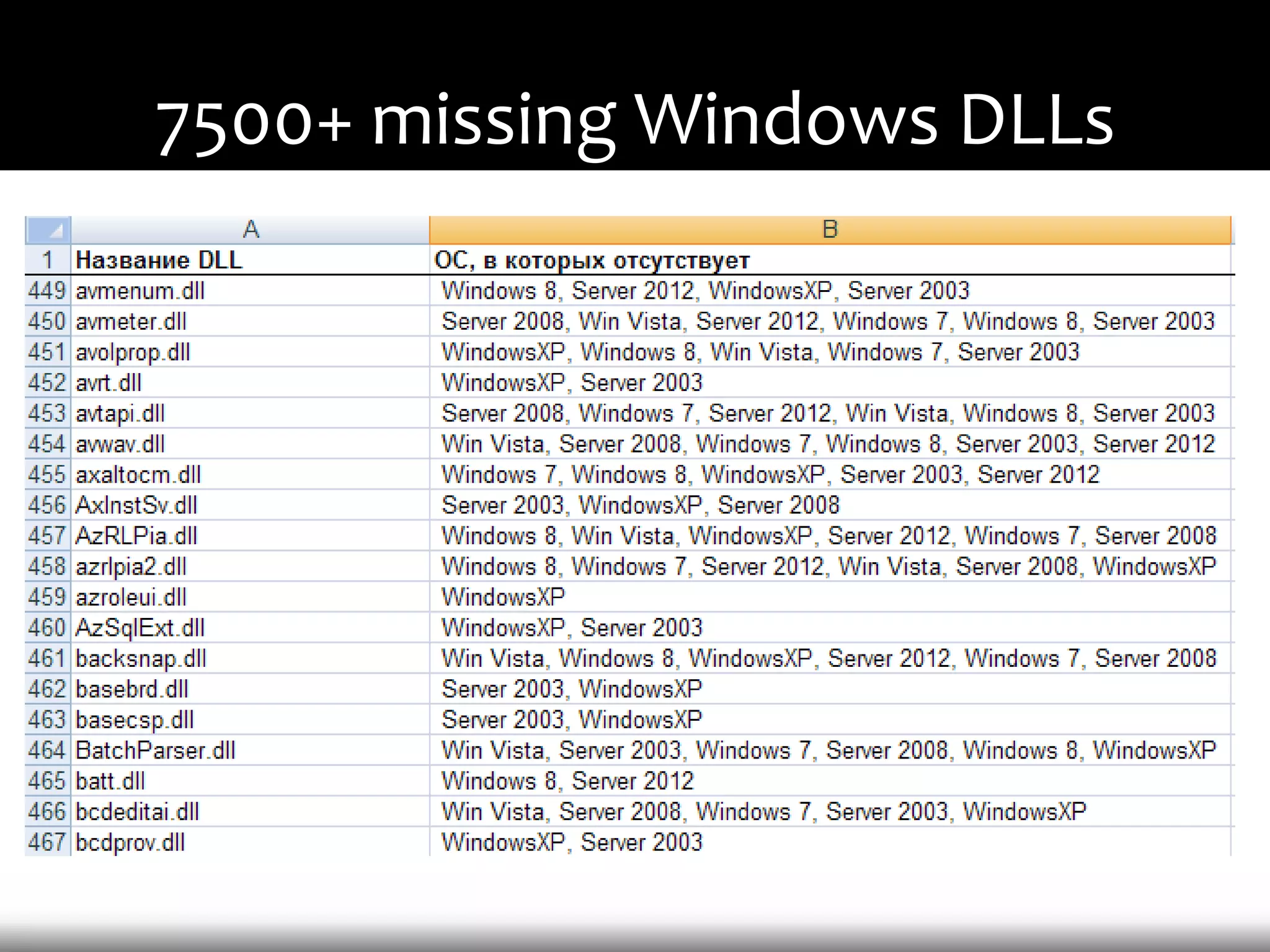
