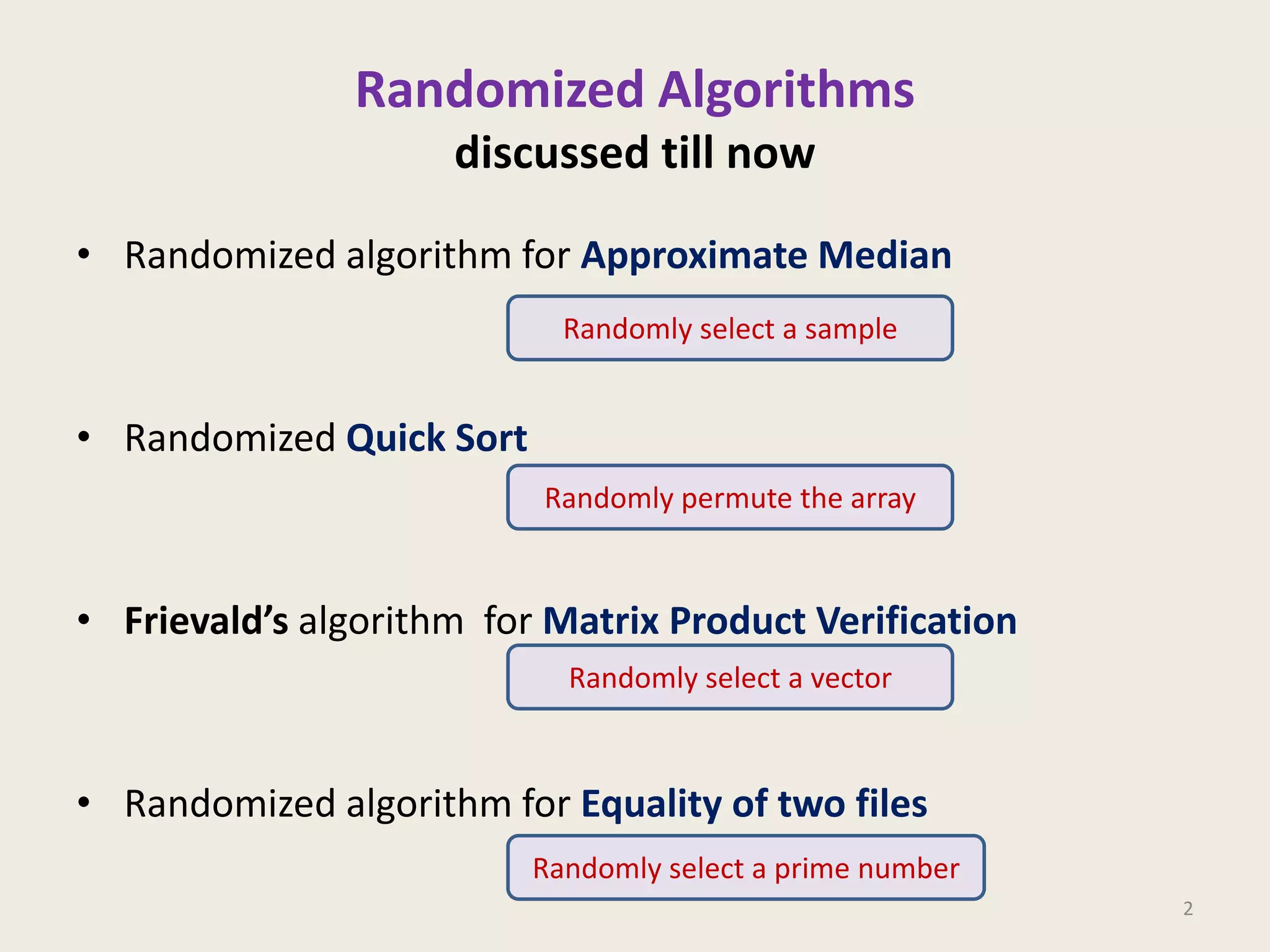
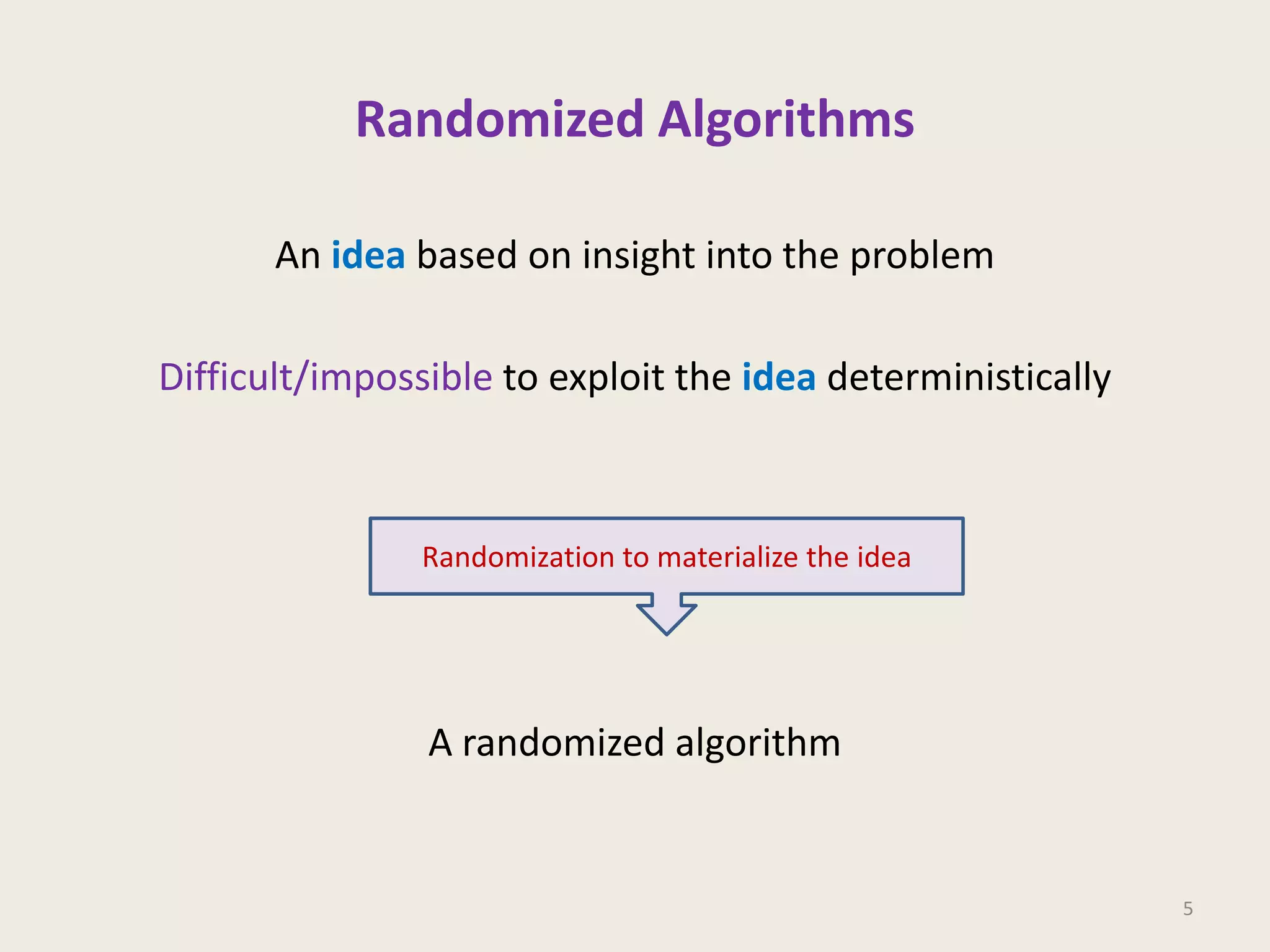
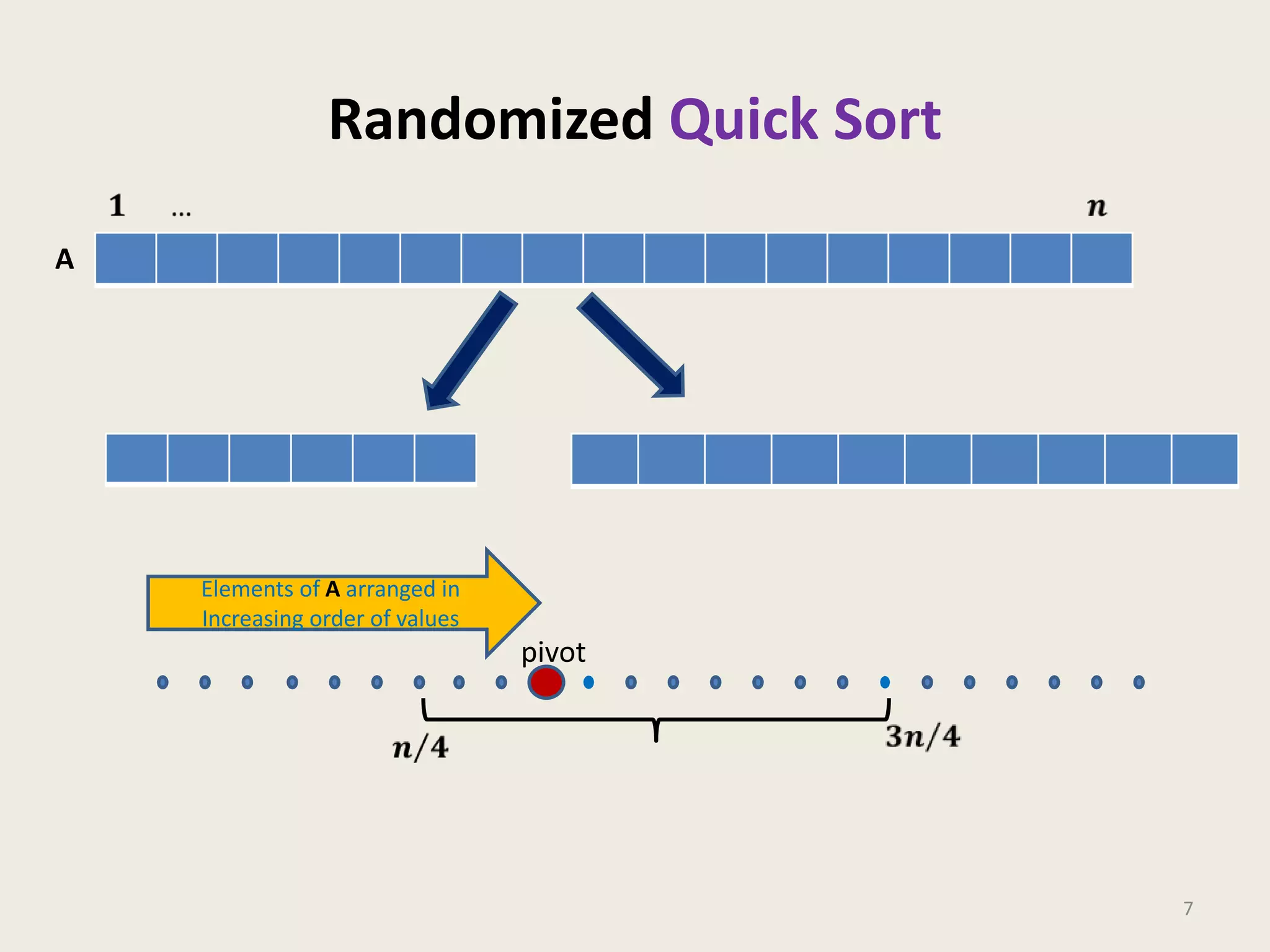
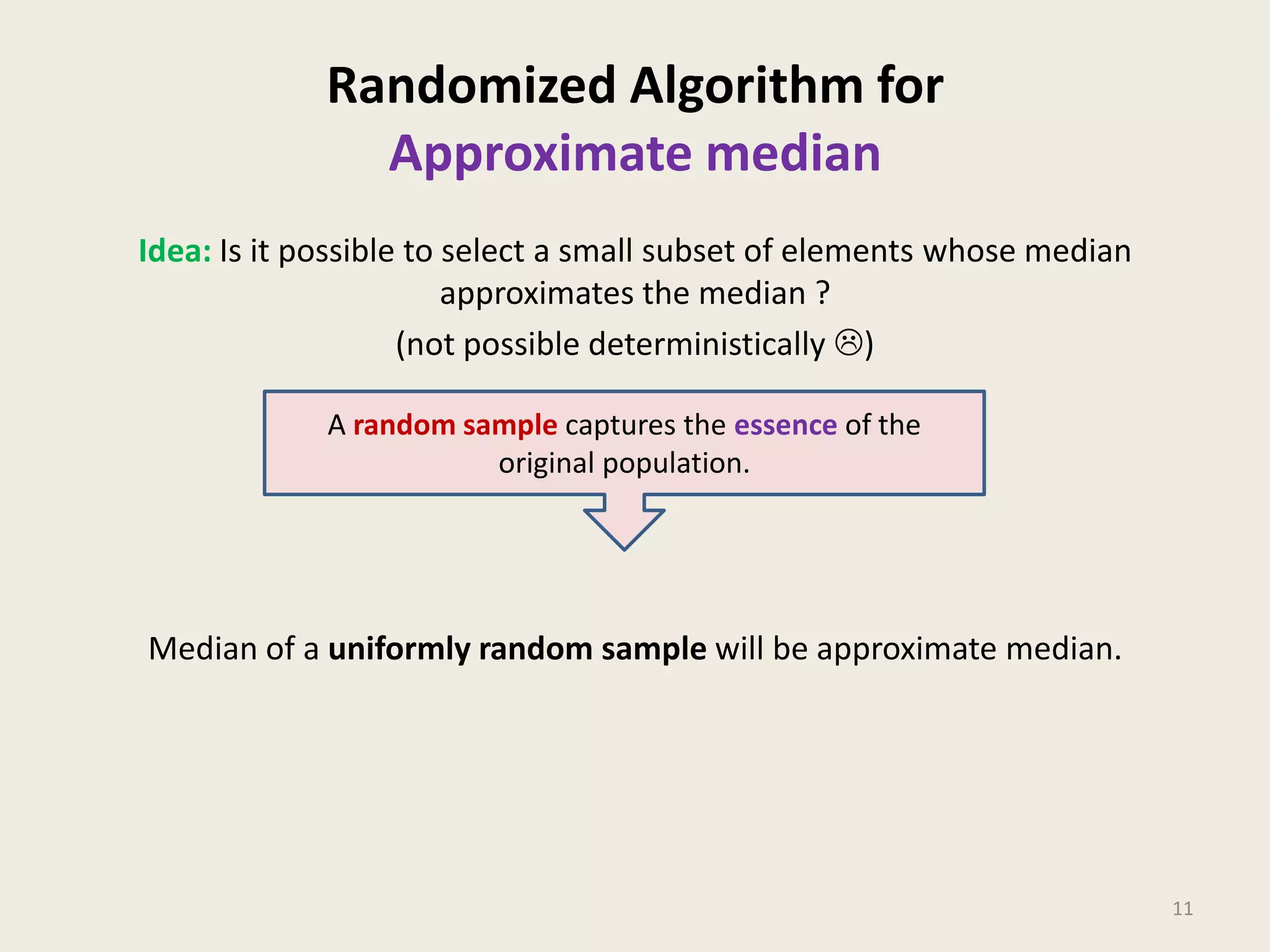
