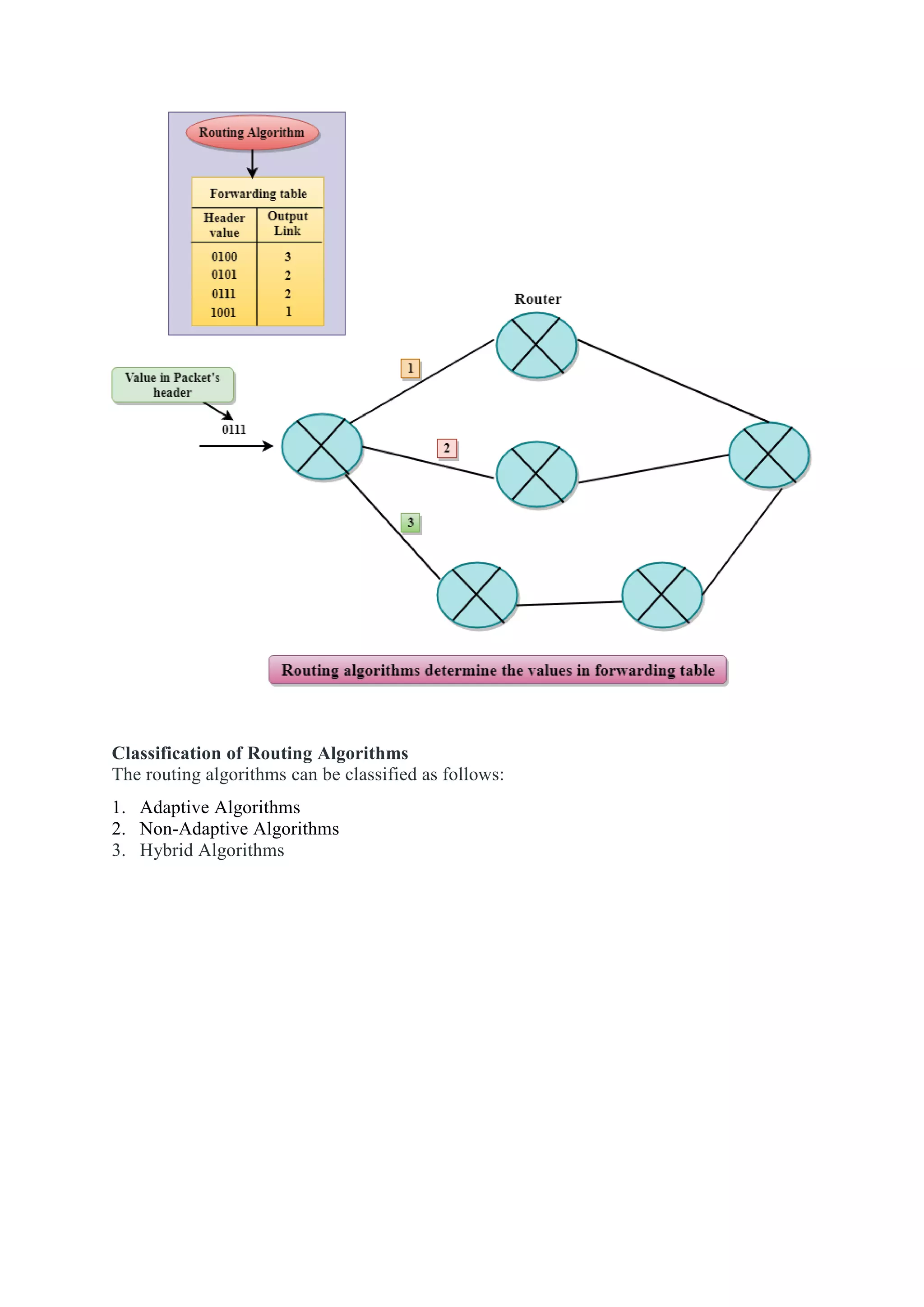
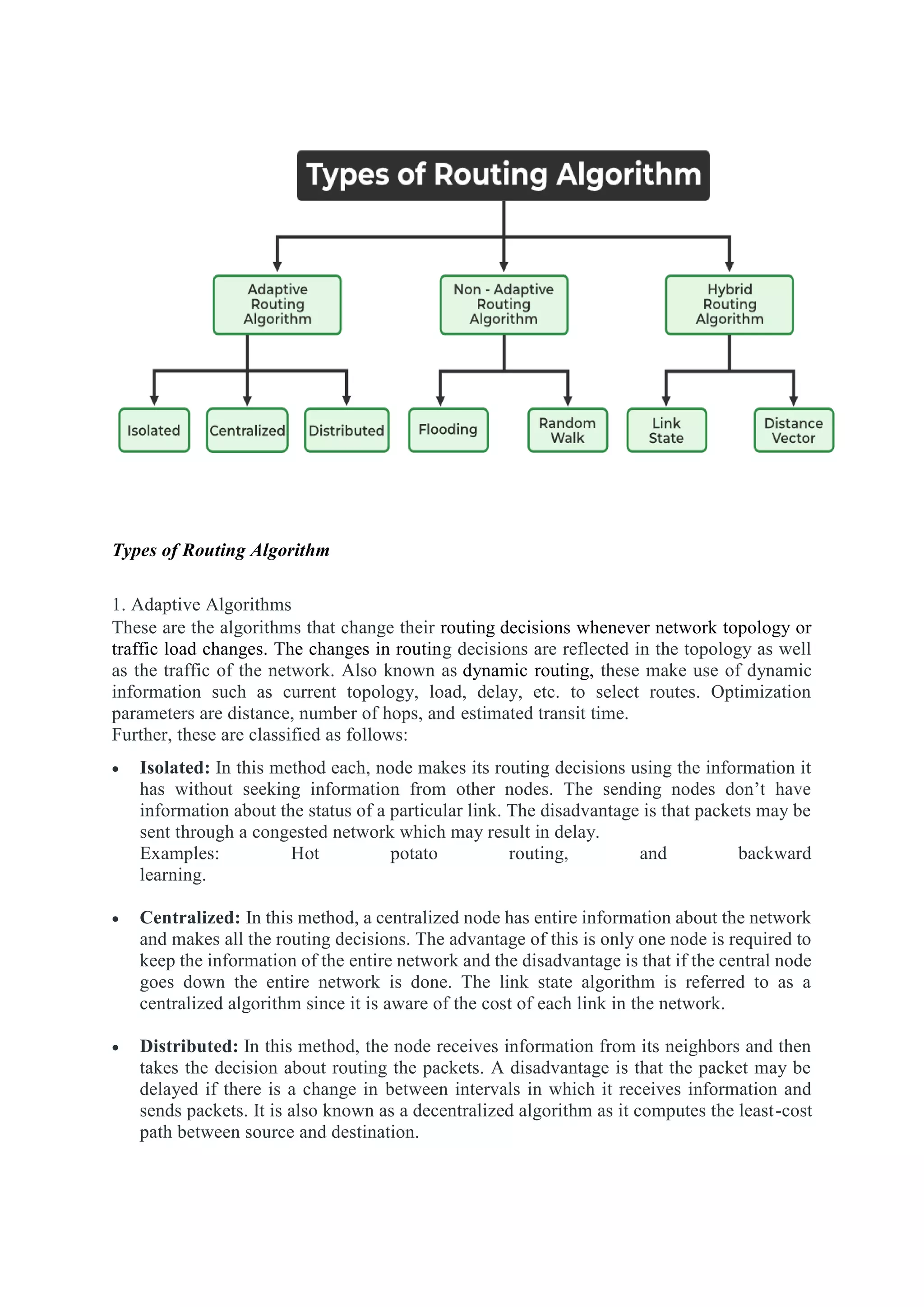
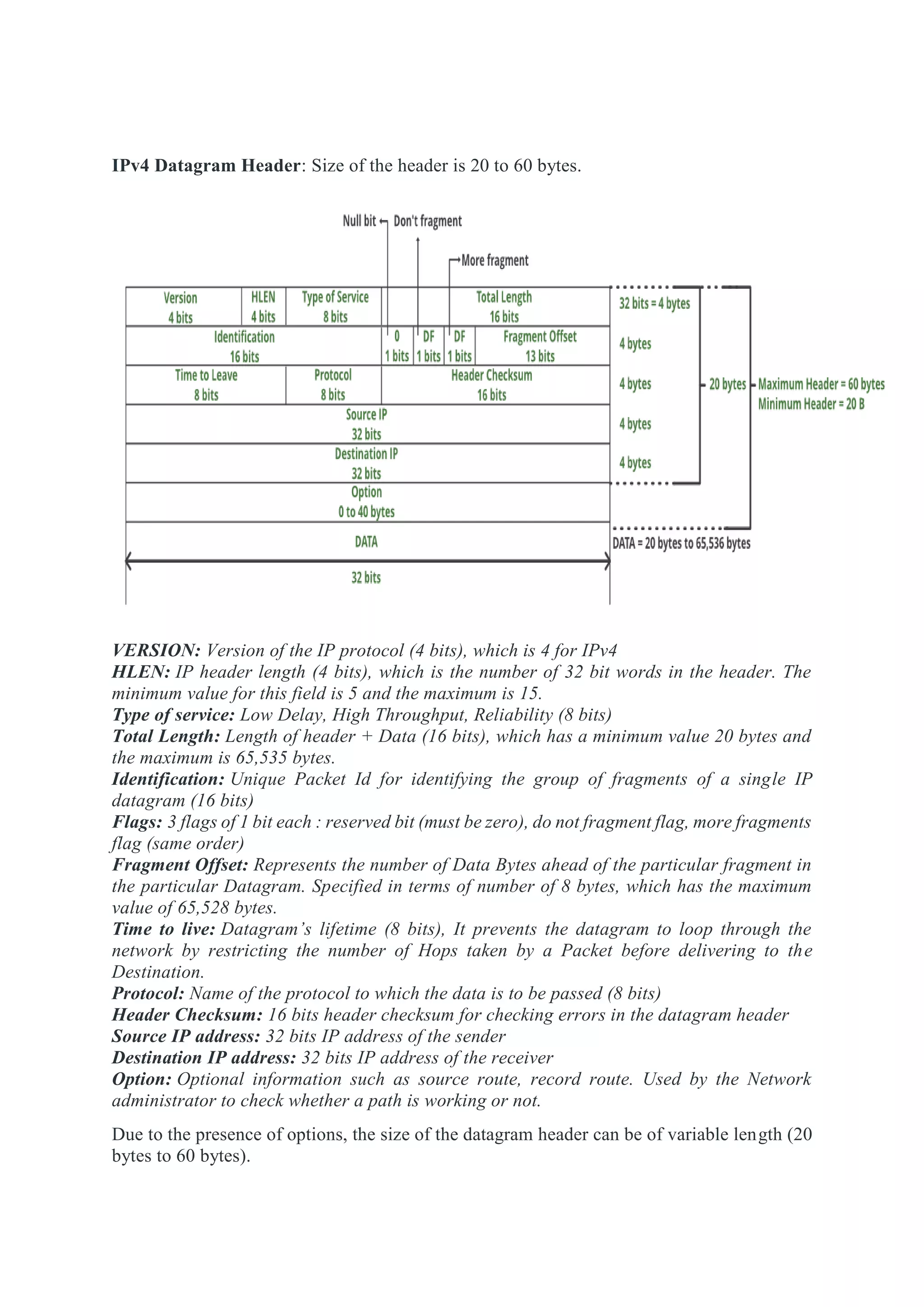