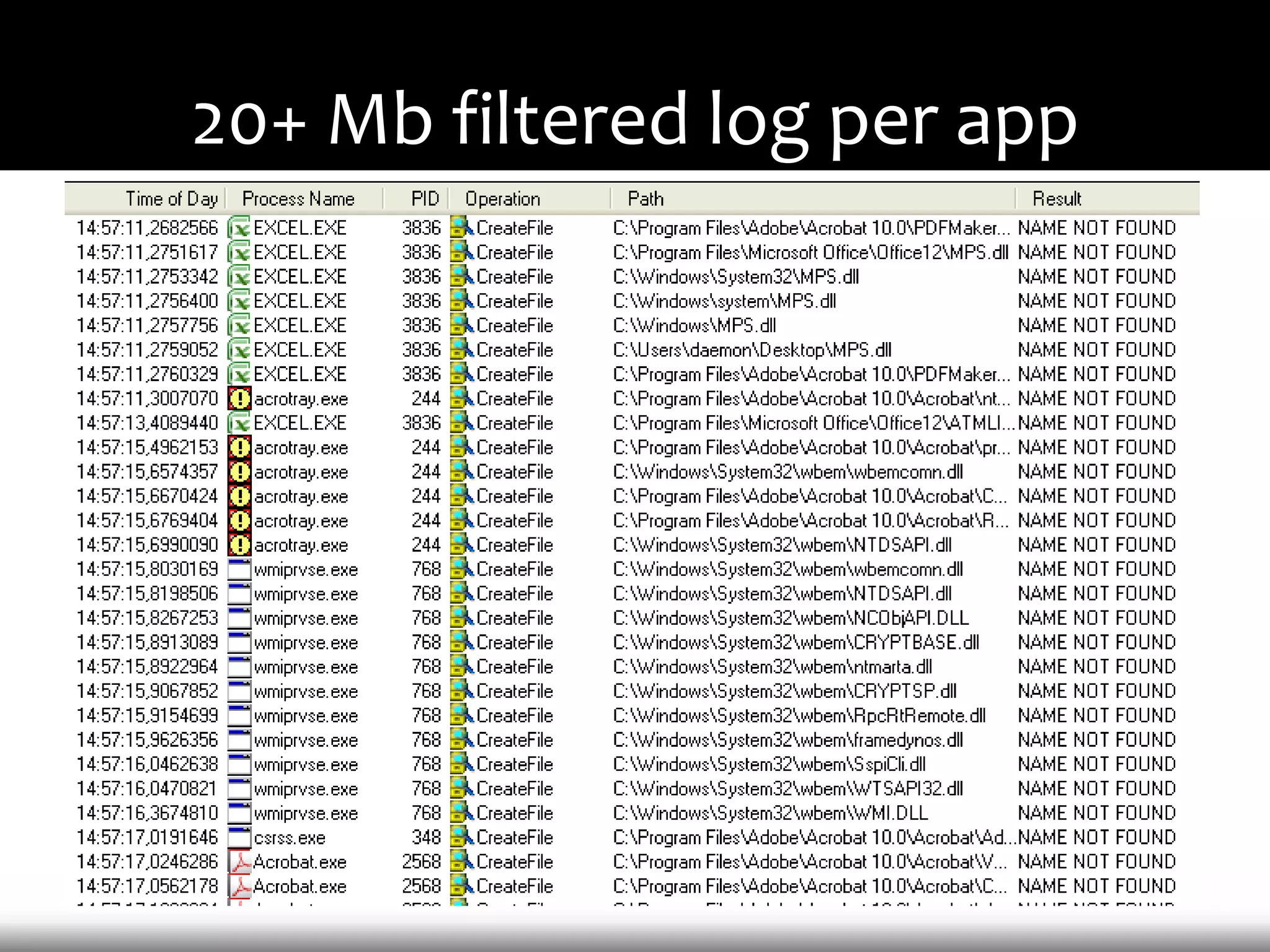
