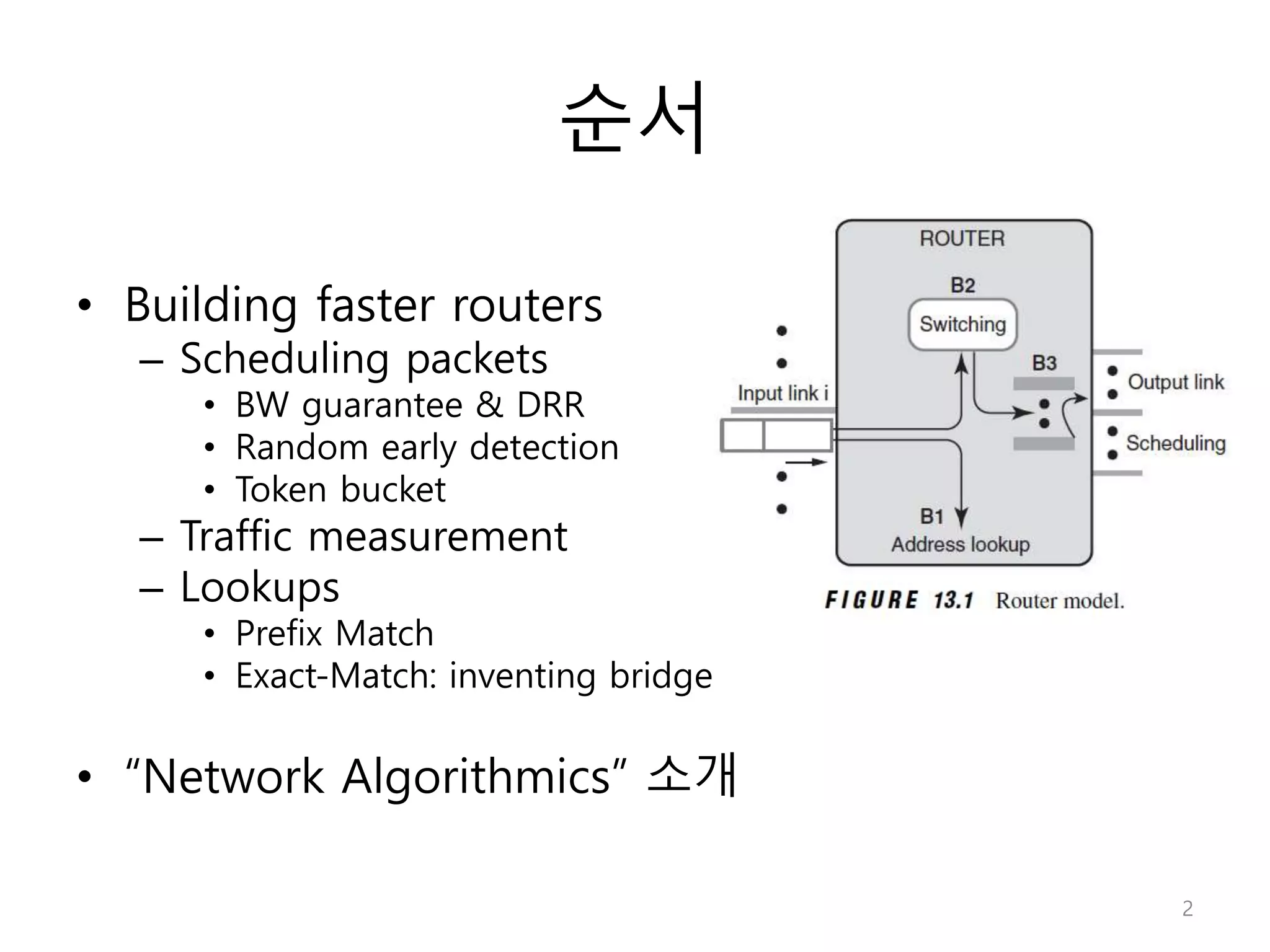
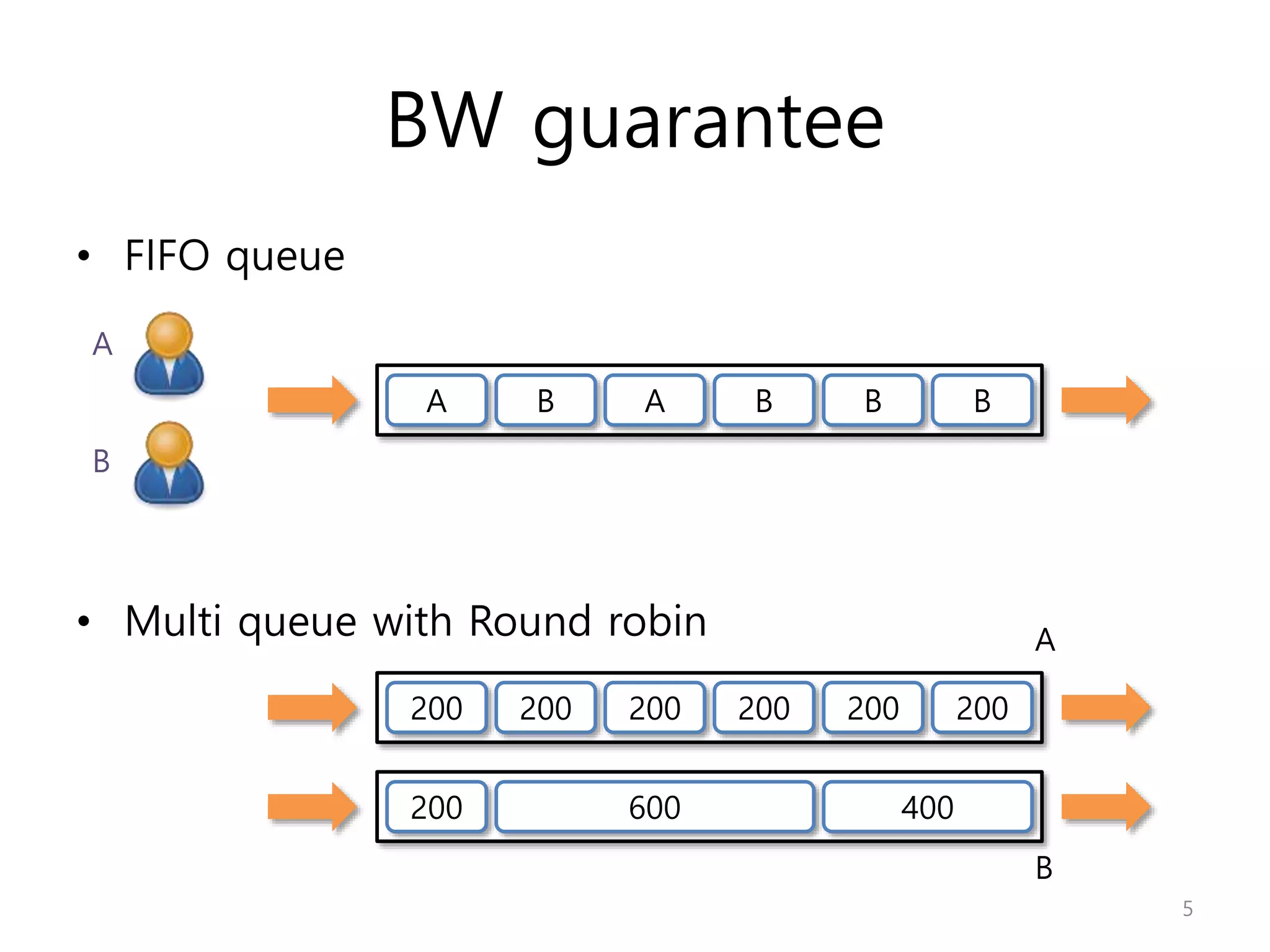
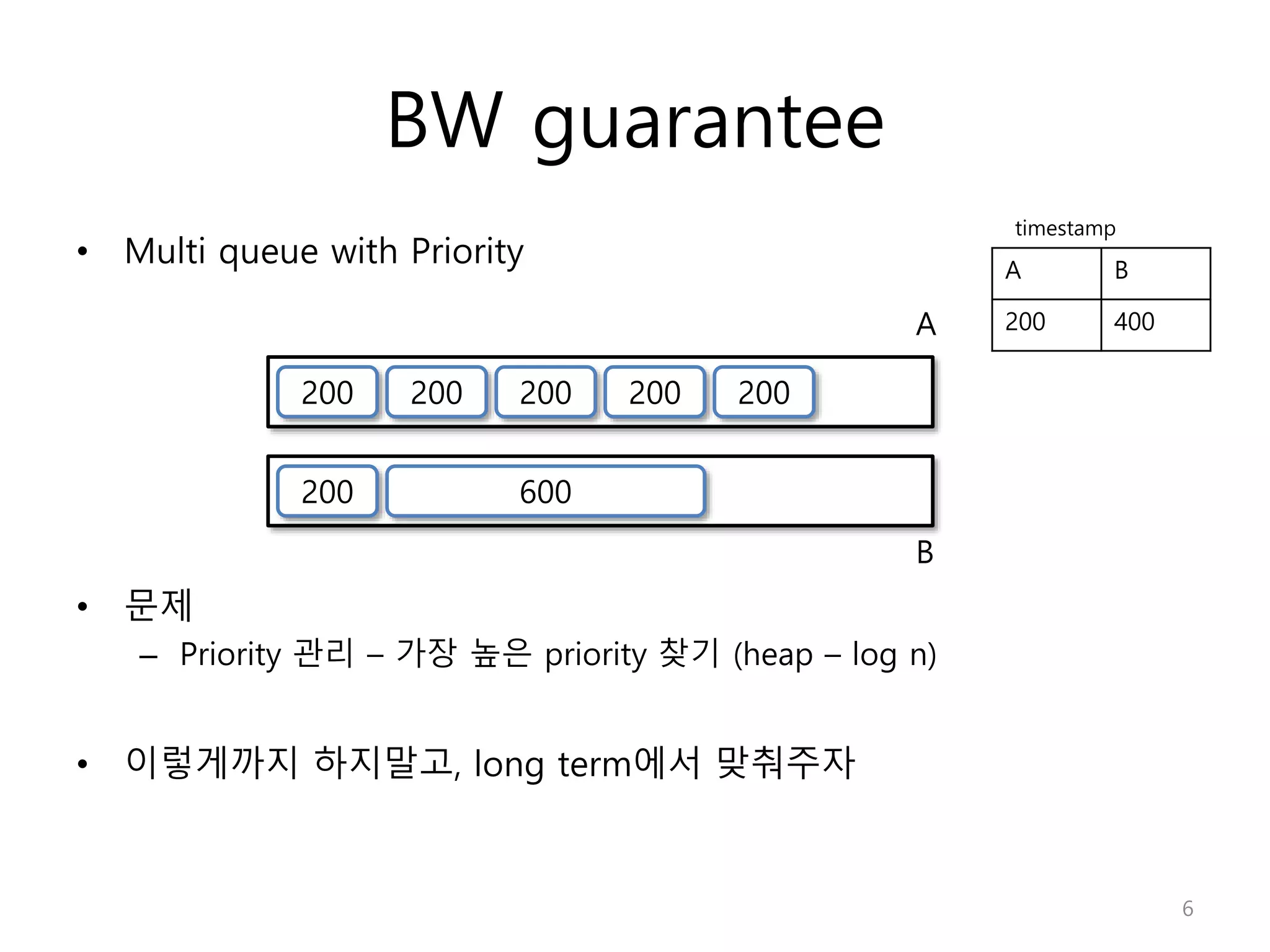
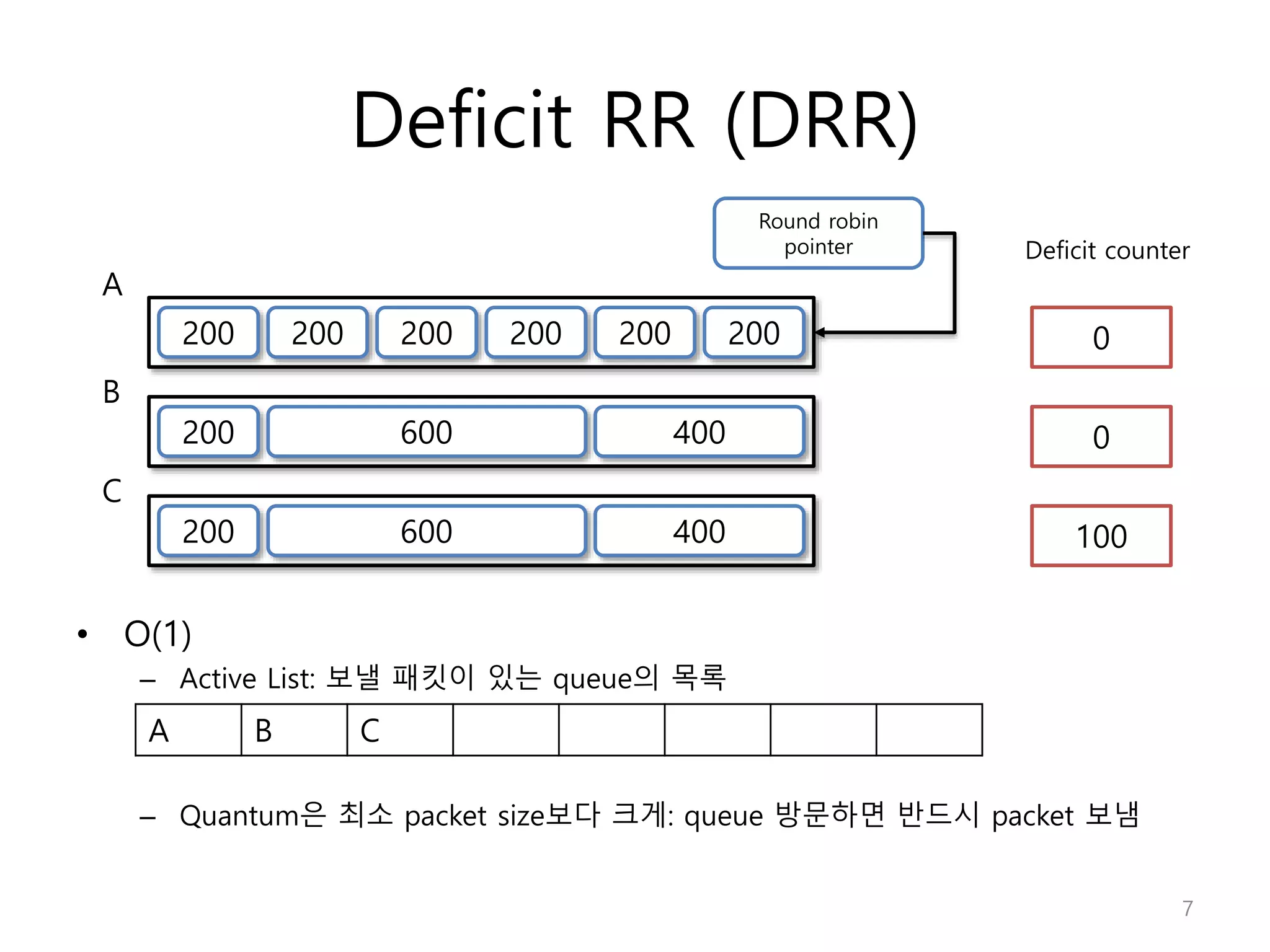
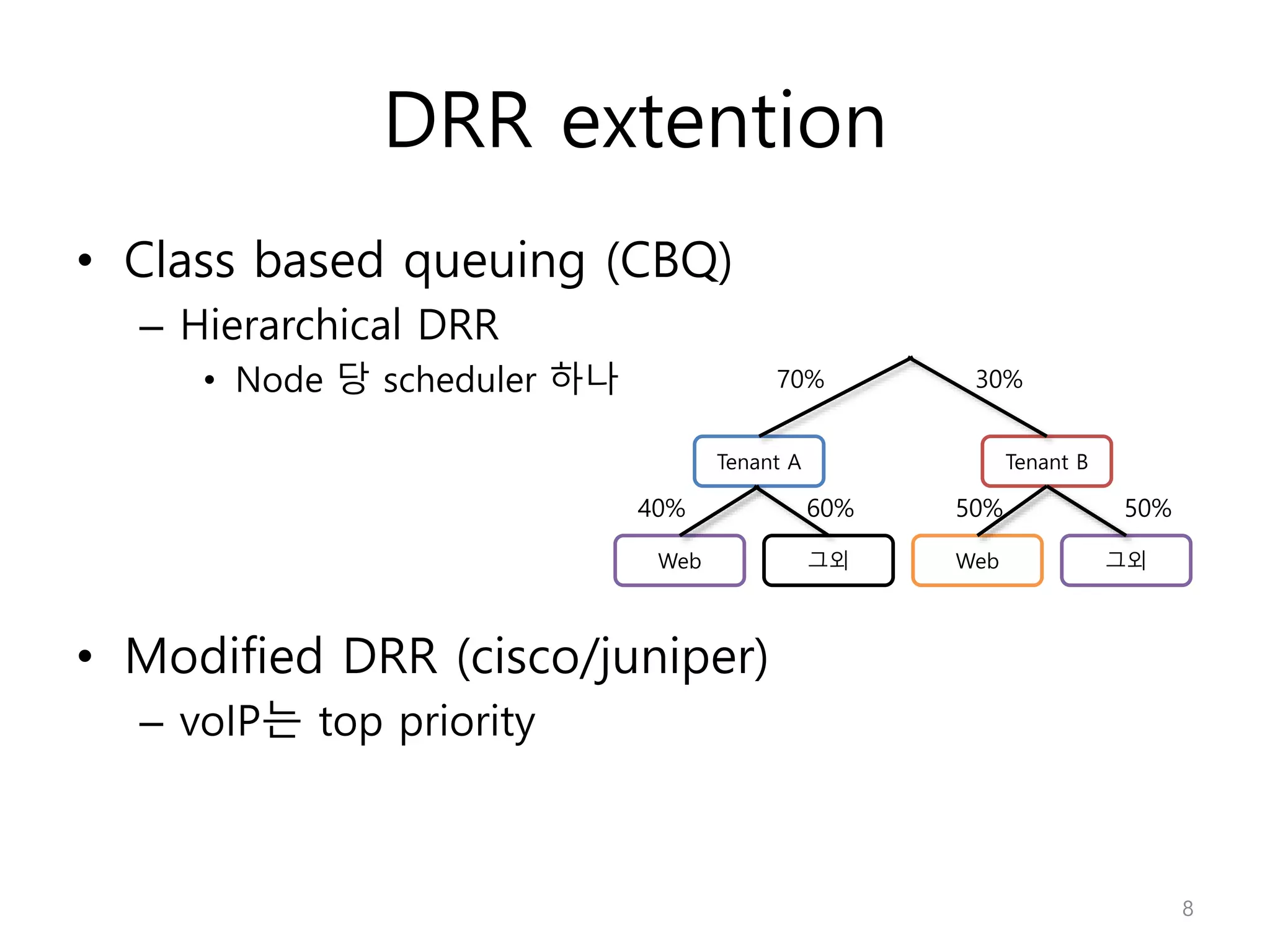
