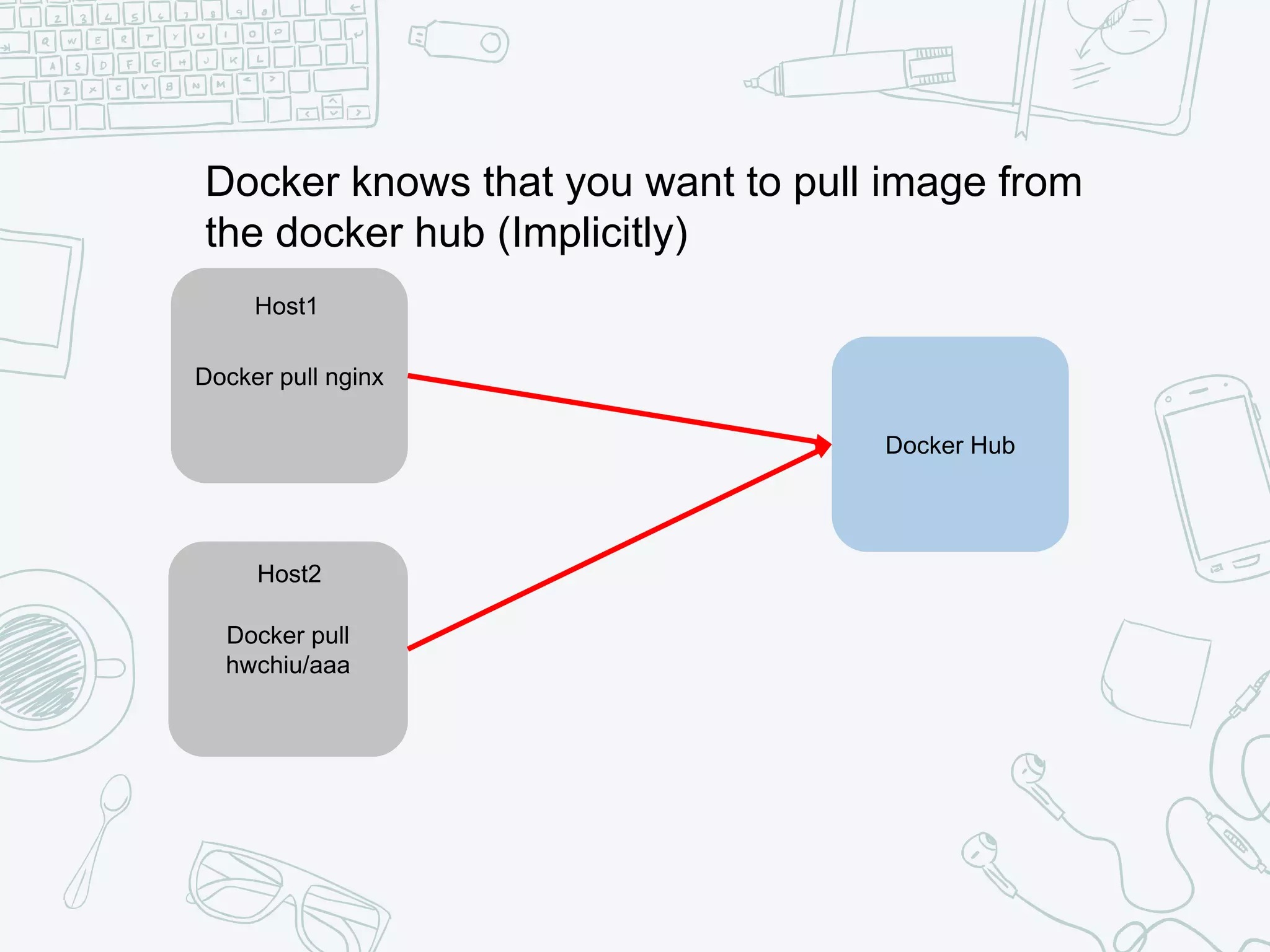
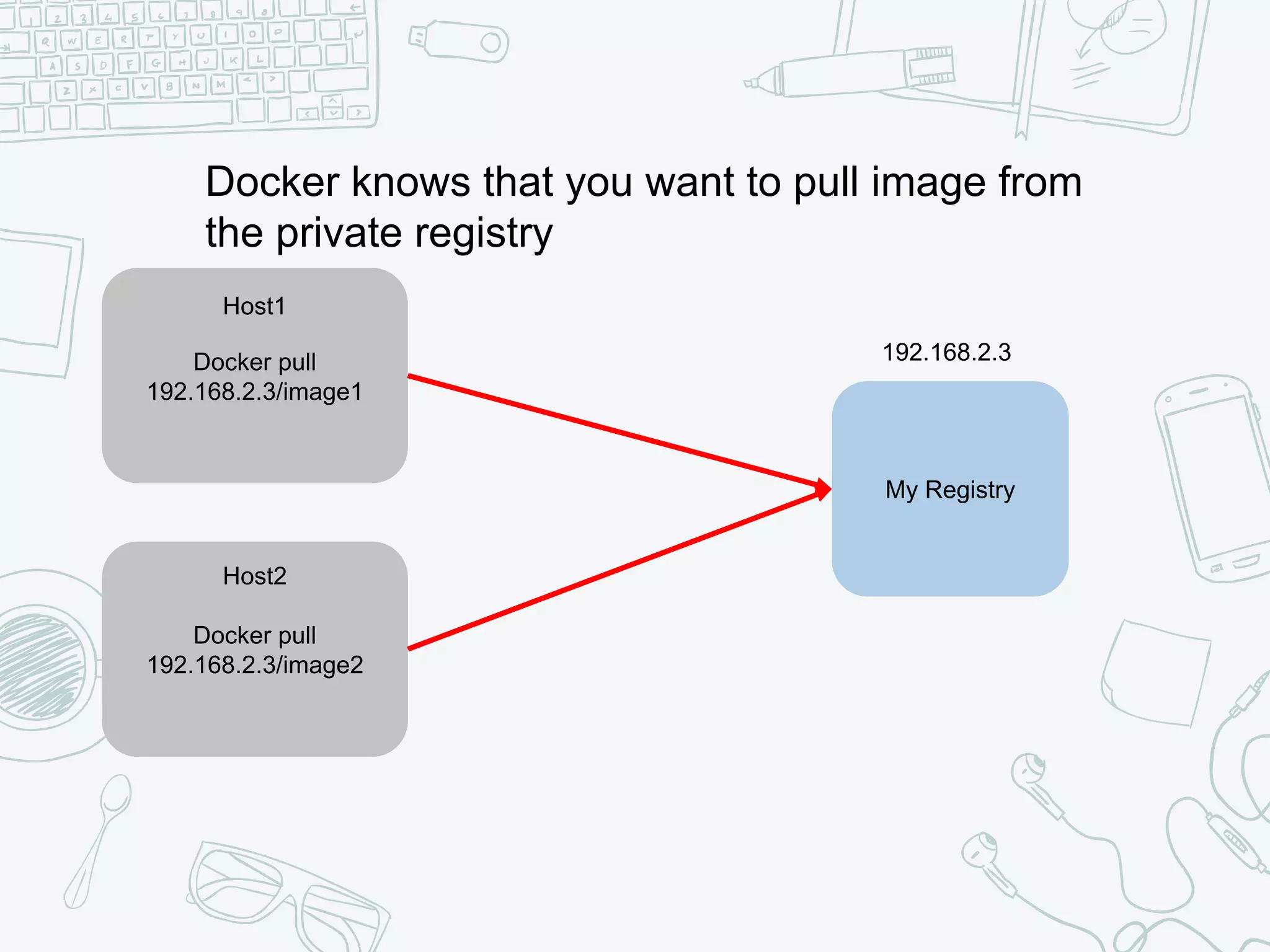
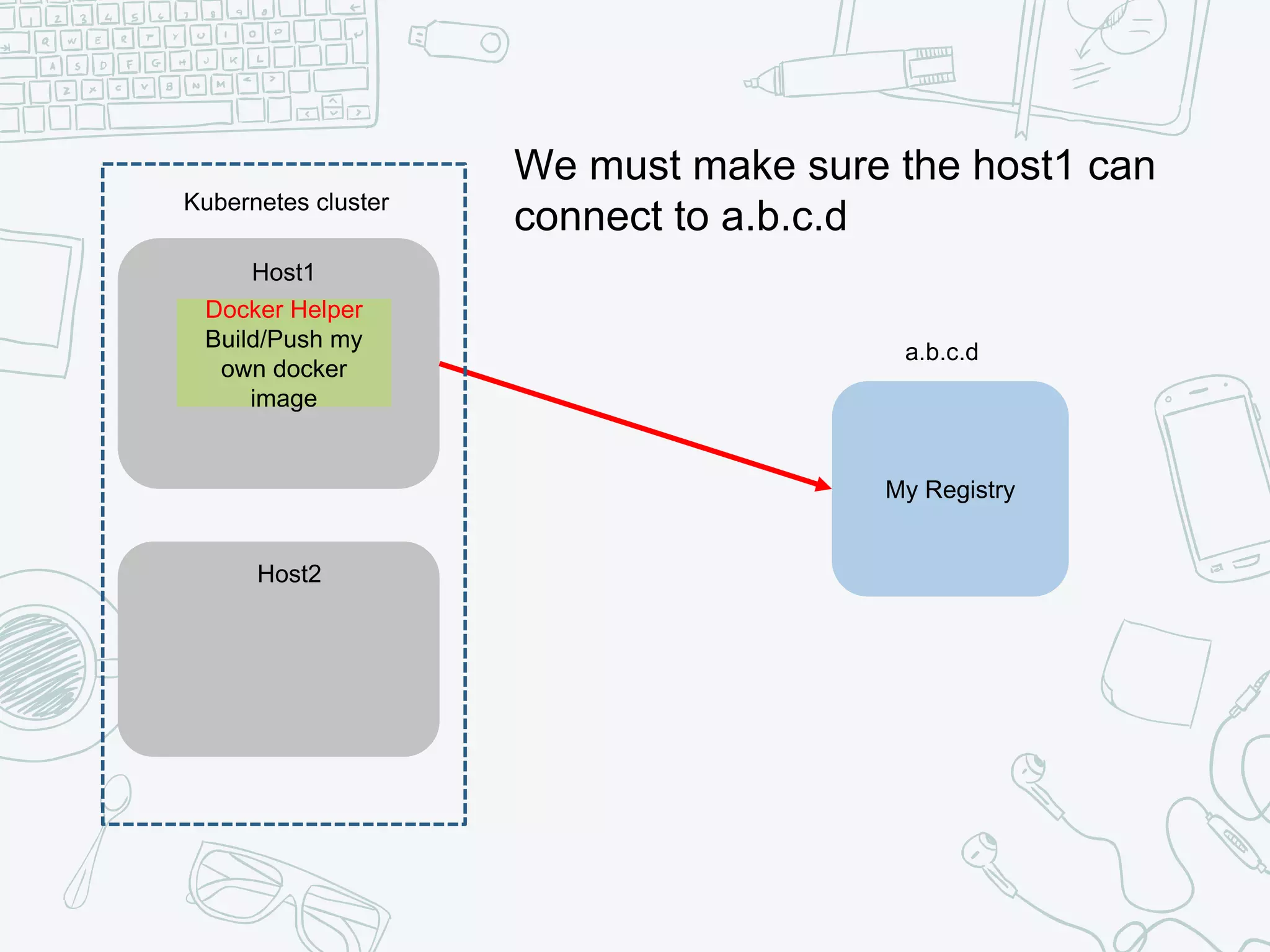
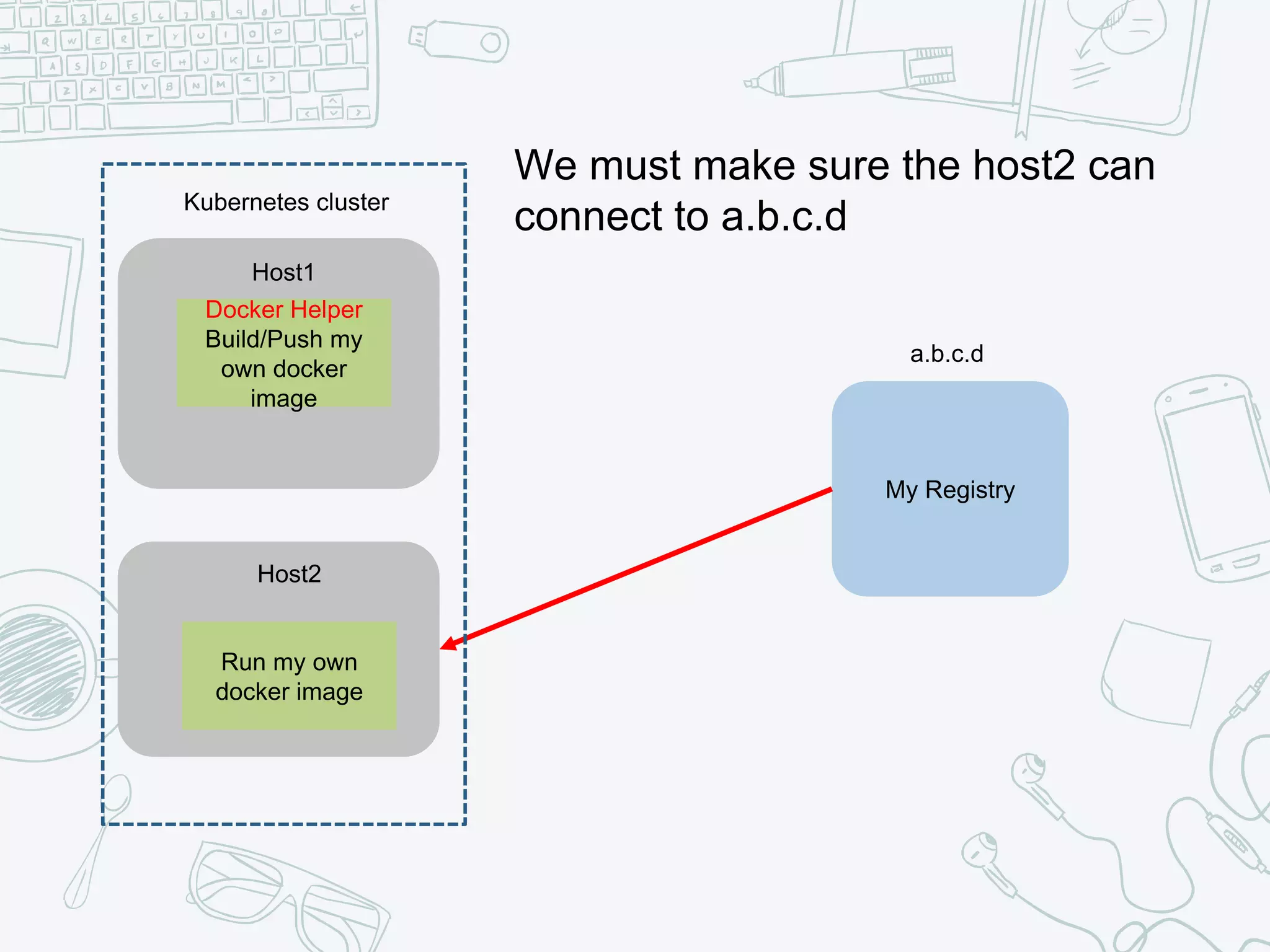
