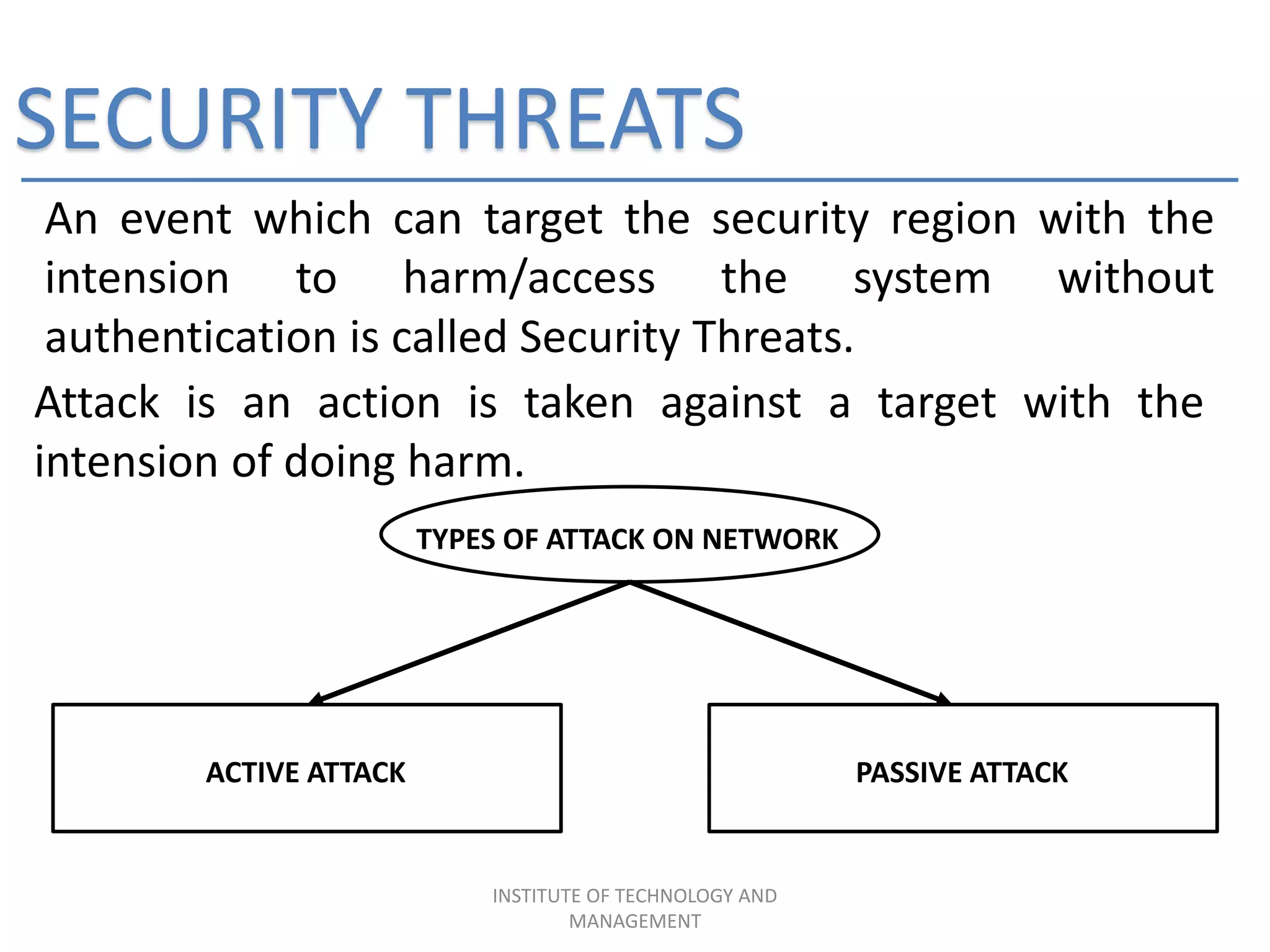
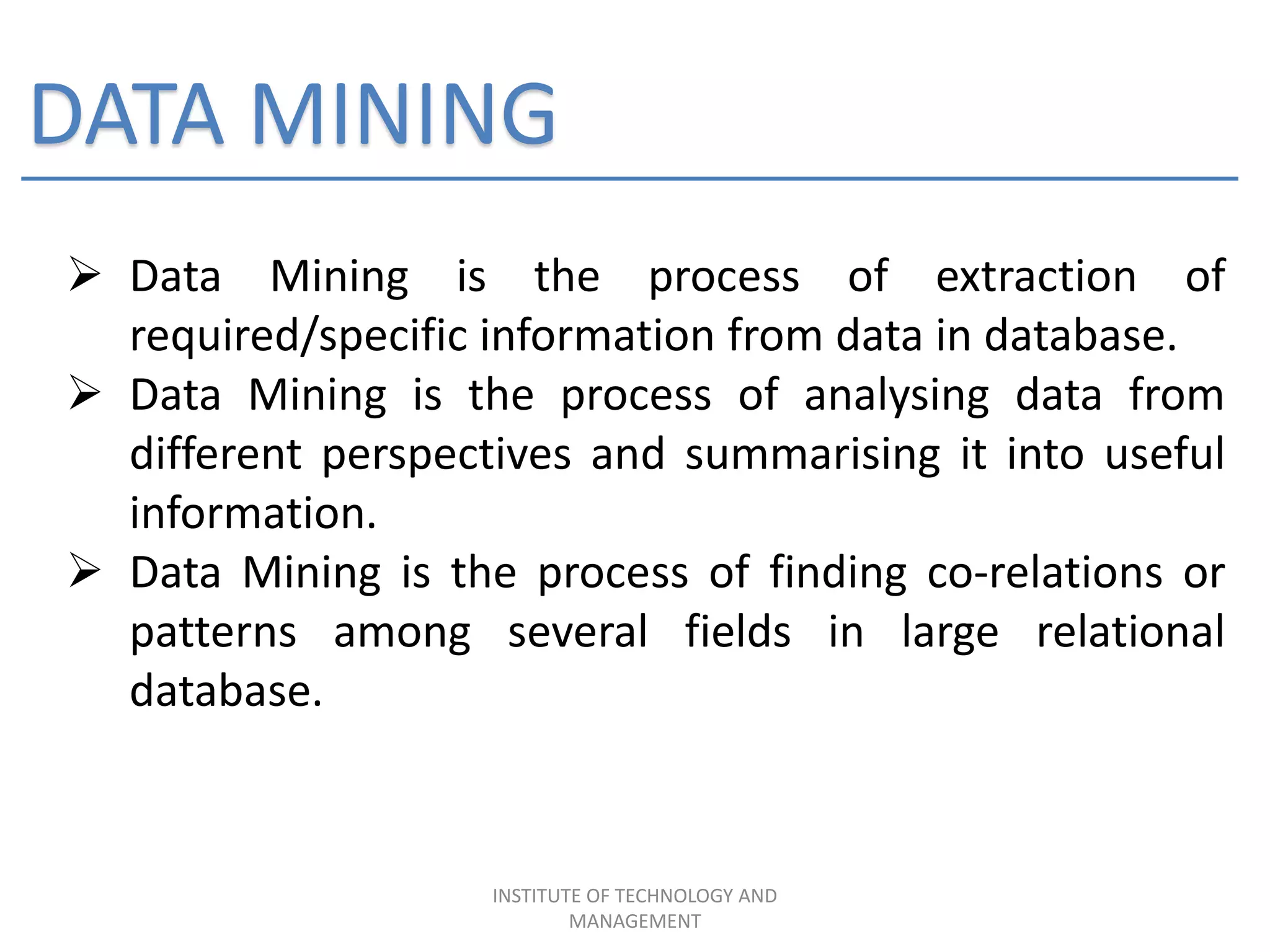
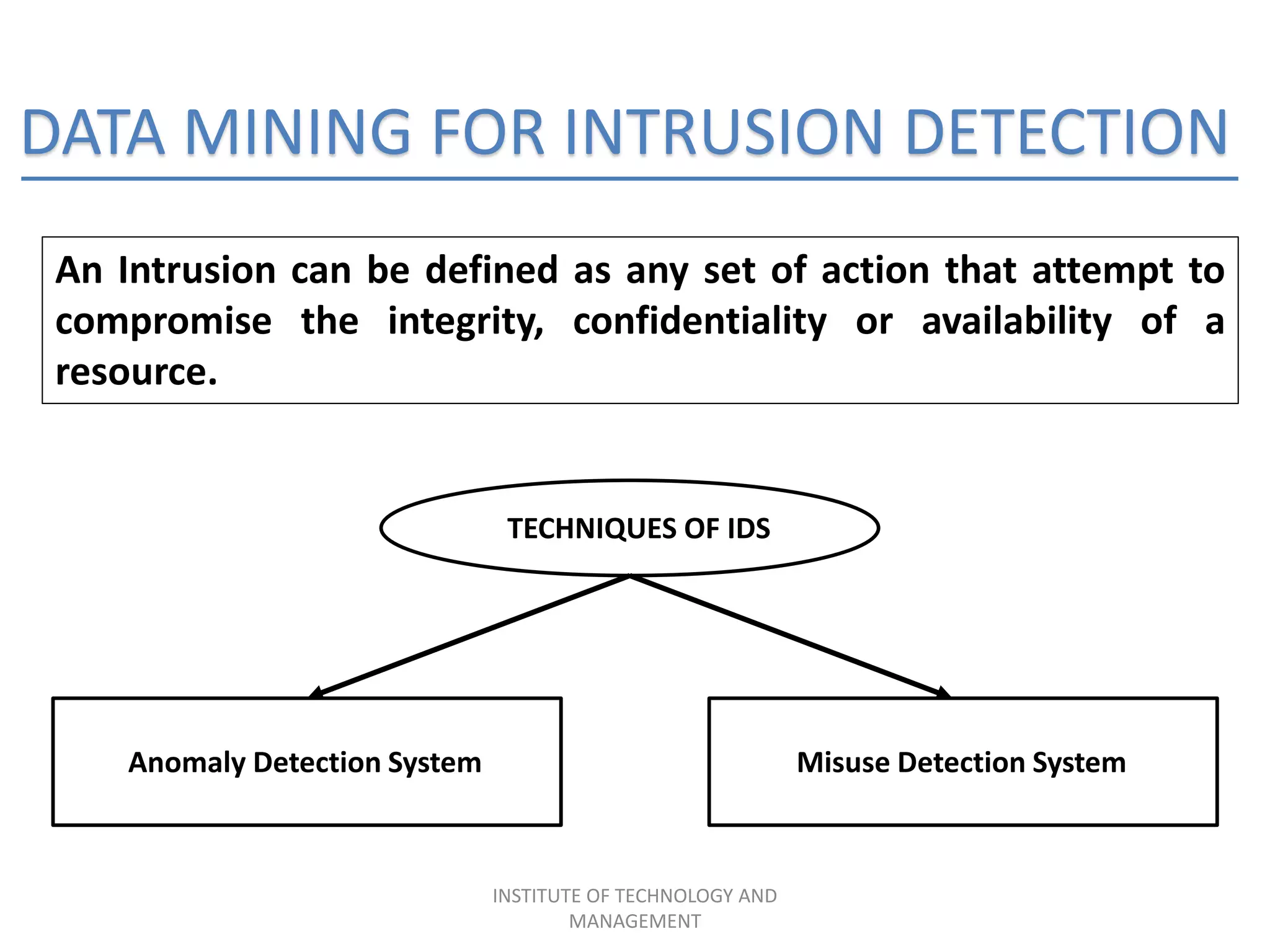
