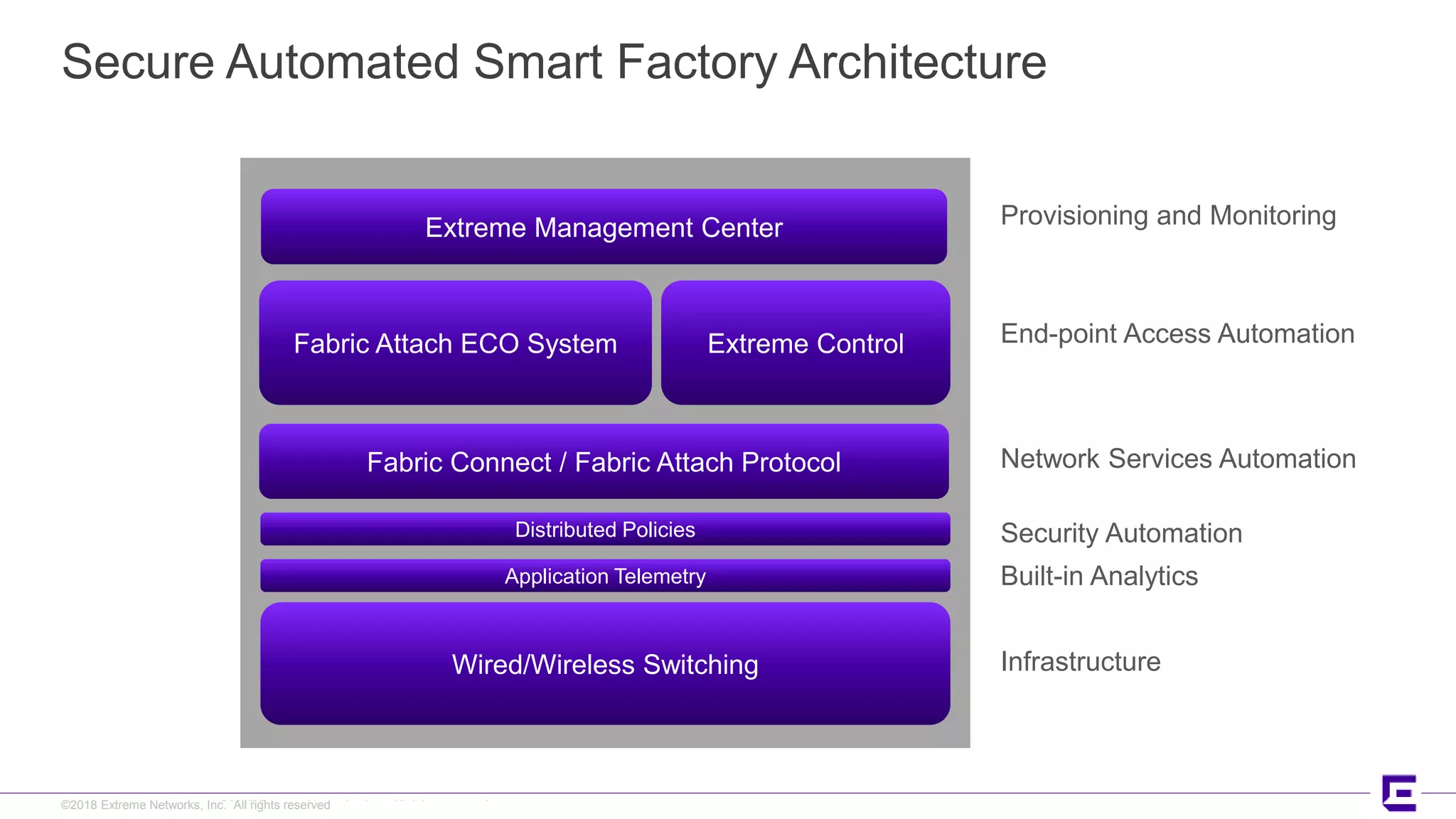
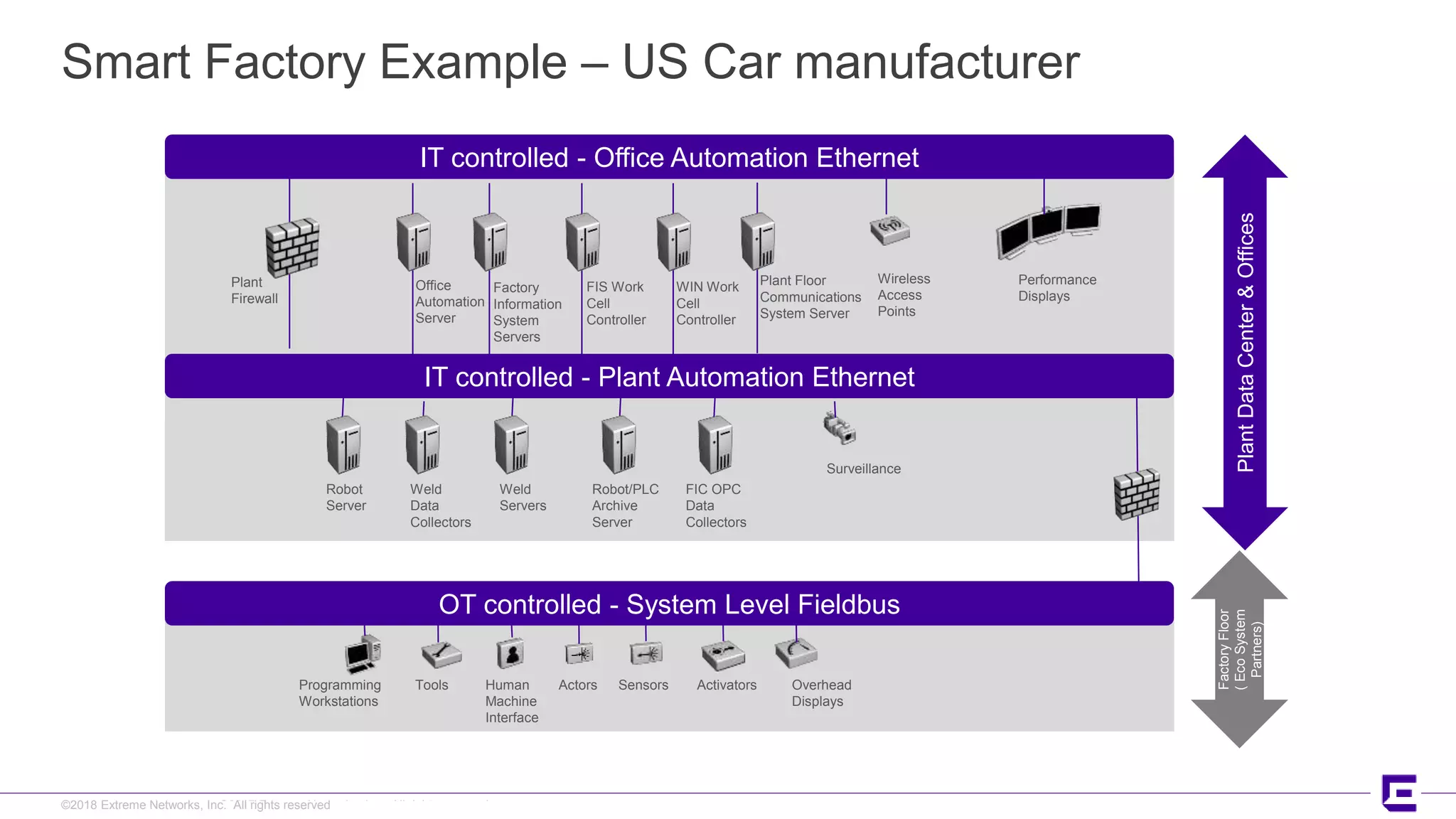
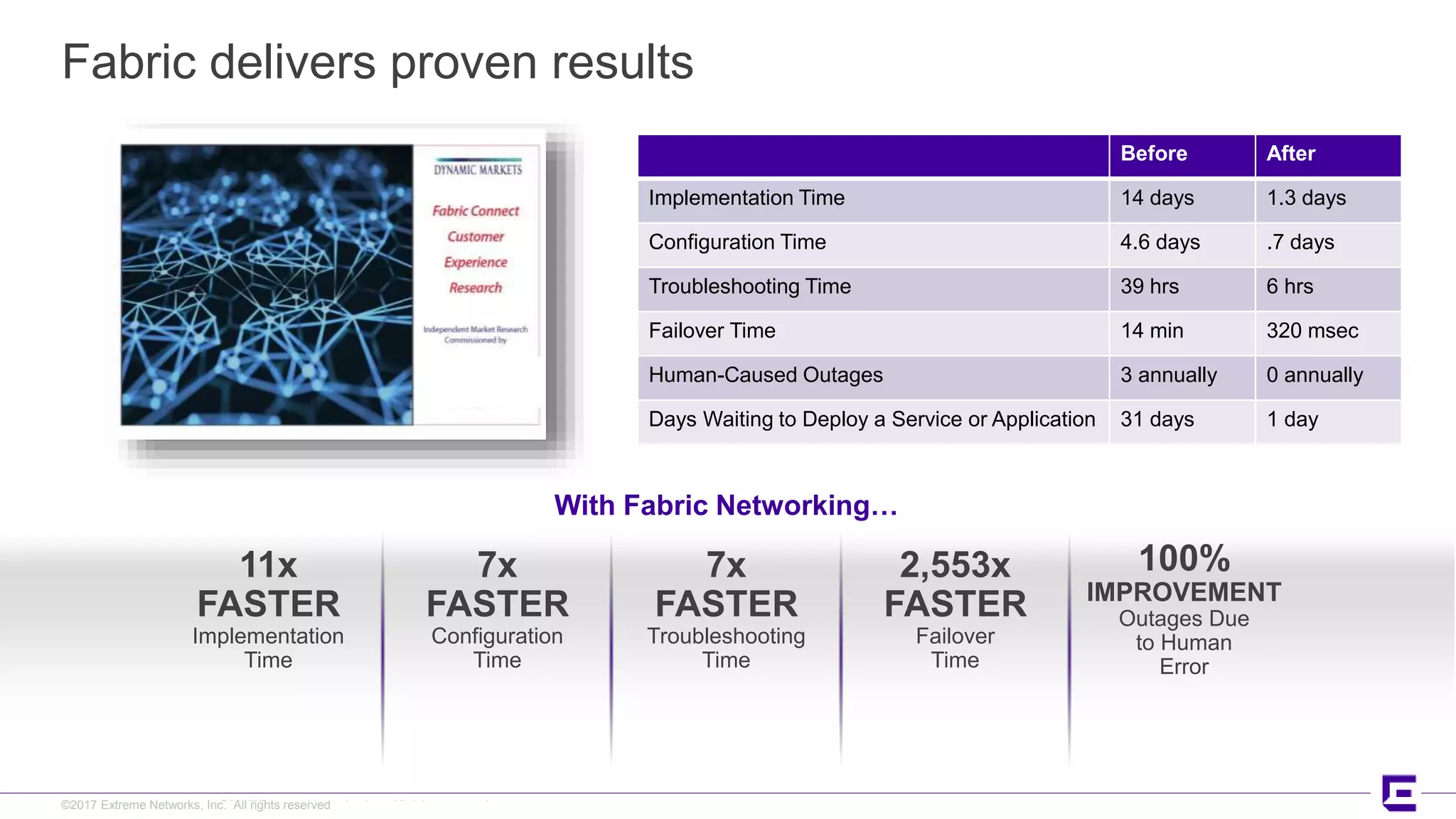
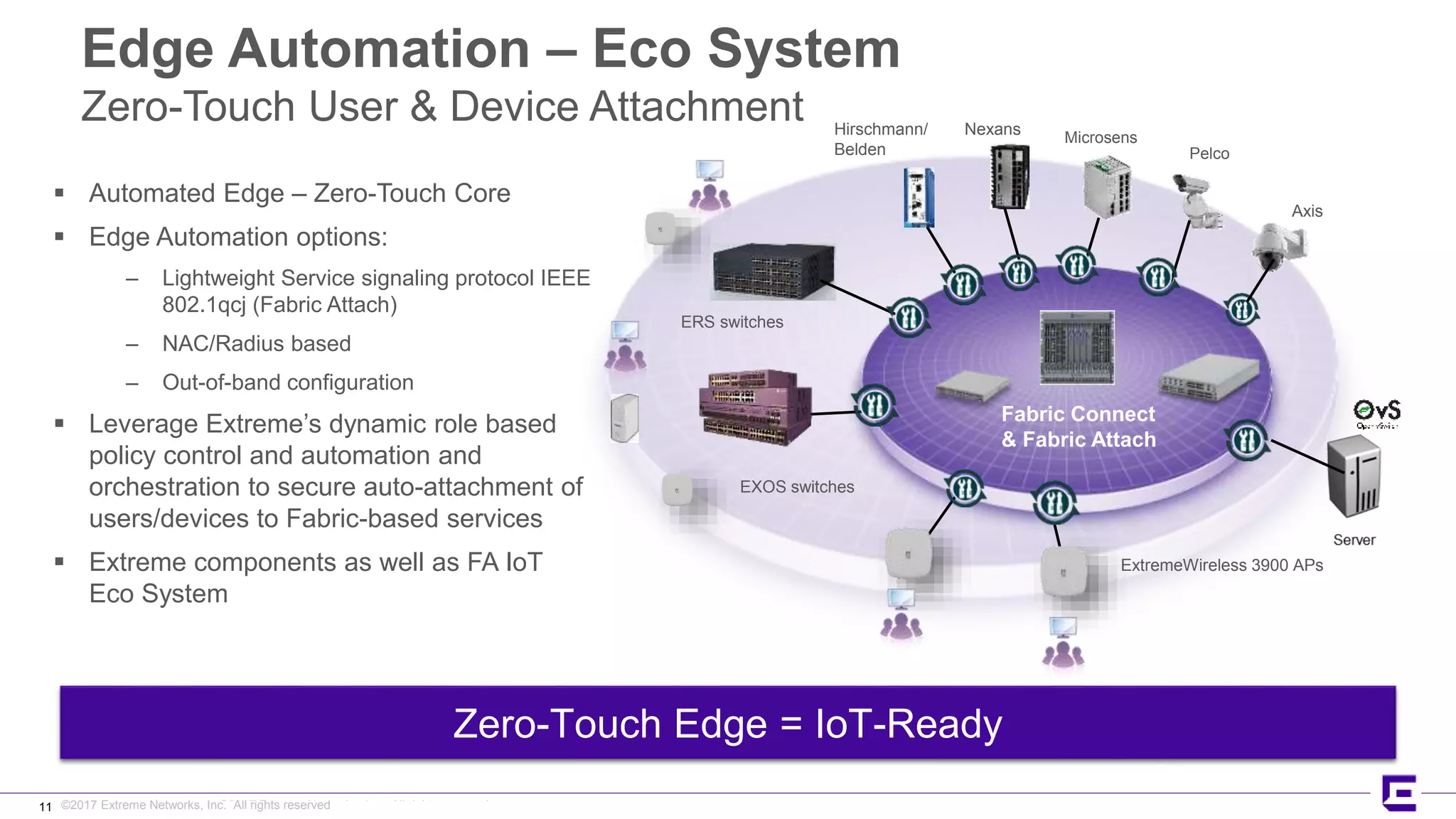