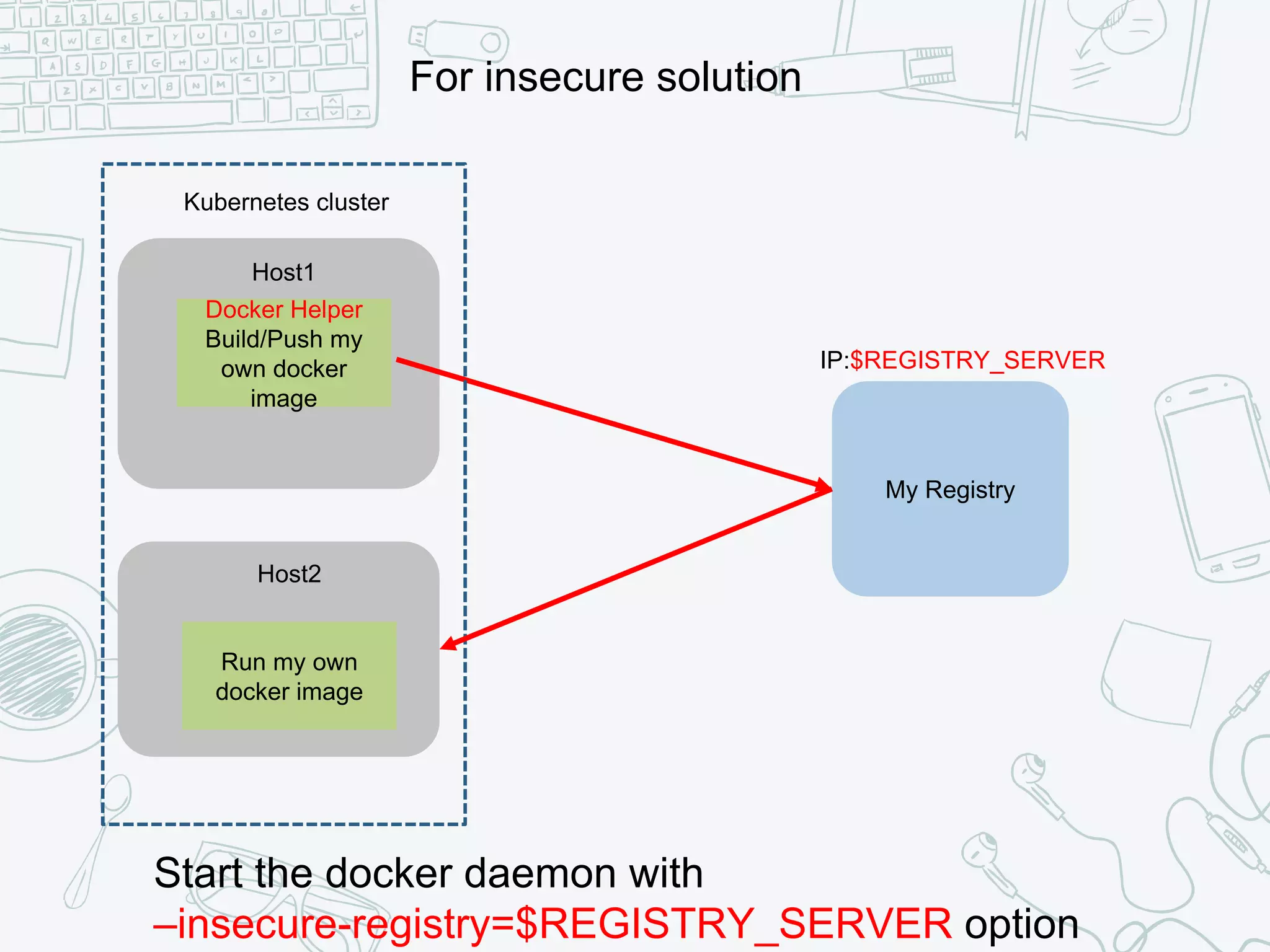
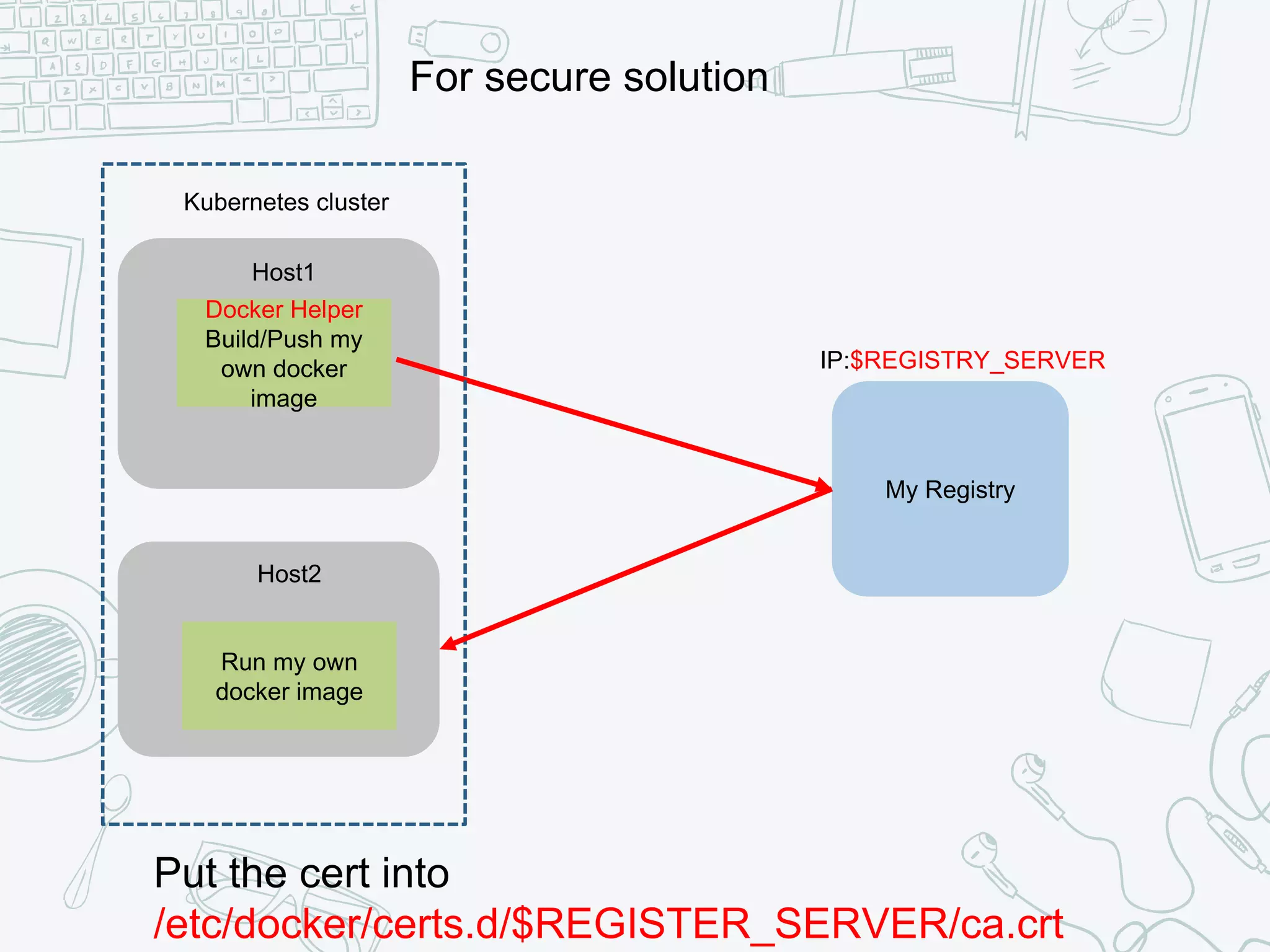
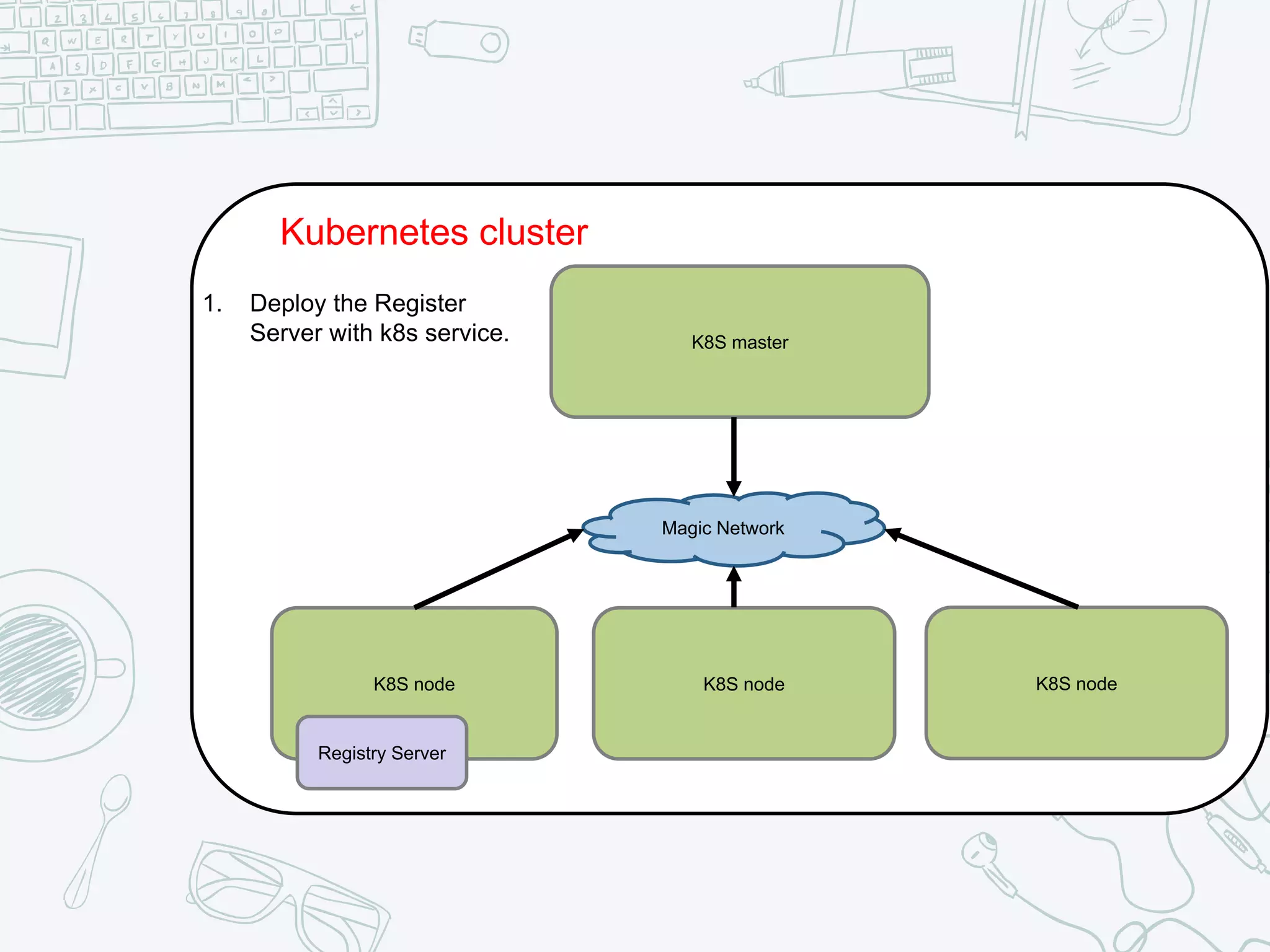
