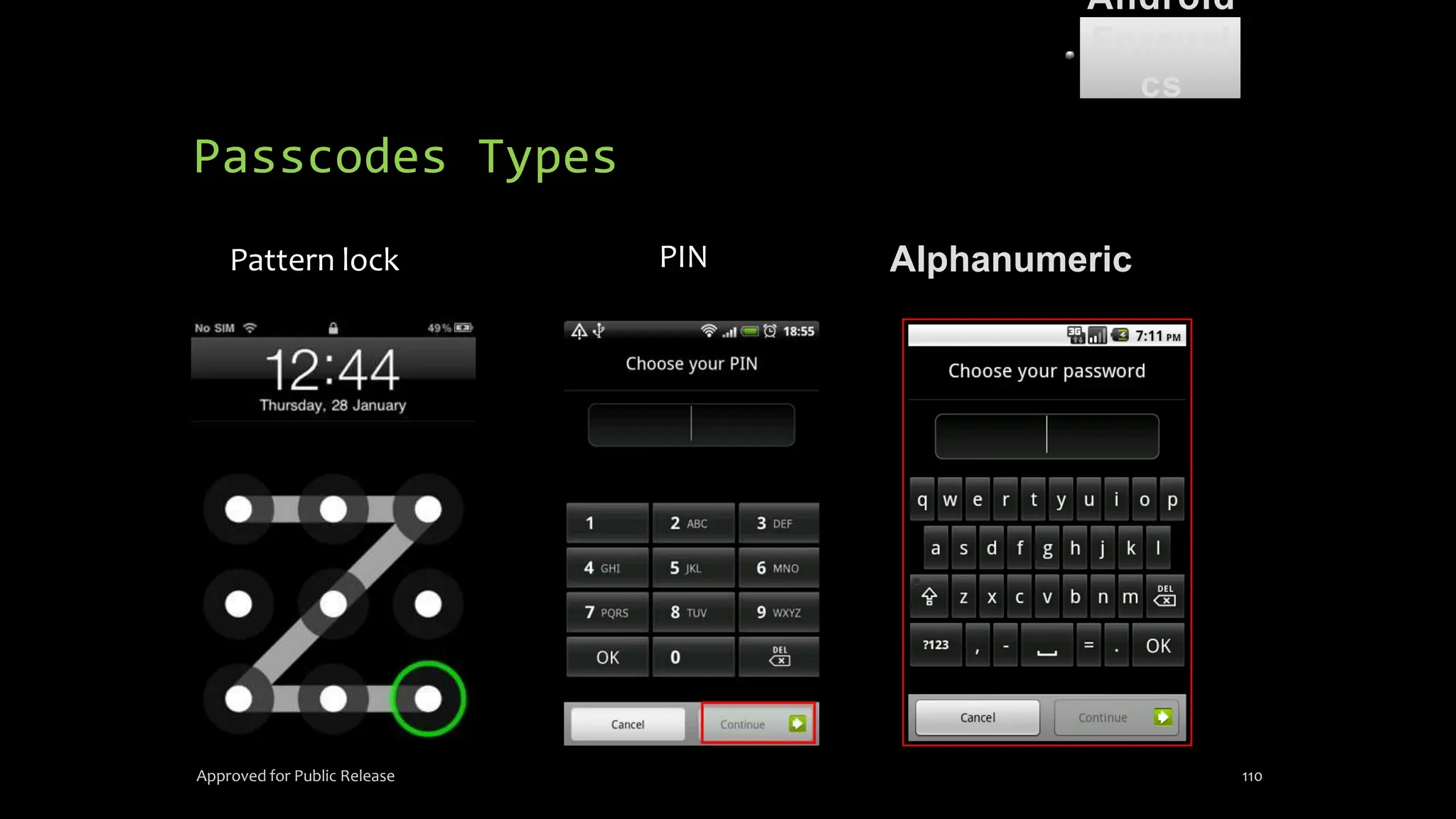
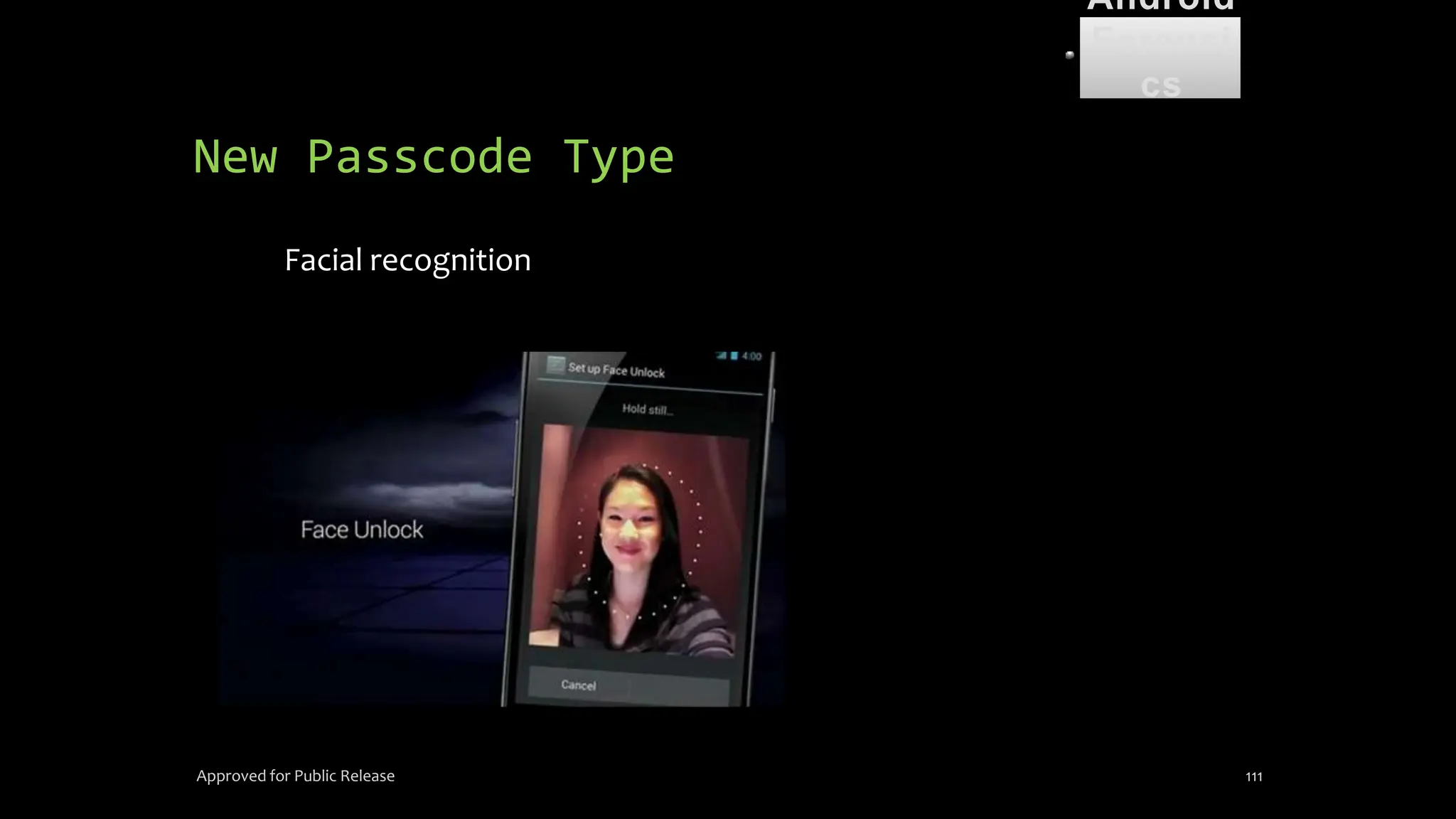
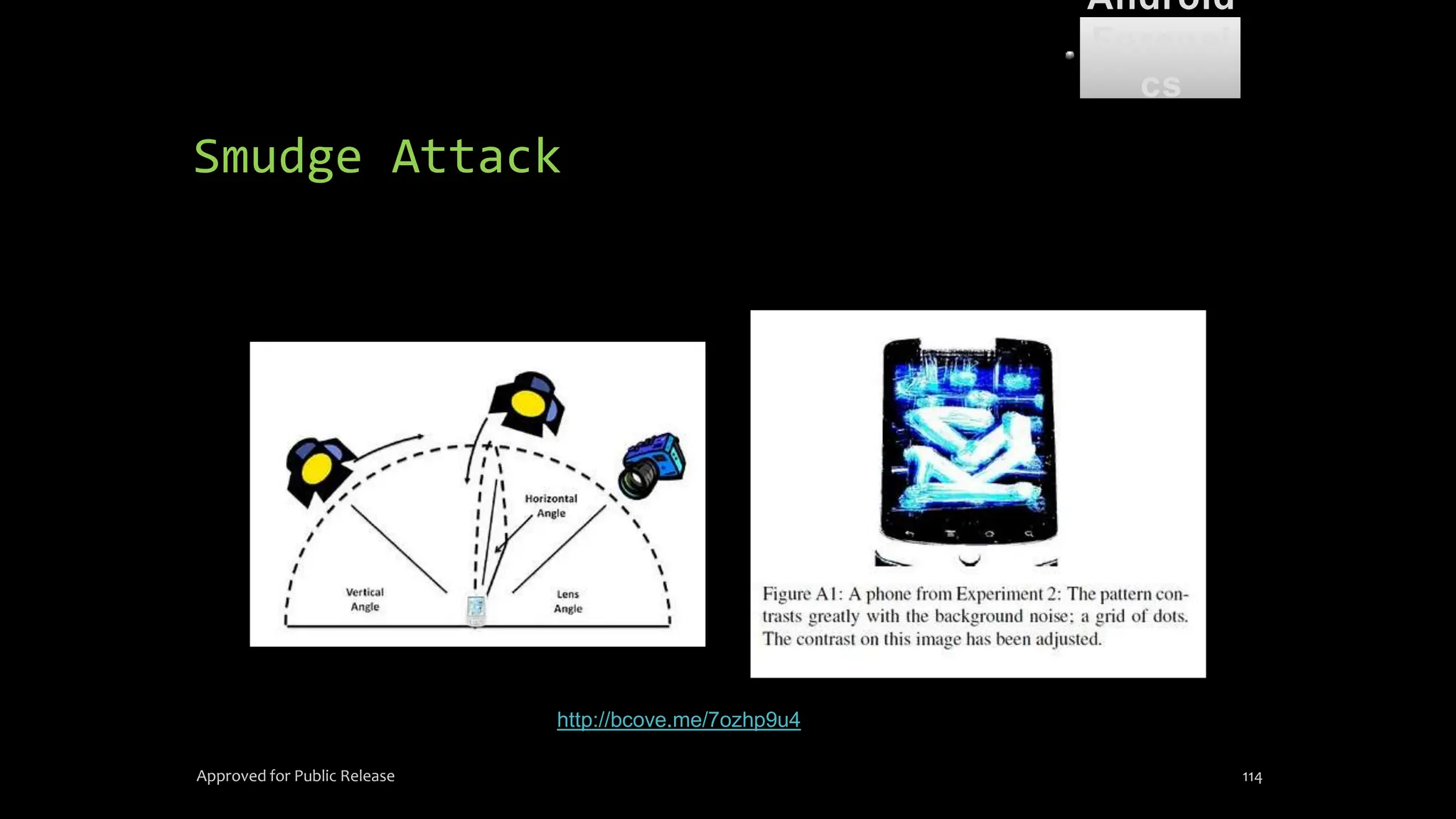
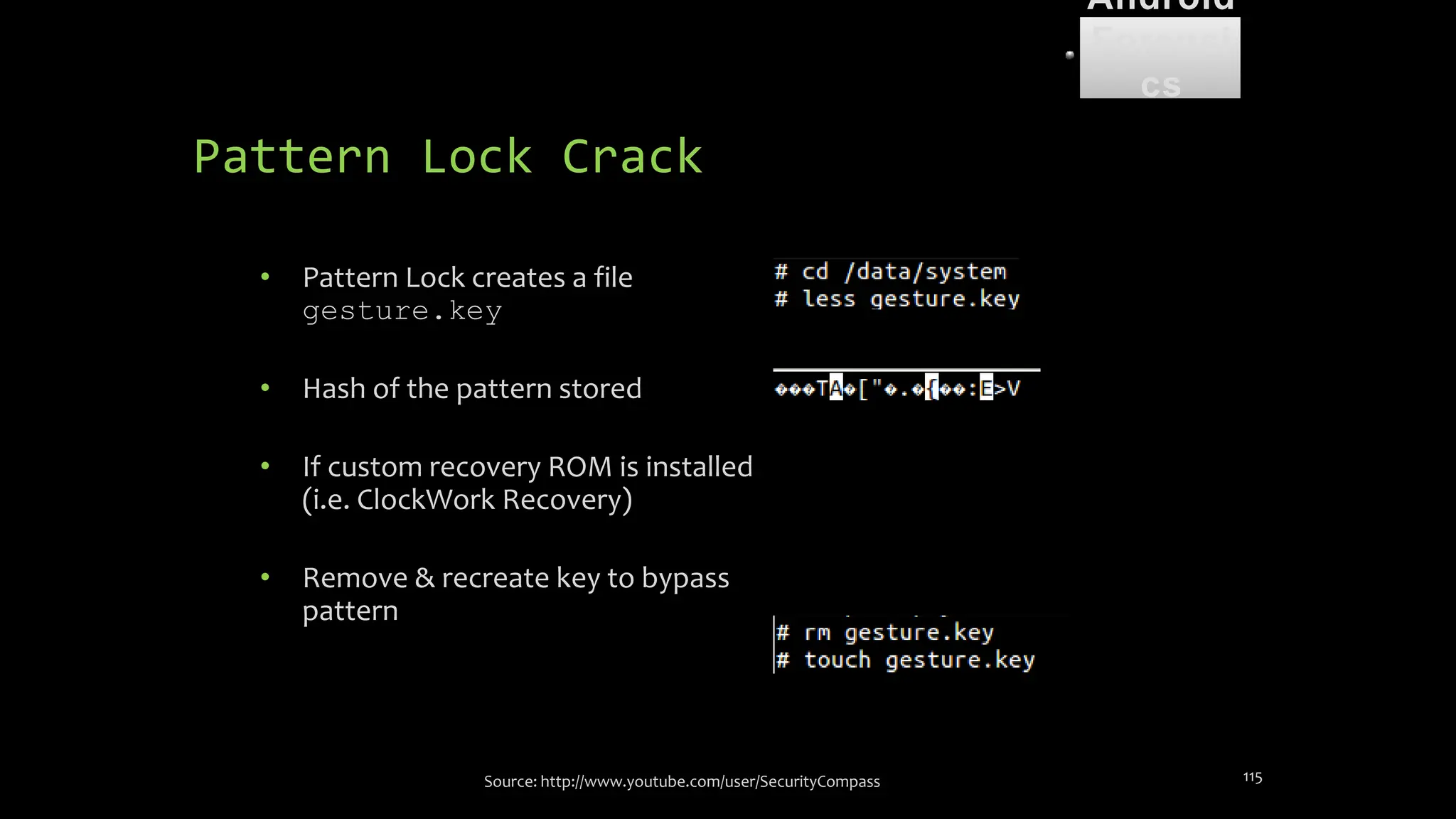
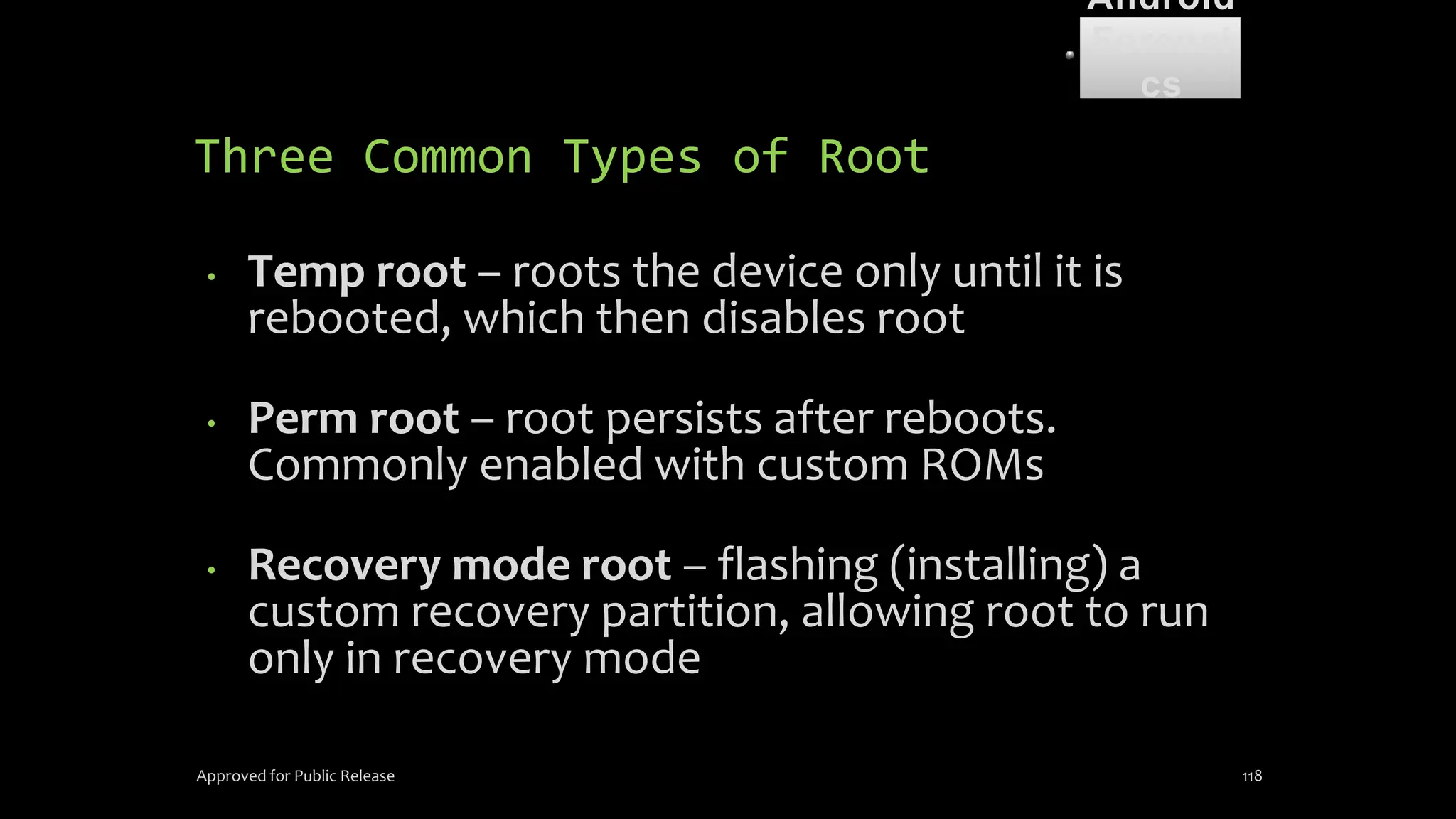
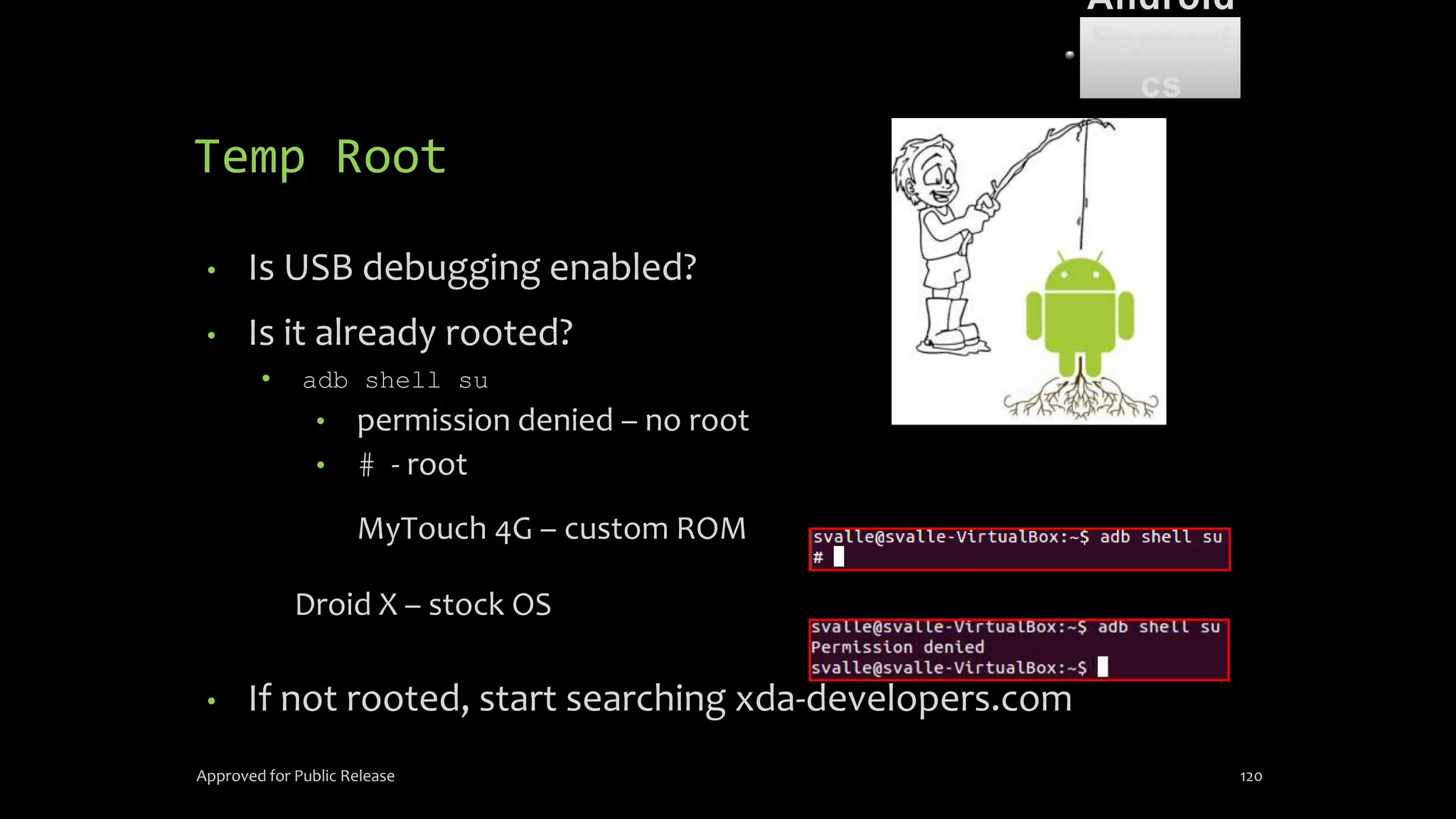
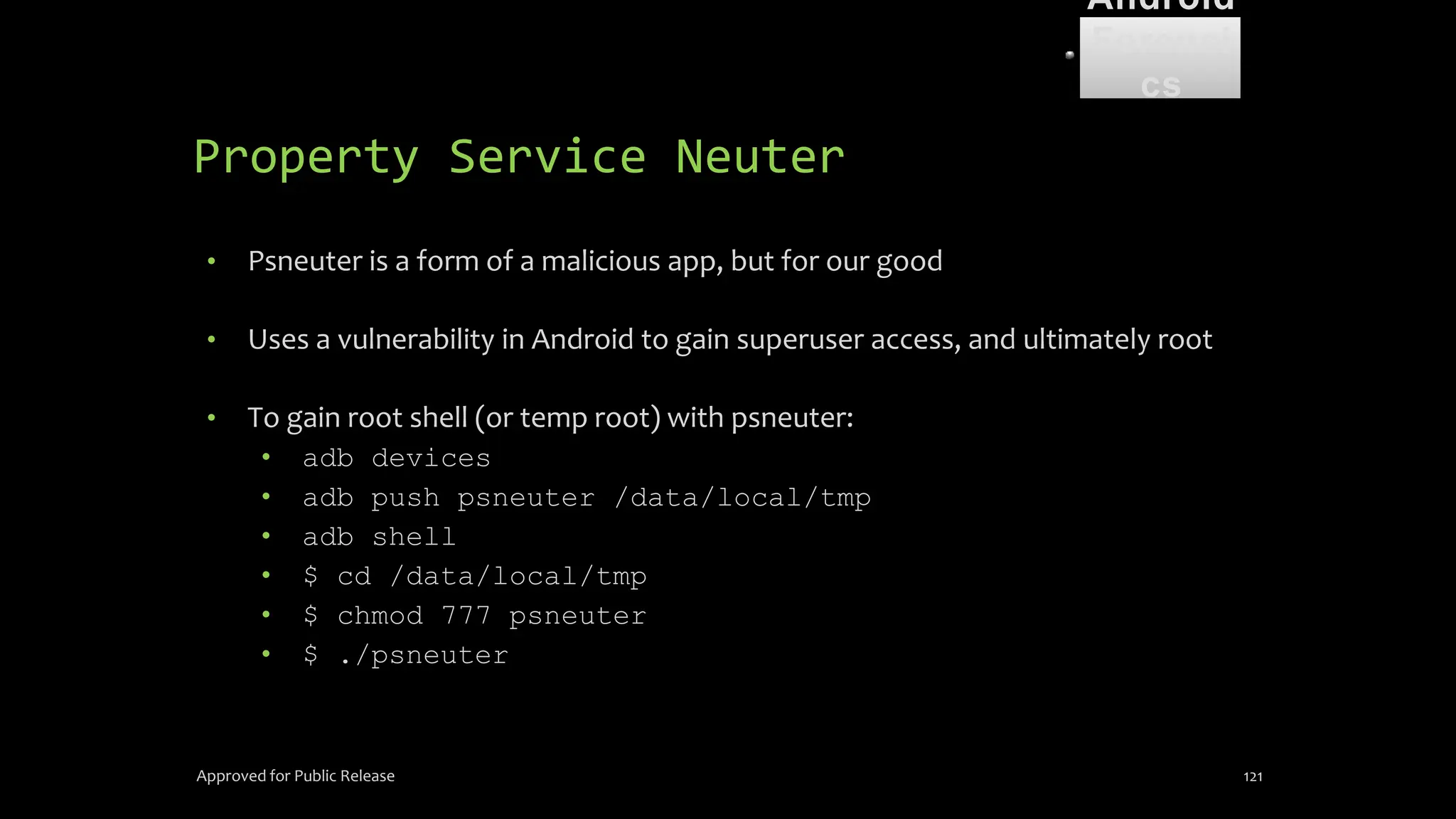
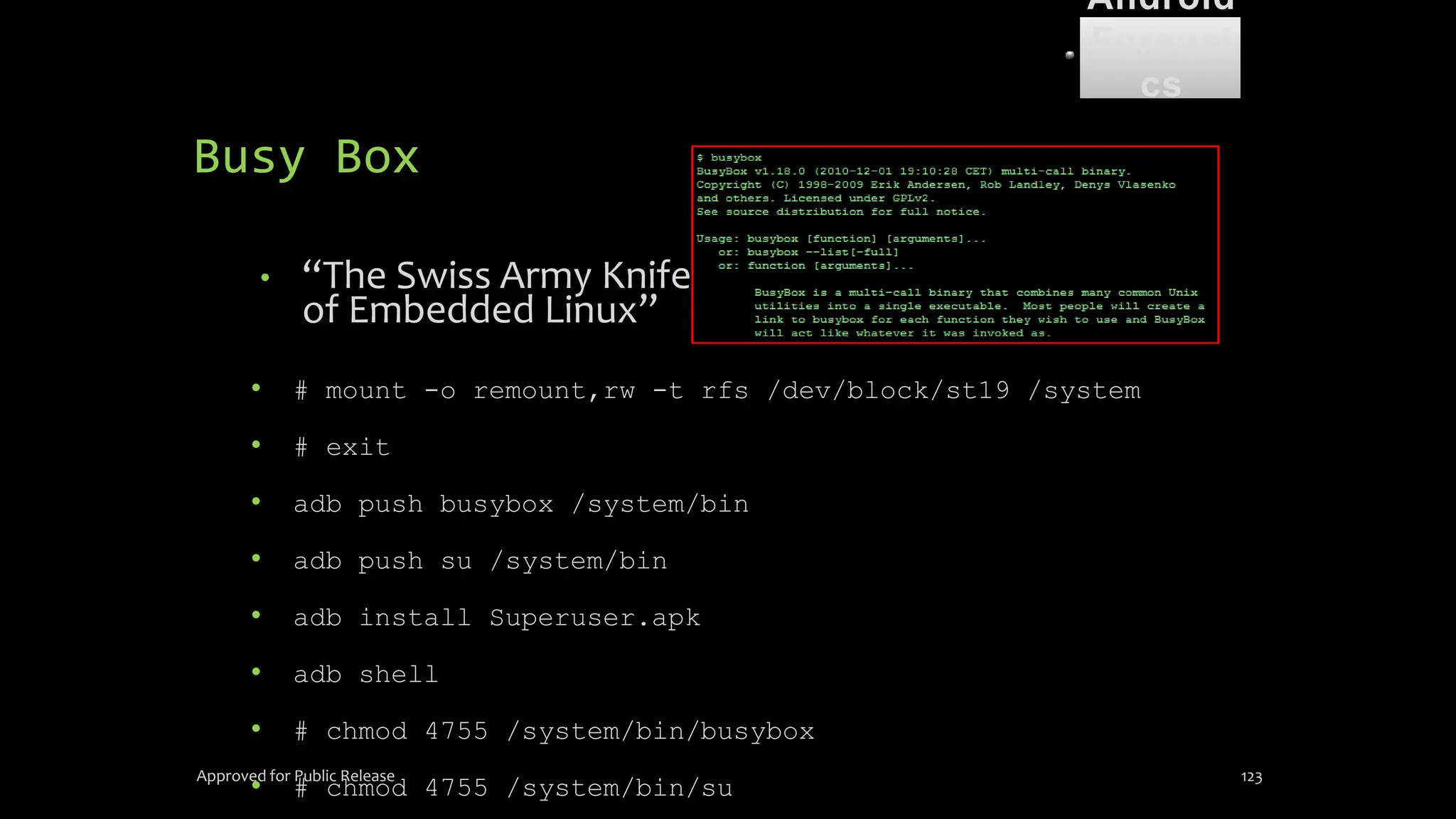
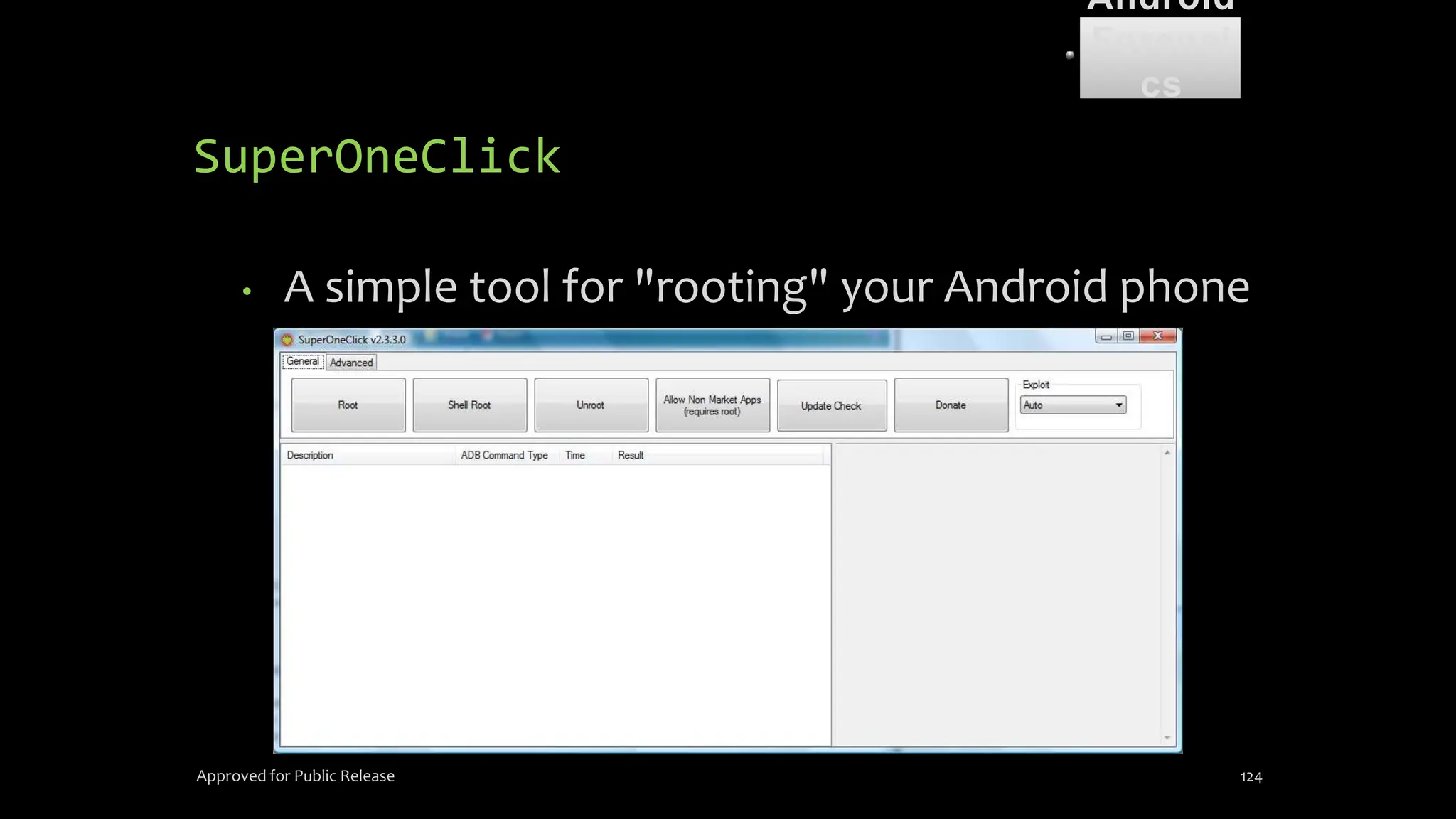