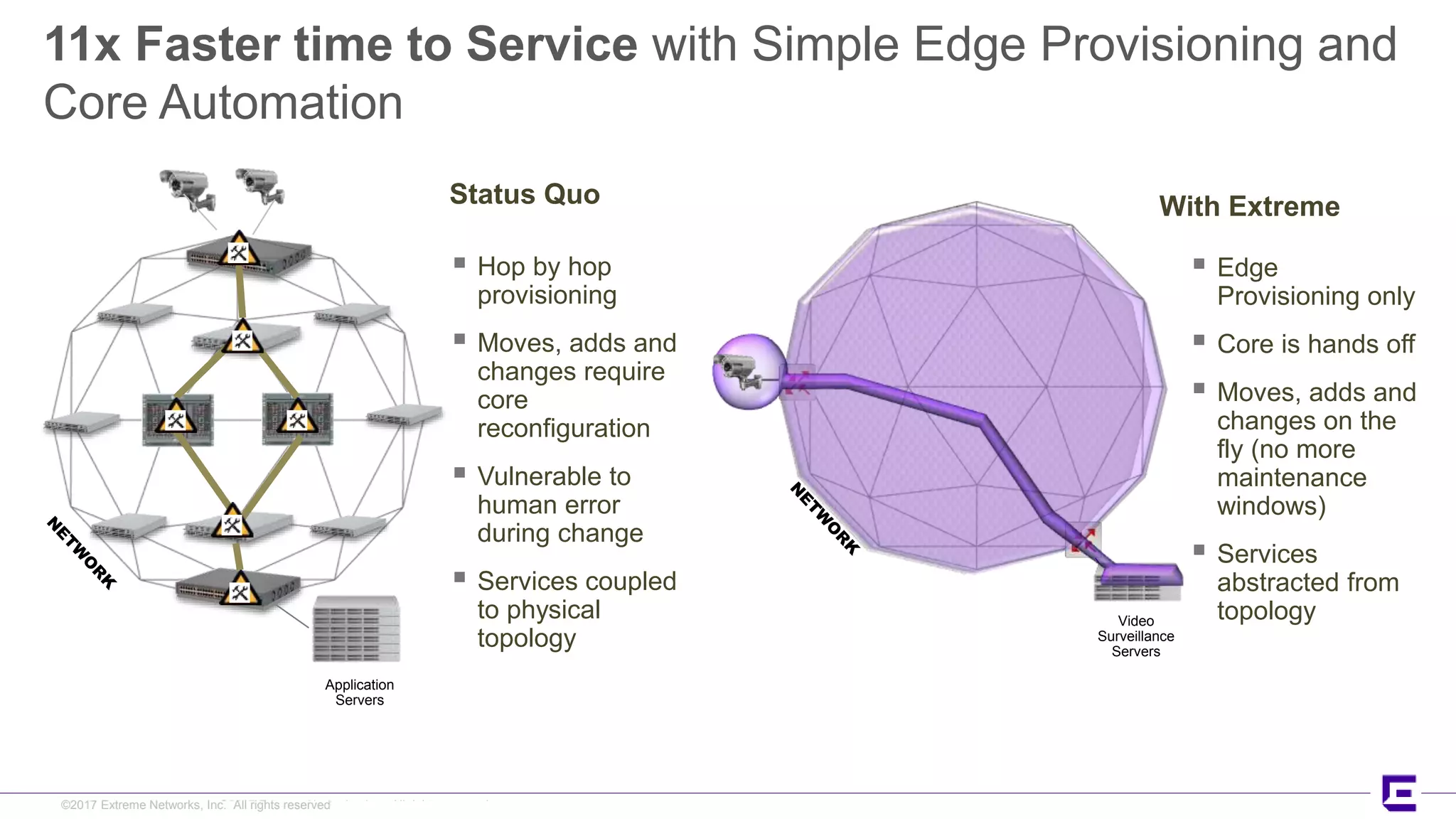
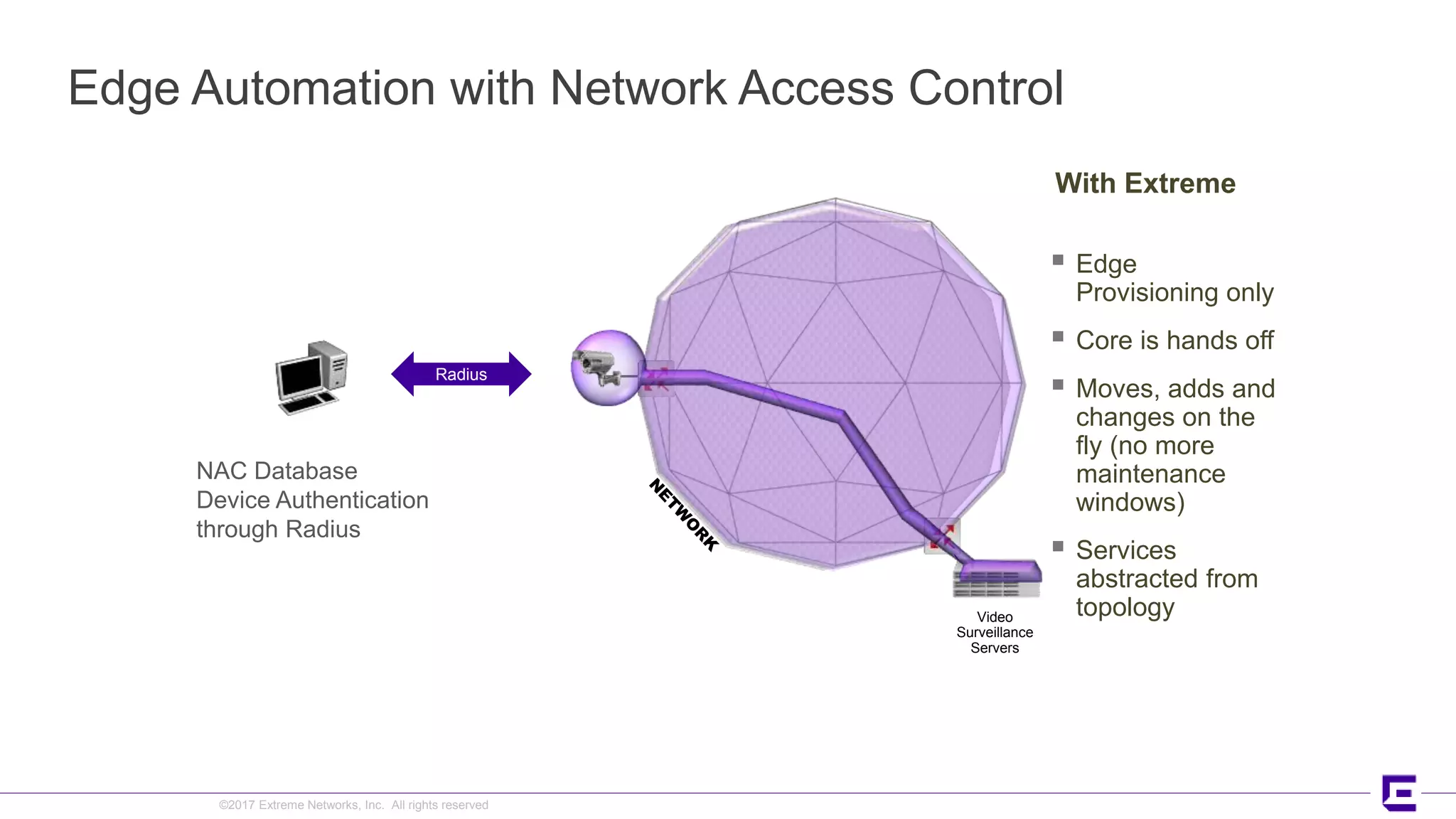
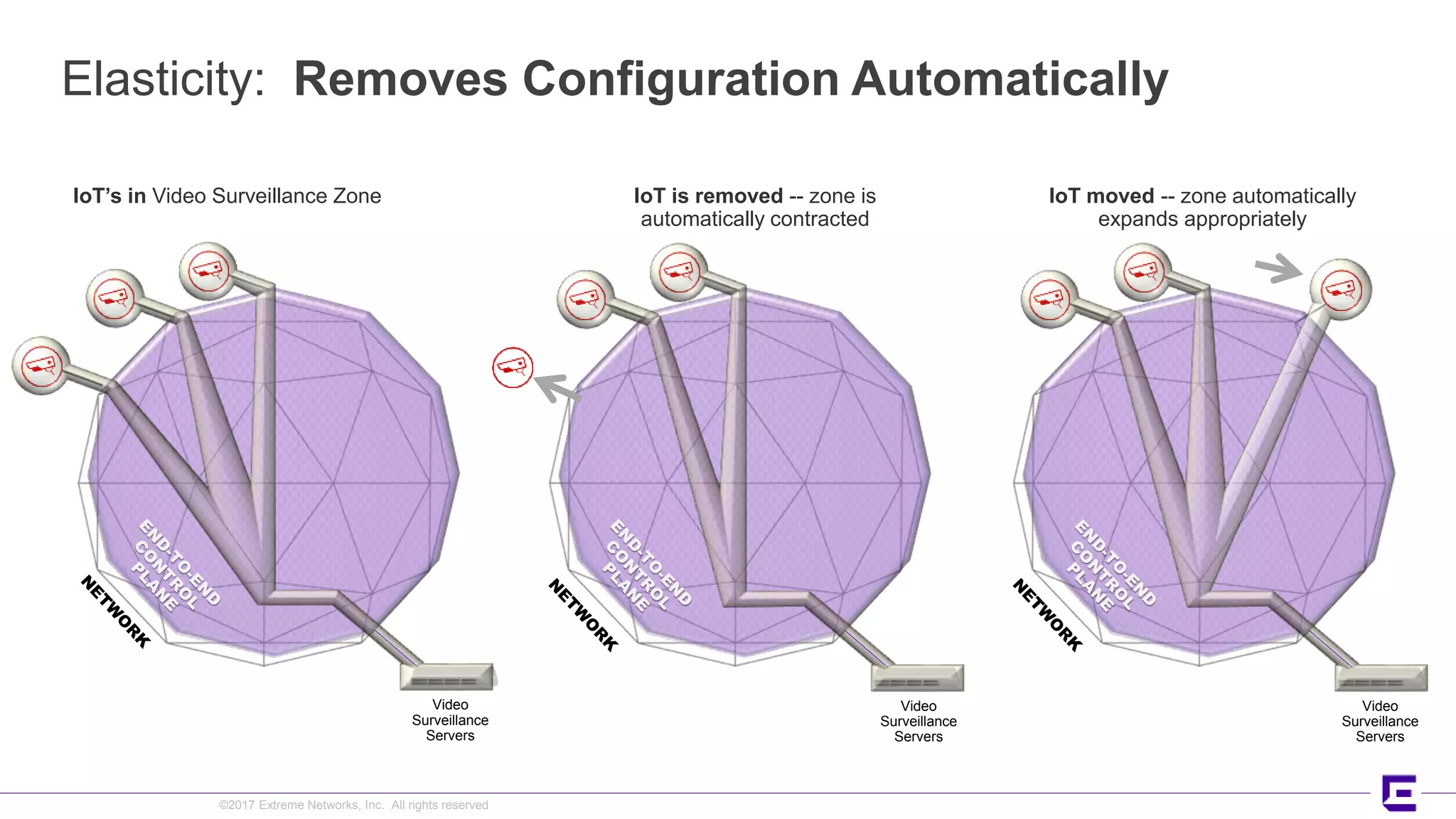
