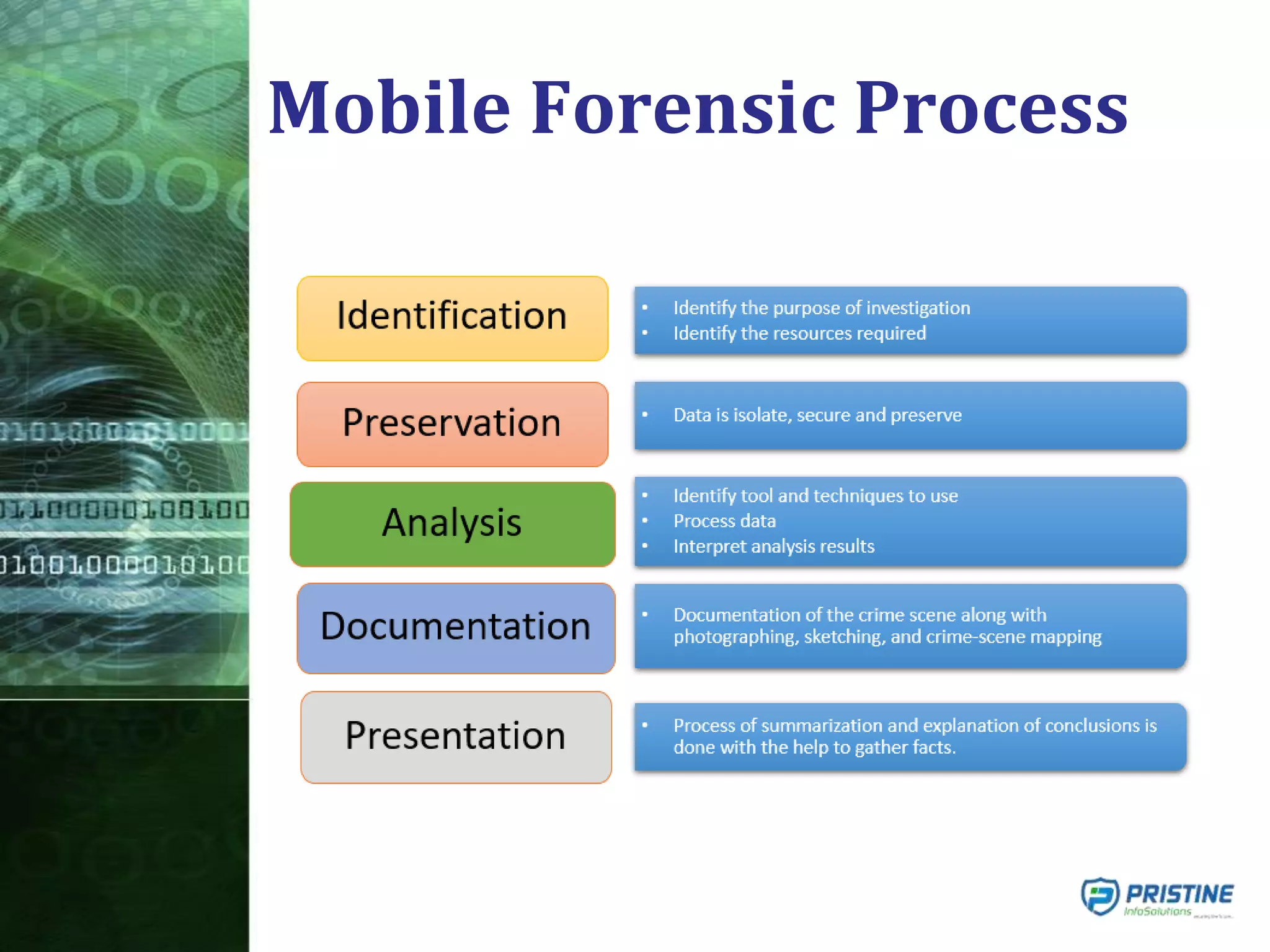
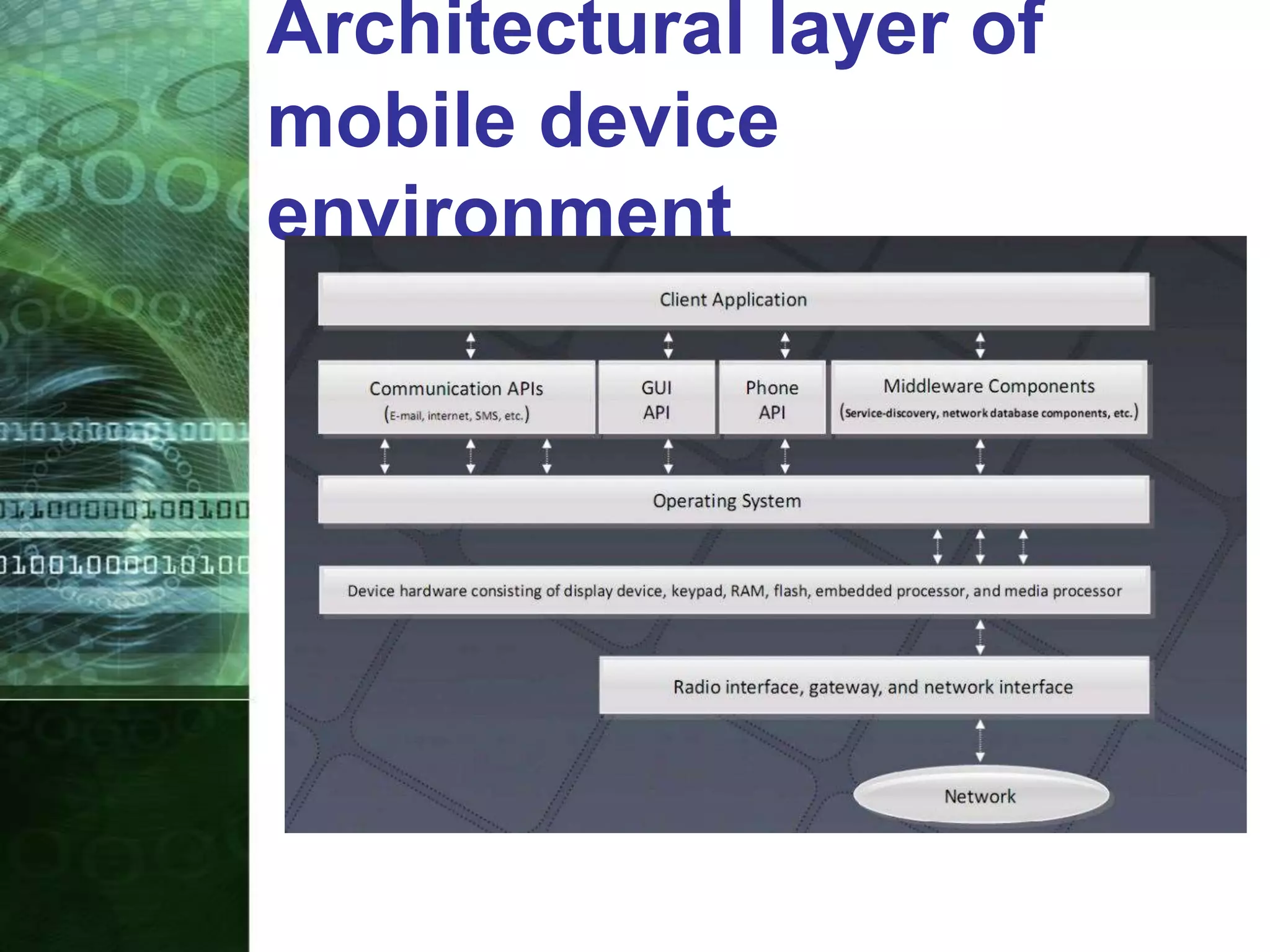
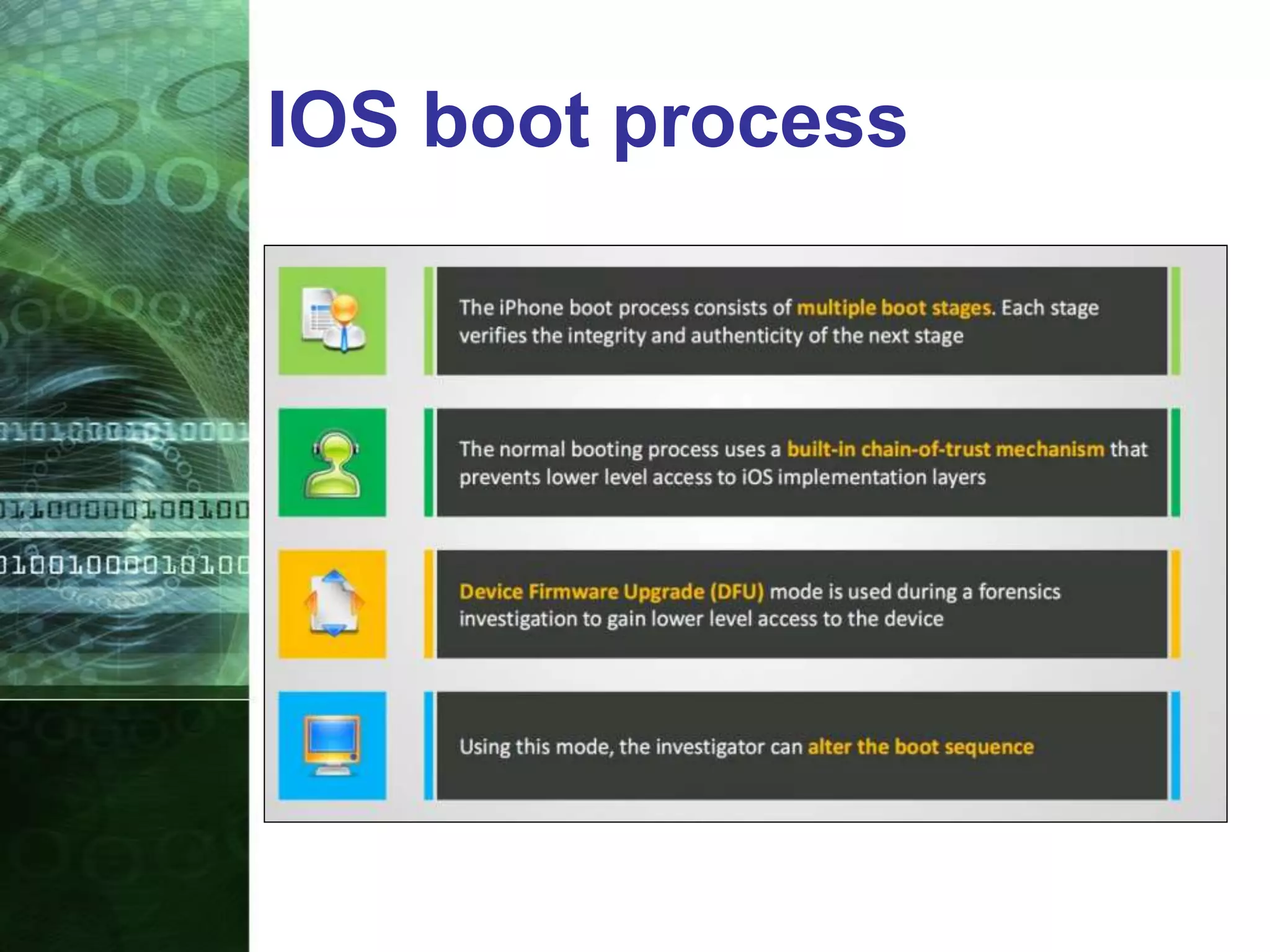
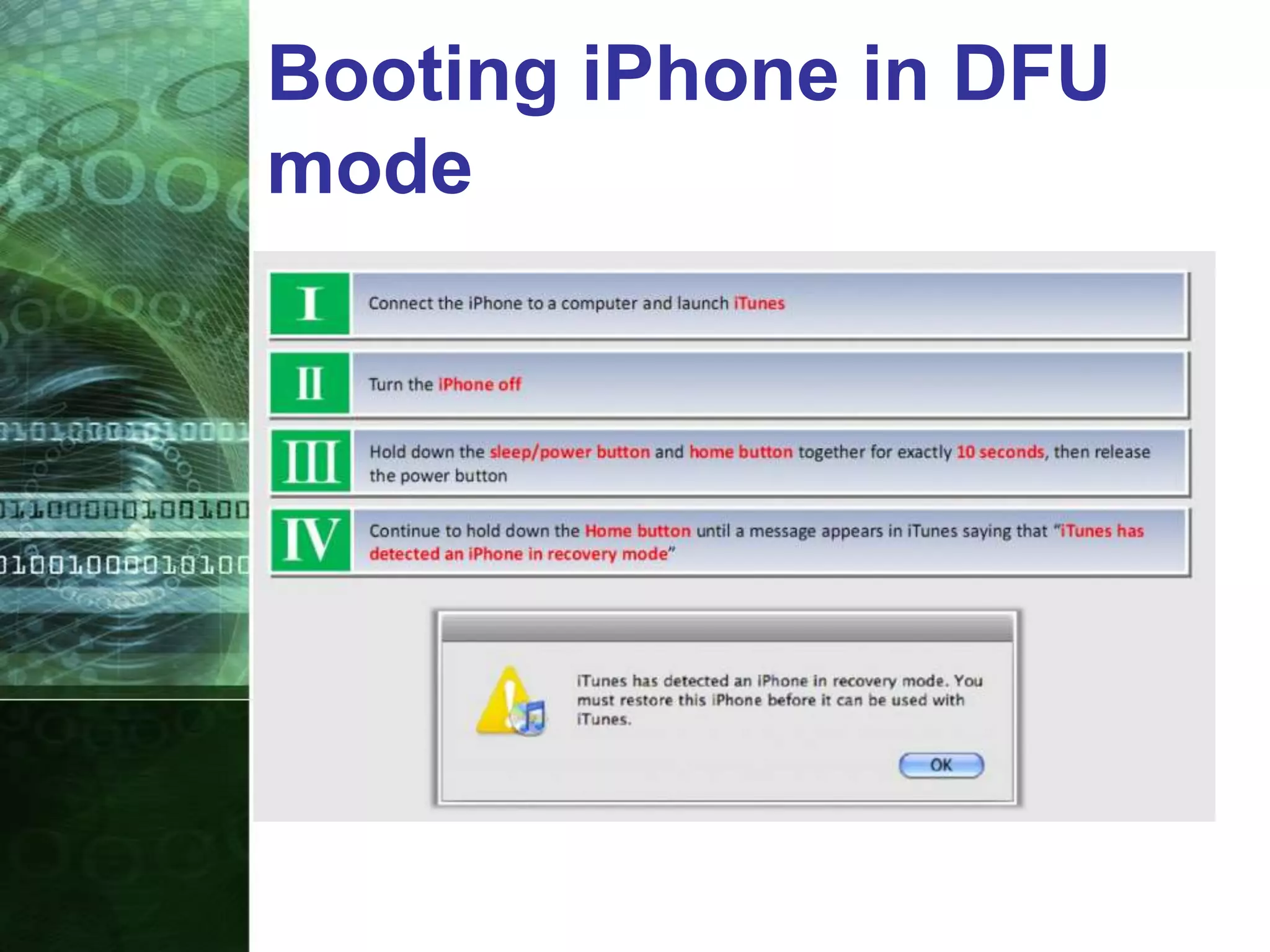
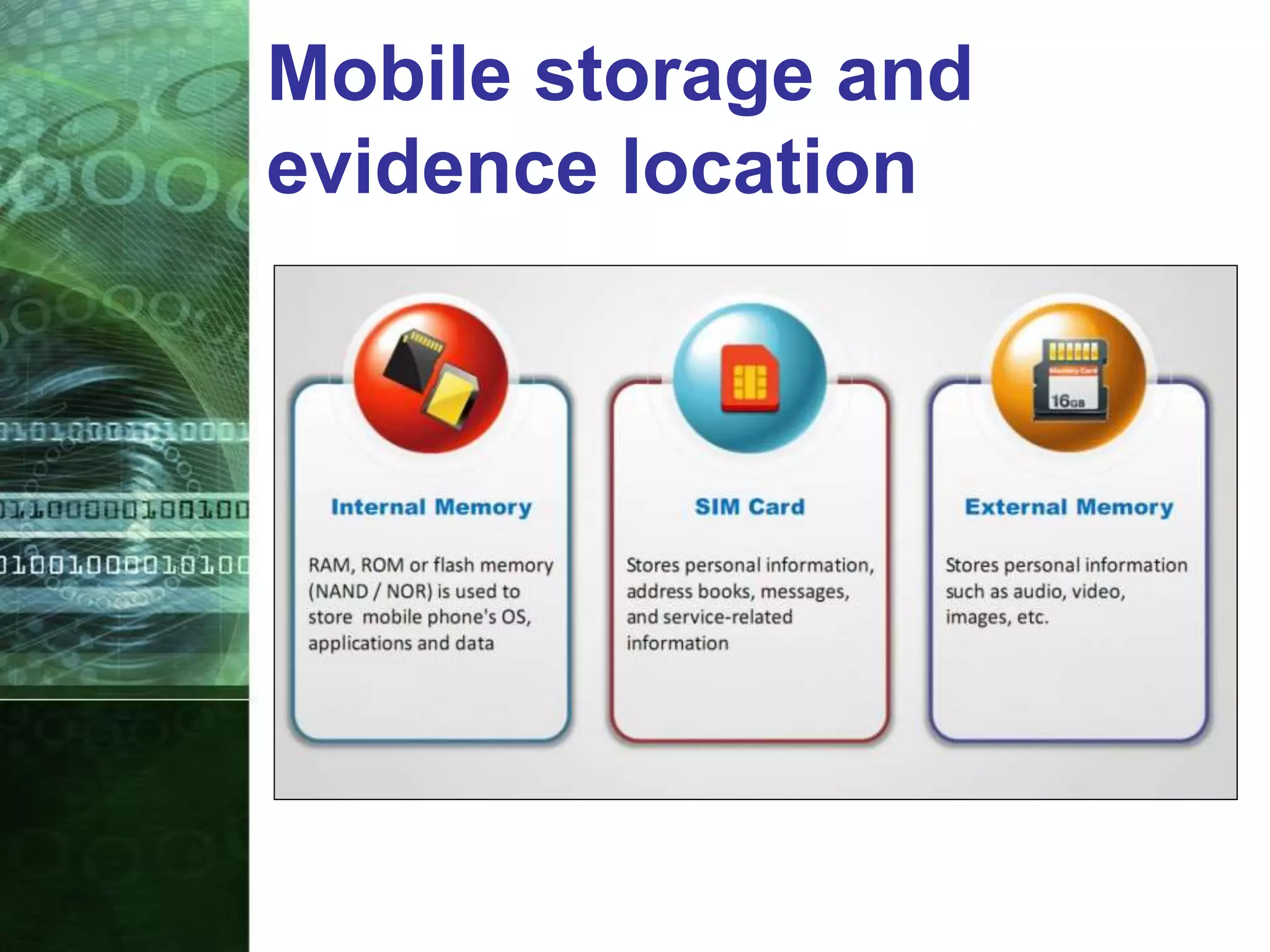