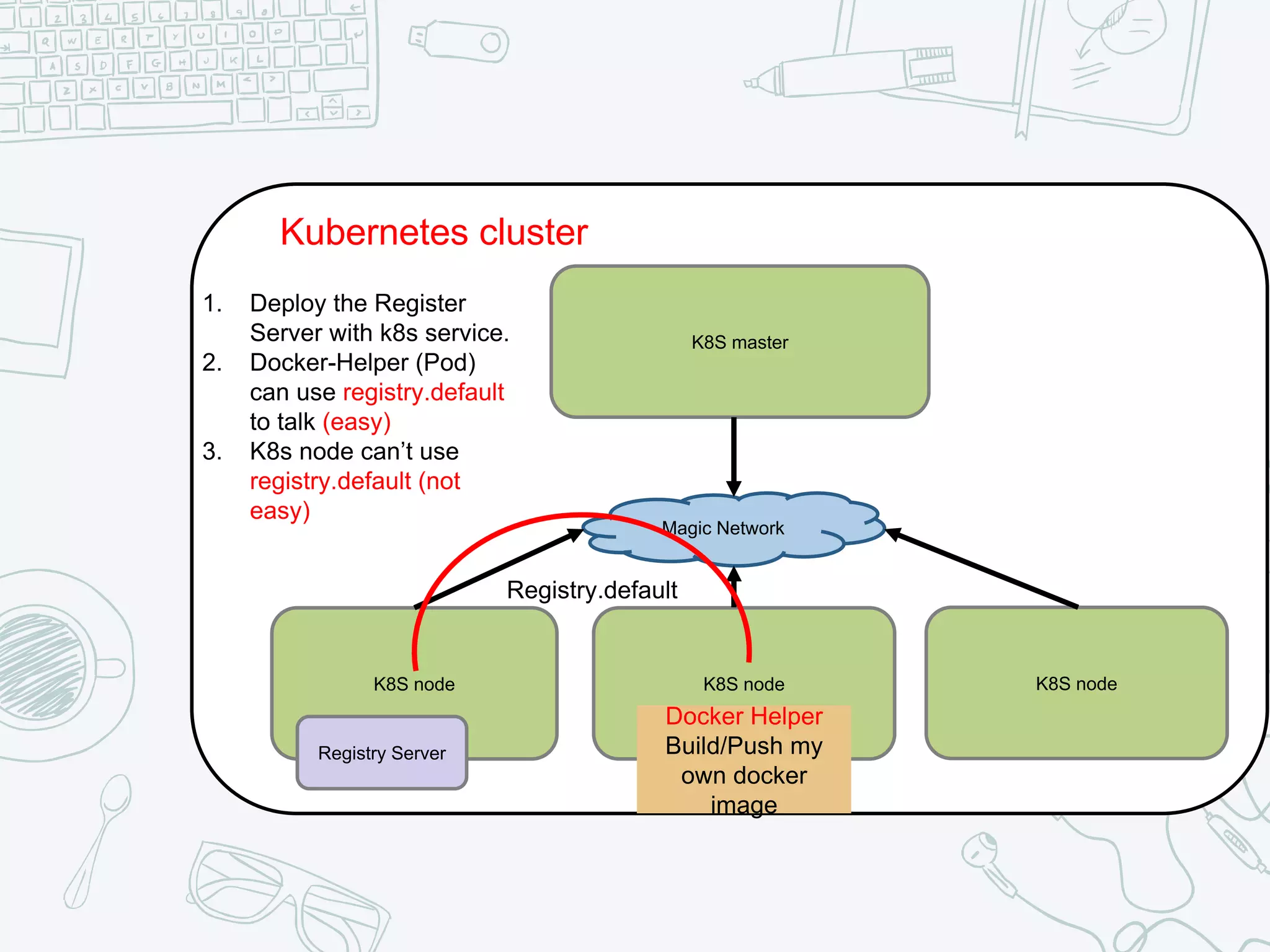
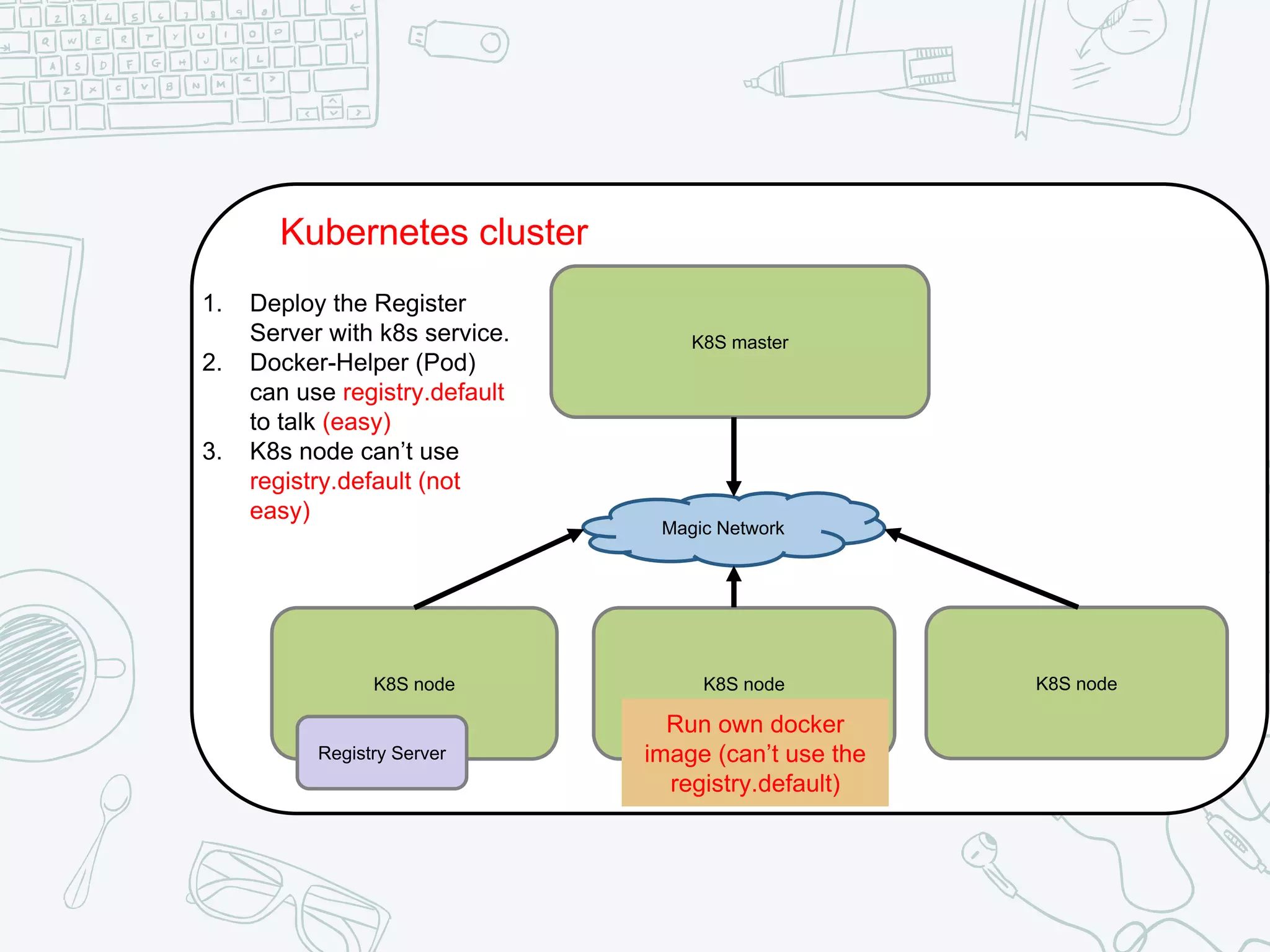
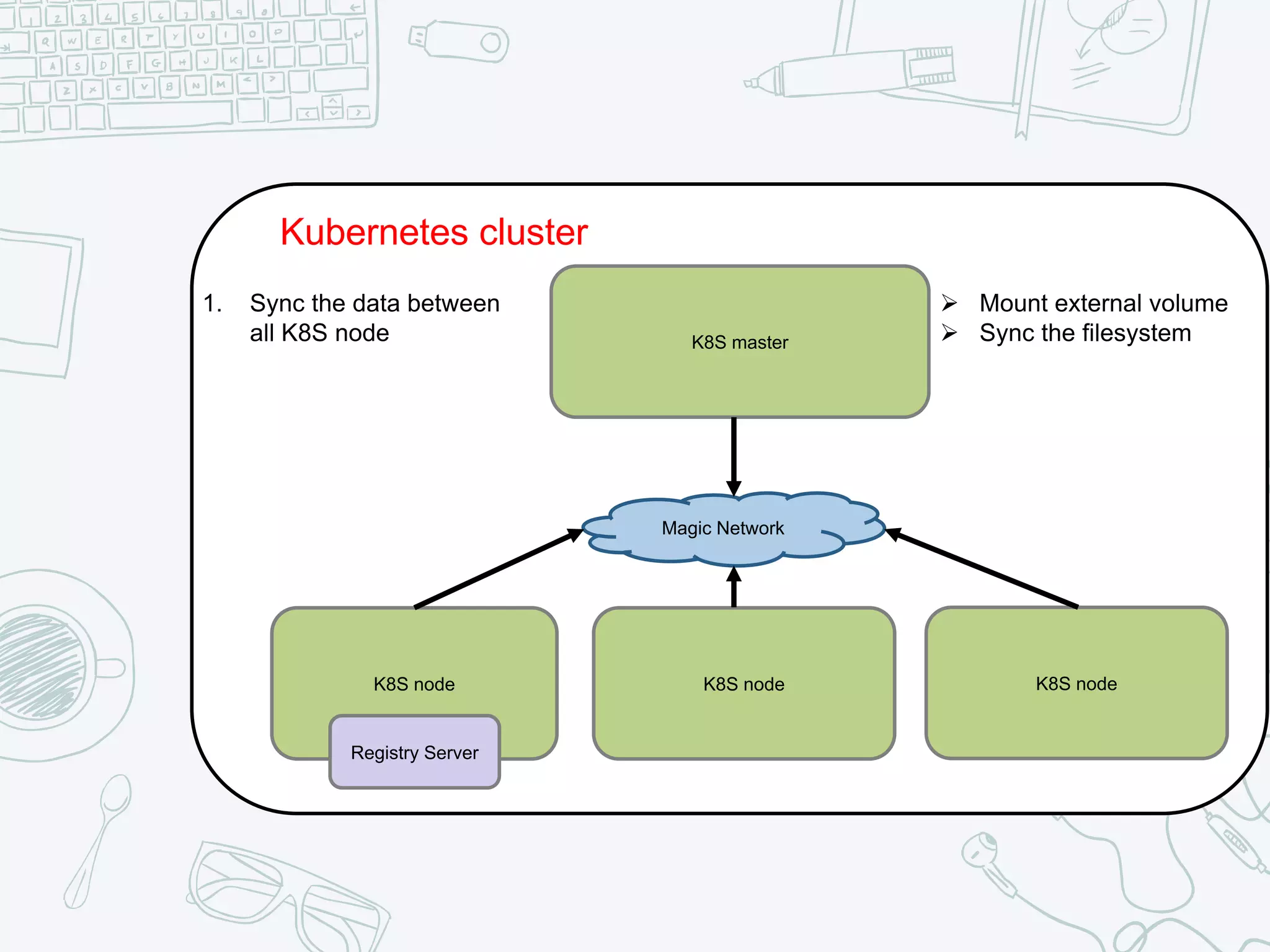
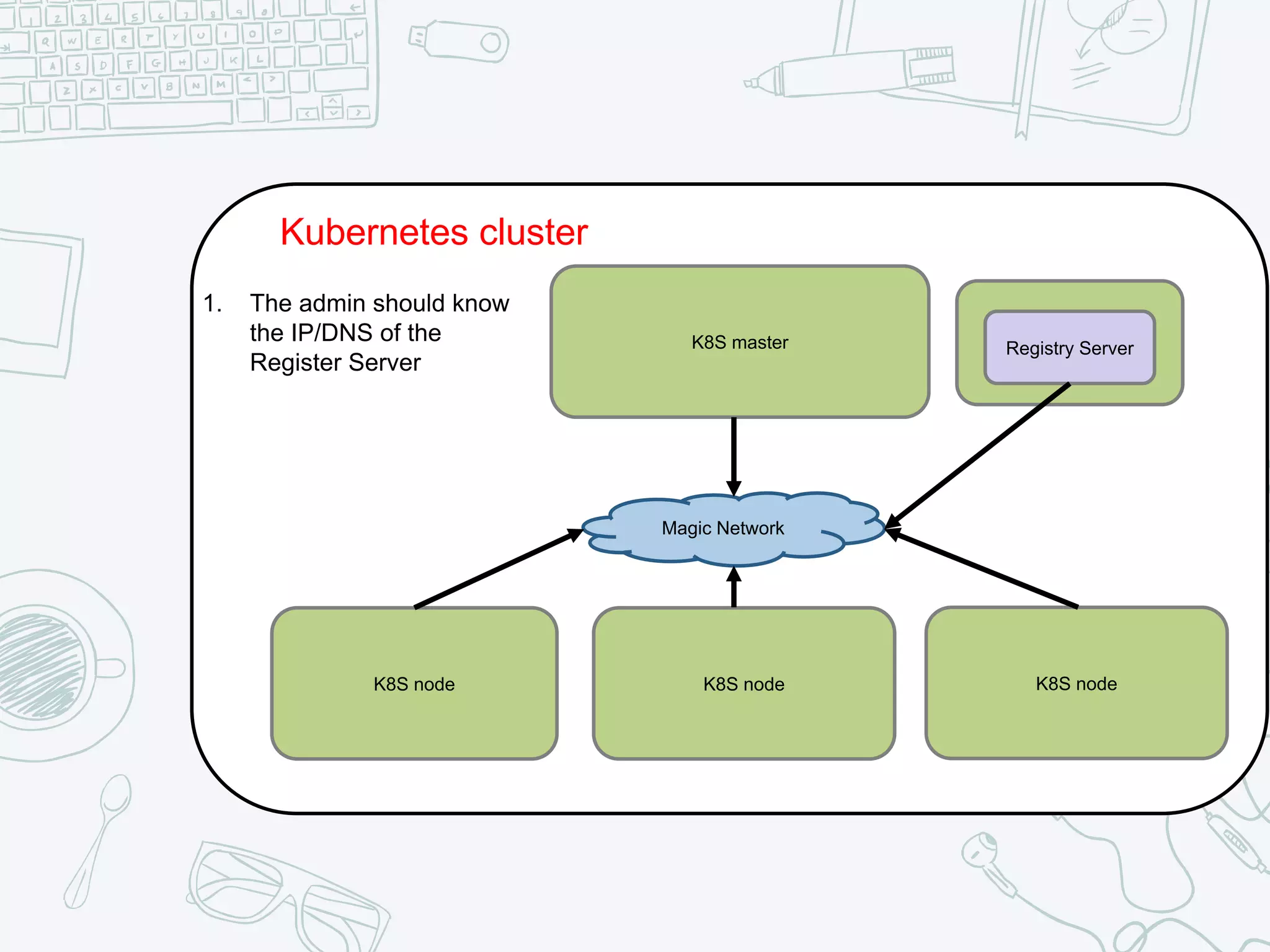