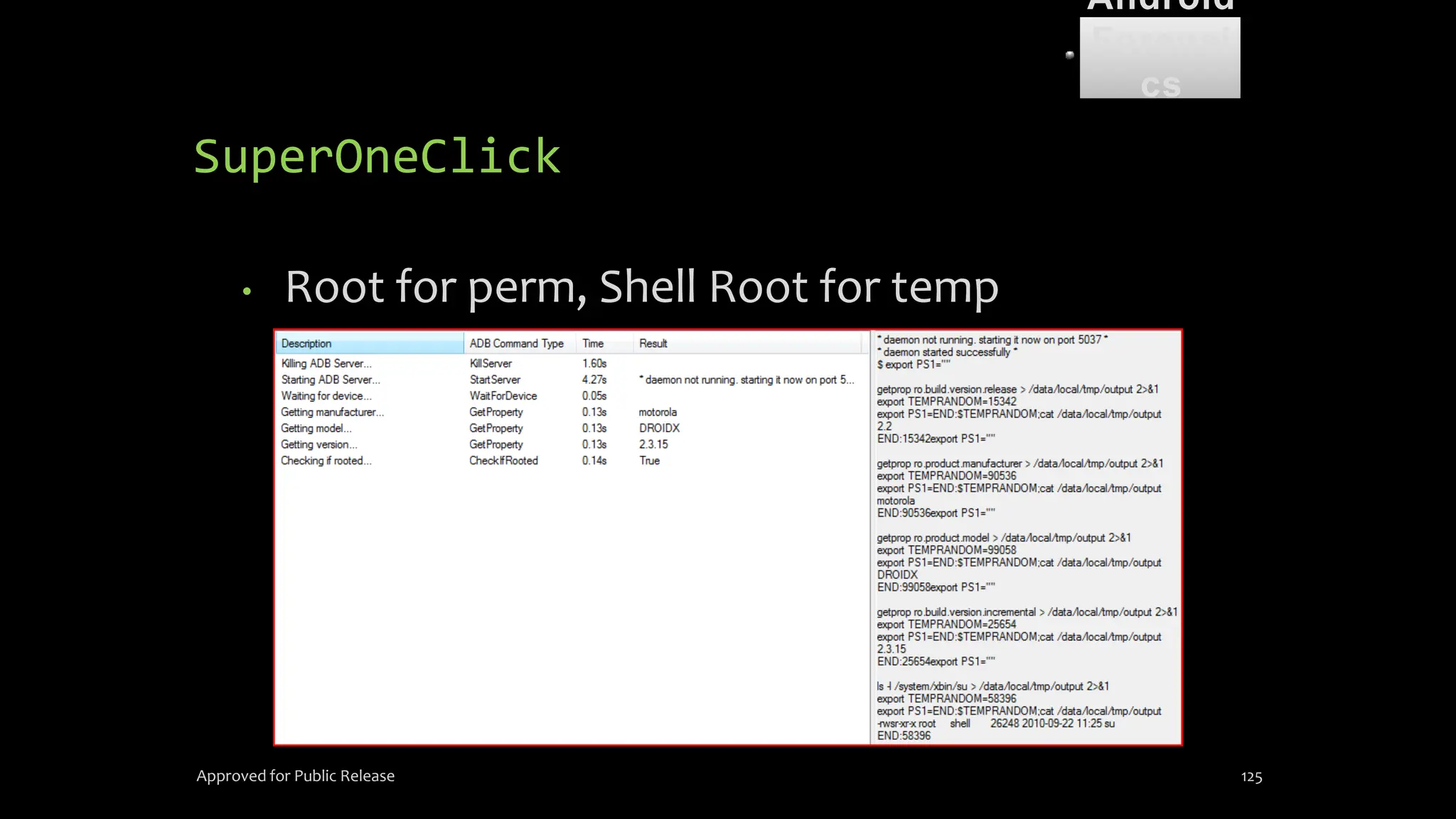
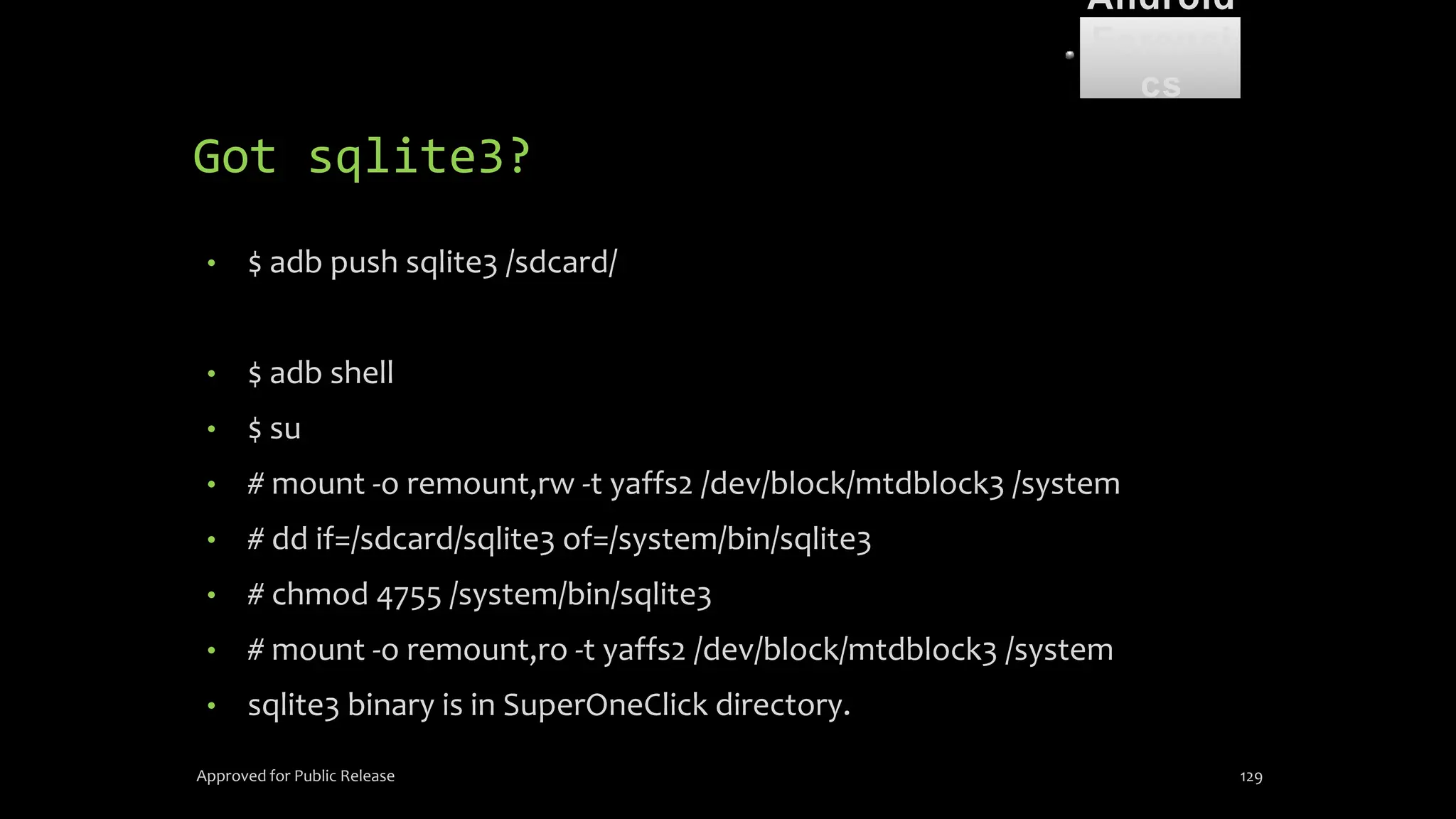
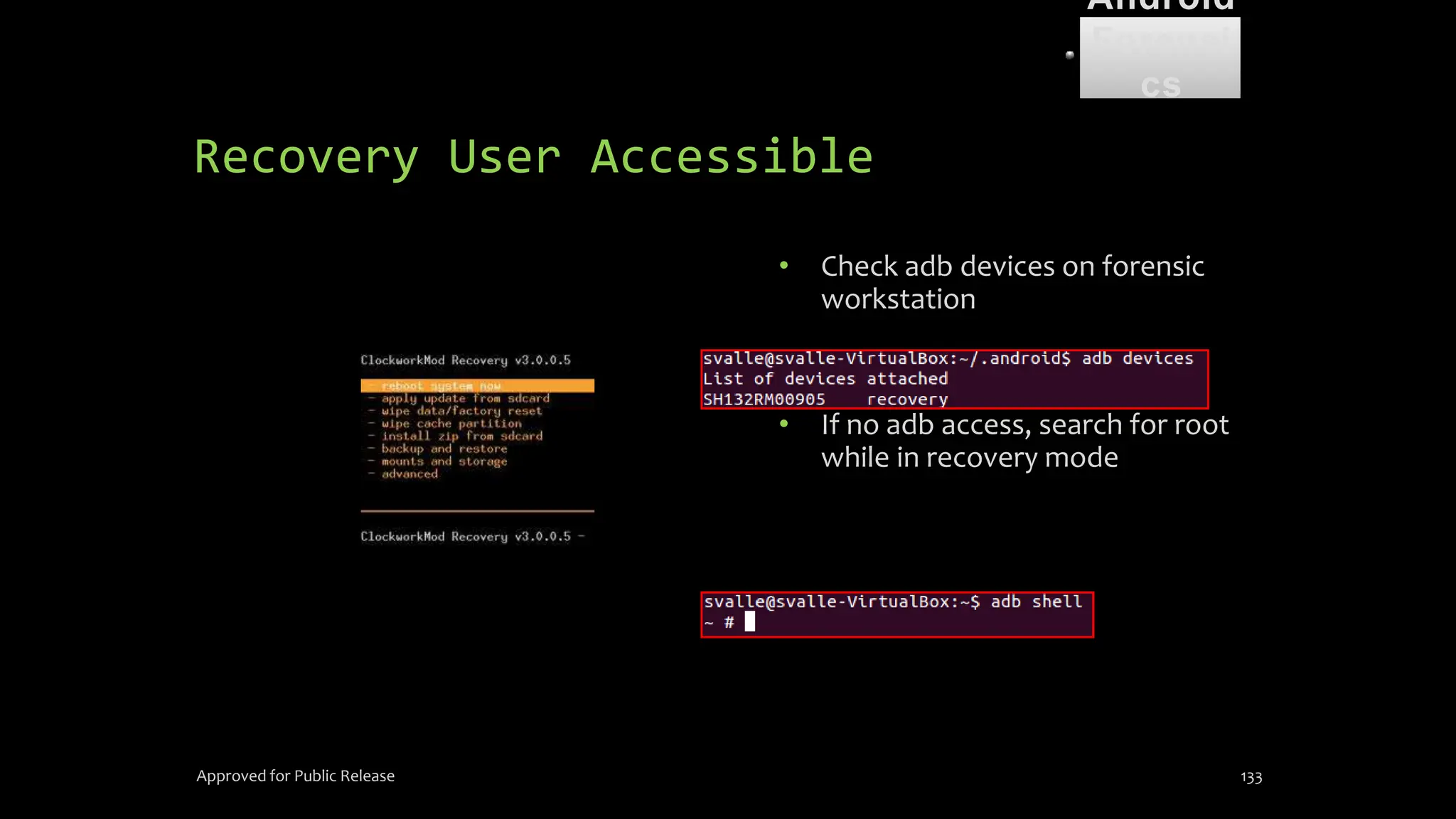
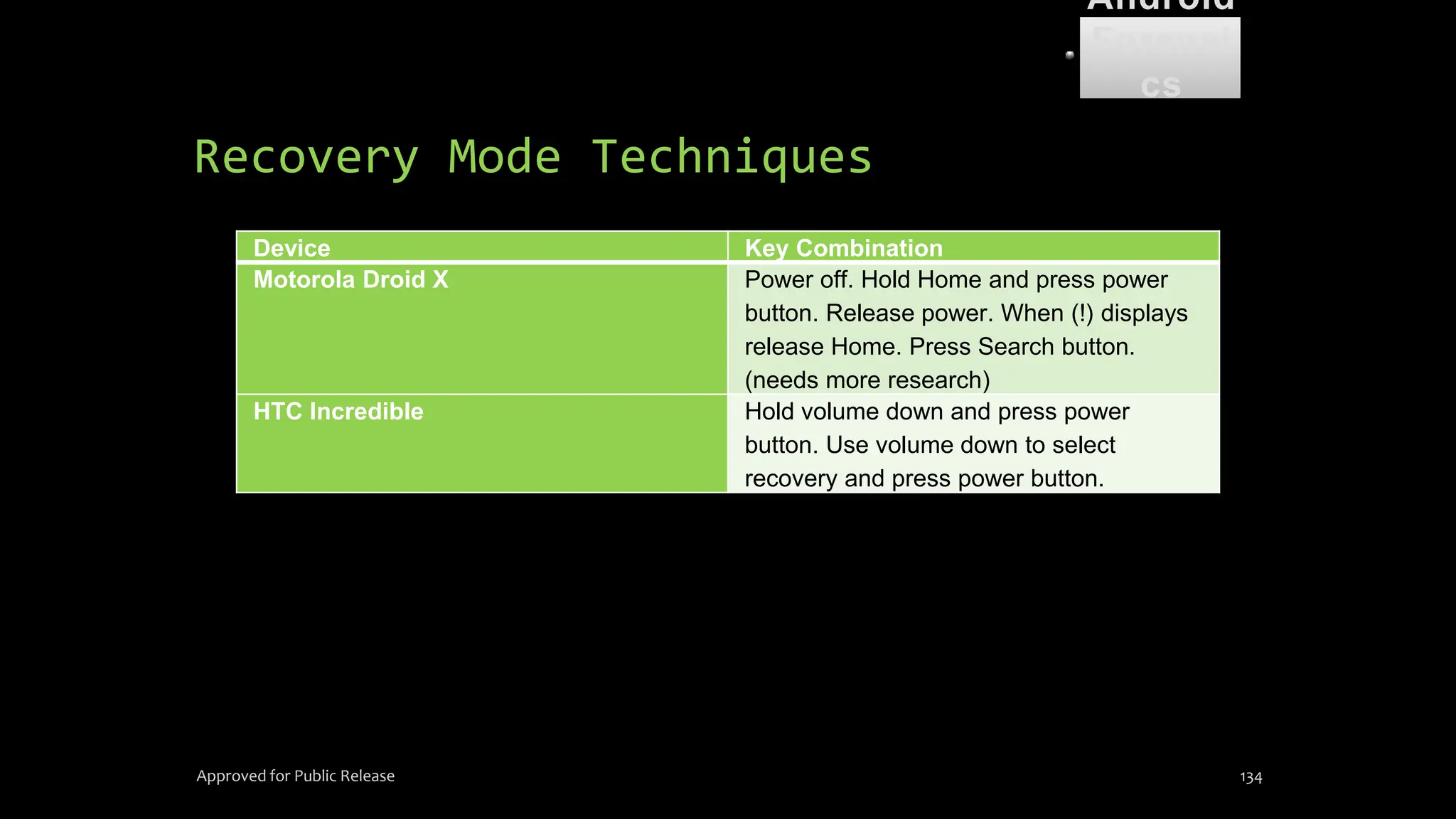
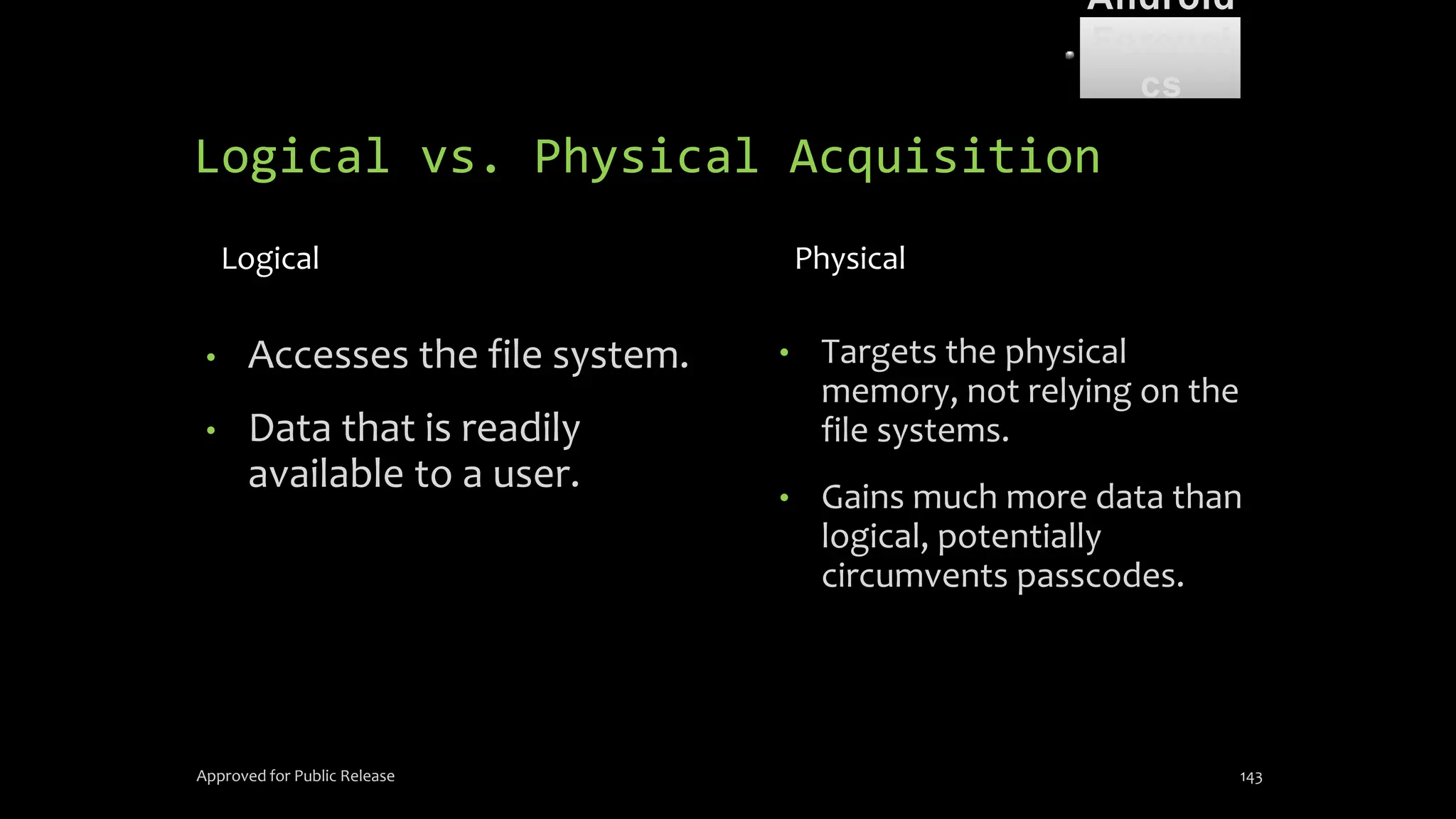
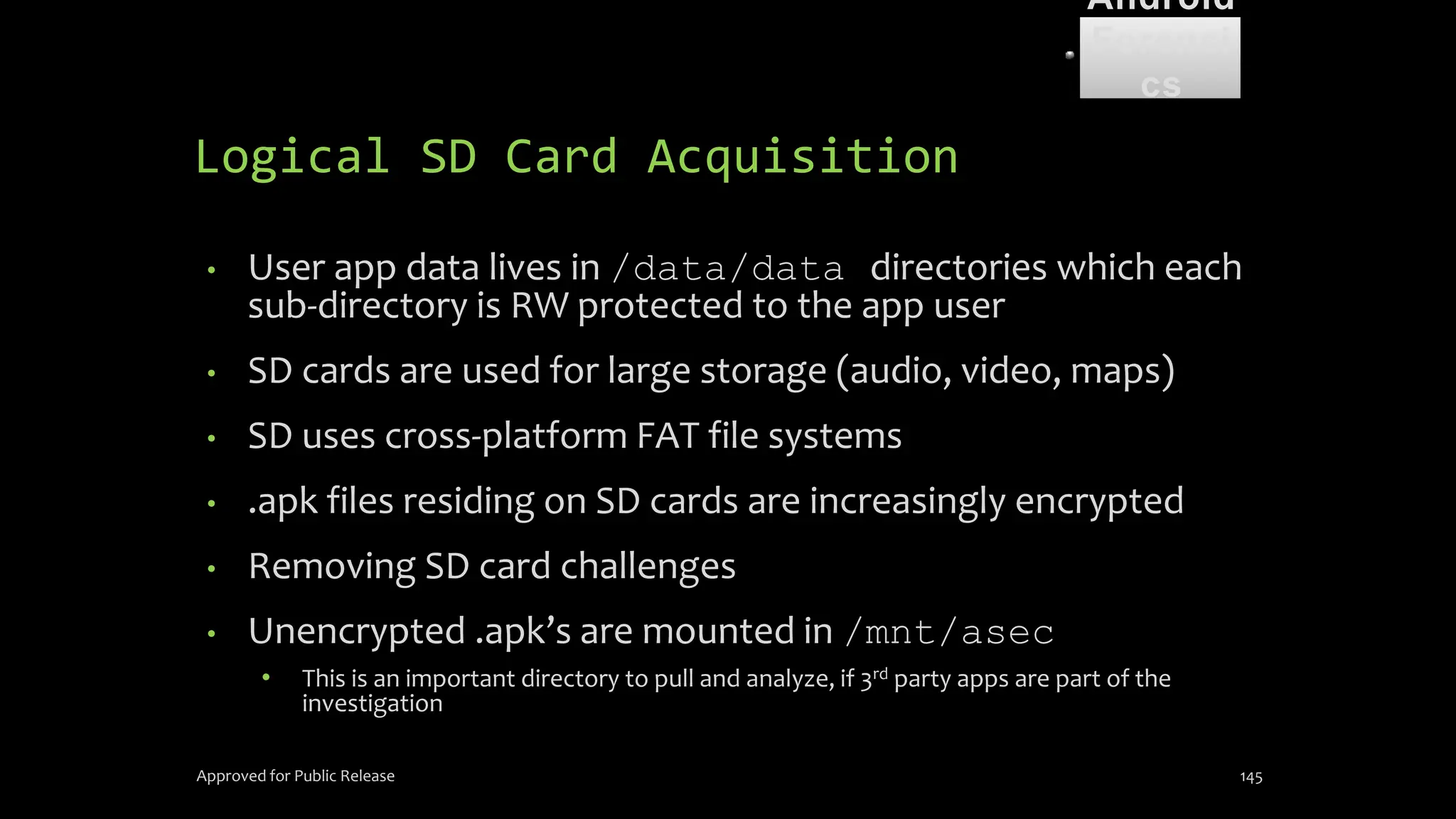
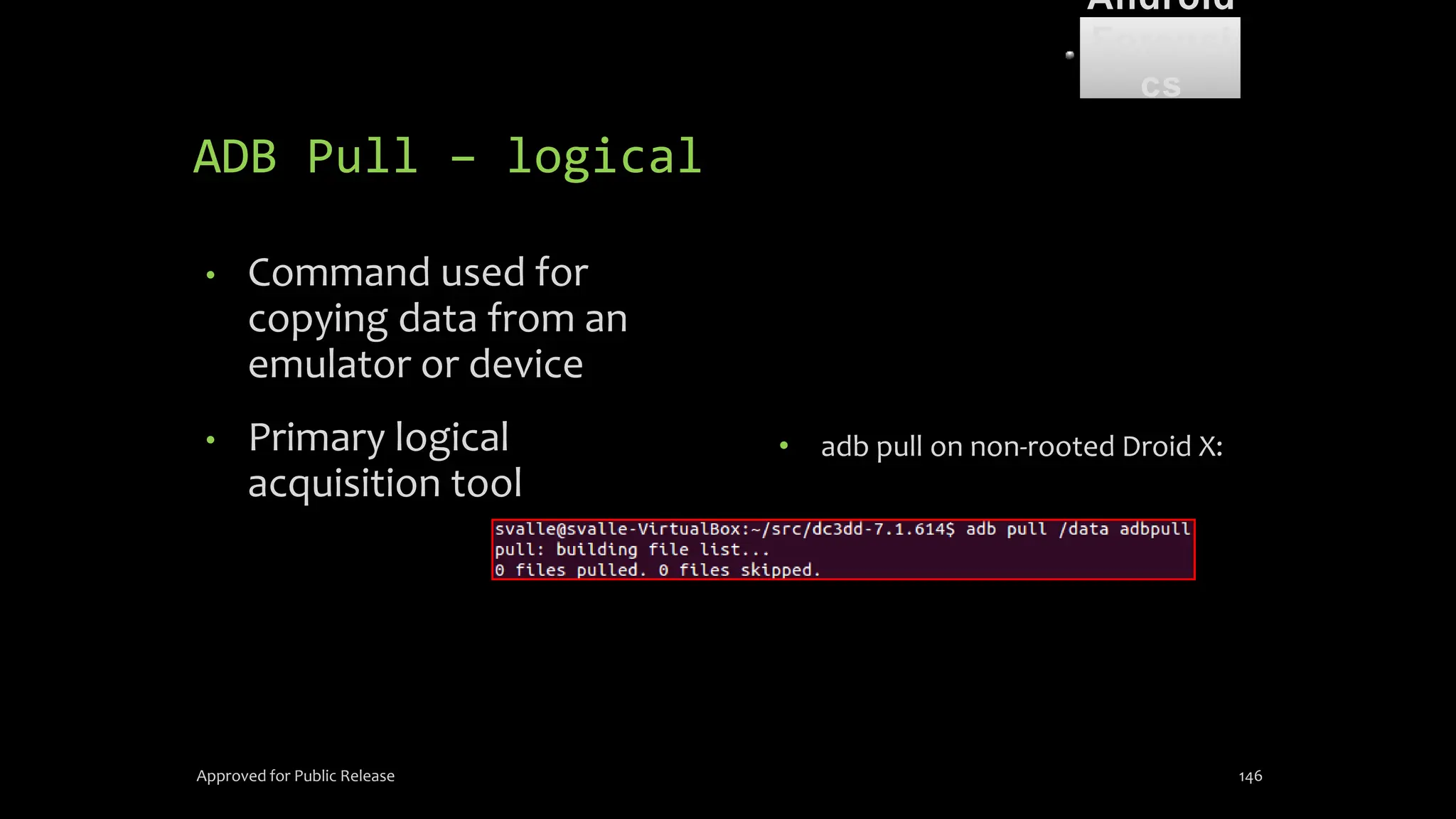
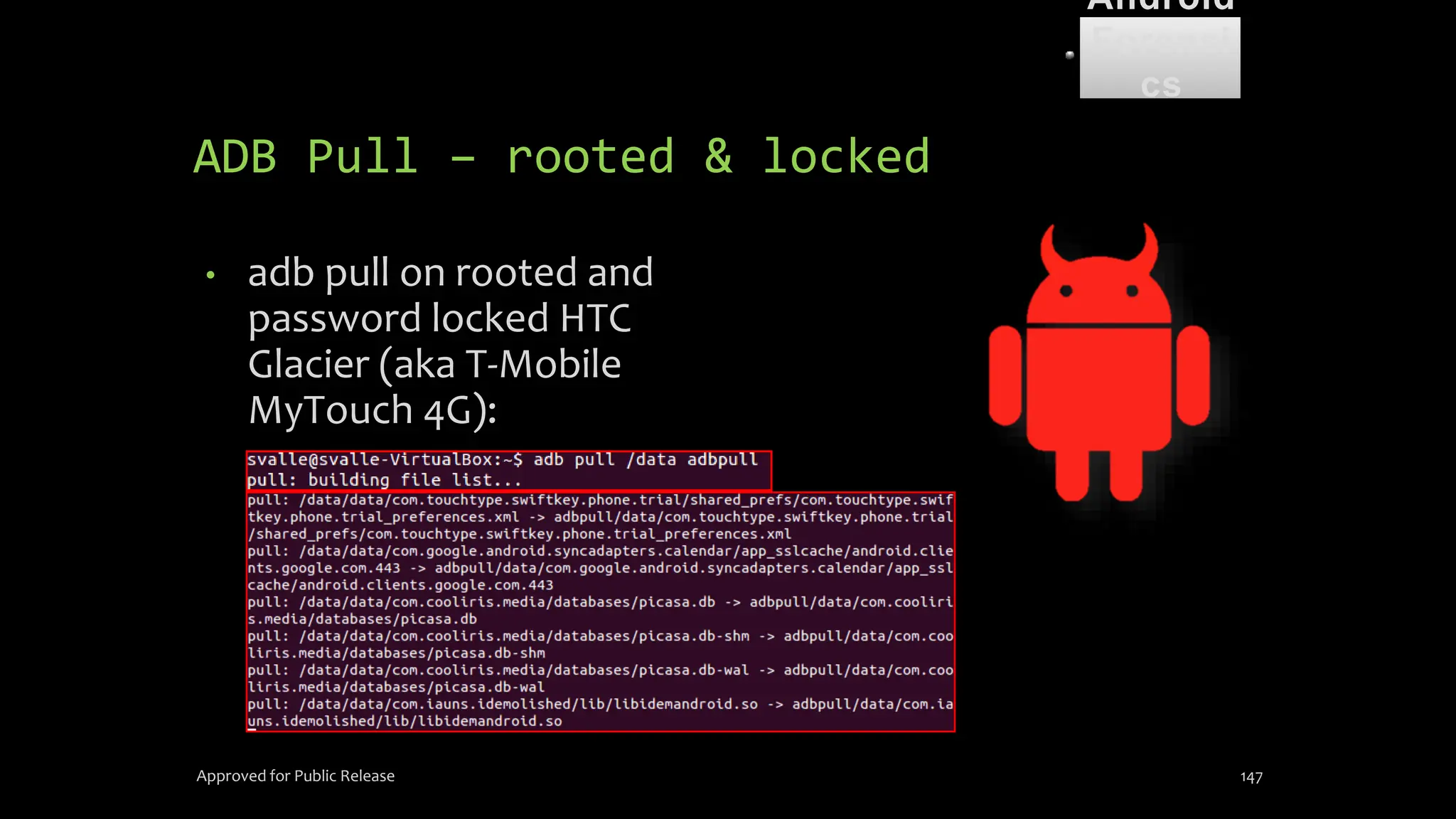
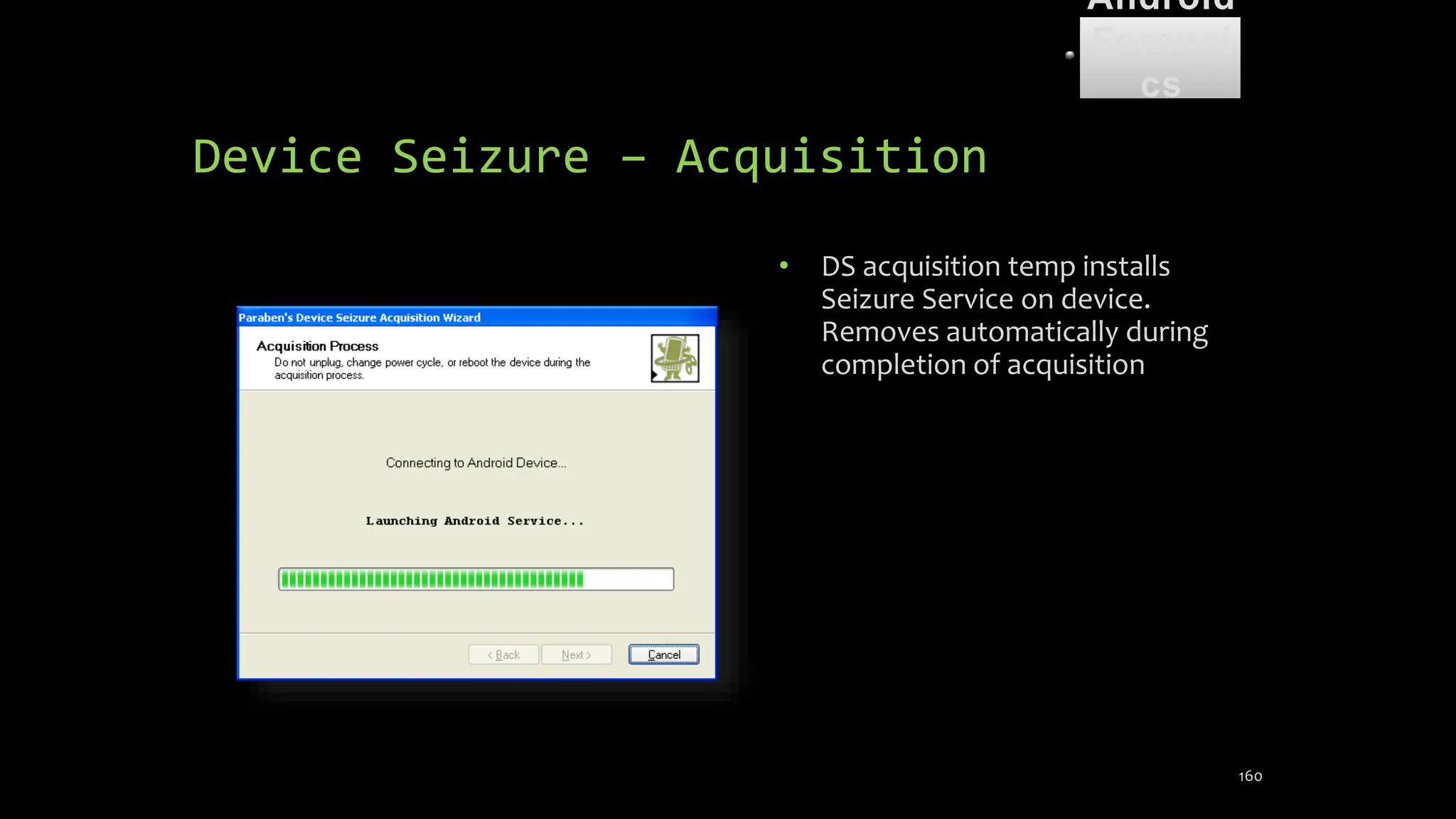
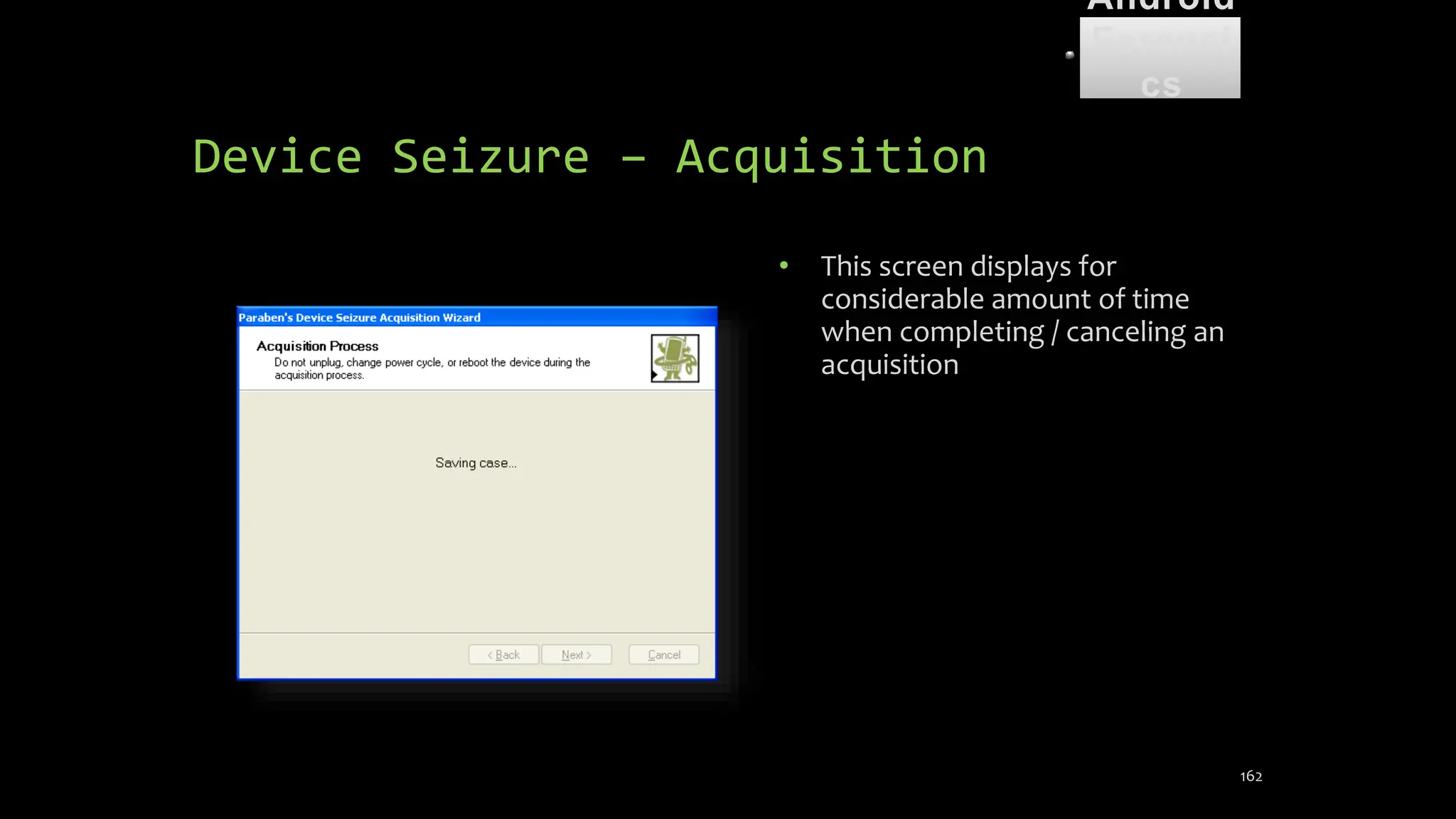
