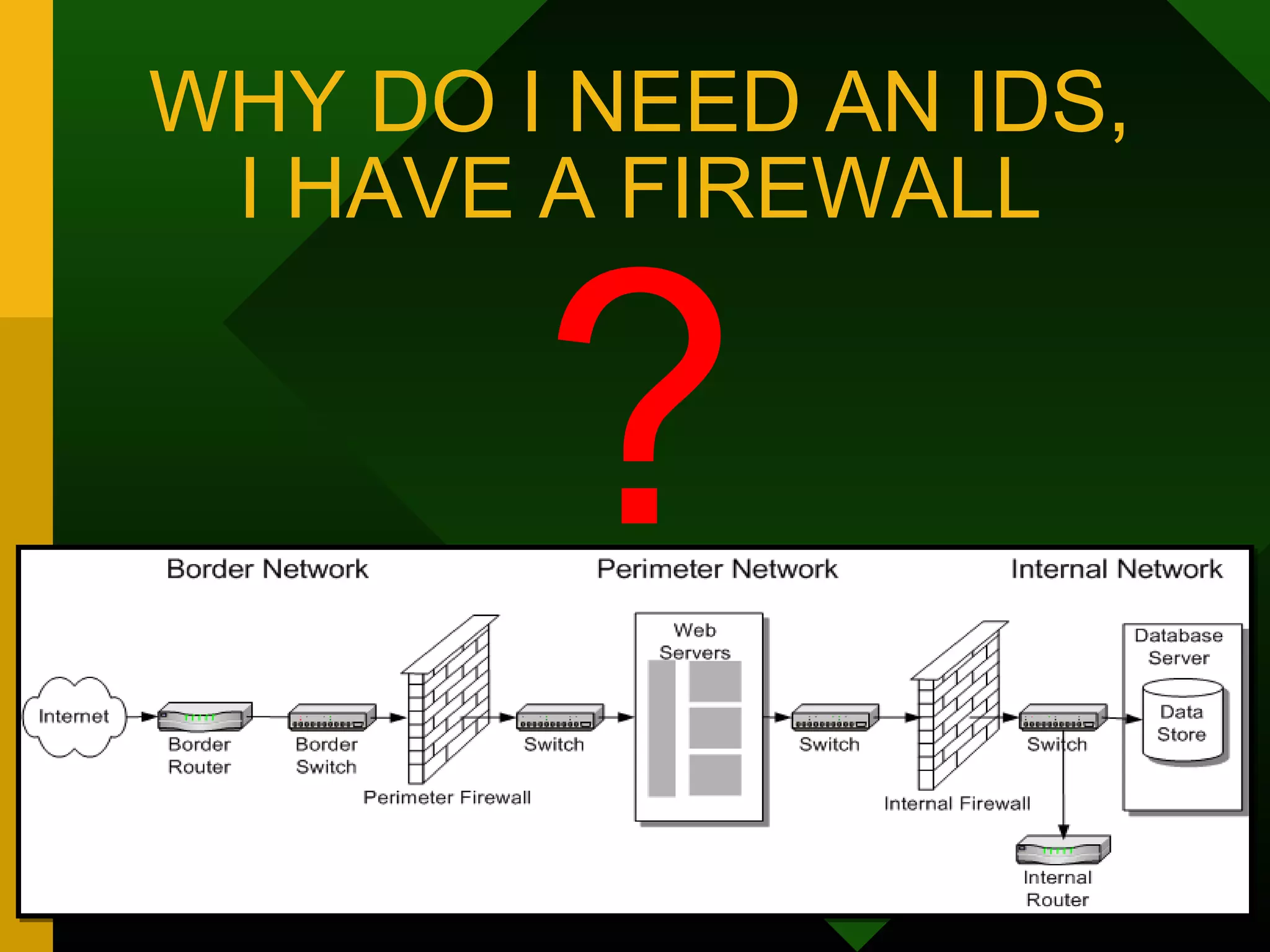
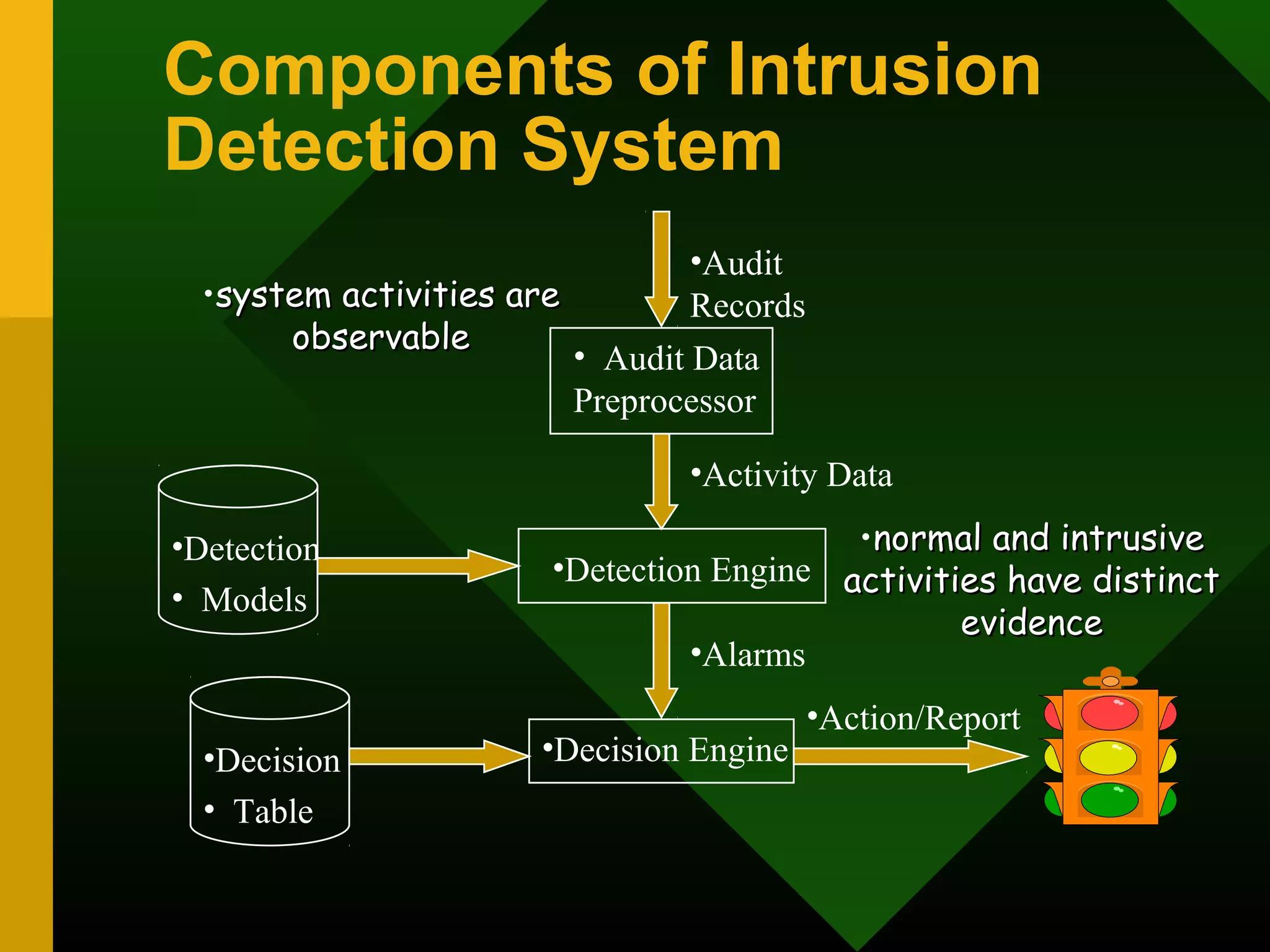
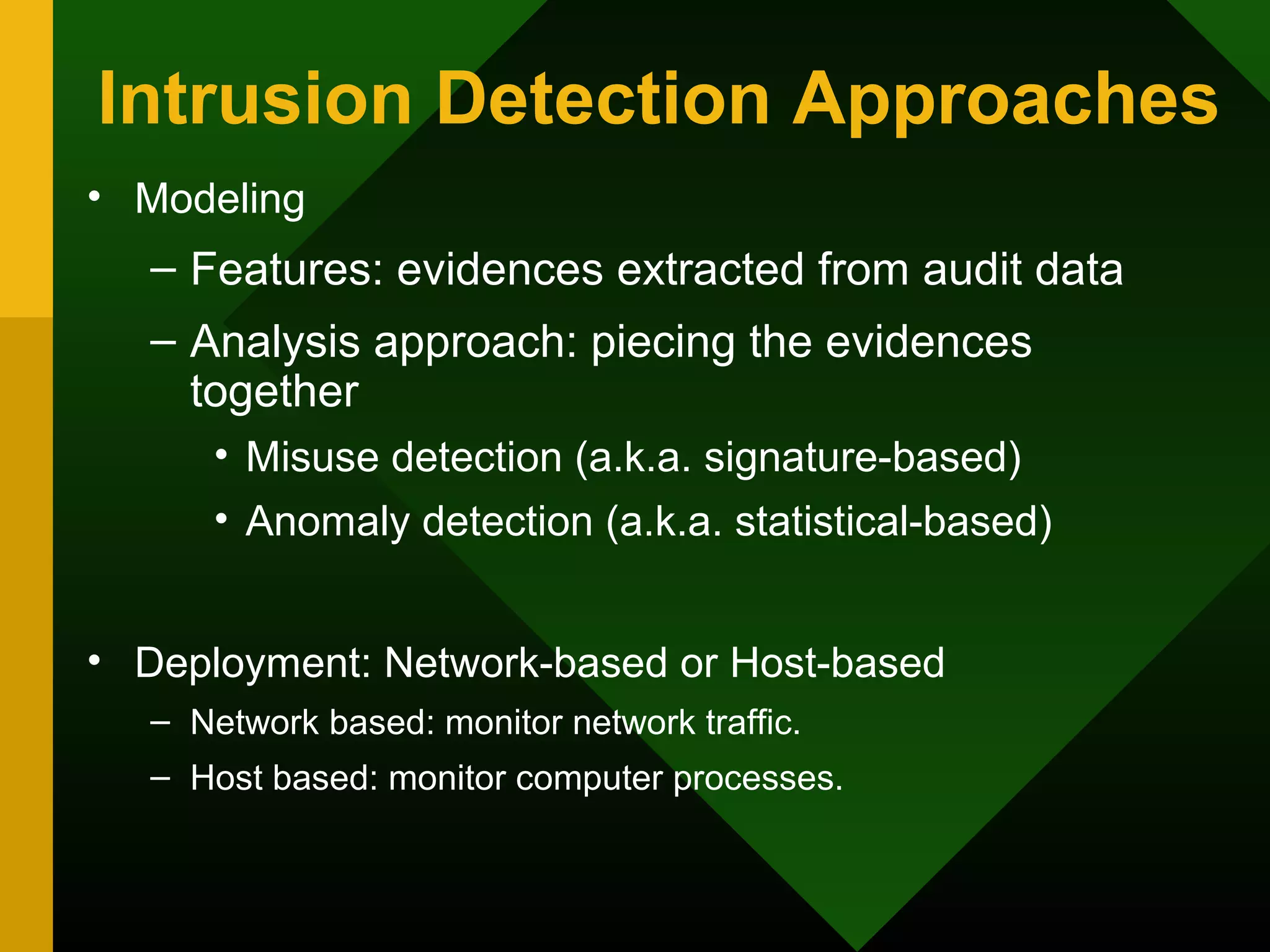
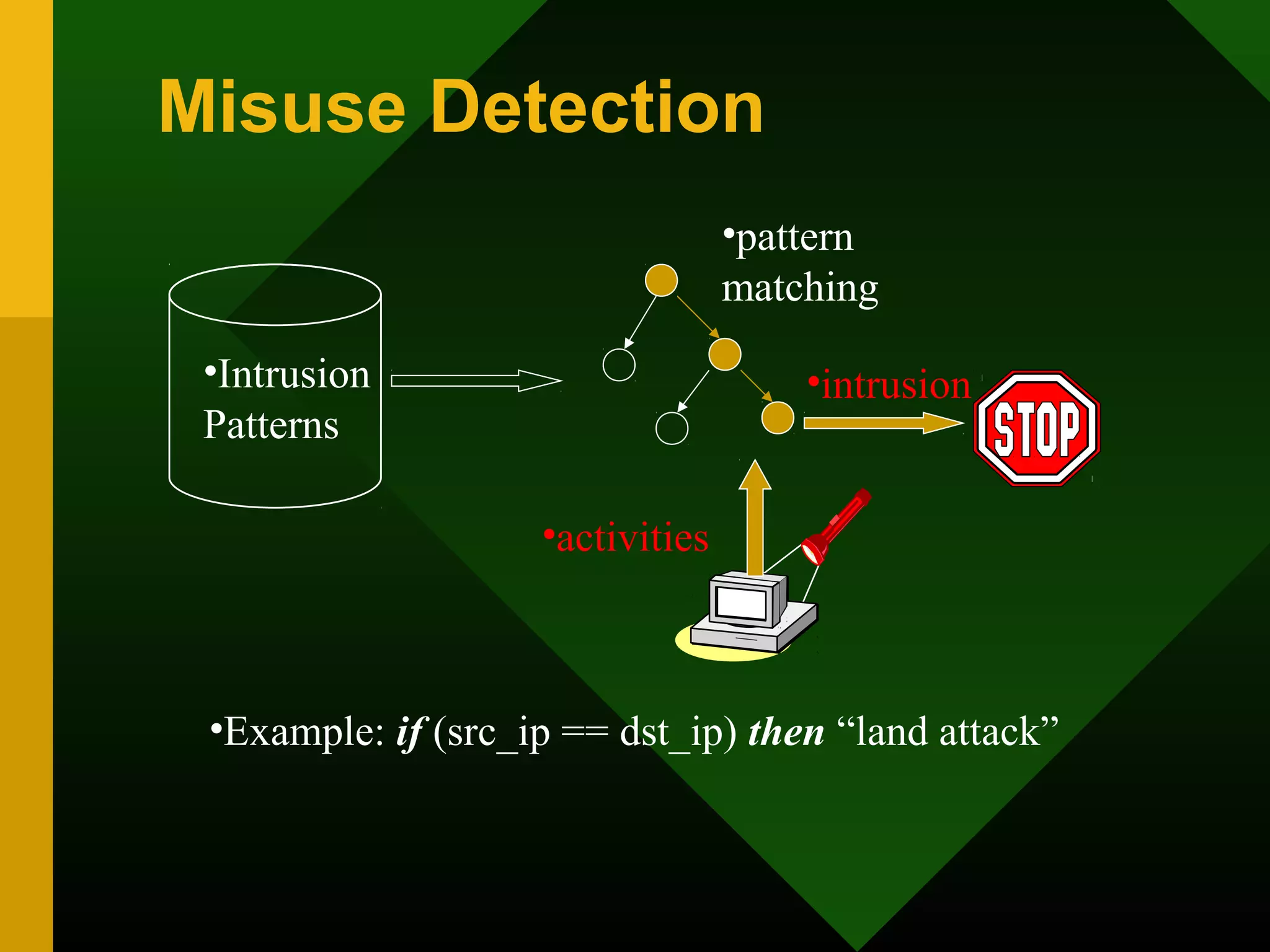