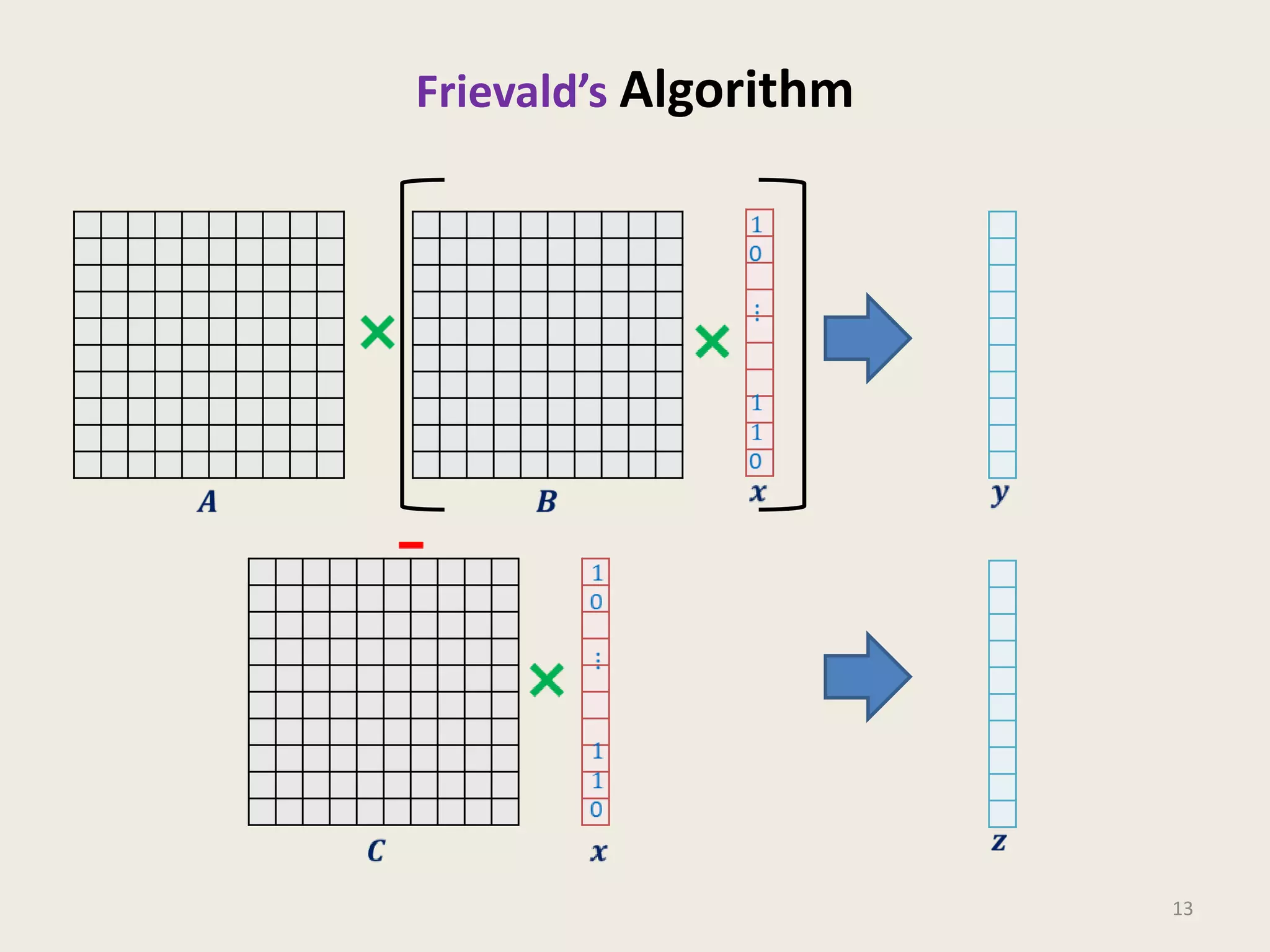
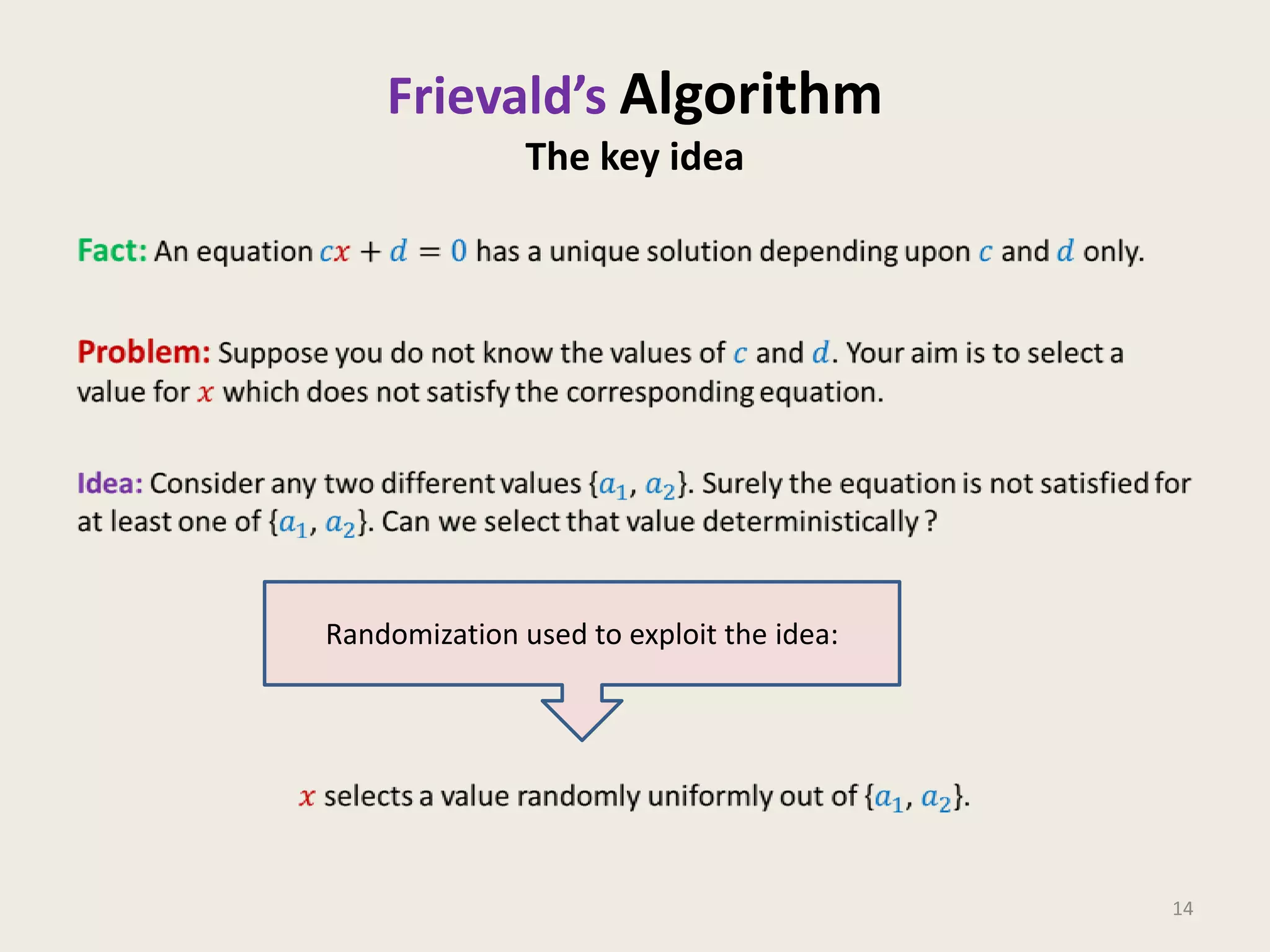
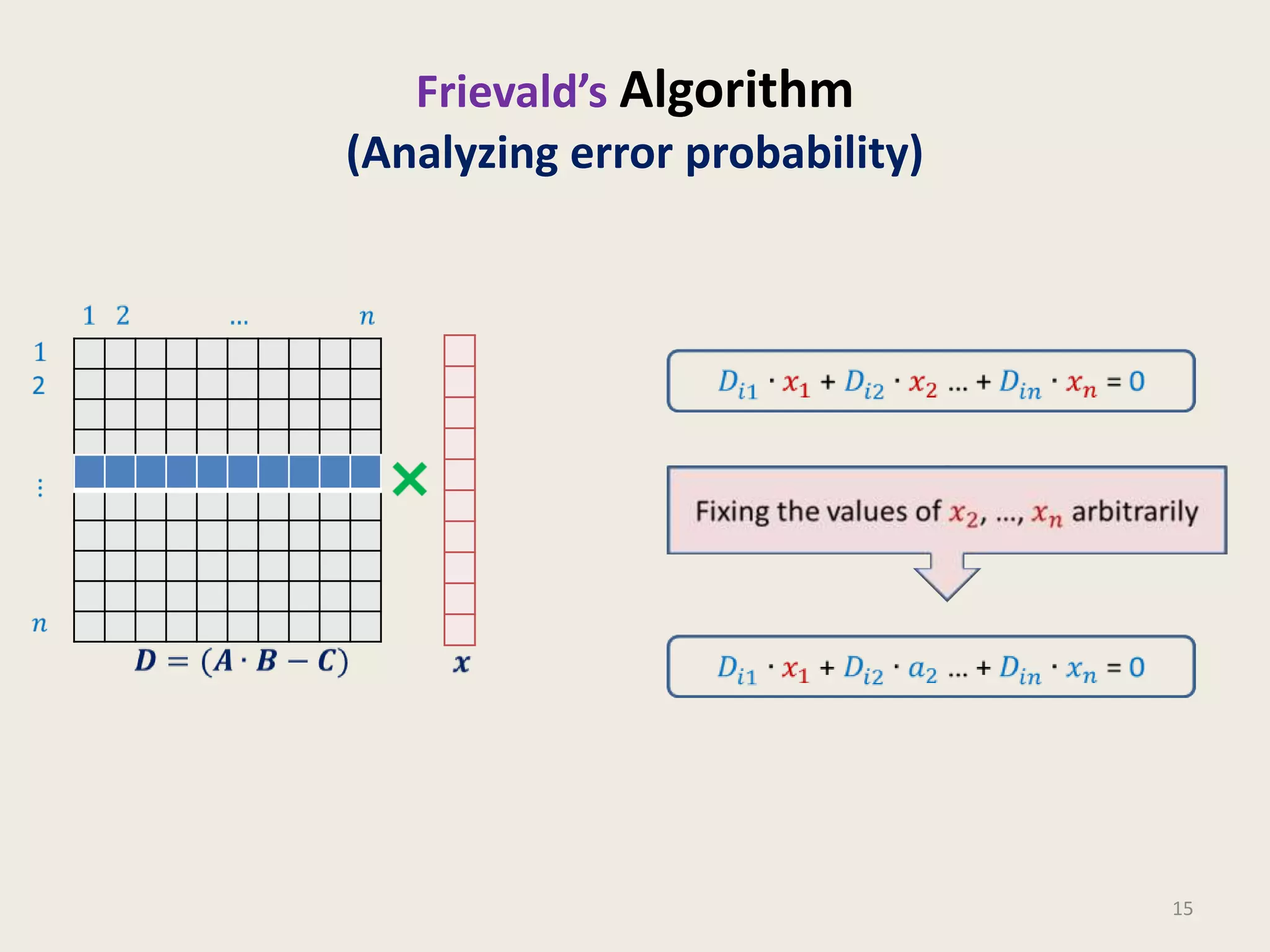
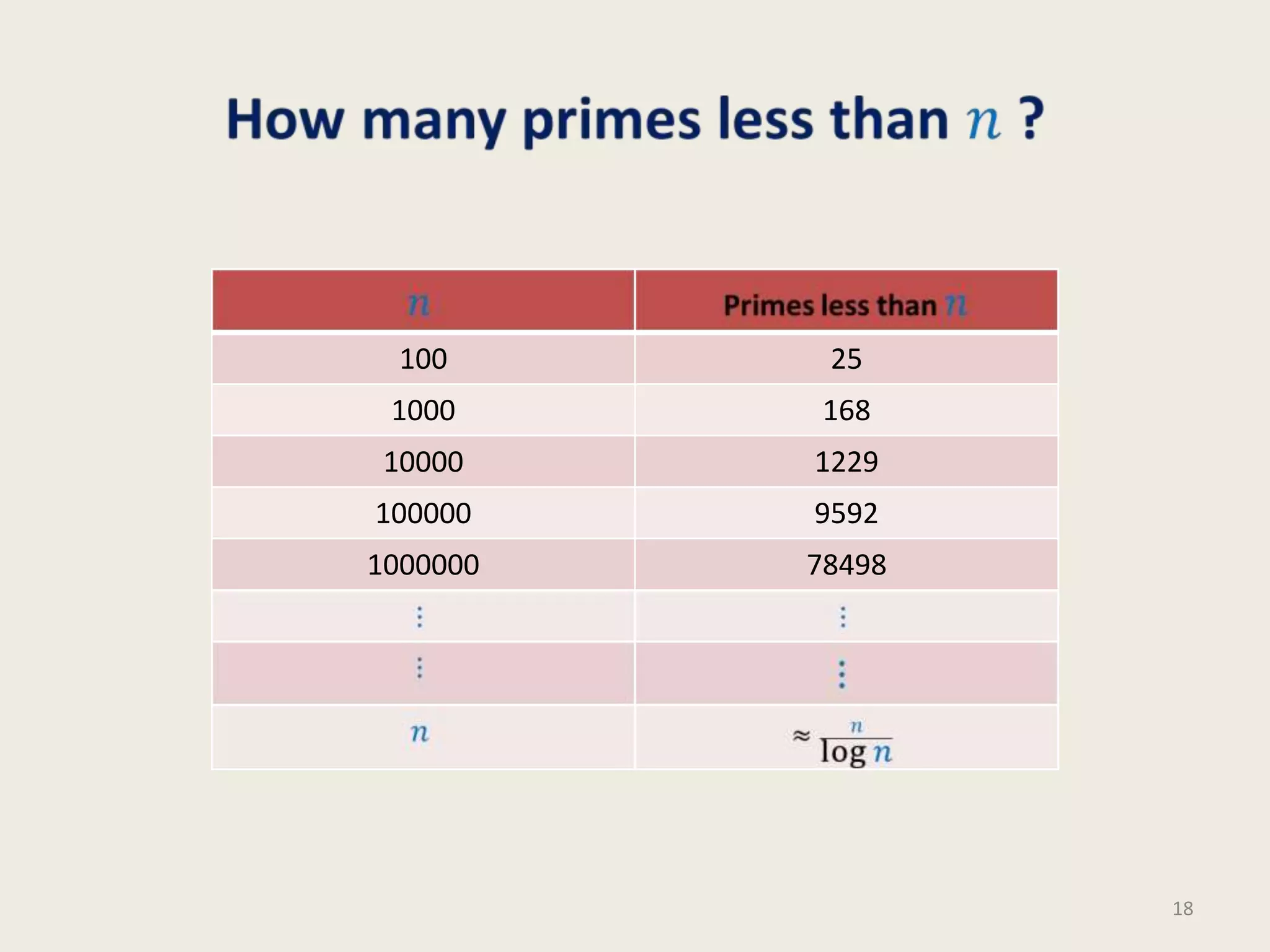