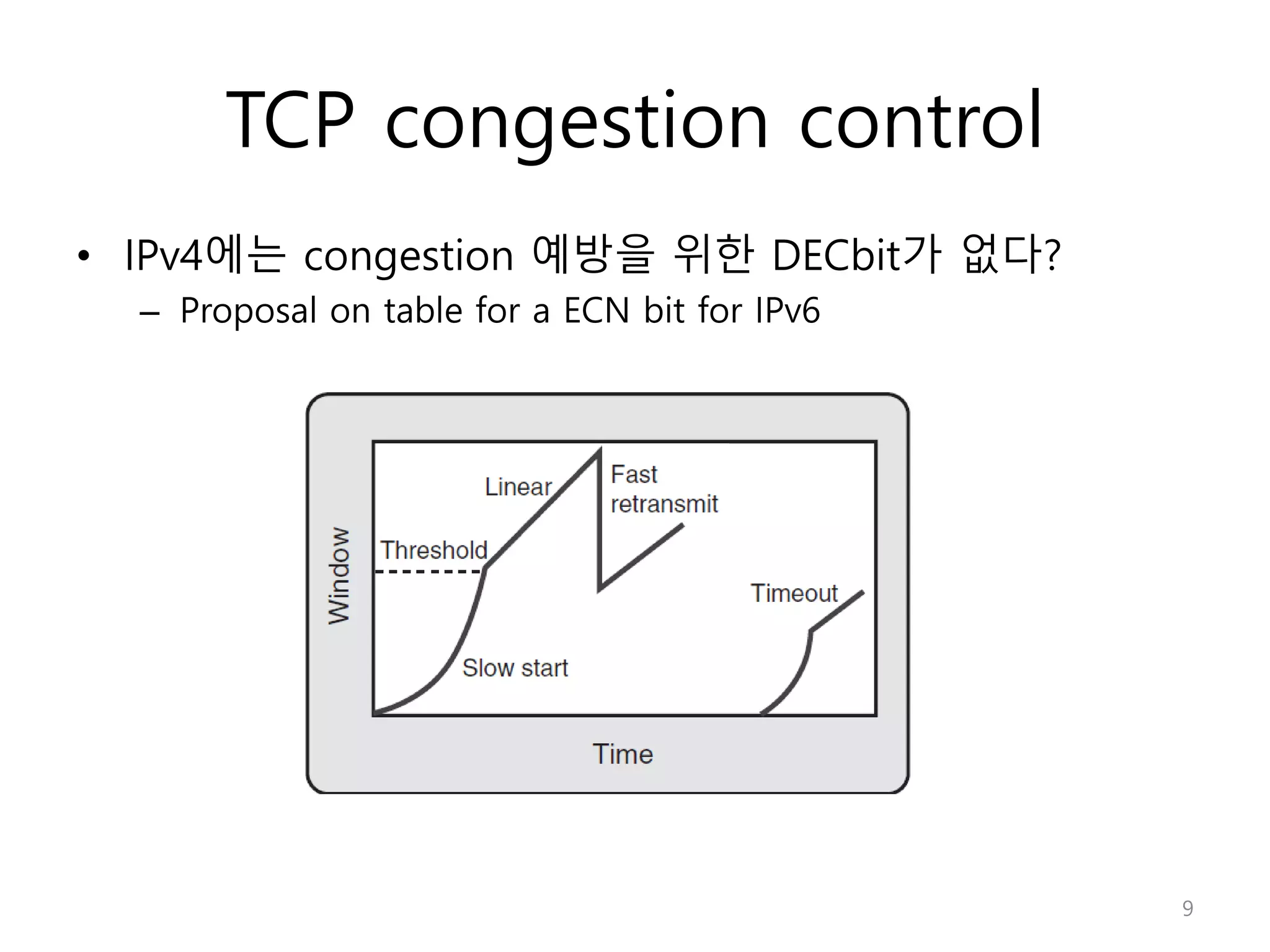
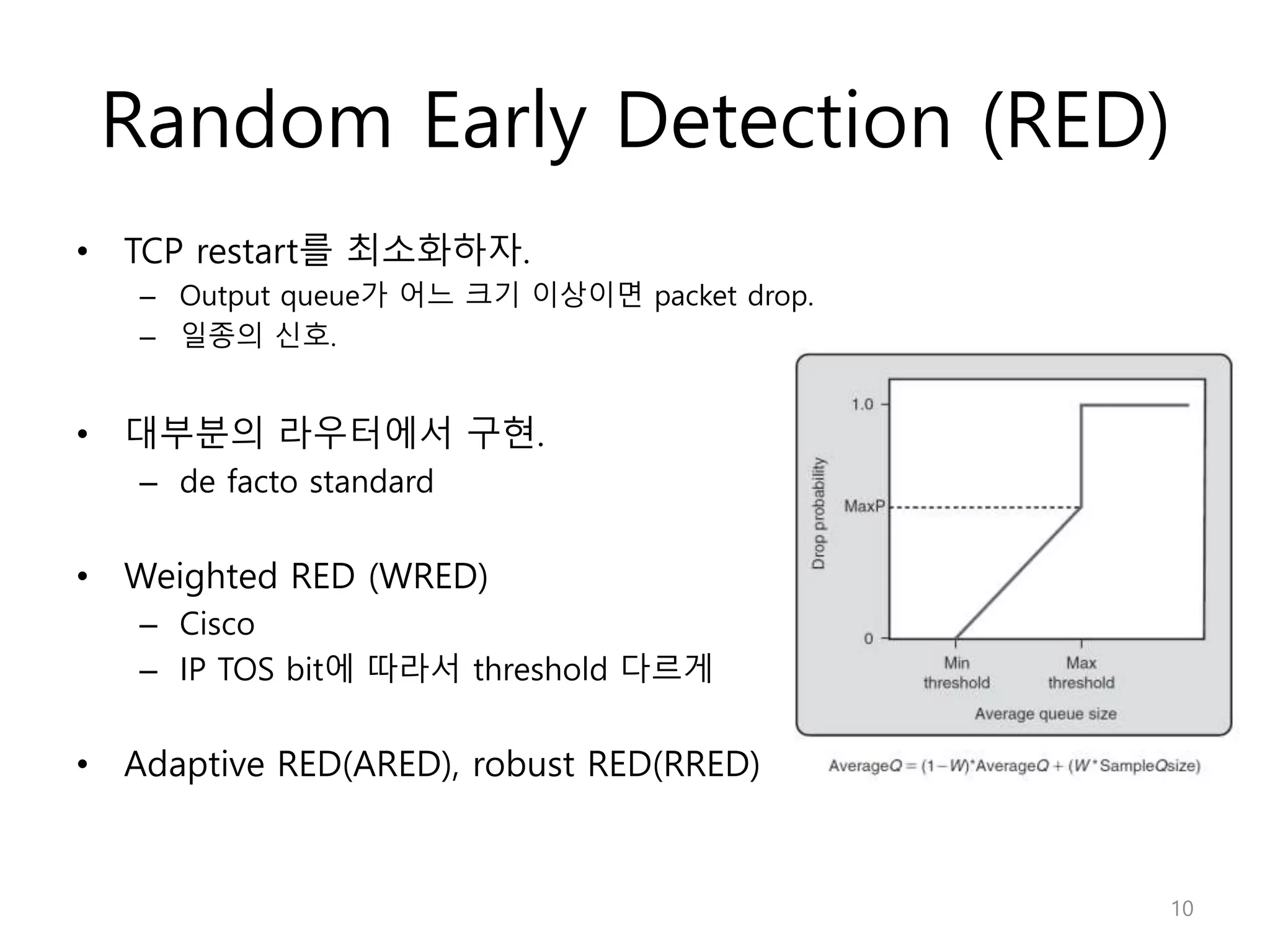
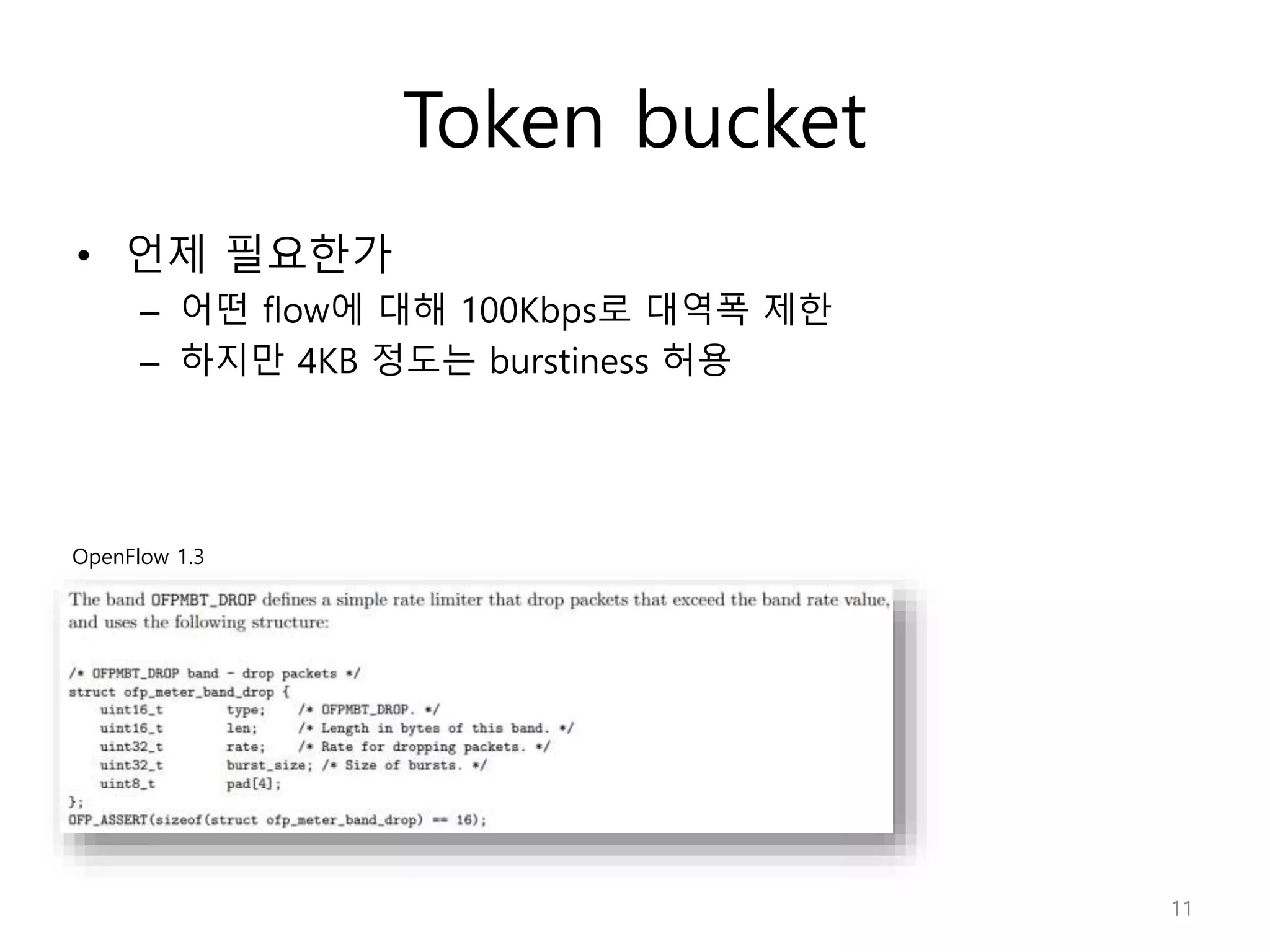
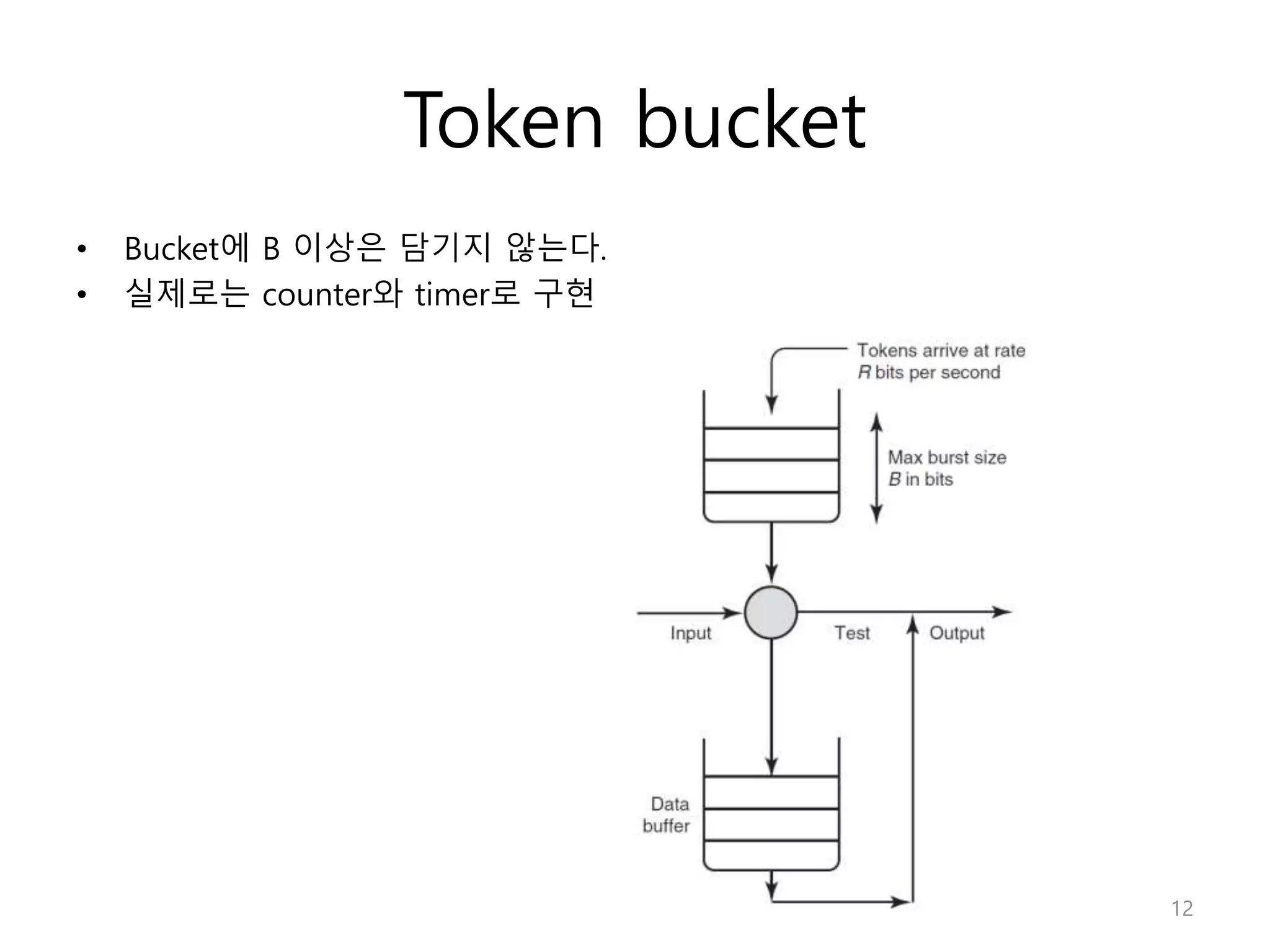
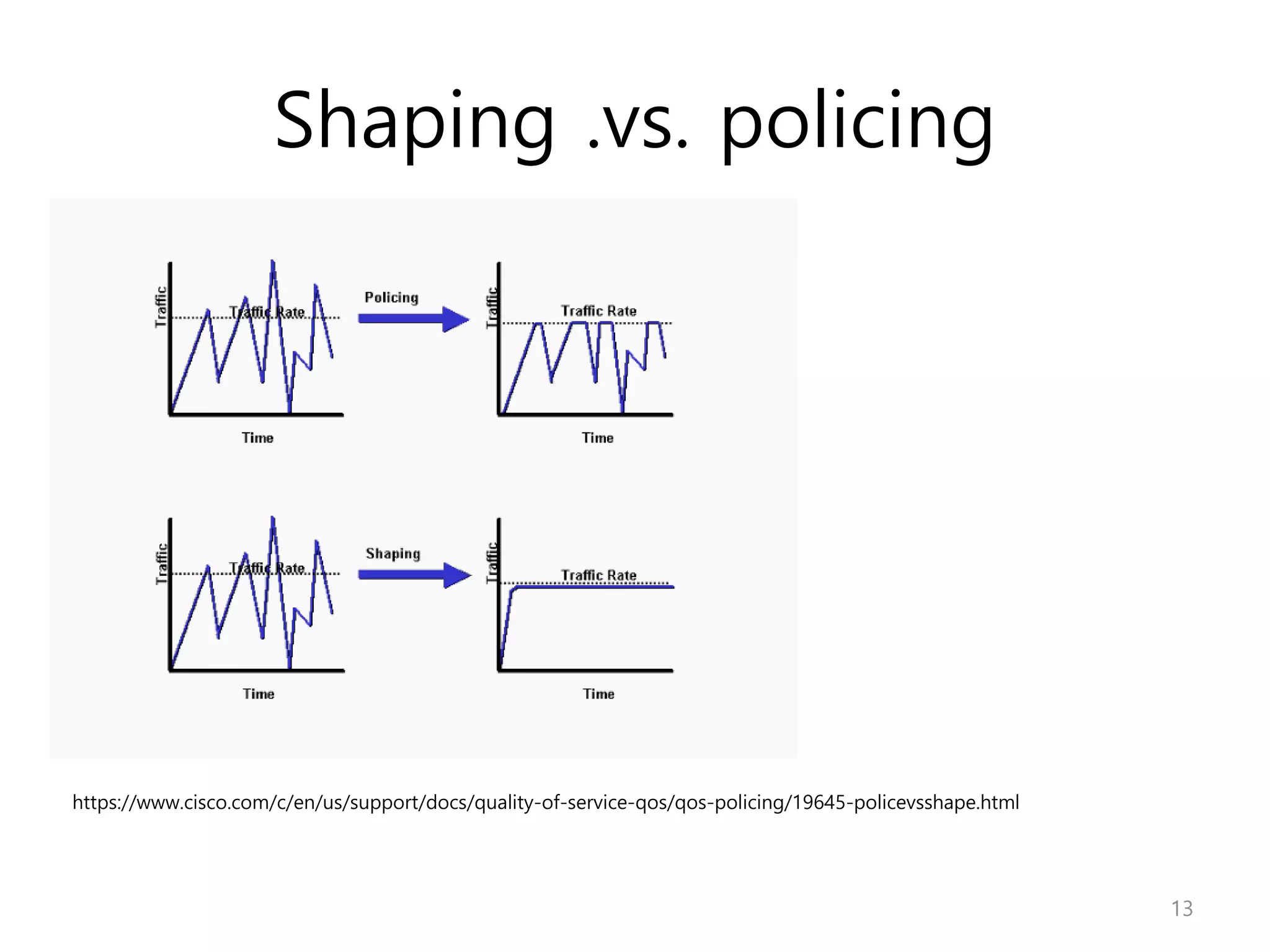