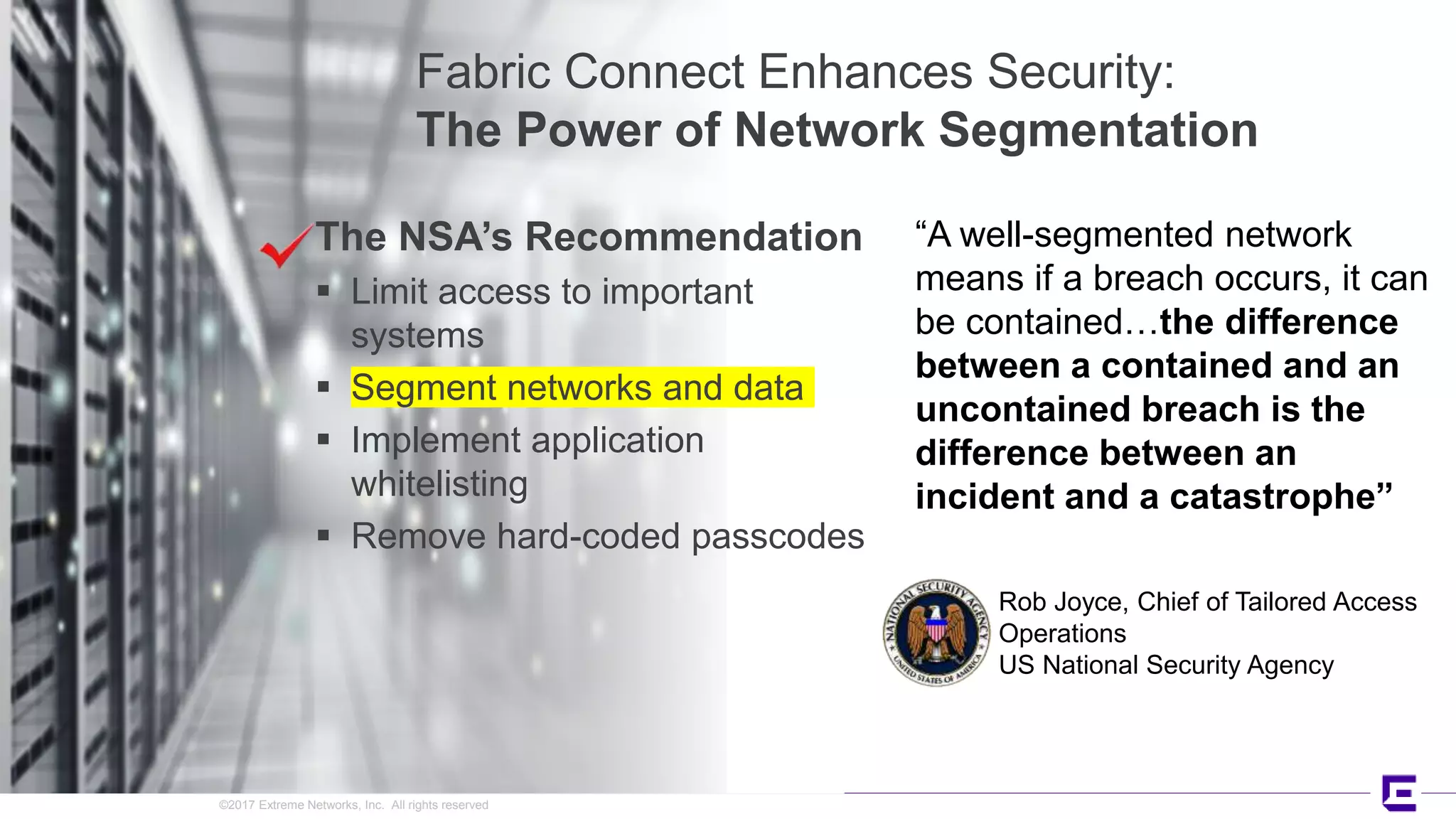
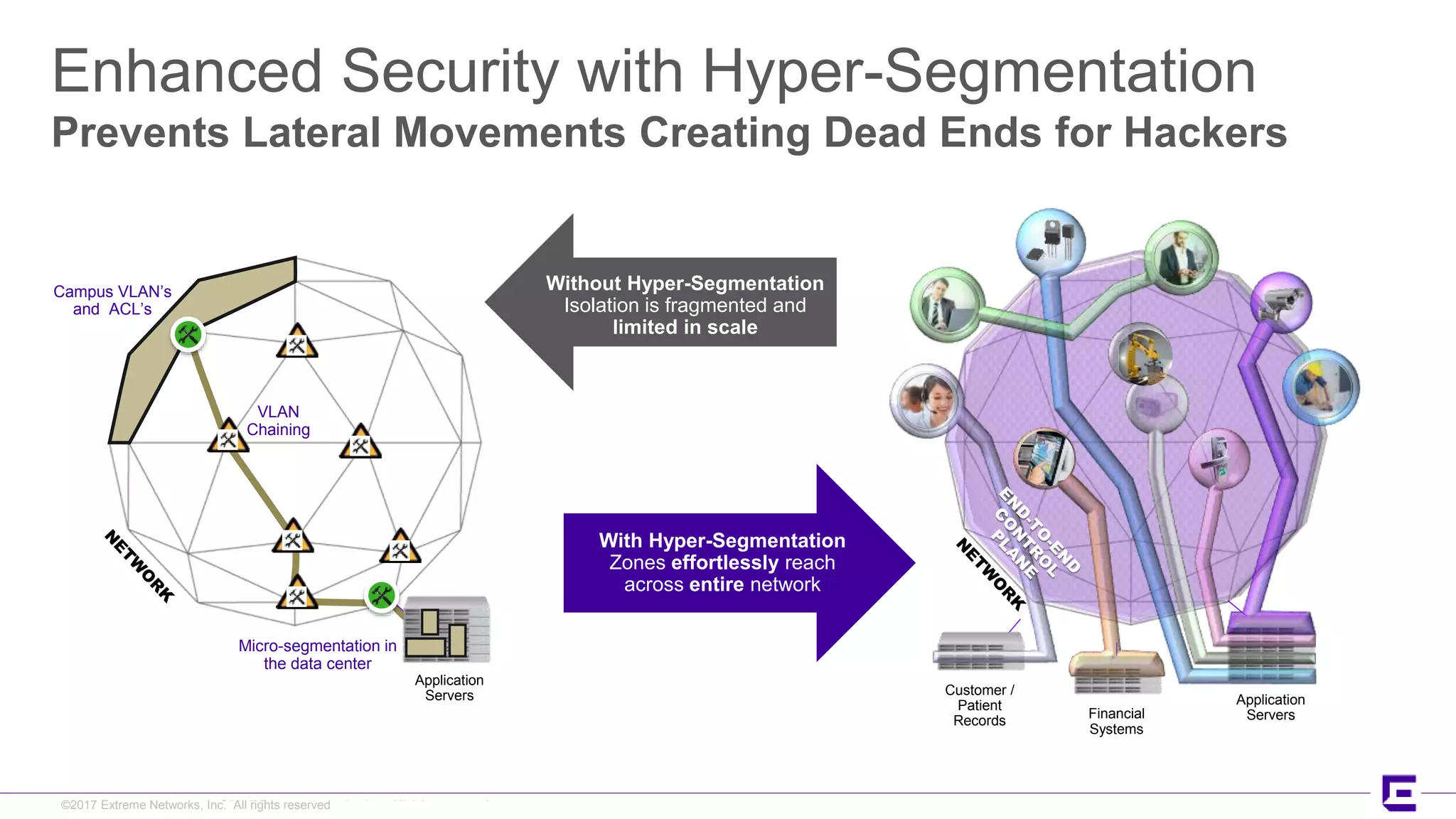
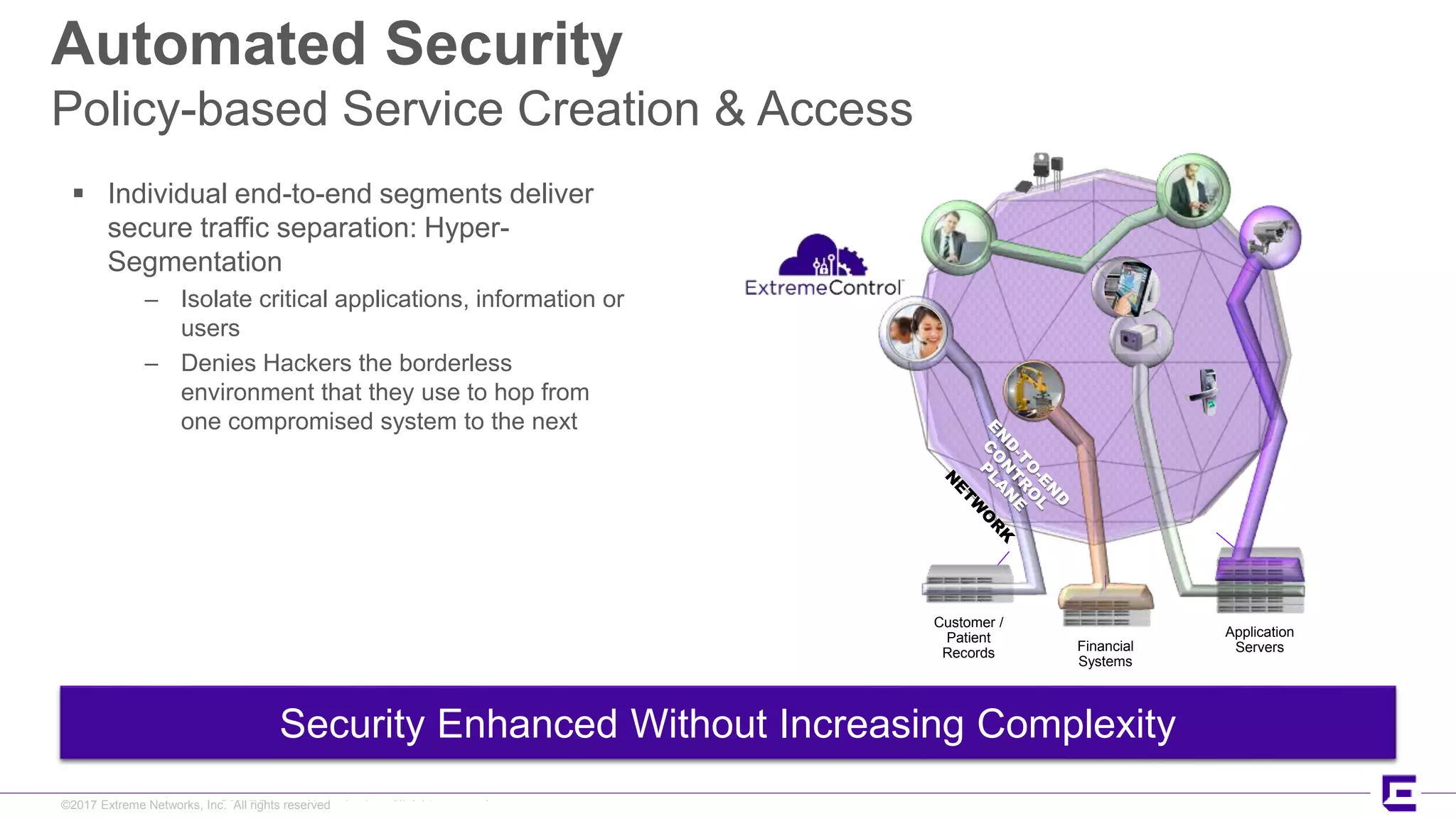
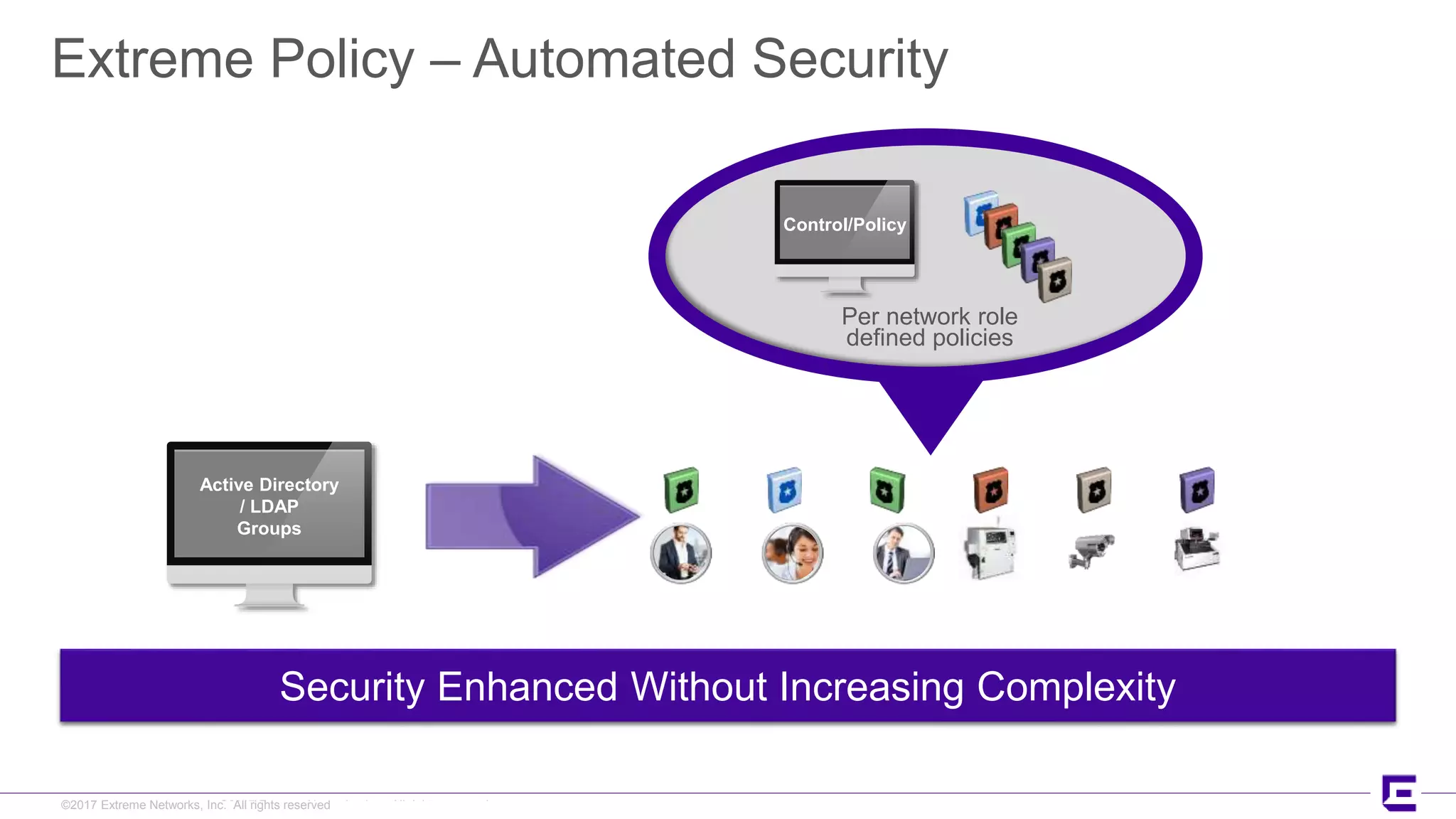