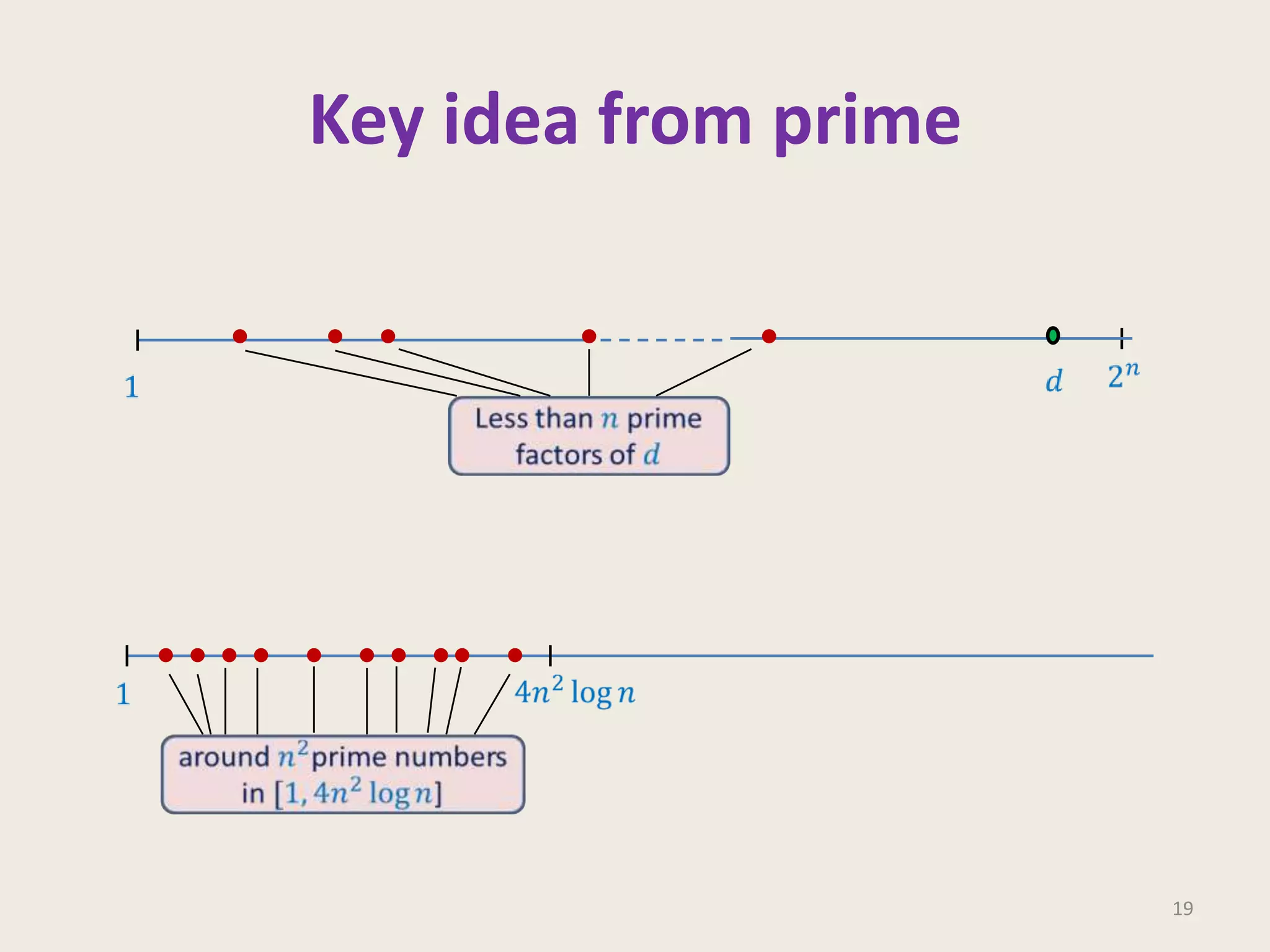
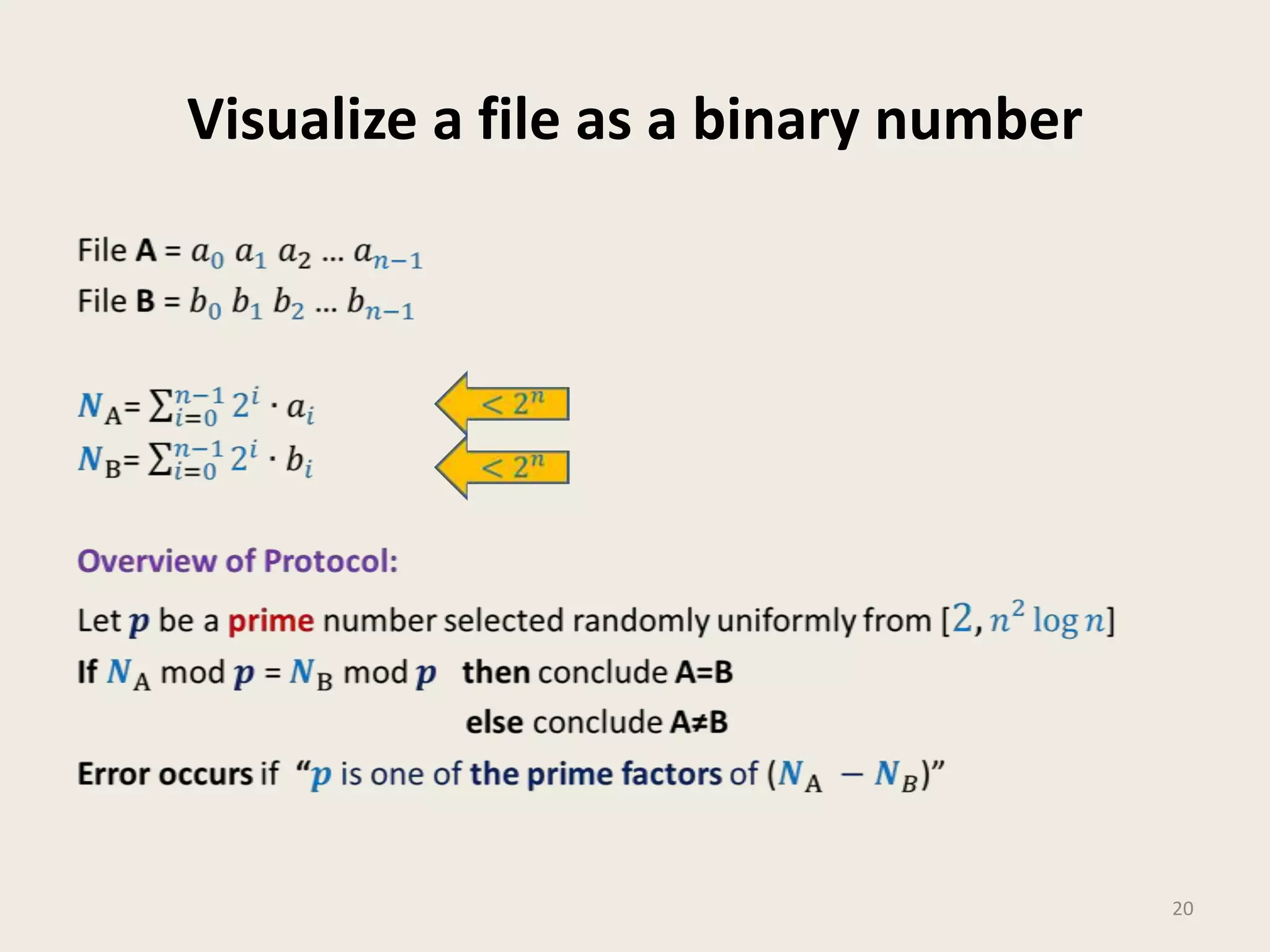
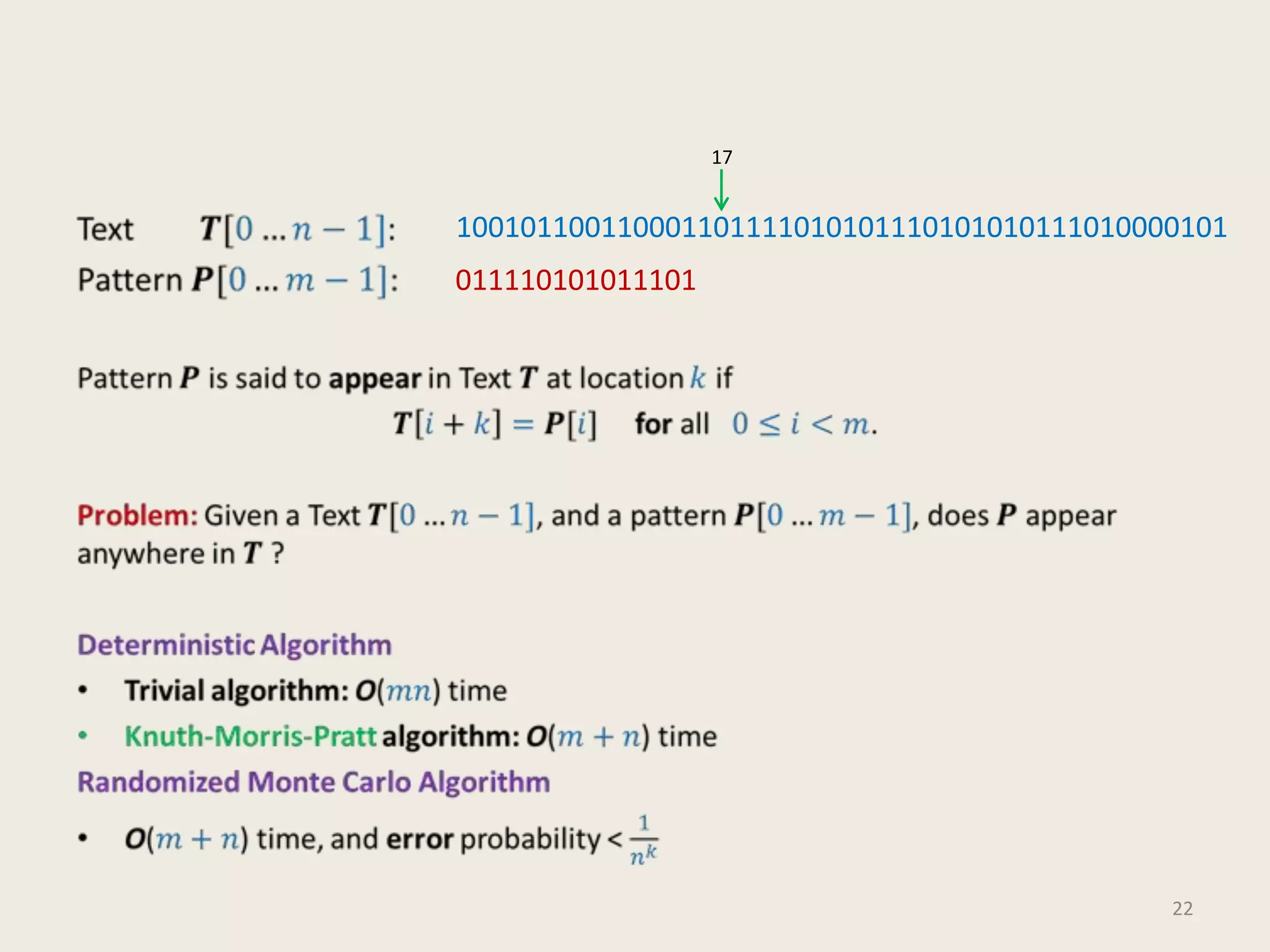
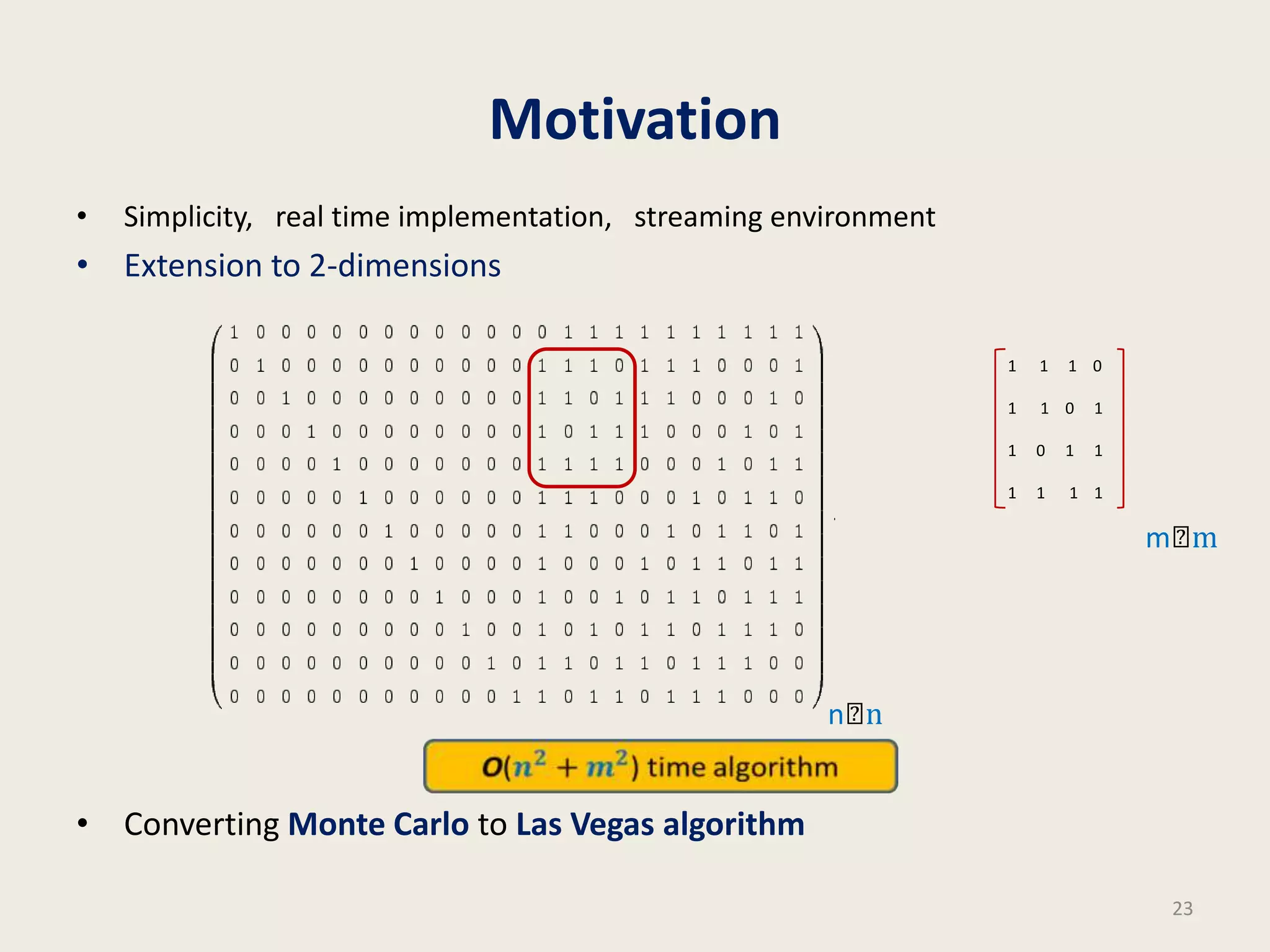
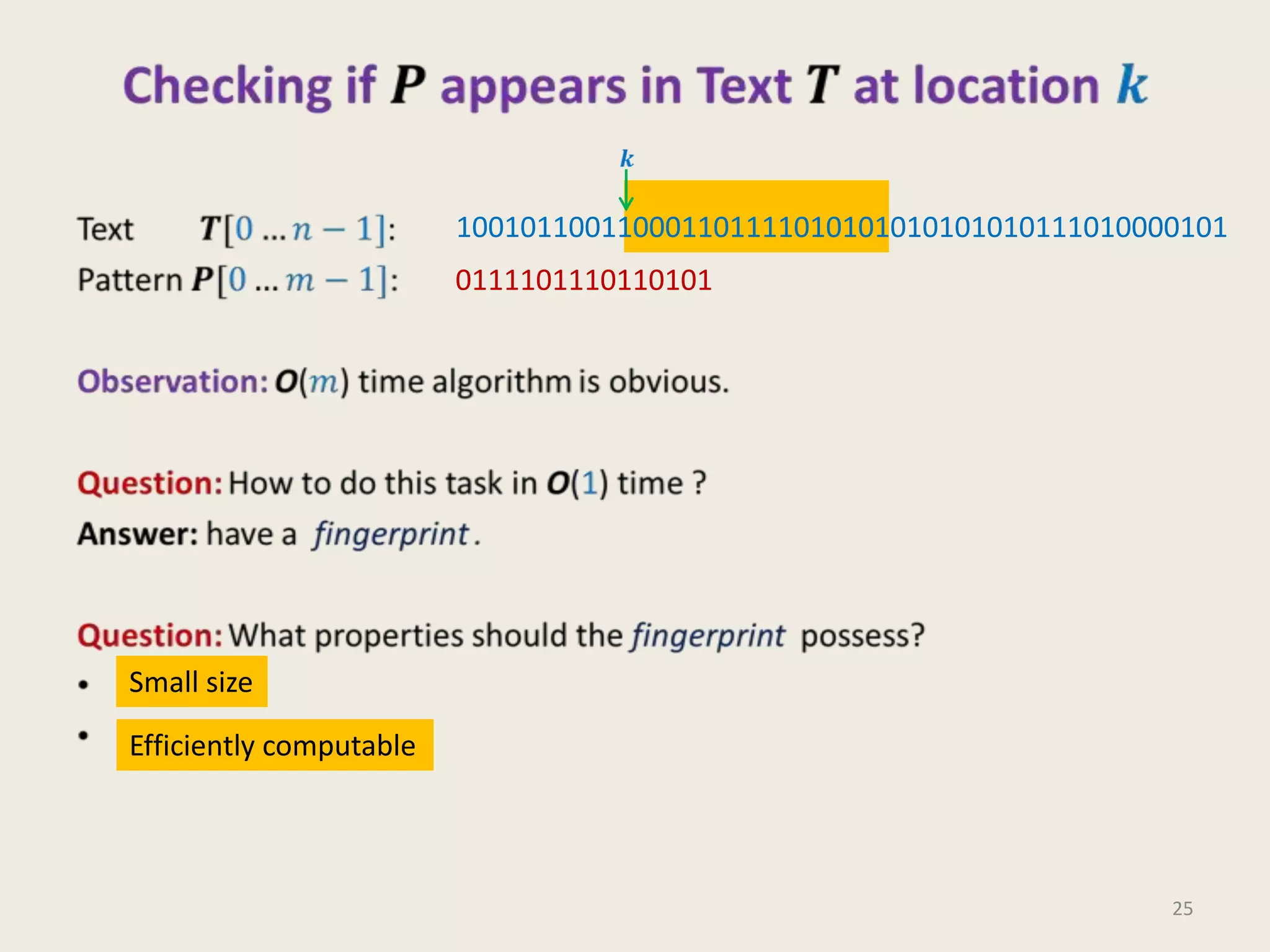
