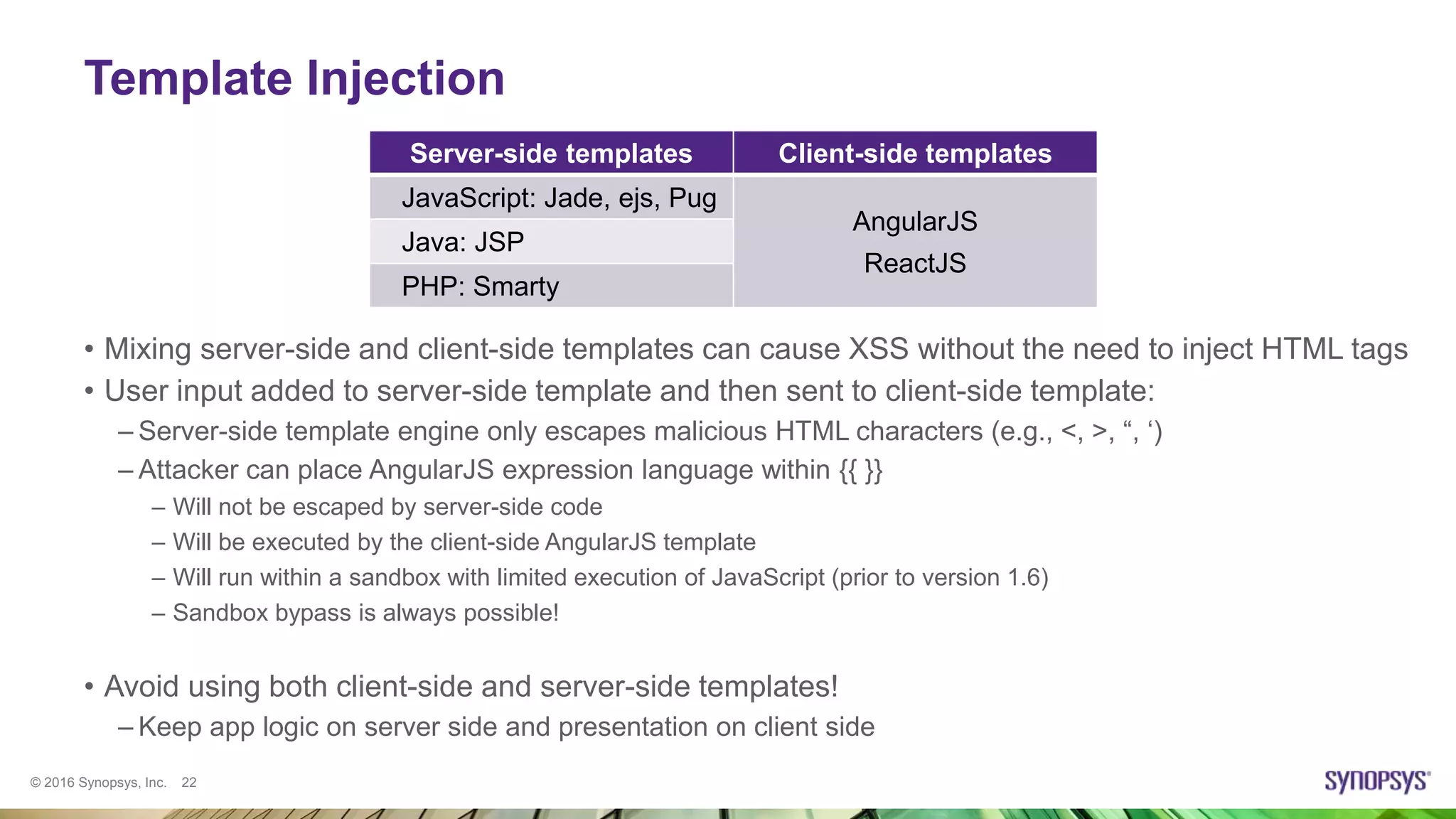
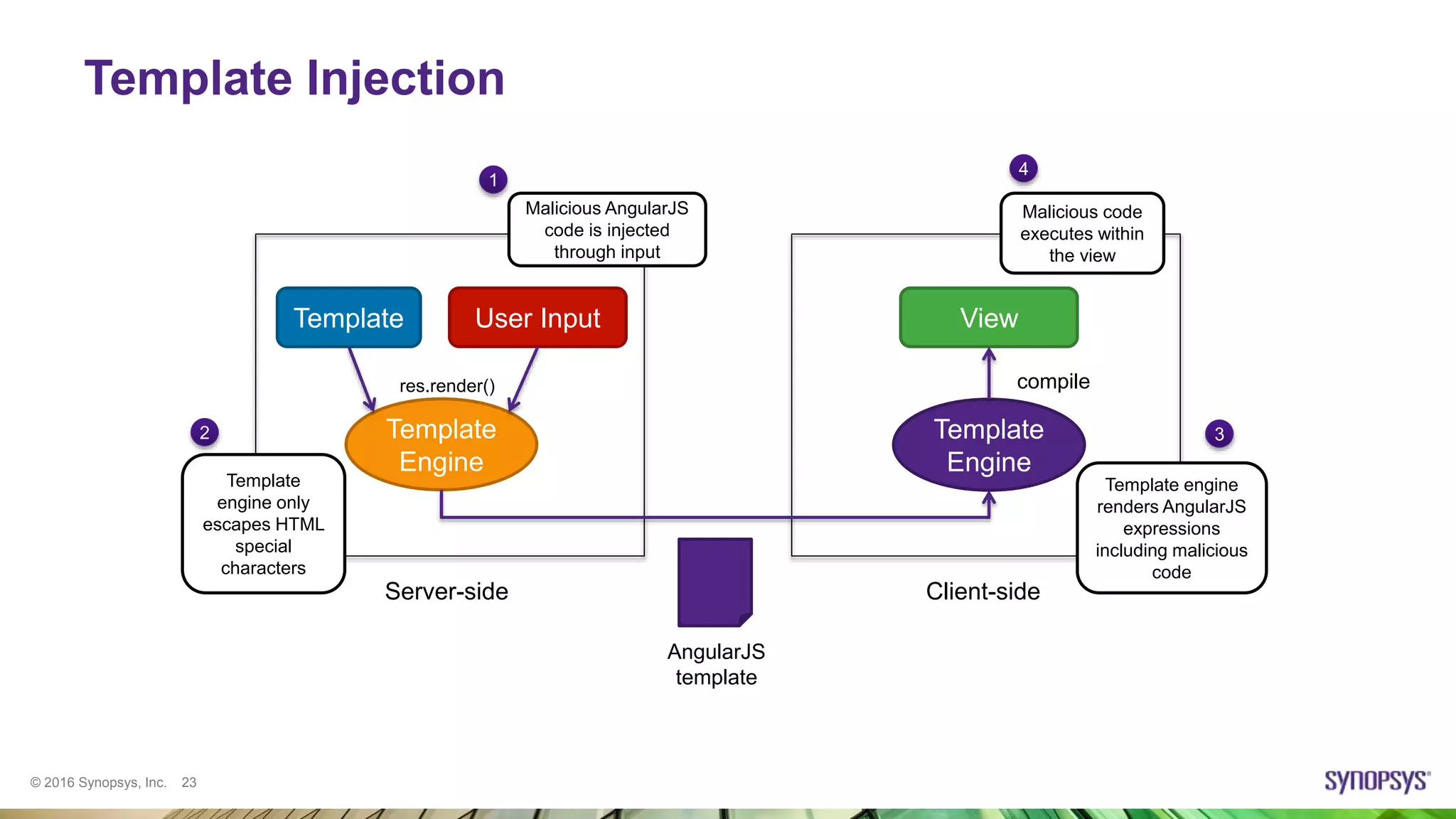
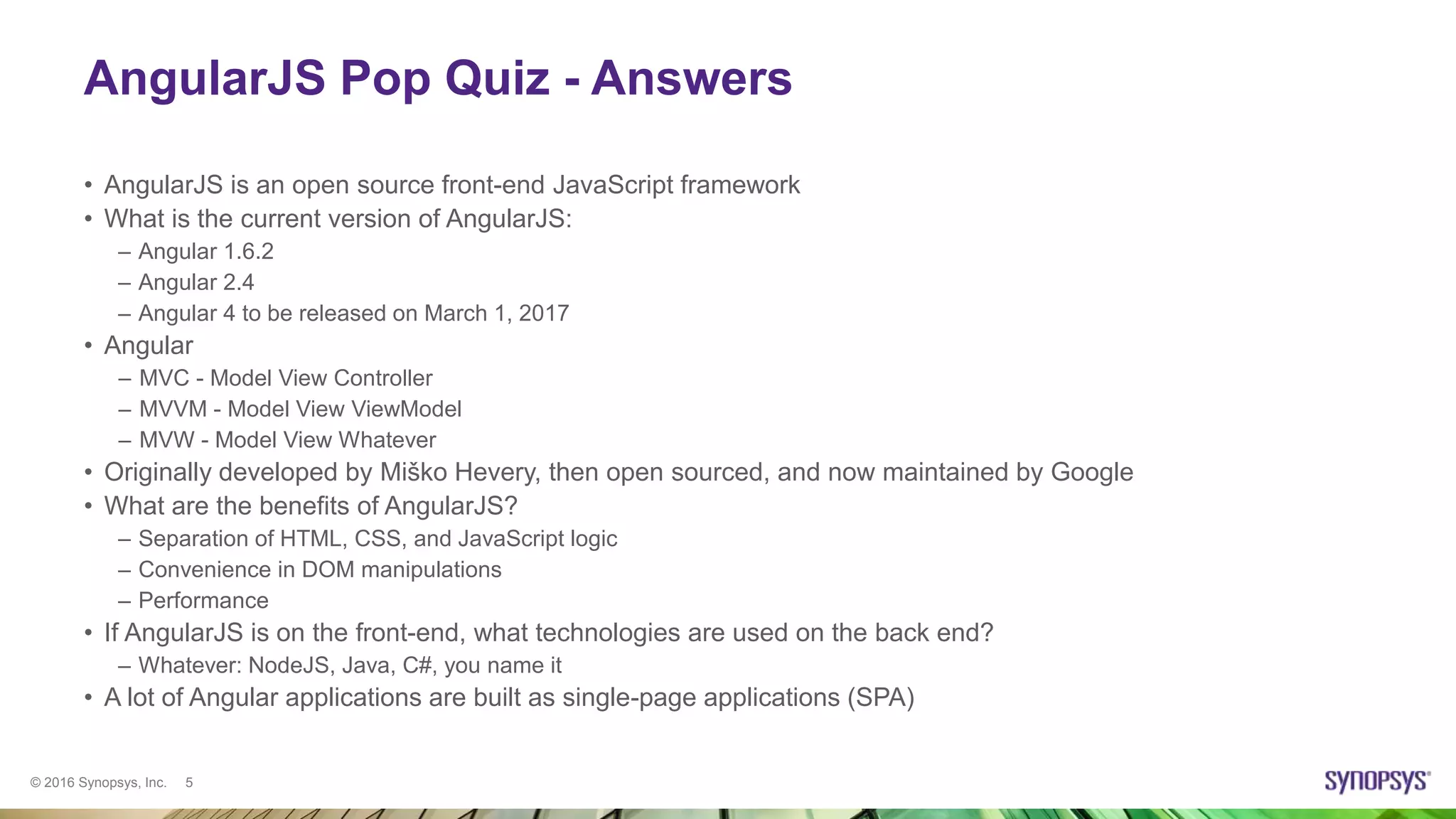
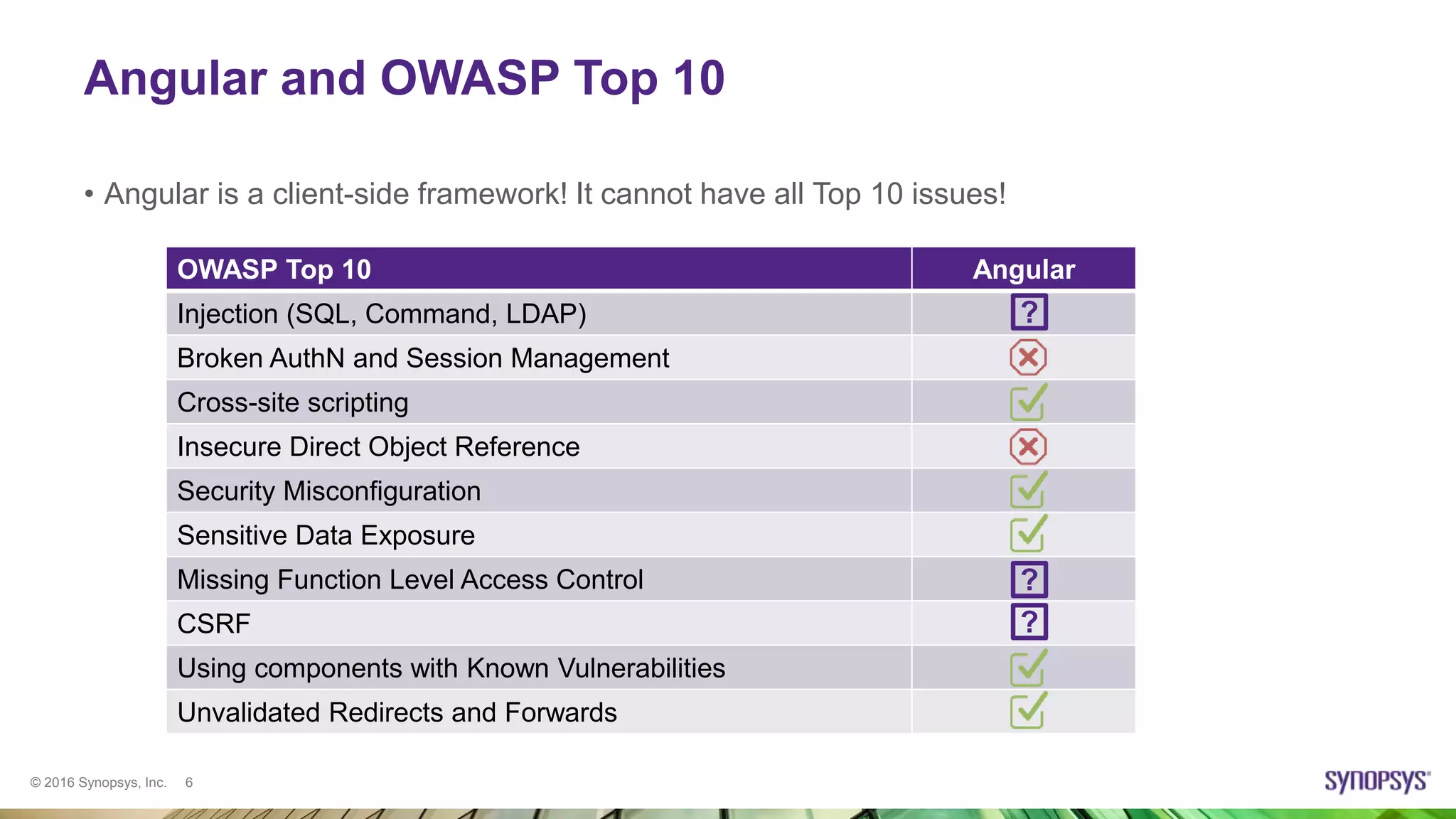
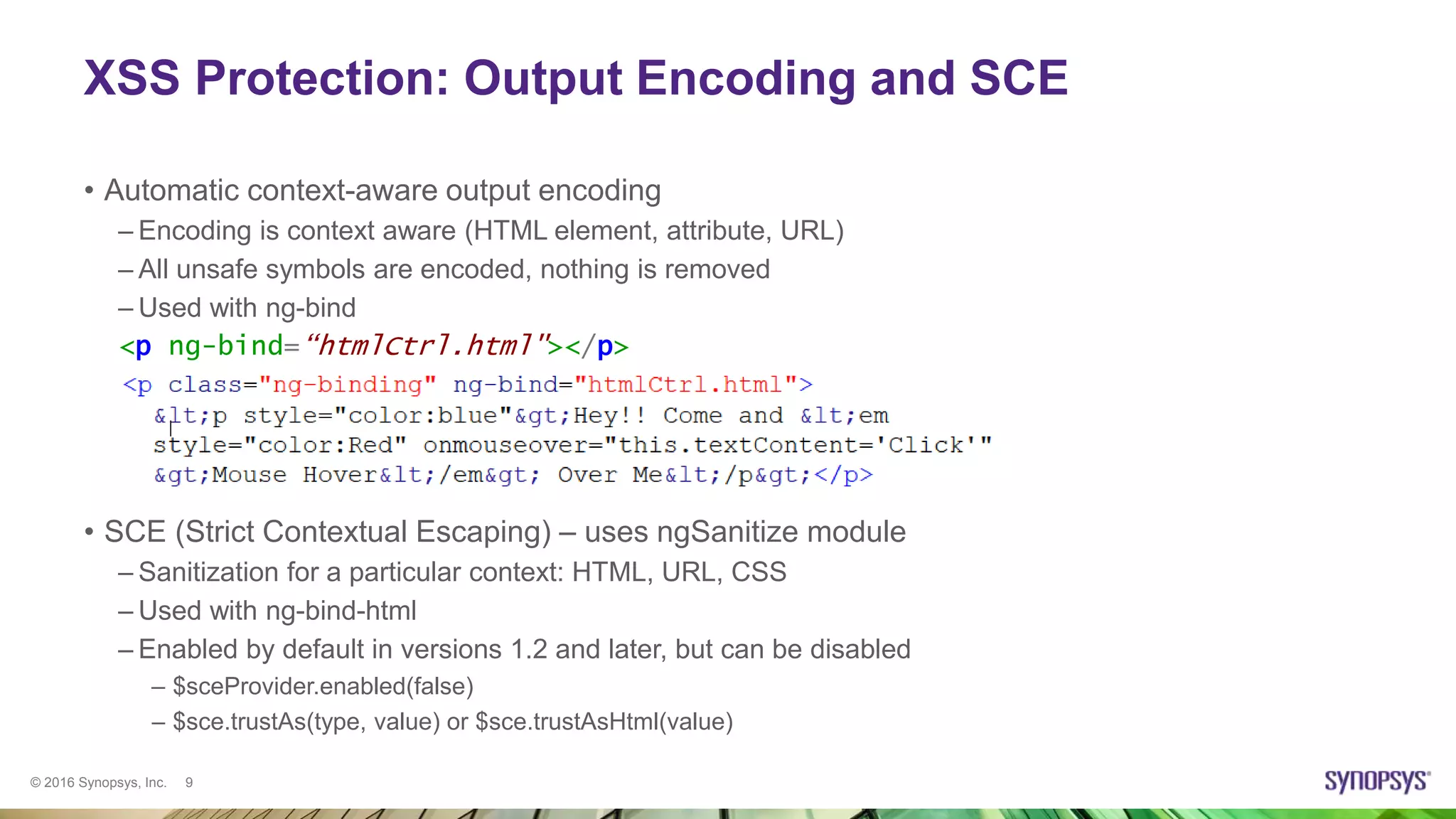
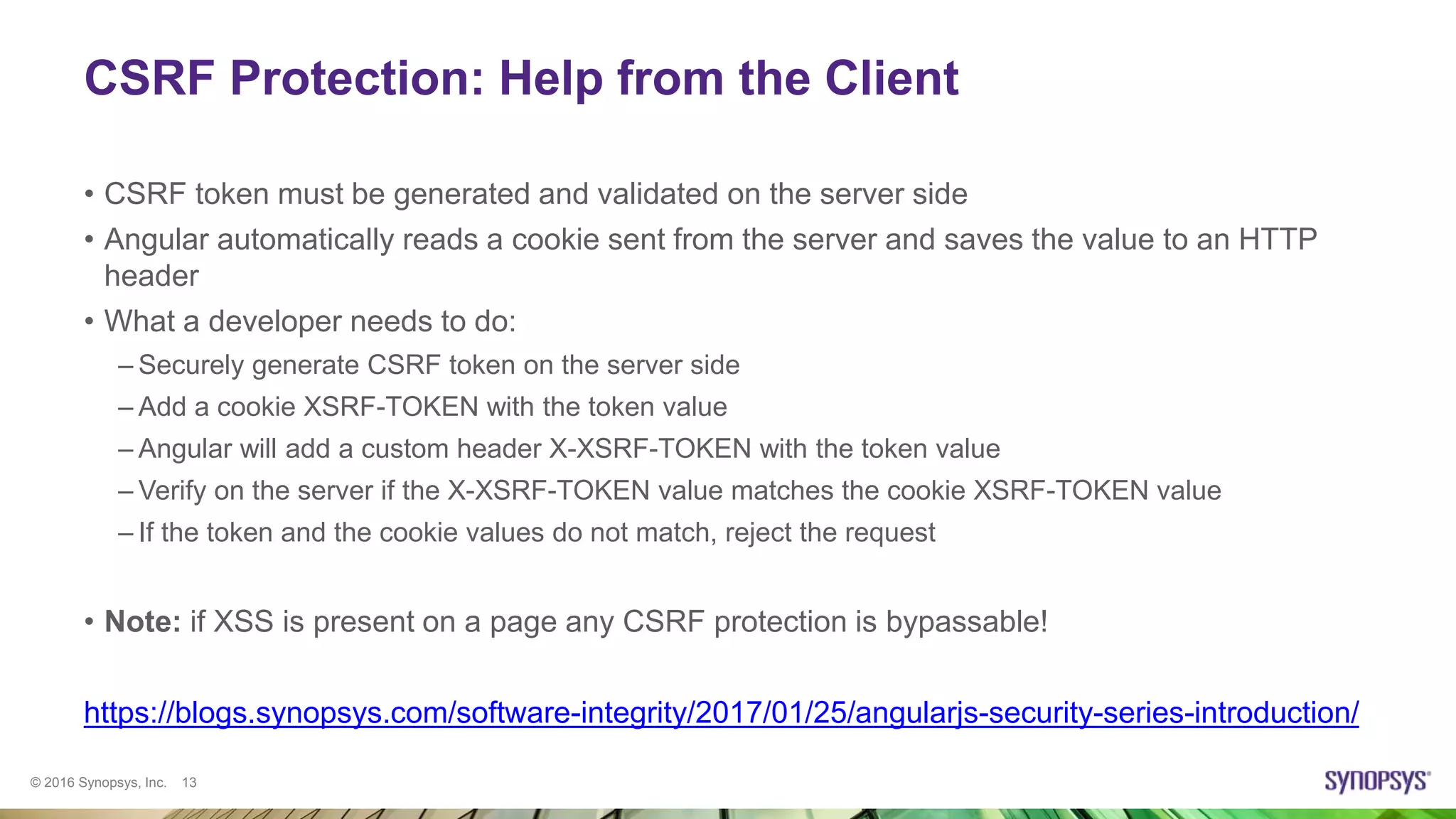
Ksenia Peguero gave a presentation on AngularJS security. She discussed how AngularJS addresses some common vulnerabilities like XSS and CSRF. However, she noted some issues remain, such