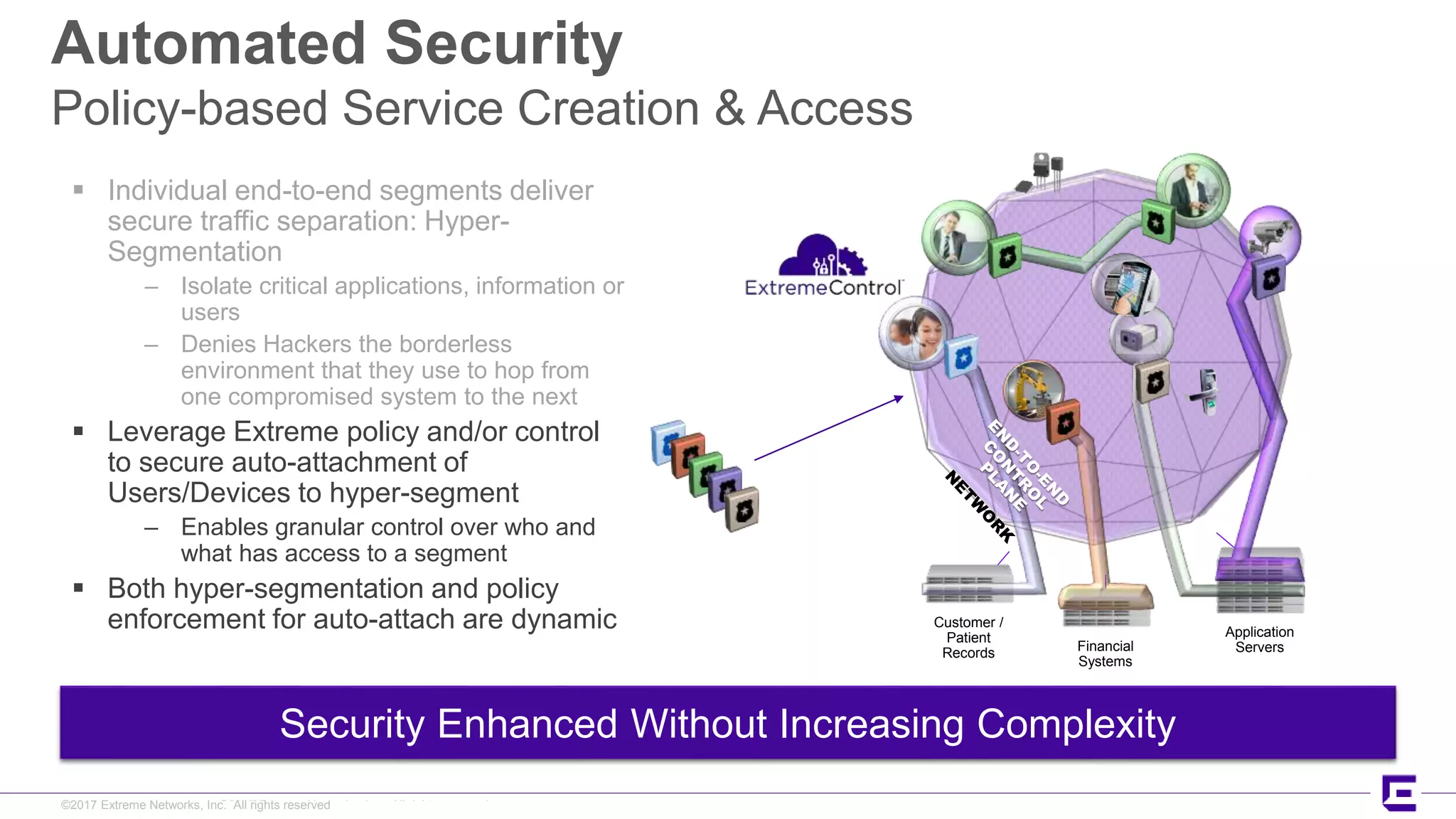
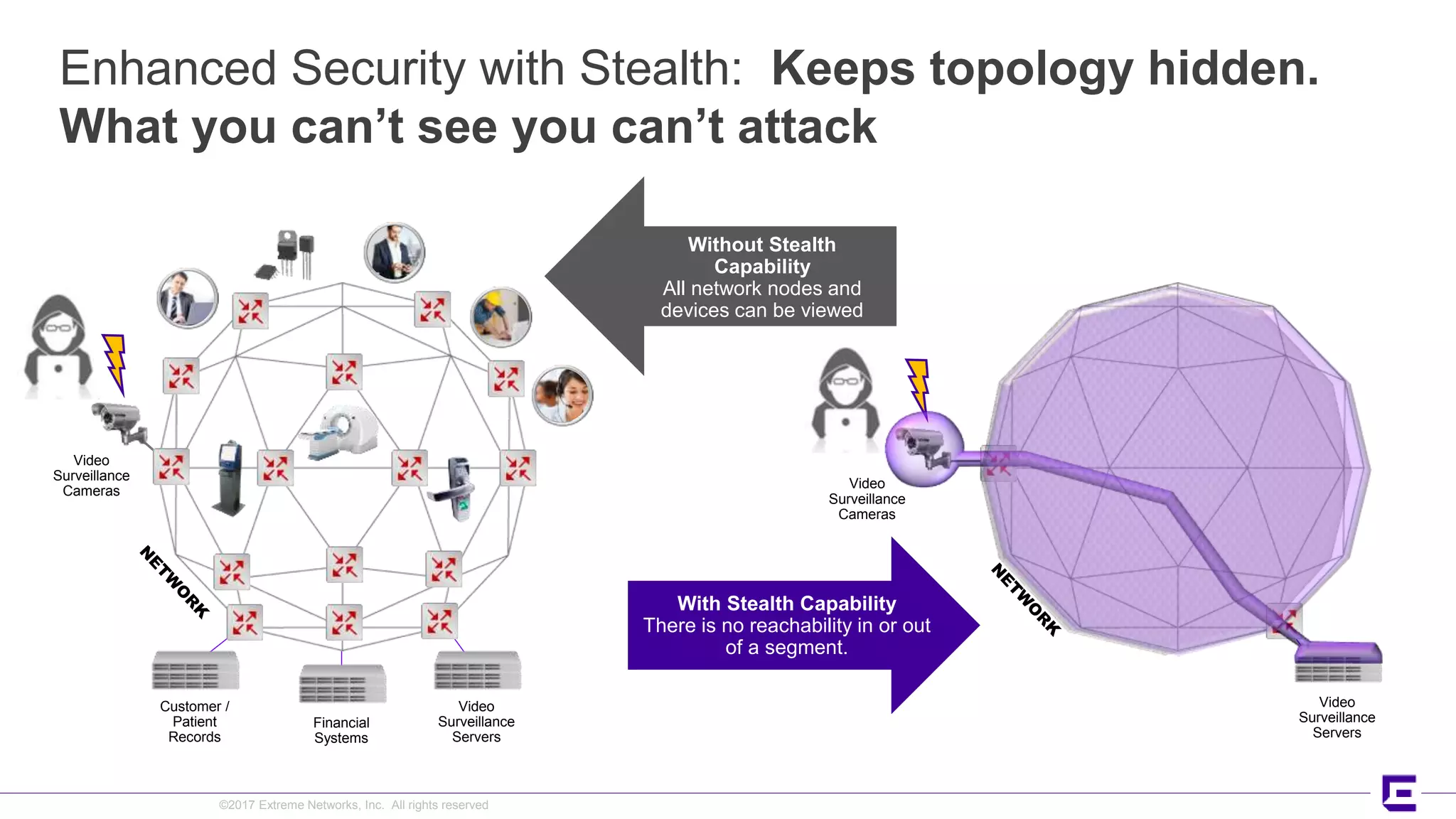
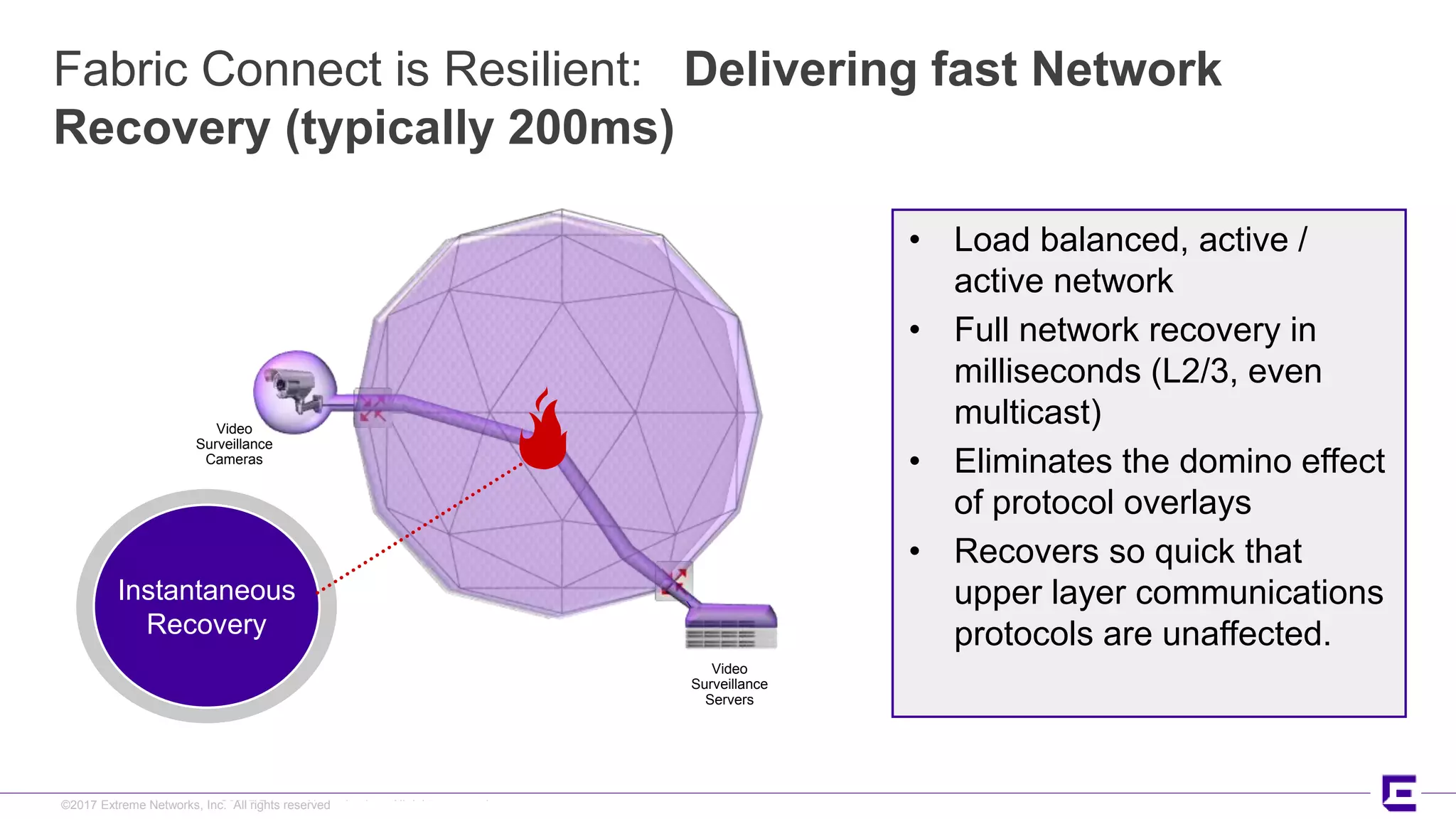
