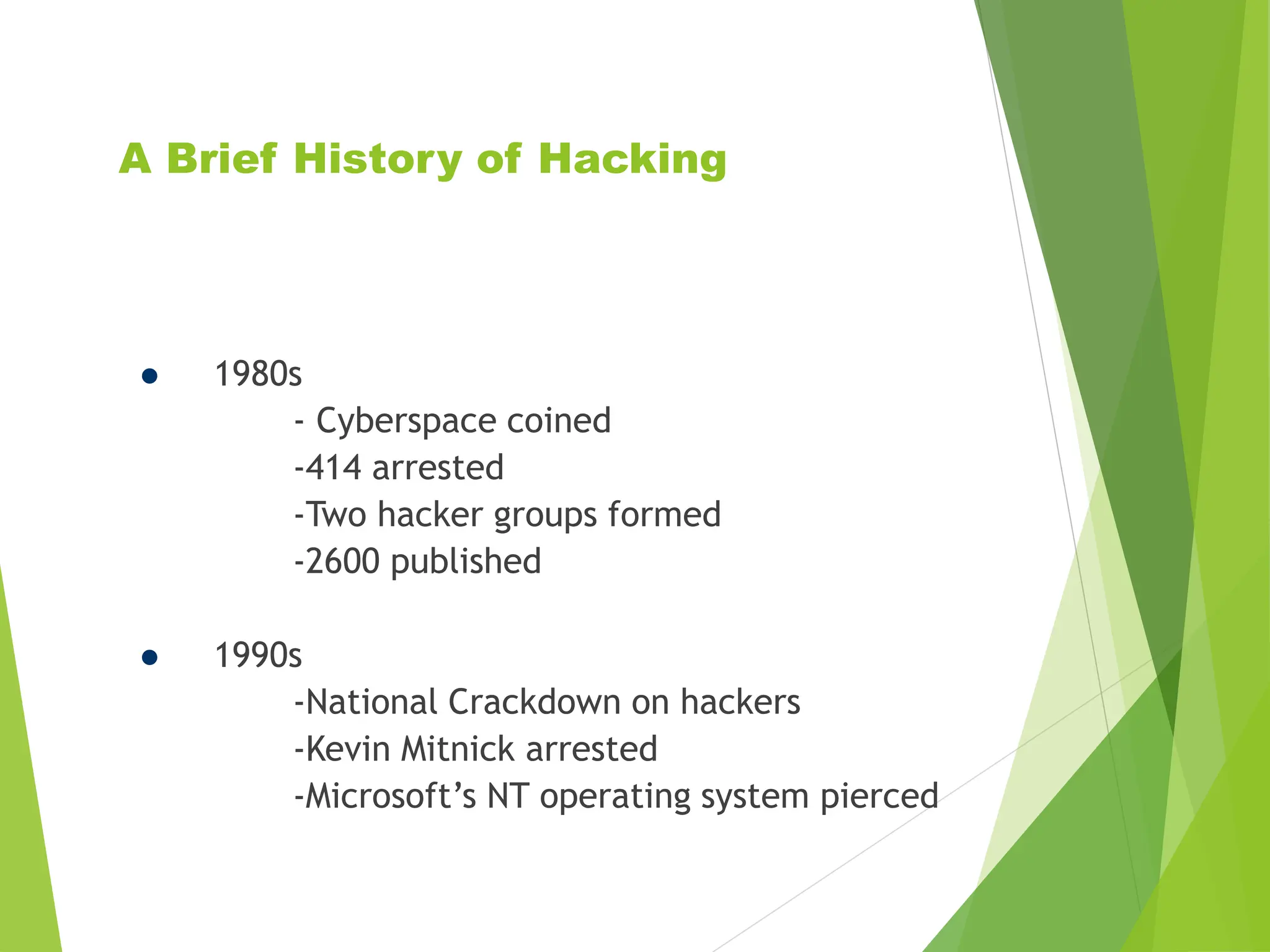
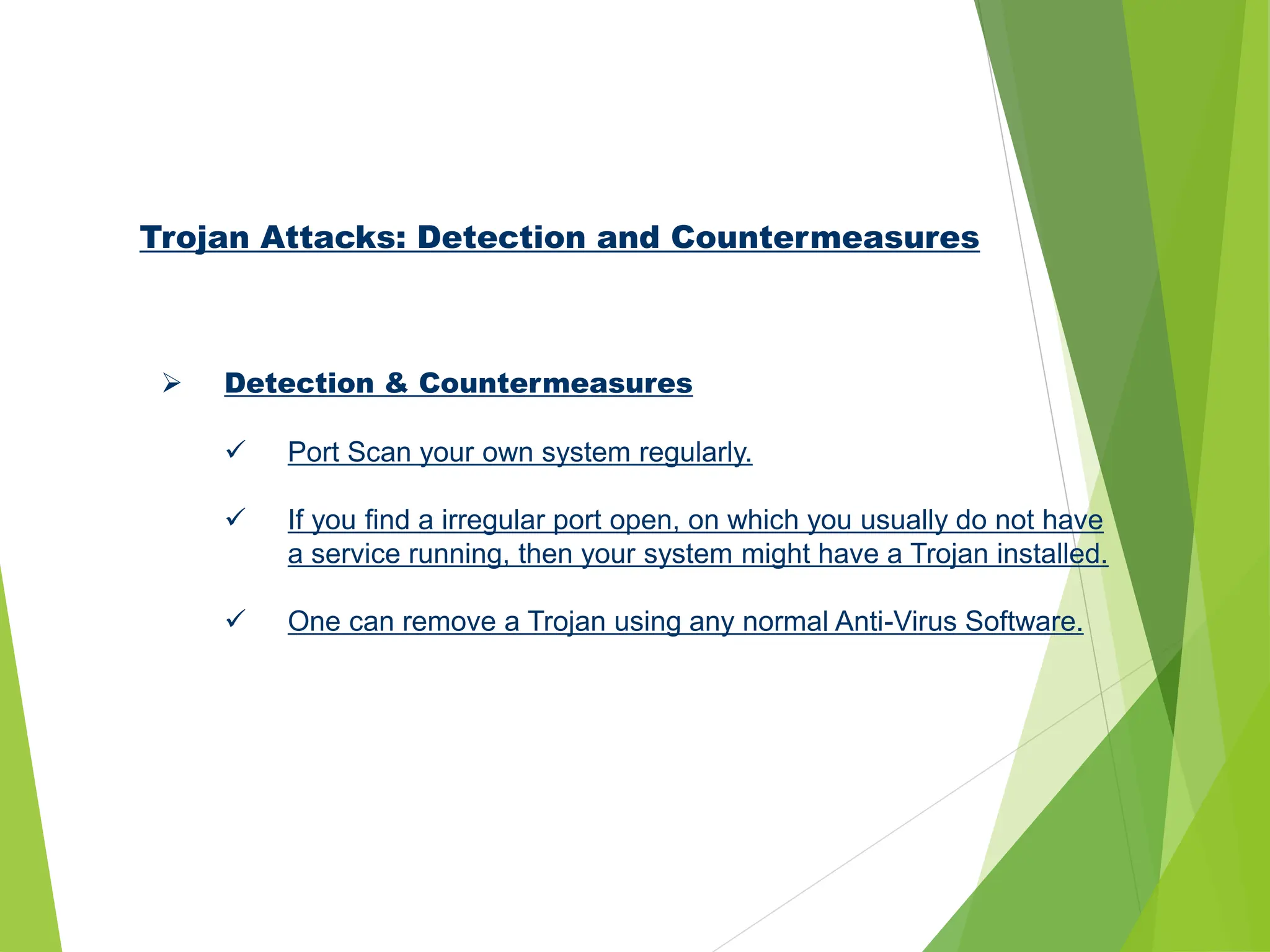
This document discusses ethical hacking and network security. It begins by defining hacking and providing a brief history of hacking from the 1980s to the 2000s. It then lists some famous hackers and describes basic hacking skills like programming and using Linux. The document outlines common hacking methods like finding target IP addresses through chat programs. It discusses various types of attacks like denial of service attacks and trojans. Finally, it lists modes of ethical hacking and topics covered by the Ec-Council on the subject.