as DOM-XSS vulnerabilities in Angular elements and third-party plugins. She demonstrated template injection and sandbox bypass issues. Her conclusion was that AngularJS provides good security when used properly, but one should not rely on the sandbox and should avoid mixing server-side and client-side templates. She advised checking plugins for issues and using the latest versions.








![© 2016 Synopsys, Inc. 12
XSS Protection: Sandbox? Not Really
• All versions of Angular up to 1.6 executed Angular Expressions in a sandbox
• Angular Expressions are evaluated against the scope object
https://www.youtube.com/watch?v=Hium4FVAR5A&index=4&list=PLhixgUqwRTjwJTIkNopKuGLk3P
m9Ri1sF
• Every version had a sandbox escape “vulnerability”
• Sandbox was never considered to protect code for security reasons
• What does it mean “to escape a sandbox”?
– Directly manipulate the DOM
– Execute plain old vanilla JavaScript
• Example payload:
{{x = {'y':''.constructor.prototype}; x['y'].charAt=[].join;$eval('x=alert(1)');}}
• As of Angular 1.6 sandbox has been completely removed
https://blogs.synopsys.com/software-integrity/2016/12/28/angularjs-1-6-0-sandbox/](https://image.slidesharecdn.com/angularjssecurity-180629012746/75/How-Secure-Is-AngularJS-12-2048.jpg)

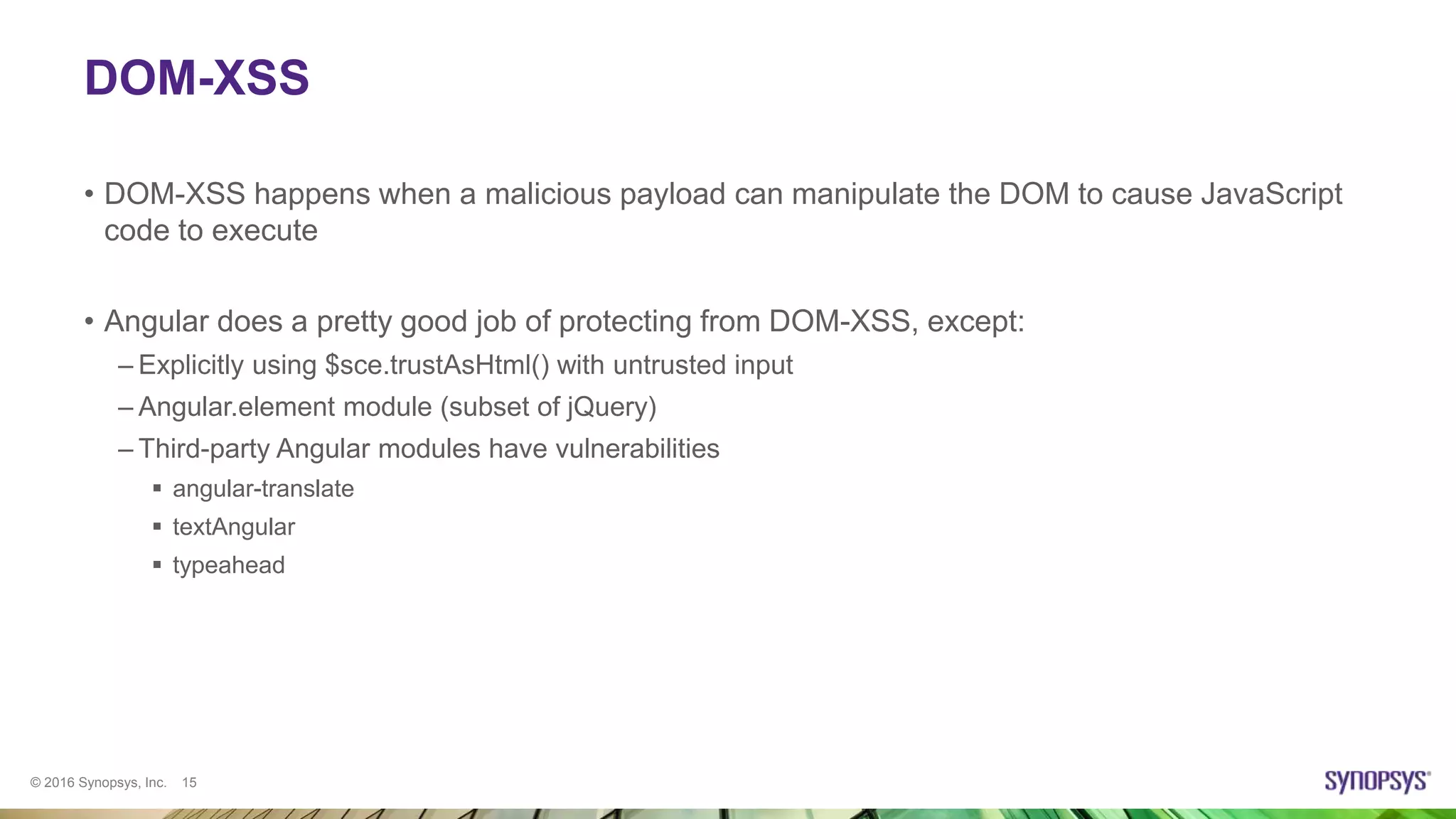
