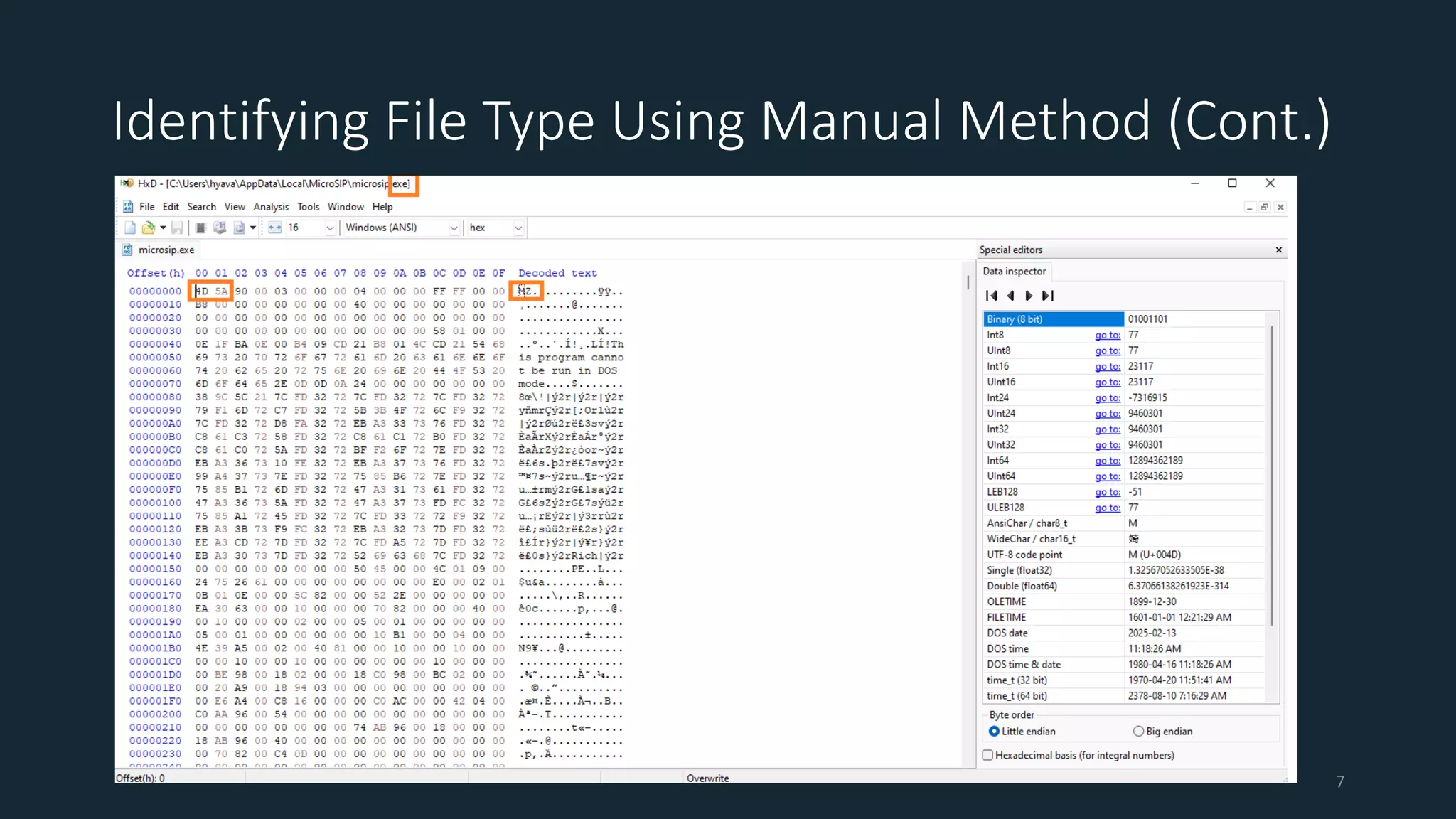
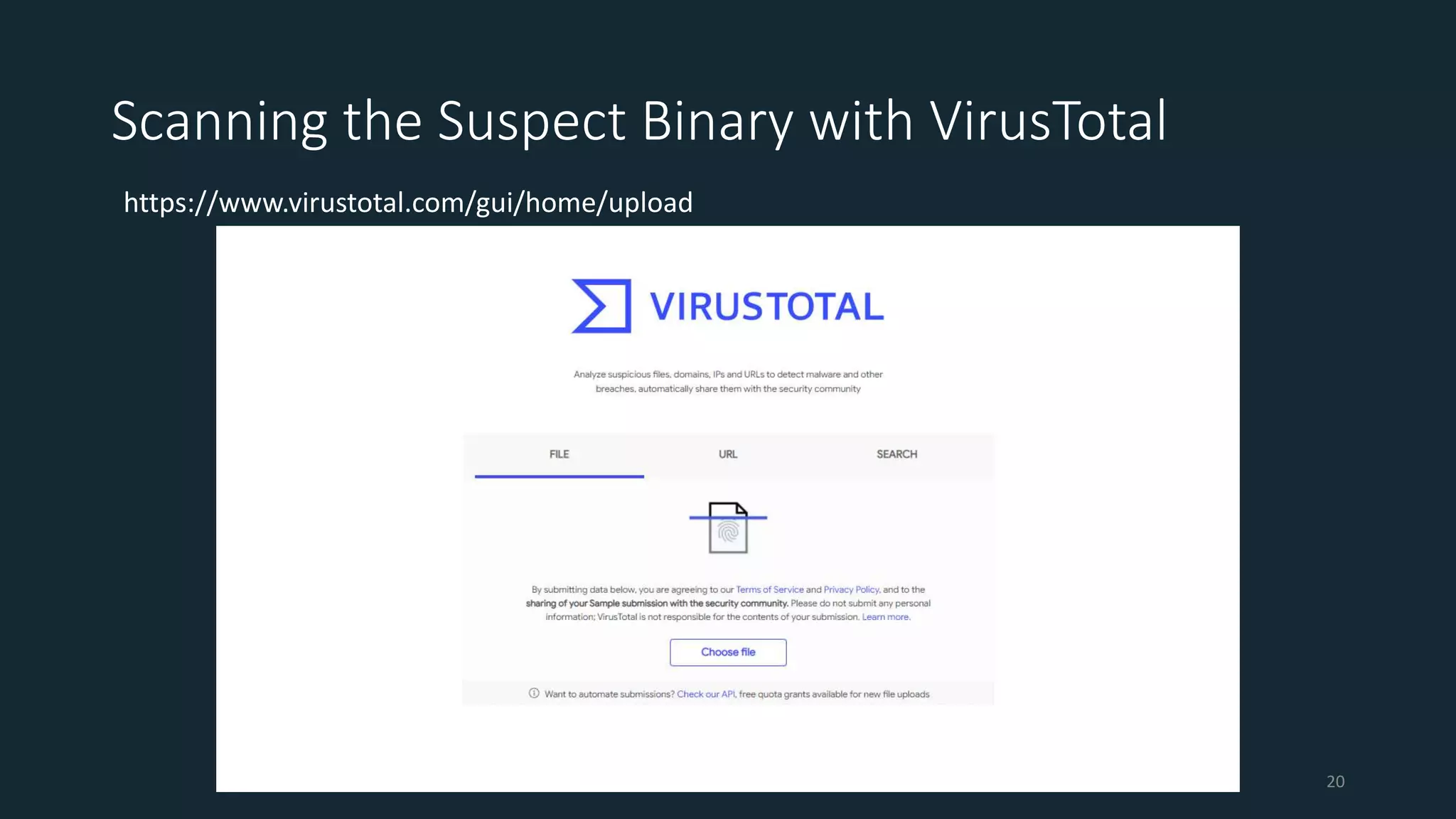
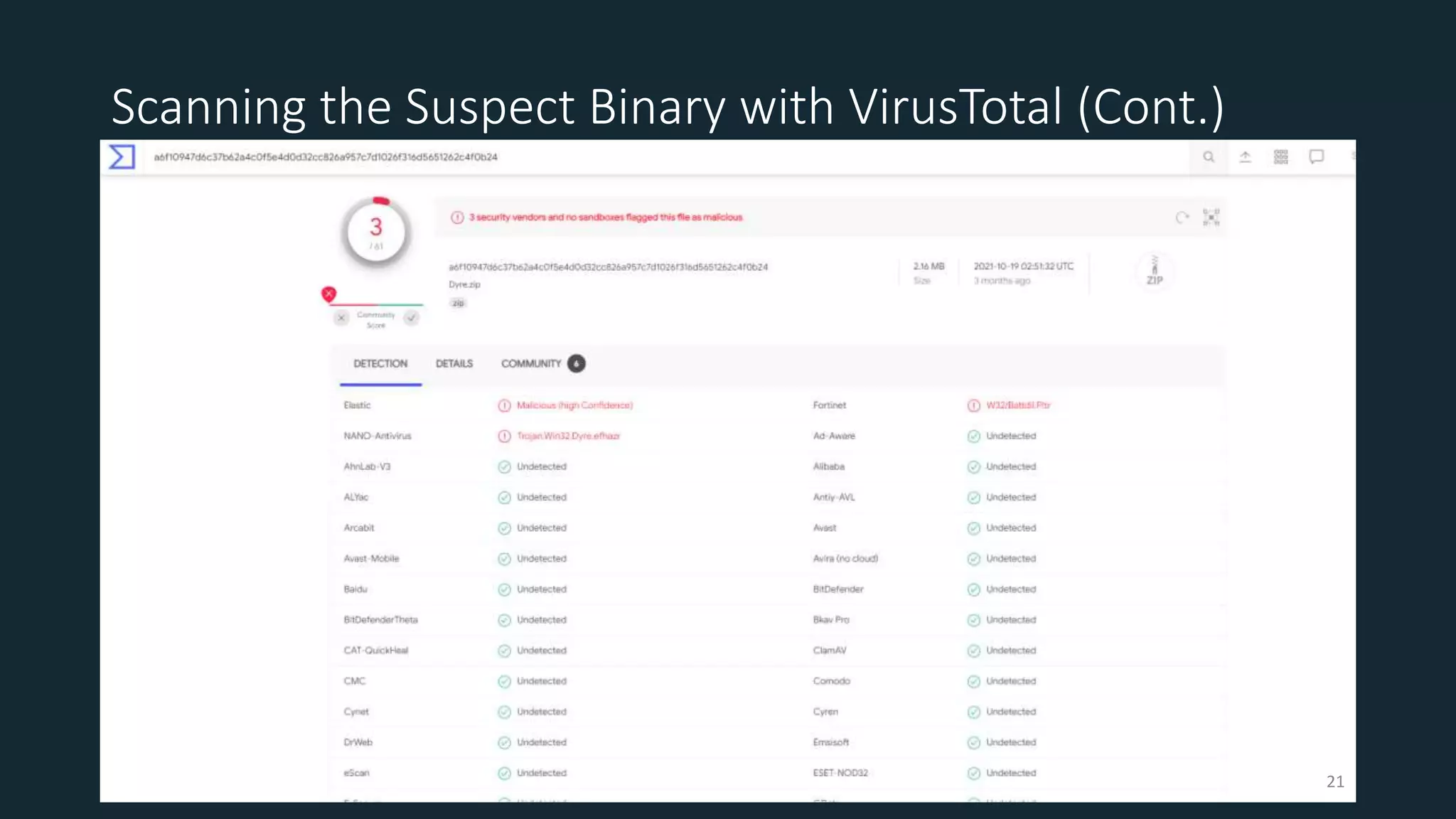
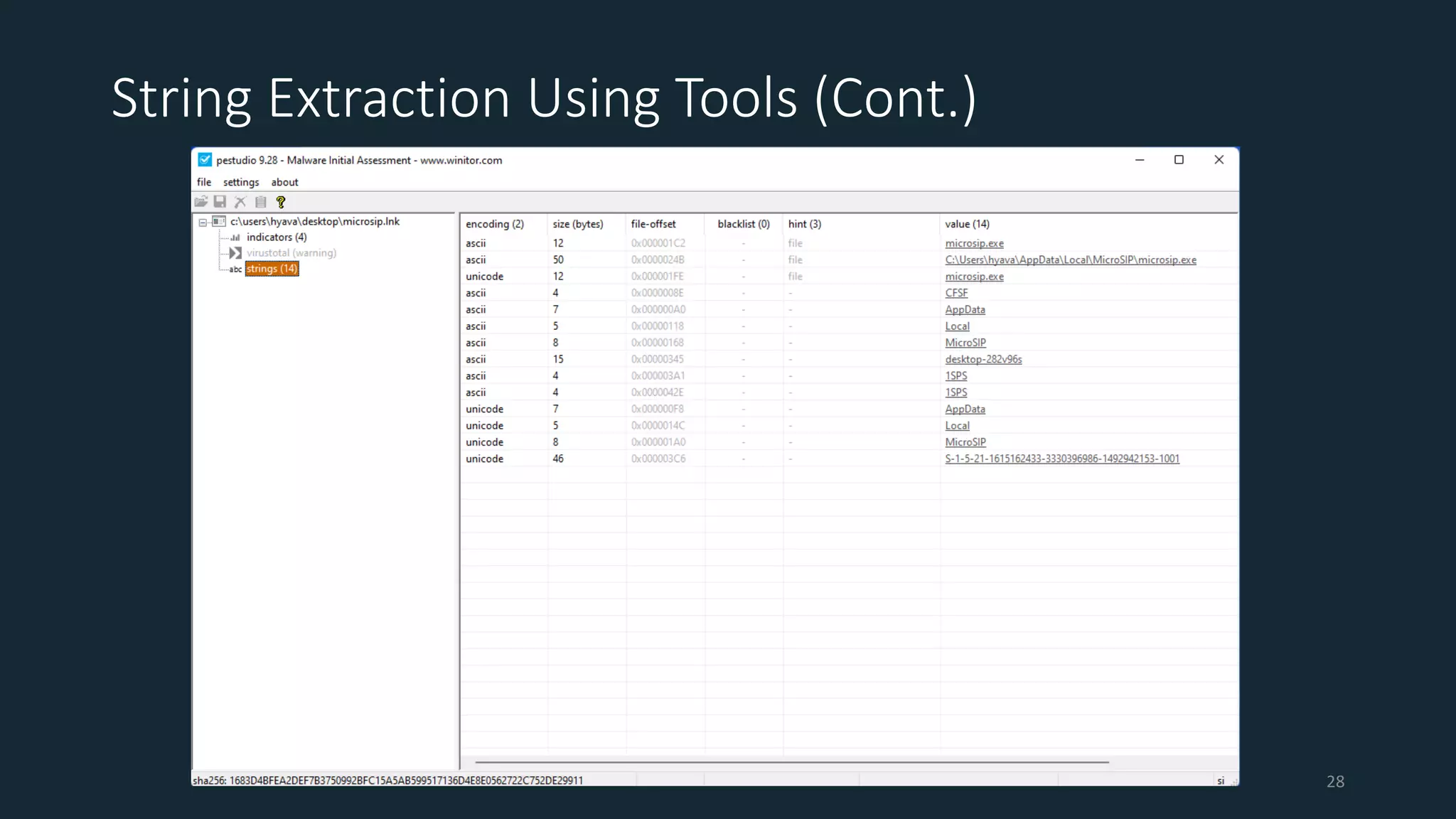
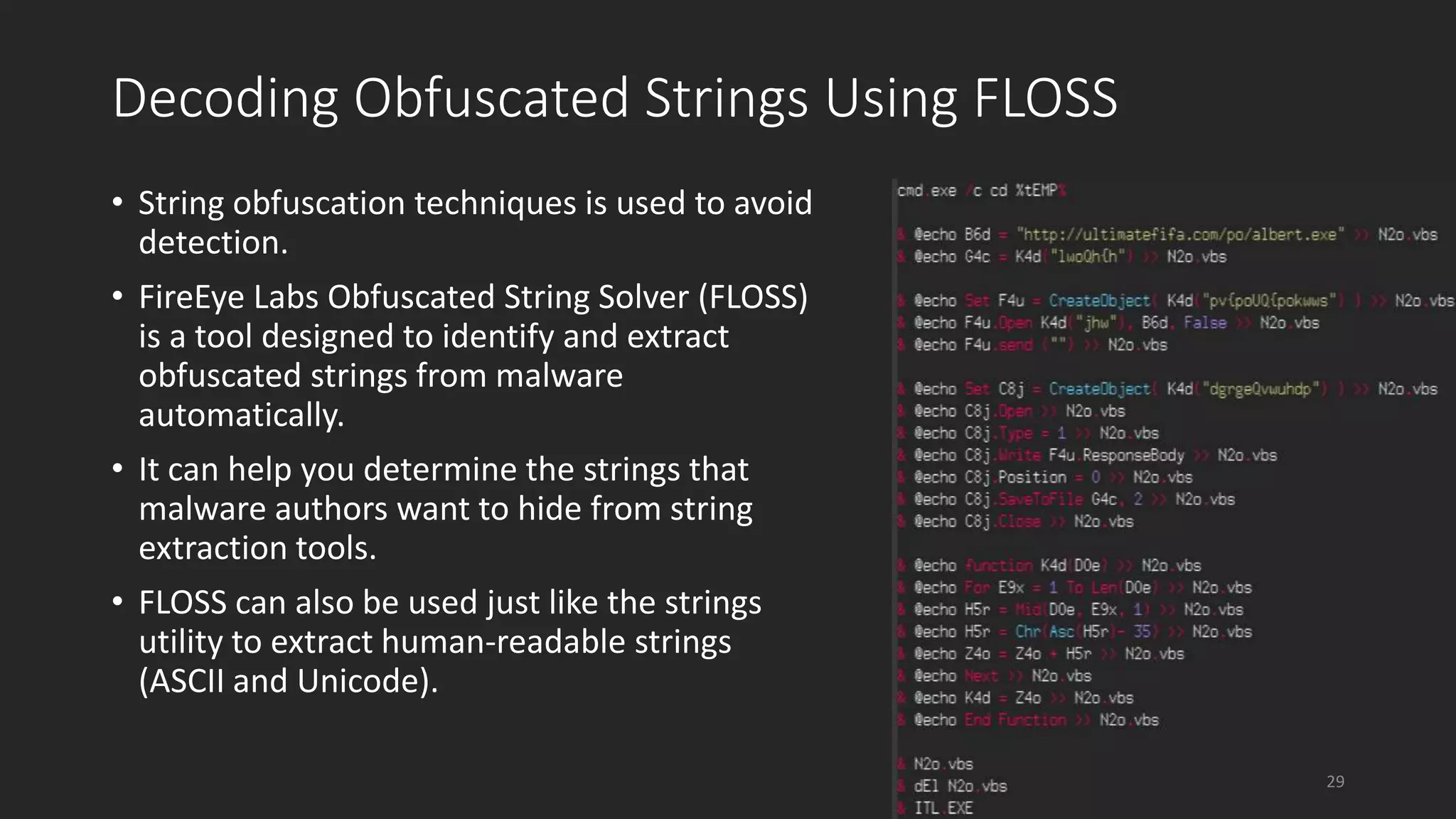