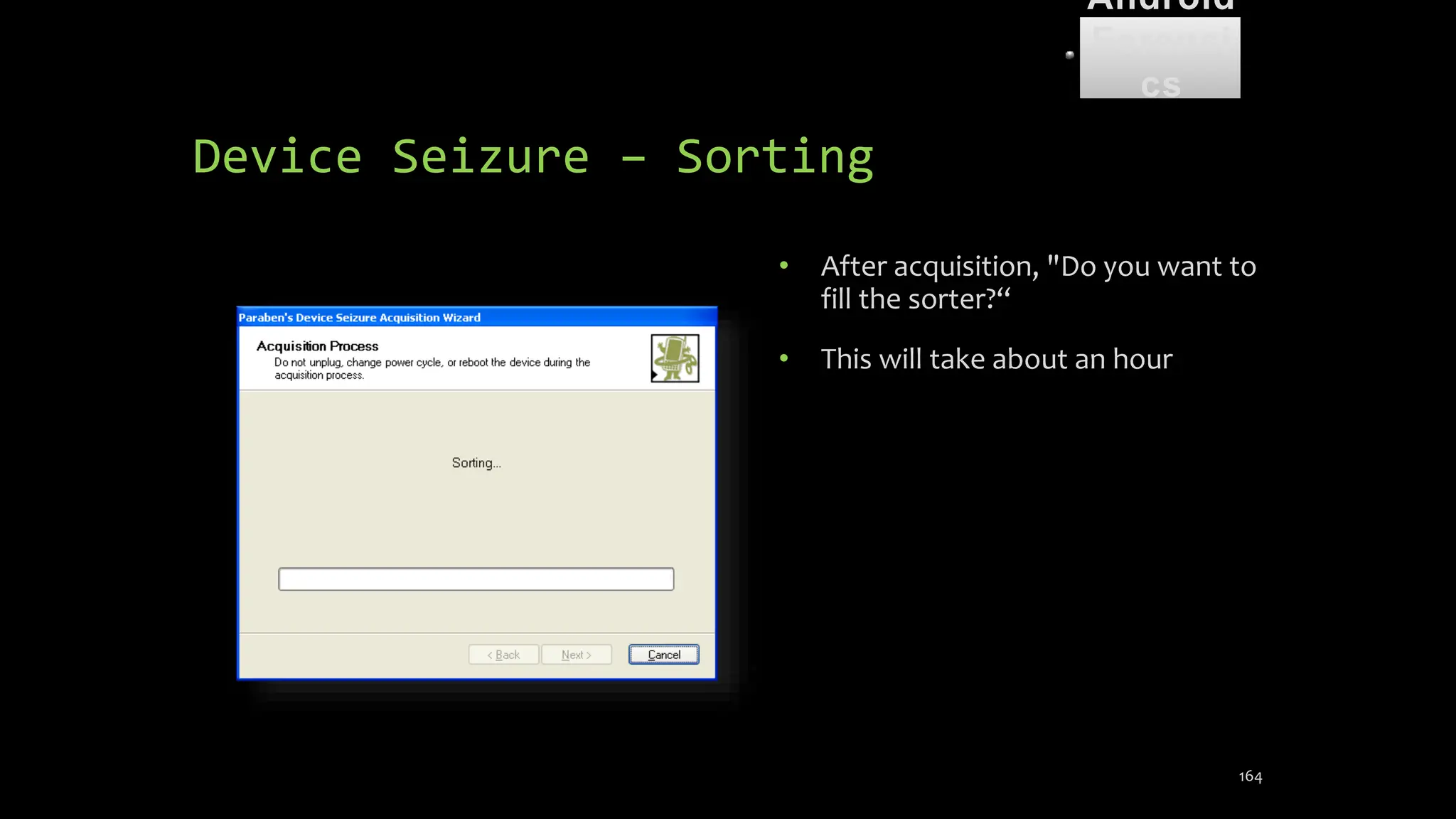
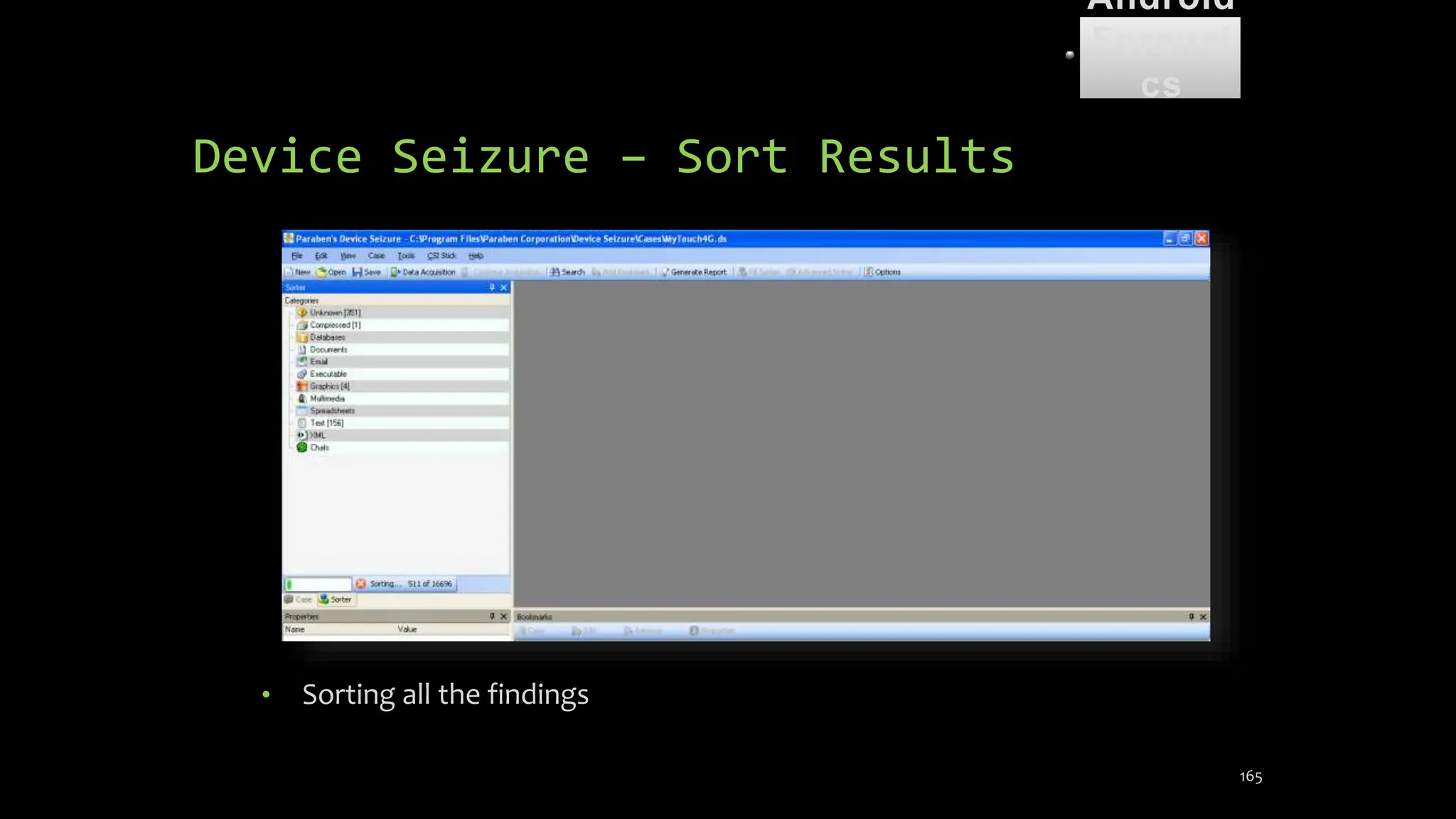
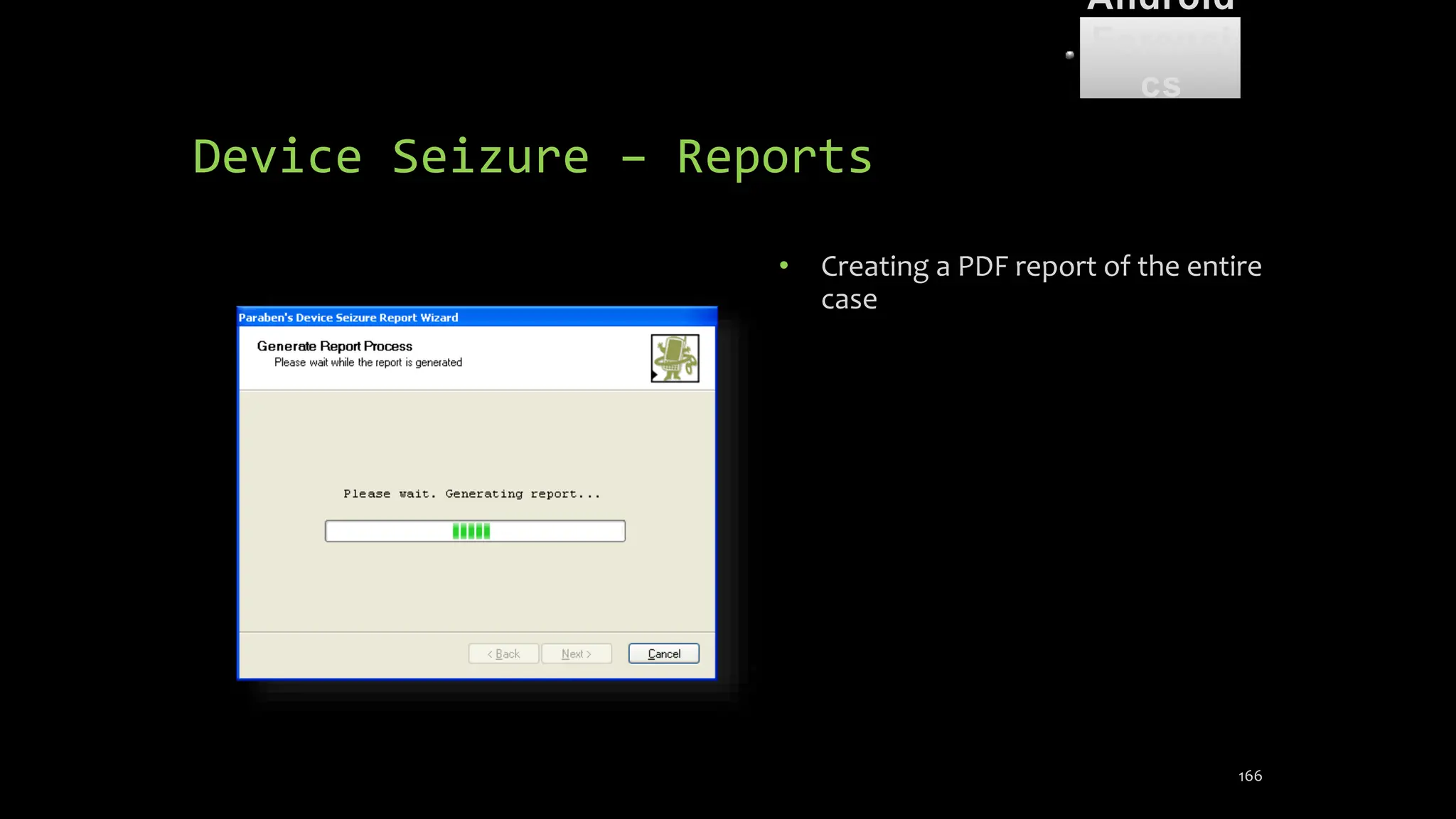
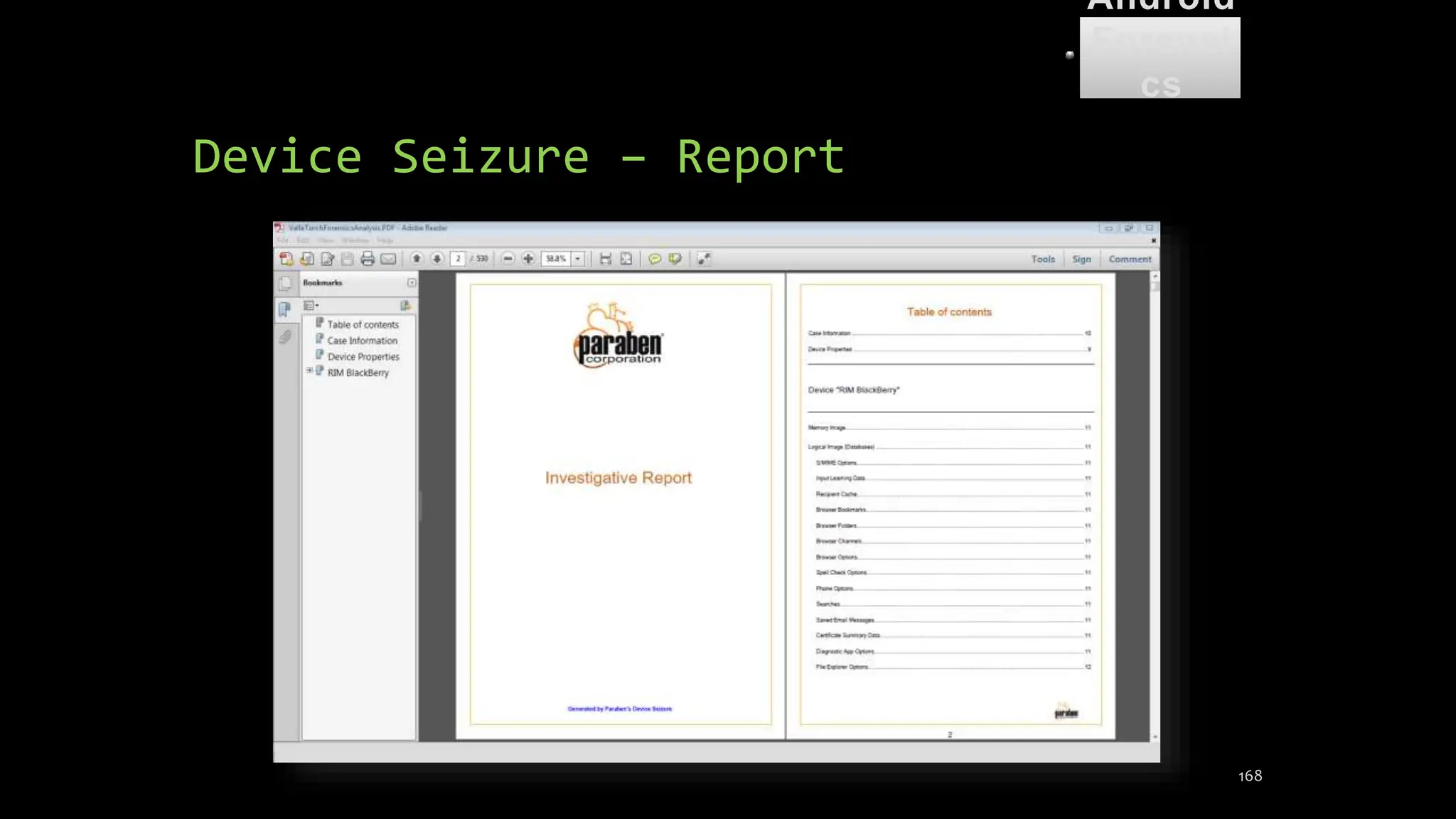
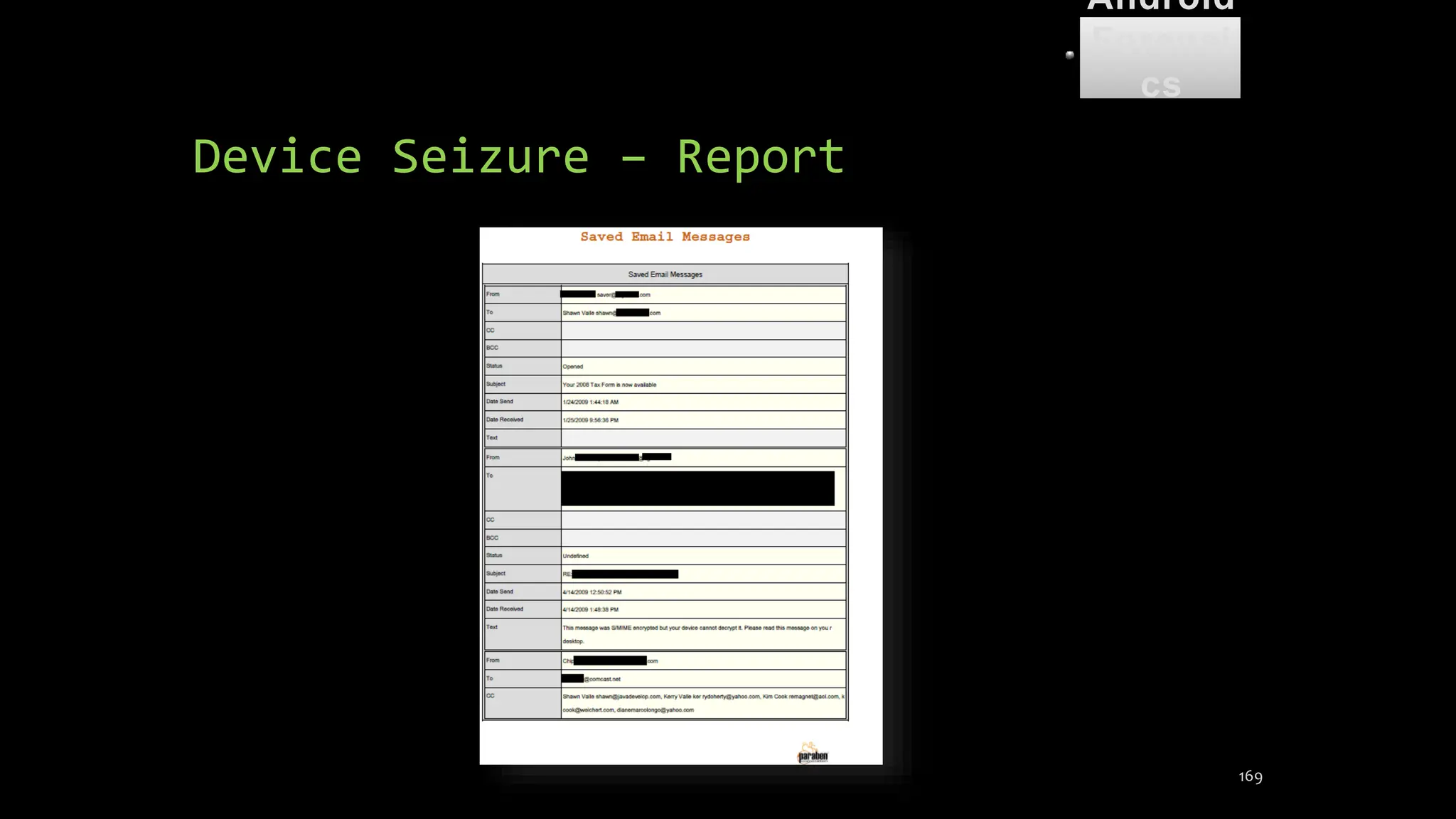
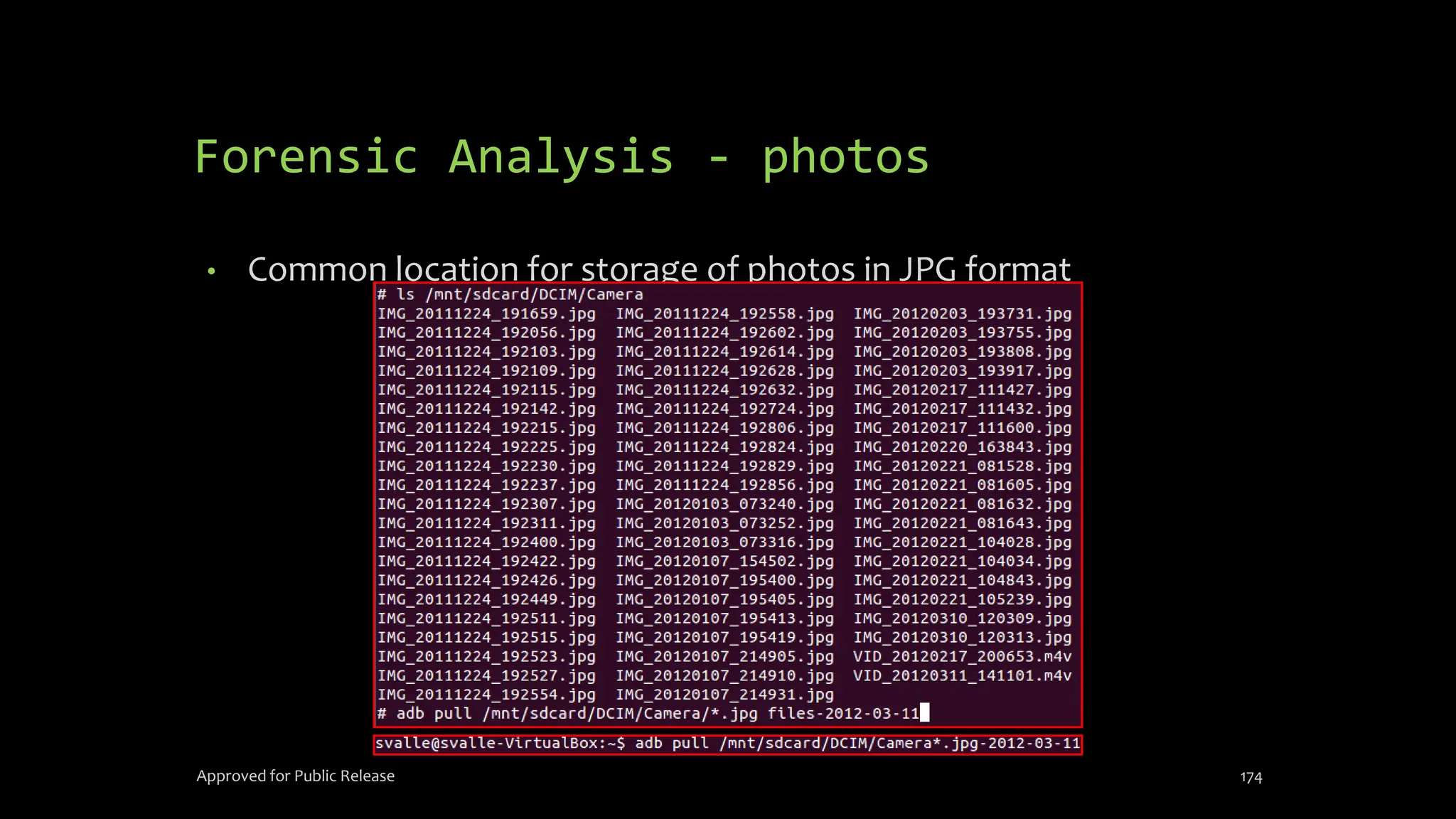
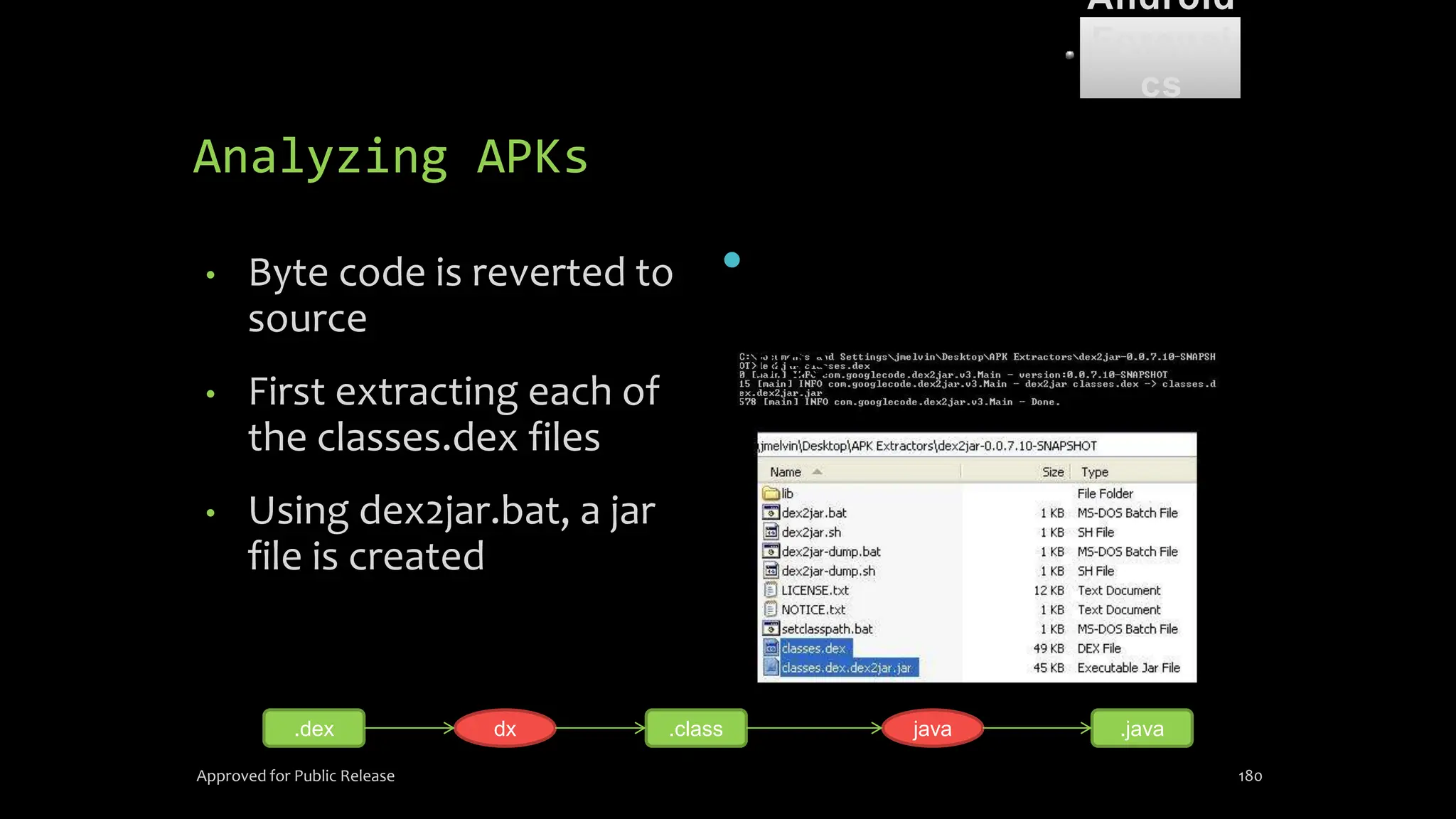
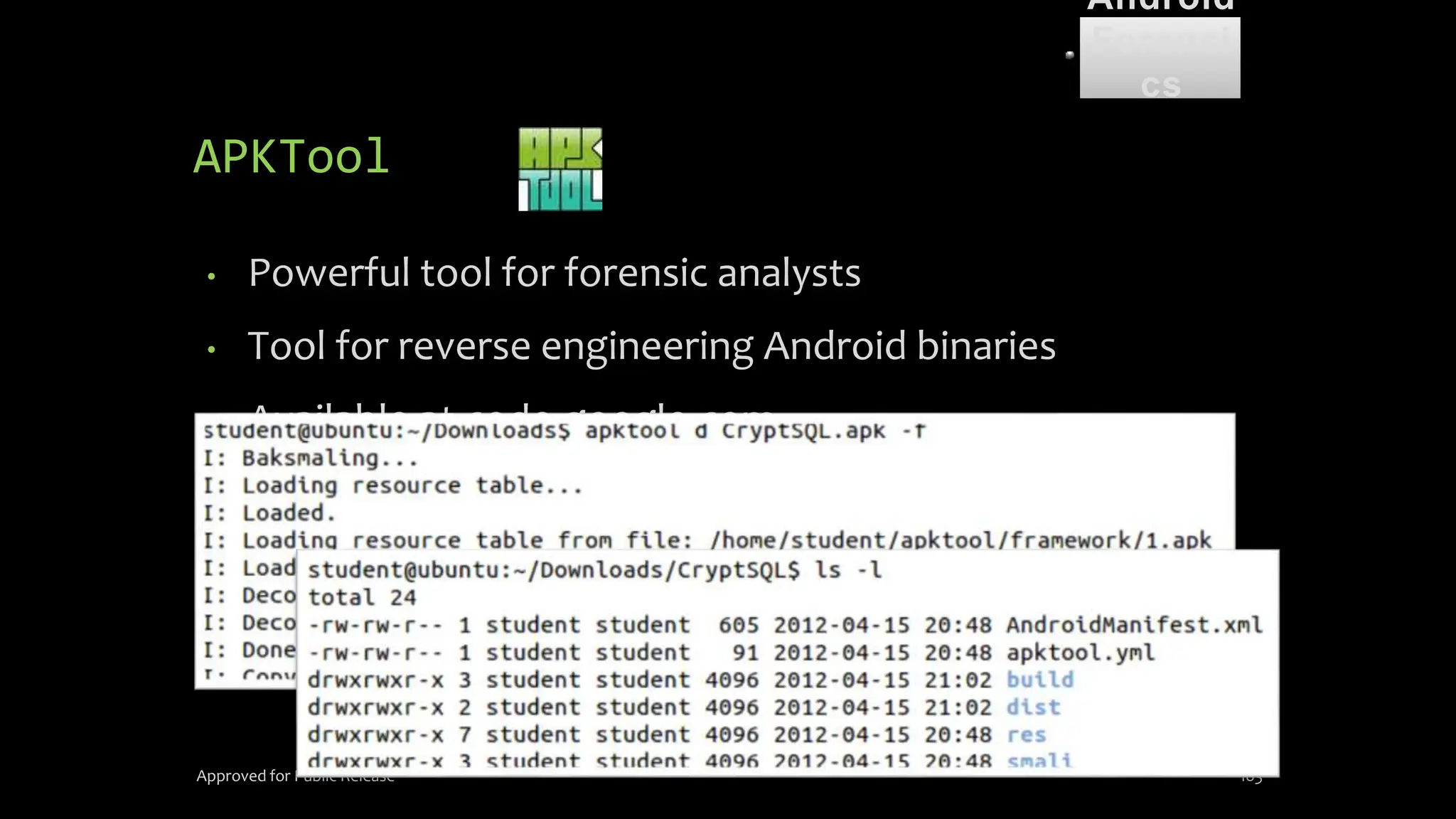
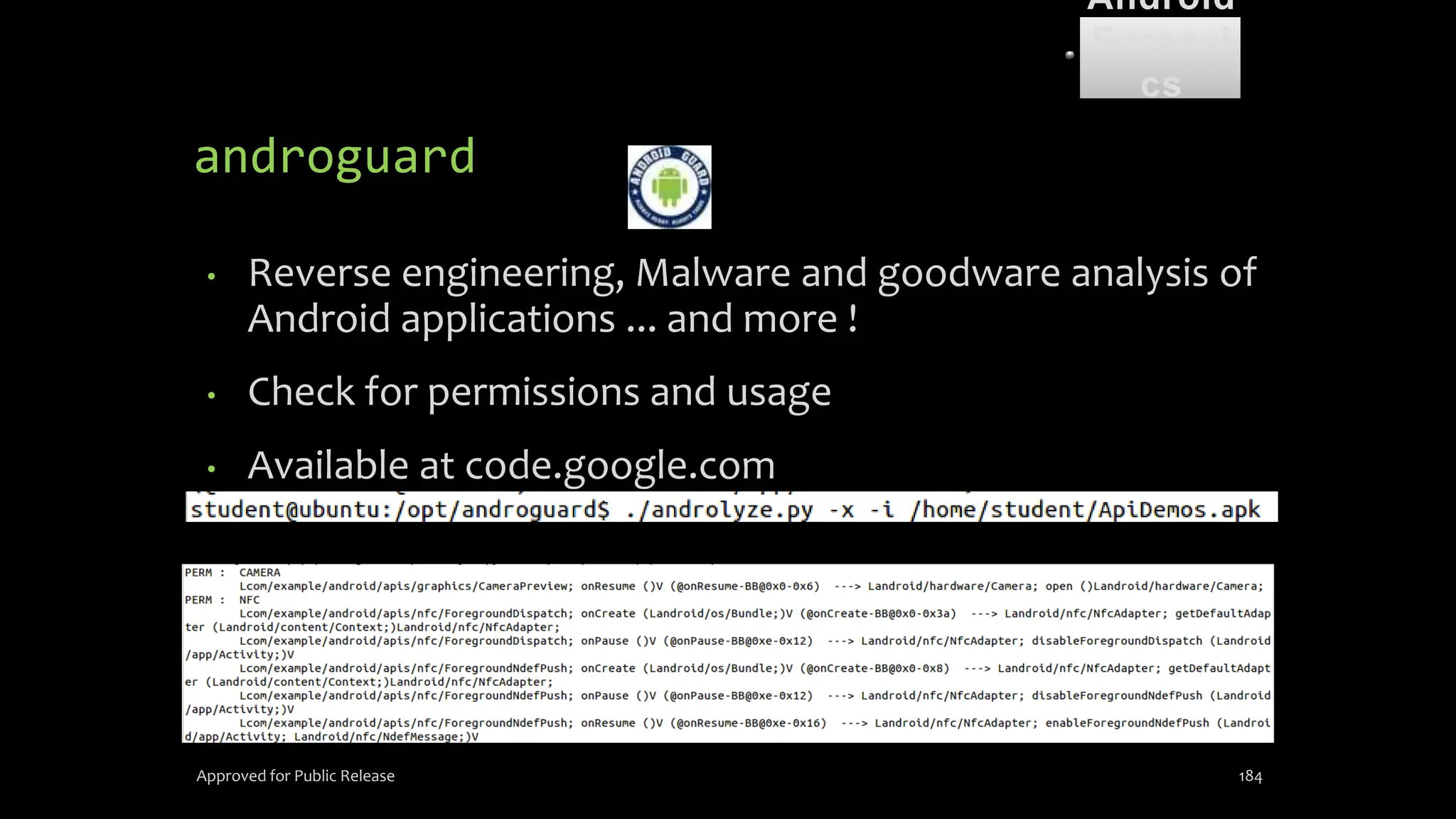