![© 2016 Synopsys, Inc. 16
XSS in angular.element
Reading data from user
<form>
<label>After:</label><input type="text" ng-model="afterinput" />
<button type="submit" nb-click="aftersubmit()">Submit</button>
</form>
<div ng-controller="View1Ctrl">
<div id="testDiv">{{name}}</div>
</div>
controller('View1Ctrl', ['$scope', '$document', function($scope, $document) {
$scope.name = "ChangeMe";
var element = angular.element($document[0].querySelector('#testDiv'));
$scope.aftersubmit=function()
{
if($scope.afterinput) element.after($scope.afterinput);
}
Inserting data in Angular code](https://image.slidesharecdn.com/angularjssecurity-180629012746/75/How-Secure-Is-AngularJS-16-2048.jpg)
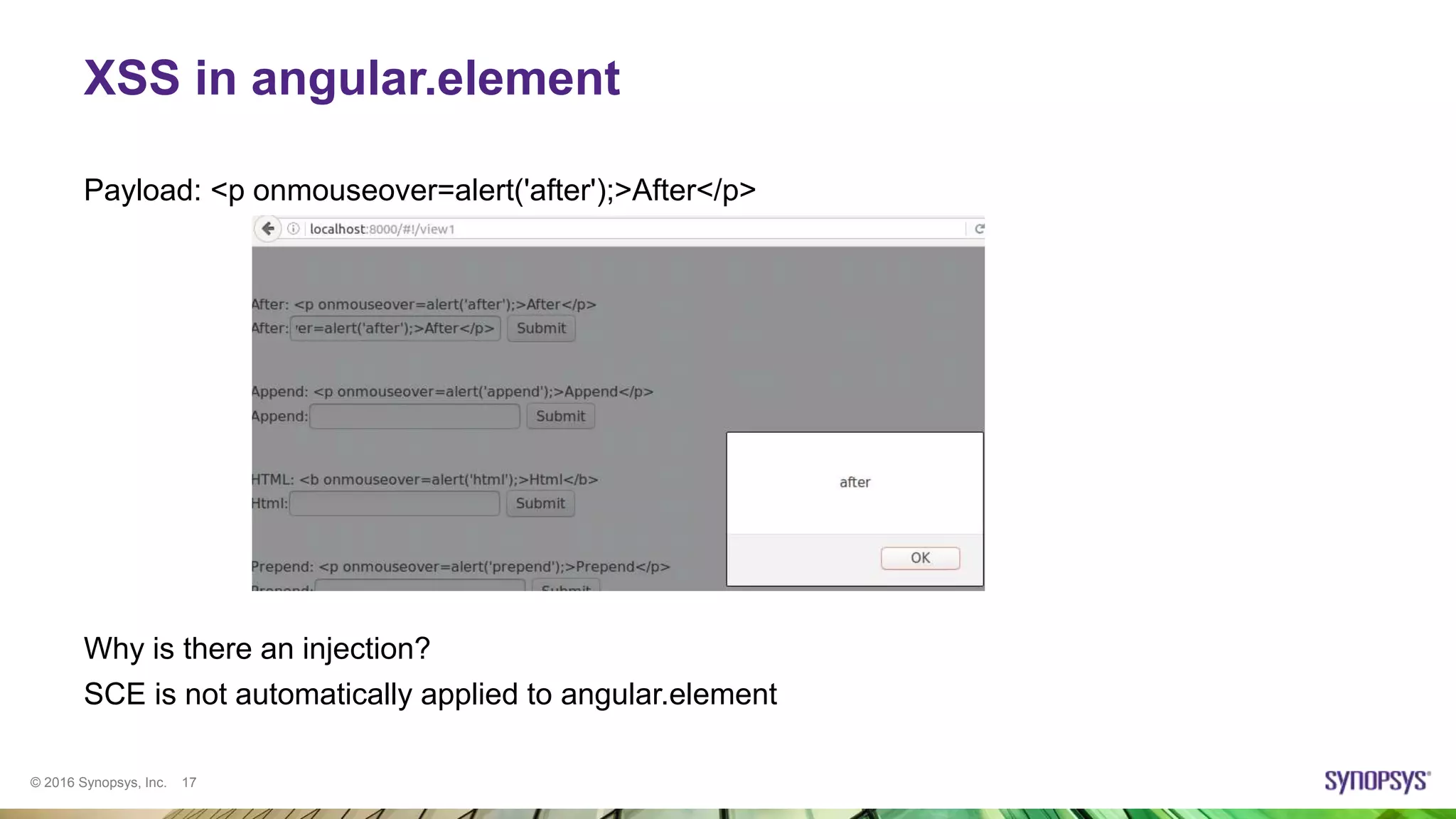
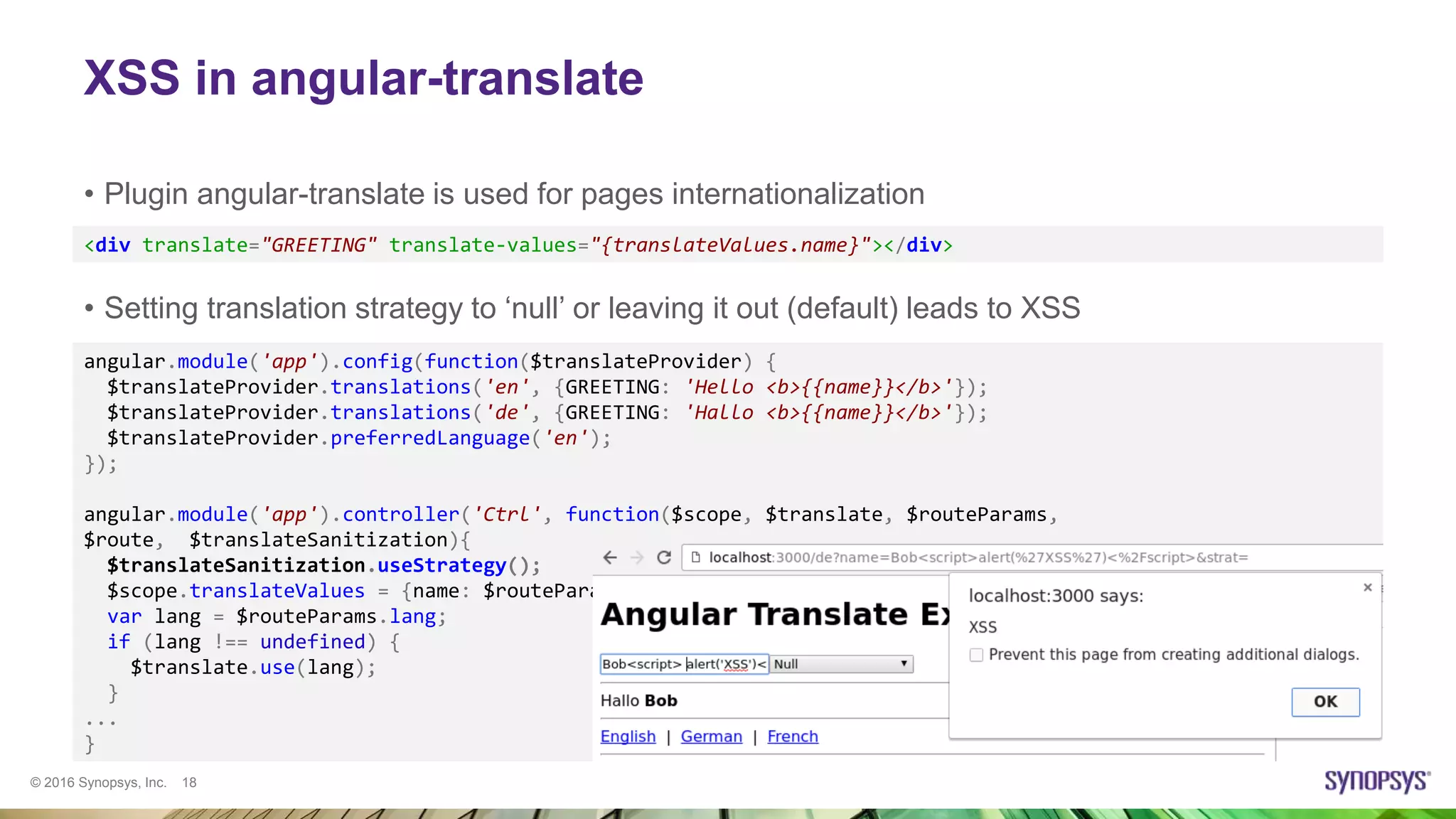
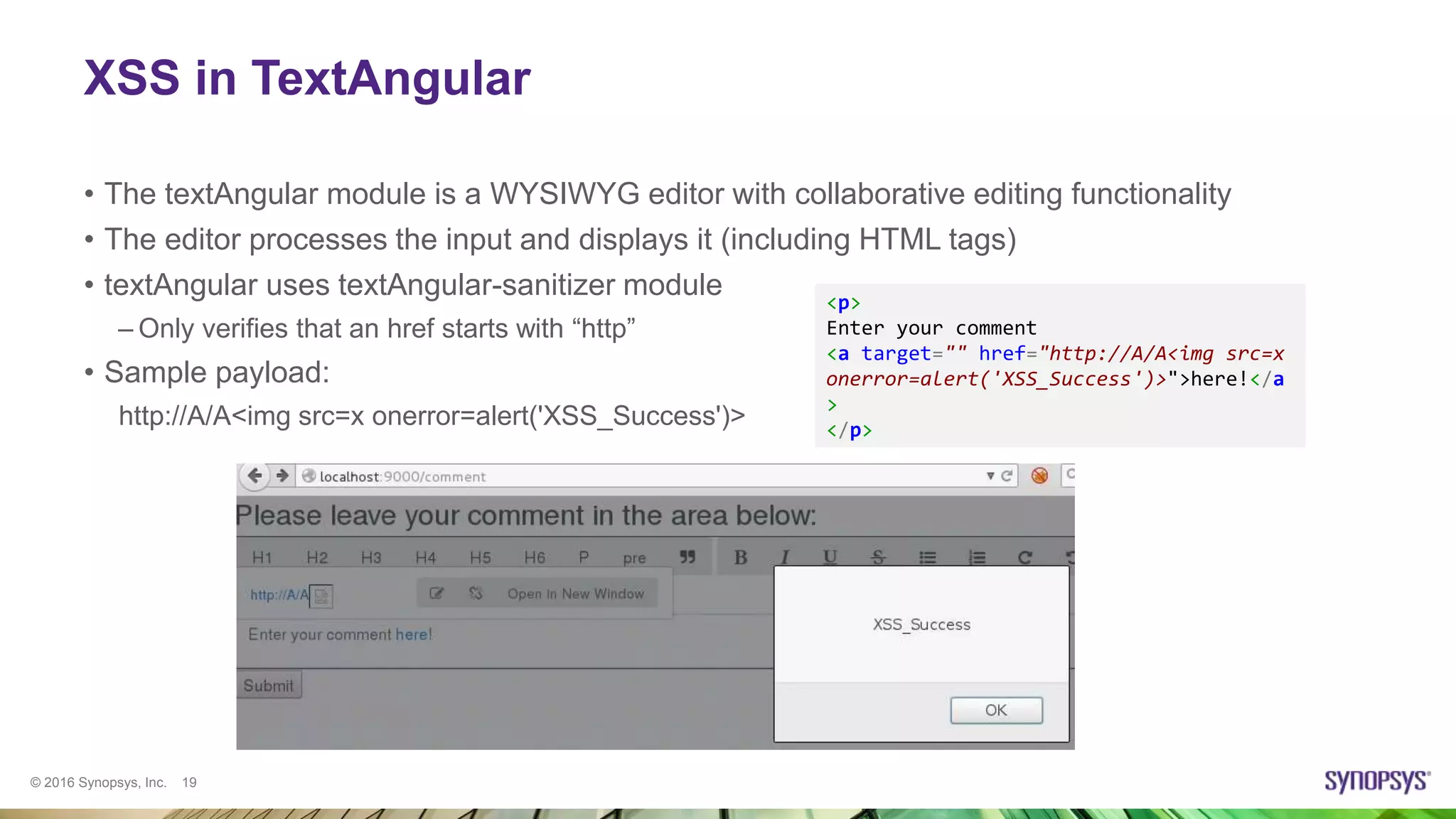
![© 2016 Synopsys, Inc. 20
XSS in TypeAhead
• TypeAhead module shows hints as the user starts typing in a text field
• The list of hints is not sanitized if at least one condition is met:
– ui.bootstrap version prior to 0.13.4 is used
– ngSanitize is not included
<form ng-submit="submit()">
<input type="text"
ng-submit="submit()"
ng-model="search_val"
typeahead="search_val for search_val in searches"
class="form-control">
<input type="submit" value="Search"/>
</form>
module.controller(
'TypeaheadCtrl',
function($scope,$http) {
$scope.selected = undefined;
$scope.searches = [
decodeURIComponent(window.location.search.split("?")[1])
];
}
<script src="http://angular-ui.github.io/bootstrap/ui-bootstrap-tpls-0.13.3.js"></script>
var module = angular.module('app', ['ui.bootstrap']](https://image.slidesharecdn.com/angularjssecurity-180629012746/75/How-Secure-Is-AngularJS-20-2048.jpg)