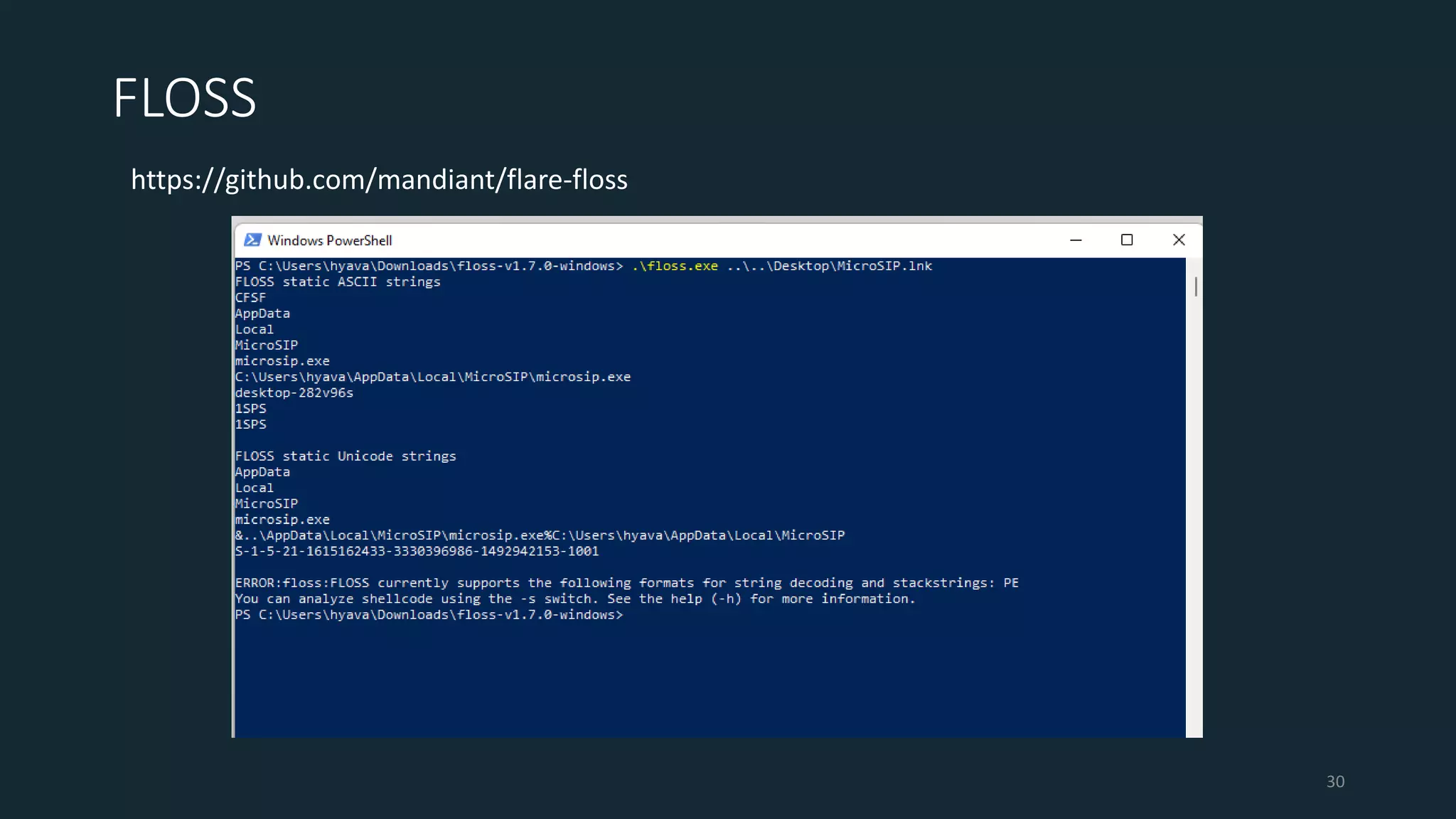
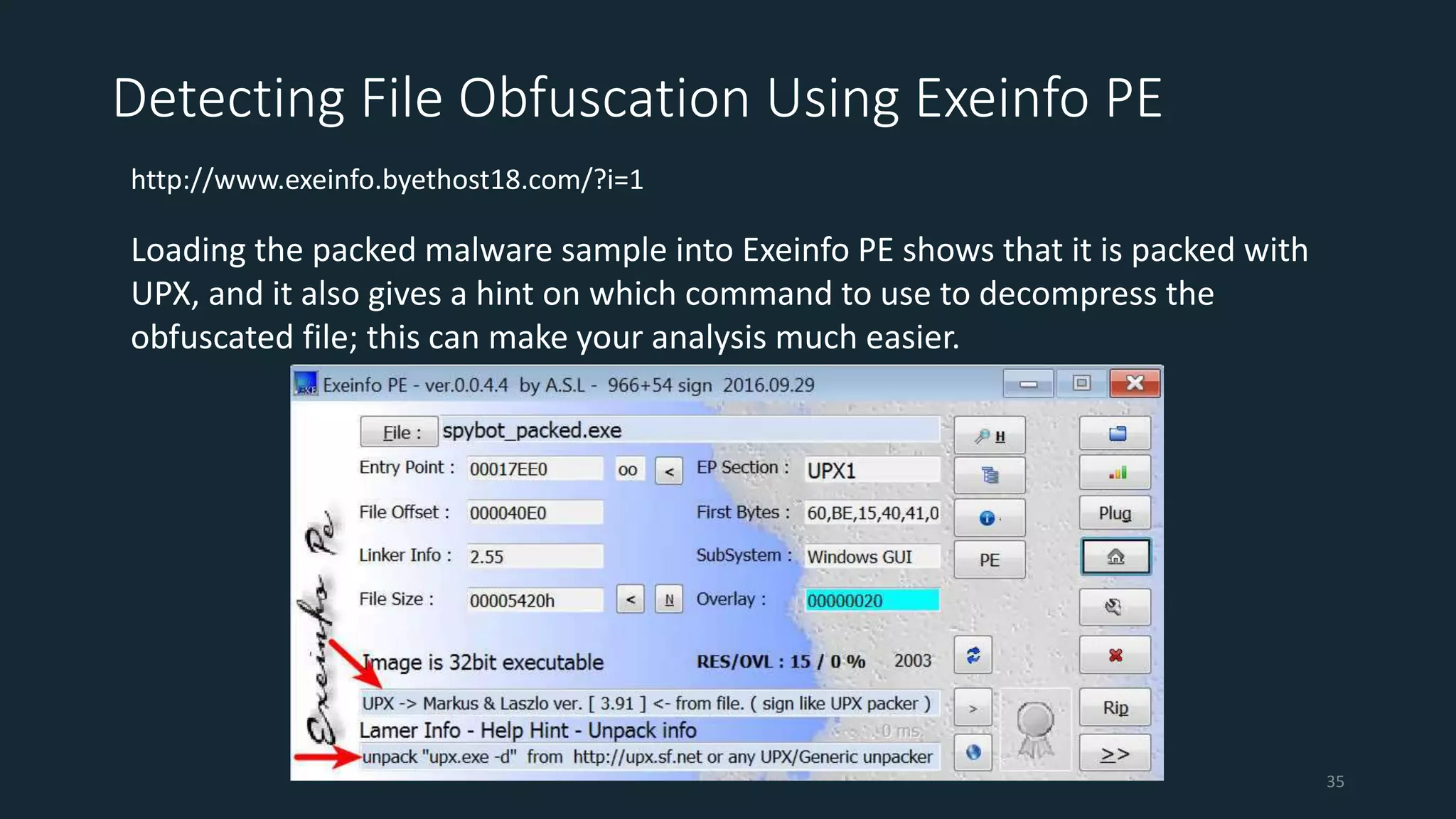
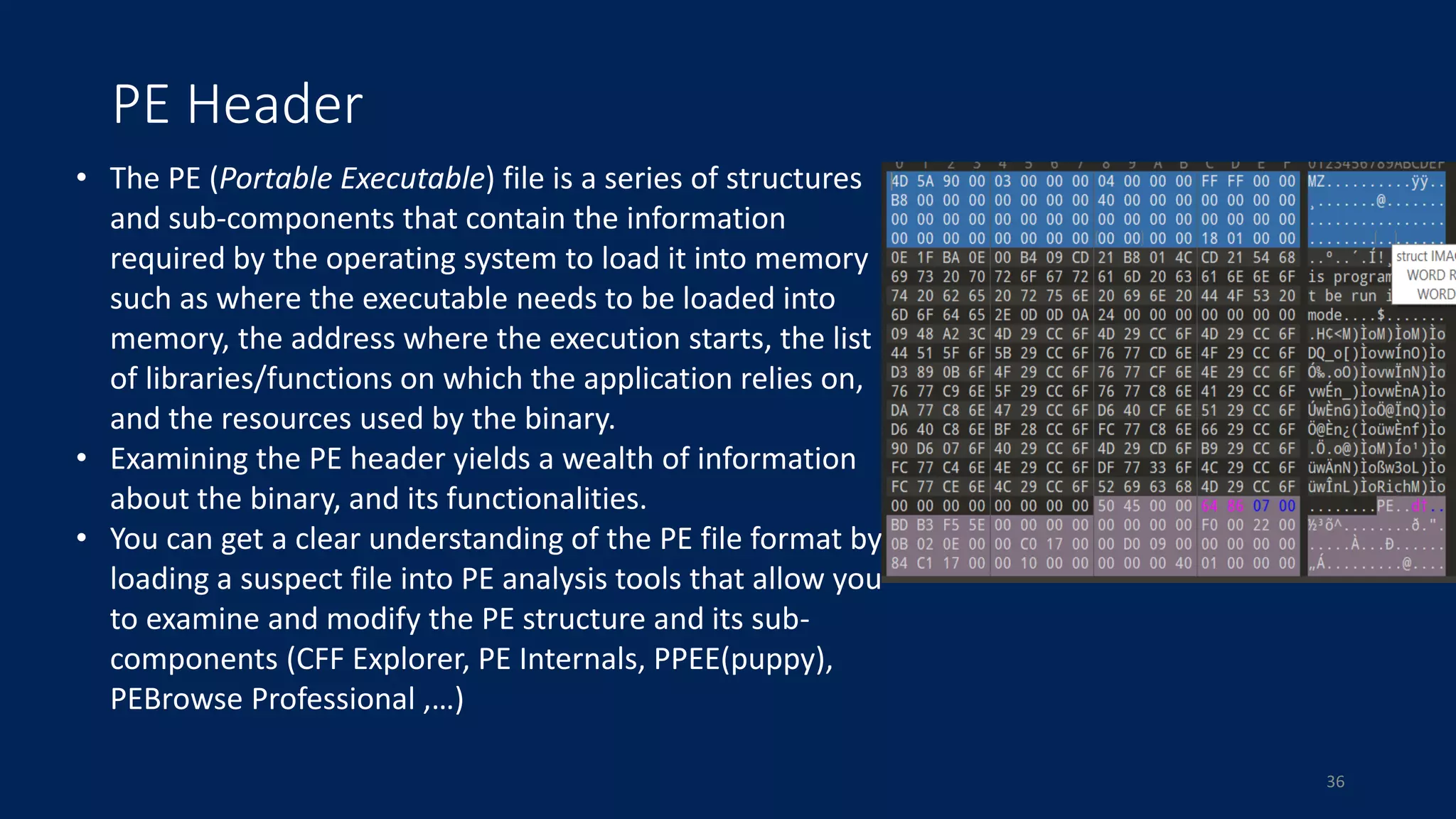
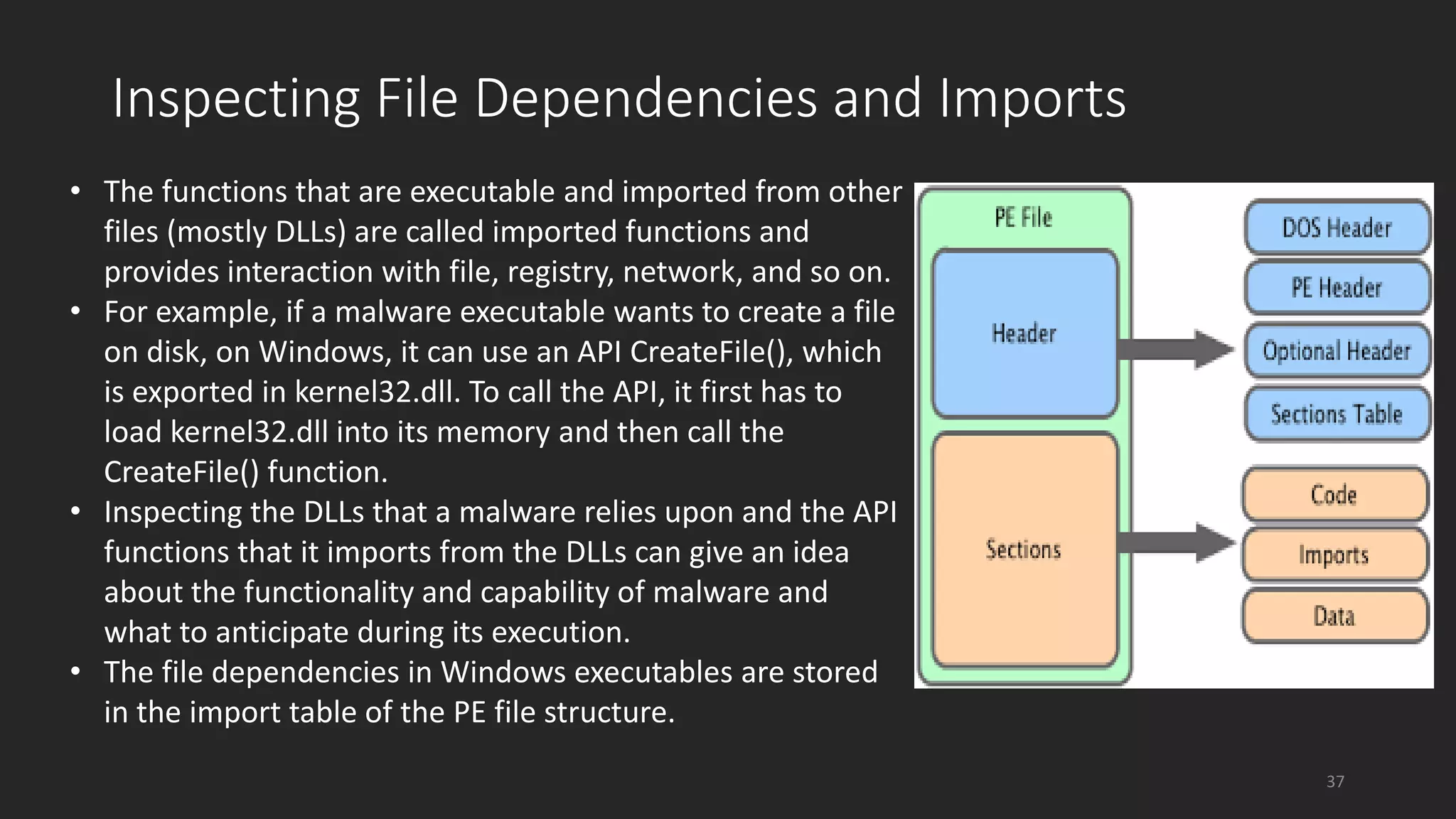
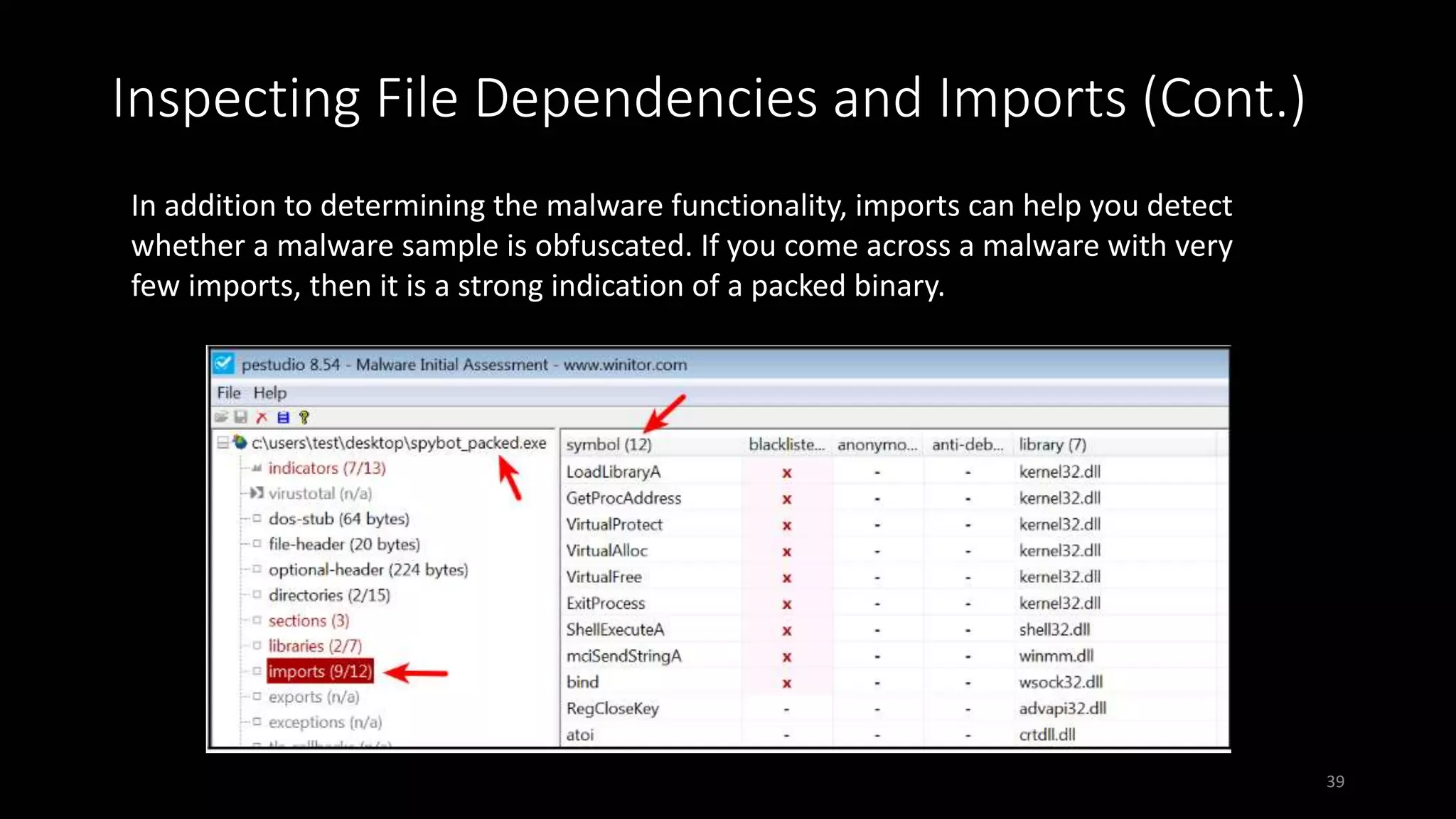
