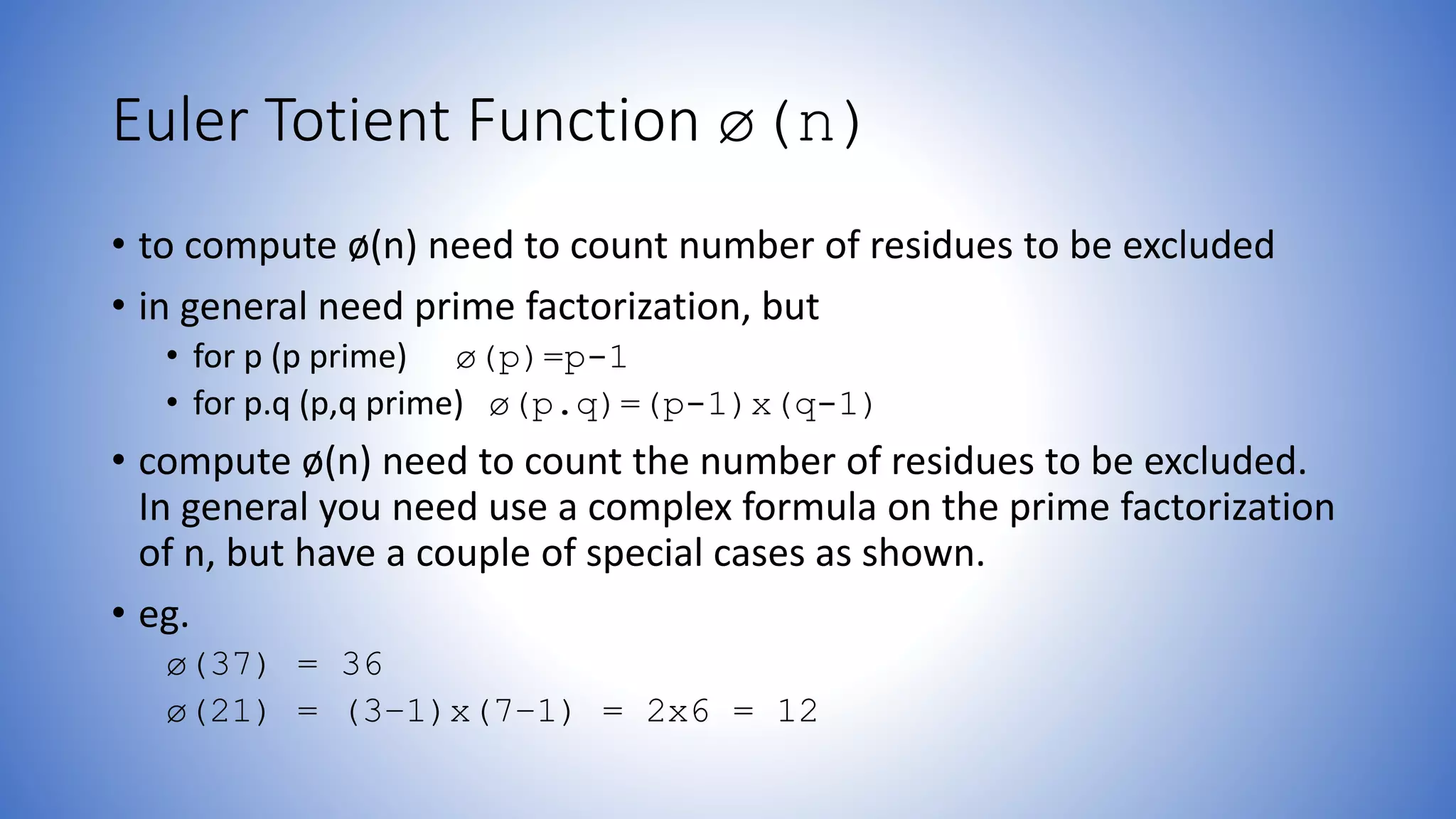
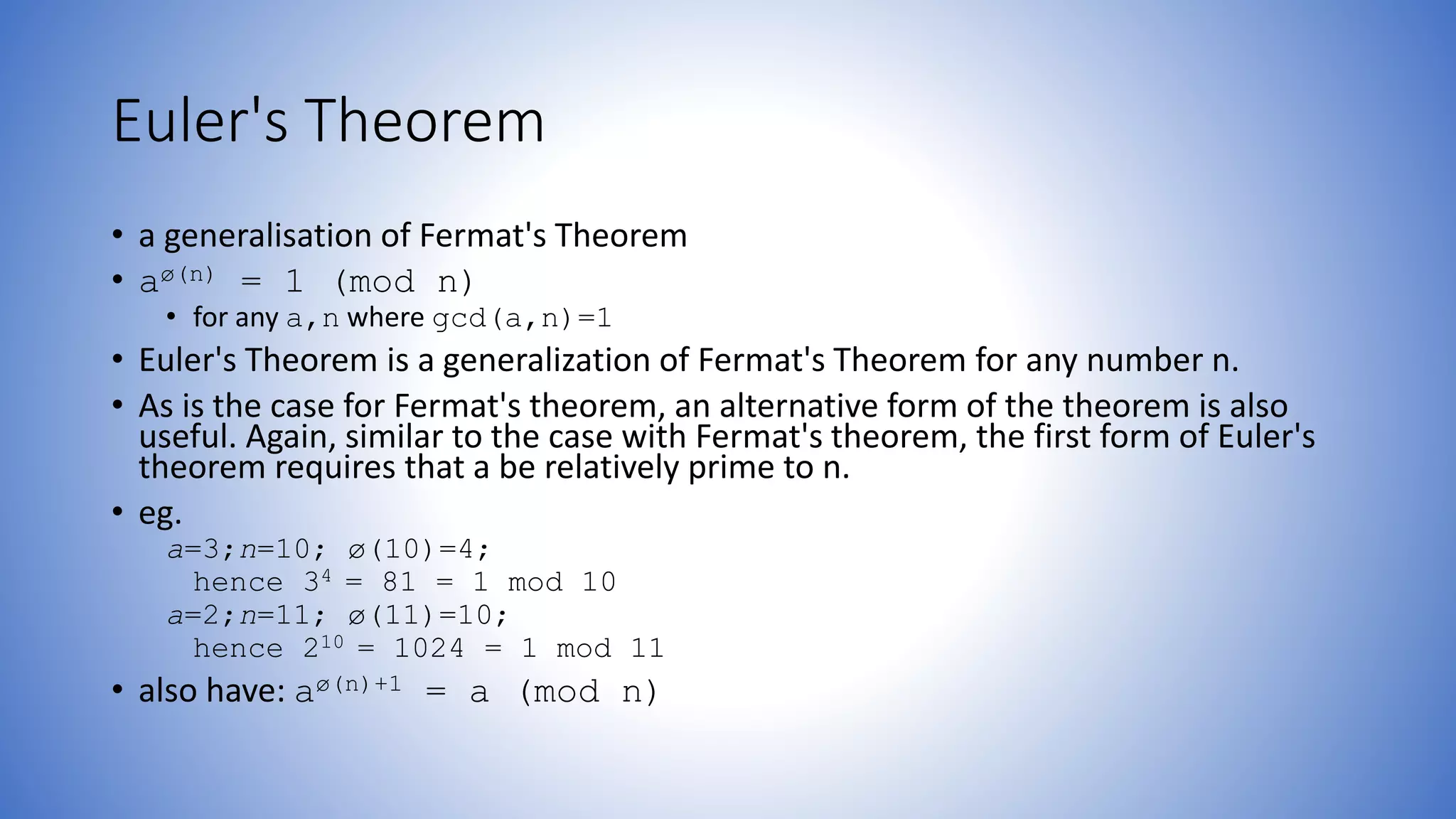
The document discusses the properties and importance of prime numbers, including definitions, prime factorization, greatest common divisors, and various relevant theorems like Fermat's and Euler's. It outlines methods for primality testing and emphasizes the role of prime numbers in cryptography. Additionally, it provides formulas for Euler's totient function and explains concepts related to relatively prime numbers and their significance.