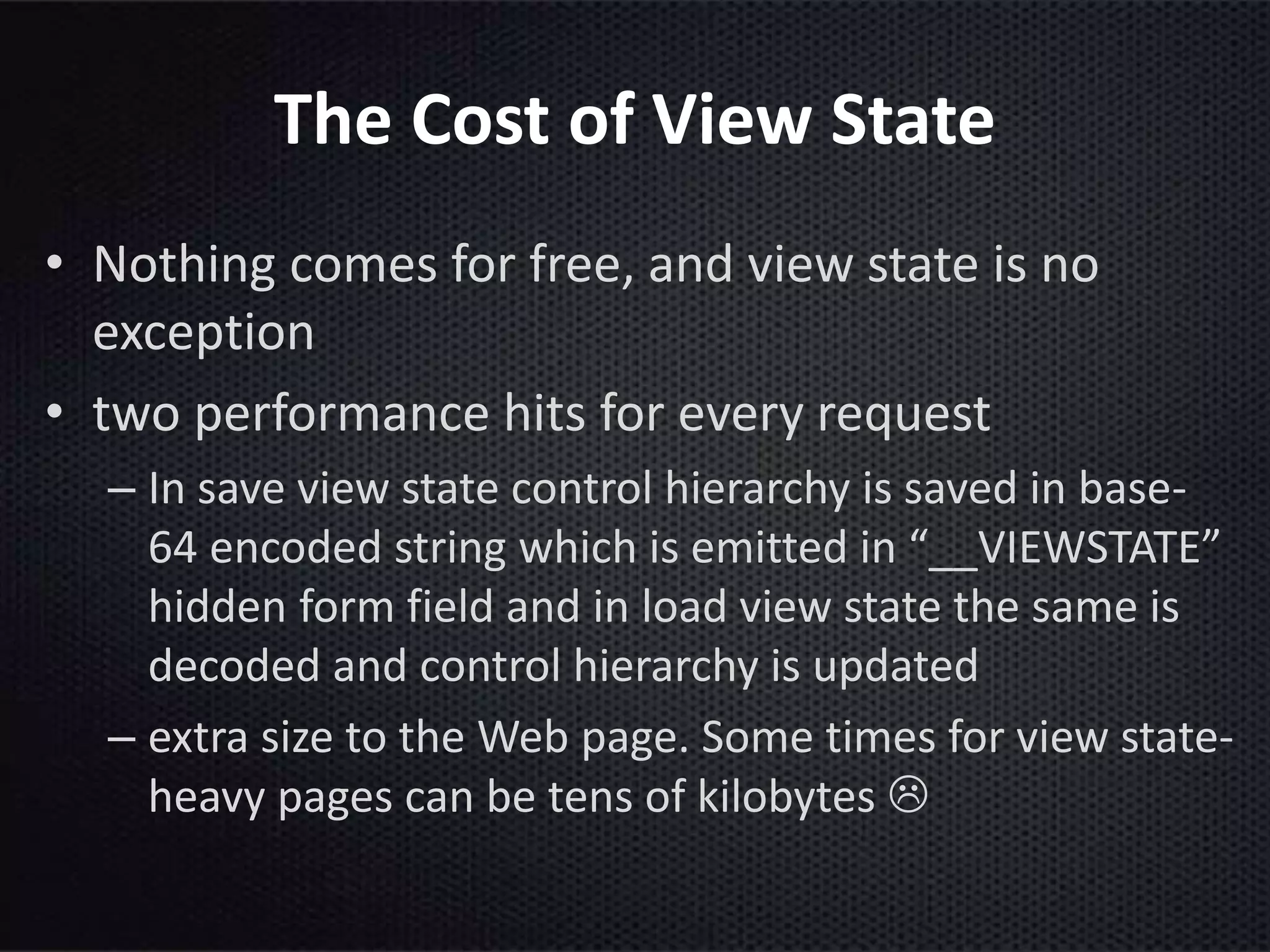
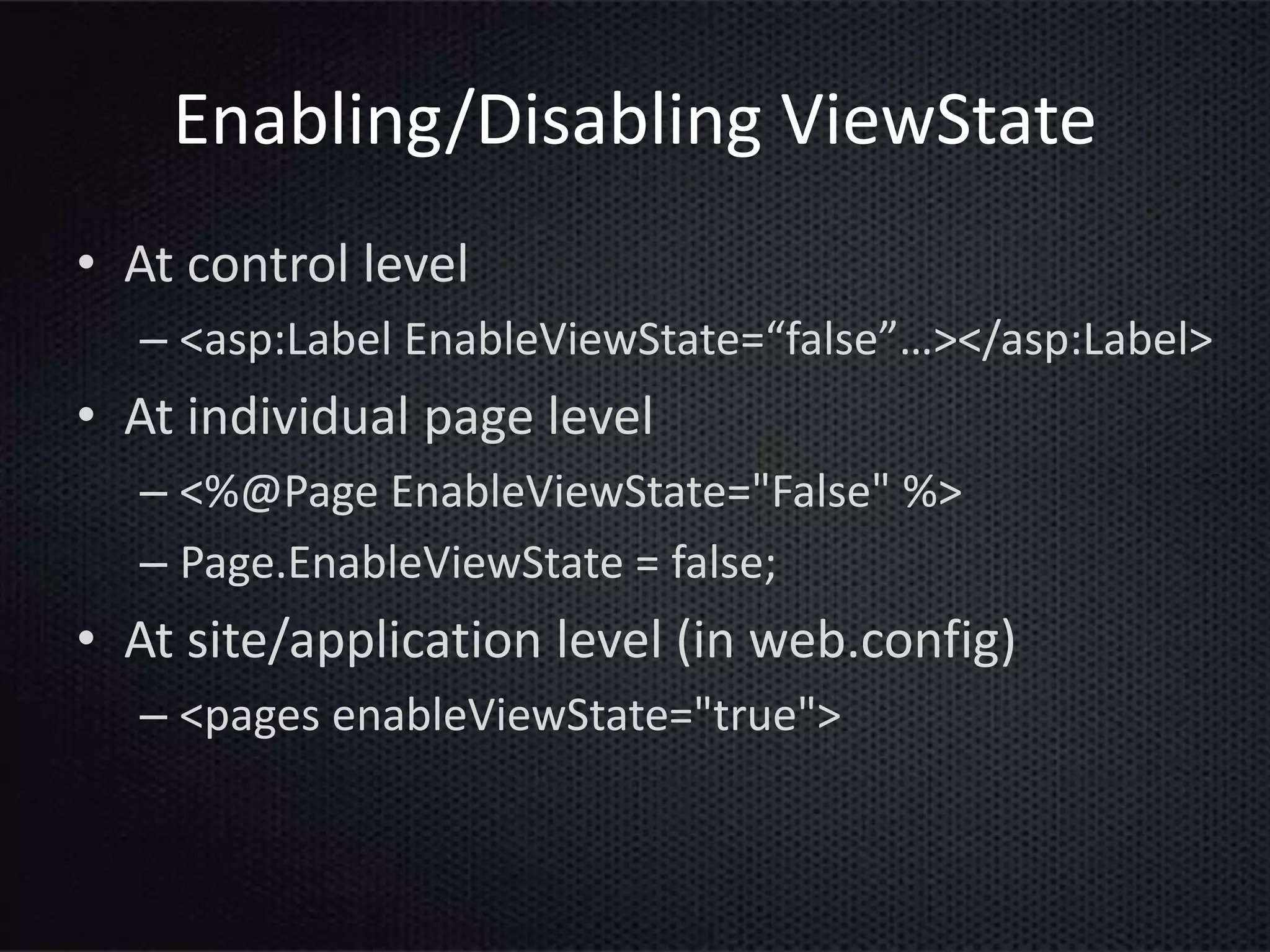
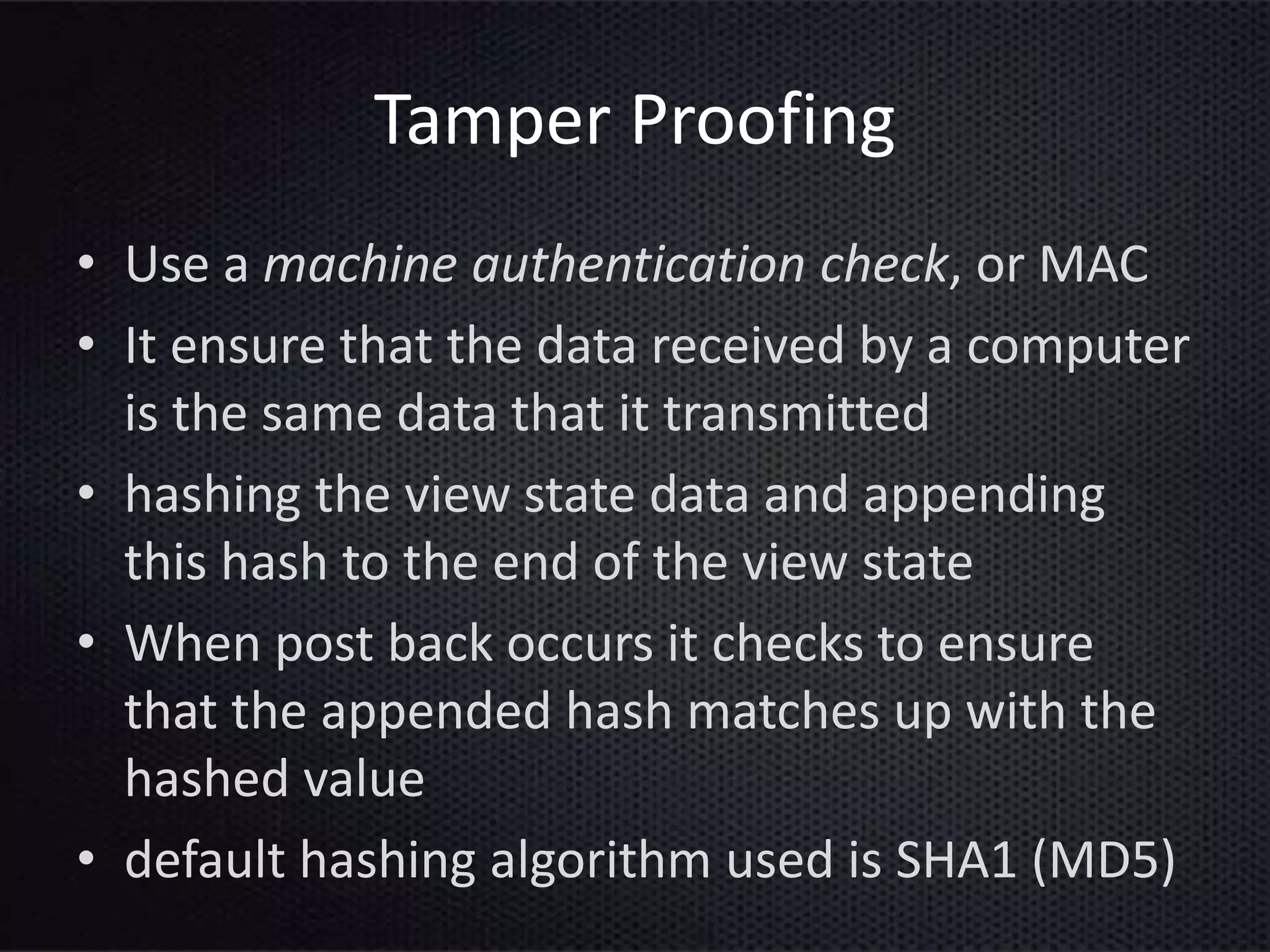
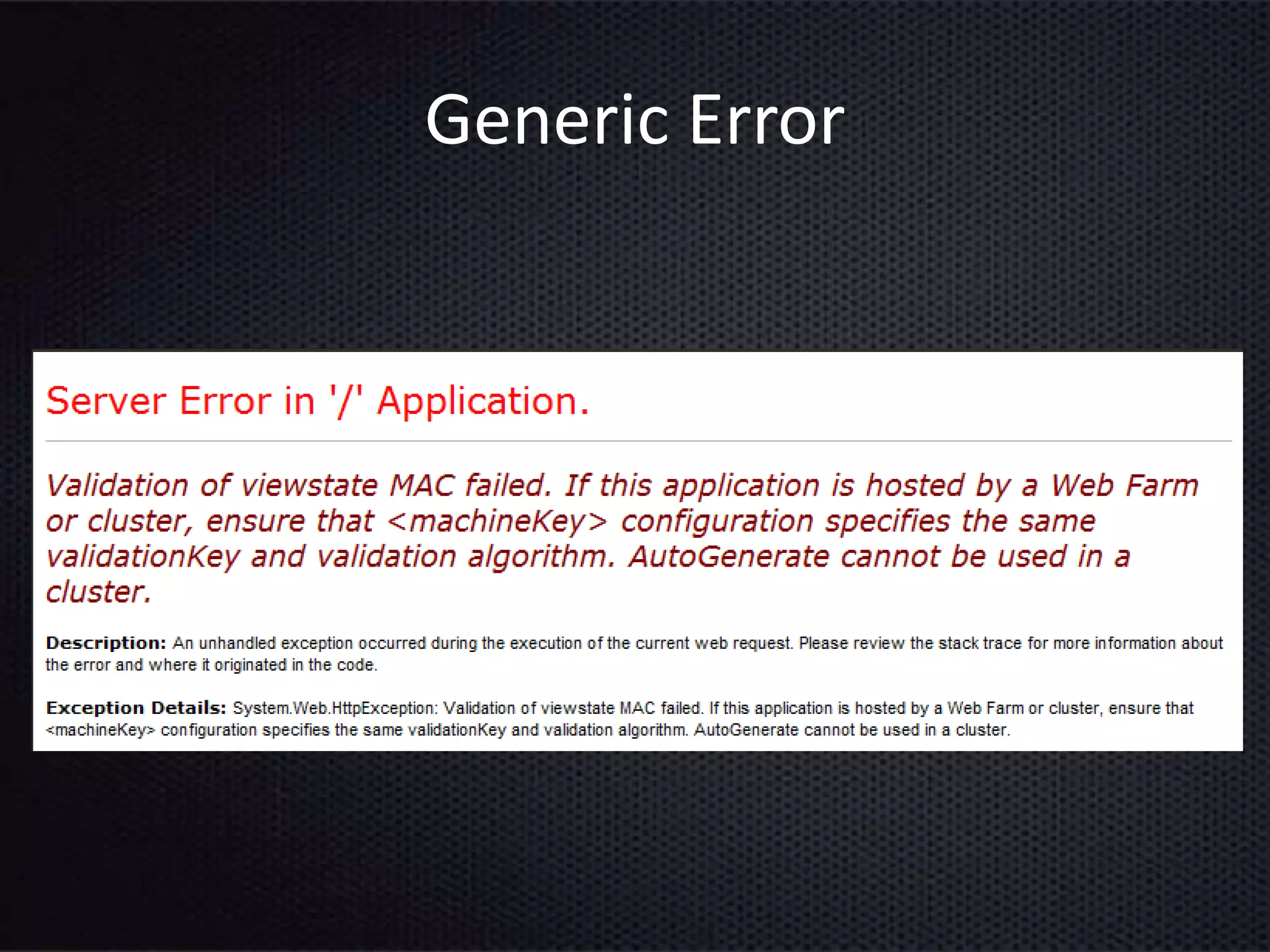
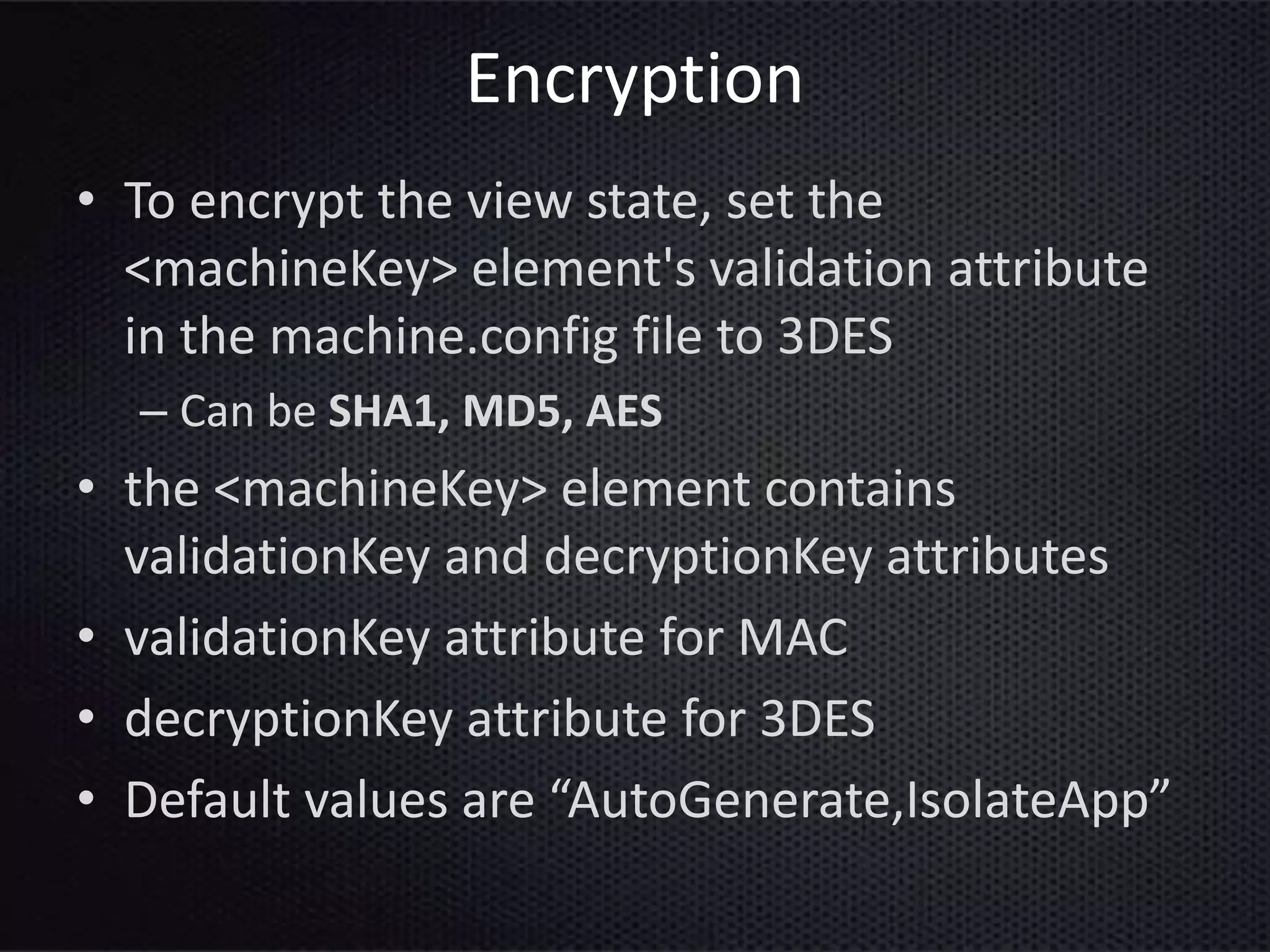