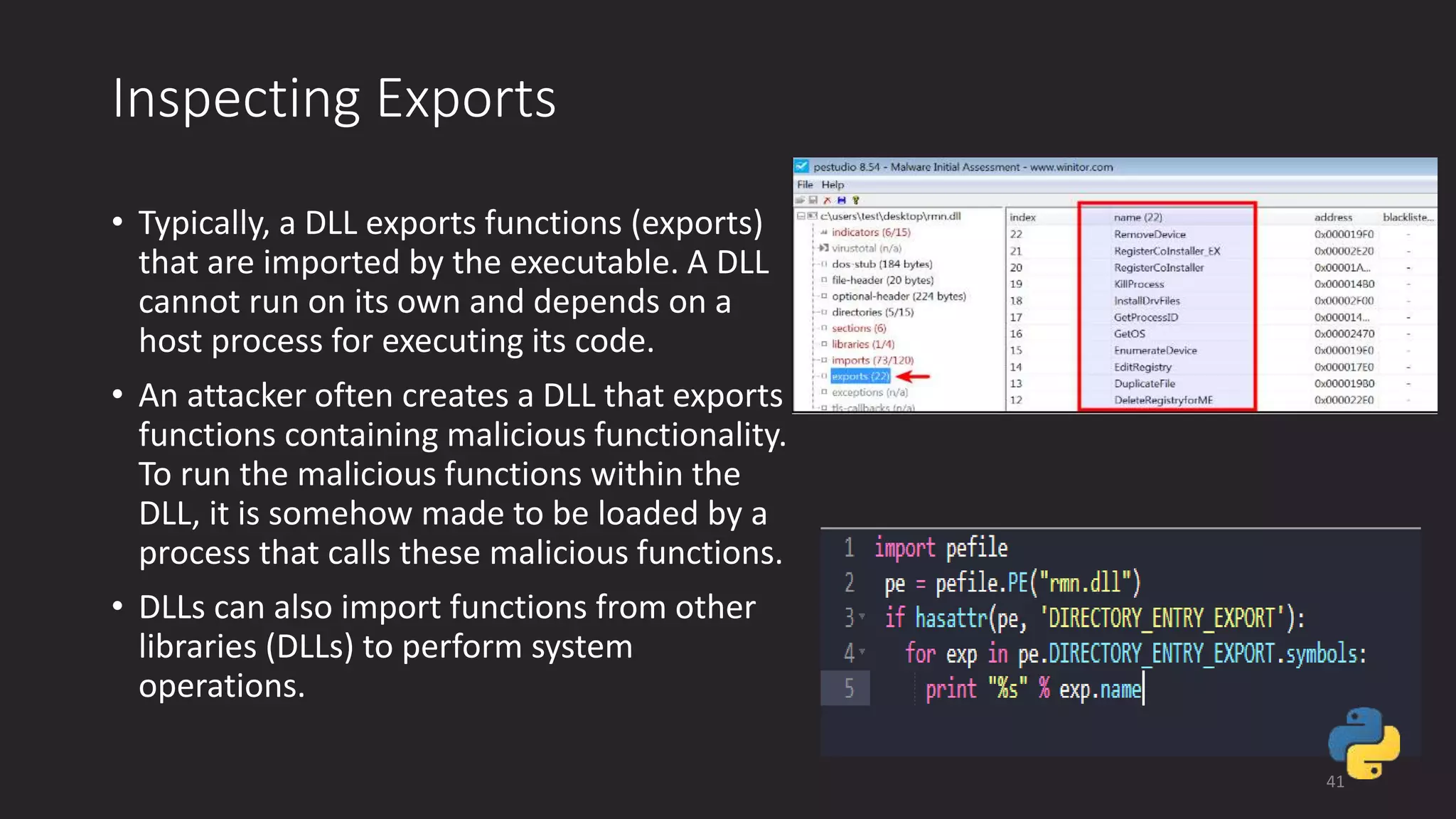
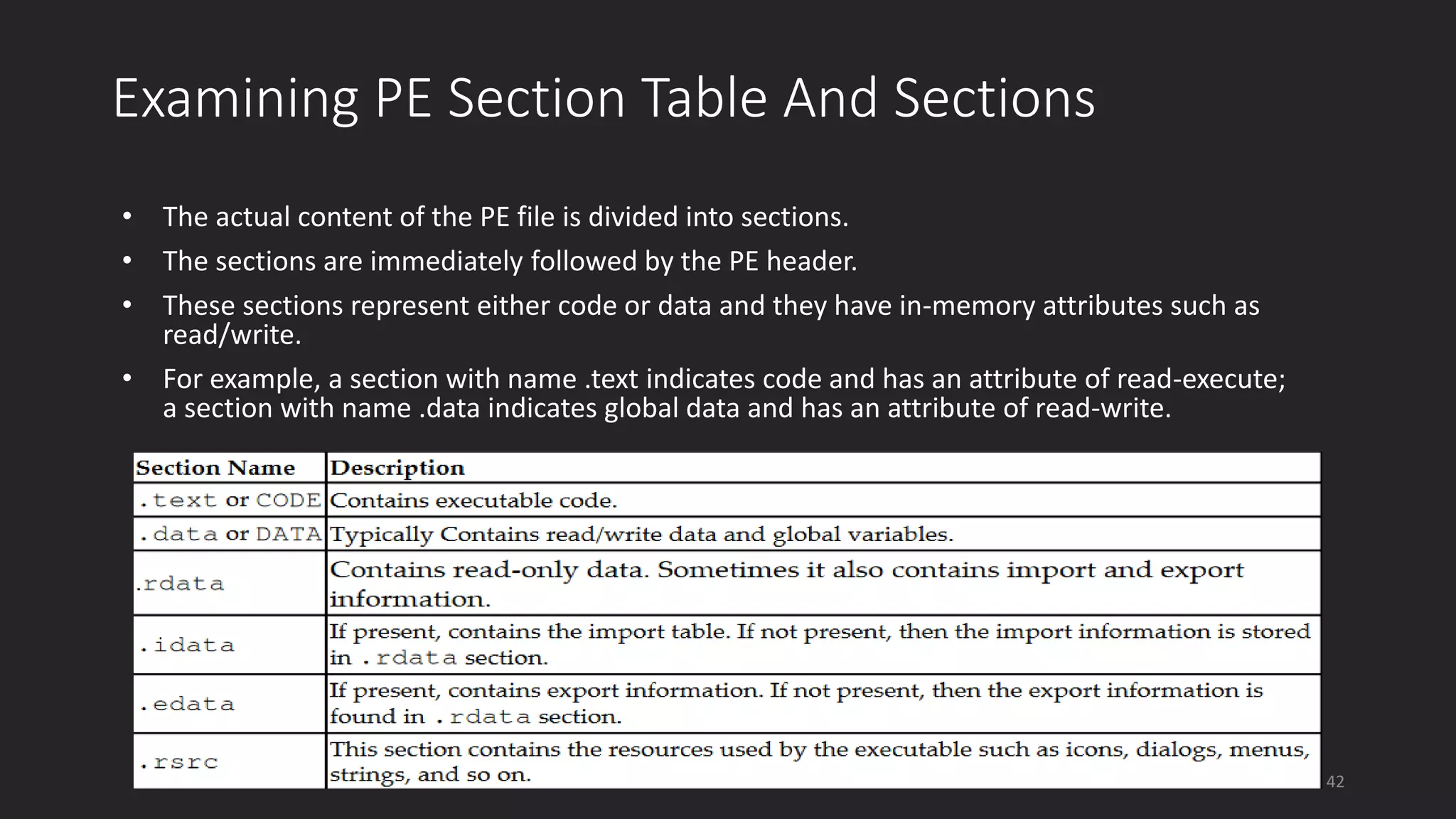
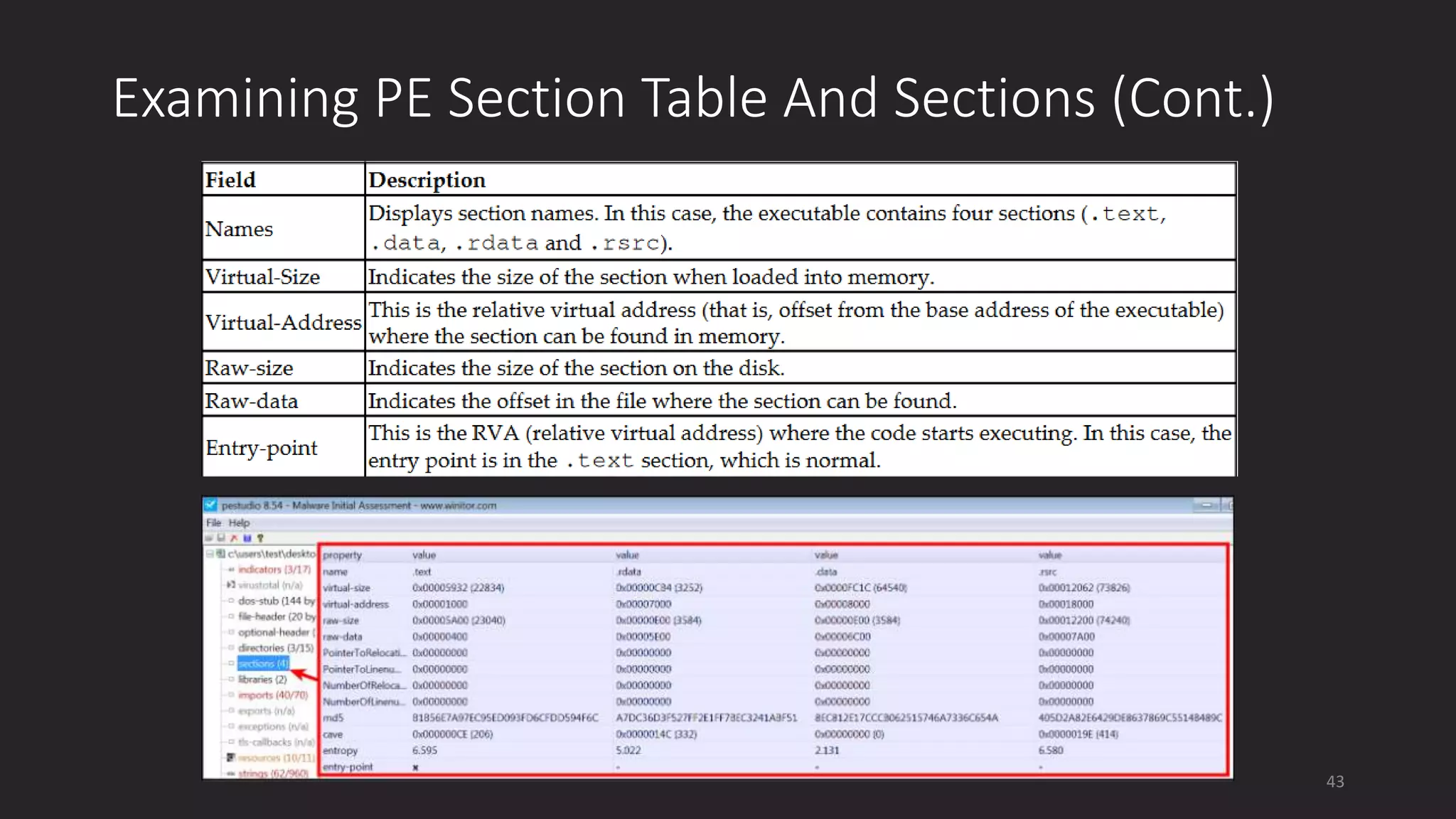
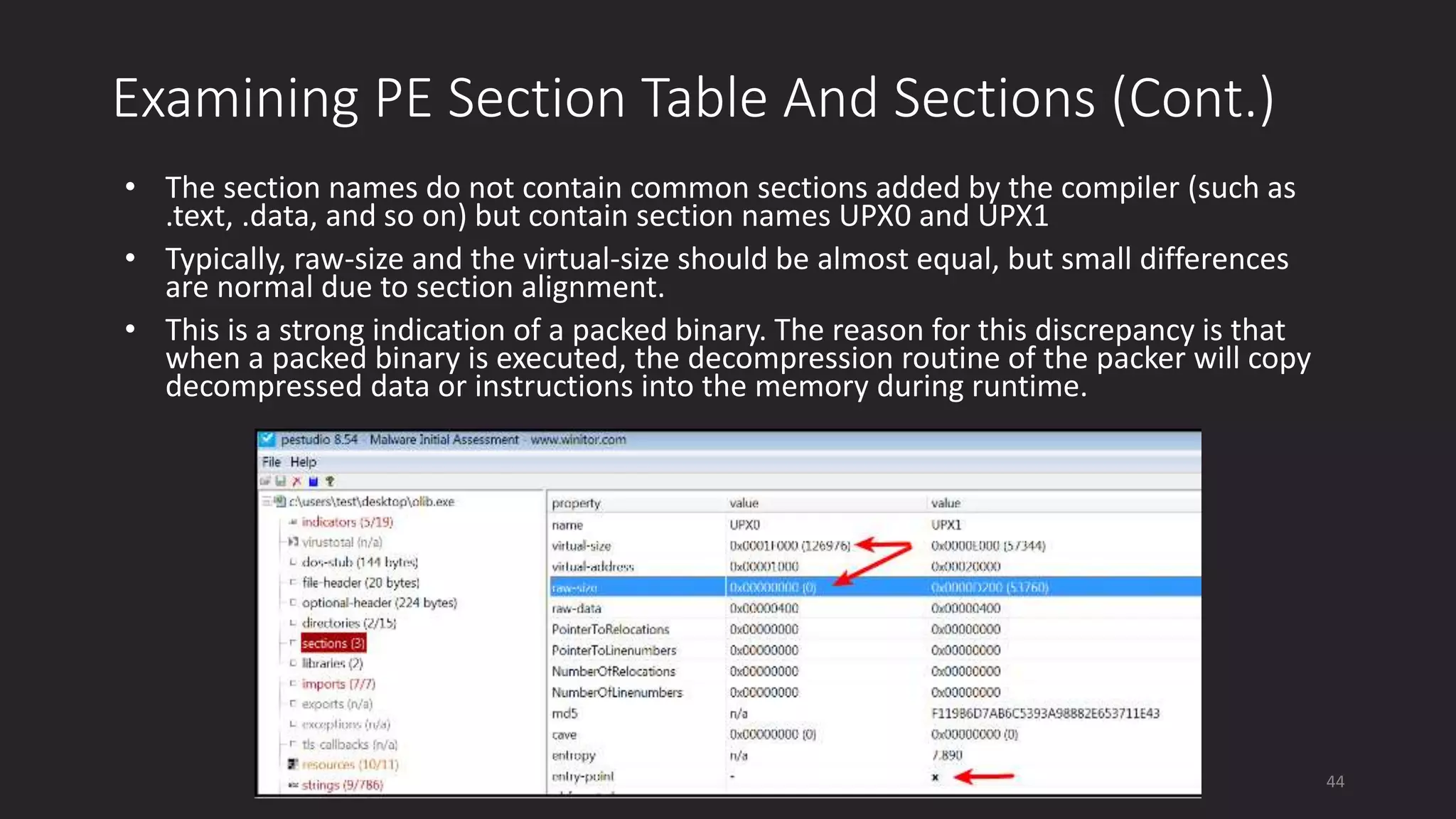
