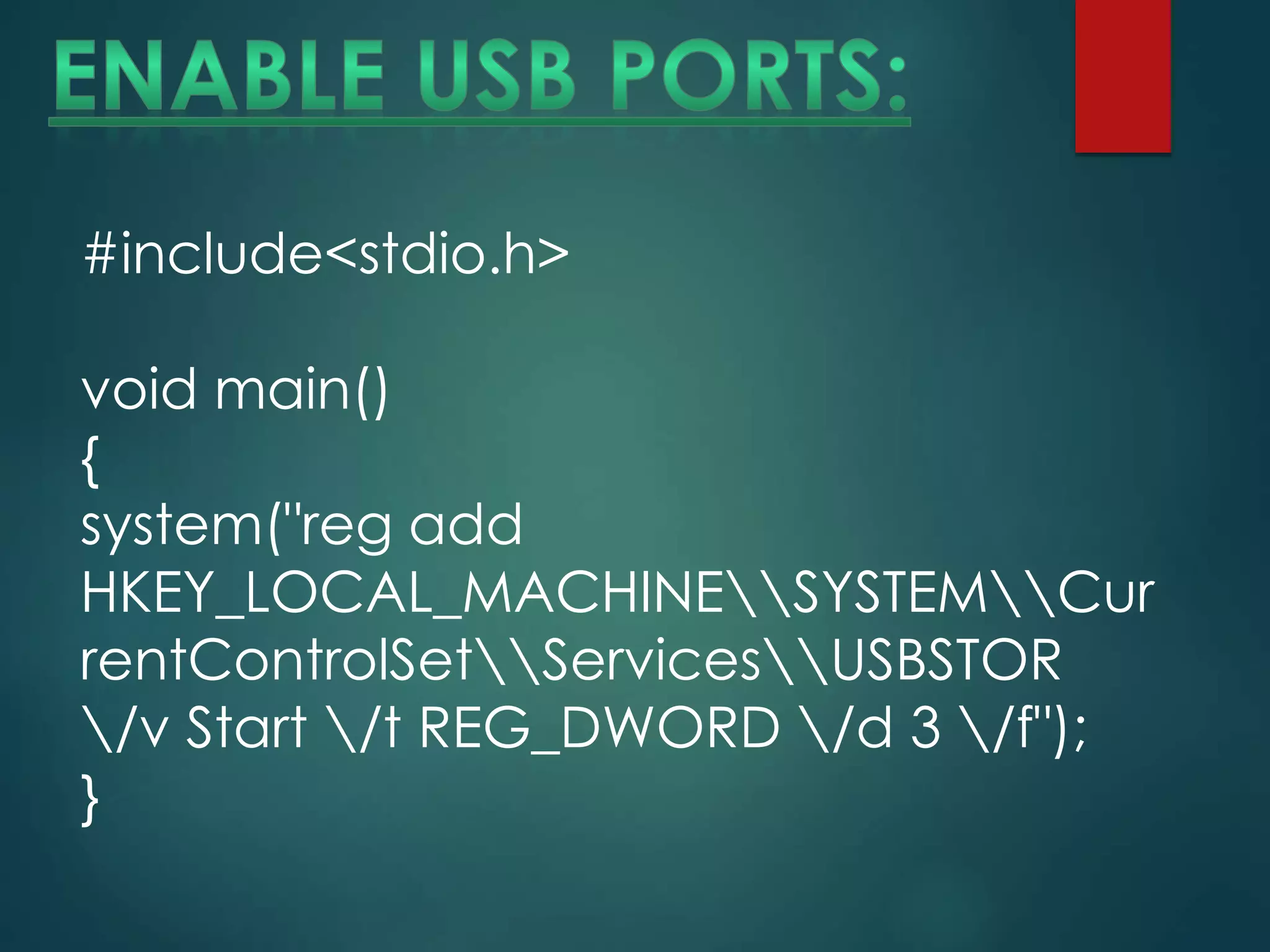
Hacking originally referred to constructive work by MIT engineers in the 1960s and involves good intentions in technical experimentation. Key skills for hacking include programming and familiarity with open-source UNIX systems, particularly Linux. Malicious hacking, or cracking, involves unauthorized access and harmful software like logic bombs, viruses, and worms that can damage and replicate without human intervention.