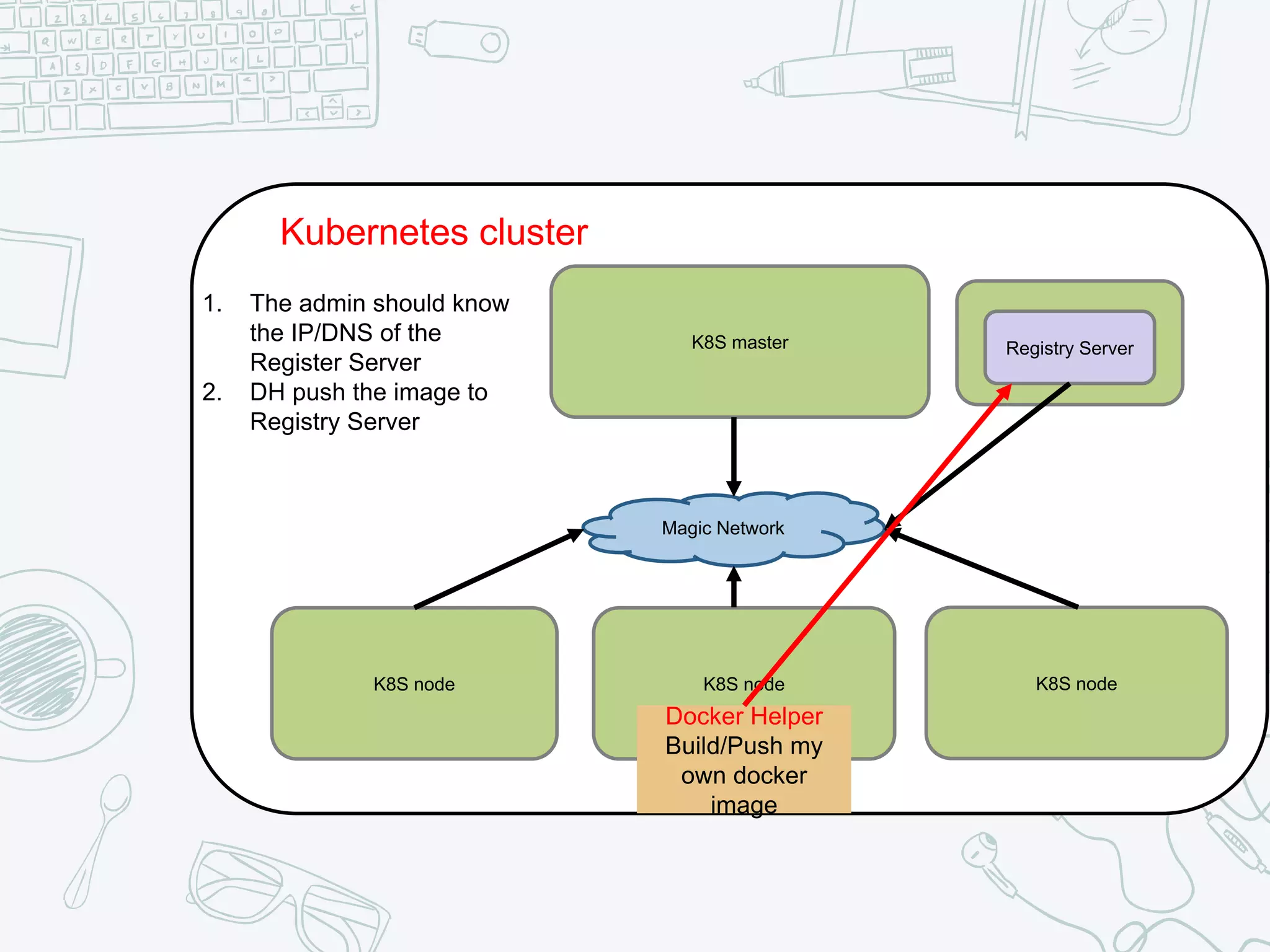
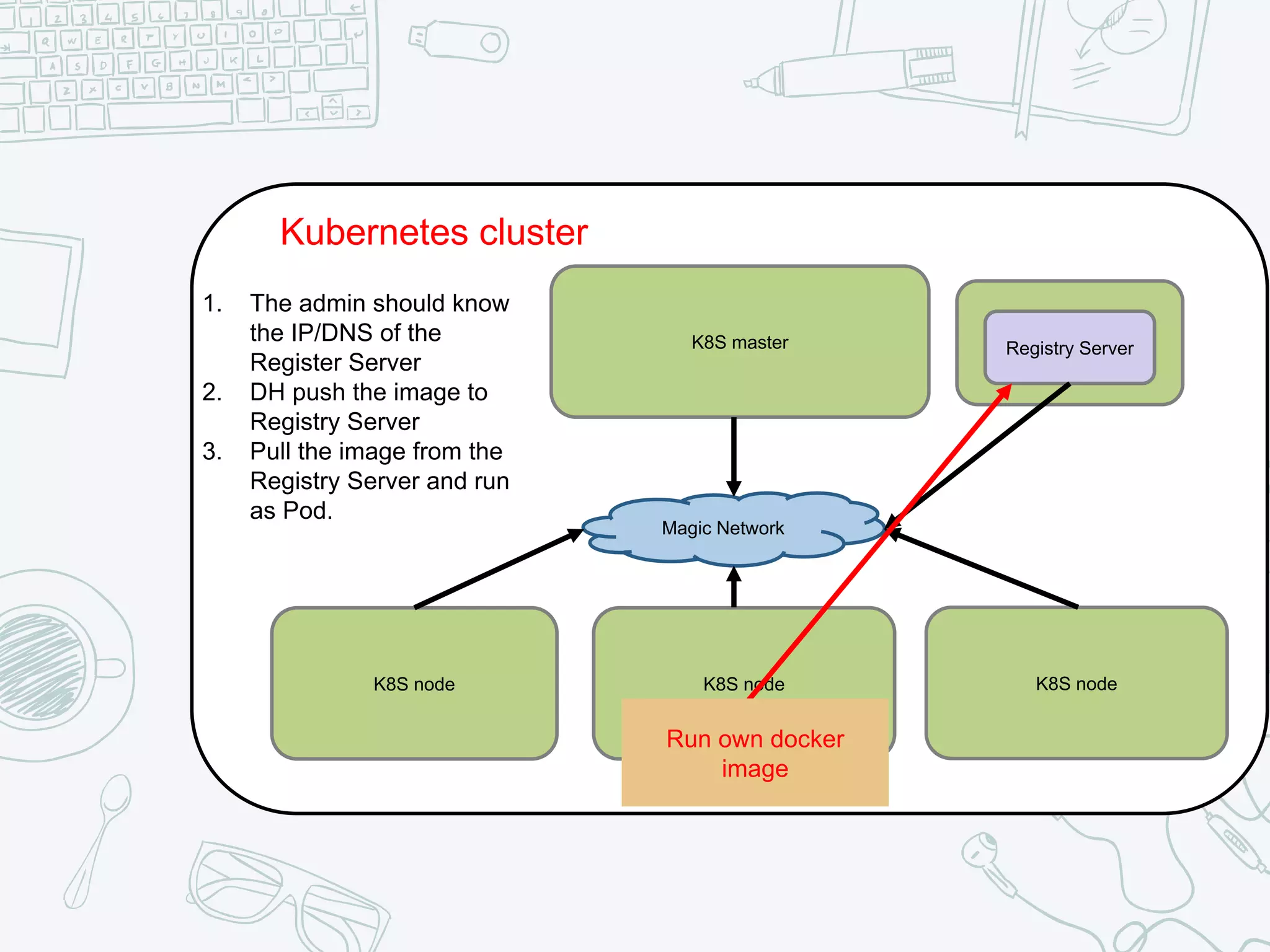
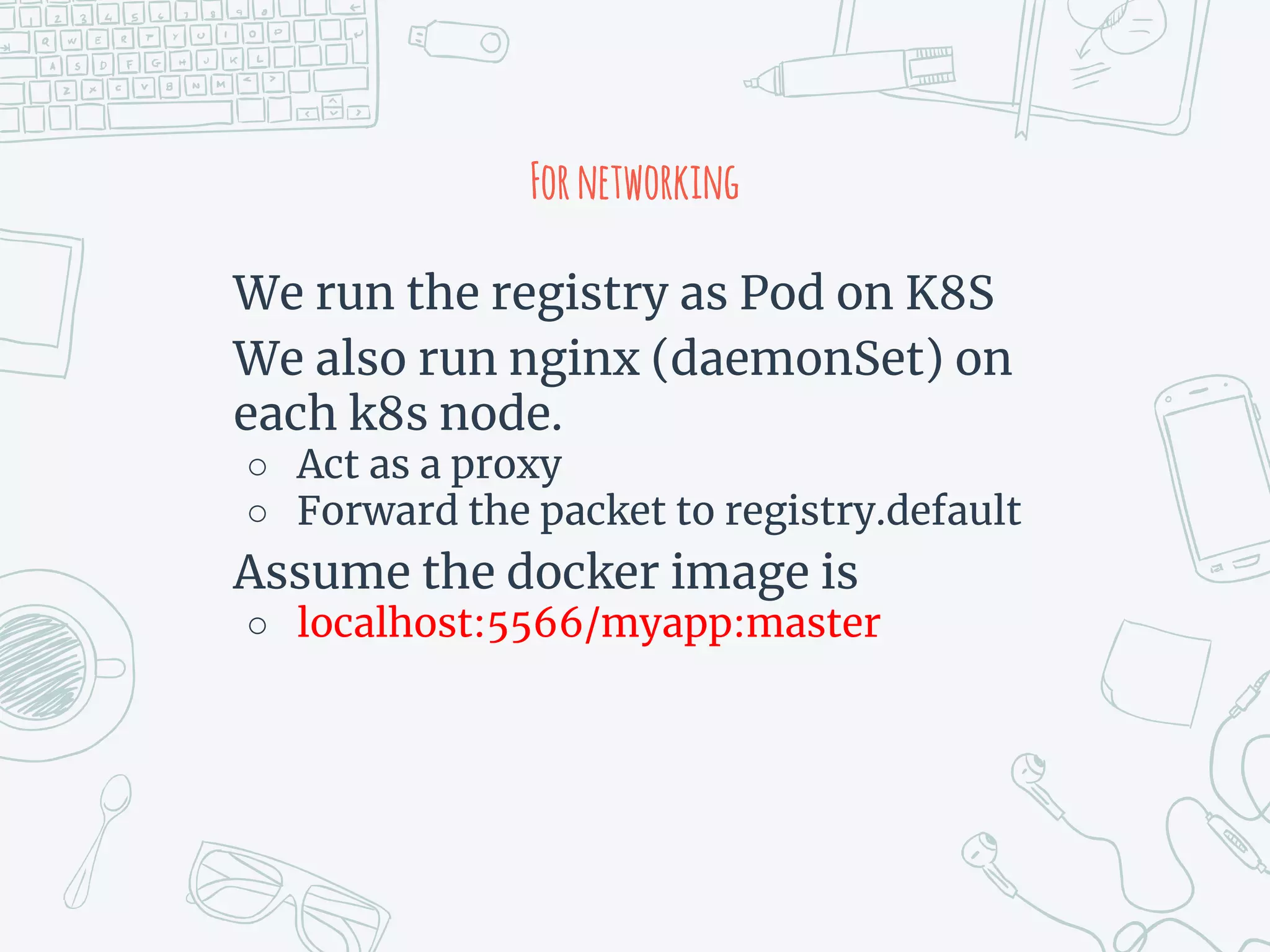