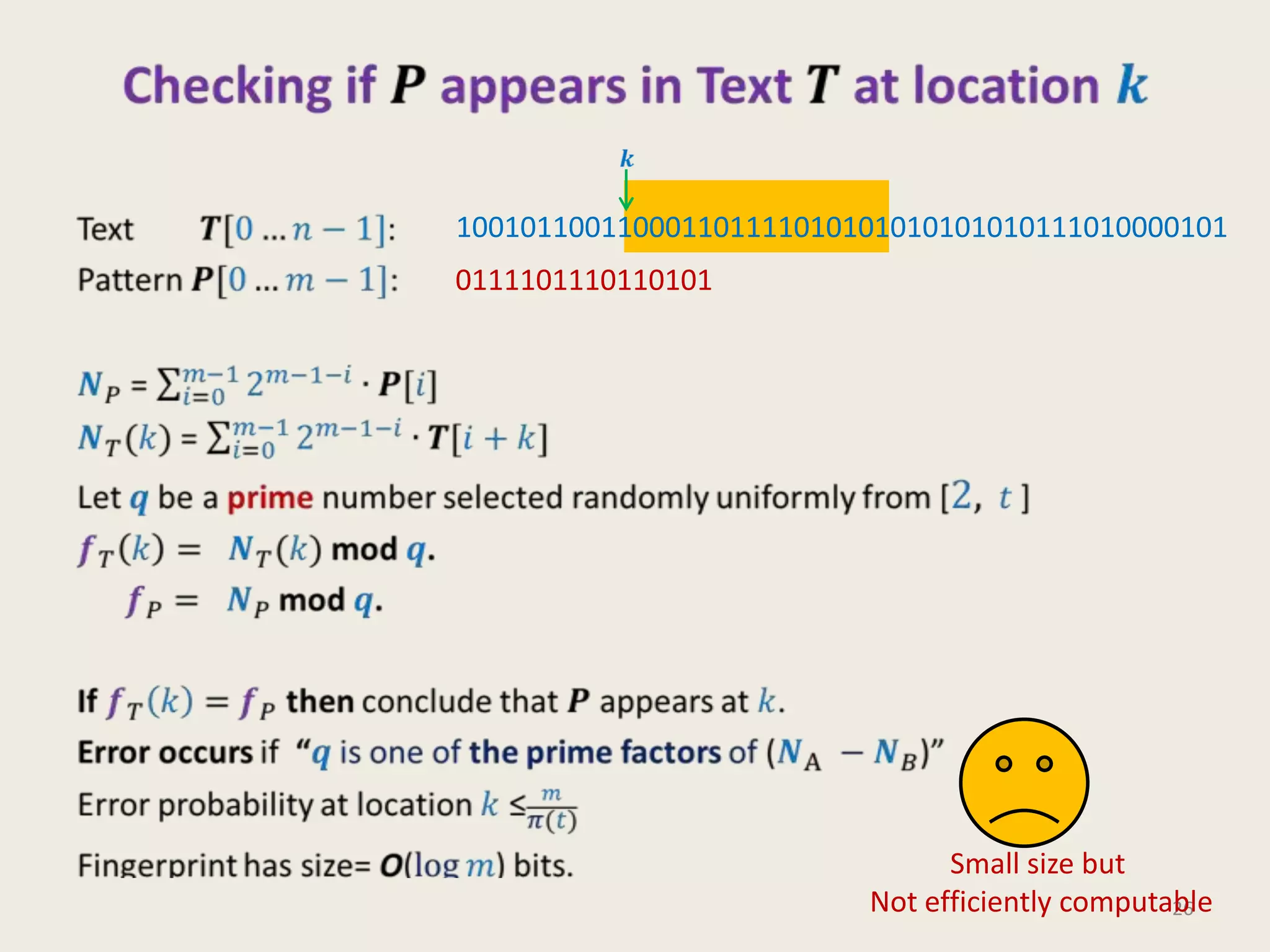
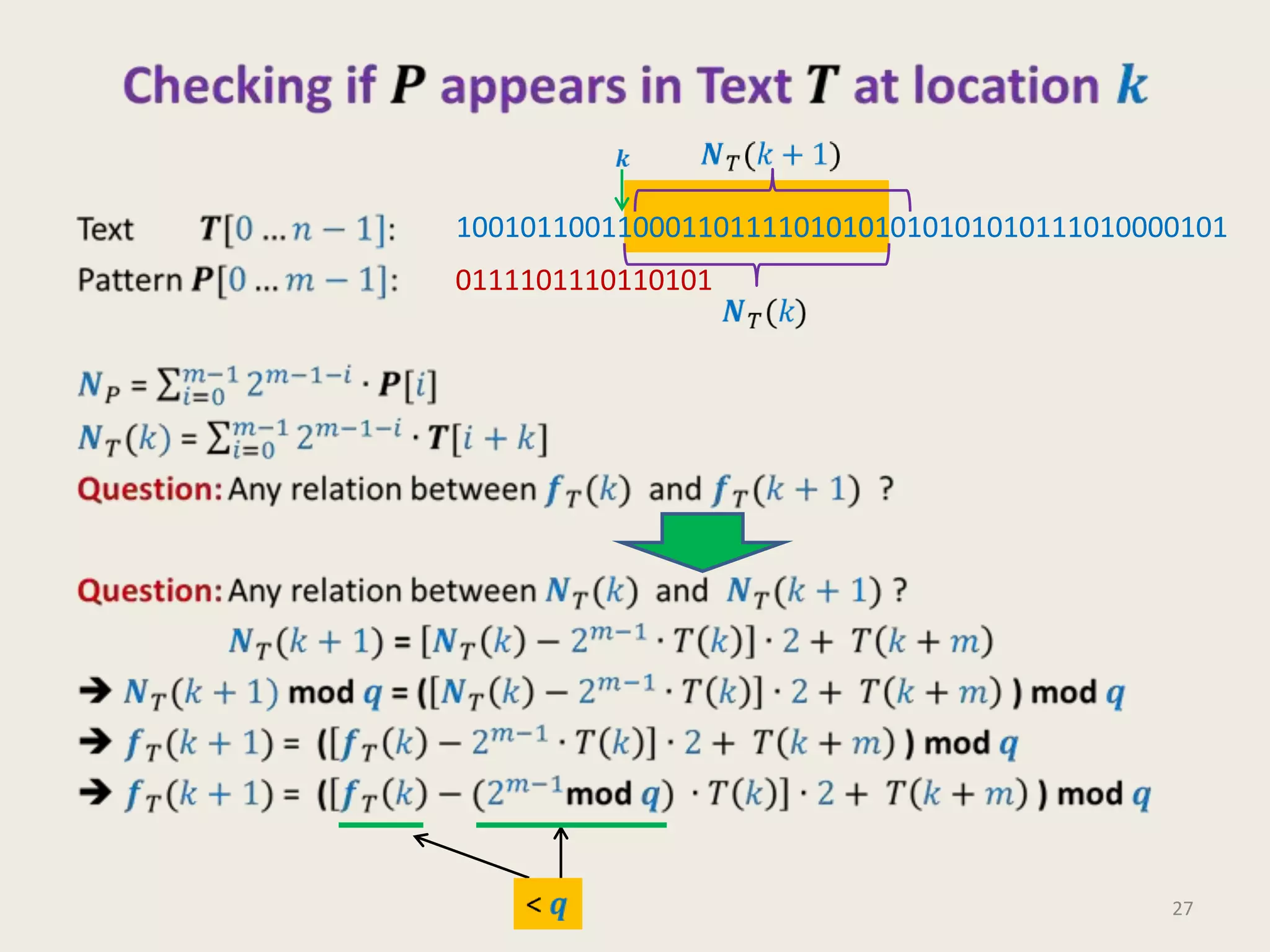
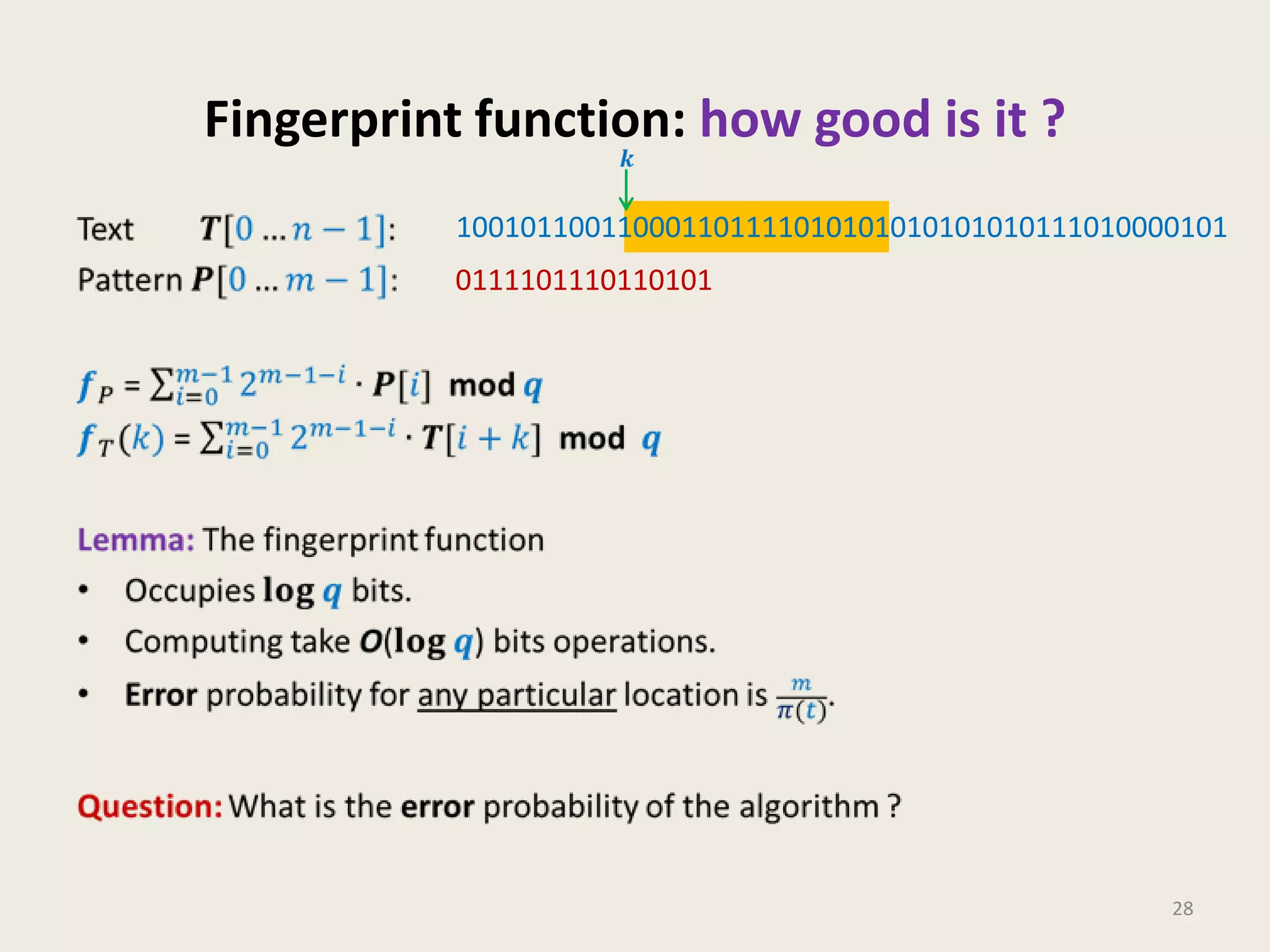
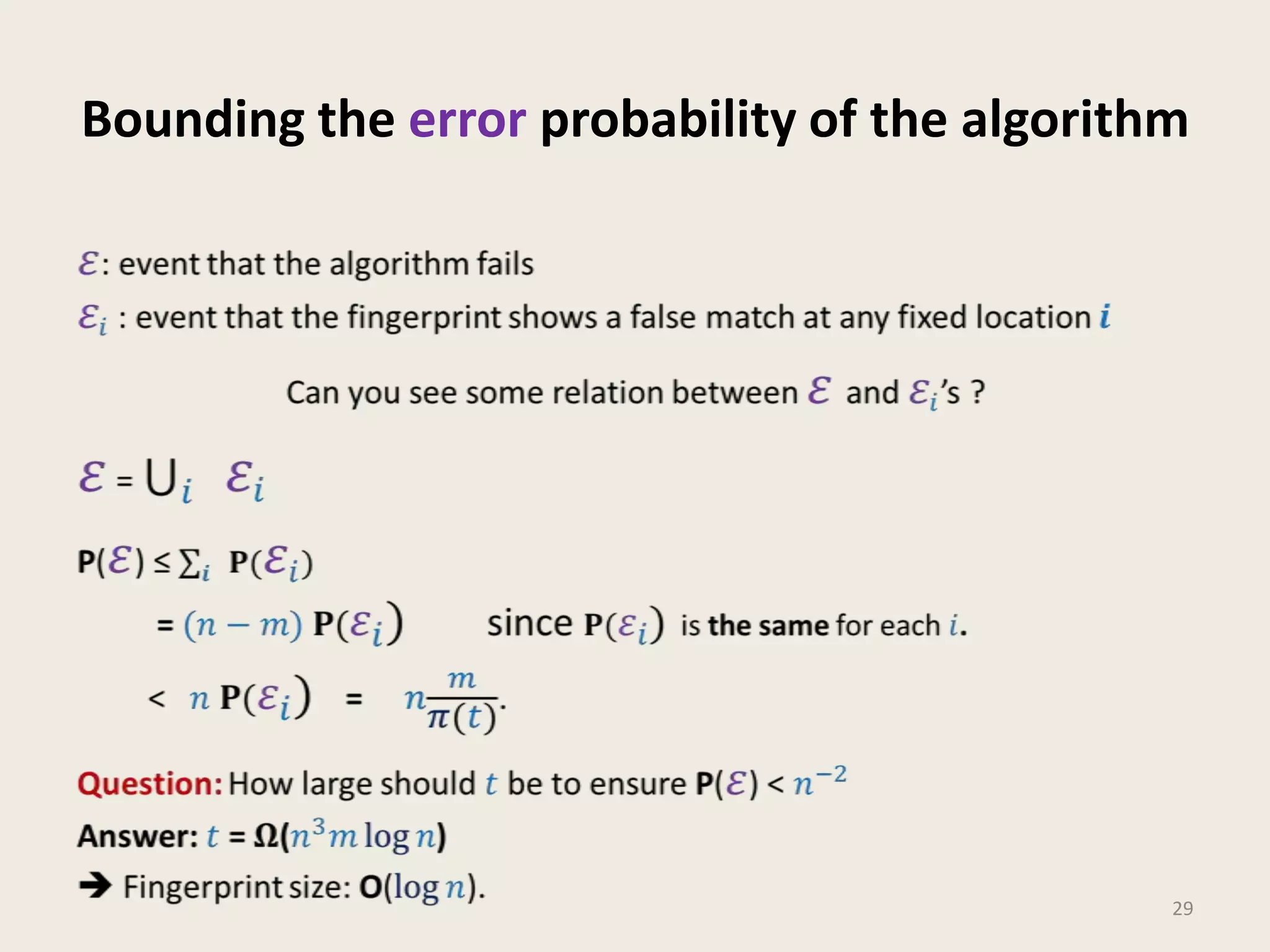