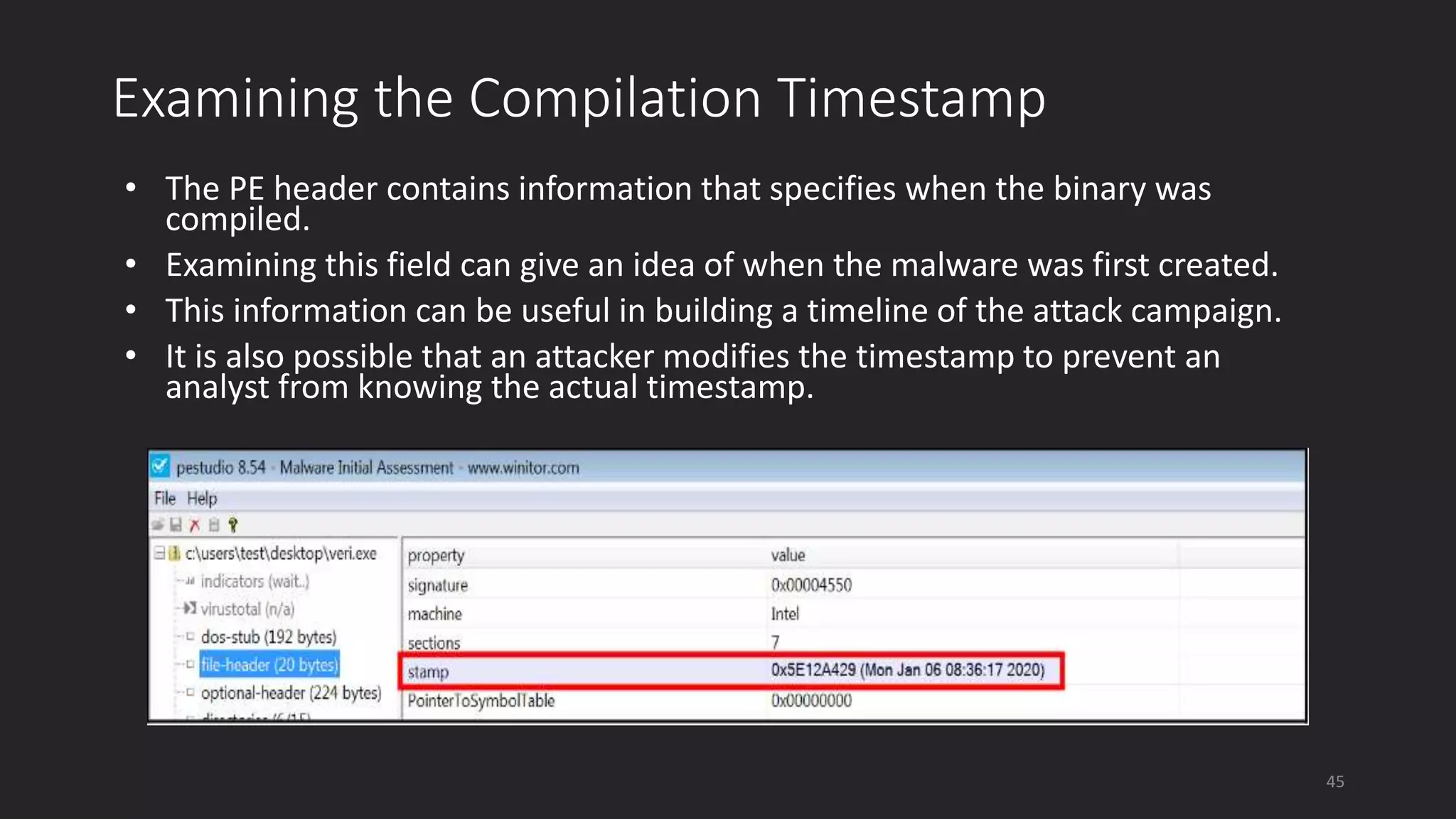
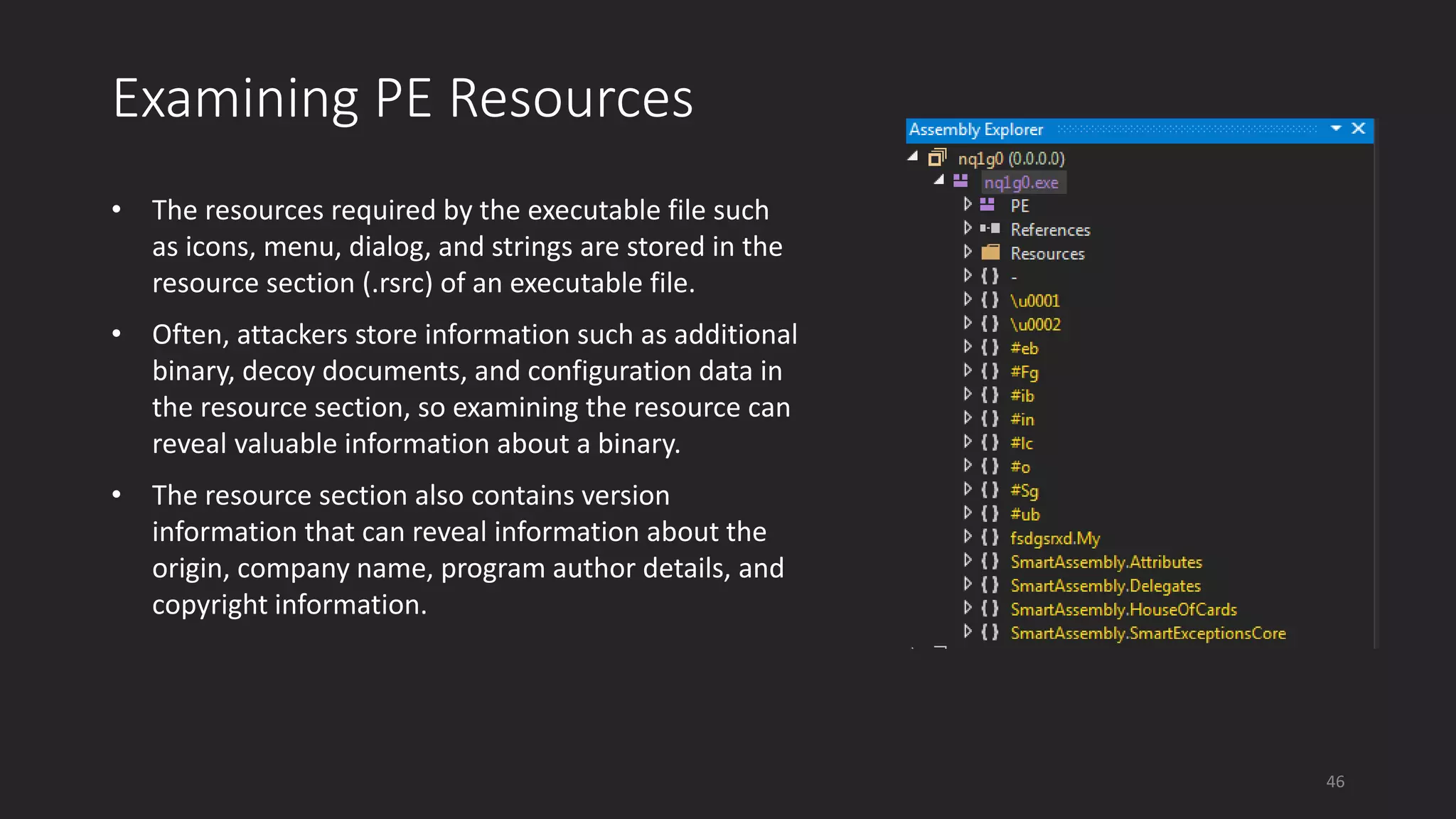
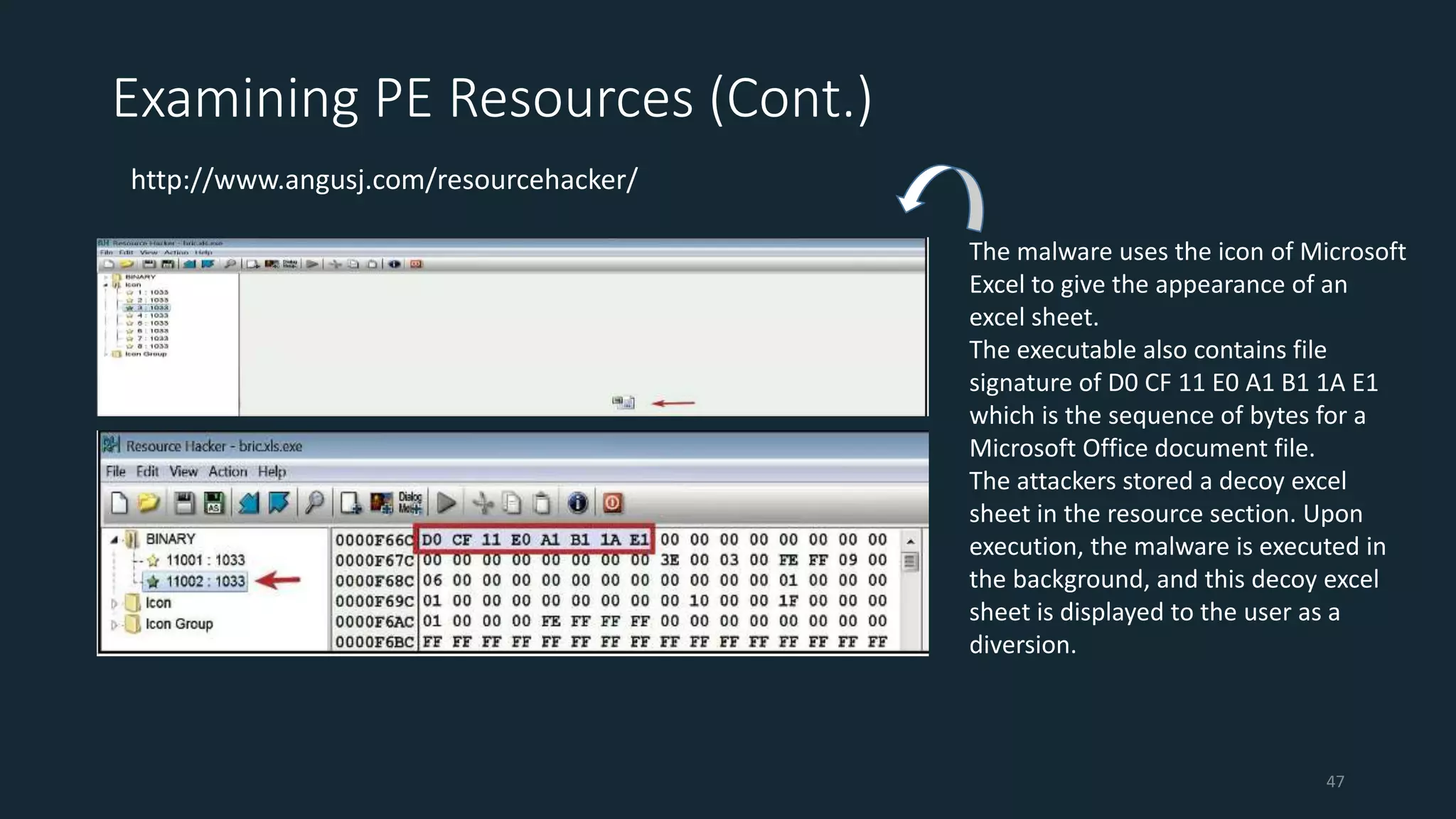
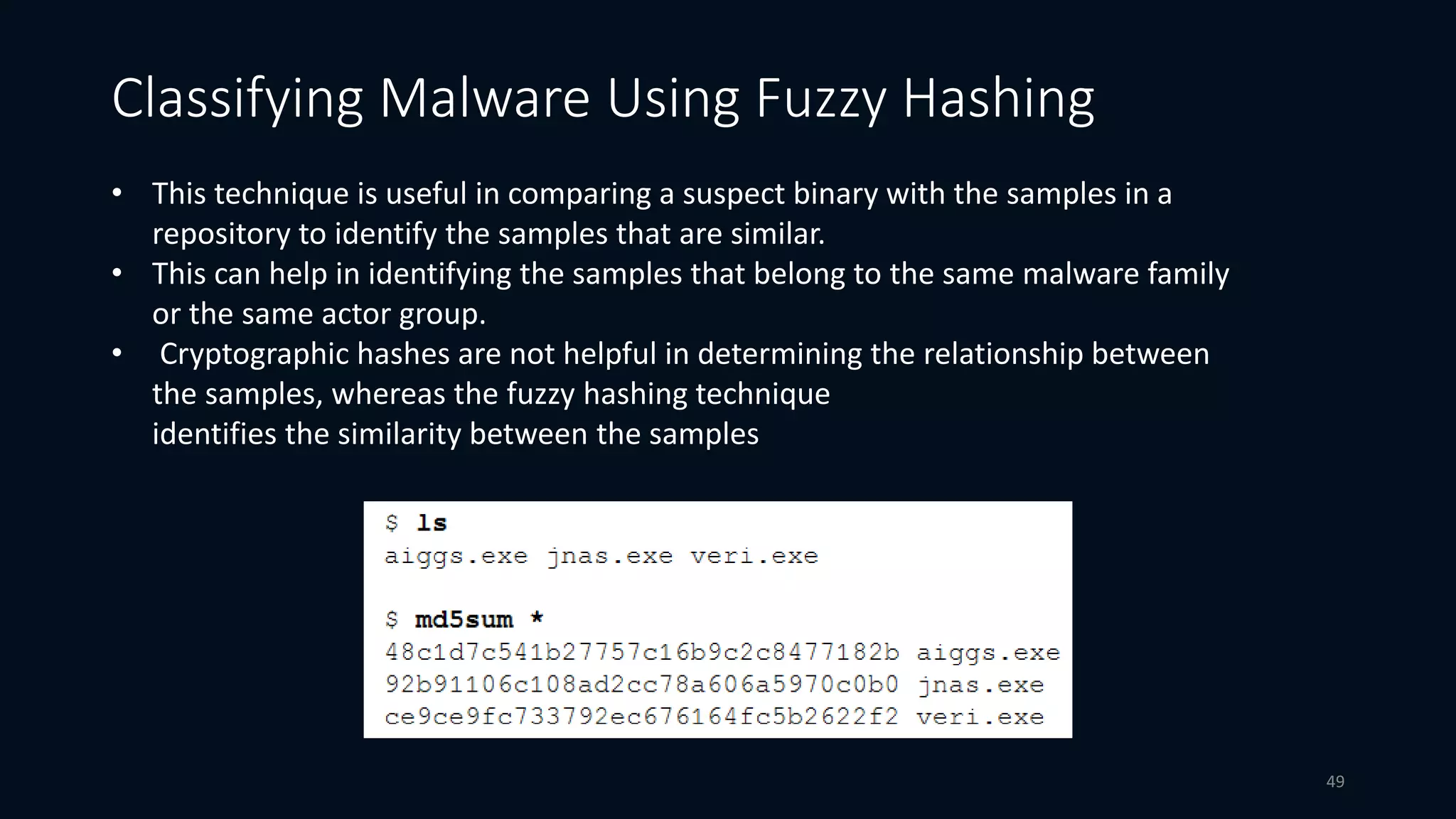
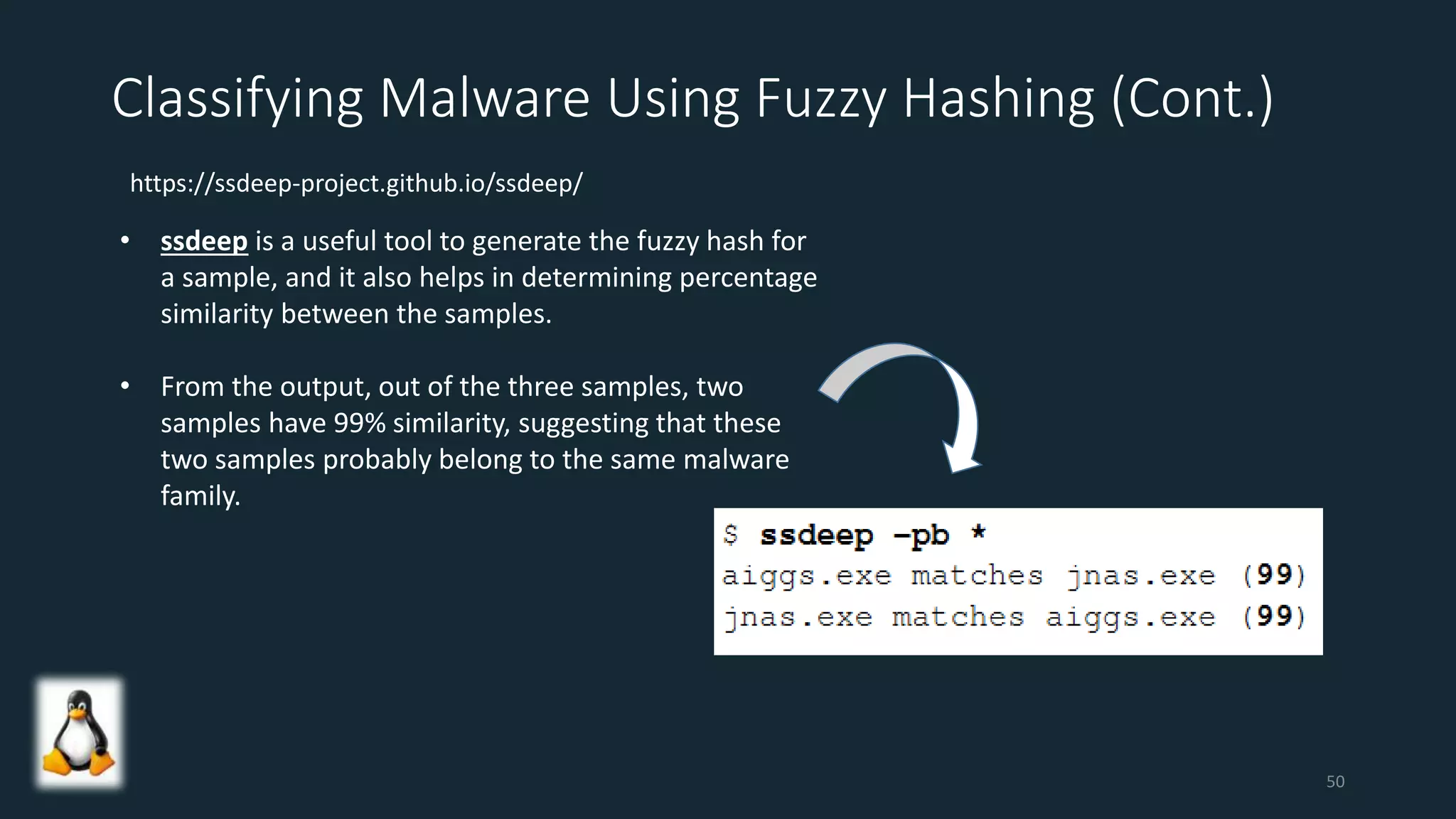