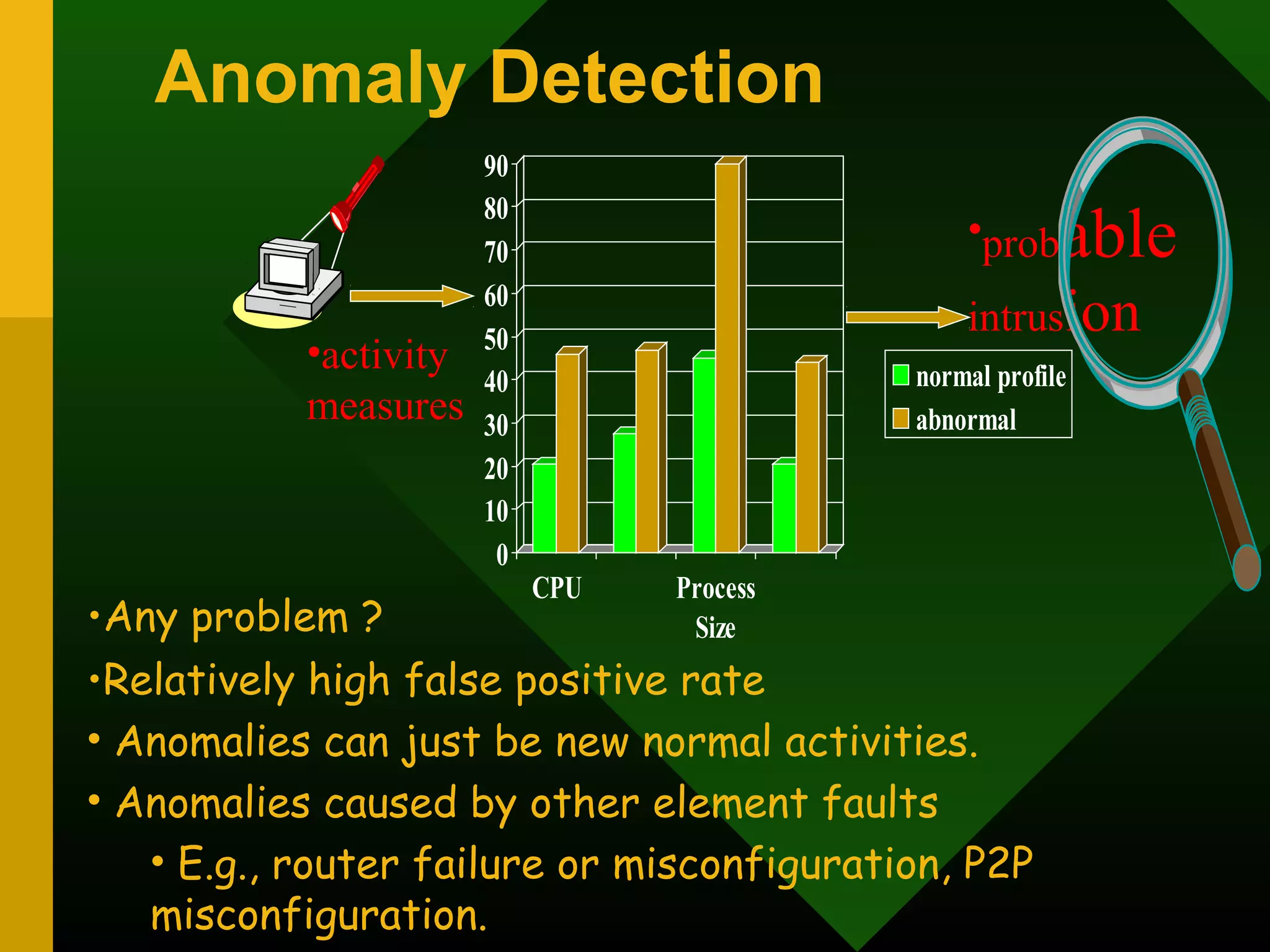
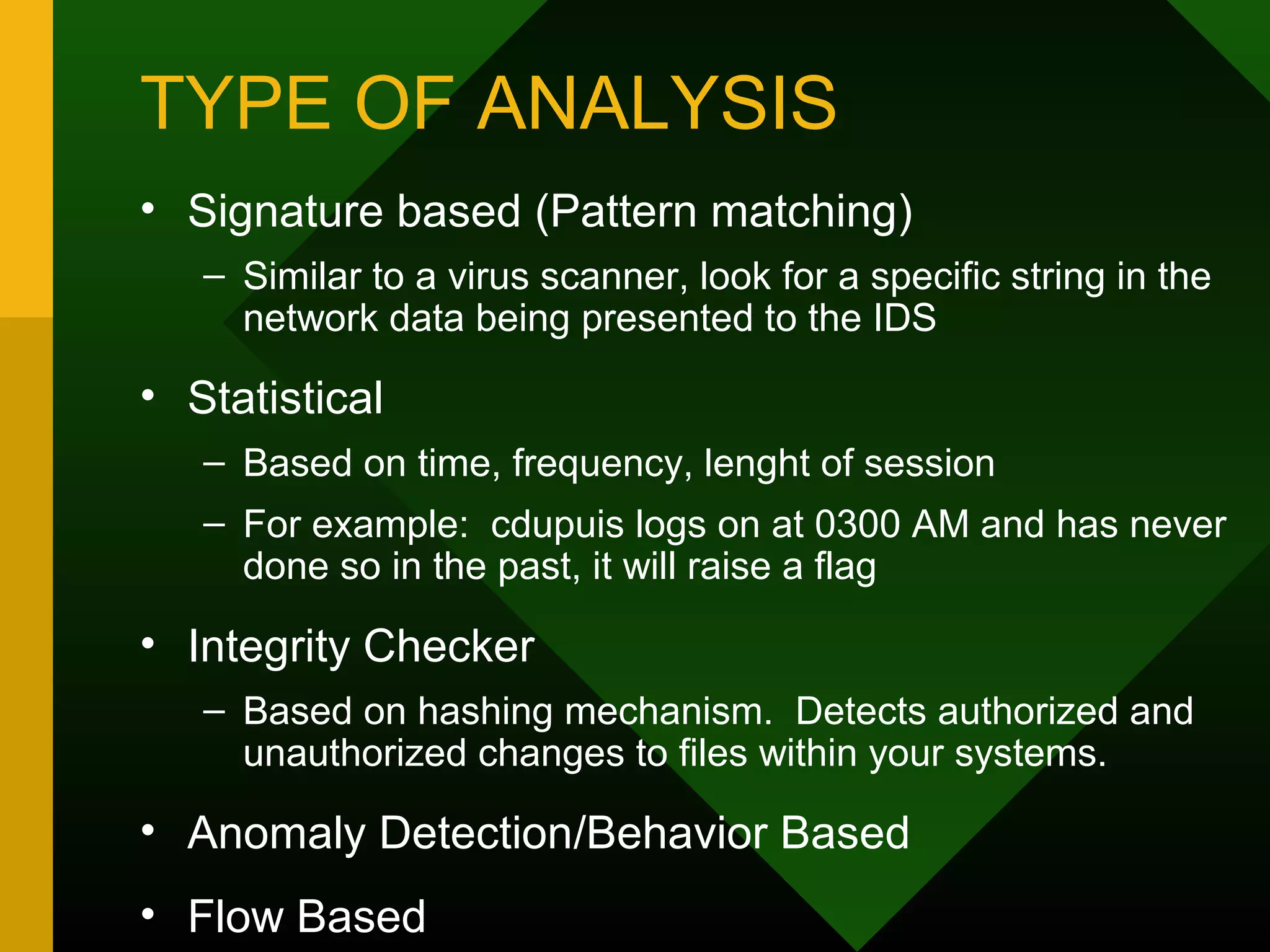
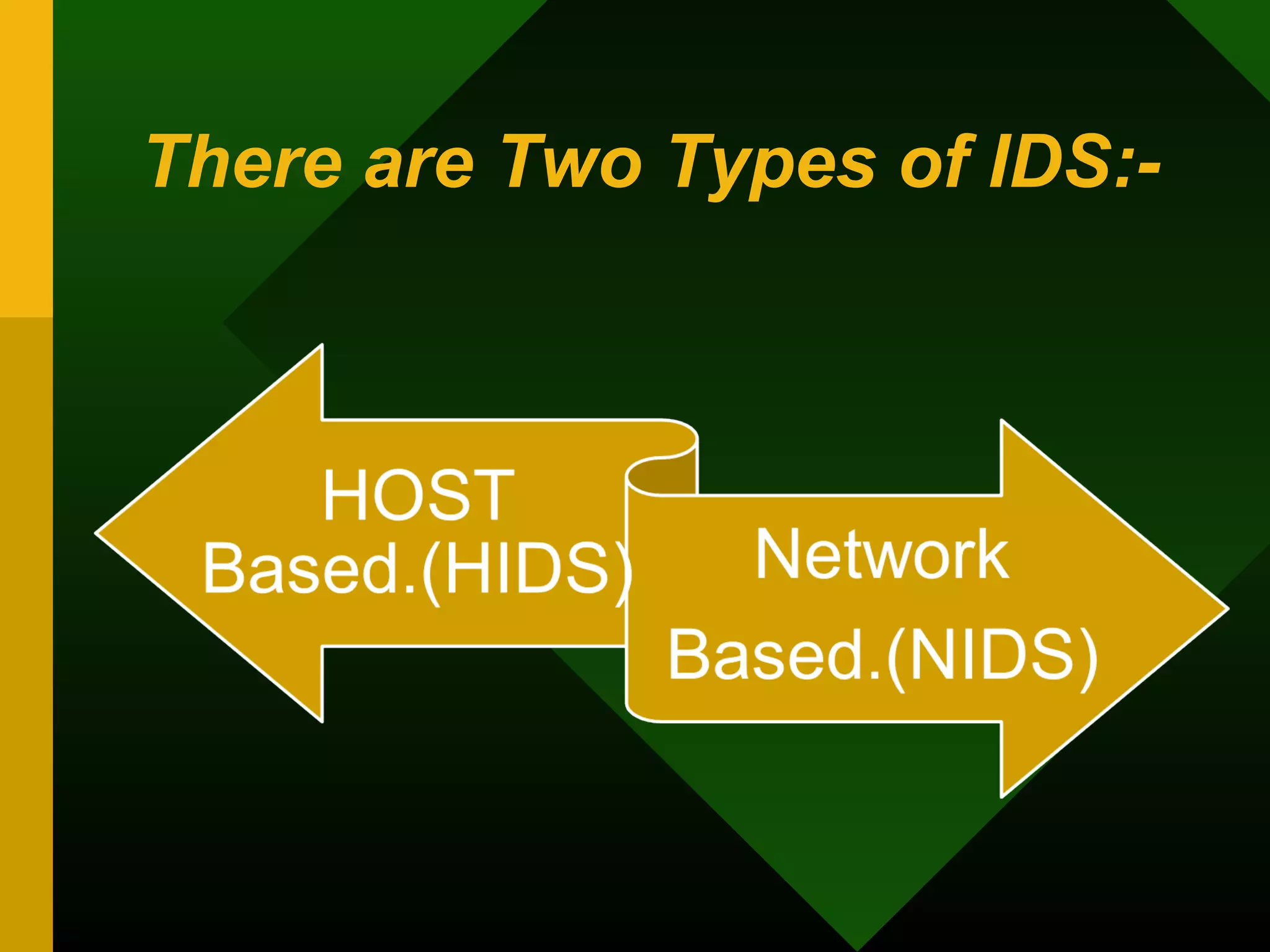