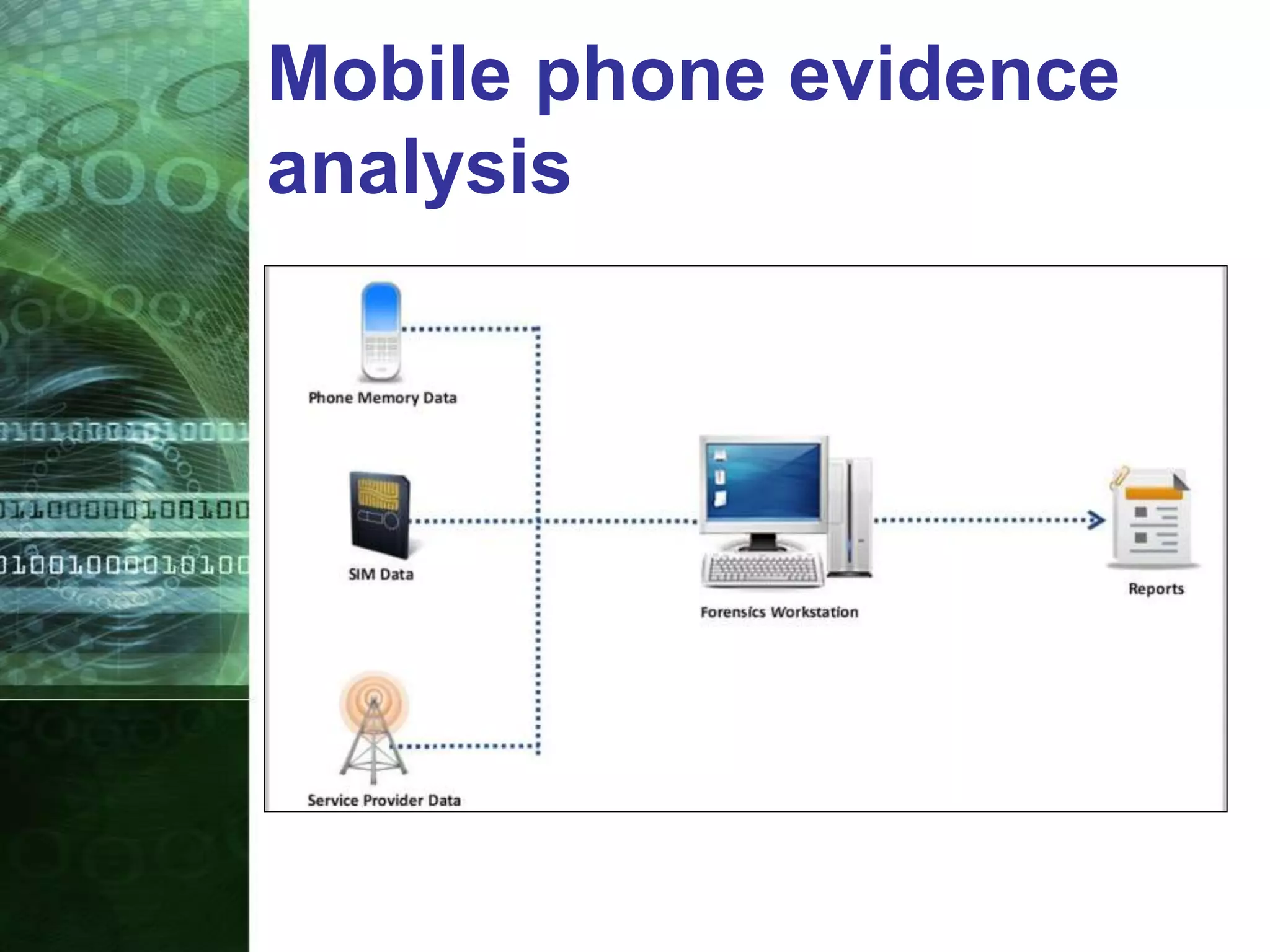
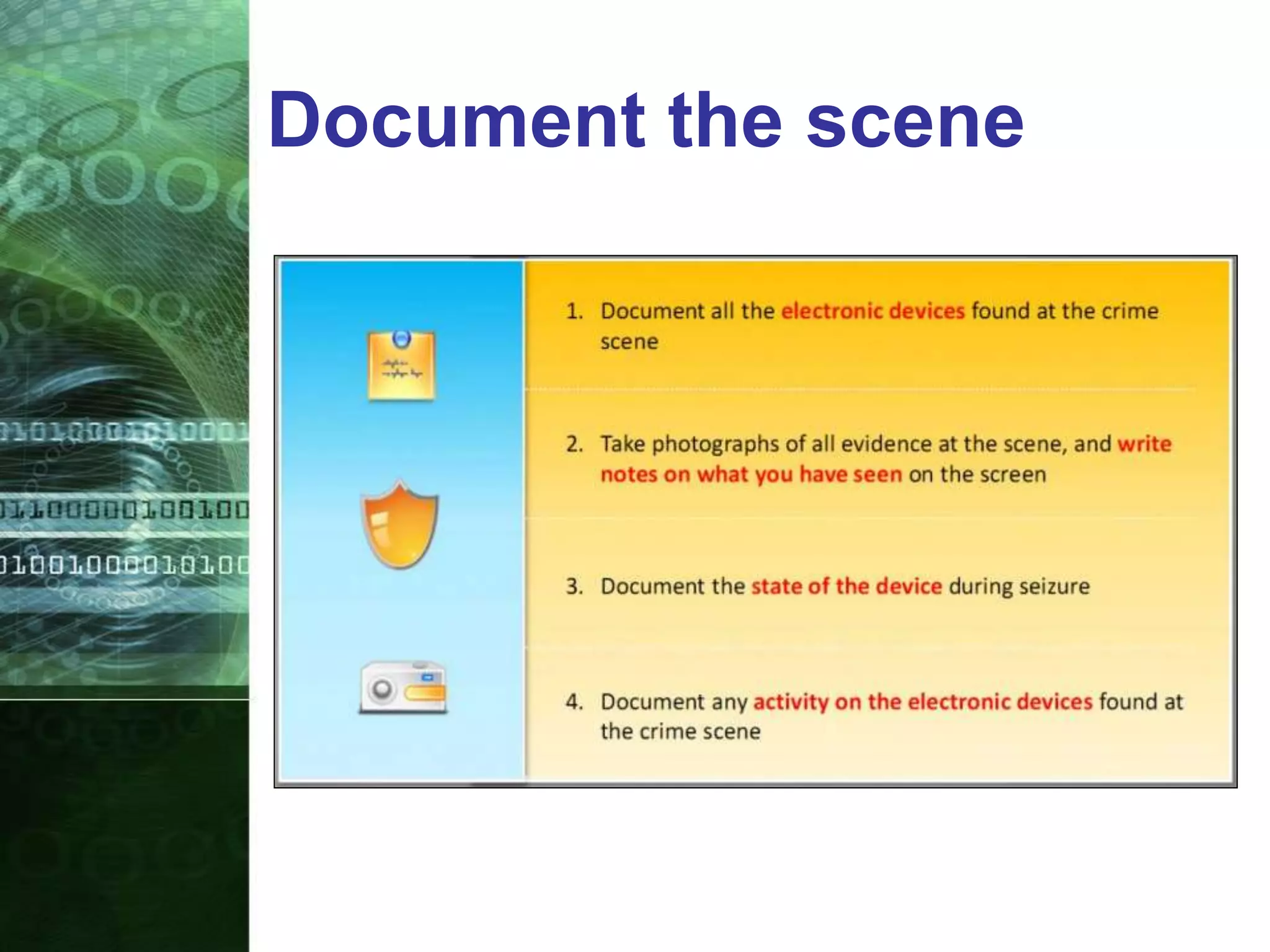
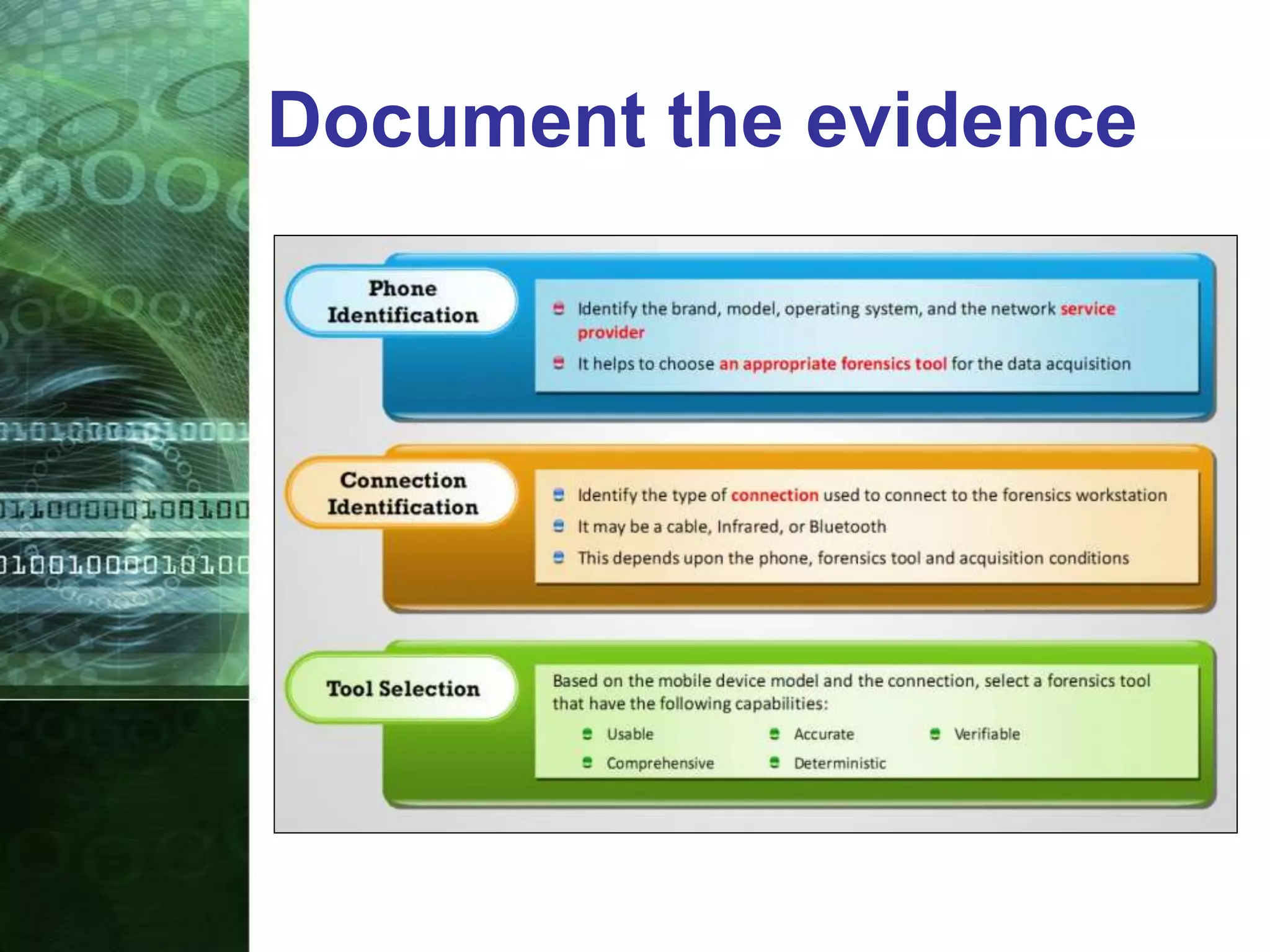
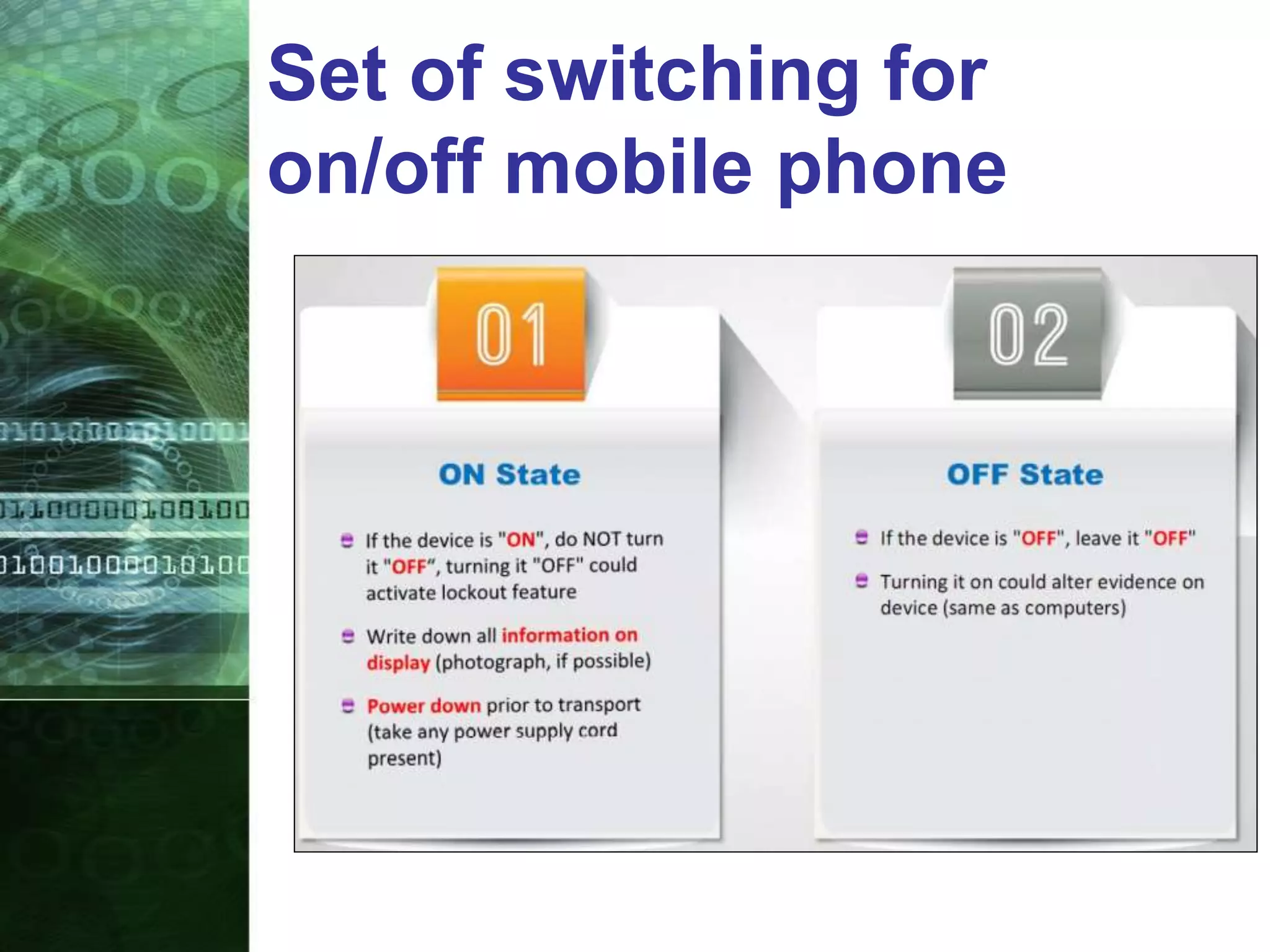