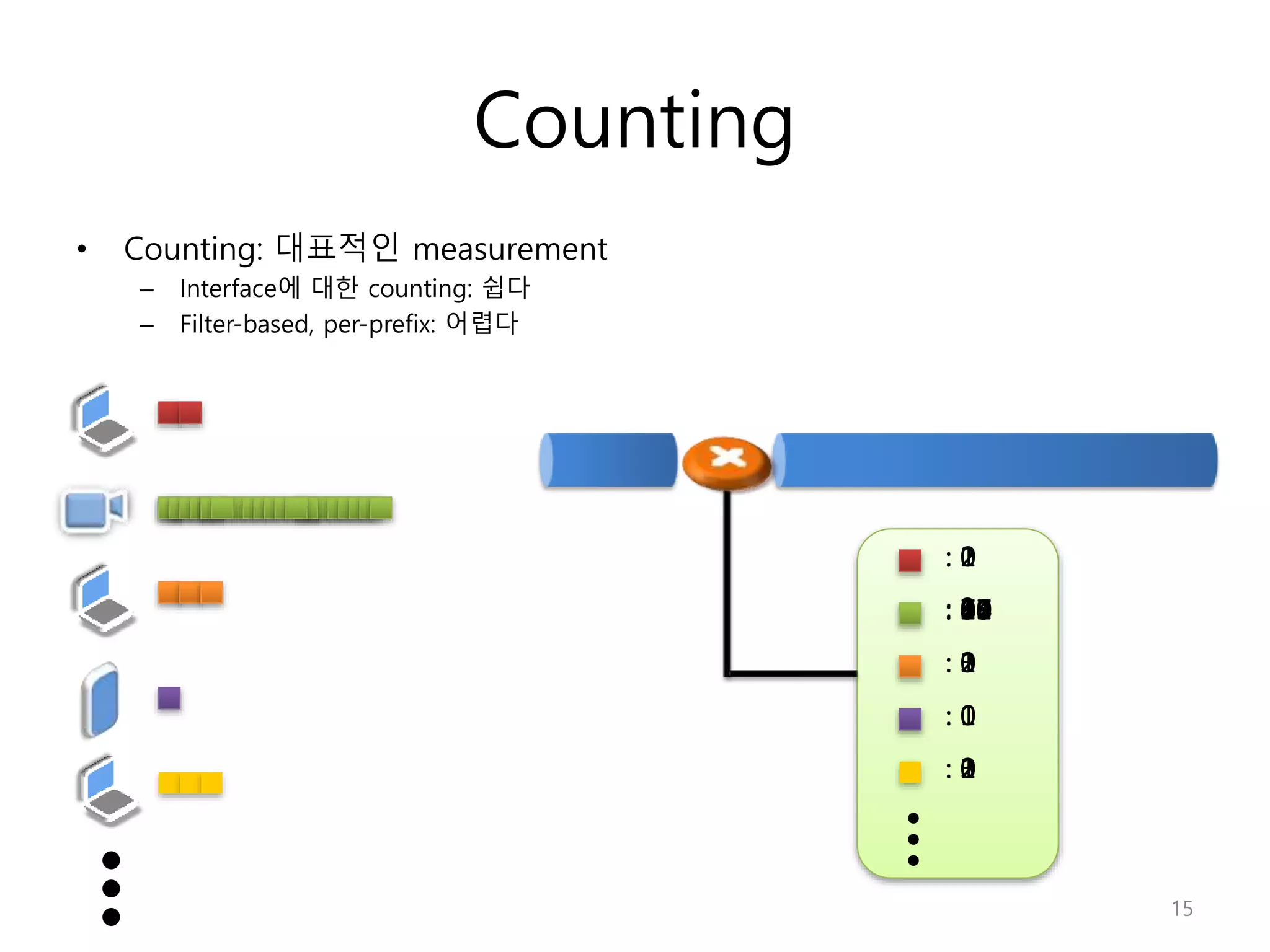
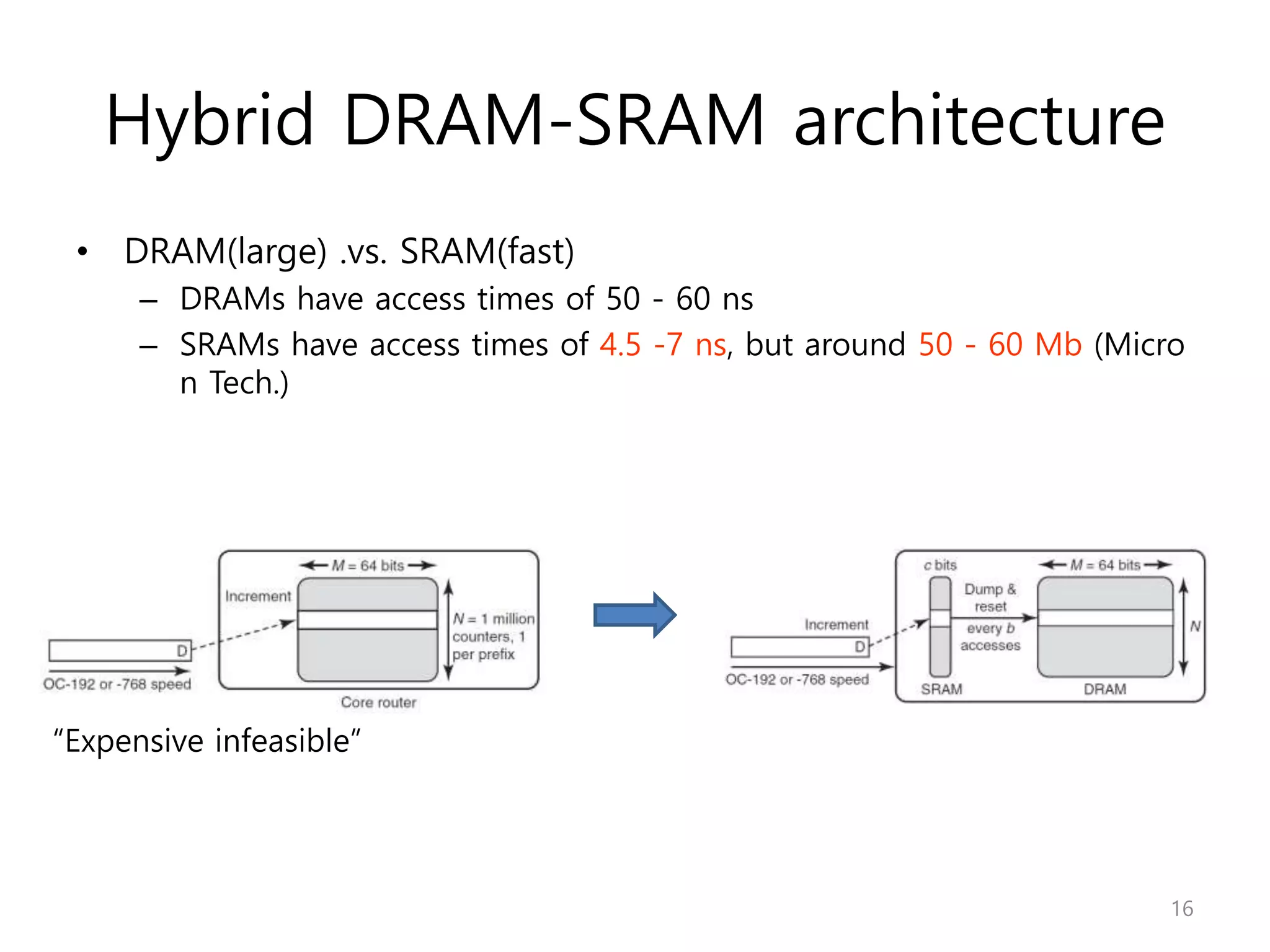
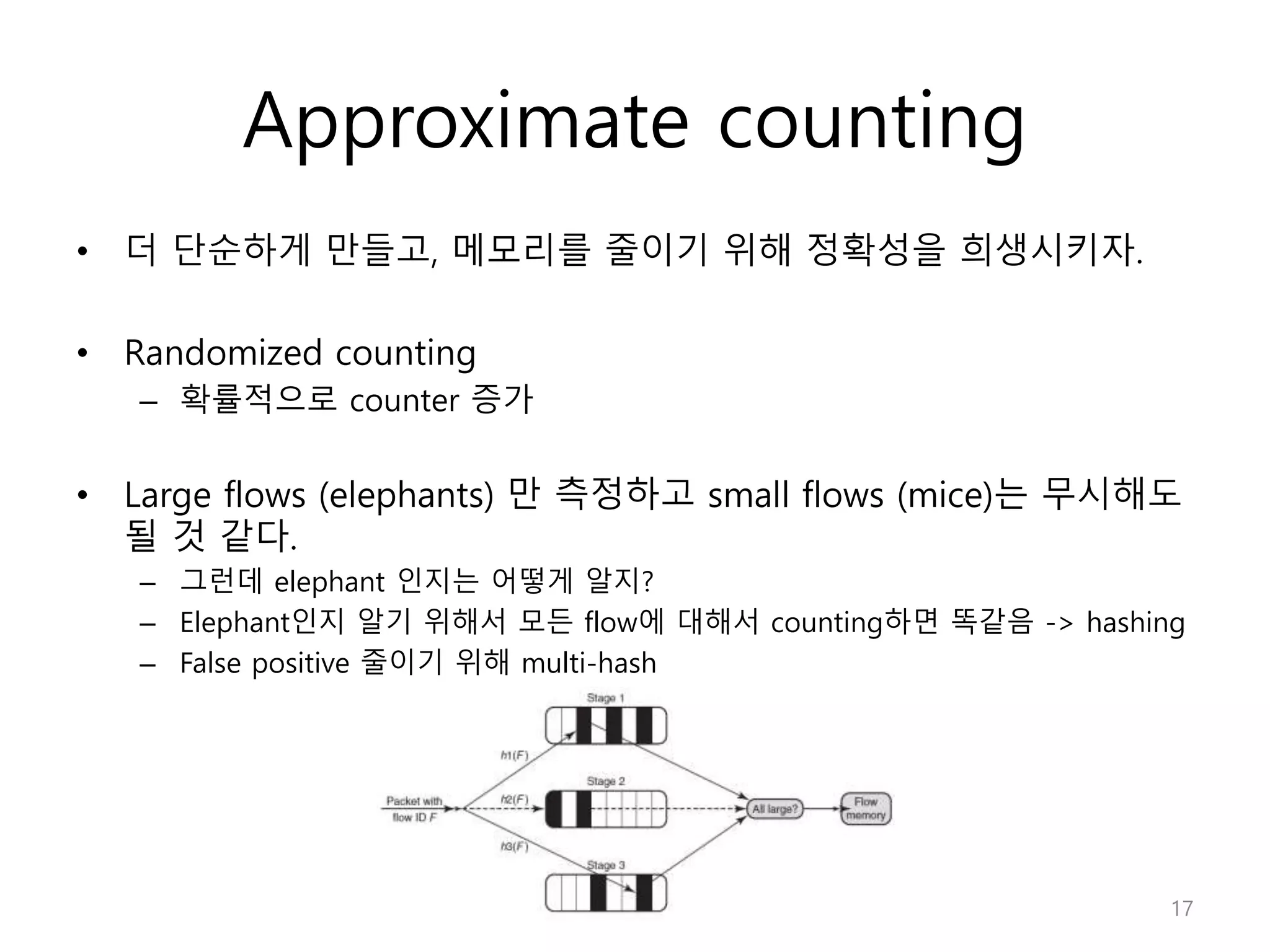
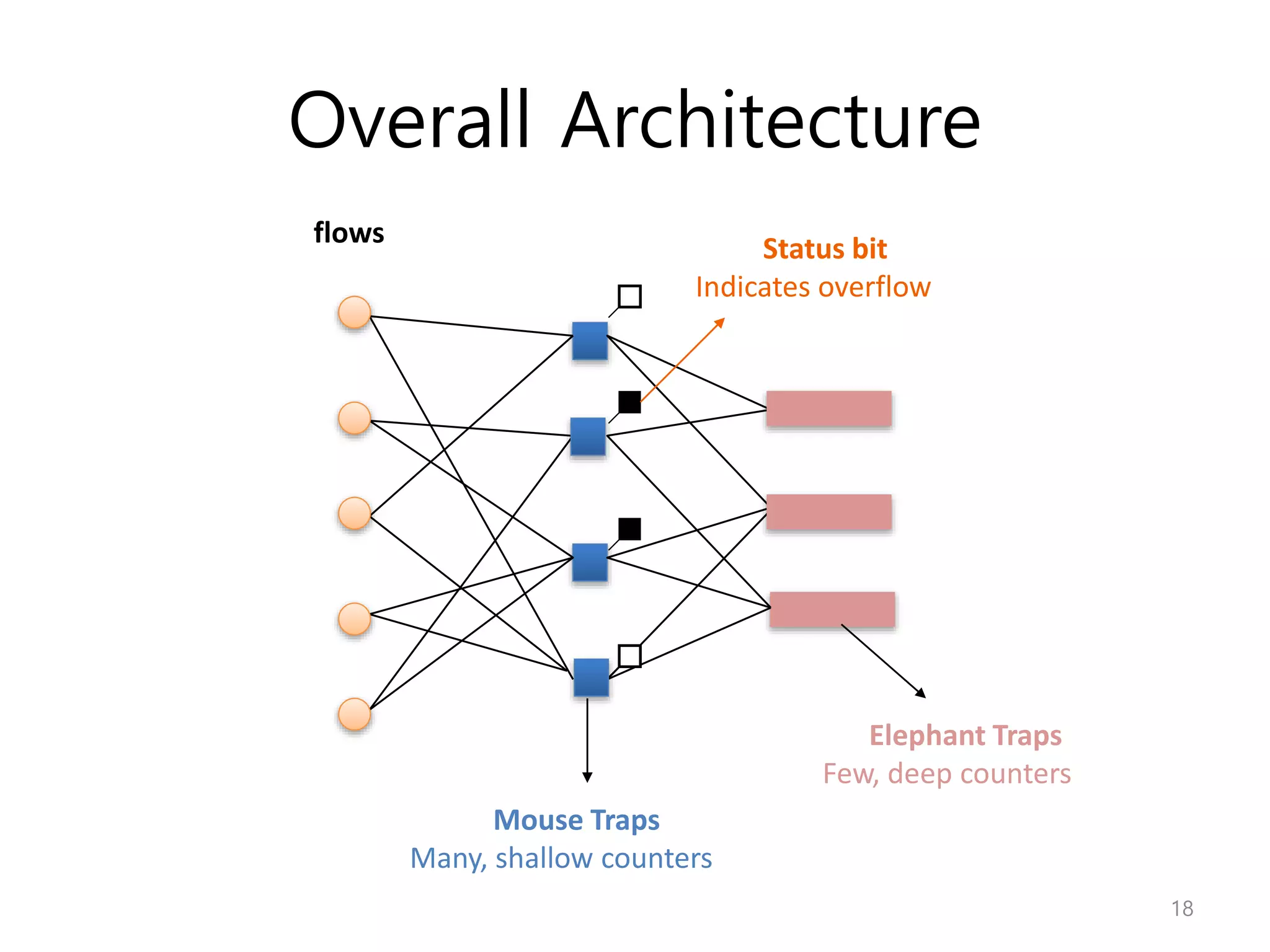
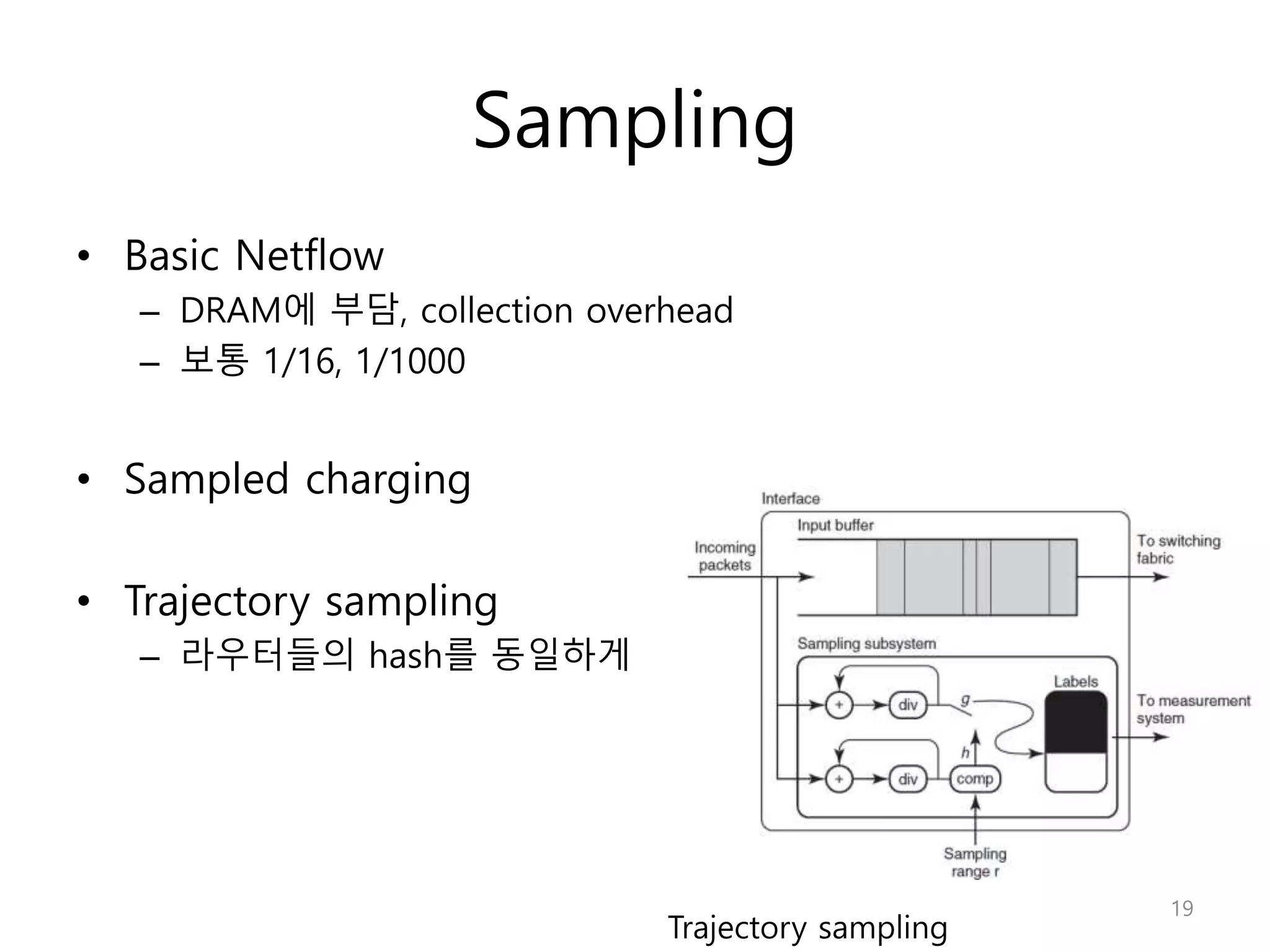