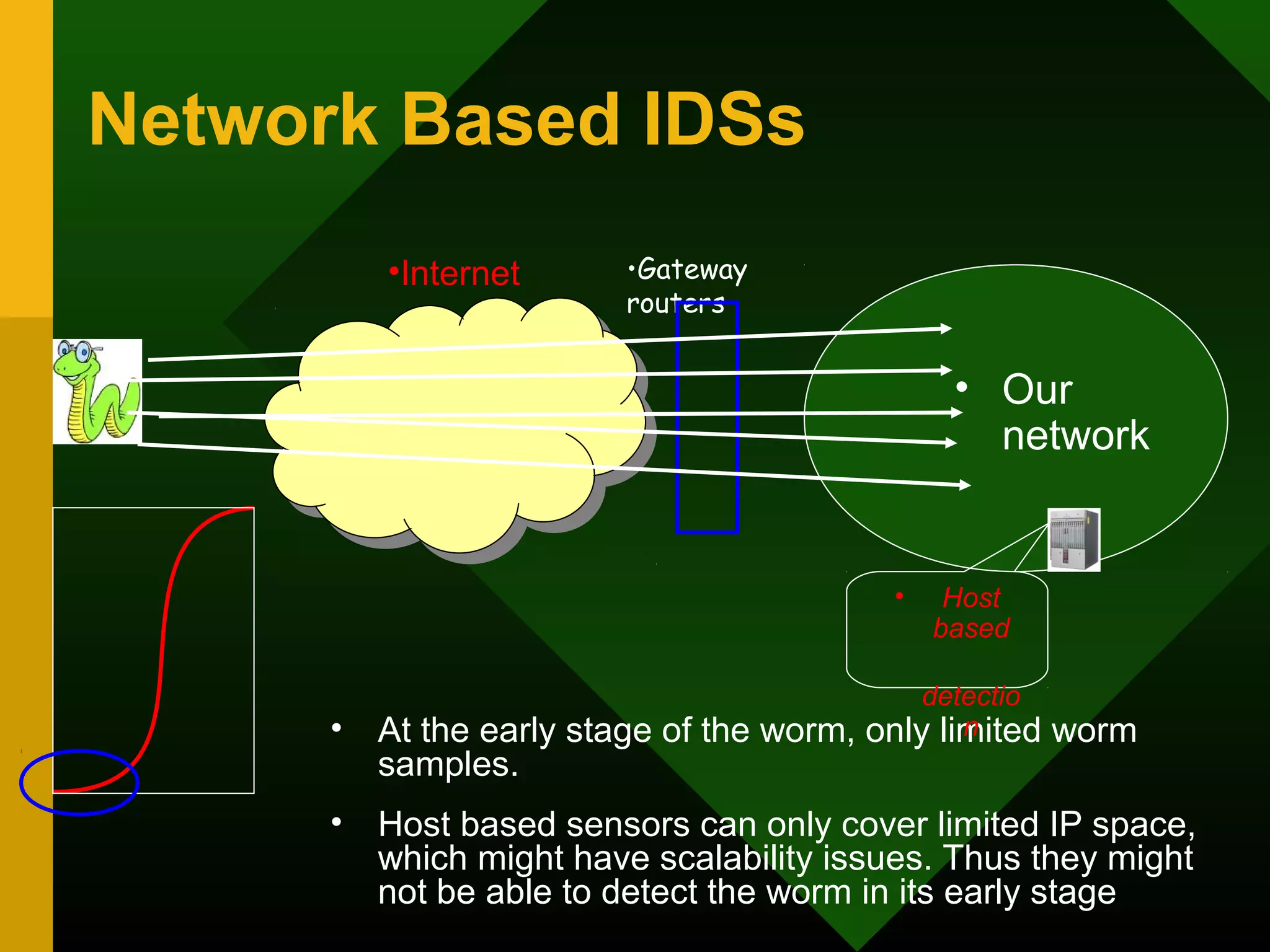
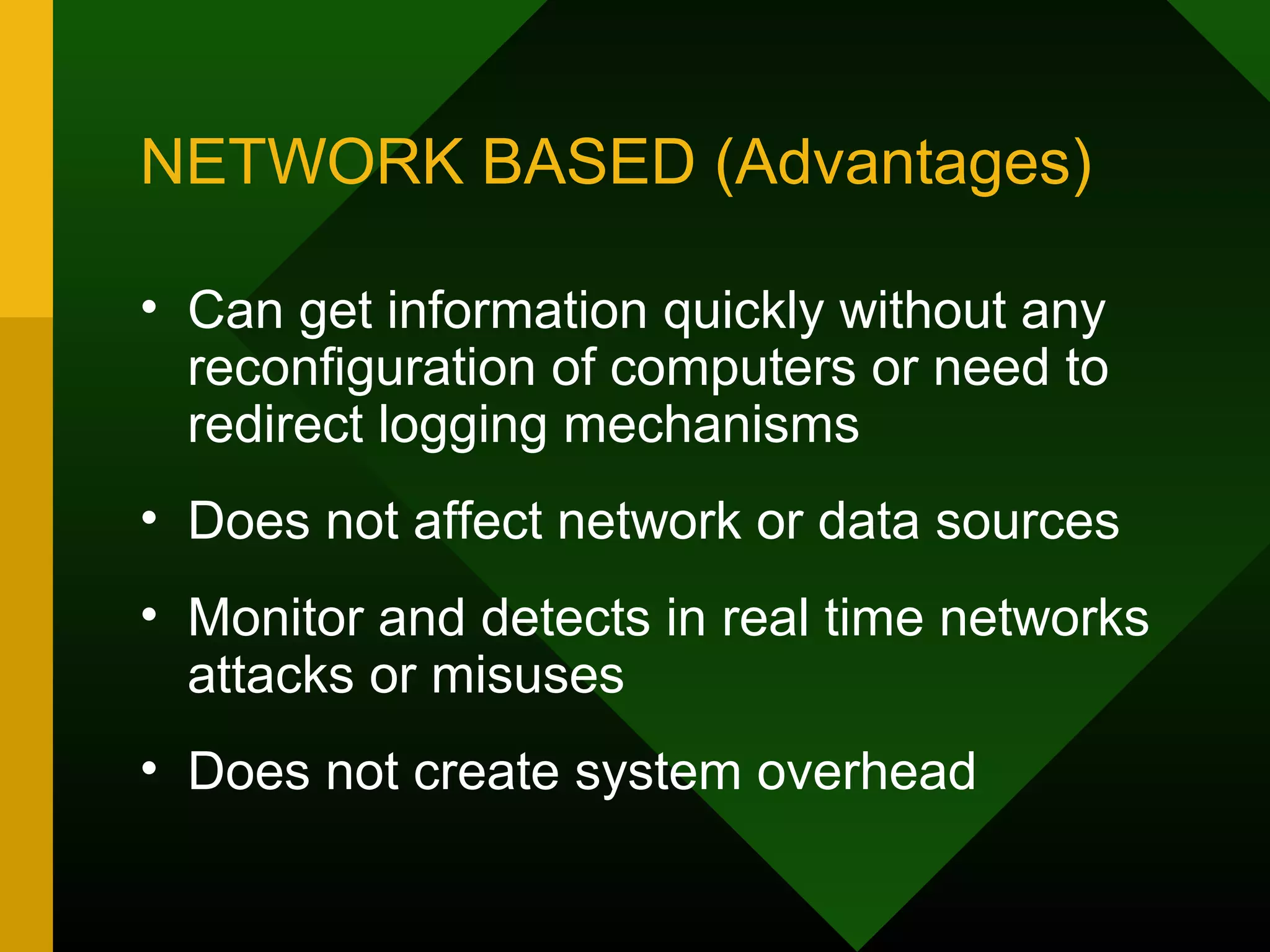
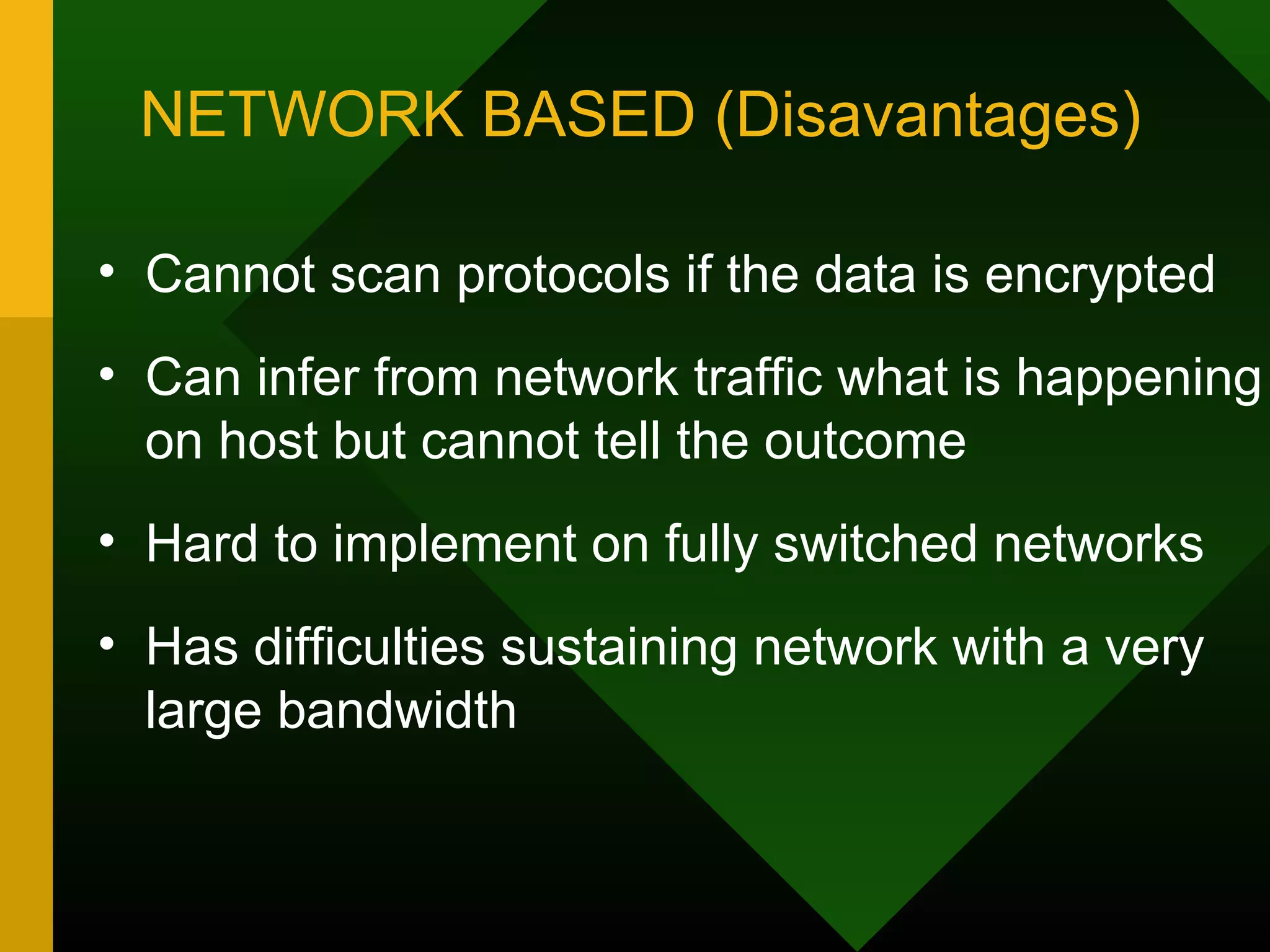
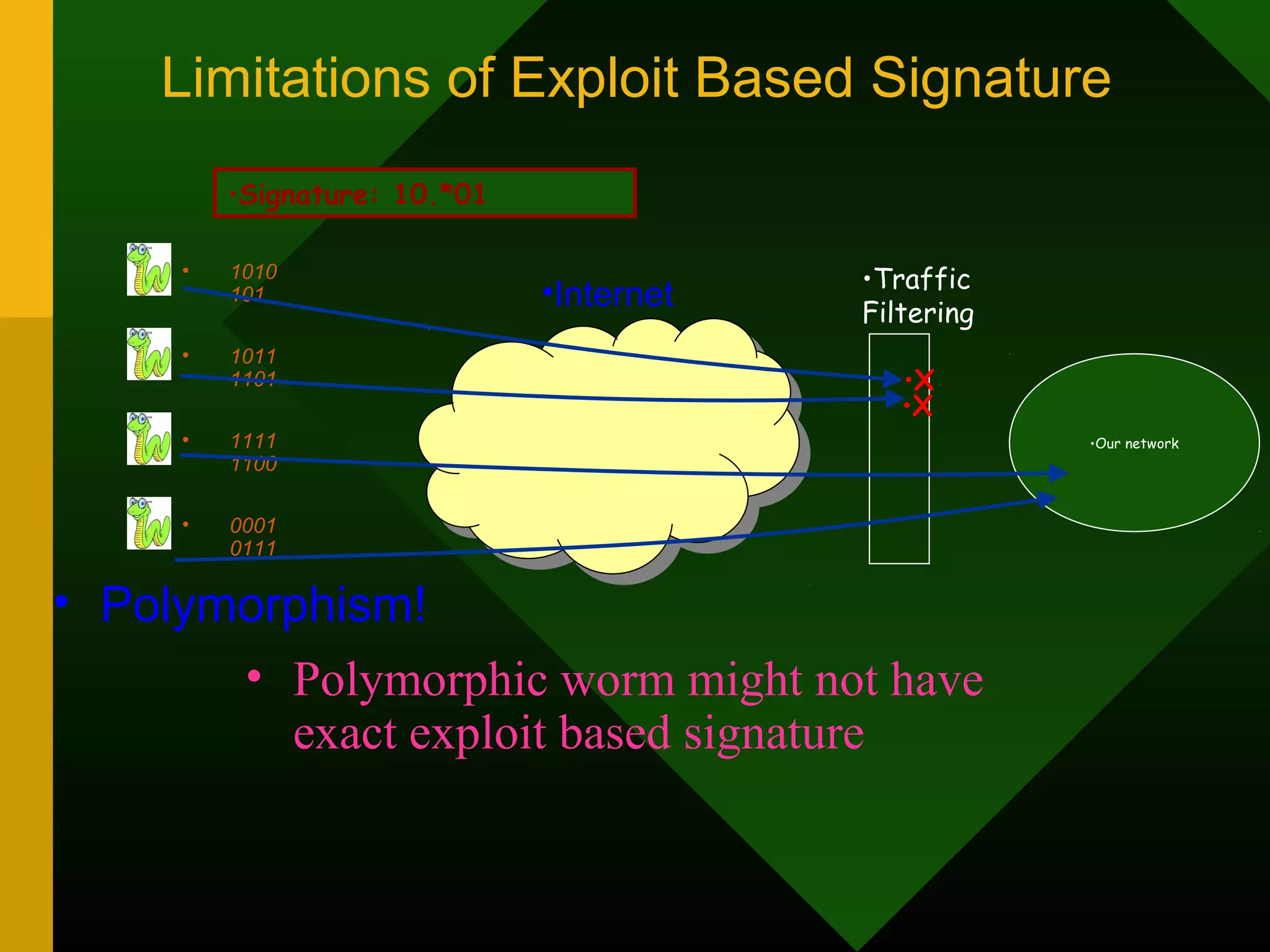