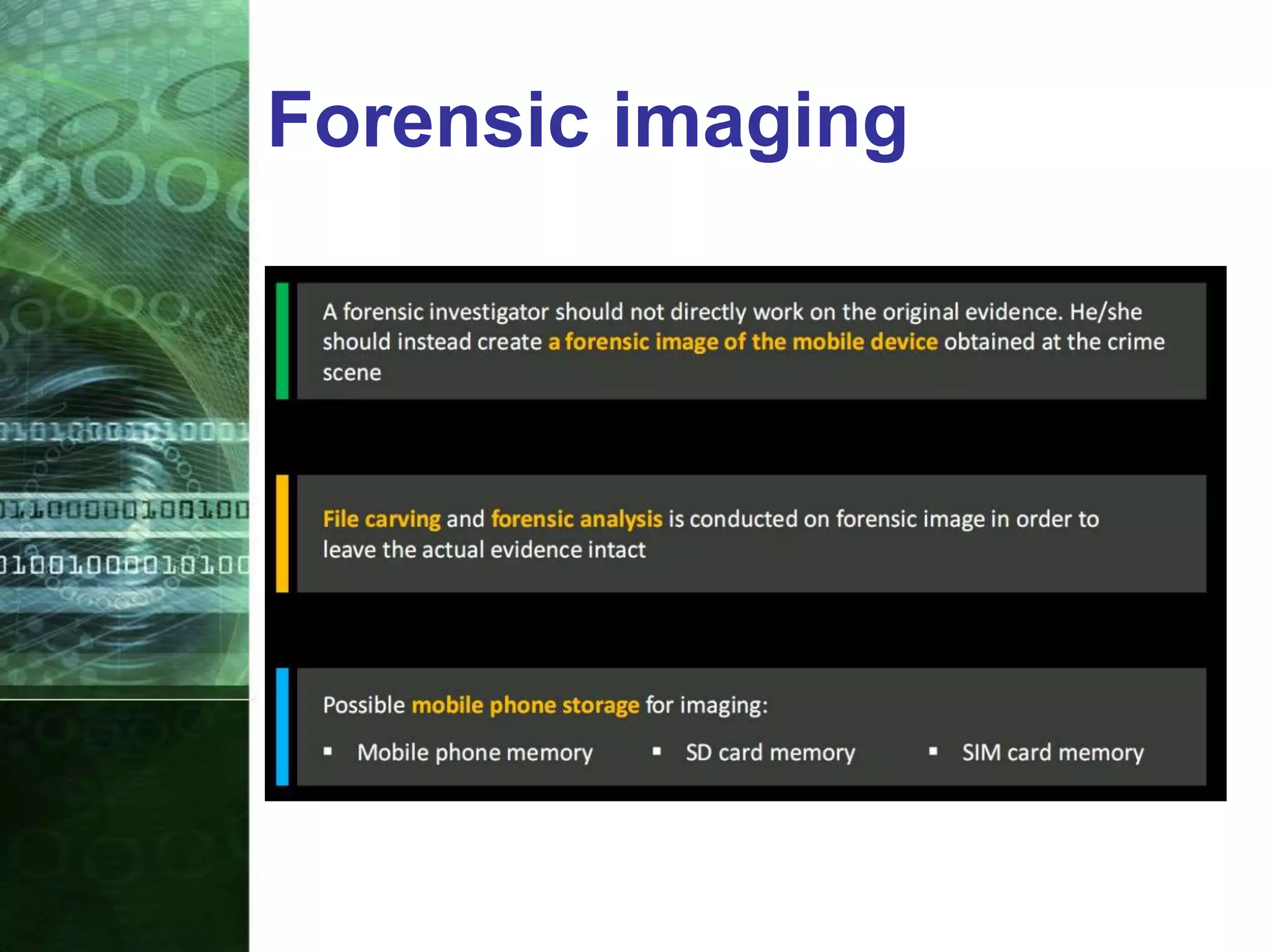
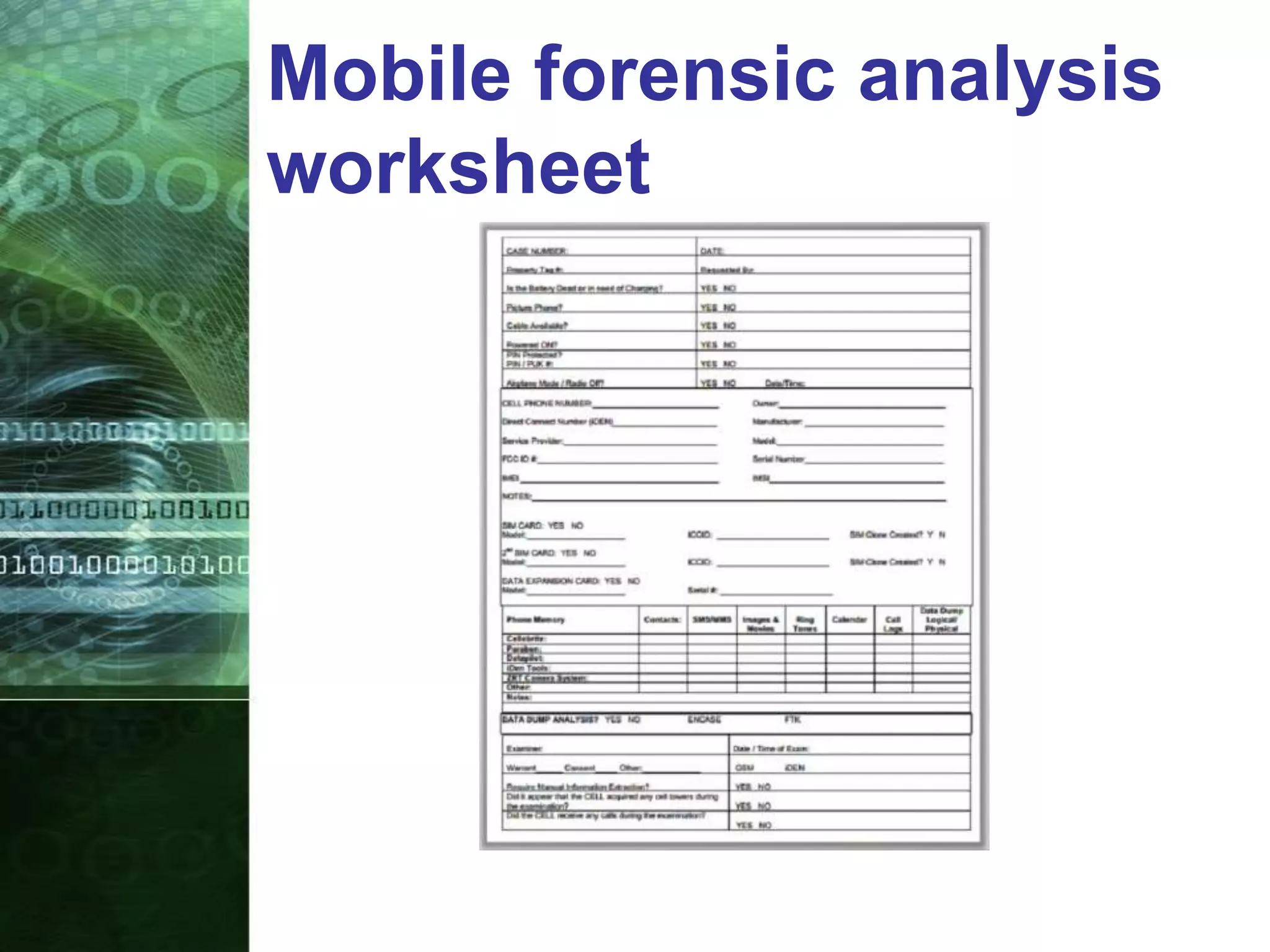
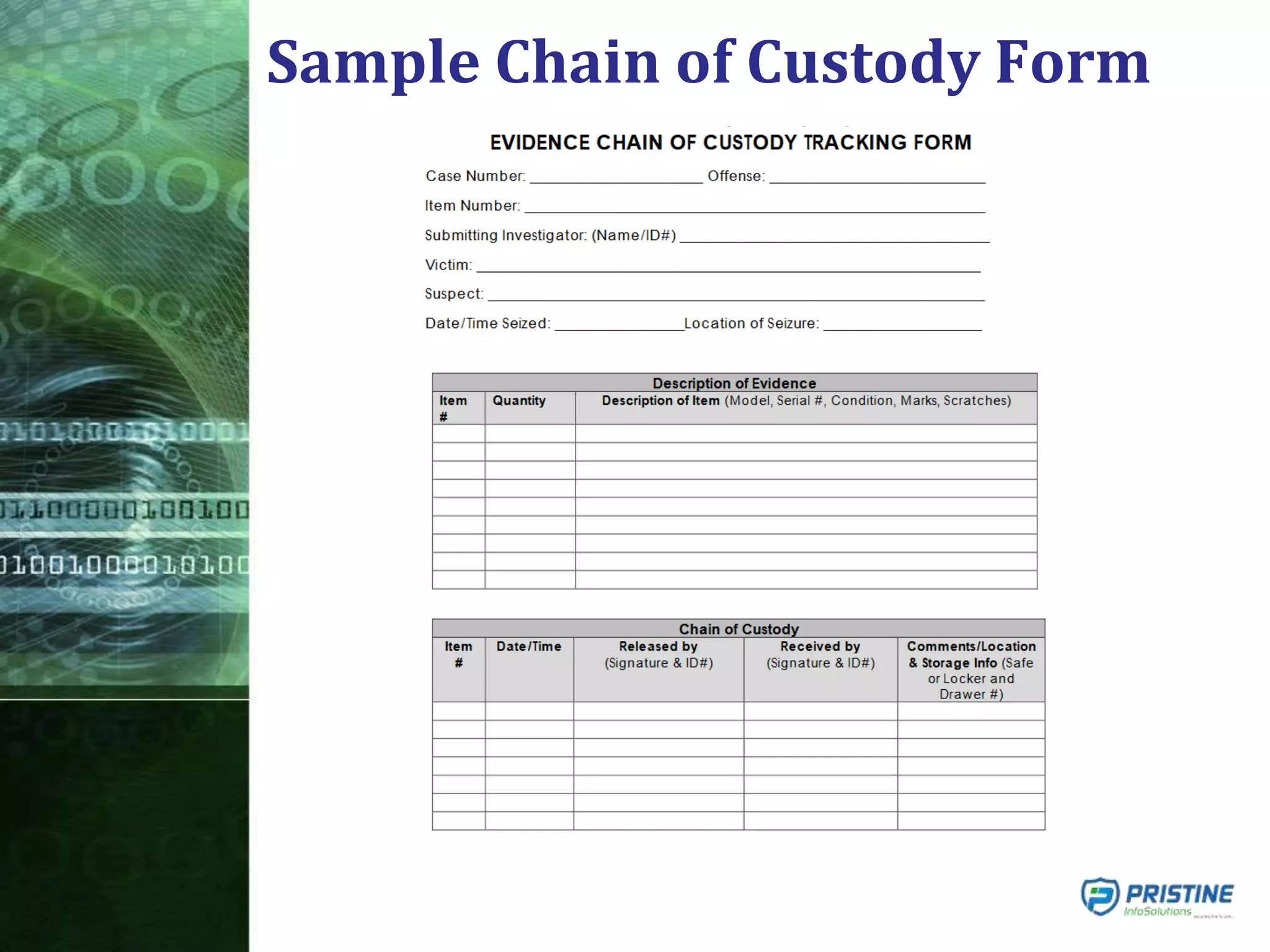
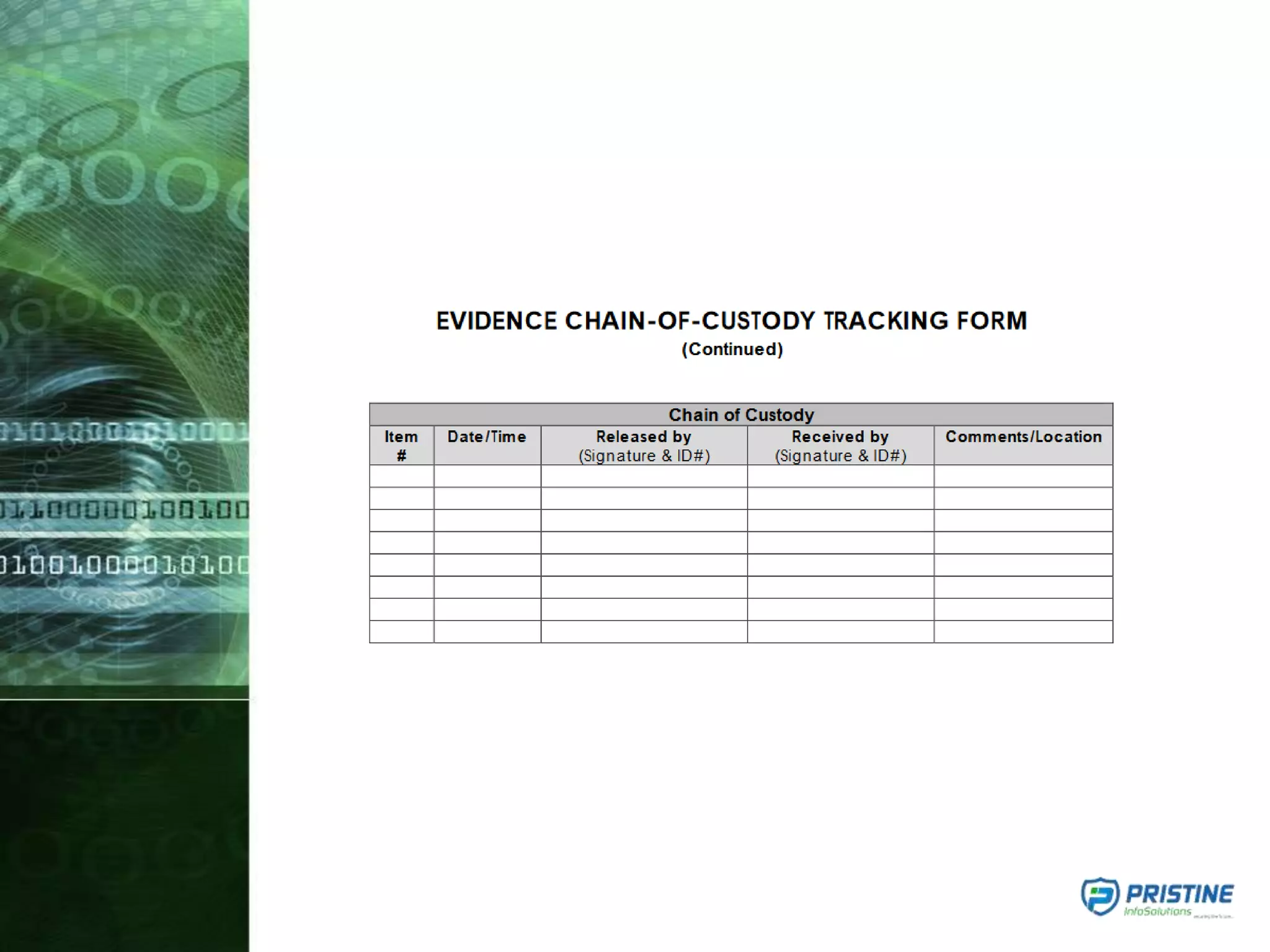
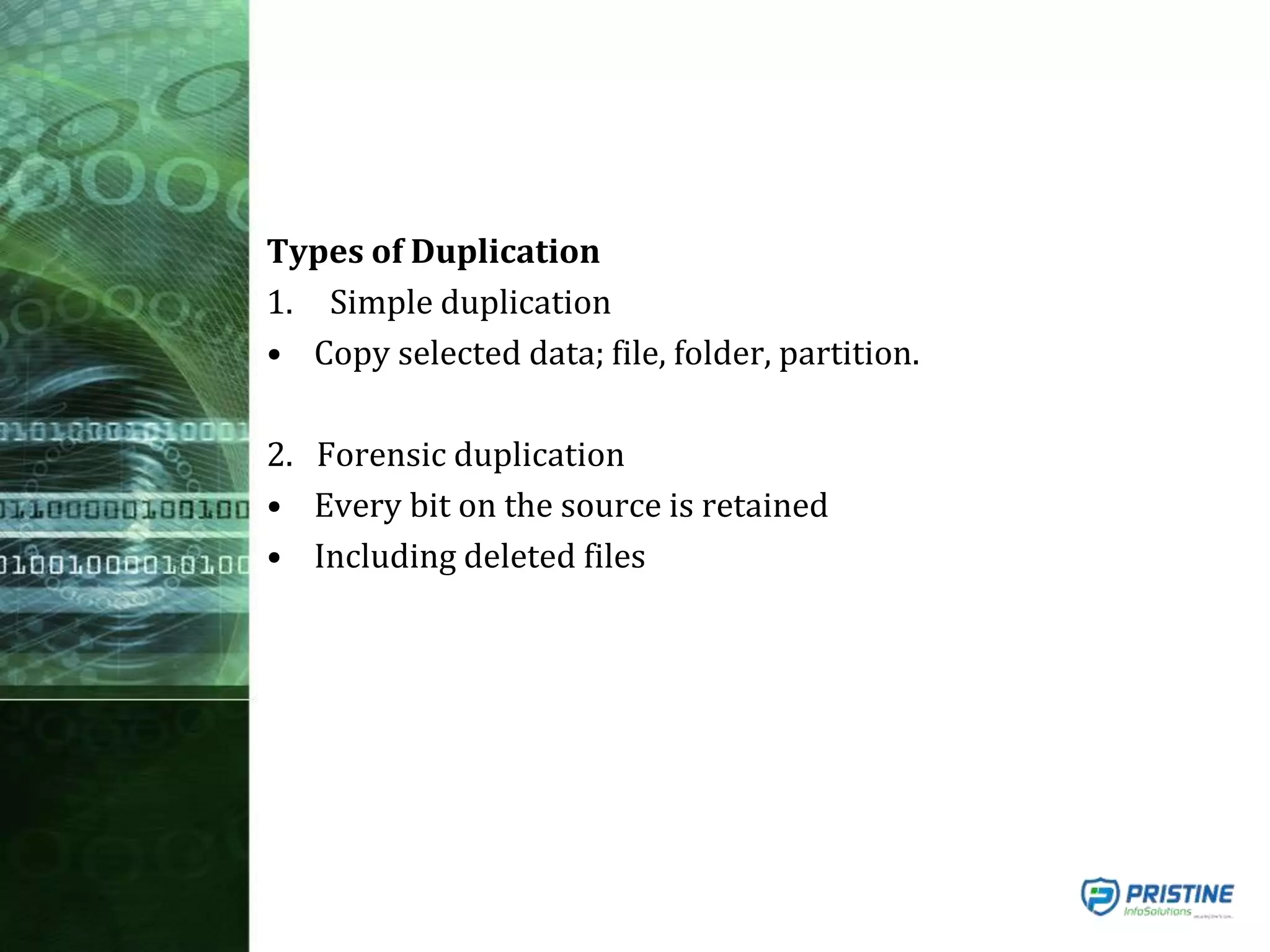