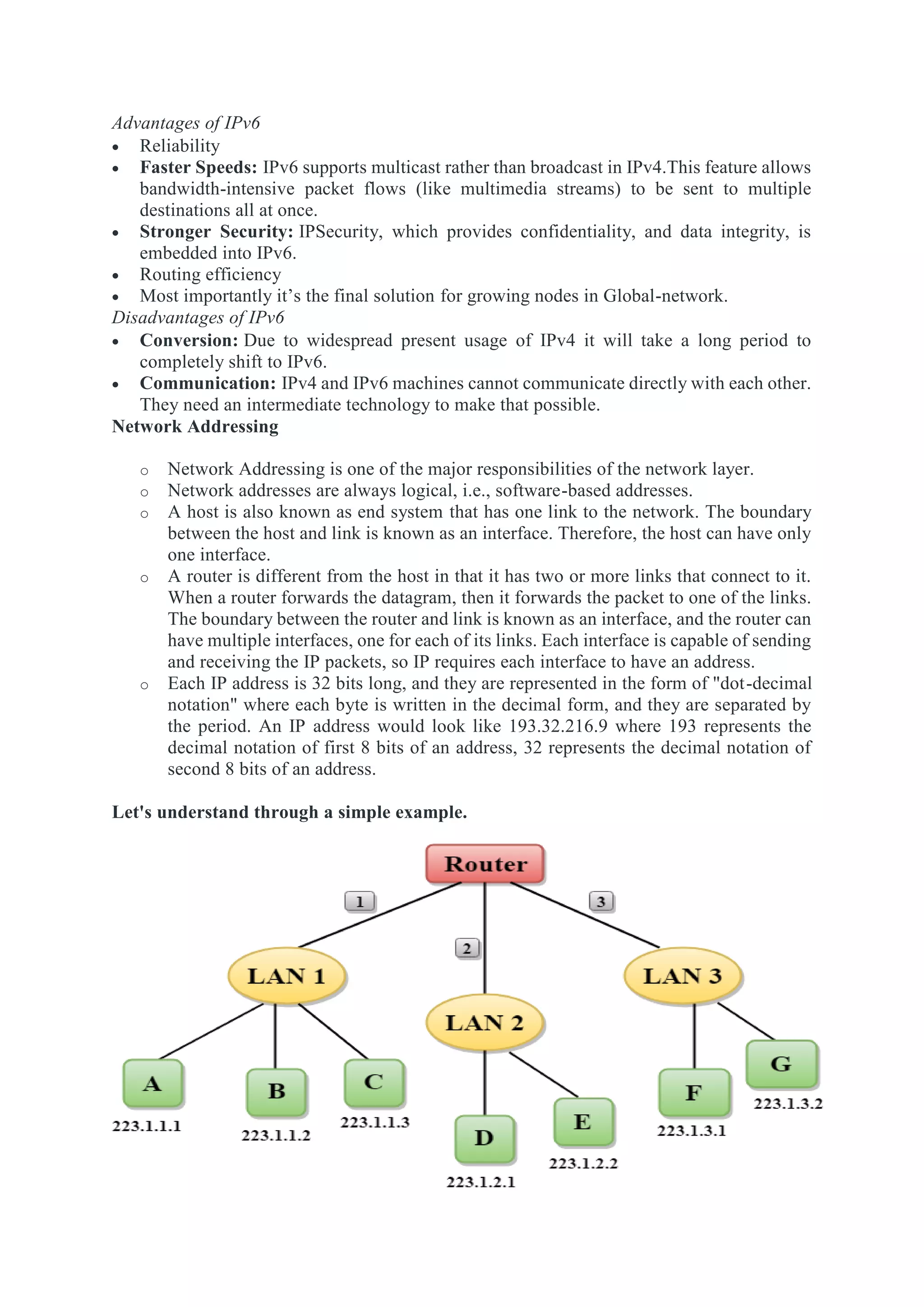
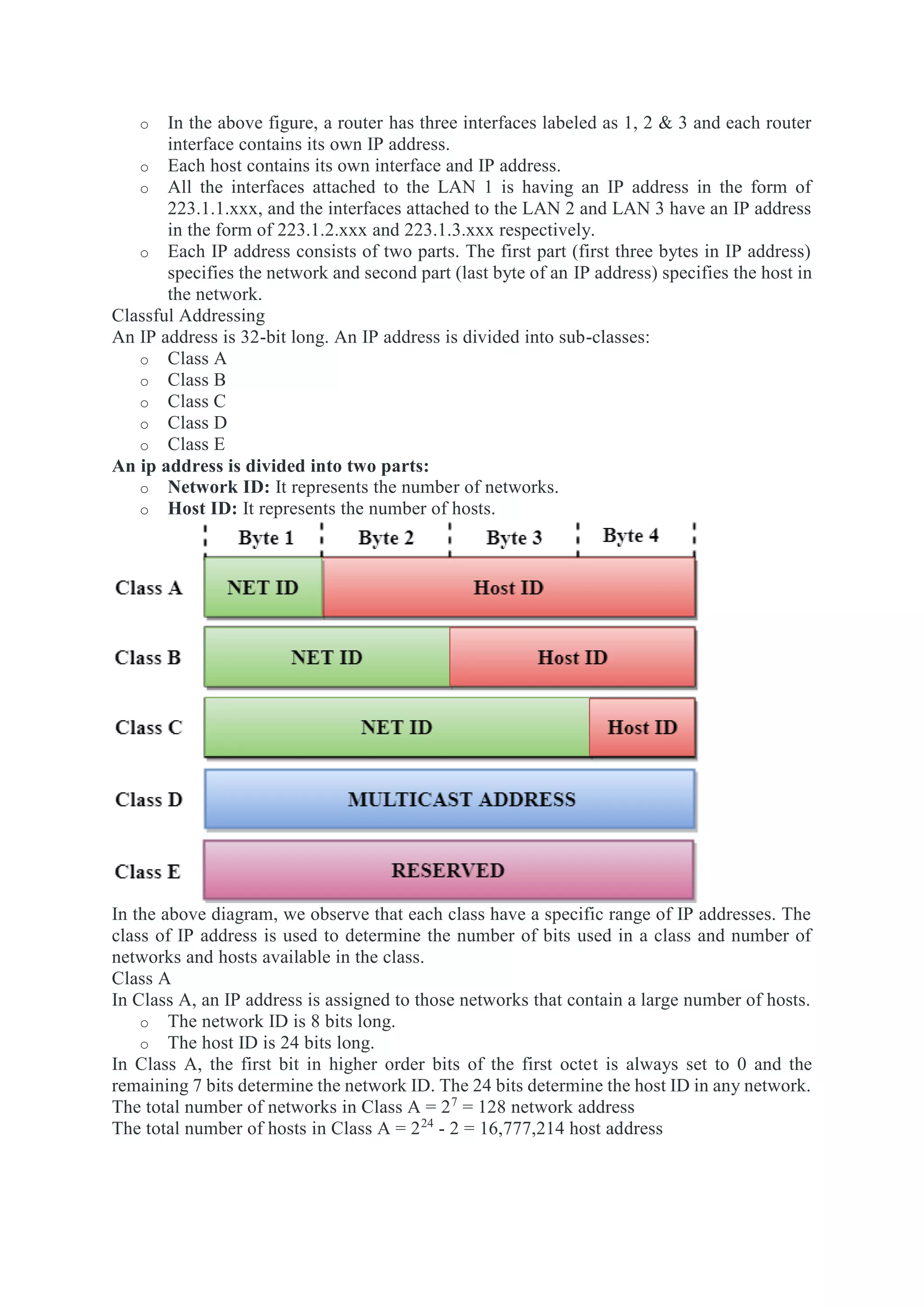