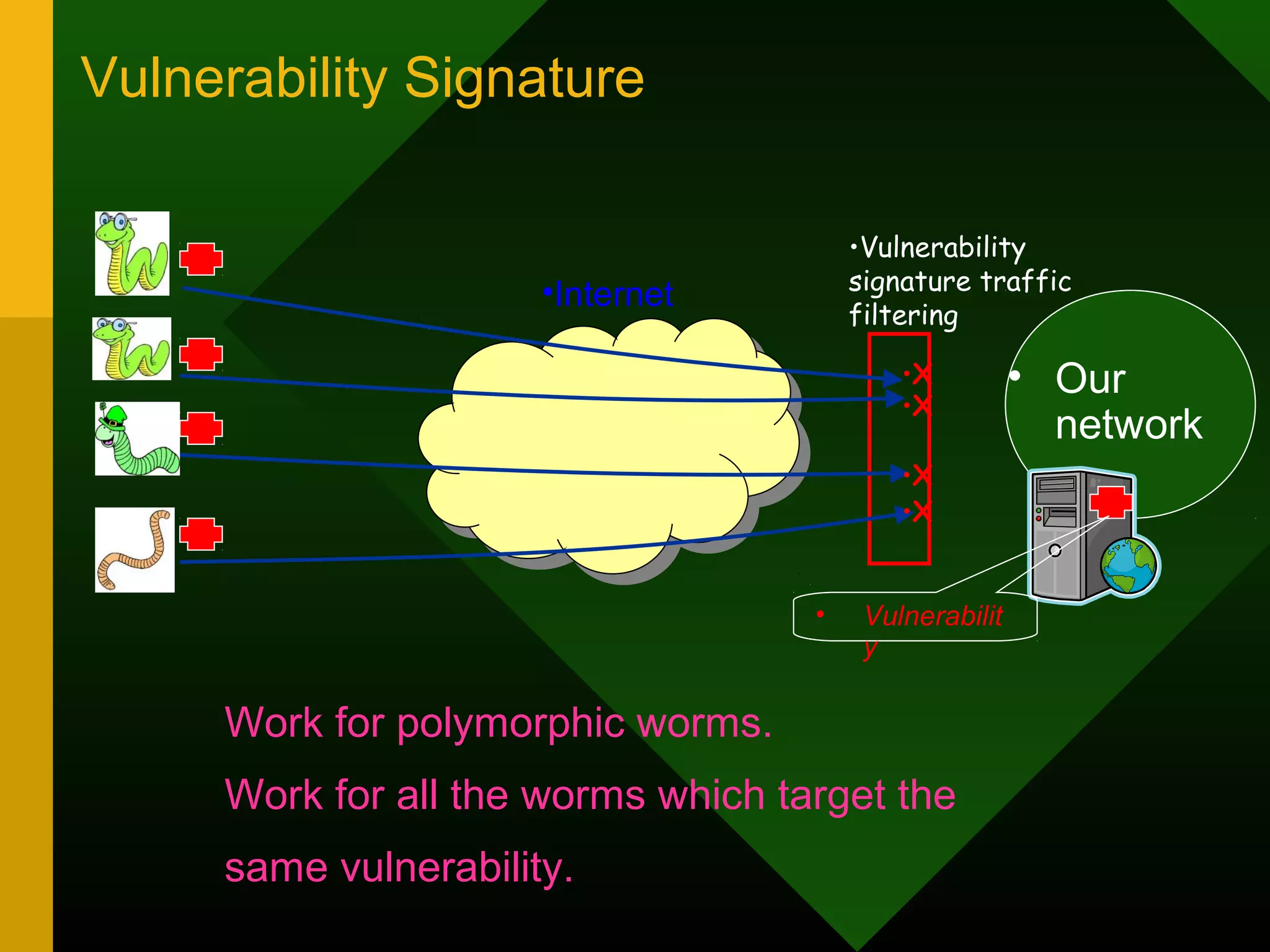
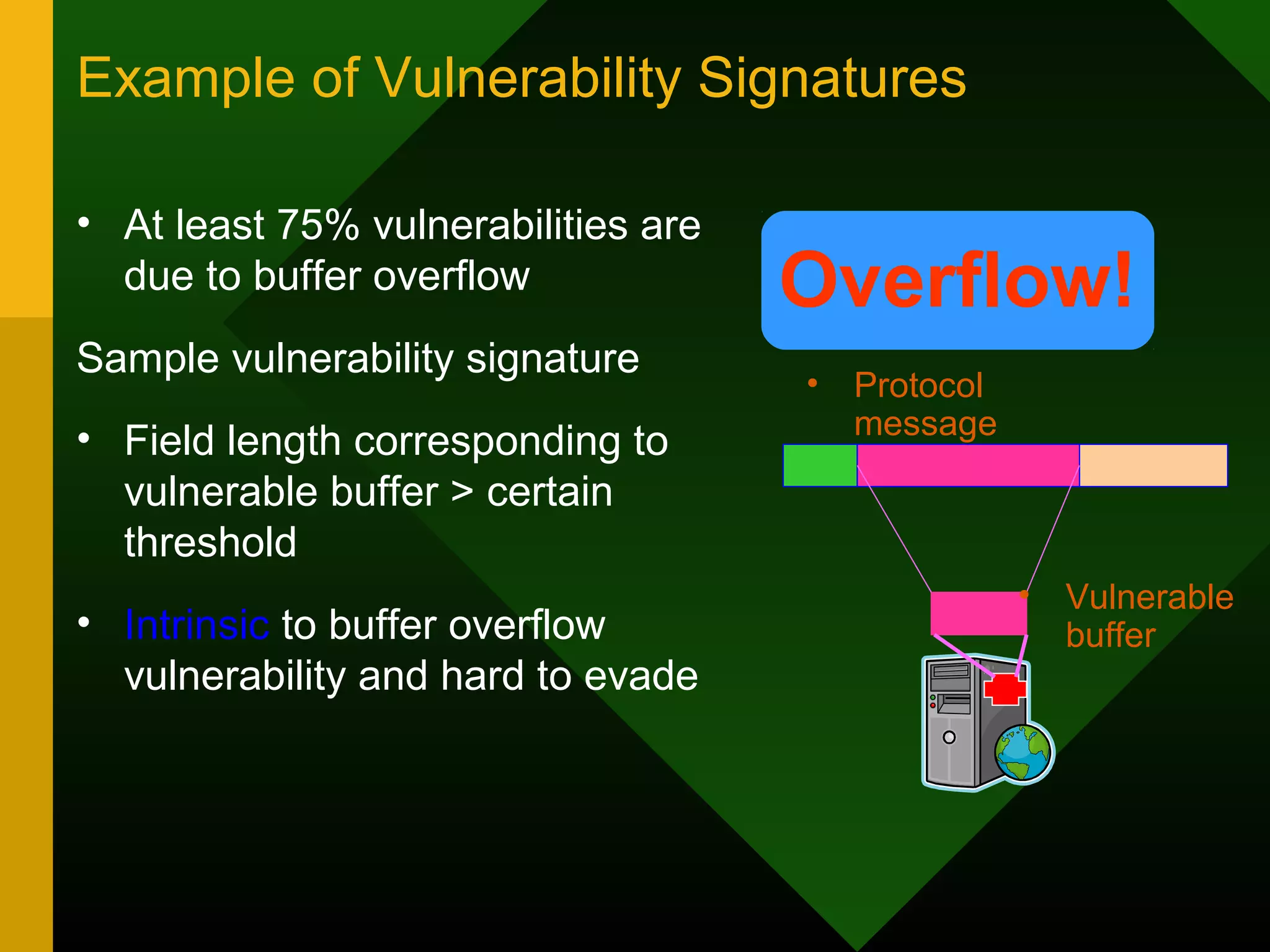
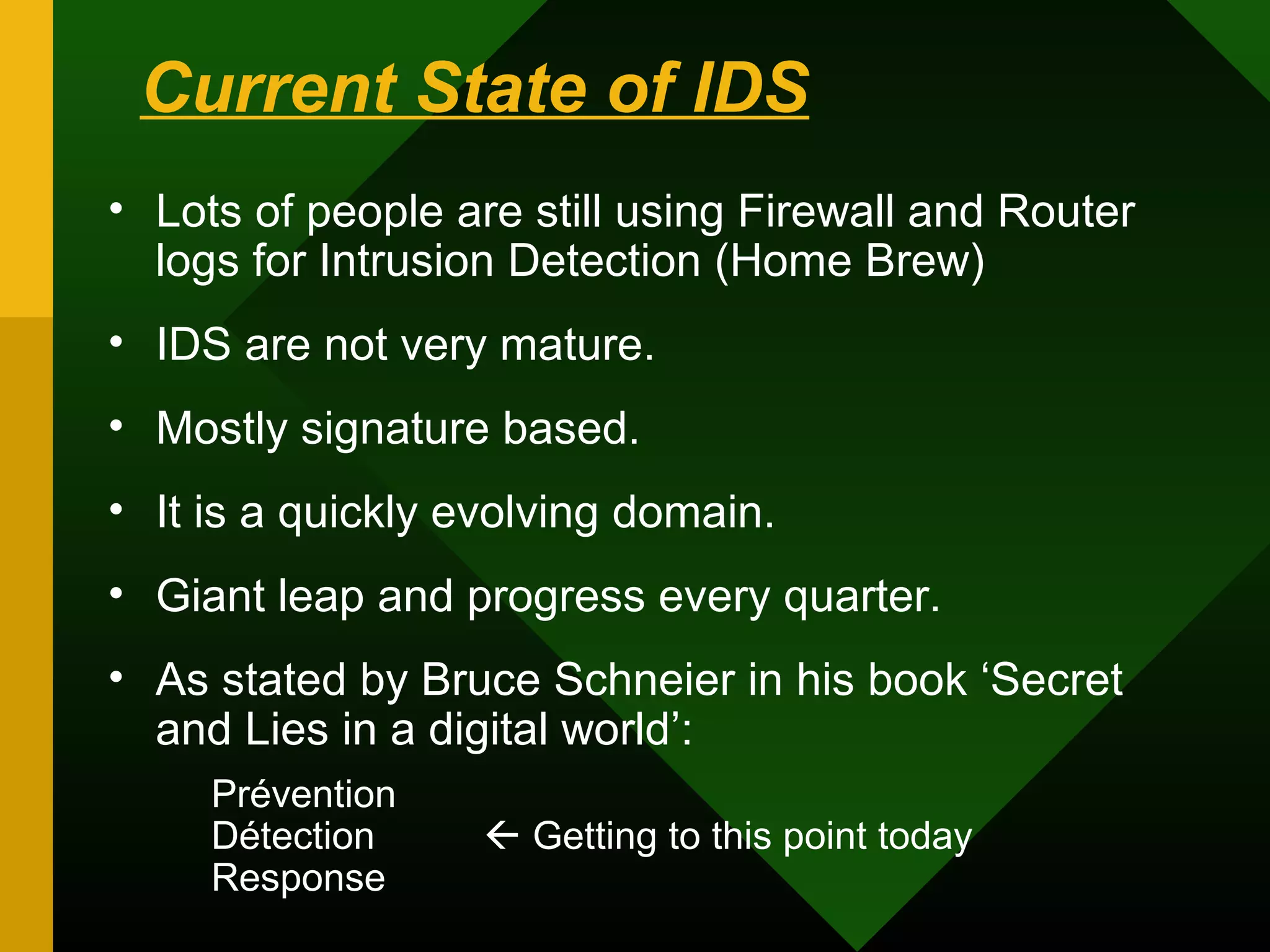
This document discusses intrusion detection systems (IDS). It defines intrusion, intrusion detection, and intrusion prevention. It explains the components of an IDS including audit data, detection models, and detection and decision engines. It describes misuse detection using signatures and anomaly detection using statistical analysis. It also discusses host-based and network-based IDS, their advantages and disadvantages, and limitations of exploit-based signatures. The document emphasizes the importance of selecting and properly deploying the right IDS for an organization's needs.