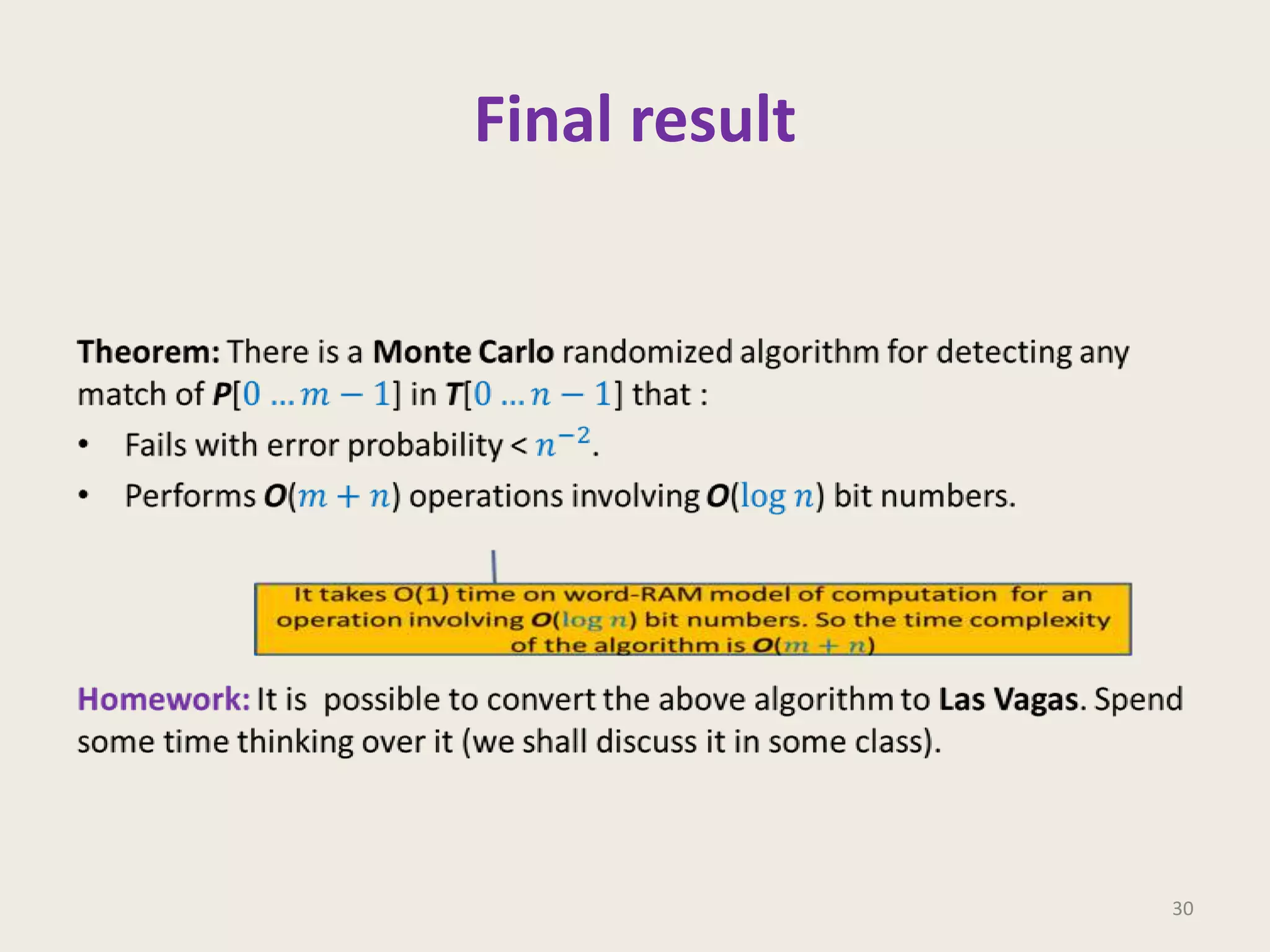
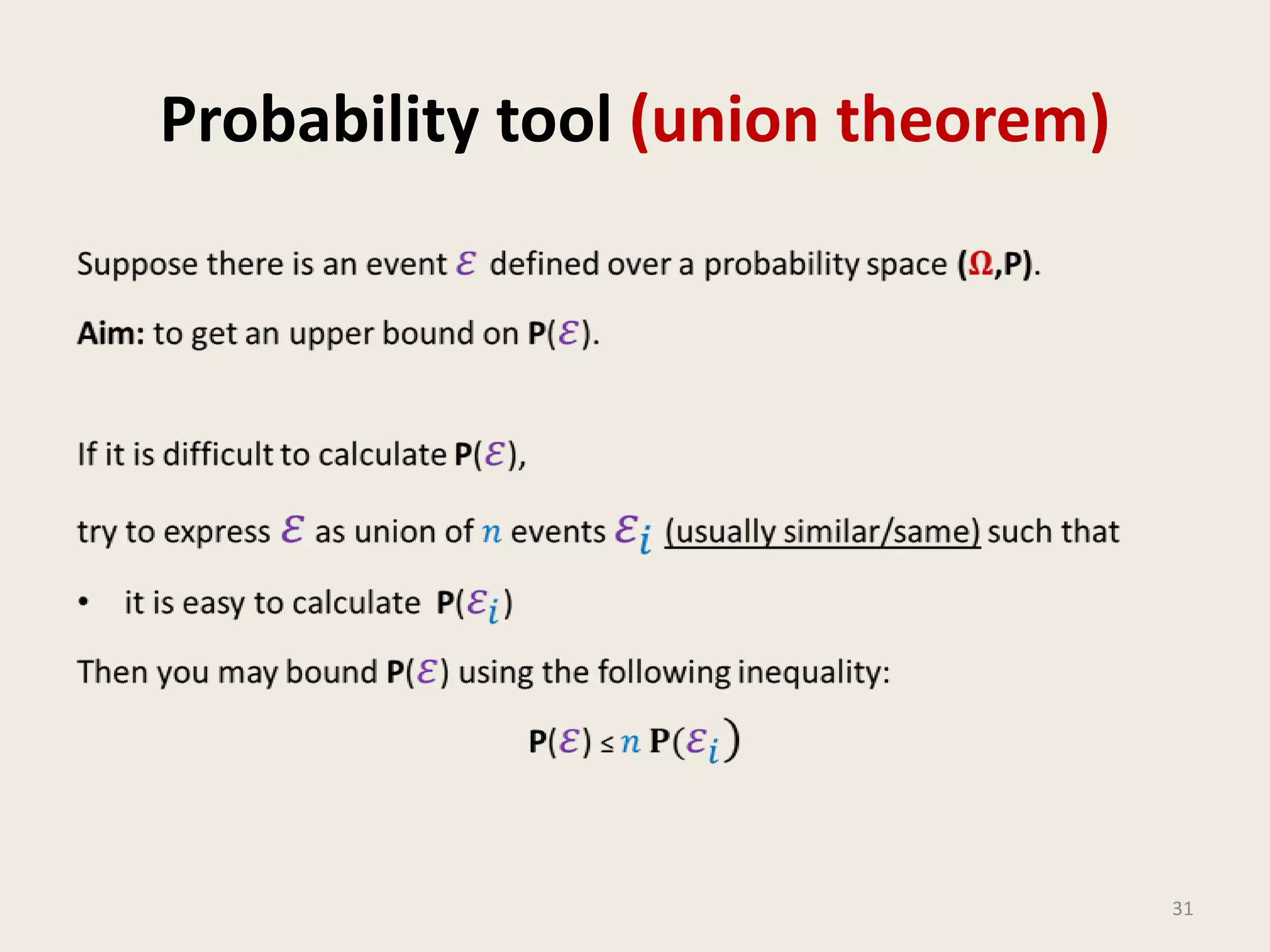
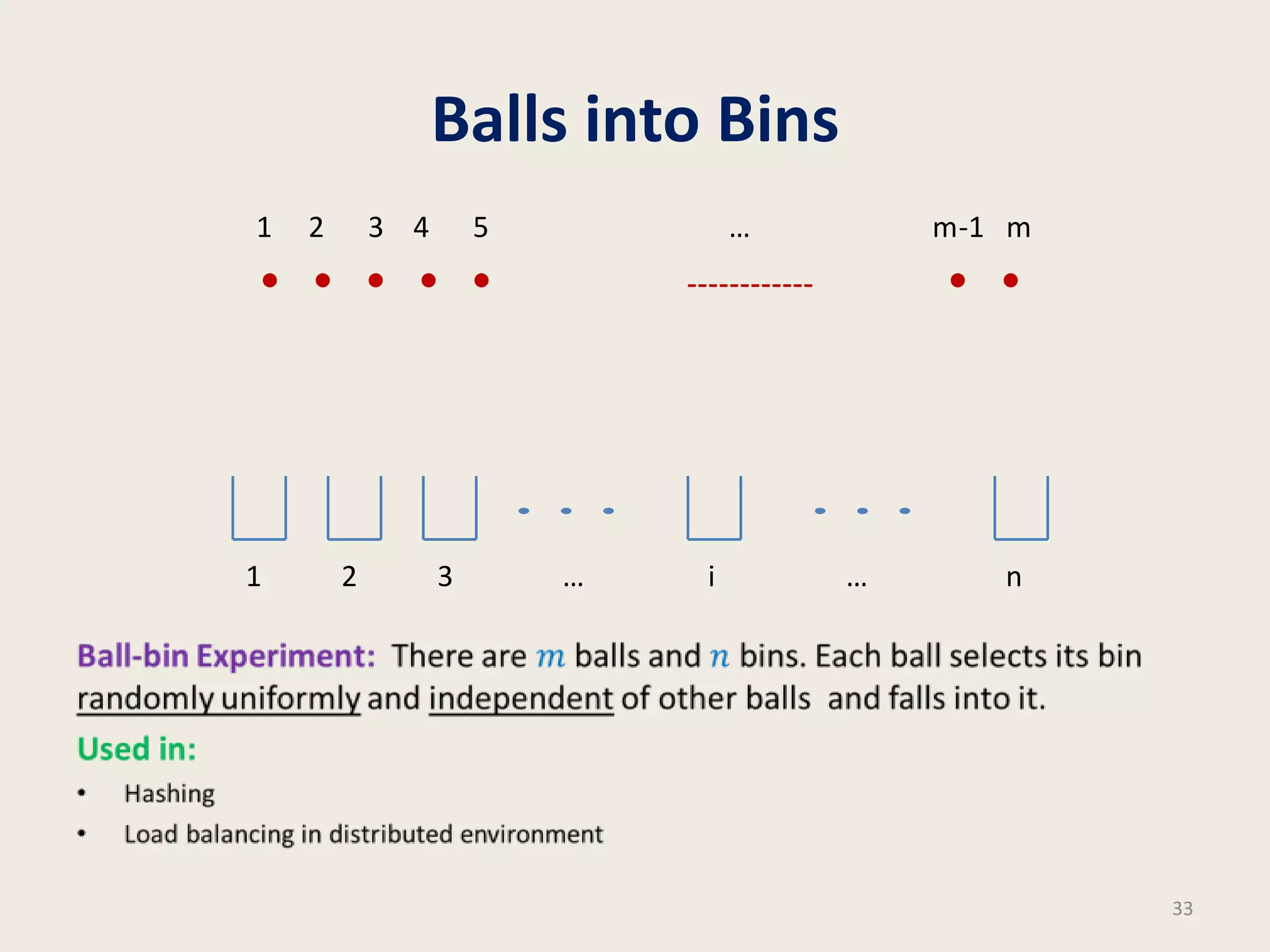
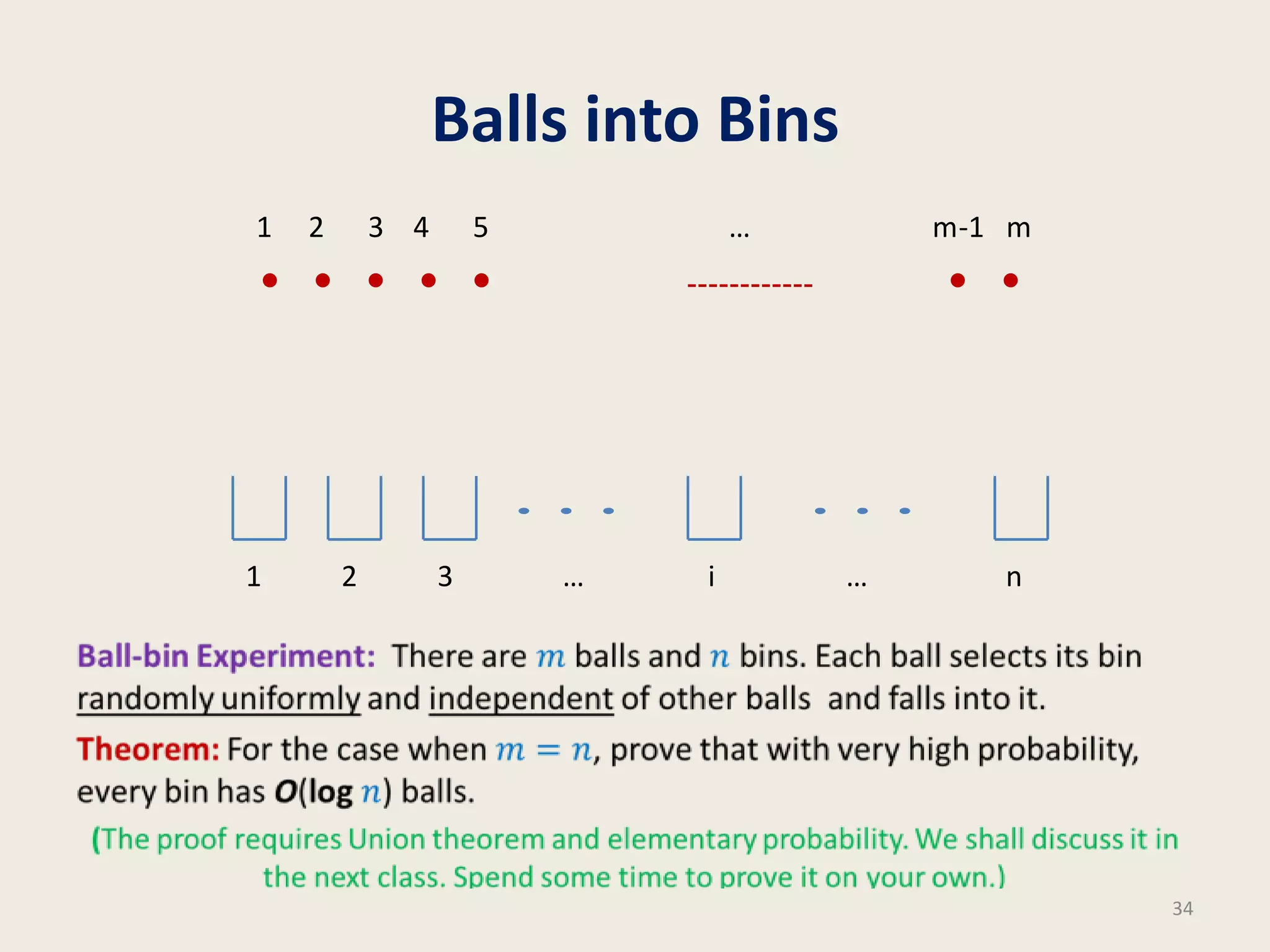
This document discusses randomized algorithms and provides examples. It reviews the last 3 lectures on randomized algorithms, including applications of fingerprinting techniques and 1-dimensional pattern matching. It then discusses randomized quicksort, the randomized algorithm for approximate median, Frievald's technique for matrix product verification, and randomized fingerprinting algorithms. It focuses on how randomization can be used to design algorithms and analyzes the error probabilities of randomized algorithms.