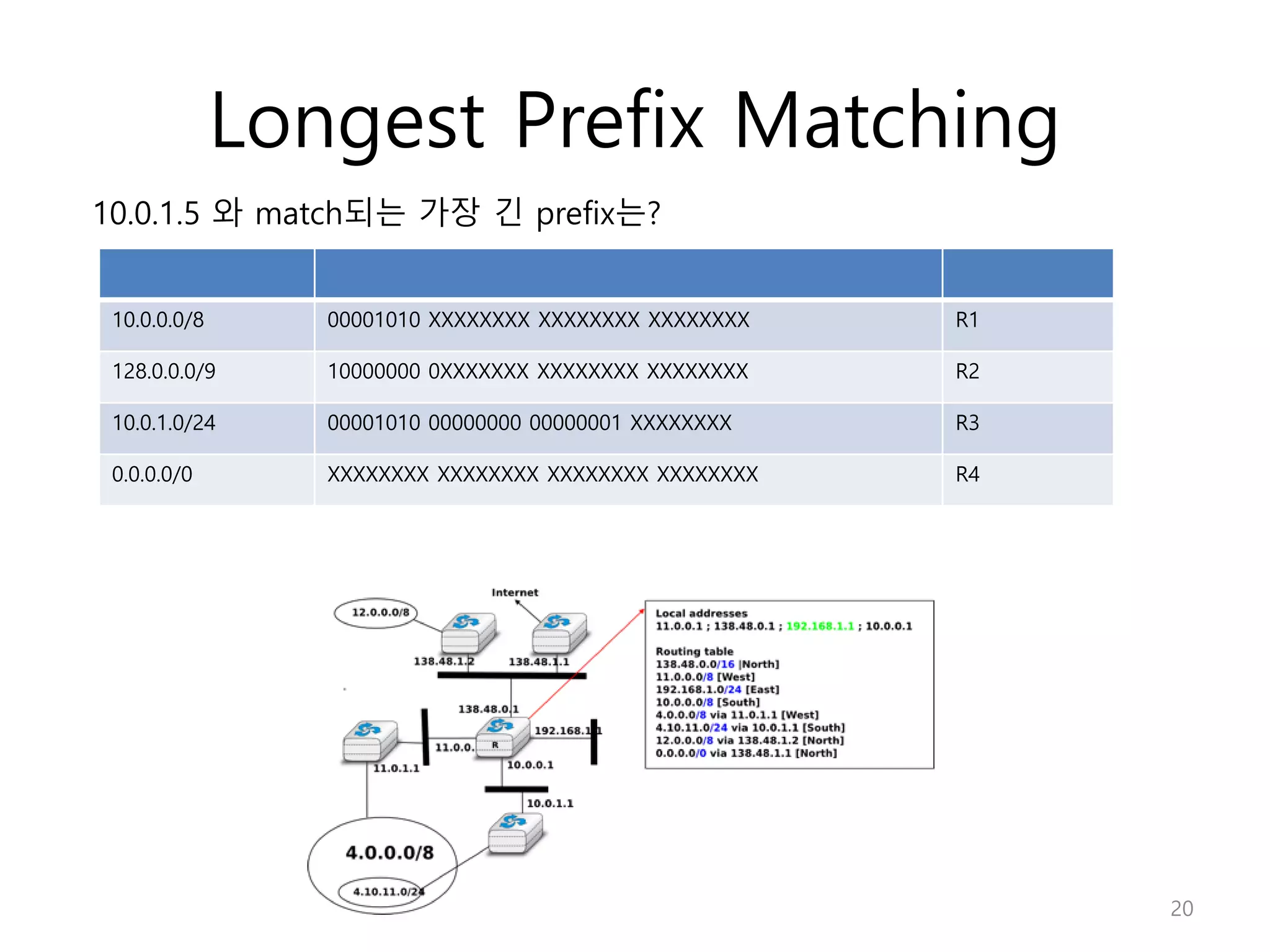
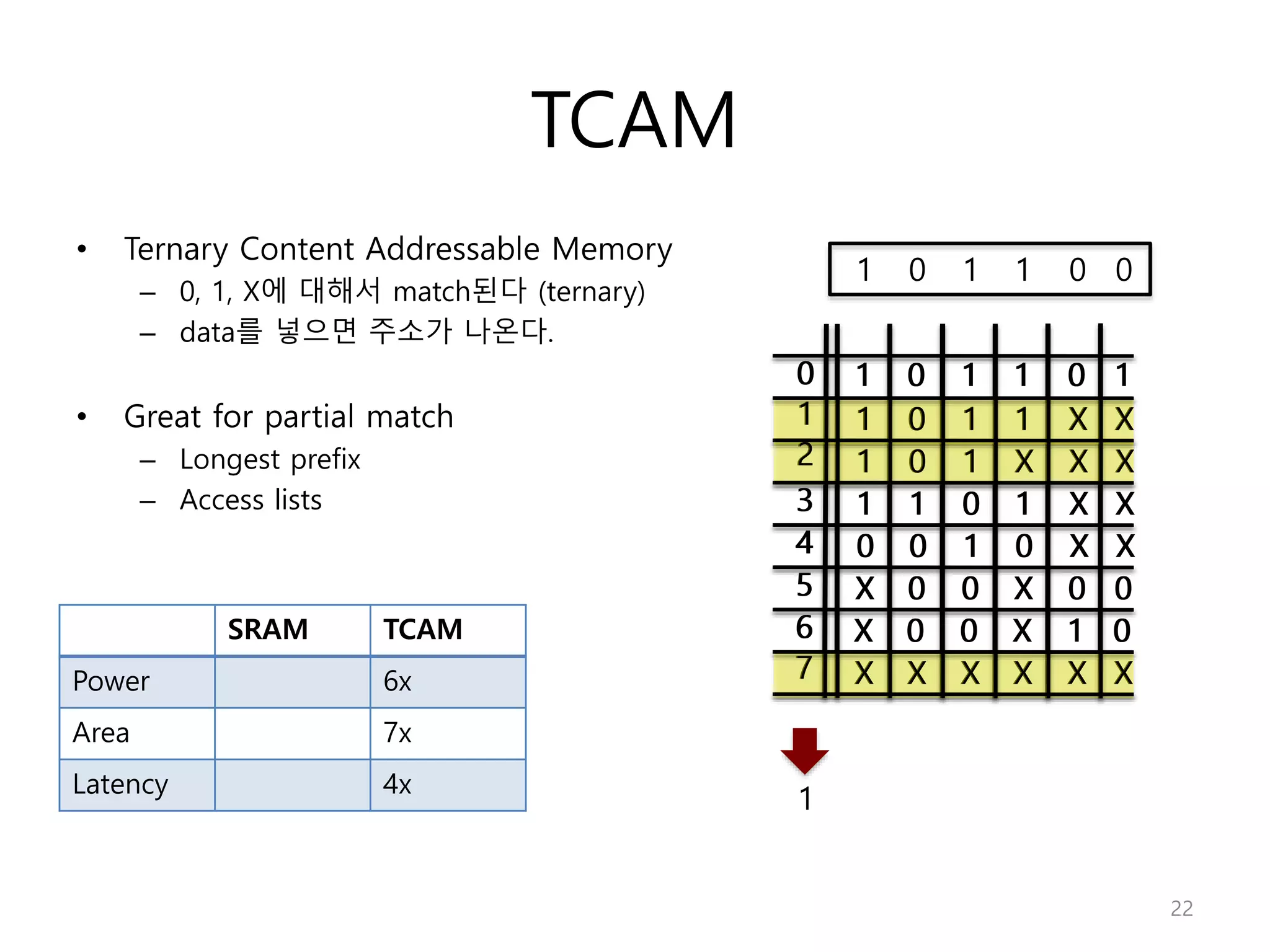
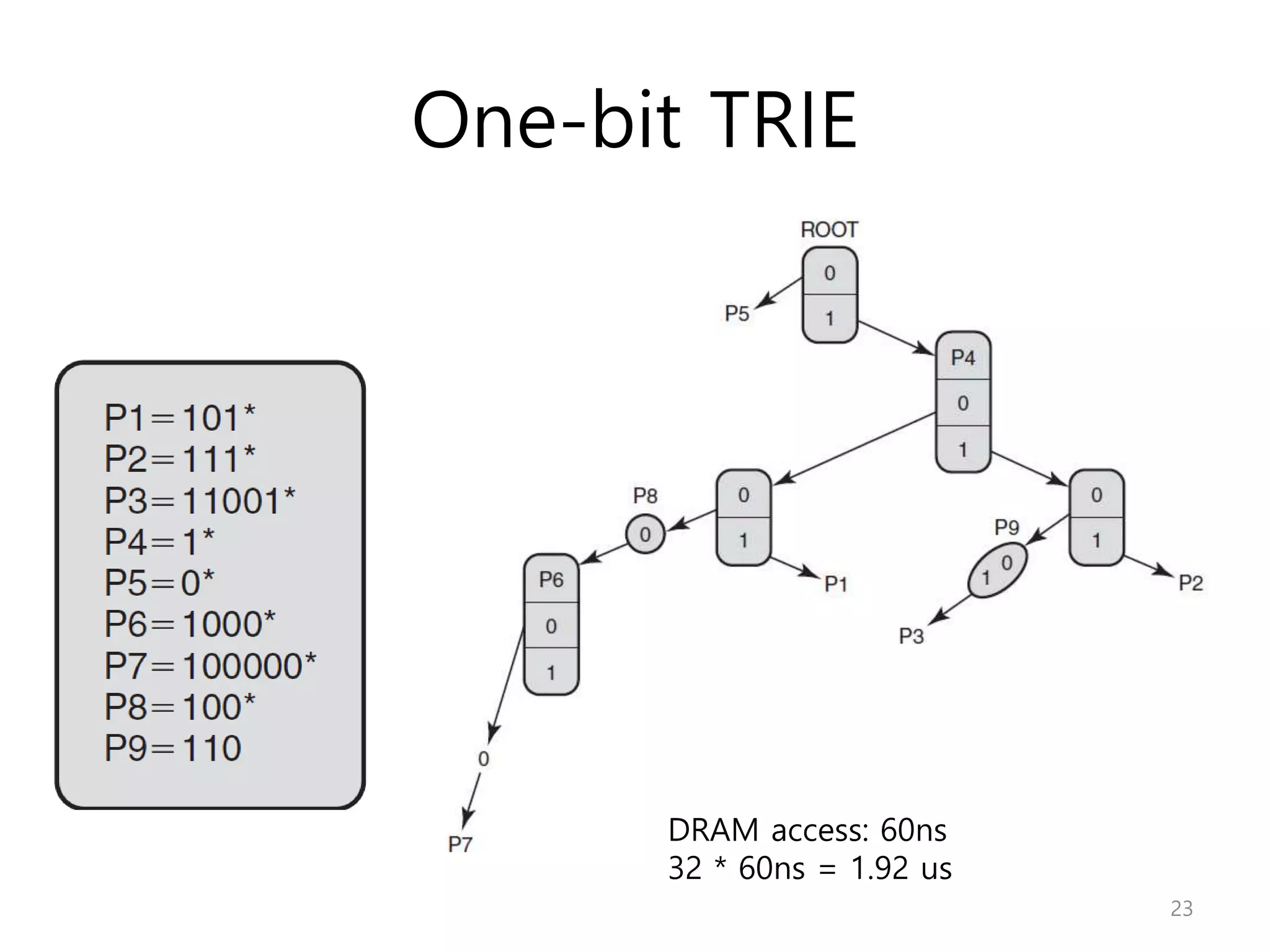
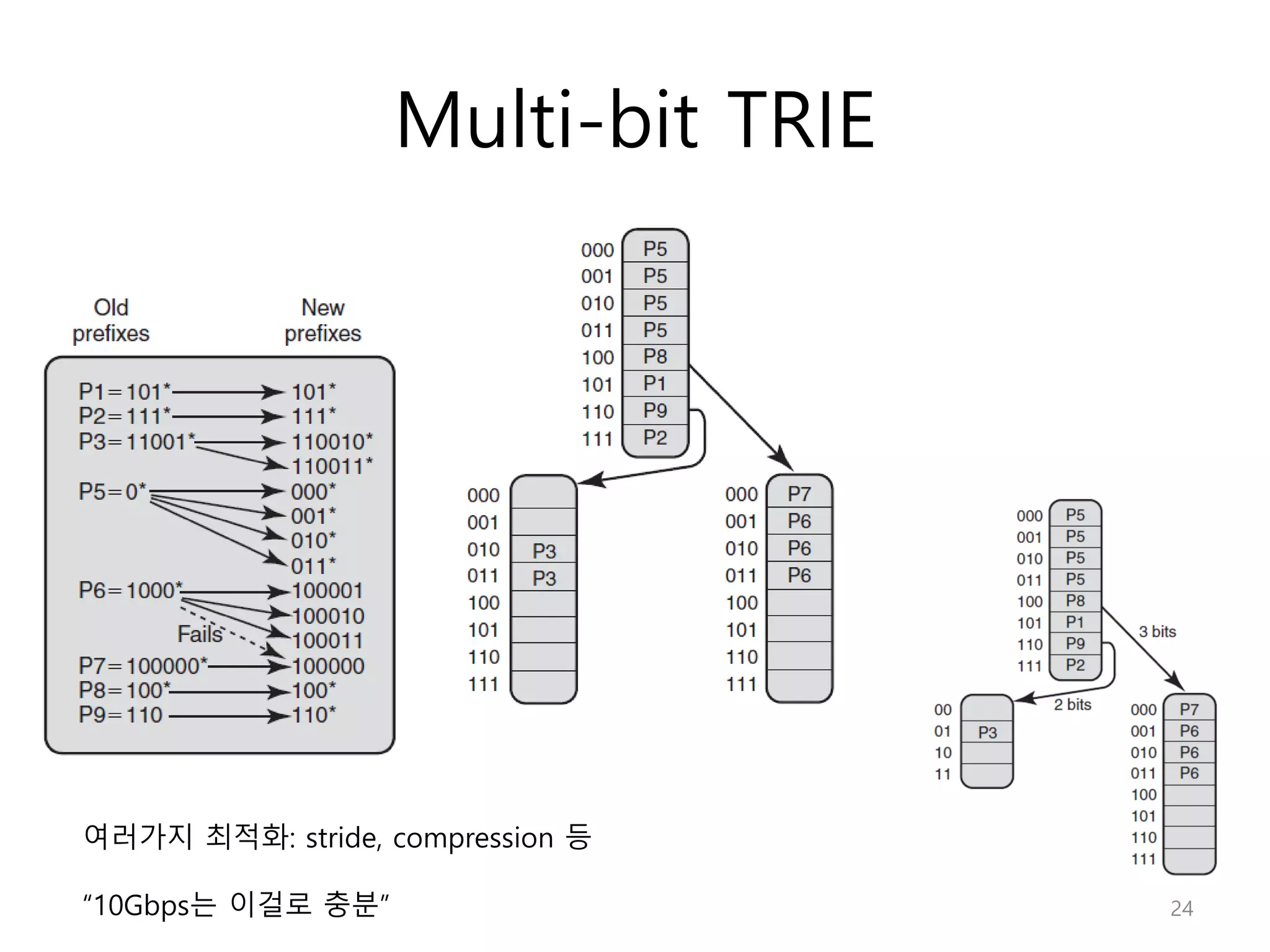
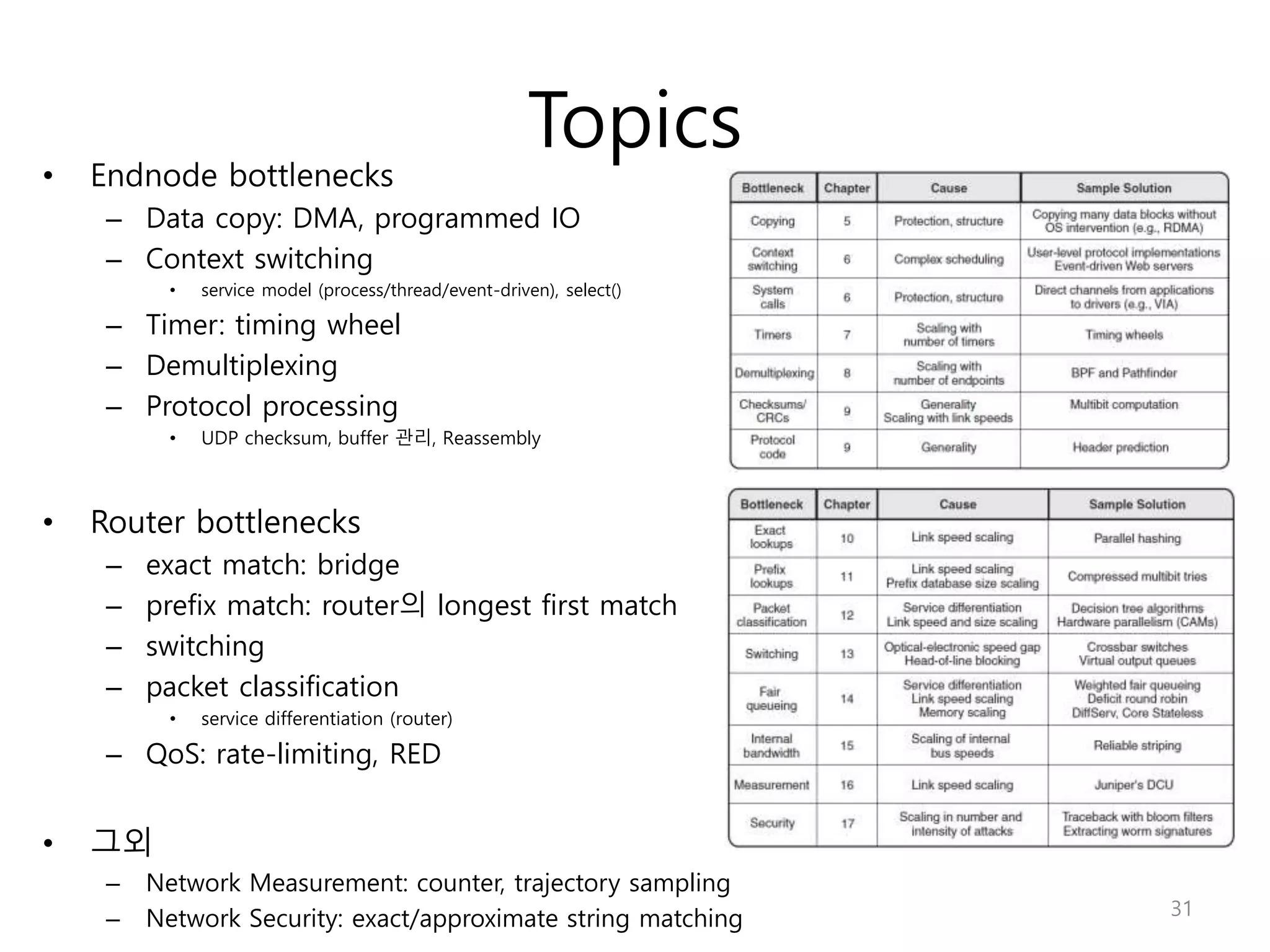
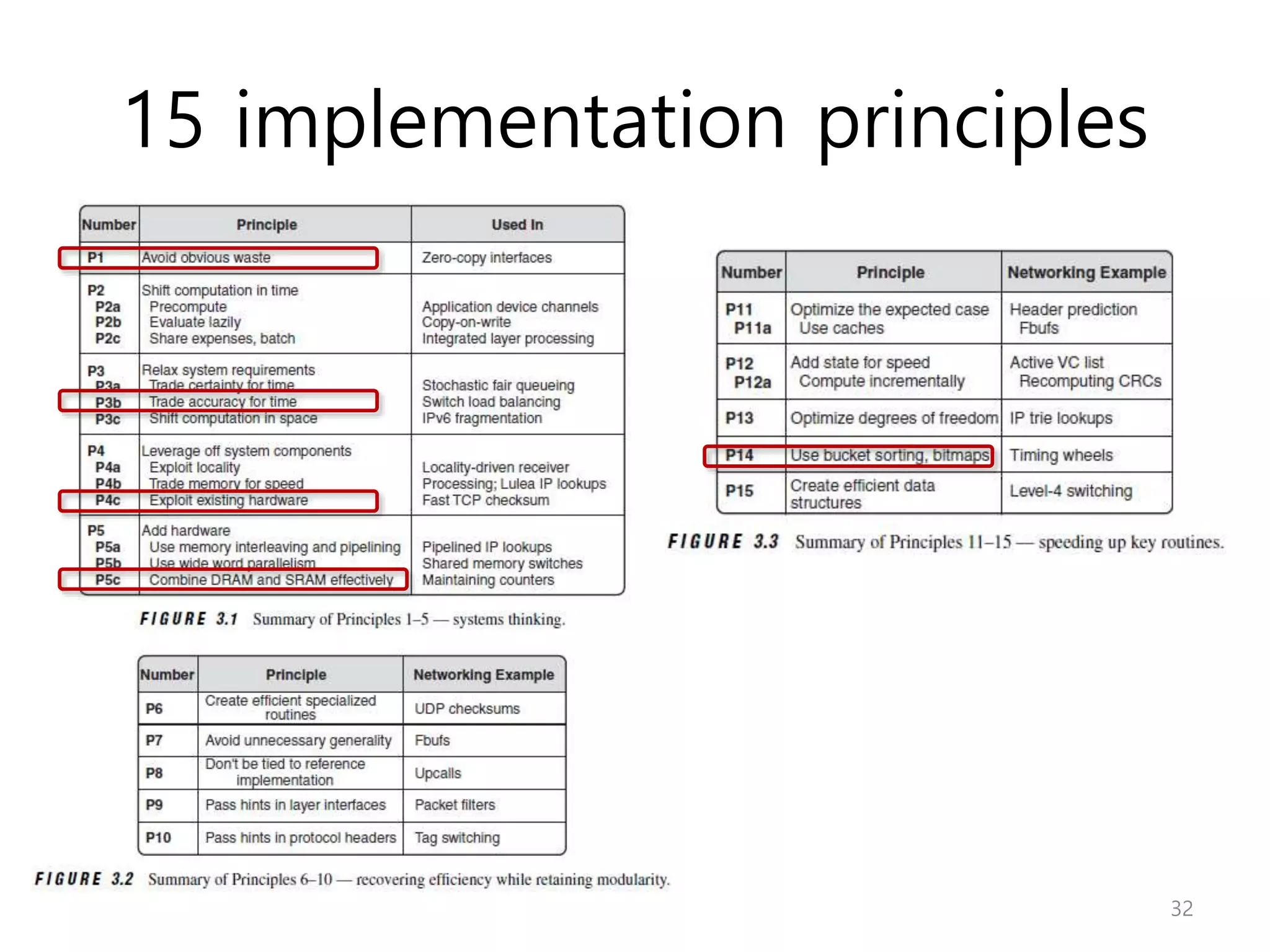