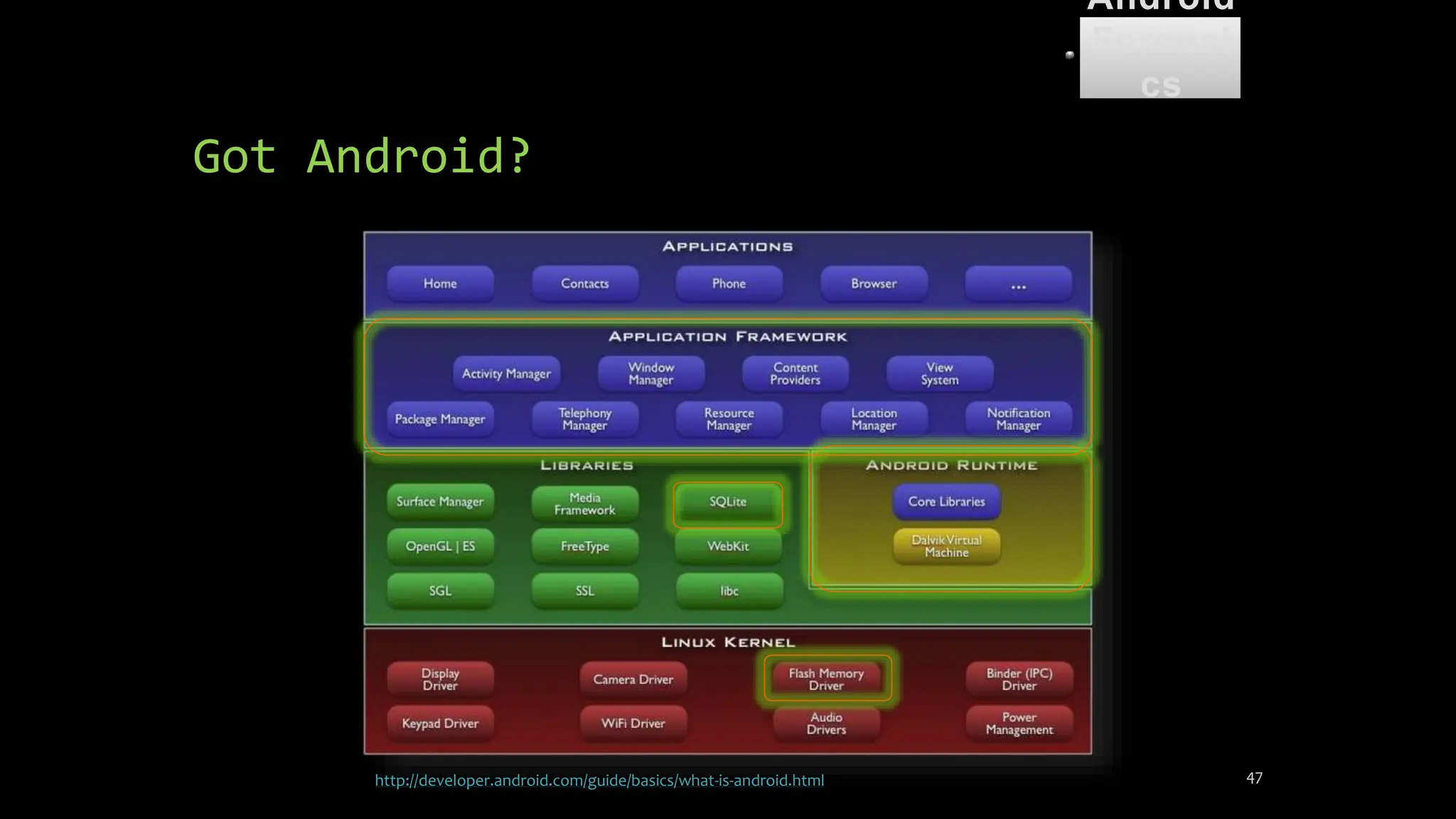
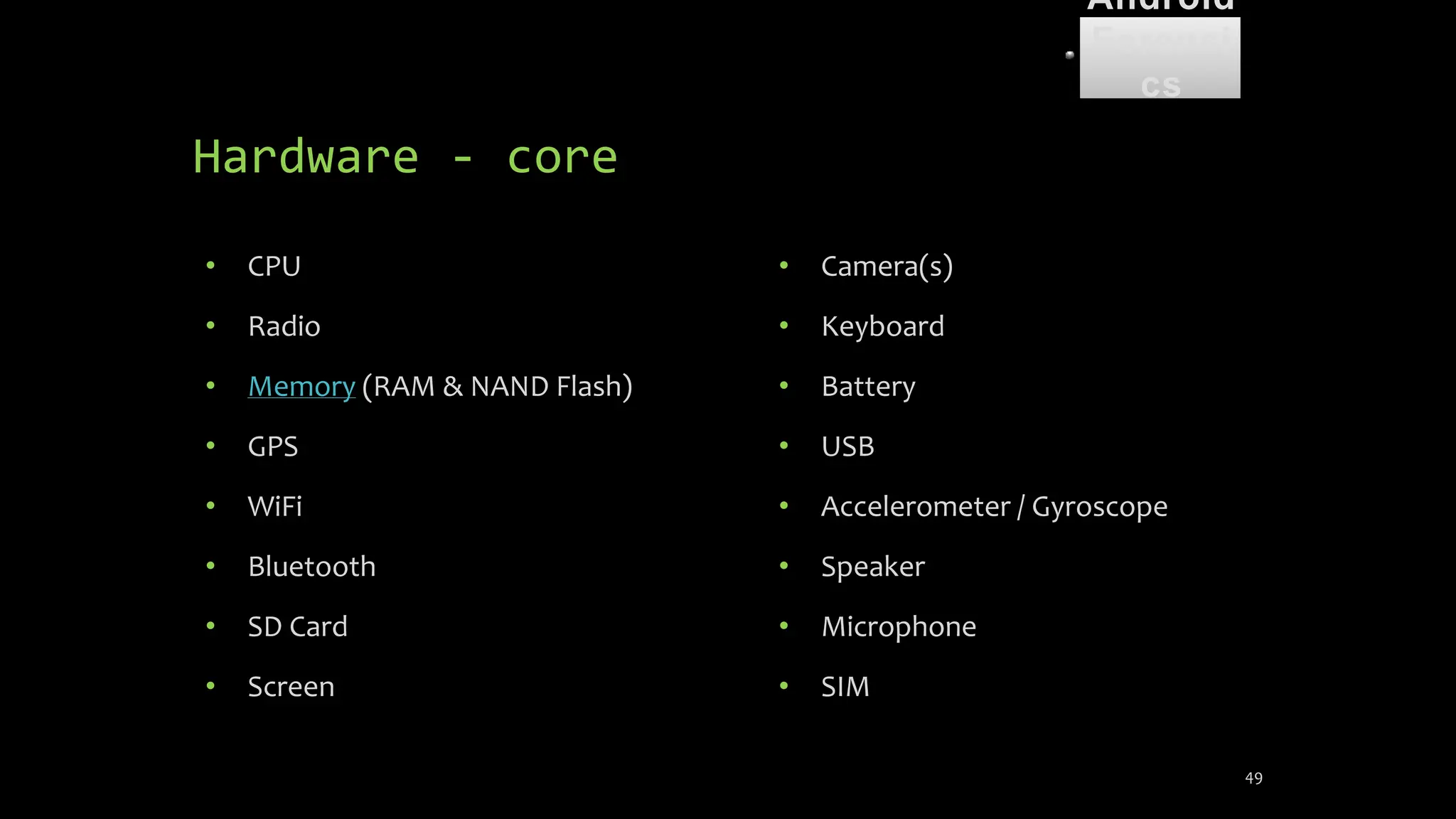
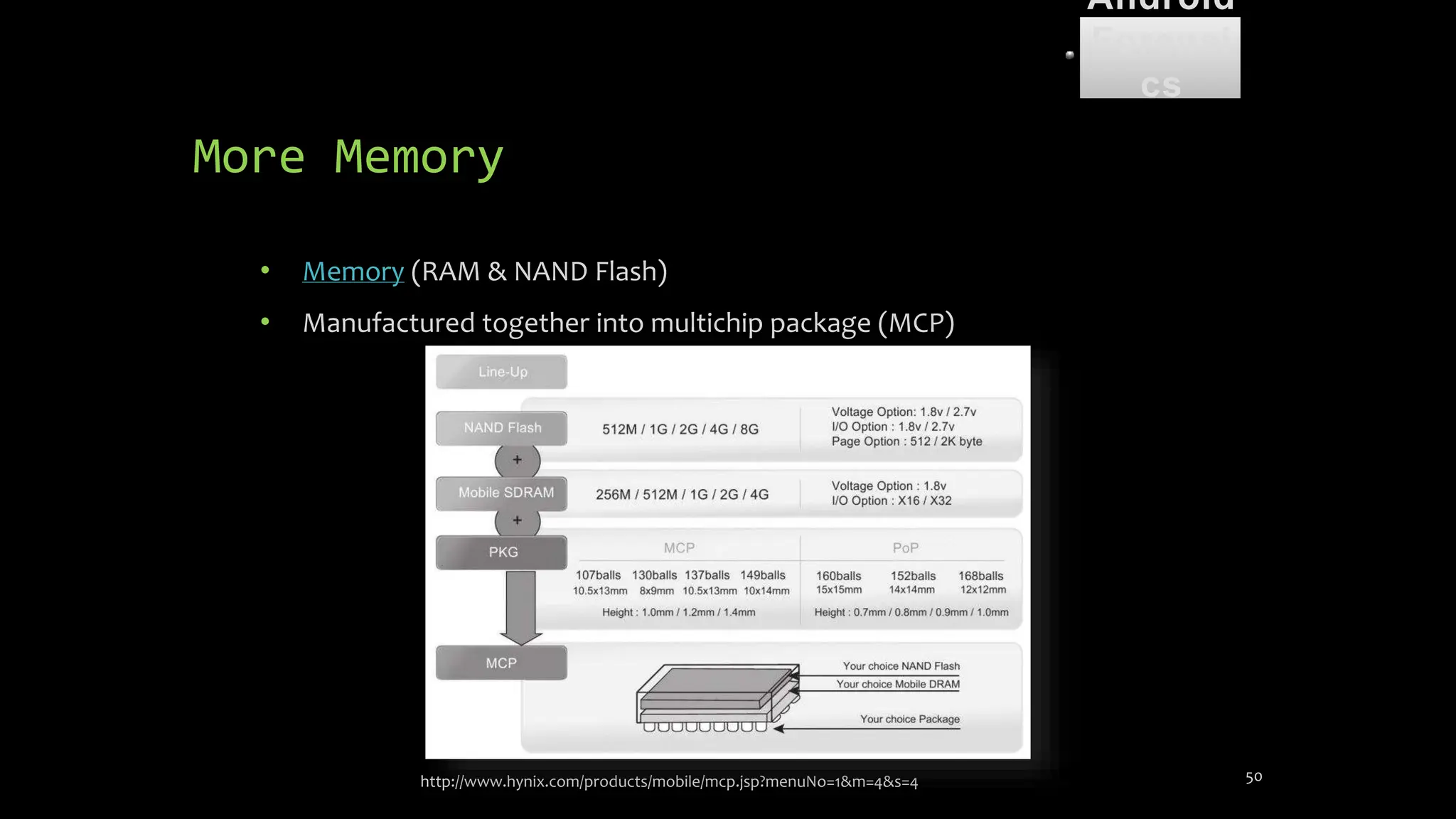
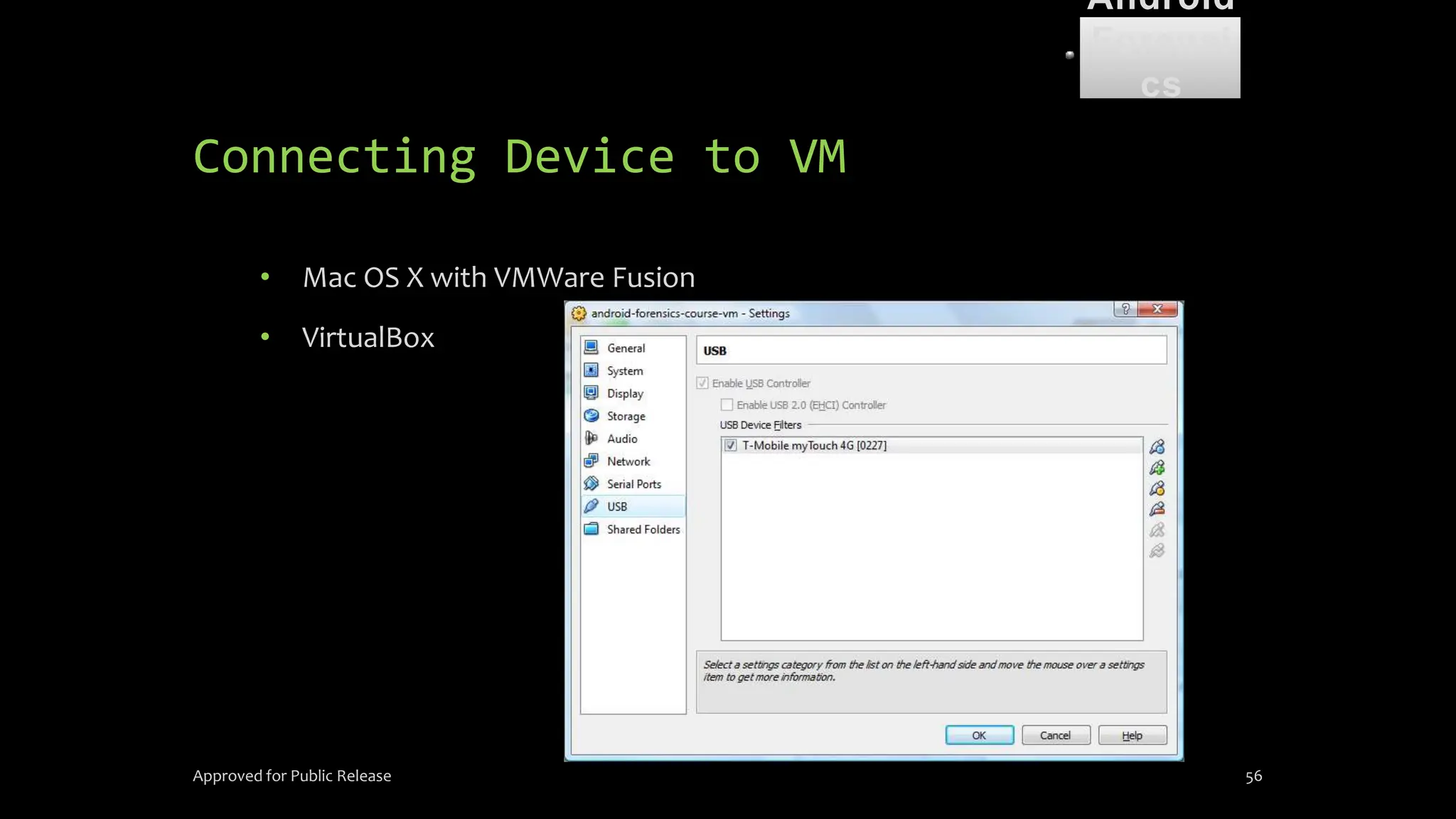
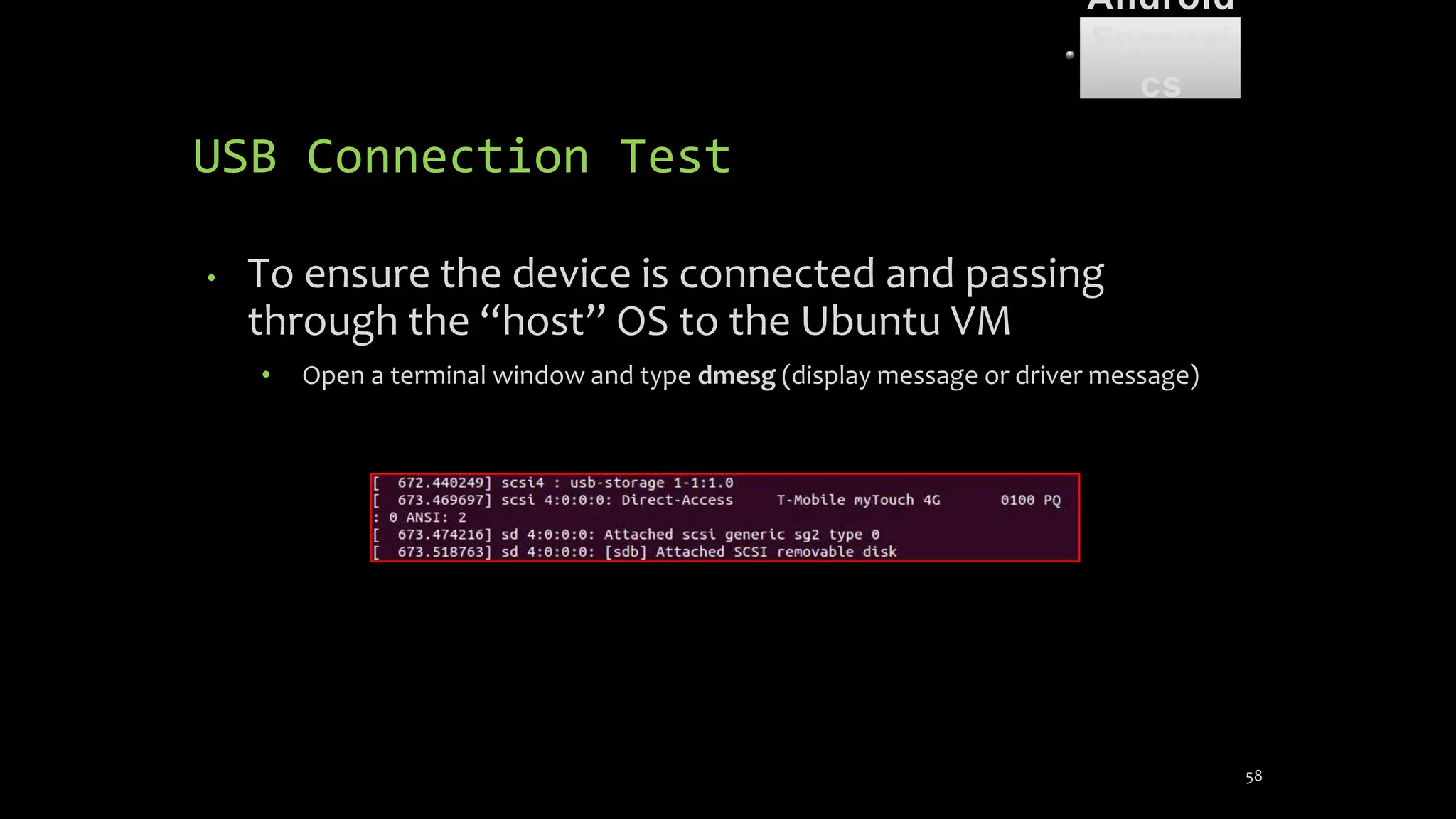
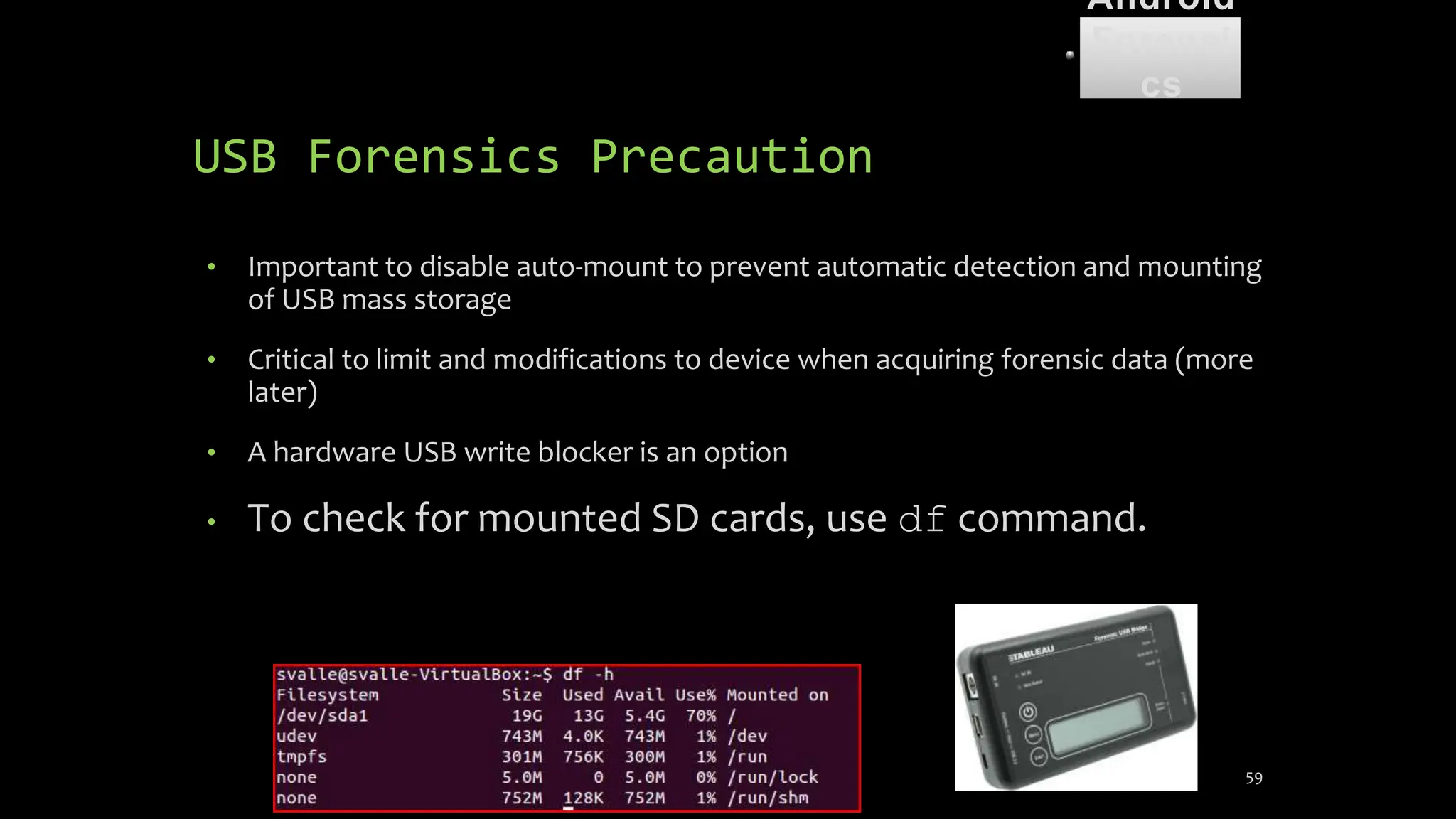
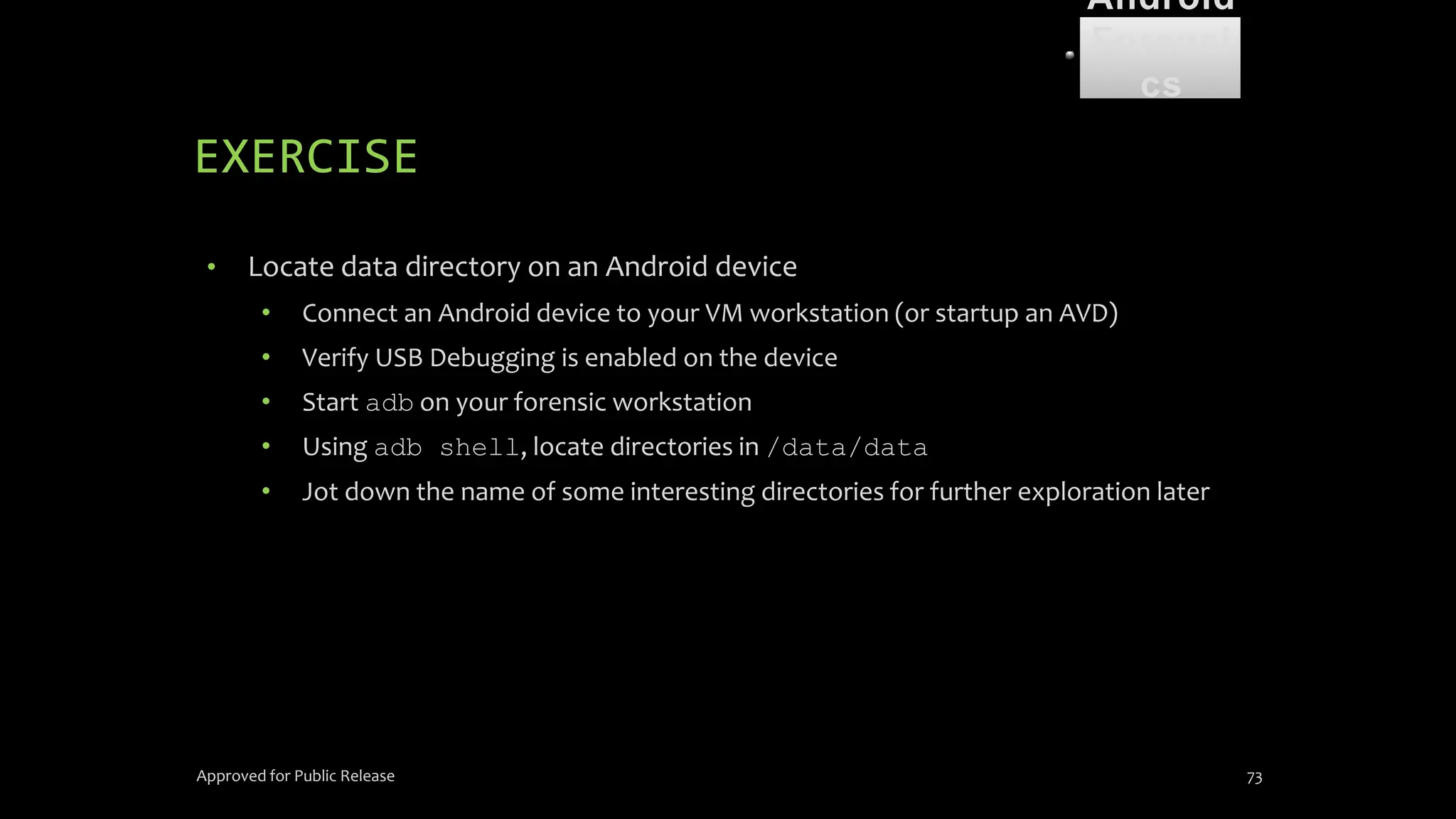
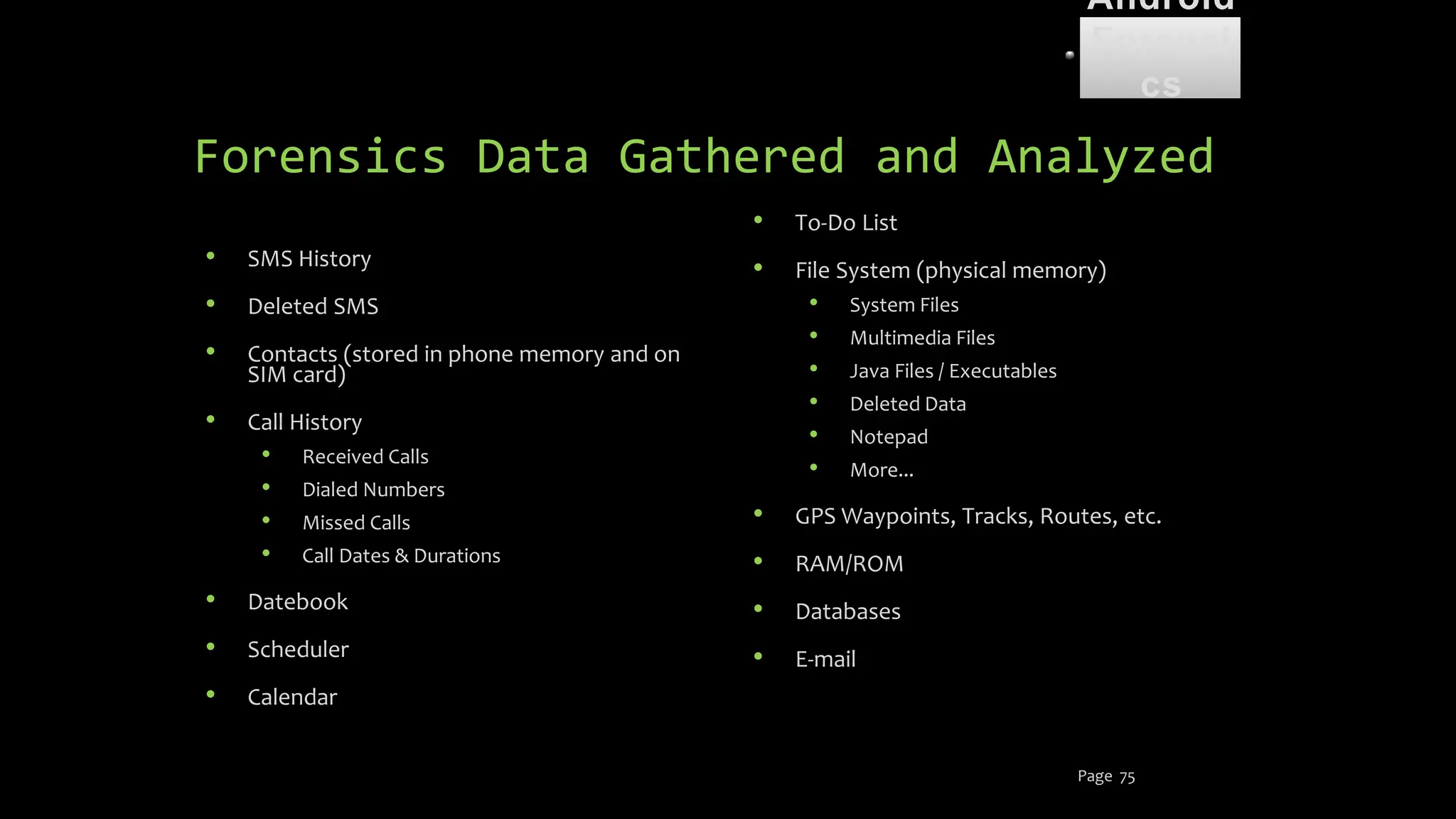
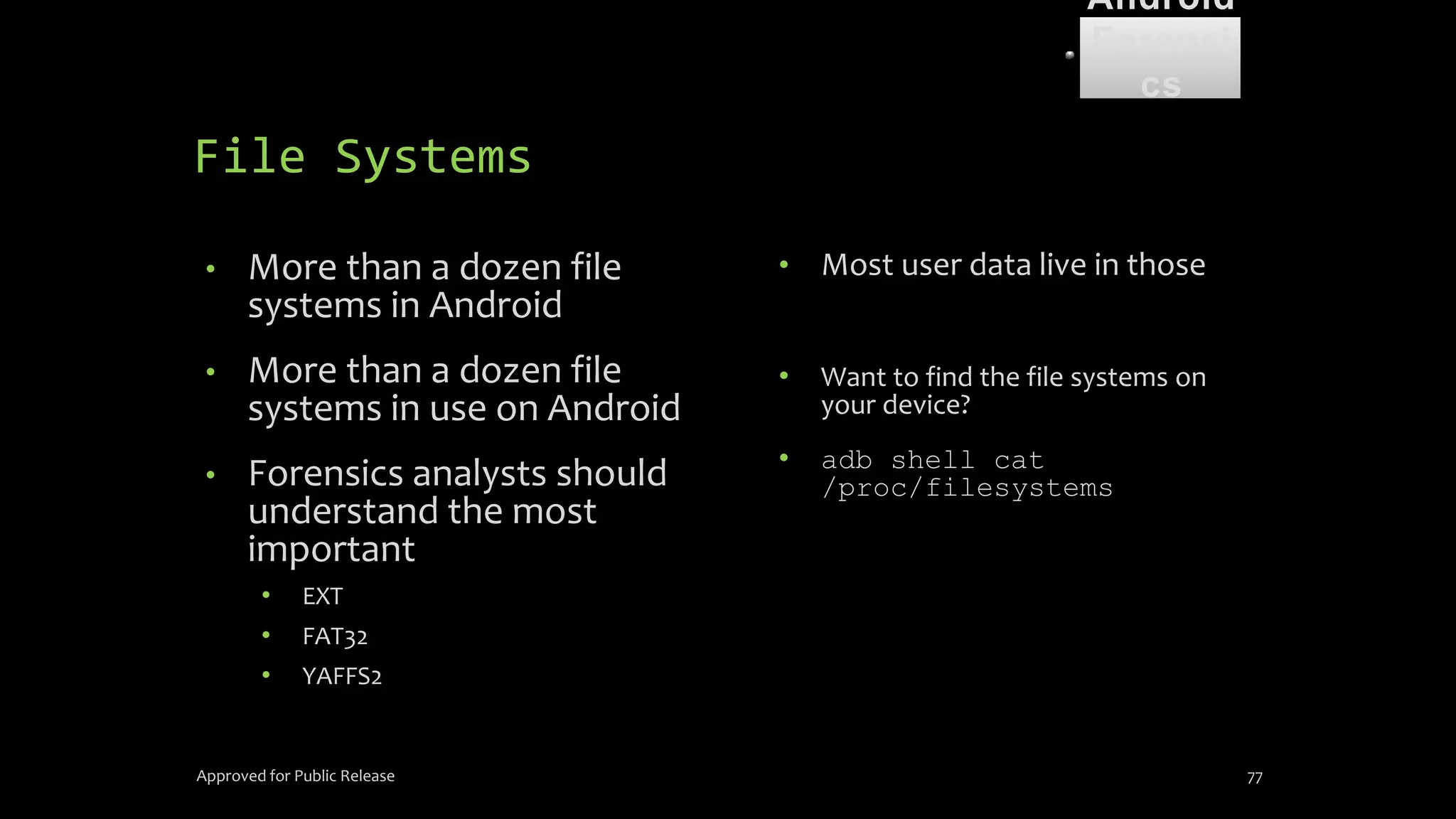