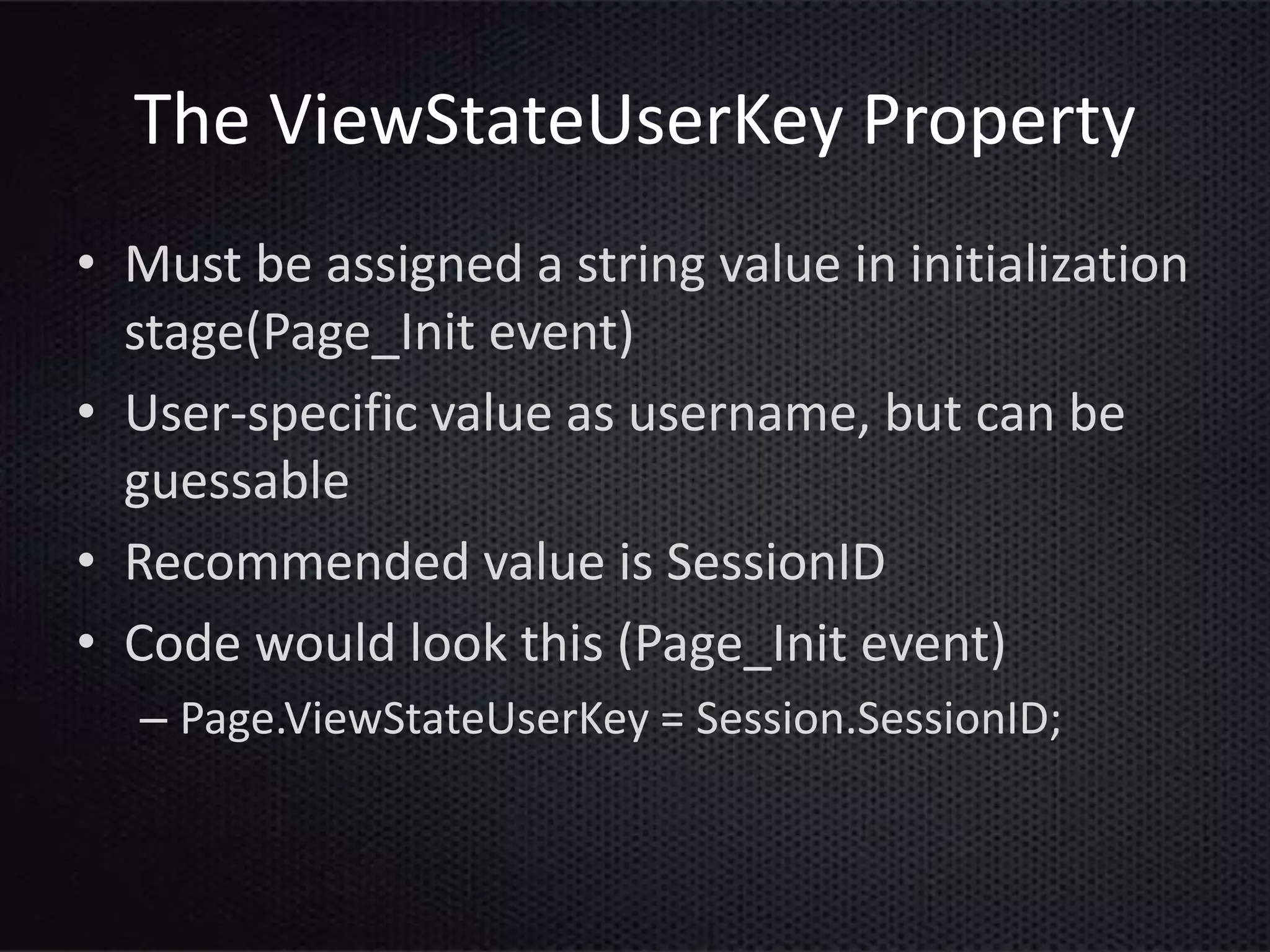
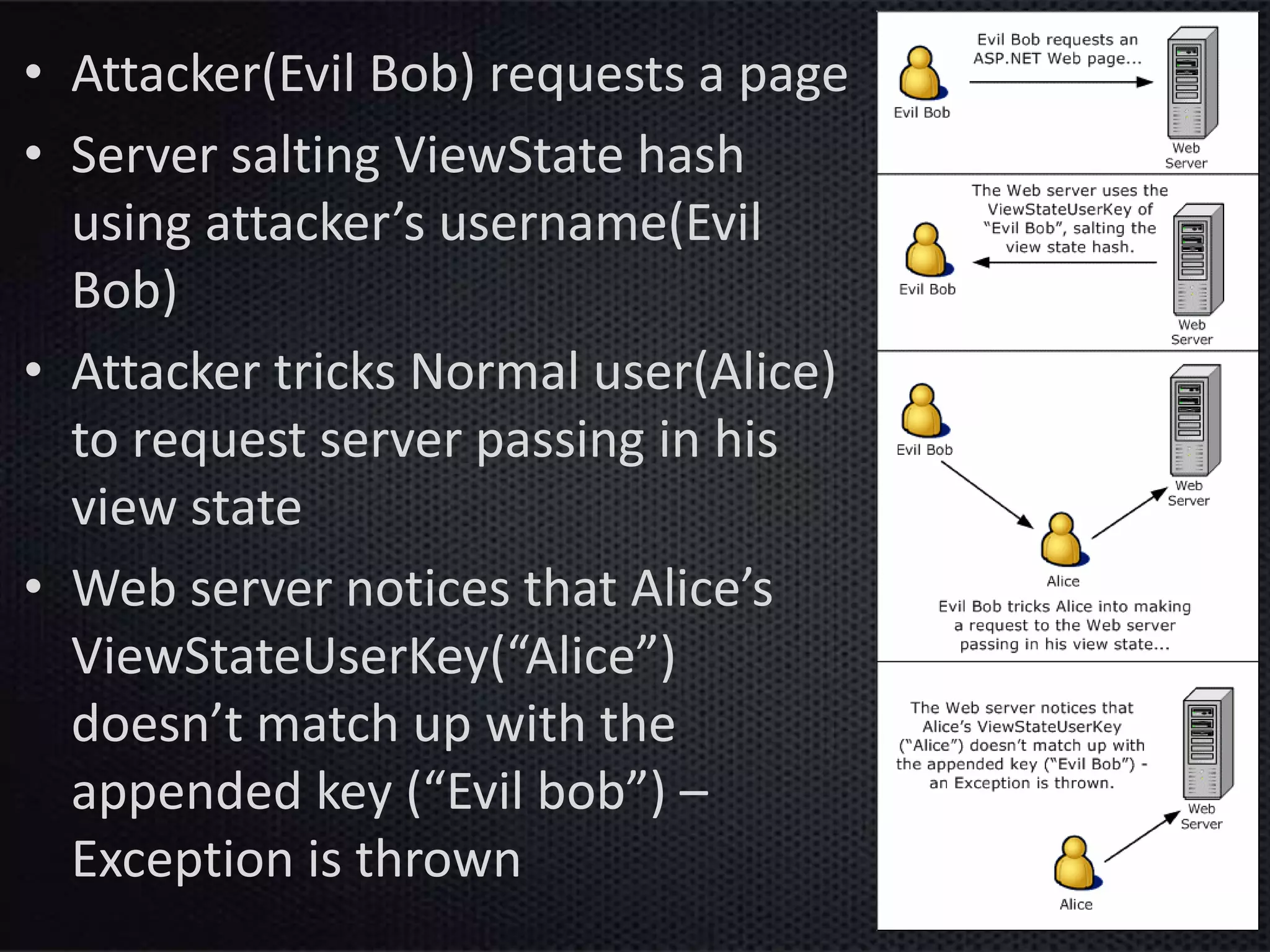
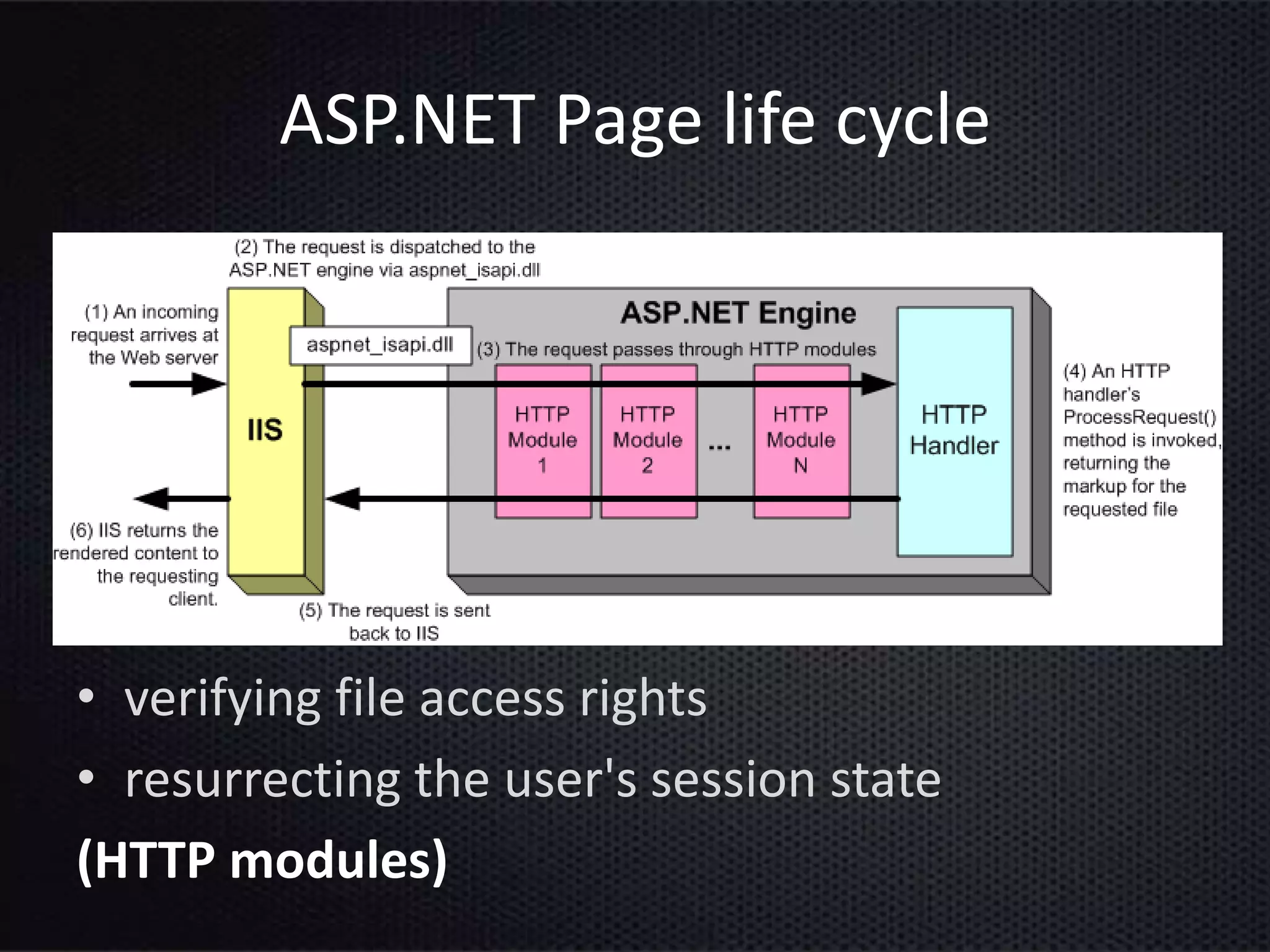
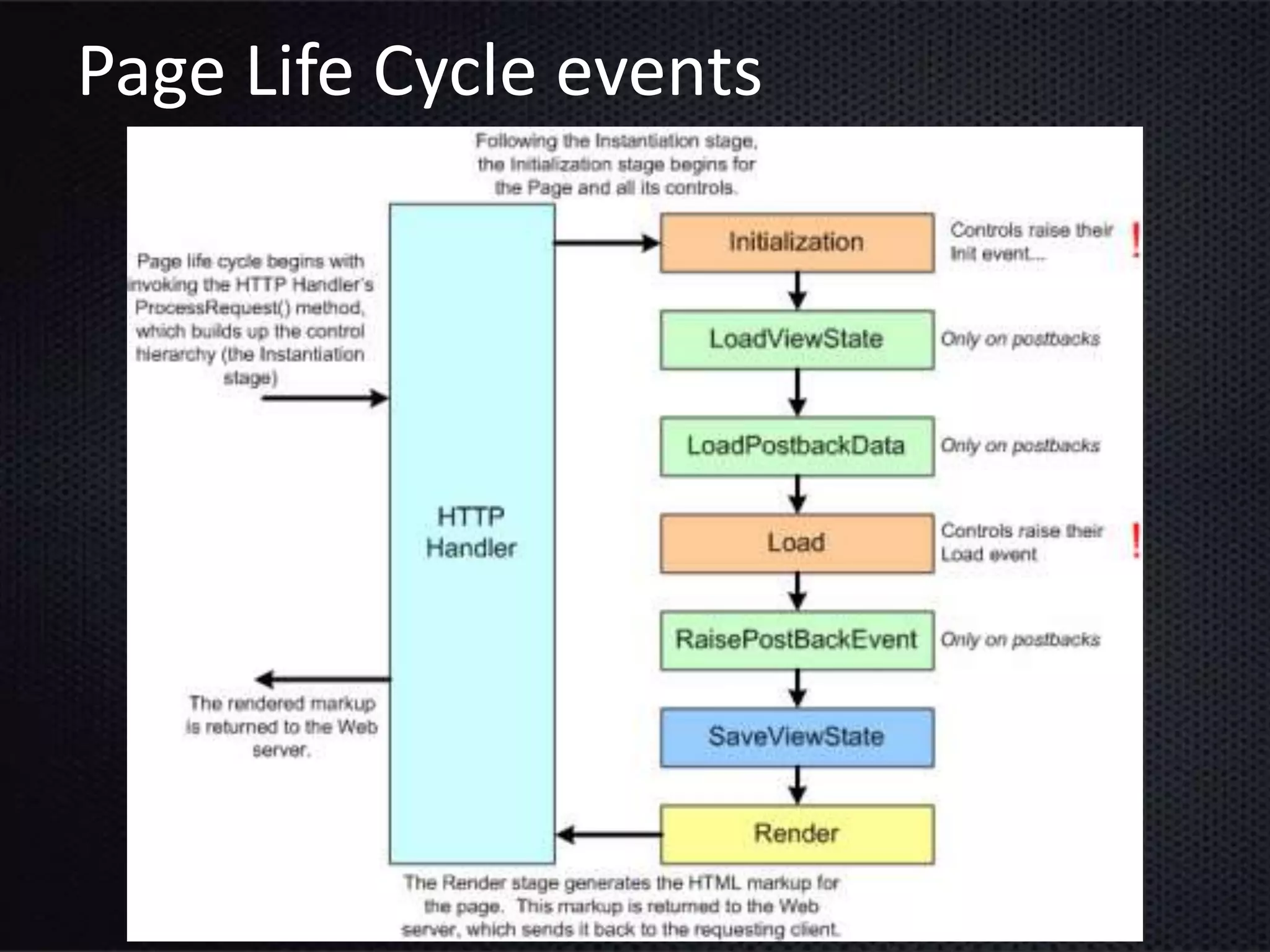
This document provides an introduction to ASP.NET ViewState. It discusses how ViewState is used to maintain state across postbacks in an HTTP protocol which is stateless. It describes where ViewState fits in the ASP.NET page lifecycle. It explains that ViewState persists state by storing name and value pairs in a base64 encoded string within a hidden form field. The document also covers best practices for using ViewState, including enabling and disabling it, potential security issues, and how to prevent tampering through encryption and using the ViewStateUserKey property.



![The View State Property
• Every control can stores its state
• Example
public string NavigateUrl
{
get {
string text = (string) ViewState["NavigateUrl"];
if (text != null)
return text;
else
return string.Empty;
}
set {
ViewState["NavigateUrl"] = value;
}
}
• whenever a control's property is read, the
control's ViewState is consulted](https://image.slidesharecdn.com/viewstate-101201022517-phpapp02/75/Introduction-to-ASP-Net-Viewstate-6-2048.jpg)
![Storing Information in the Page's
ViewState Property
• persist page-specific and user-specific
information across postbacks
• Code would look like
– ViewState[keyName] = value
• example - creating a pageable, sortable DataGrid
• sort expression must be persisted across
postbacks](https://image.slidesharecdn.com/viewstate-101201022517-phpapp02/75/Introduction-to-ASP-Net-Viewstate-7-2048.jpg)