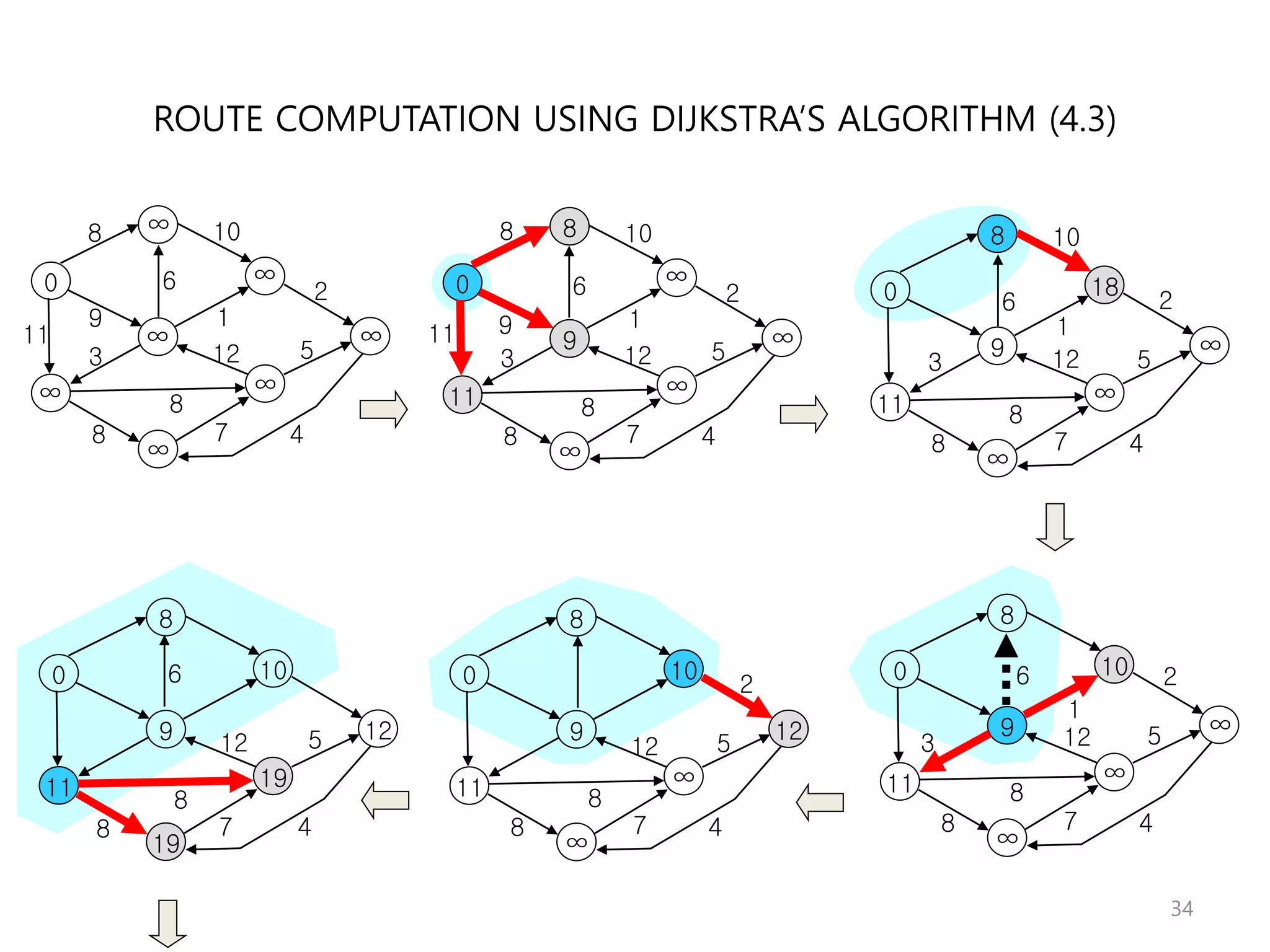
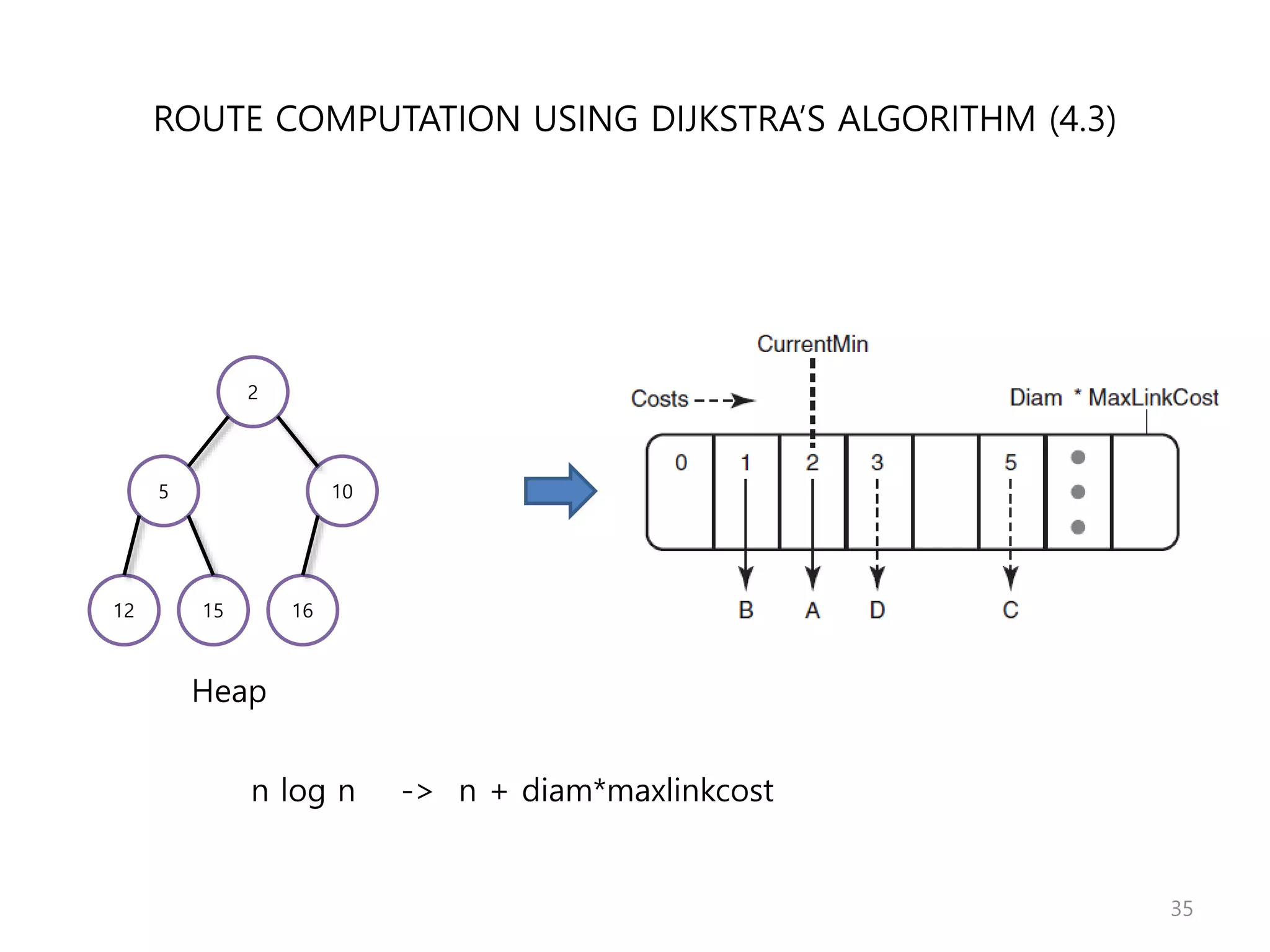
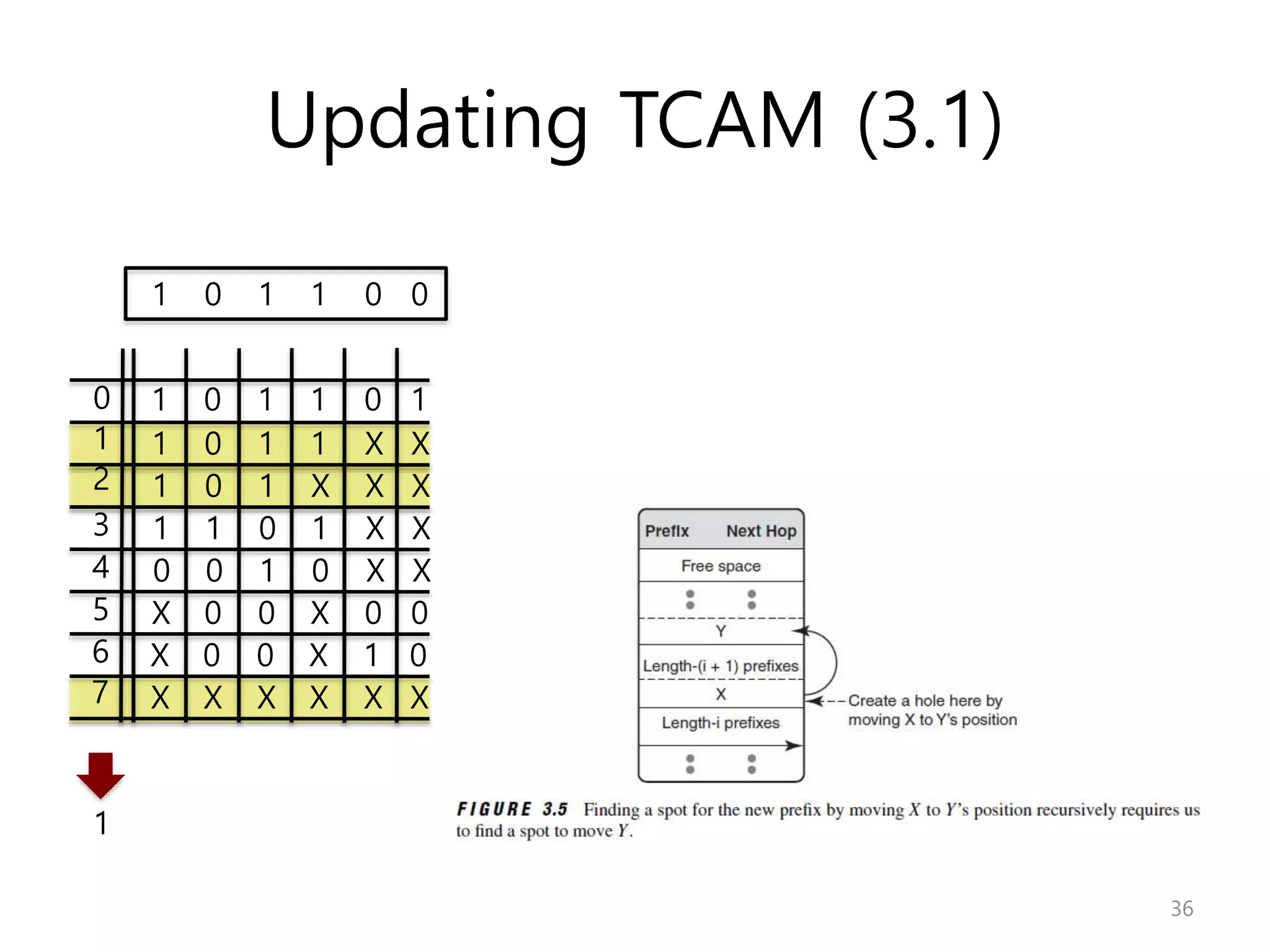
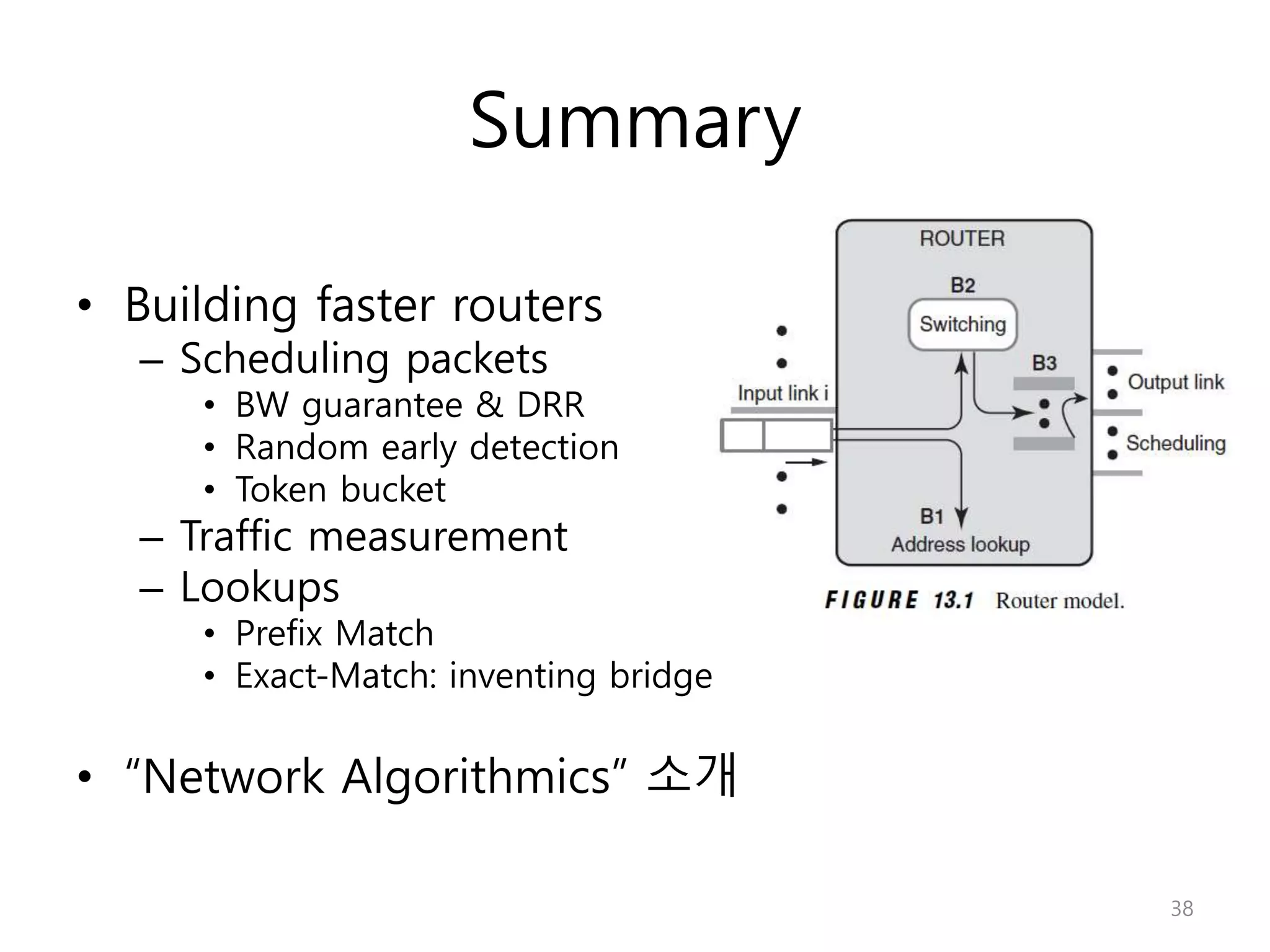
Network Algorithmics focuses on designing fast implementations of network processing tasks using an interdisciplinary systems approach and algorithmic thinking. This includes optimizing common tasks like packet scheduling, traffic measurement, and address lookups in routers. It discusses techniques like deficit round robin for bandwidth guarantees, random early detection for congestion control, and data structures like tries and ternary content-addressable memory for high-speed prefix and exact matching. The document also introduces the concept of "network algorithmics" for using algorithms and data structures to solve problems in computer networking.