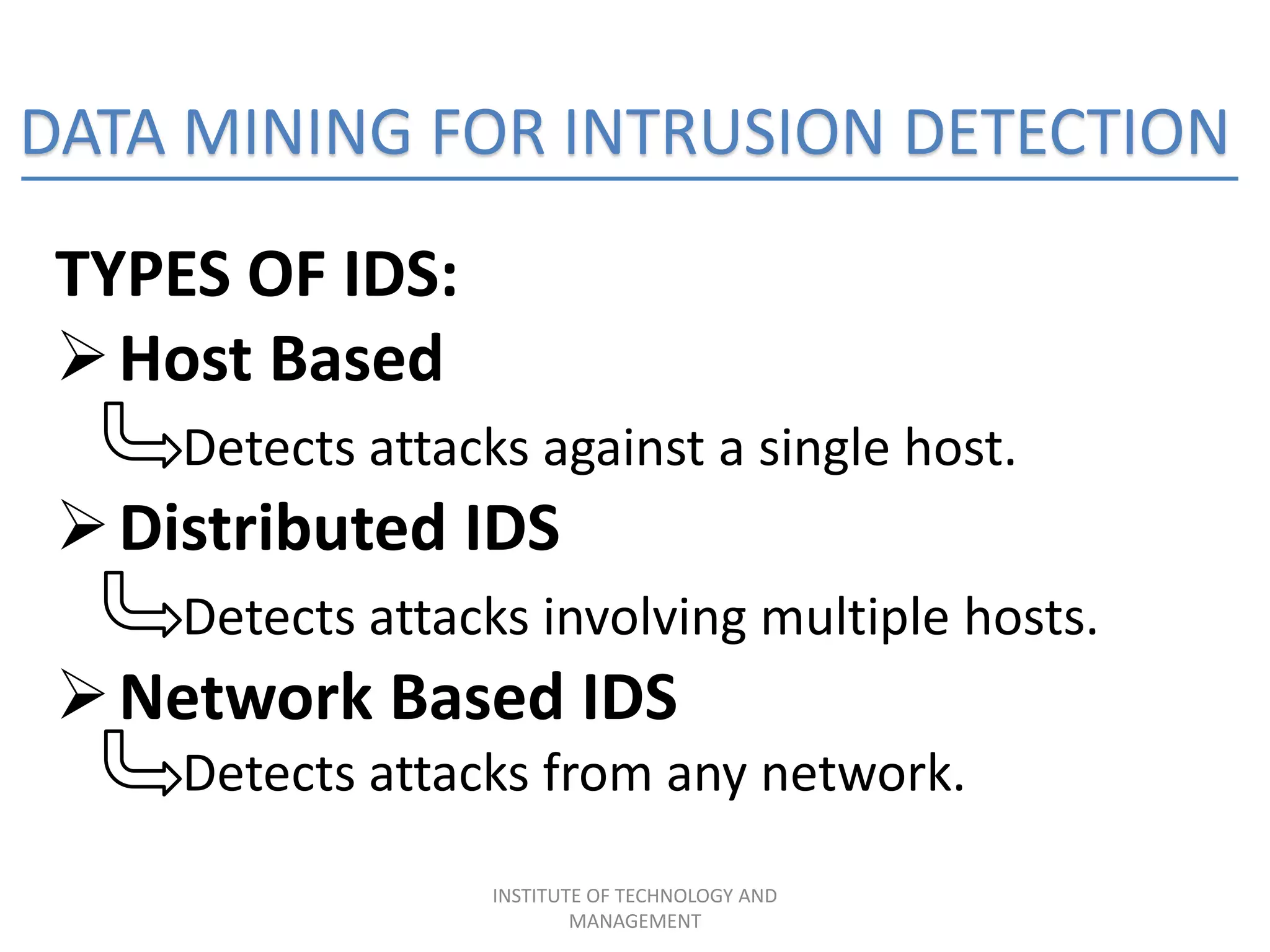
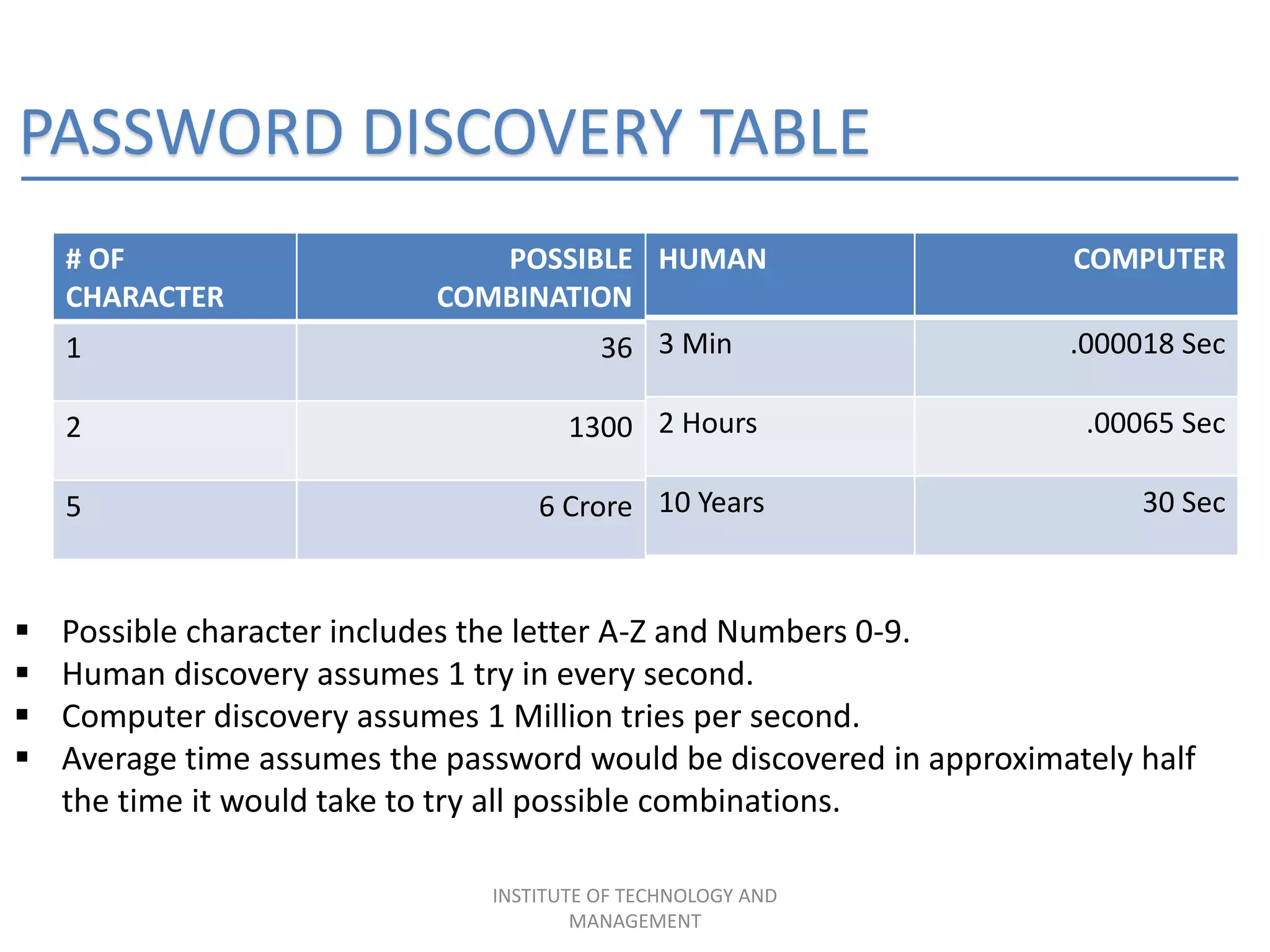