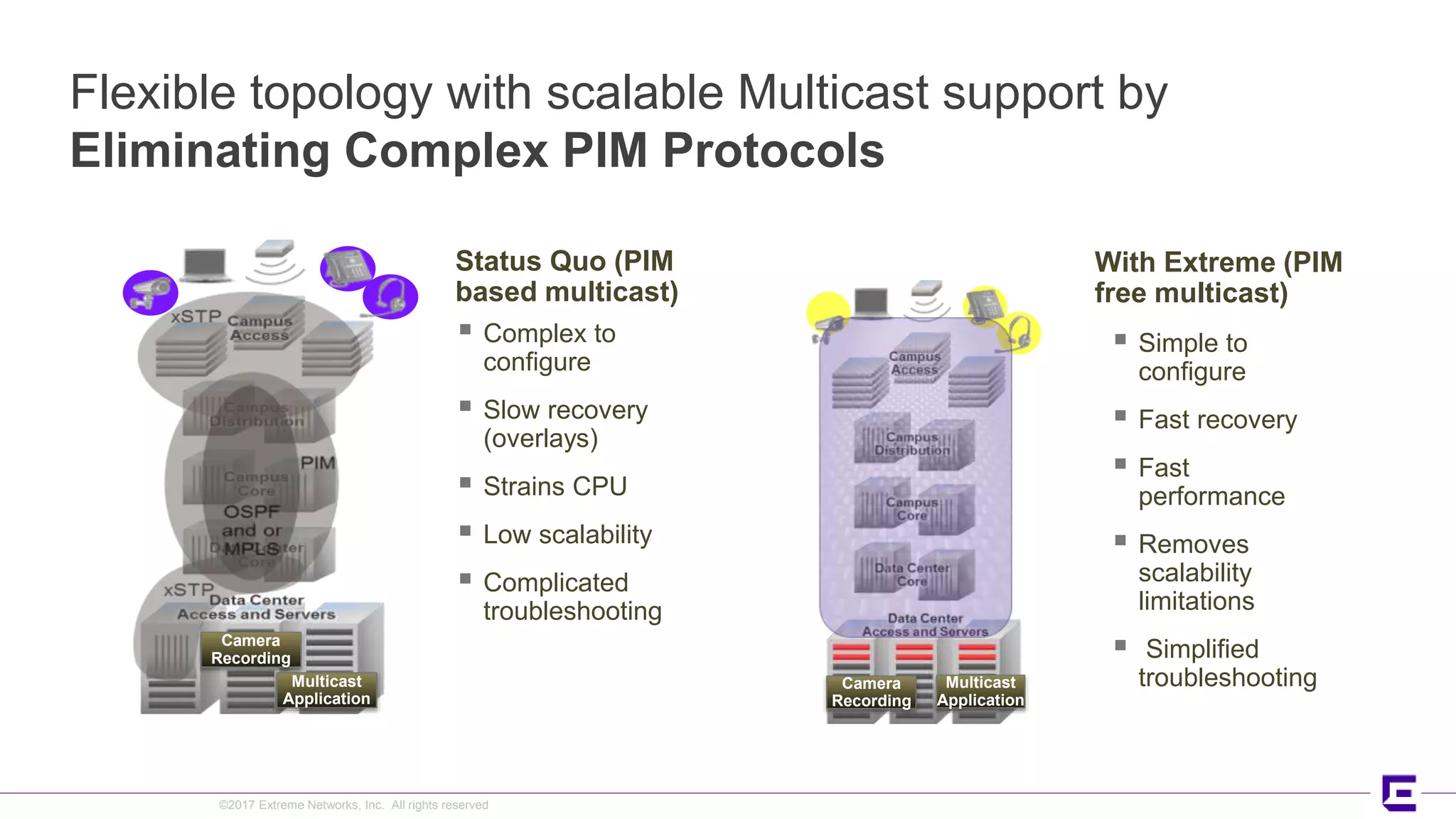
This document discusses Extreme Networks' Secure Automated Smart Factory (SASF) solution. It provides an example of how SASF was implemented for a US car manufacturer to achieve fully automated operations, network robustness, flexible network topology, and highly secure segmentation. The SASF architecture provides infrastructure switching, network services automation, endpoint access automation, and distributed security policies. It allows for rapid service provisioning, reduced change windows, and isolation of network segments.