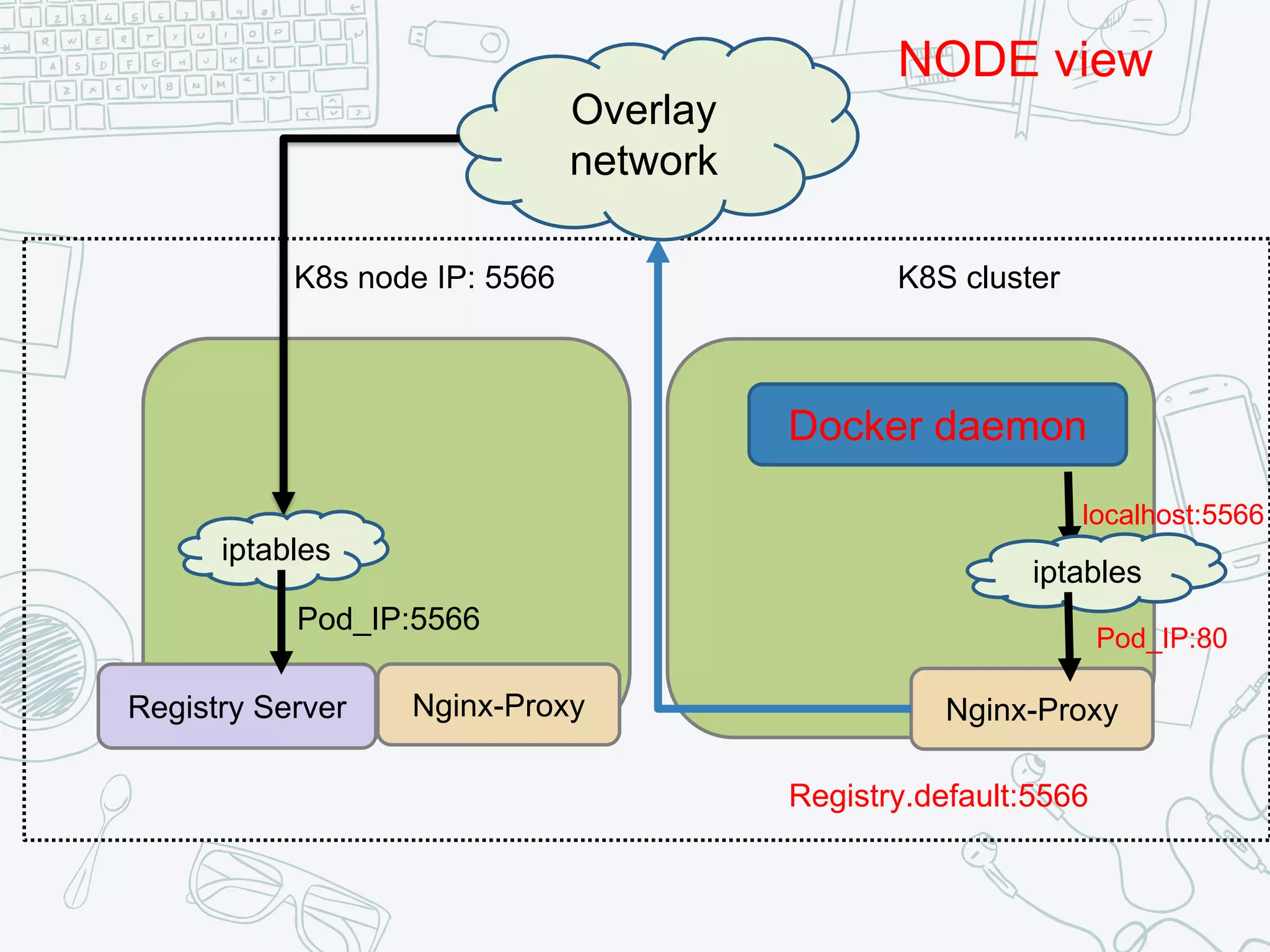
The document outlines the setup and usage of a private Docker registry in a Kubernetes environment, detailing the registry's purpose as a stateless and scalable application for distributing Docker images. It discusses the architecture options for deploying the registry, including pros and cons of running it inside or outside the Kubernetes cluster, and offers solutions for enabling secure connections. Additionally, it suggests using an Nginx proxy on each Kubernetes node to simplify access to the registry and mitigate certificate issues.