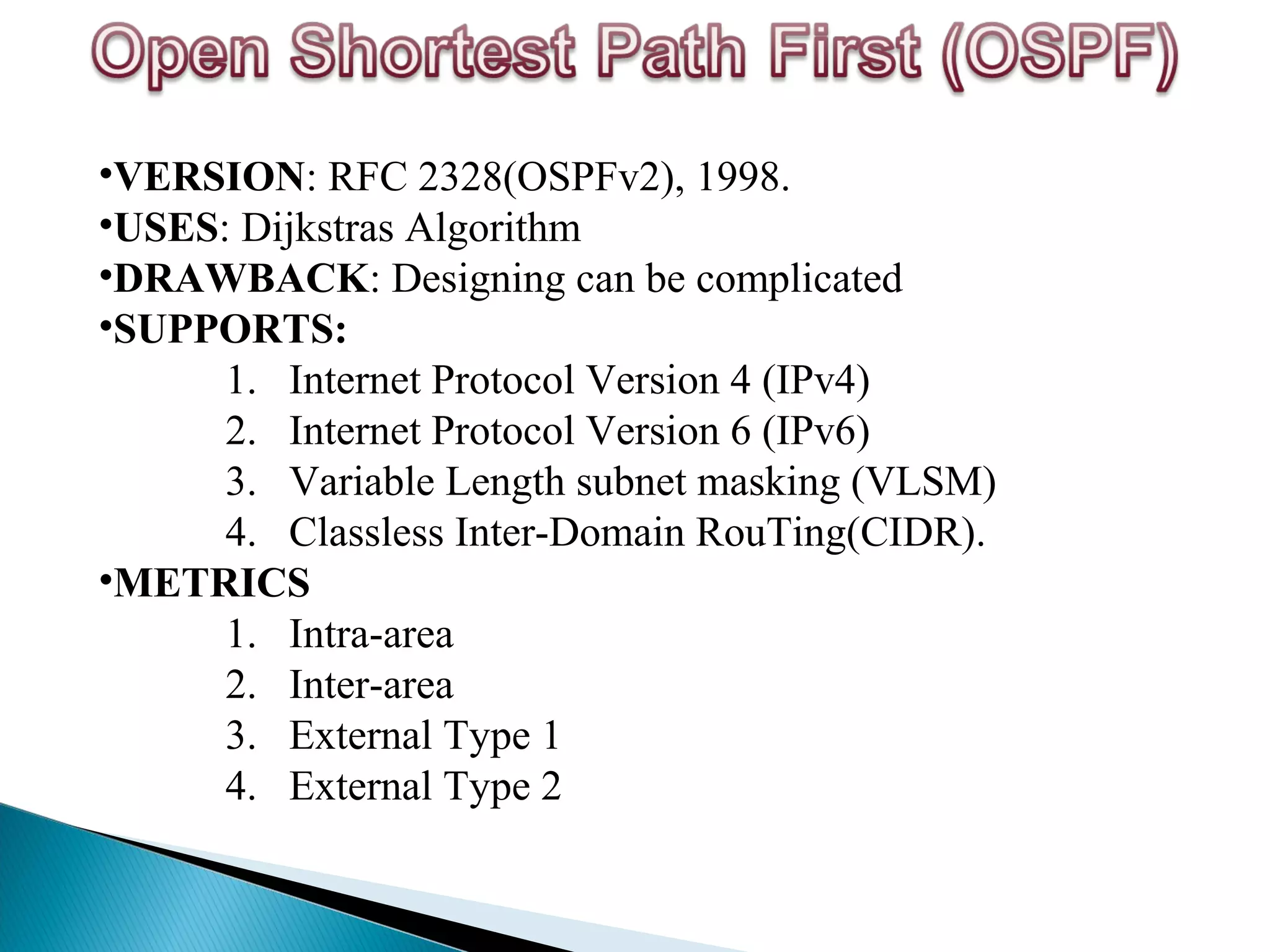
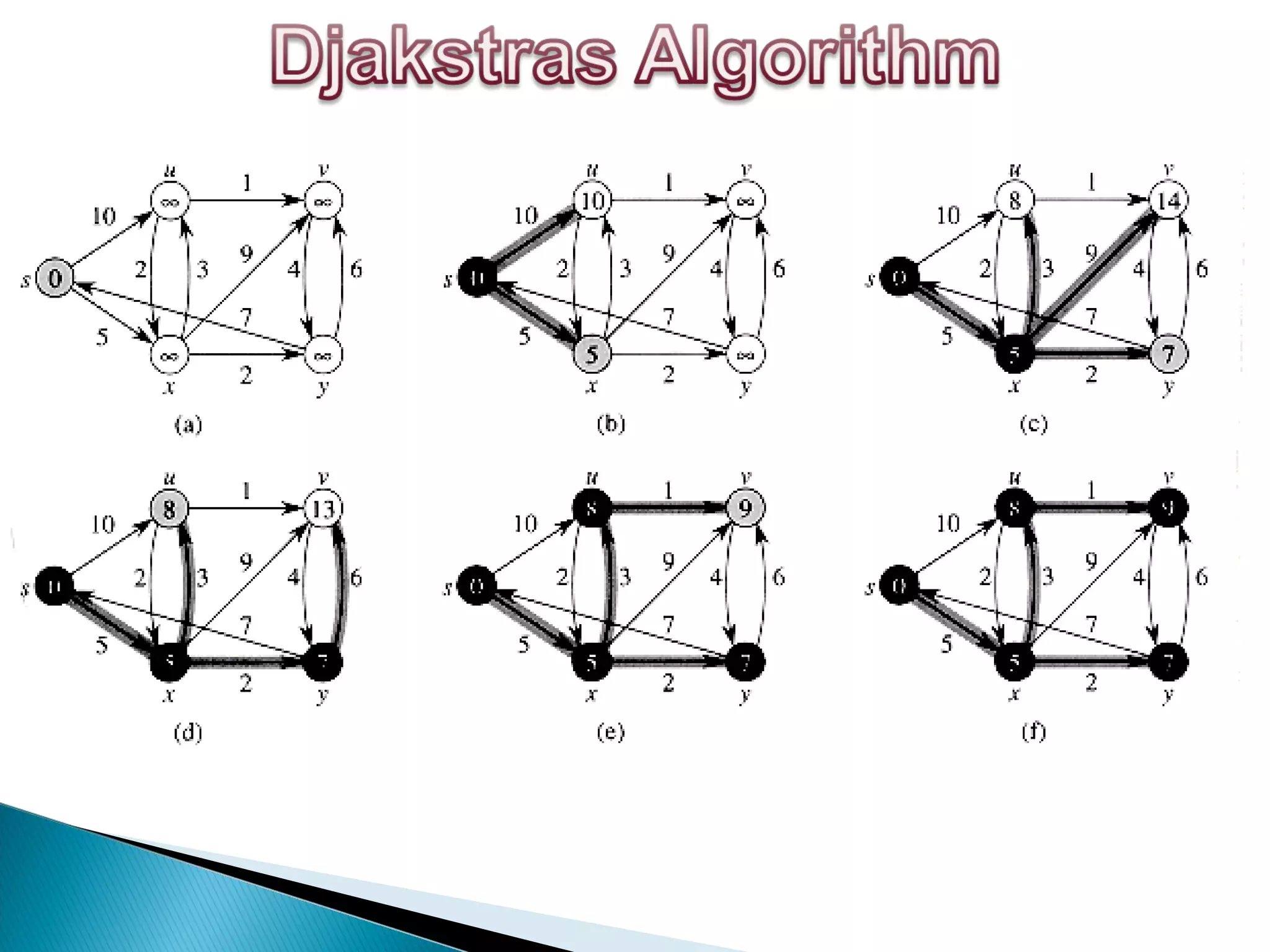
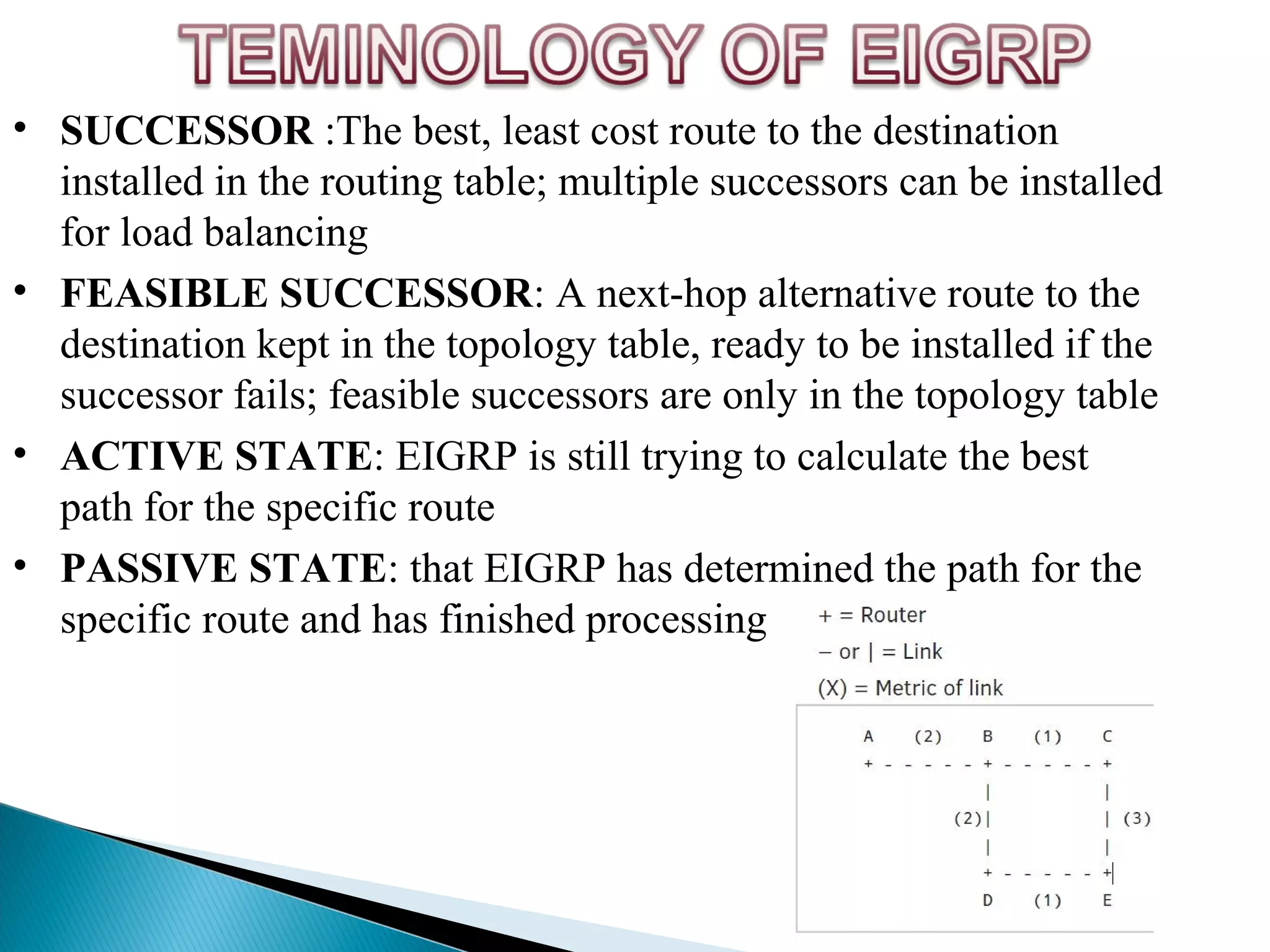
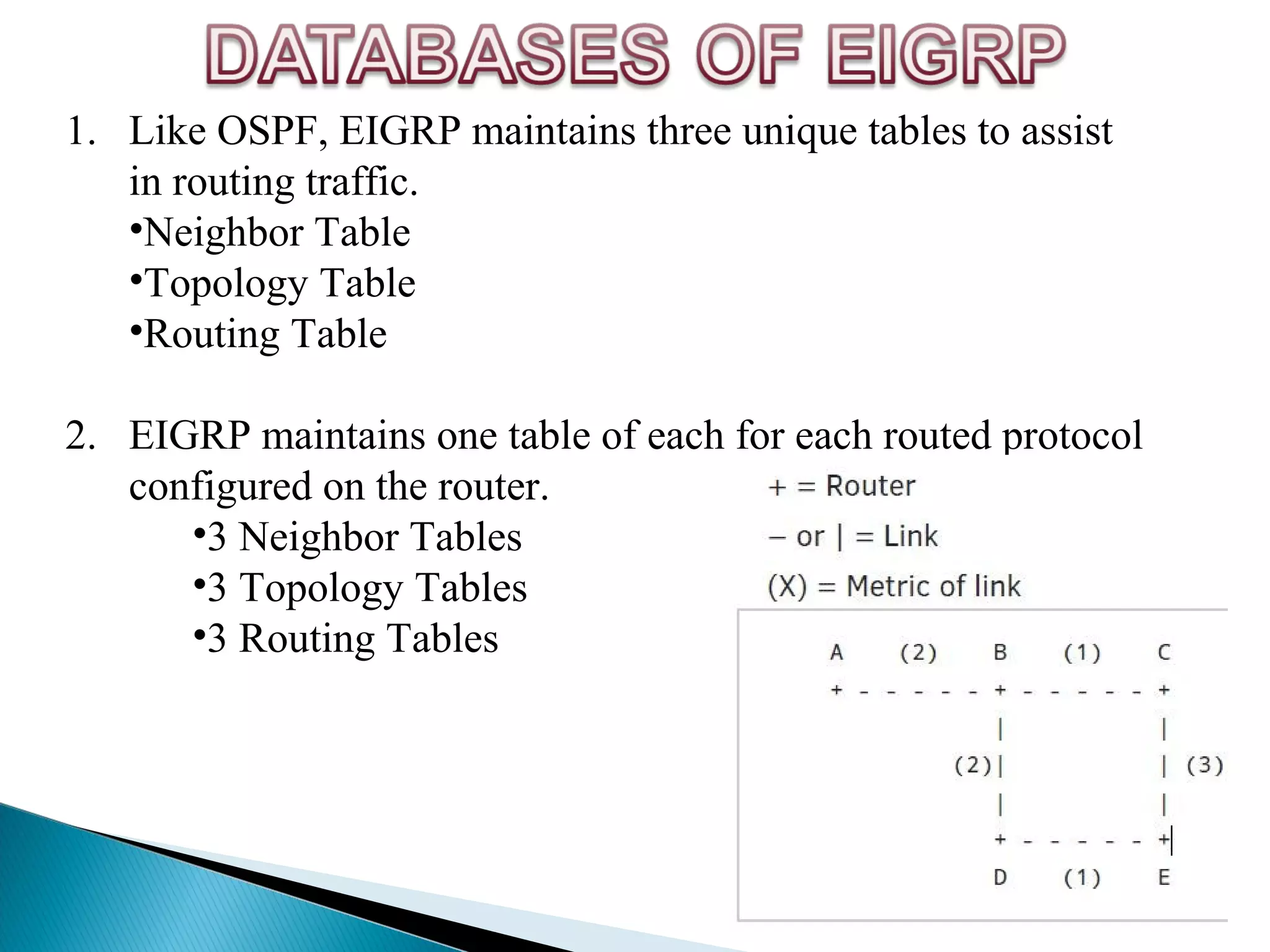
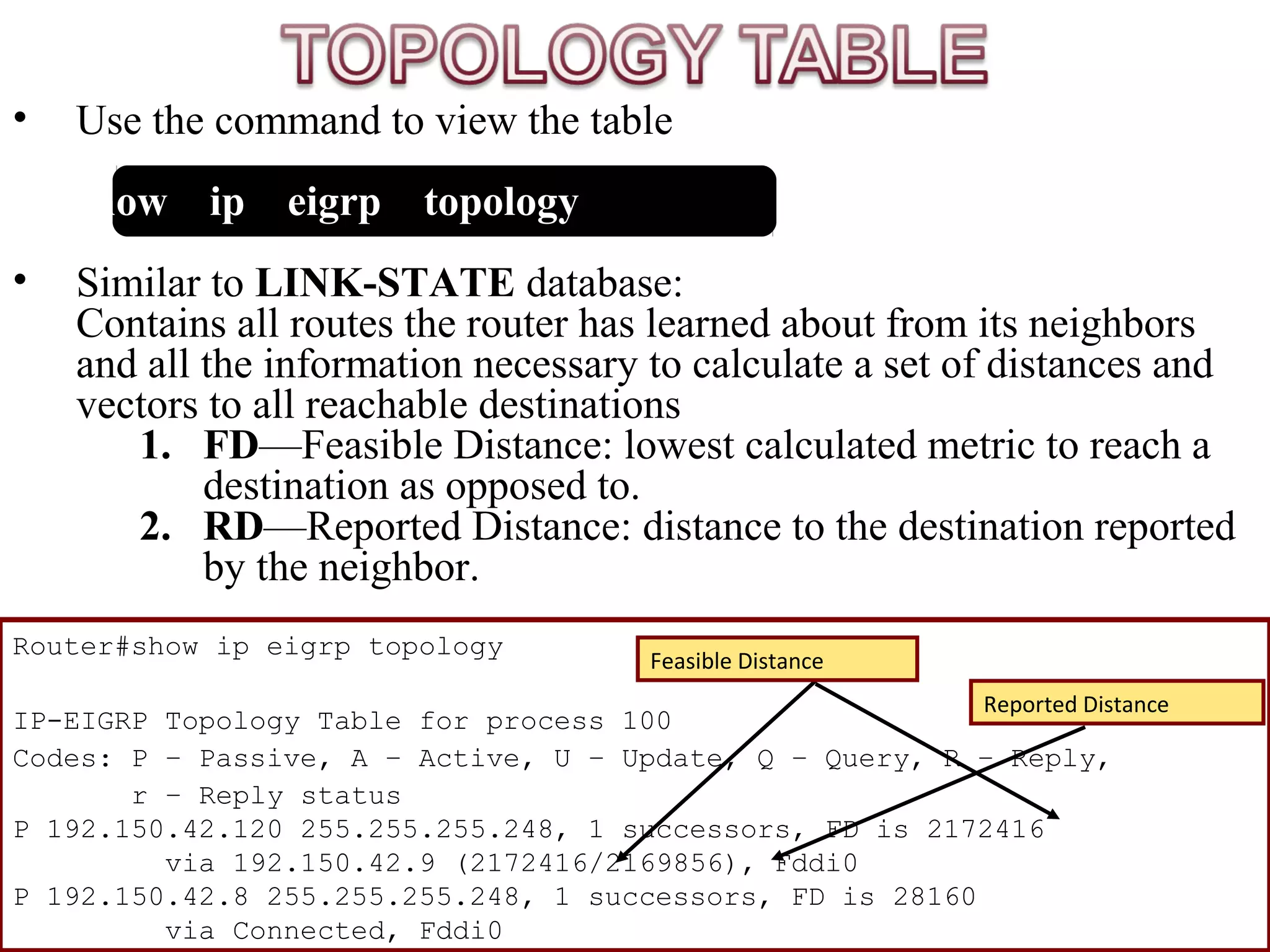
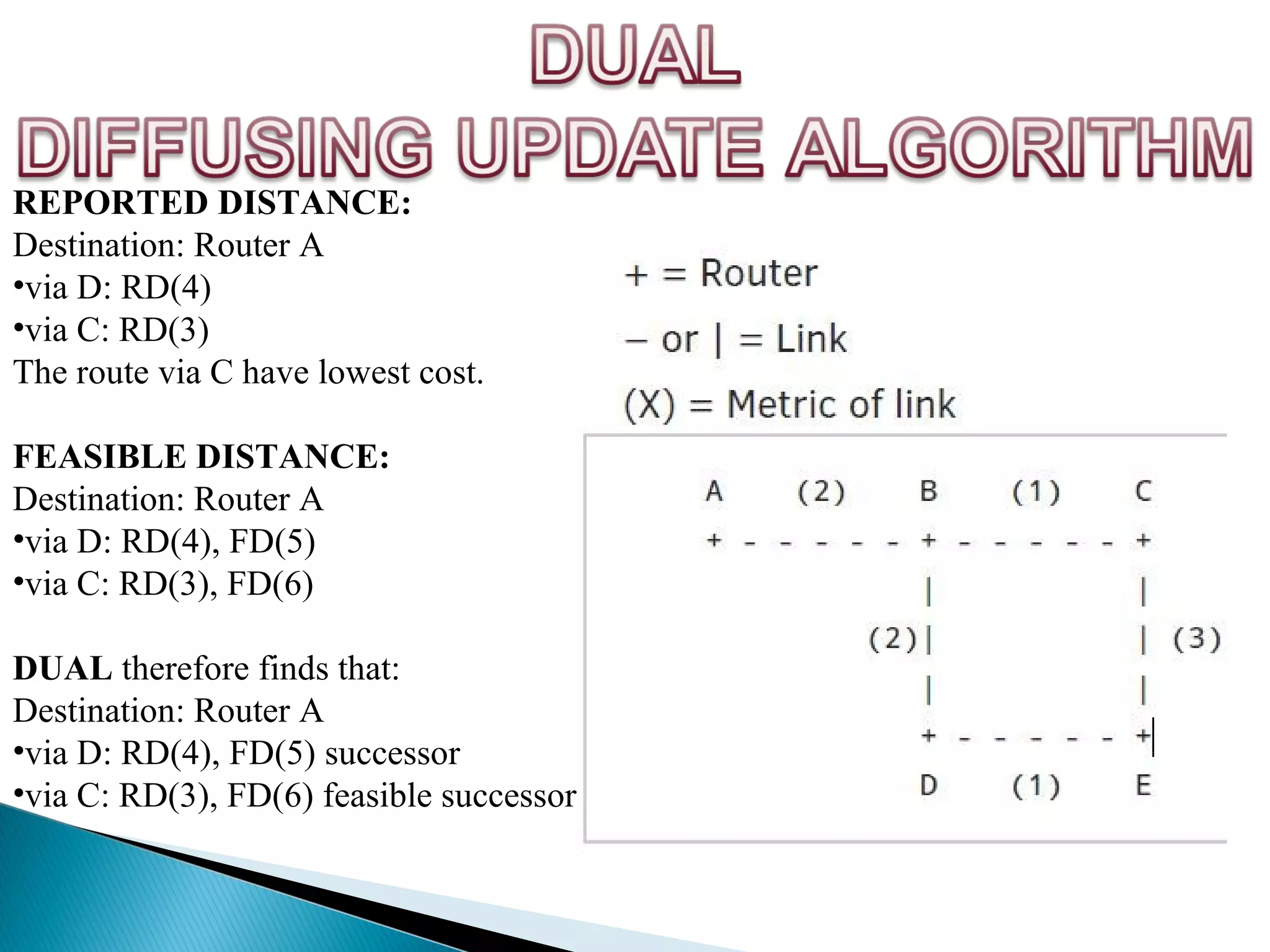