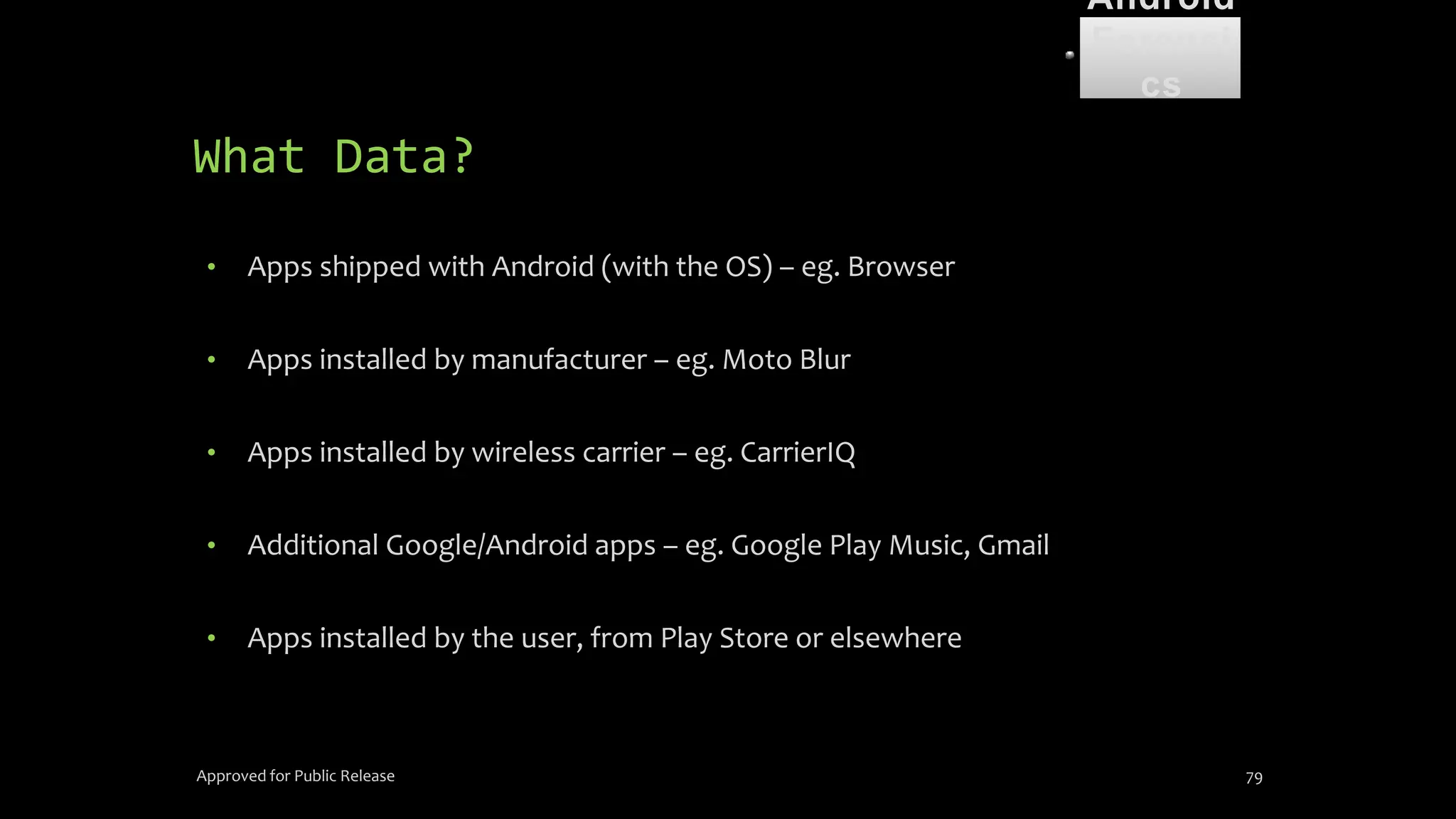
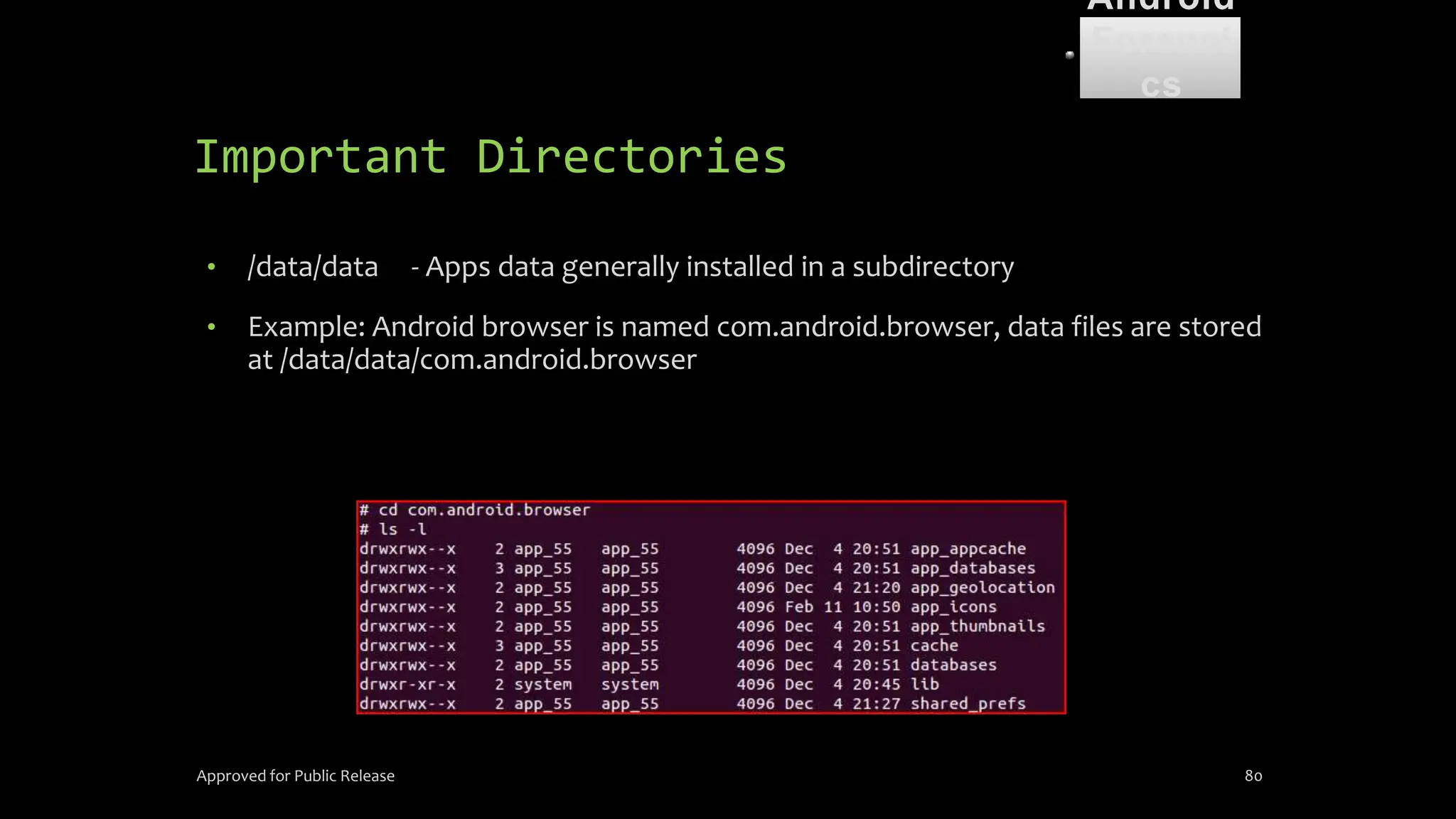
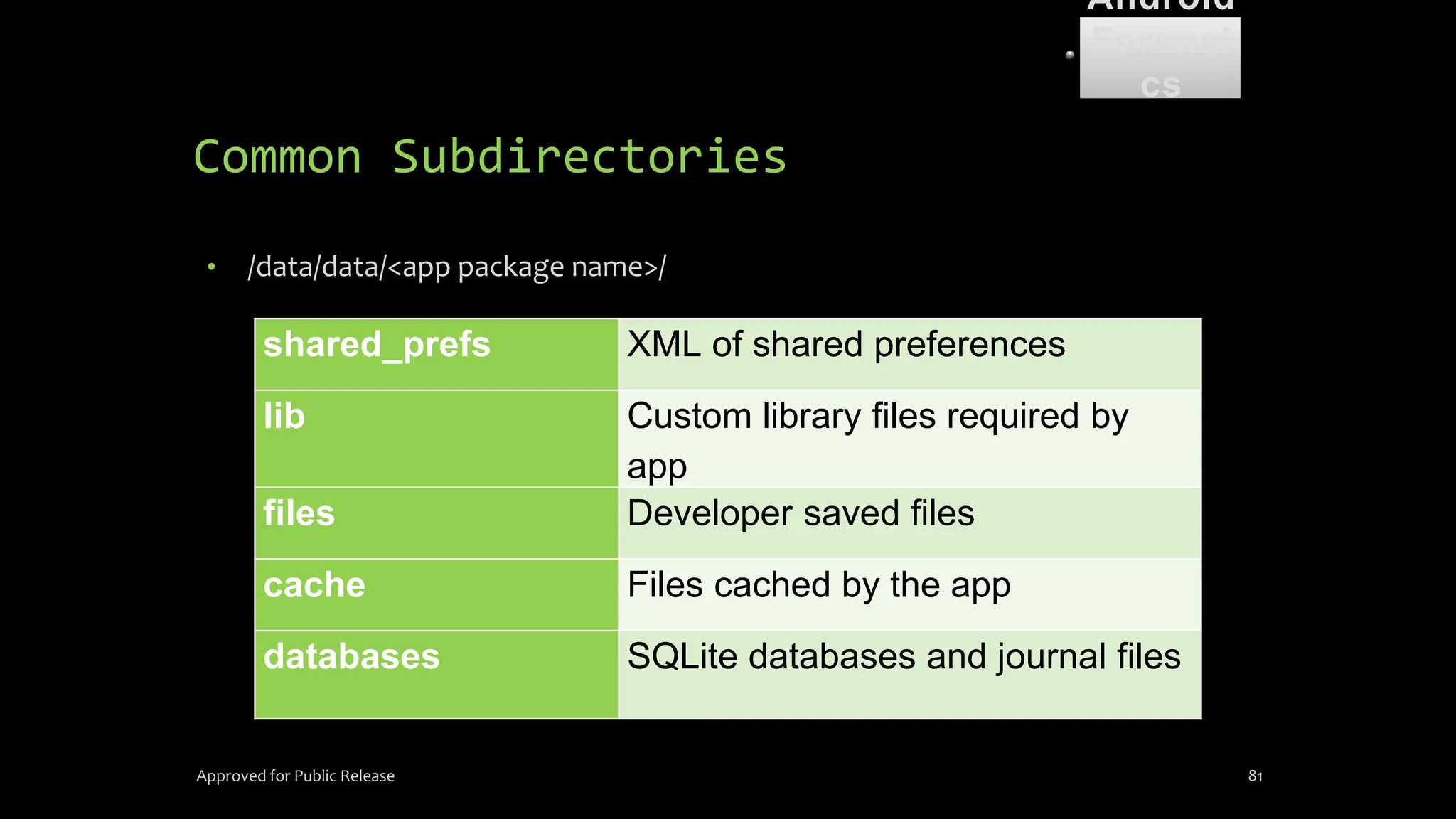
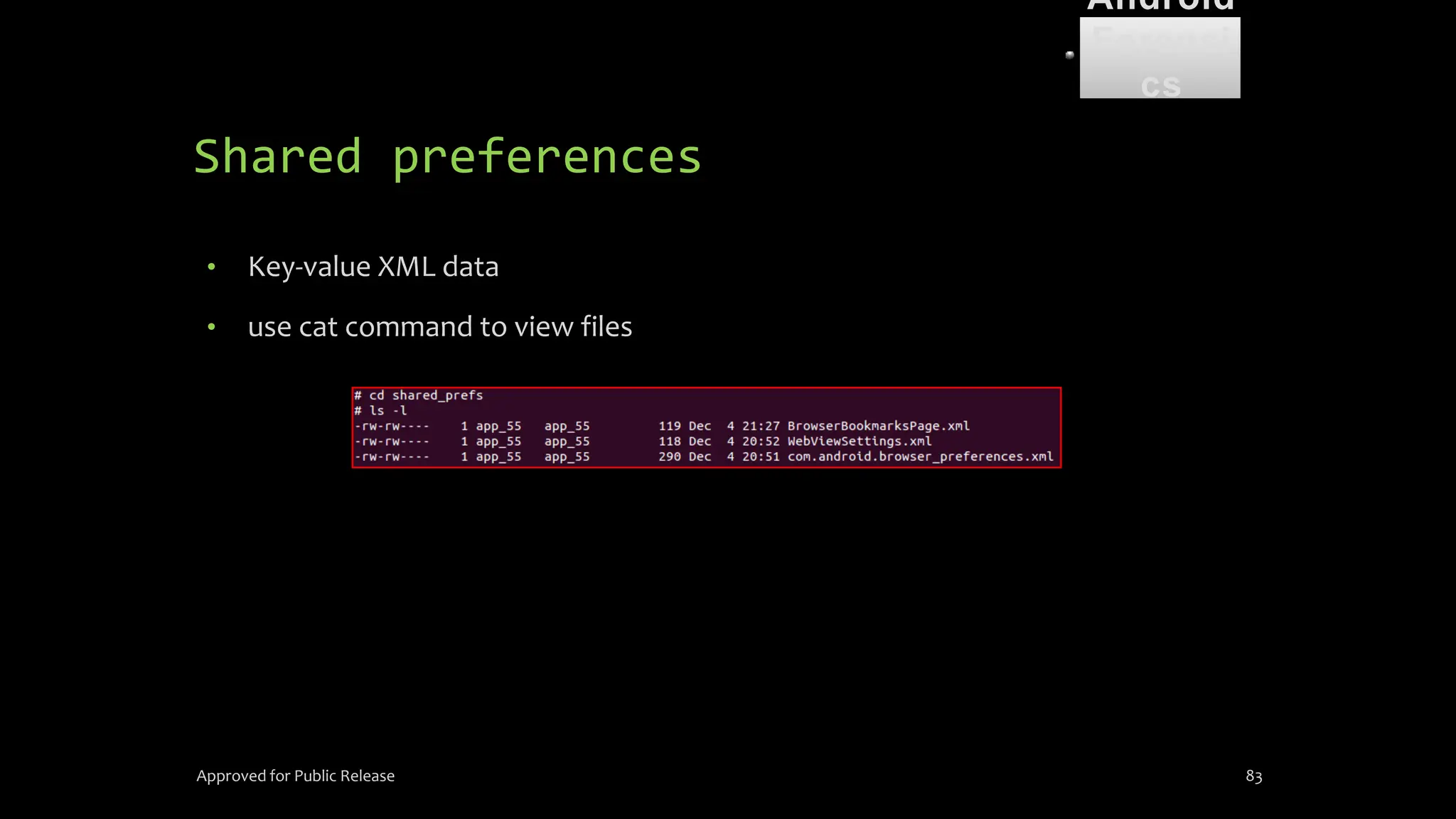
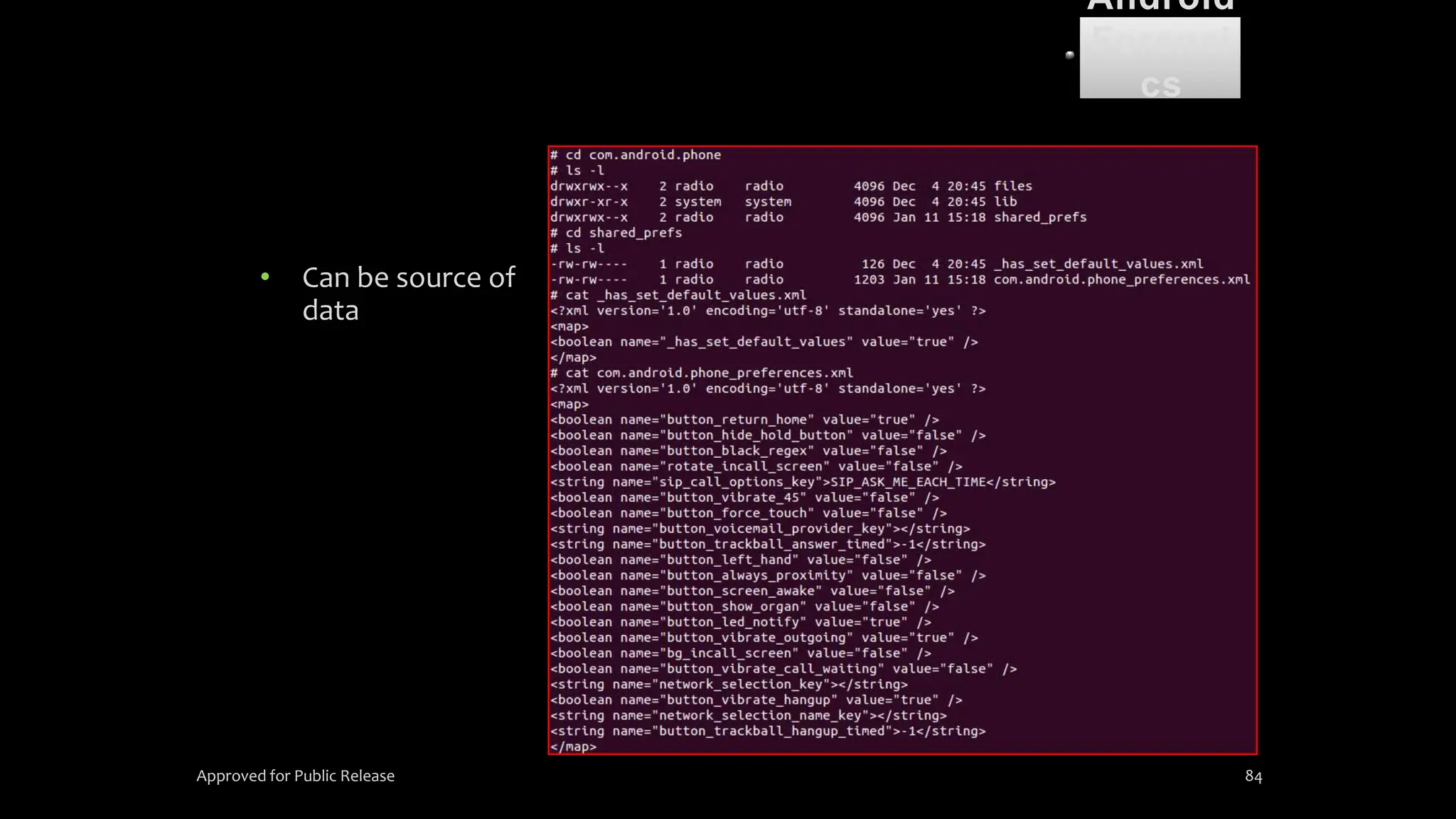
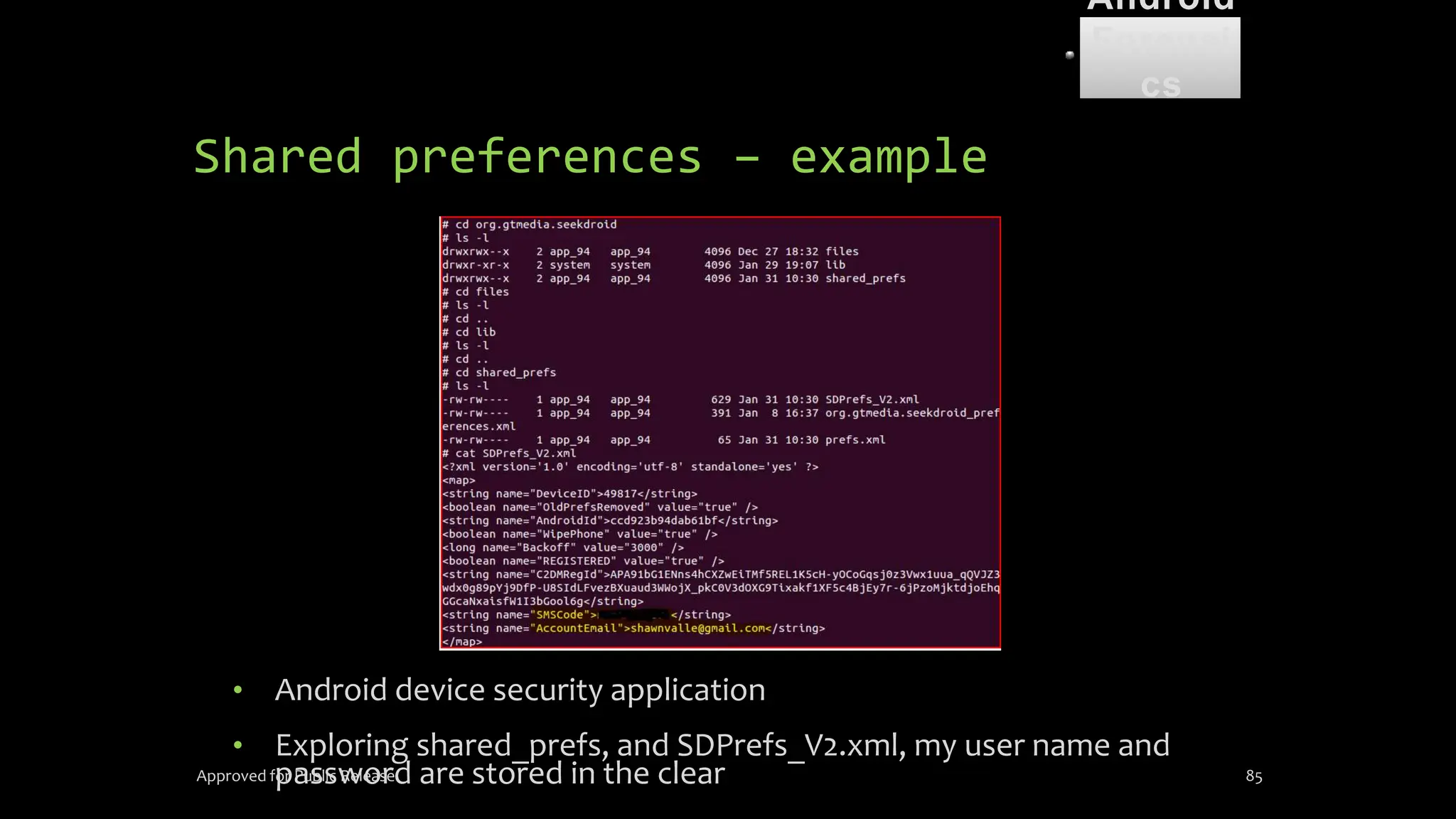
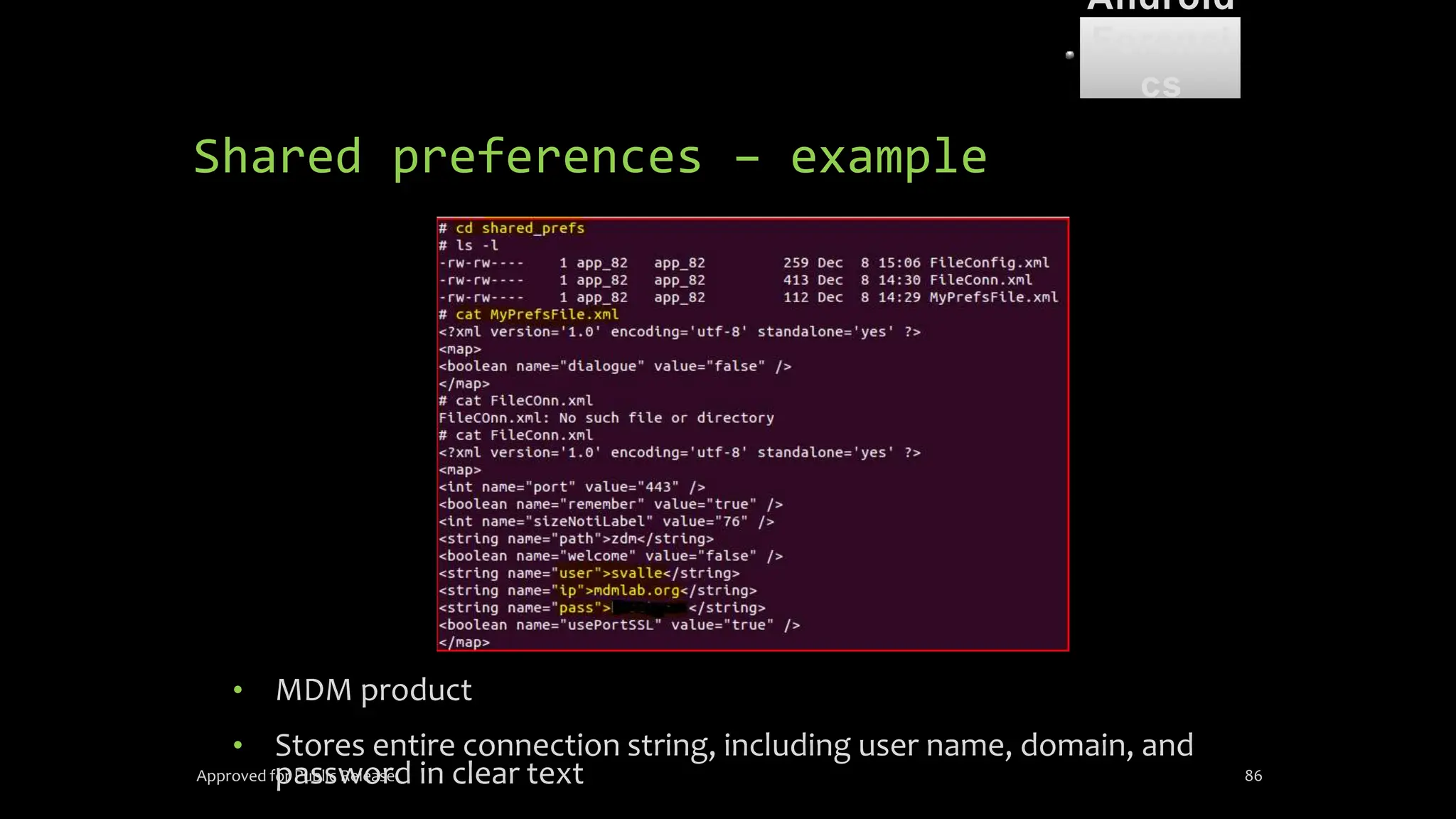
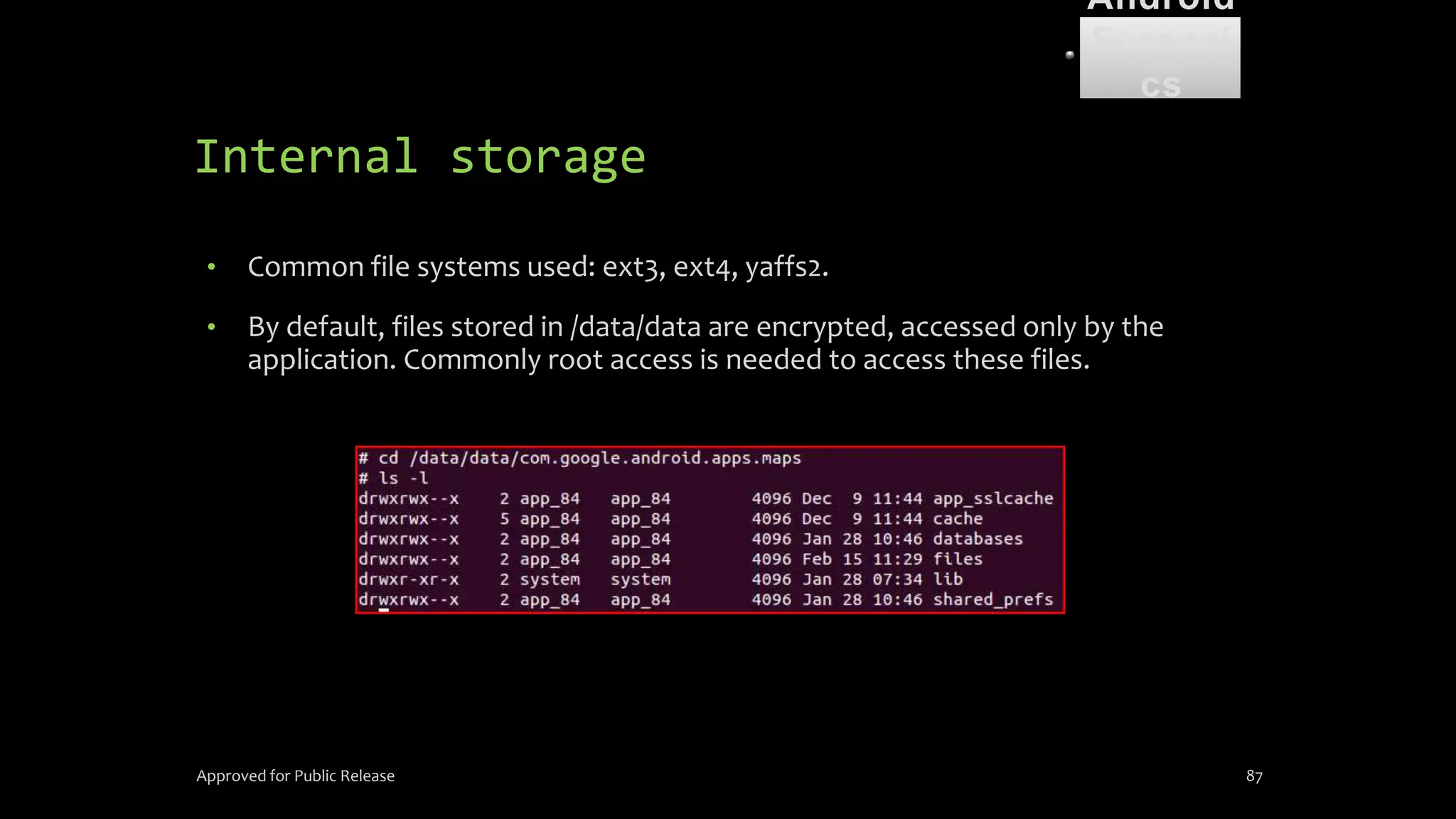
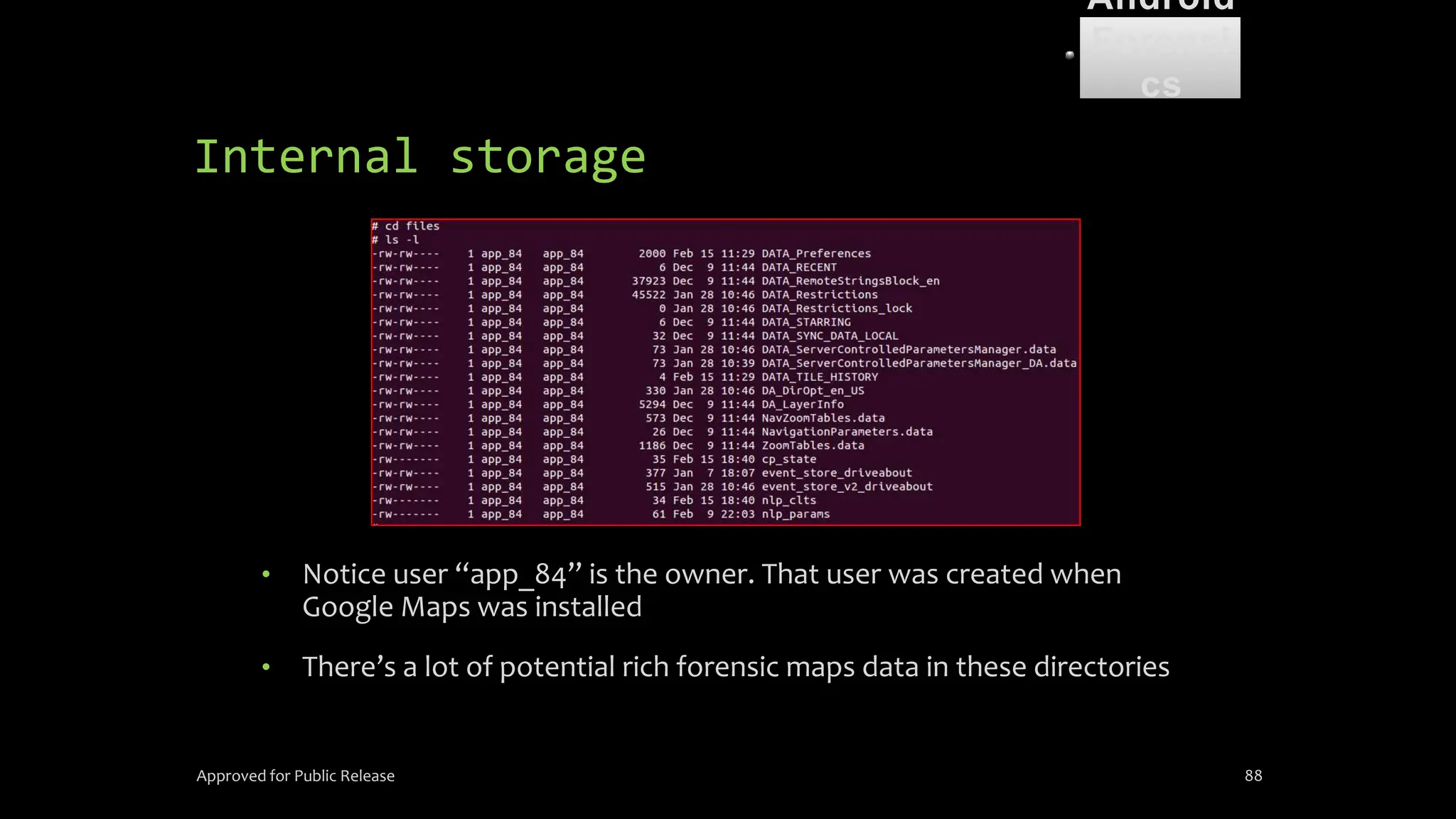