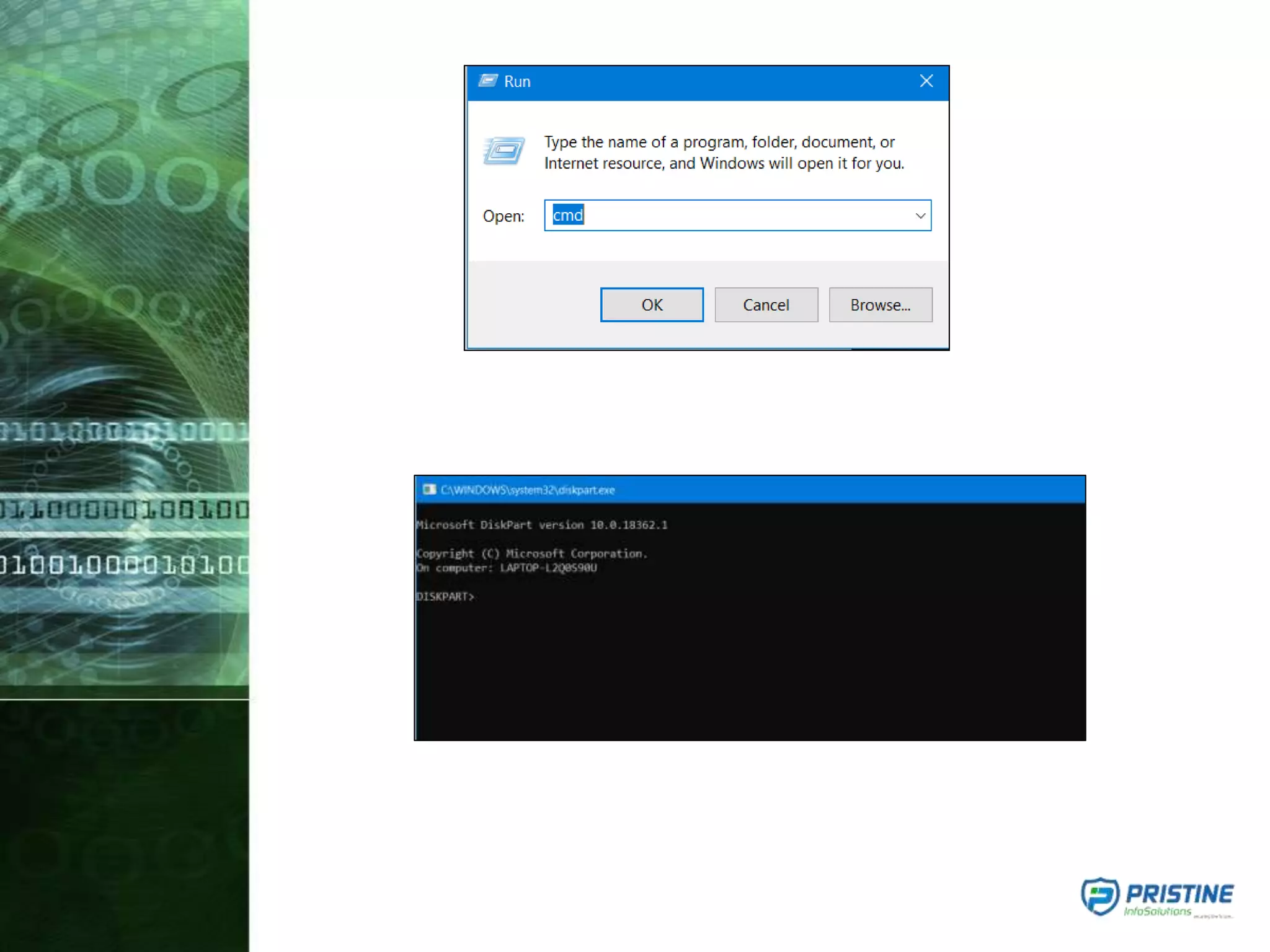
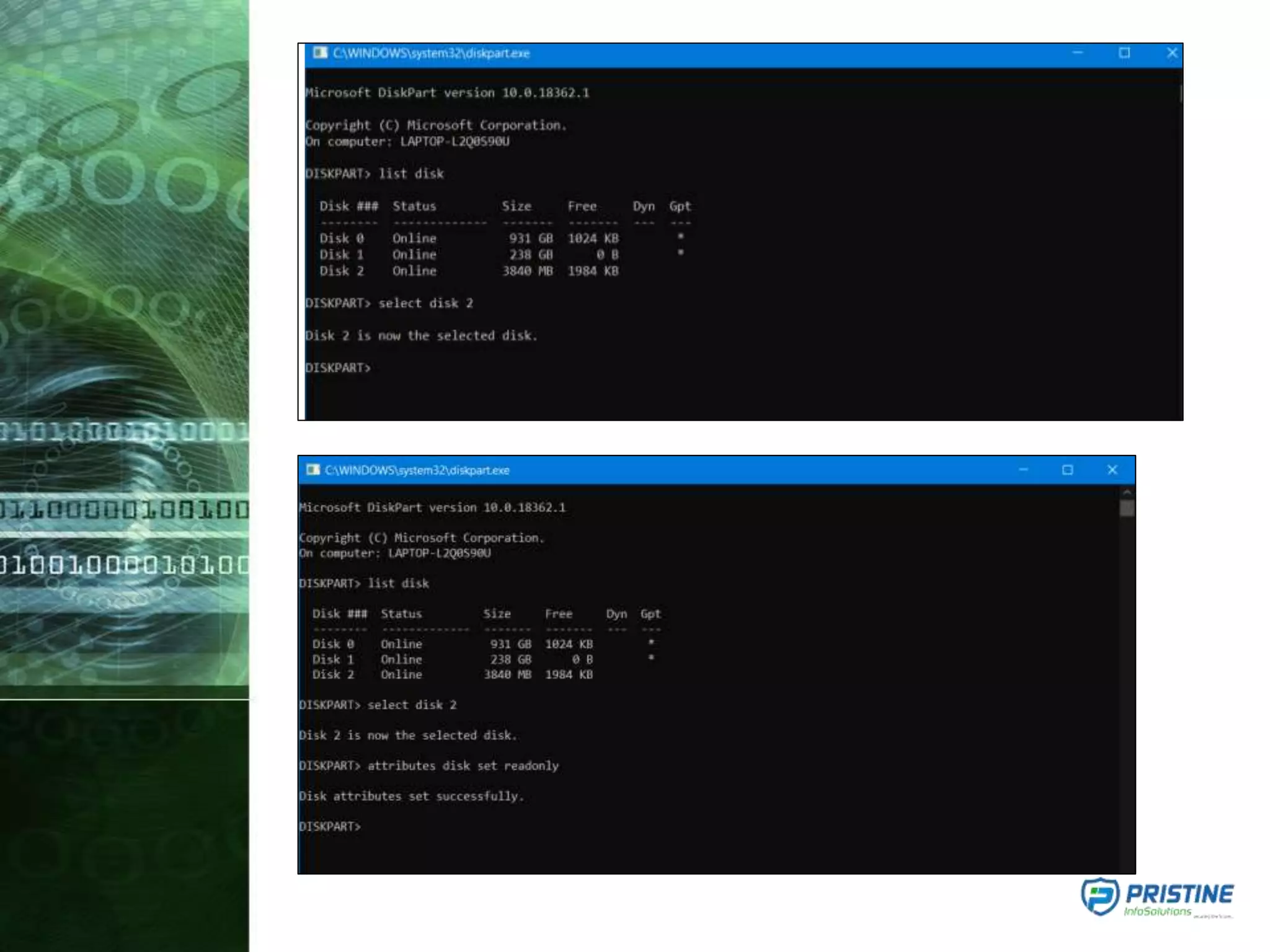
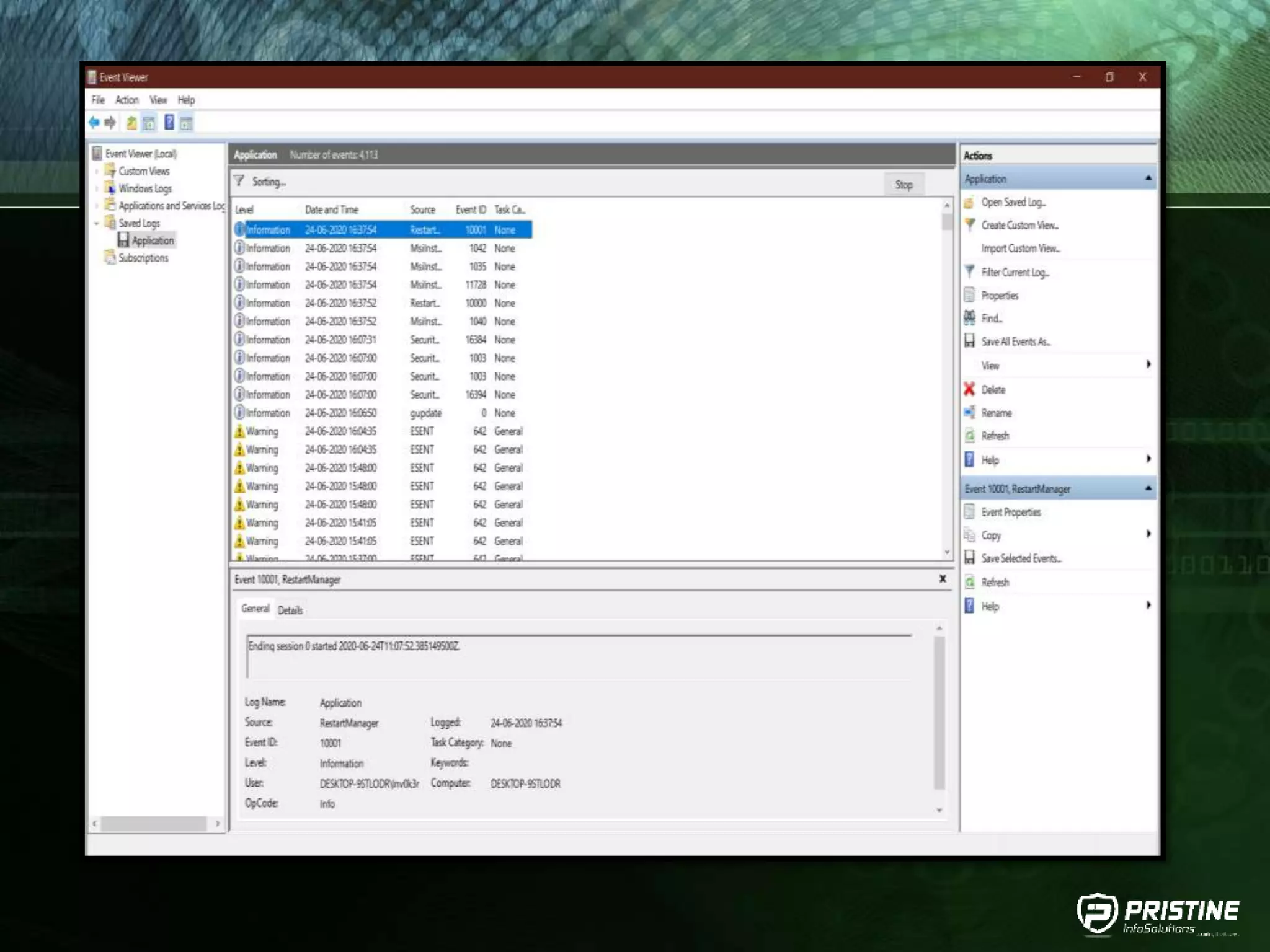
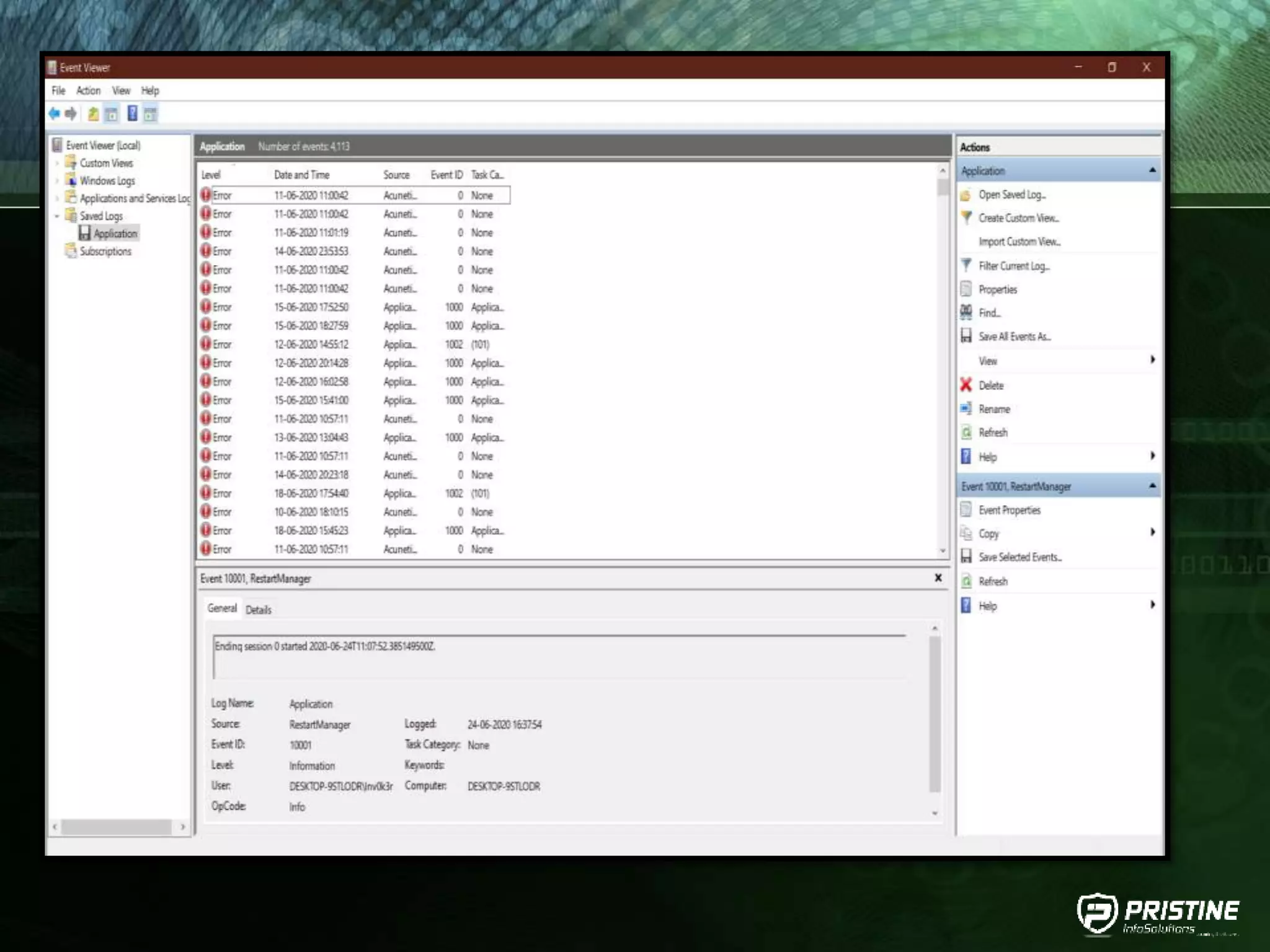
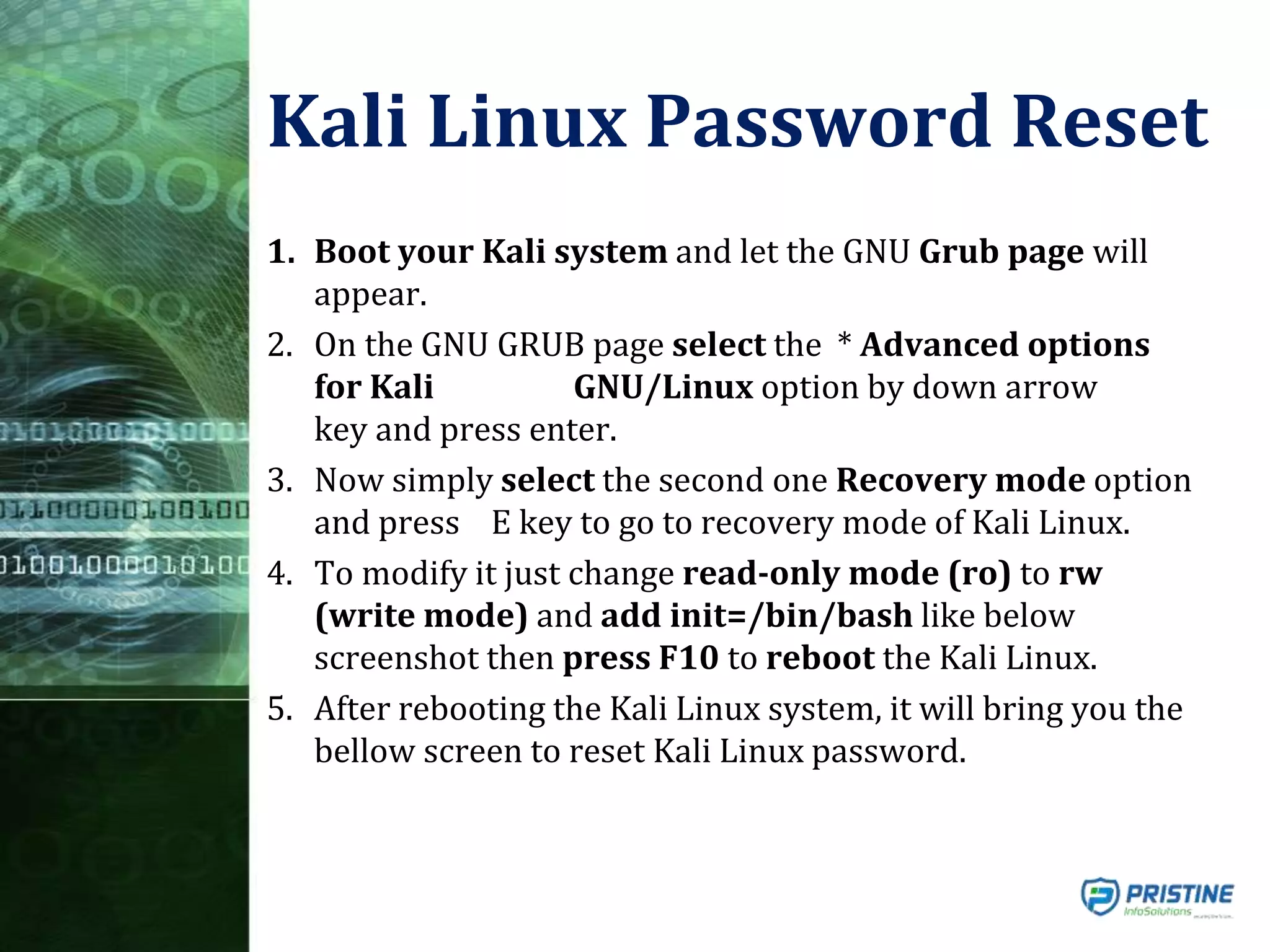