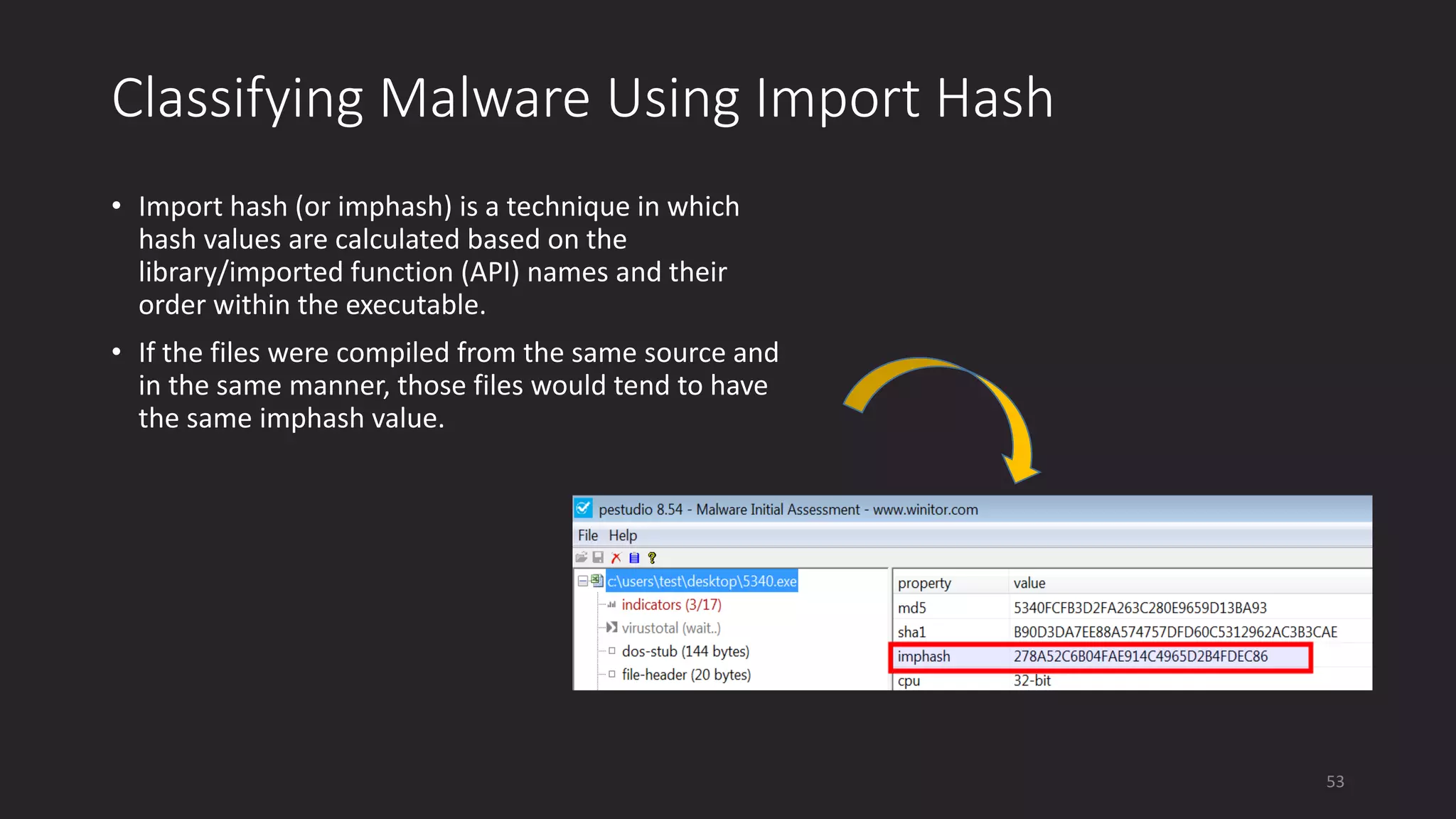
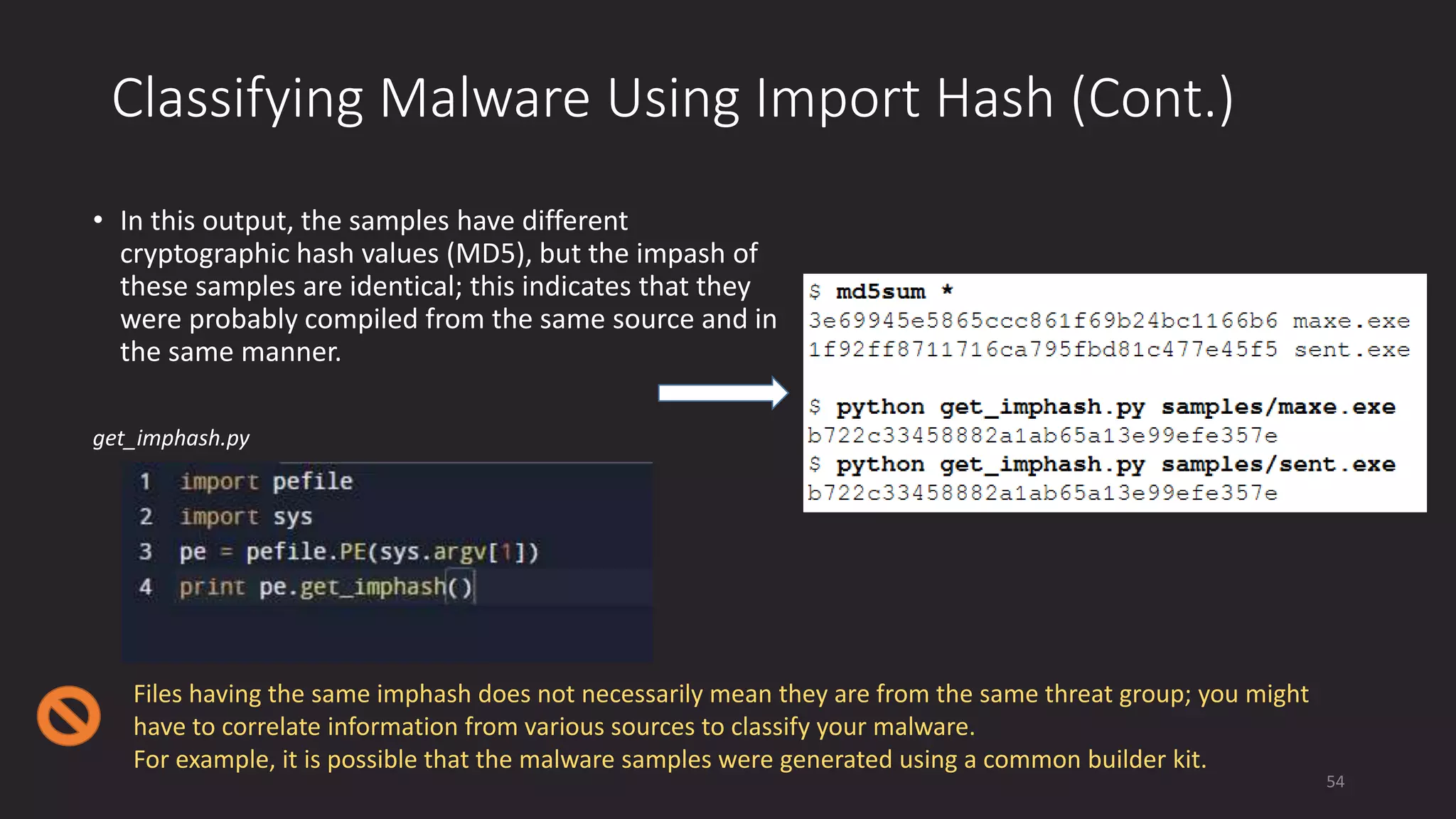
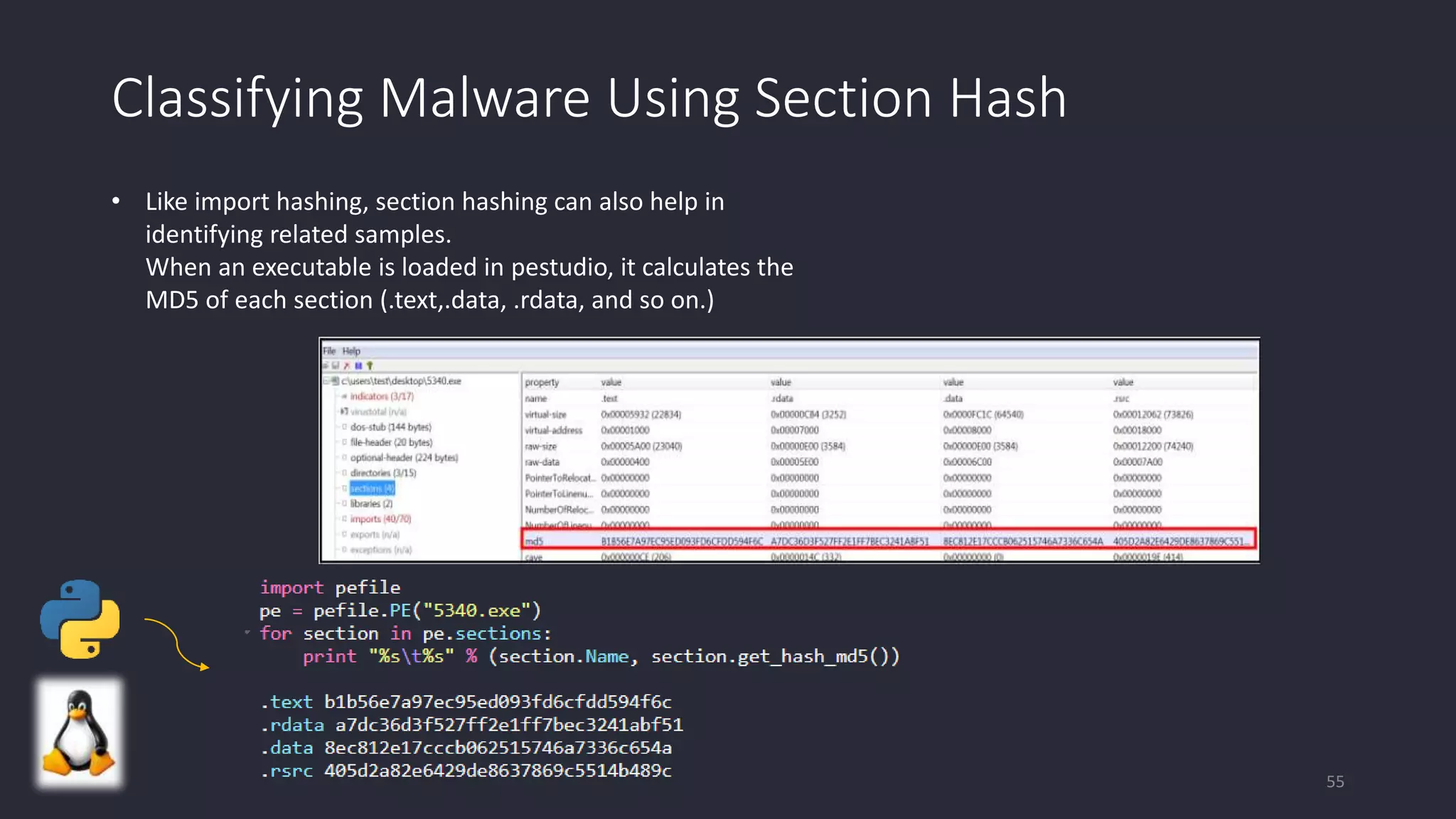
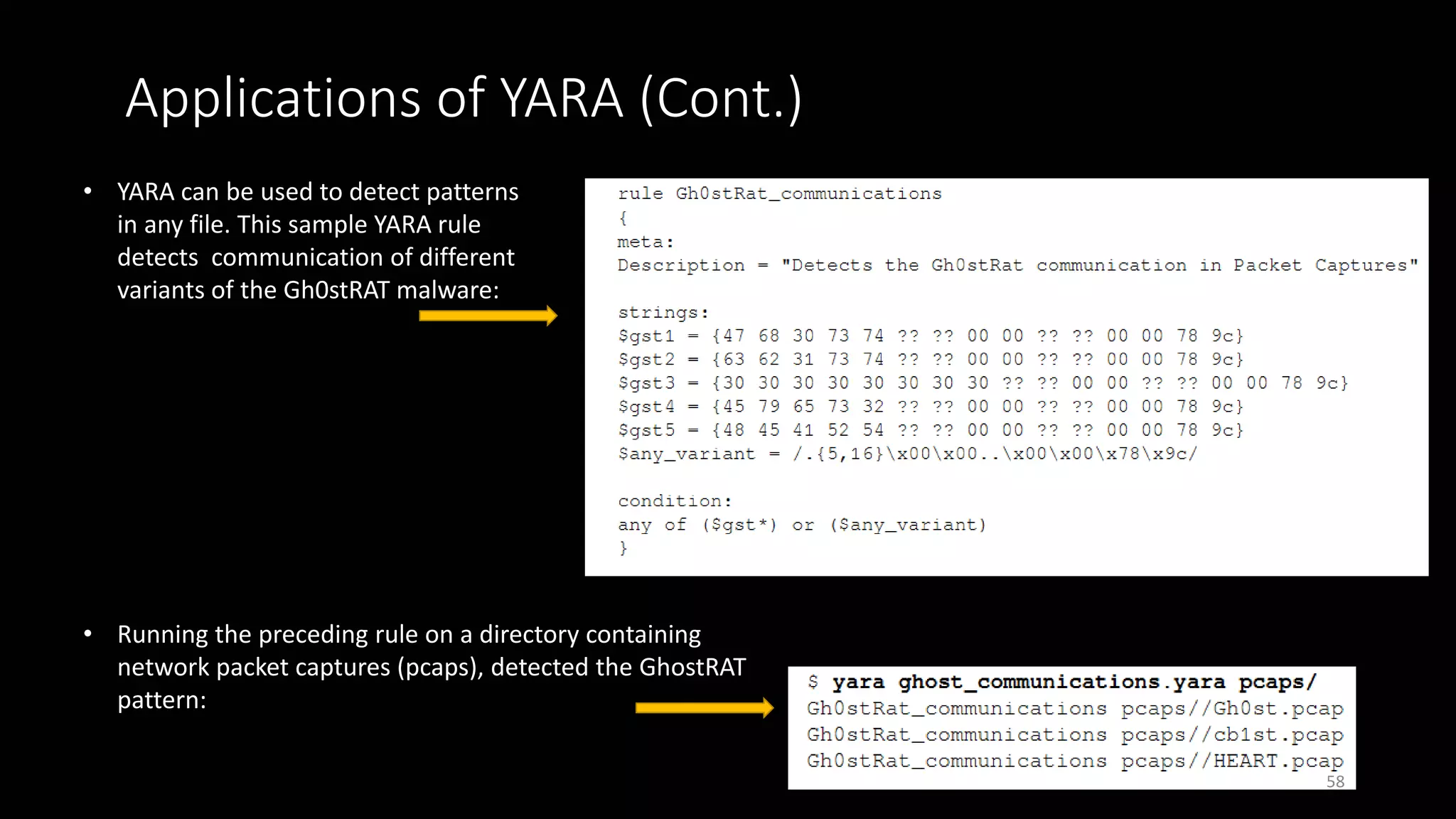
This document discusses techniques for analyzing malware samples without executing them. It covers static analysis methods like identifying the file type and architecture, fingerprinting with hashes, scanning for known signatures, extracting strings, analyzing the PE header, and comparing samples. The goal of static analysis is to learn as much as possible about the malware before executing it, in order to focus subsequent dynamic analysis efforts. Manual and automated tools are described throughout for performing static analysis tasks like string extraction, unpacking obfuscated files, and classifying samples.