This document provides information on computer networks and routing protocols. It discusses advantages and problems of computer networks. It then describes the Enhanced Interior Gateway Routing Protocol (EIGRP) and some of its key features like security, congestion handling, efficiency, and support for IPv4 and IPv6. It also discusses static and dynamic routing, different routing metrics, and compares EIGRP to other routing protocols like RIP, OSPF, and IS-IS.











![[1].Wikipedia. “Routing” http://en.m.wikipedia.org/wiki/Router_(computing). October
2014.
[2]. Sumitha J. “Routing Algorithms in Networks” Research Journal of Recent
Sciences Vol.3(ISC-2013), 1-3. February 2014.
[3]. B, Richard . "On a routing problem". Quarterly of Applied Mathematics 16: 87–90.
[4]. CISCO. “Enhanced Interior Gateway Routing Protocol”
http://www.cisco.com/c/en/us/support/docs/ip/ Interior Gateway Routing Protocol-
eigrp/16406-eigrp-toc.html. 2014
[5]. Wikipedia. “Adaptive Routing” http://en.m.wikipedia.org/wiki/Adaptive_routing.
October 2014.](https://image.slidesharecdn.com/harsh-eigrp-150614111414-lva1-app6892/75/Dynamic-Routing-All-Algorithms-Working-And-Basics-37-2048.jpg)