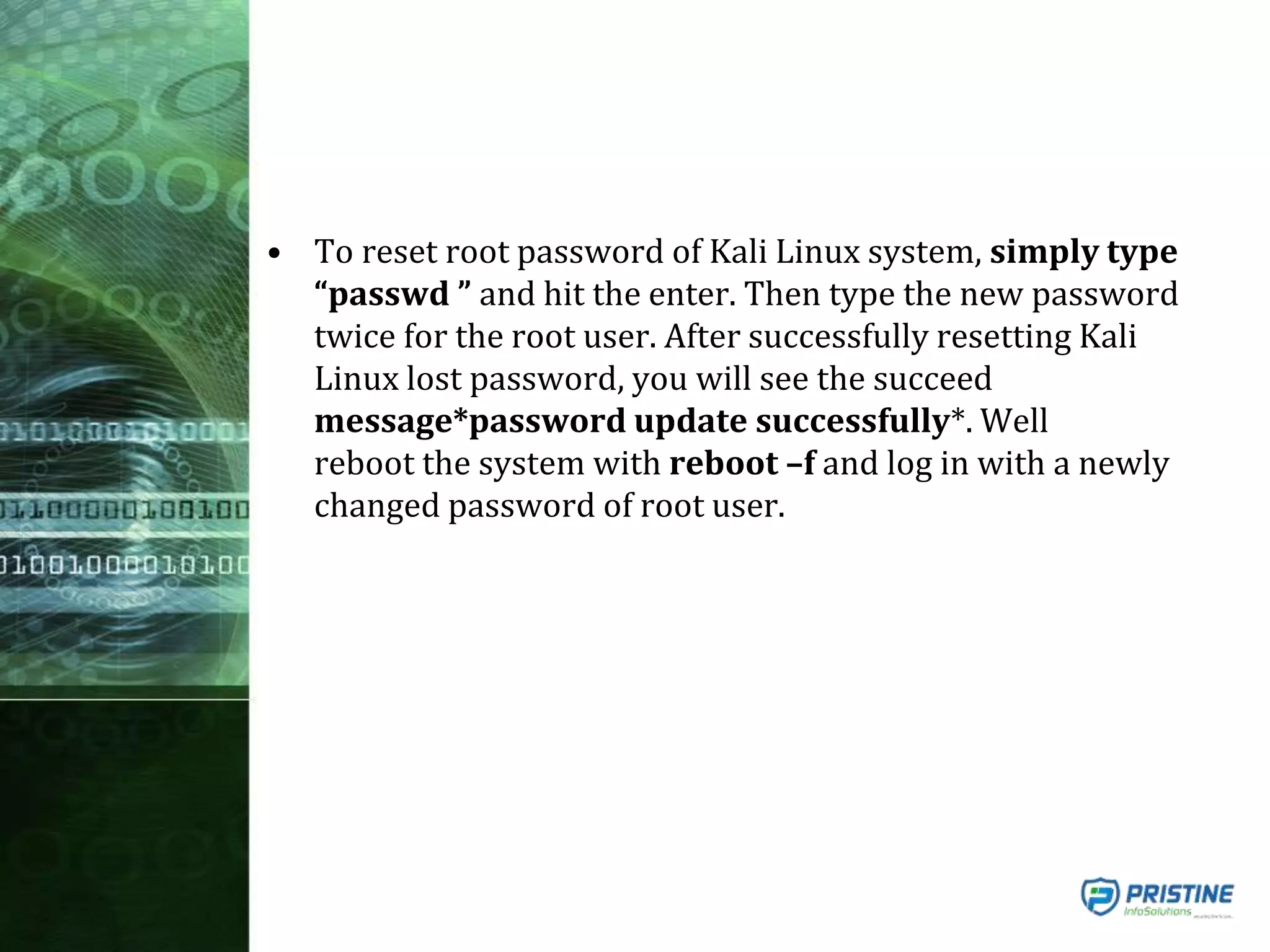
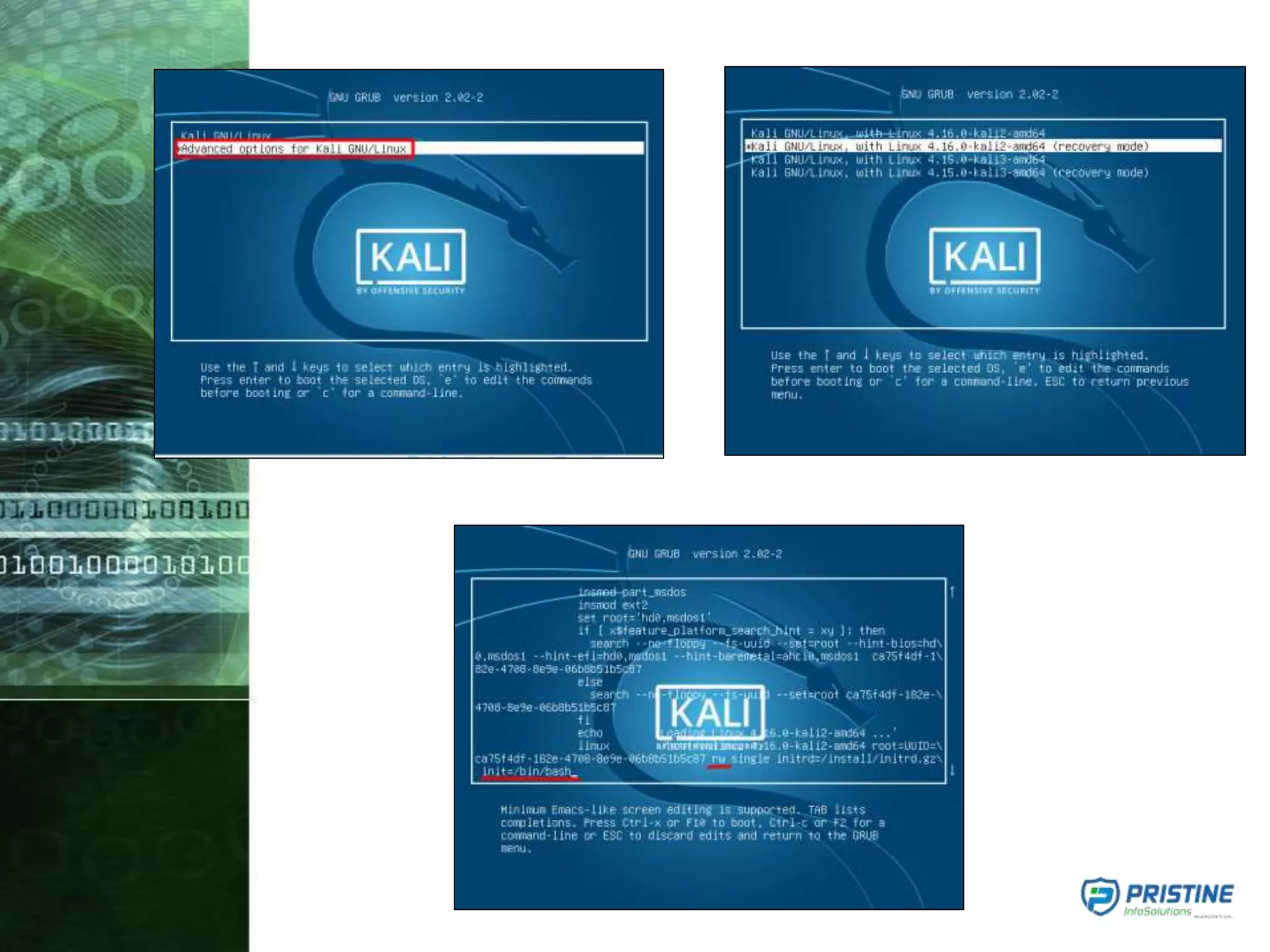
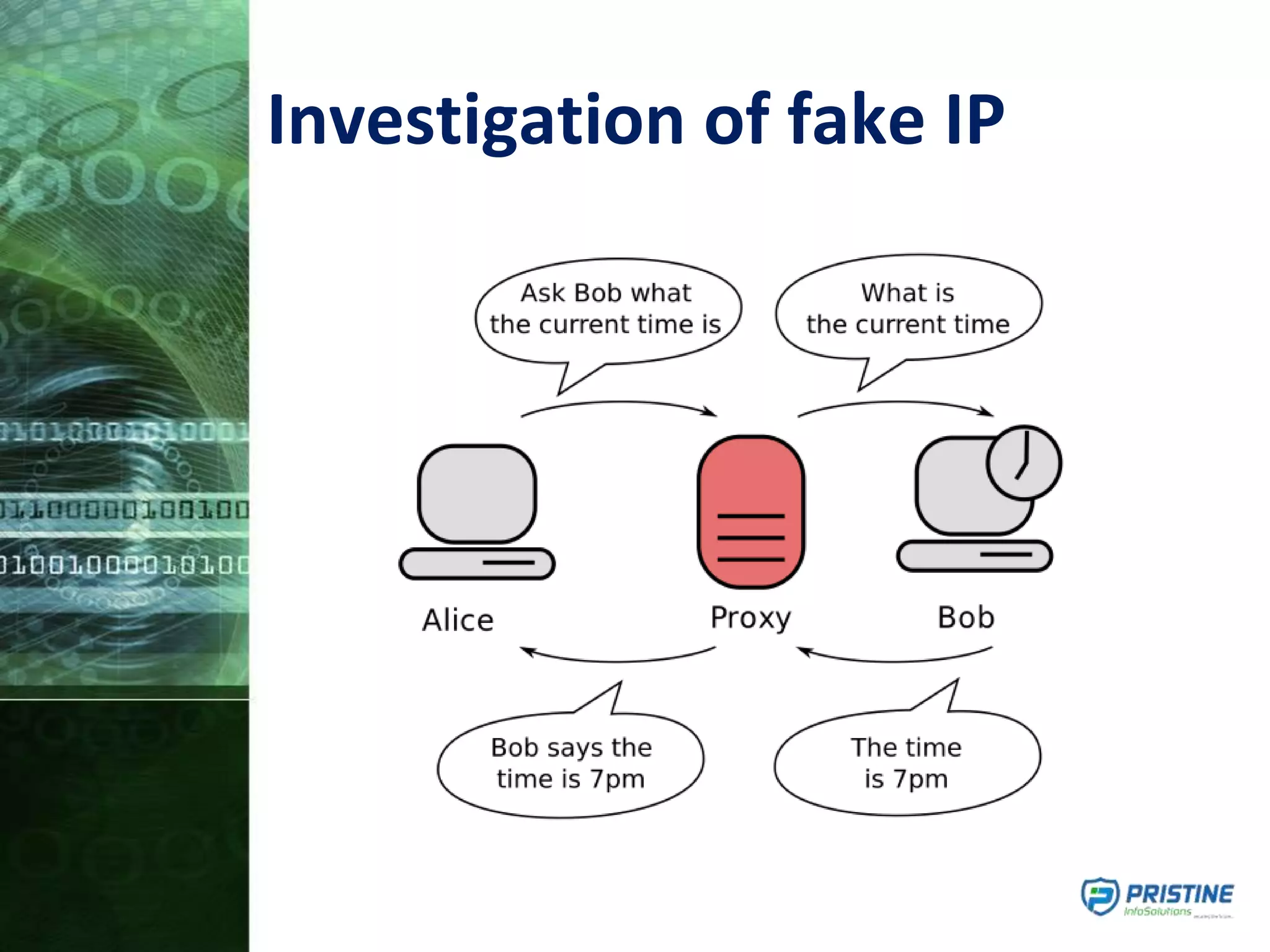
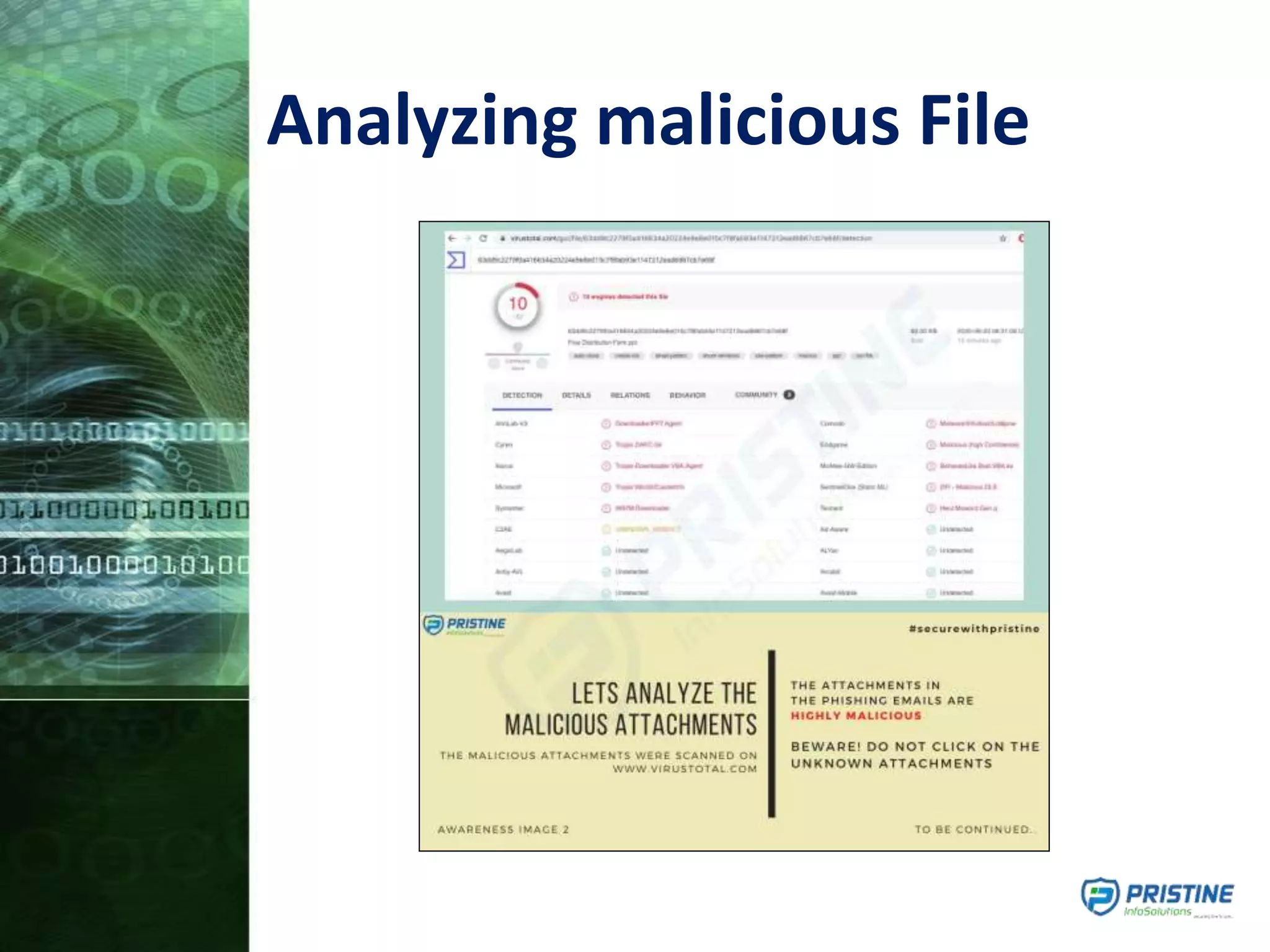
This document provides an overview of mobile forensics. It discusses key topics like the mobile forensics process, goals of mobile forensics, challenges with acquiring evidence from mobile devices, and analyzing different types of evidence. Specific techniques discussed include hashing, write protection, recovering deleted data through tools like Disk Drill, analyzing Windows and Linux event logs, and investigating malicious files. The document outlines the various components involved in a mobile forensics investigation from acquiring evidence to documenting the chain of custody.