The document discusses mobile and wireless device forensics, highlighting the various types of data stored on mobile devices, the challenges of investigating these devices, and acquisition procedures for data retrieval. It covers the significance of SIM cards, personal digital assistants (PDAs), and the importance of preserving the integrity of evidence during the acquisition process. Additionally, it outlines mobile forensics equipment, techniques for data extraction, and specific considerations for Android forensics, including the role of Android Debug Bridge (ADB) in forensic analysis.












































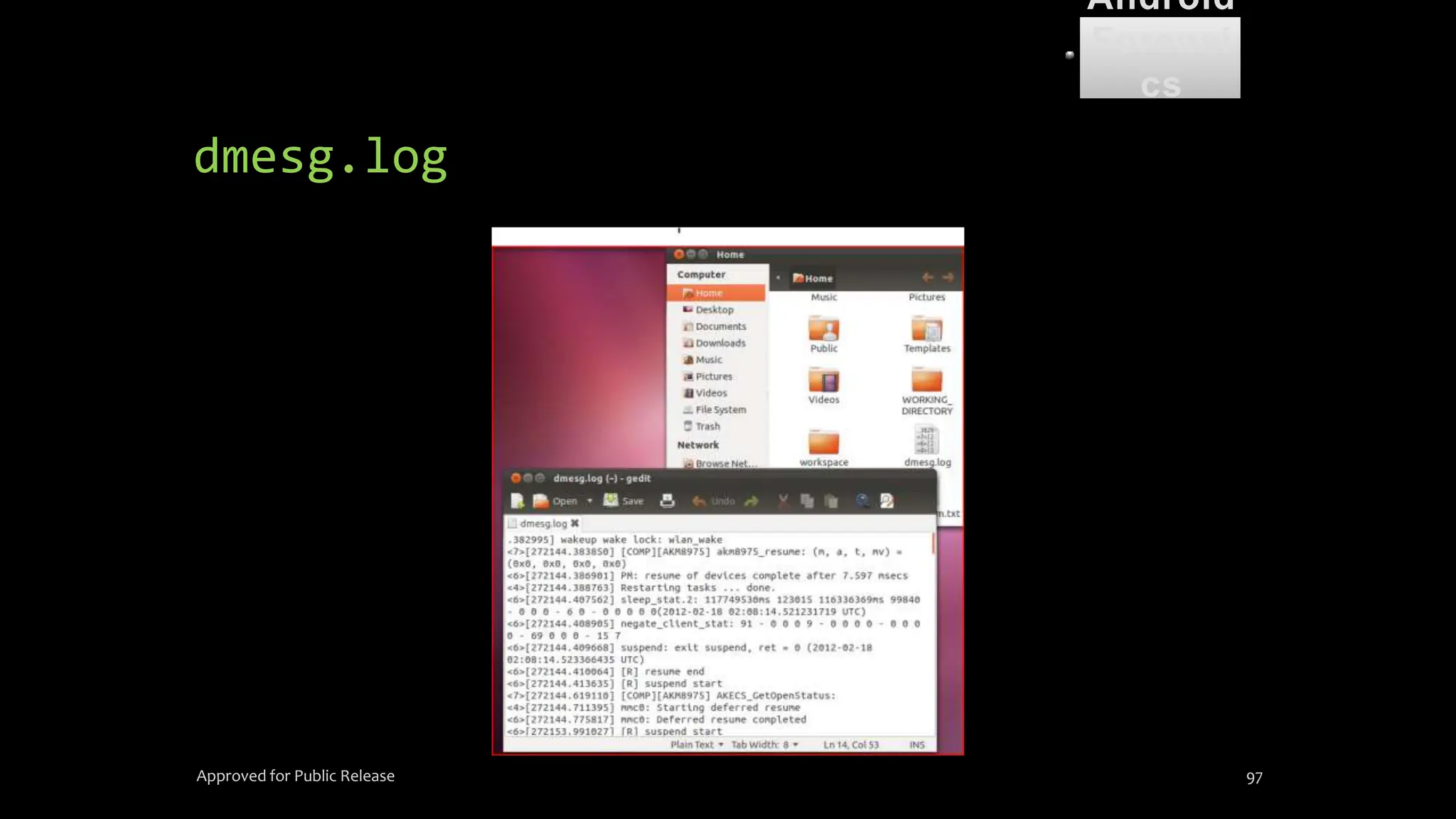
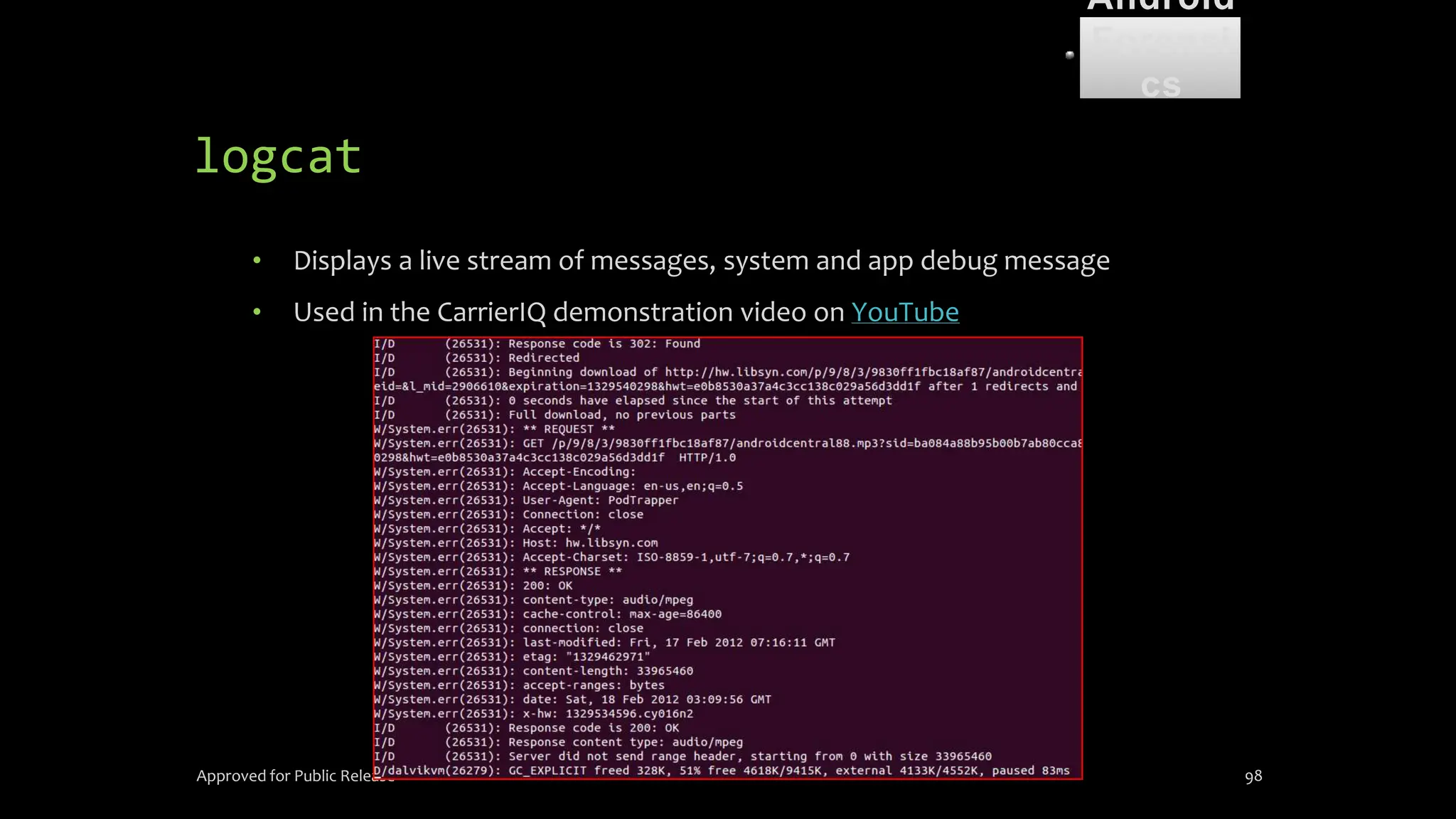
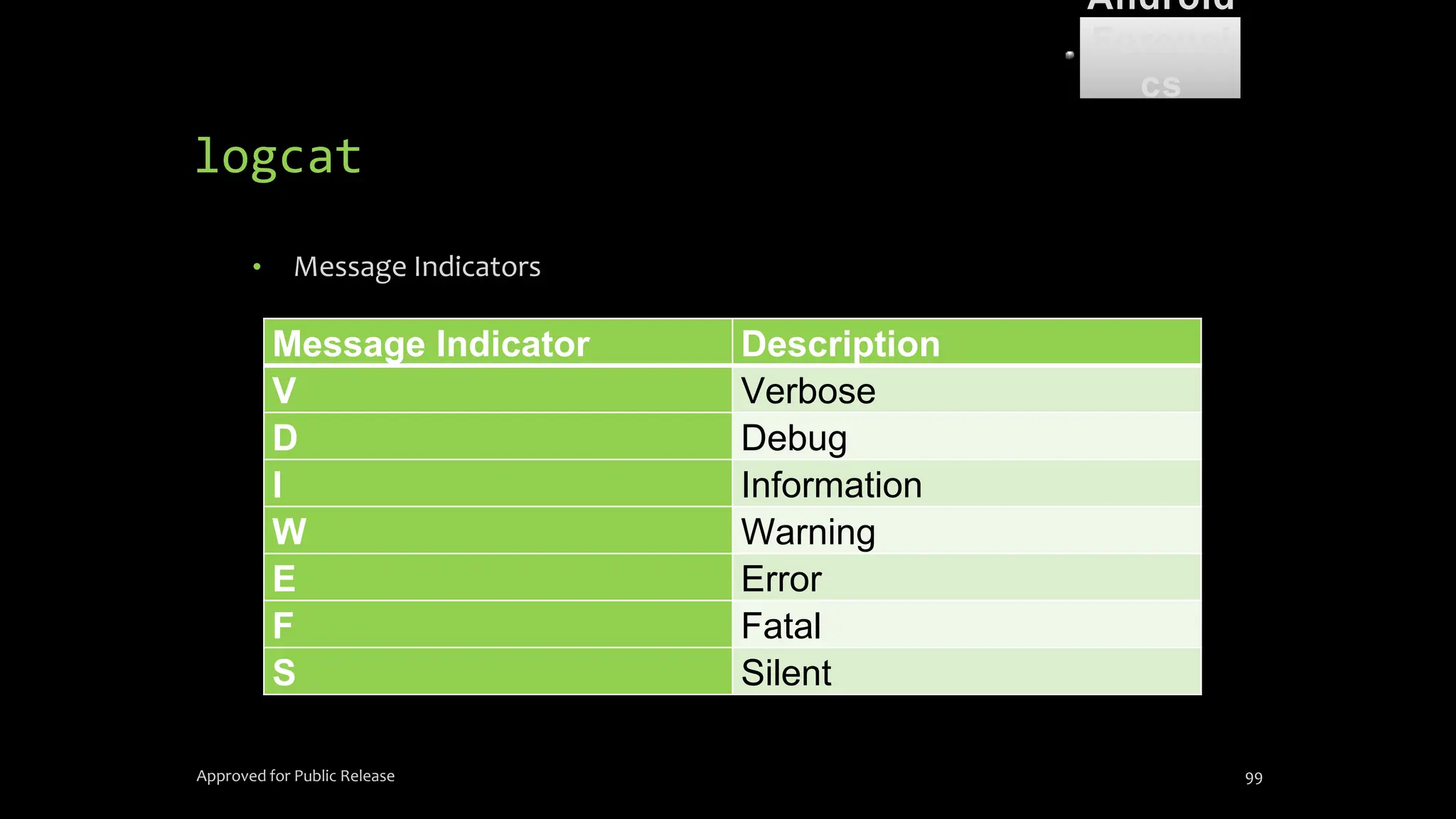
![dmesg
