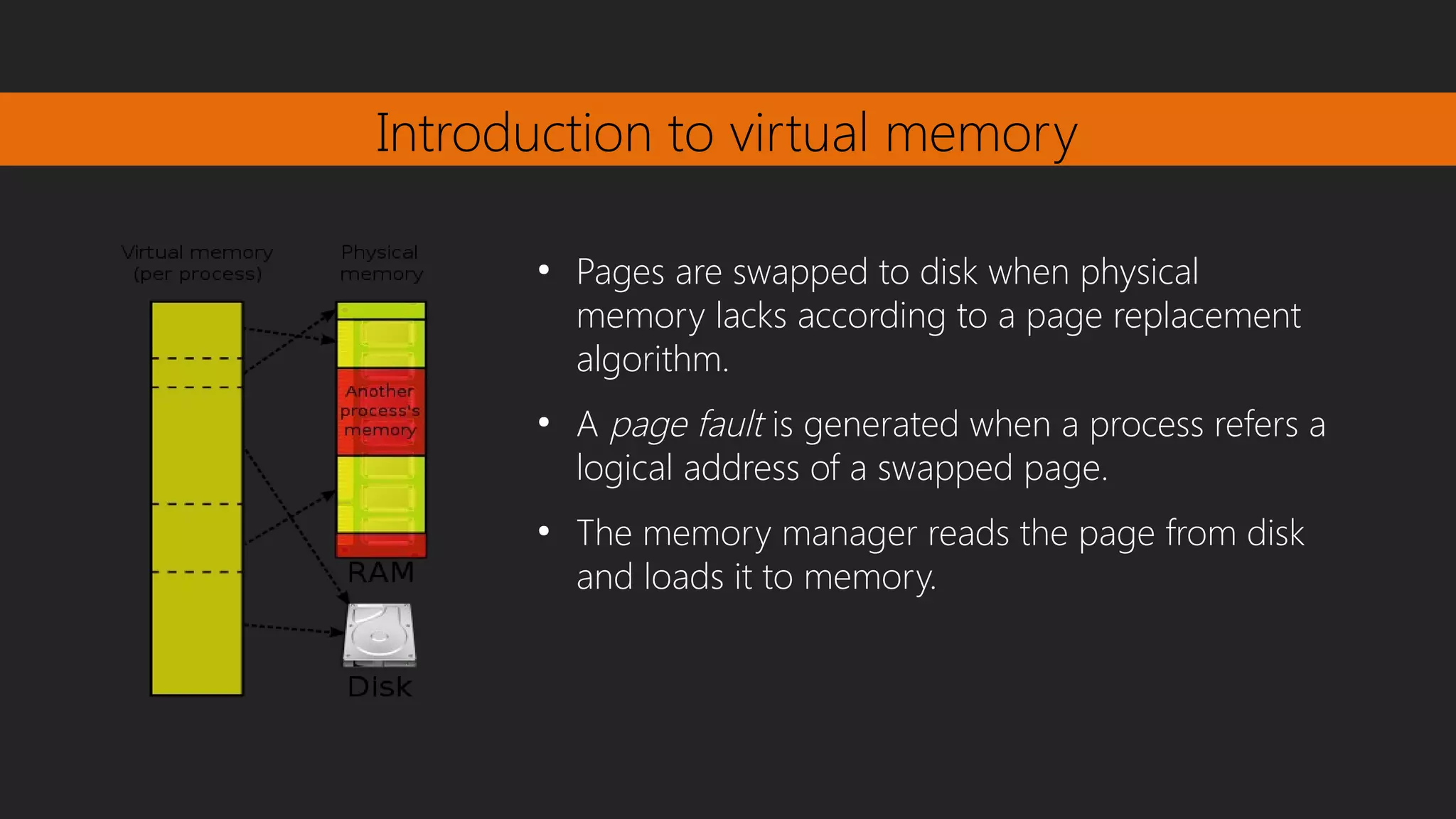
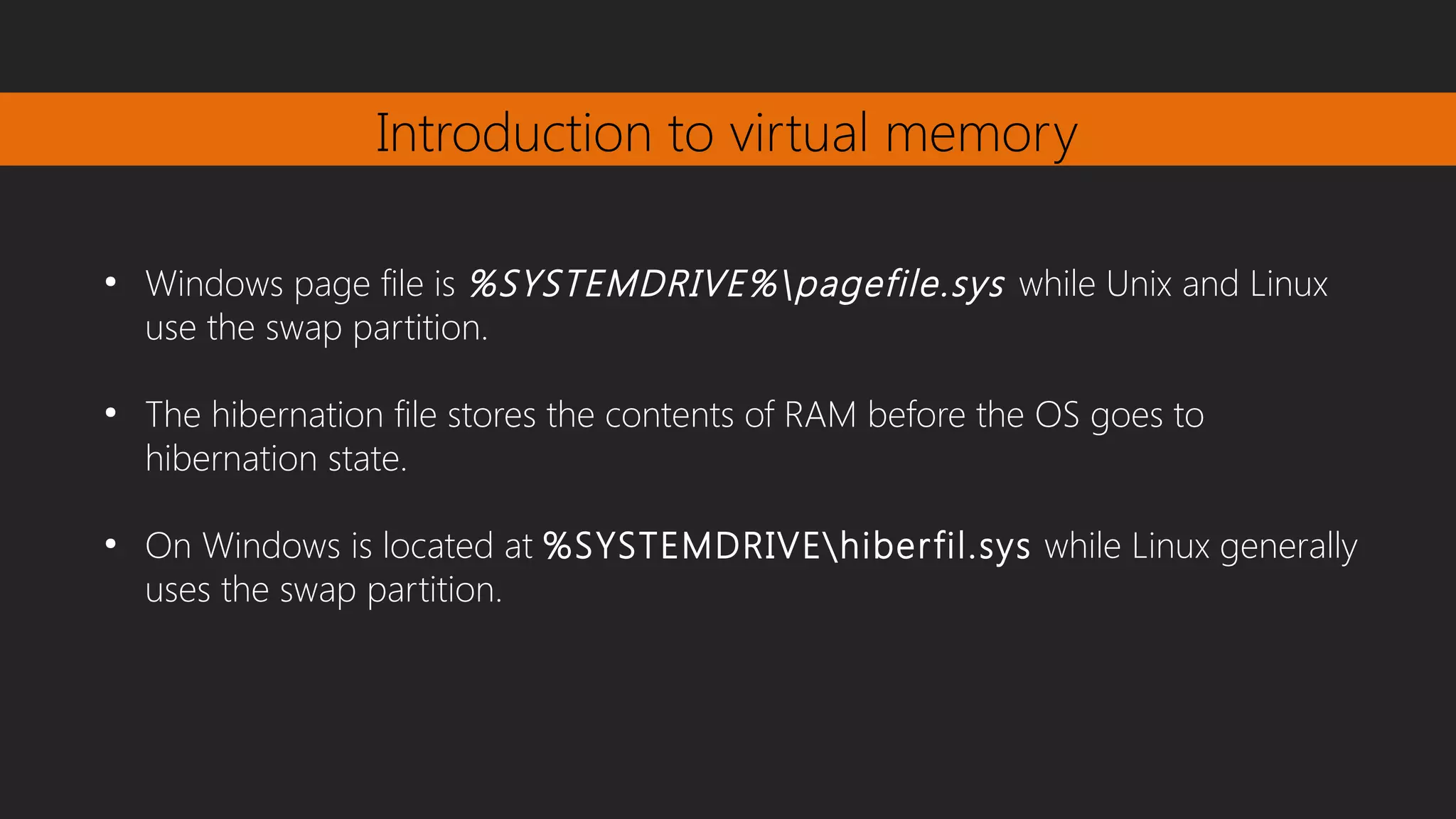
This document discusses memory forensics, focusing on acquiring and analyzing system memory using tools like the volatility framework. It covers concepts such as virtual memory management, paging, and the importance of memory forensics in investigating intrusions or malware infections. Additionally, it explains how virtual memory maps logical addresses to physical memory and addresses page replacement mechanisms.