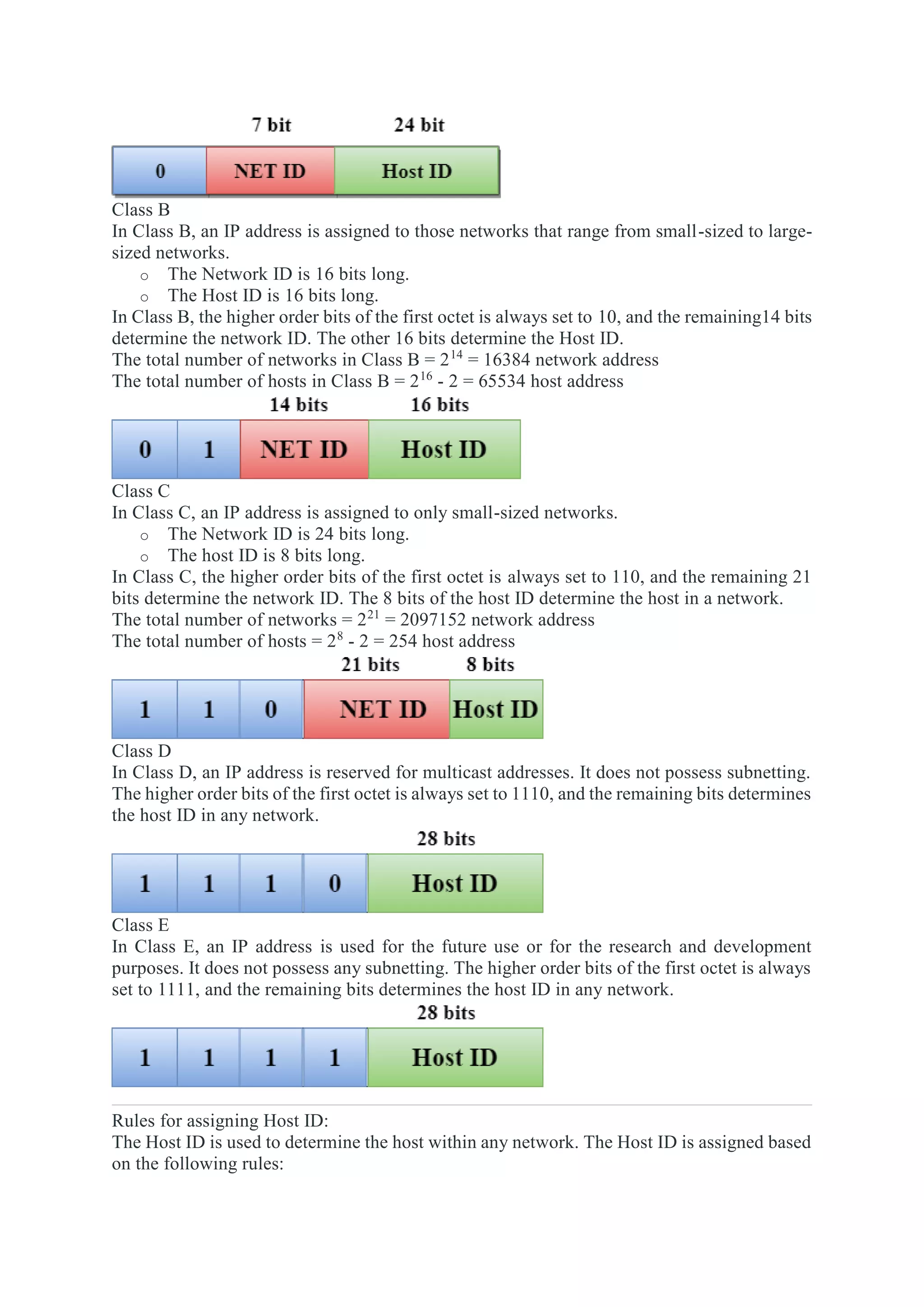
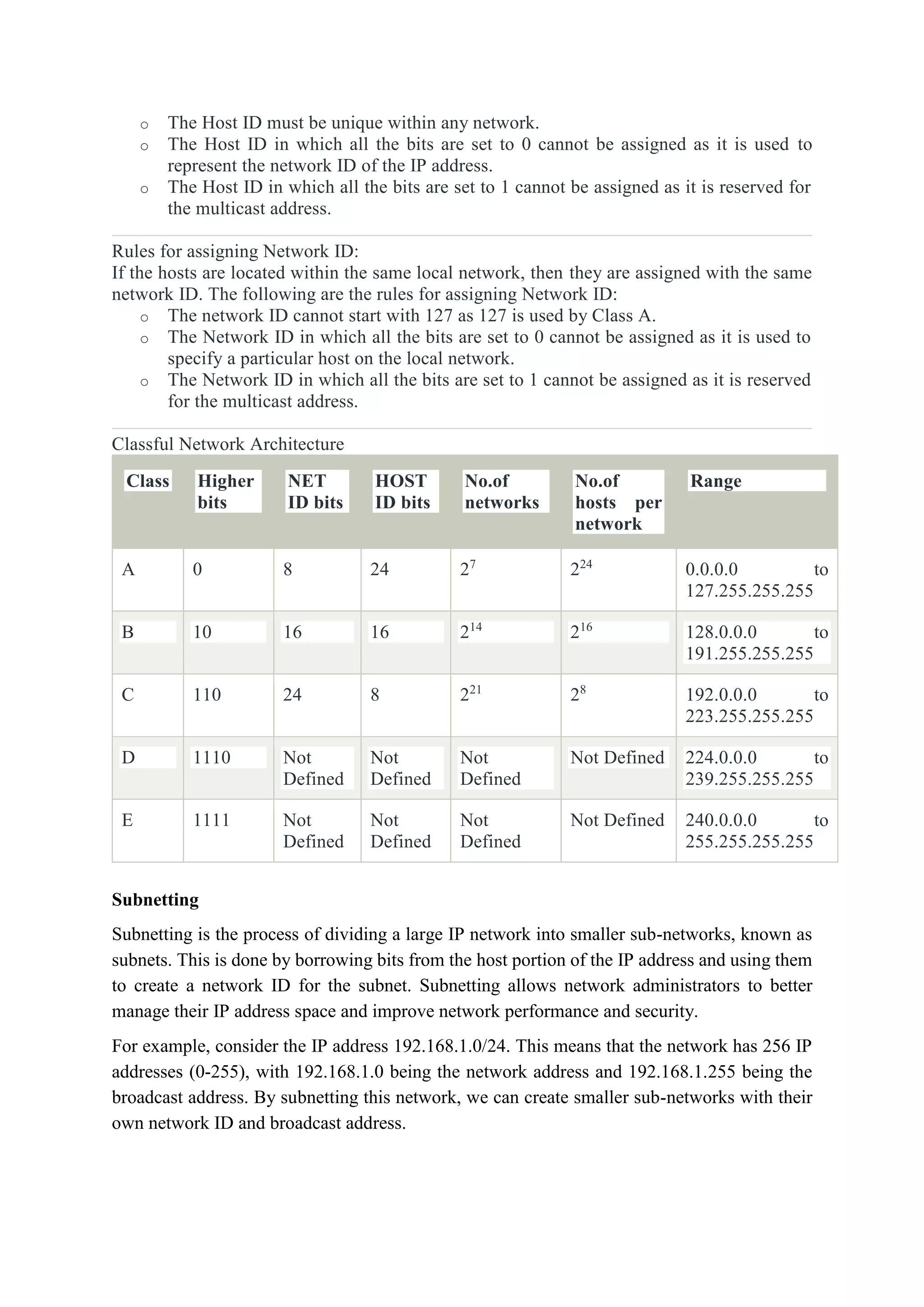
The network layer is responsible for end-to-end packet delivery across multiple hops between source and destination devices. It must choose appropriate paths through the network topology to avoid overloading some links while leaving others idle. The network layer deals with issues like routing, logical addressing, and internetworking between different network types. The main functions of the network layer are routing, logical addressing, internetworking, and fragmentation.