• Notice [KEY] above. Possibly something logging keystrokes. May be
worth further investigation
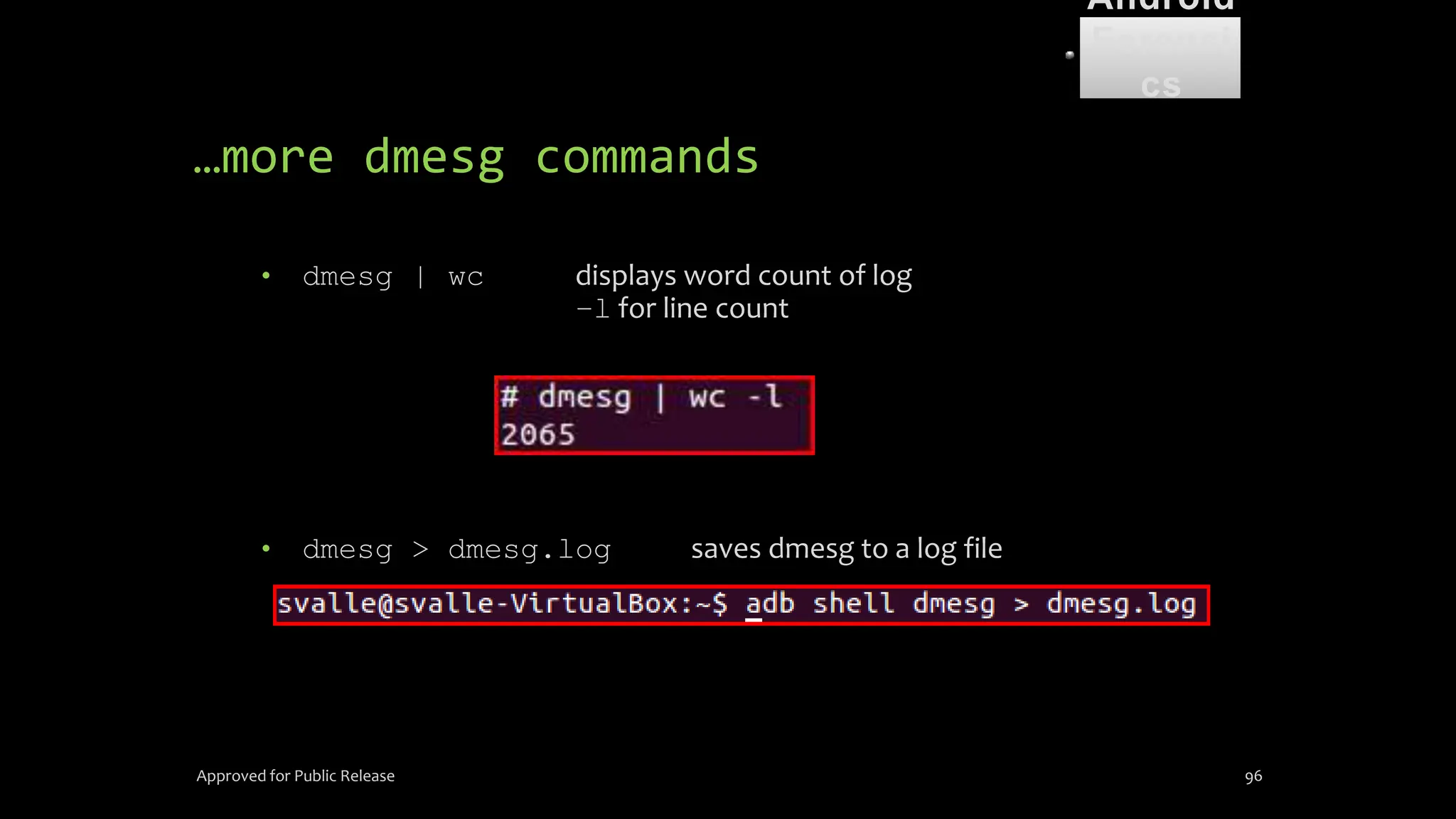
• Root access is not needed for dmesg, just USB
debugging
Approved for Public Release 95
Android
Forensi
cs](https://image.slidesharecdn.com/unit3-mwdfs-240507105618-28cebdcd/75/Mobile-Forensics-and-Investigation-Android-Forensics-95-2048.jpg)