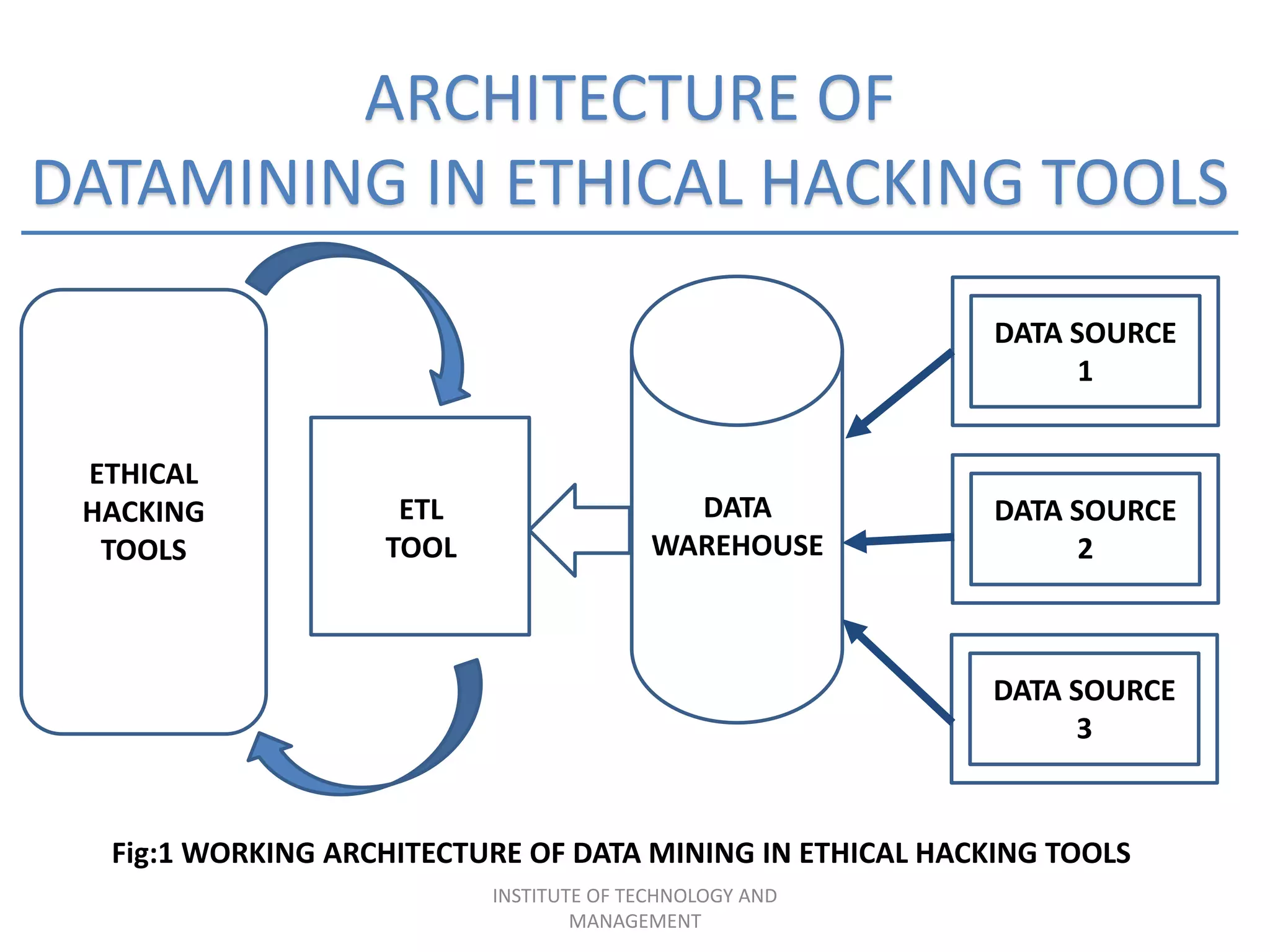
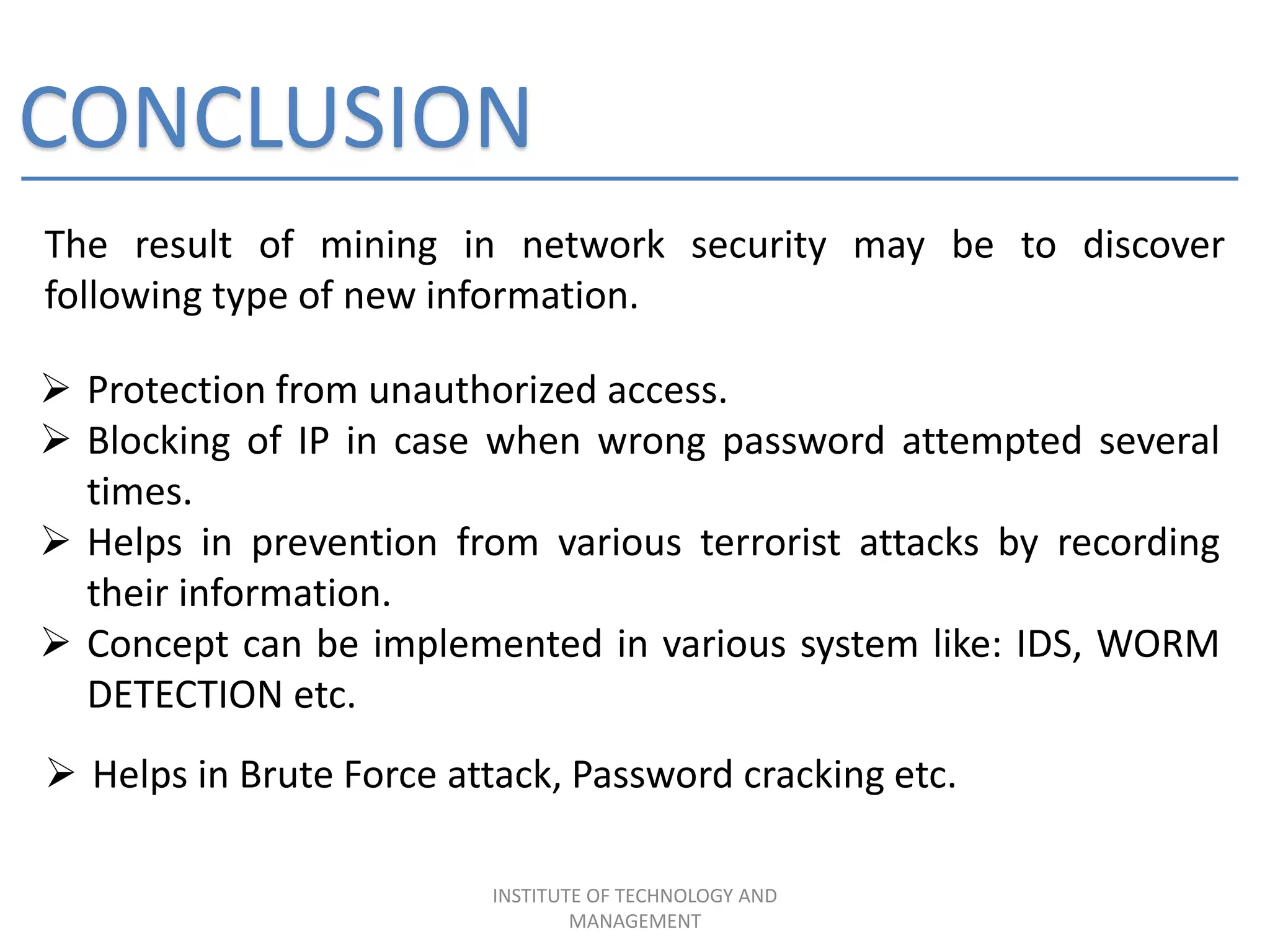
The document discusses the integration of data mining concepts with network security to combat various security threats, including active and passive attacks. It outlines the processes of data mining, its application in intrusion detection, and the architecture of ethical hacking tools. The conclusion emphasizes the benefits of this integration, including enhanced security measures against unauthorized access and potential terrorist attacks.