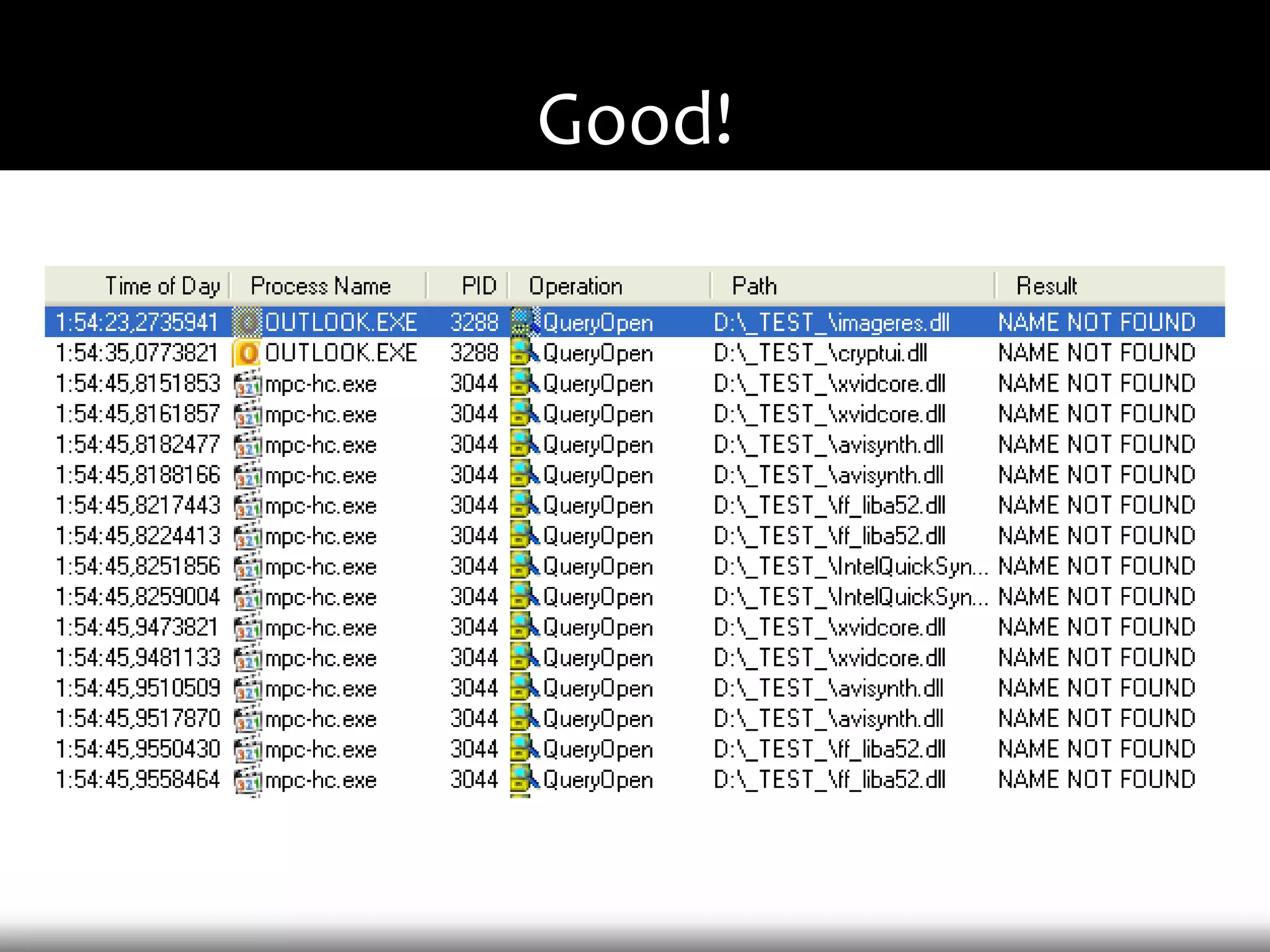
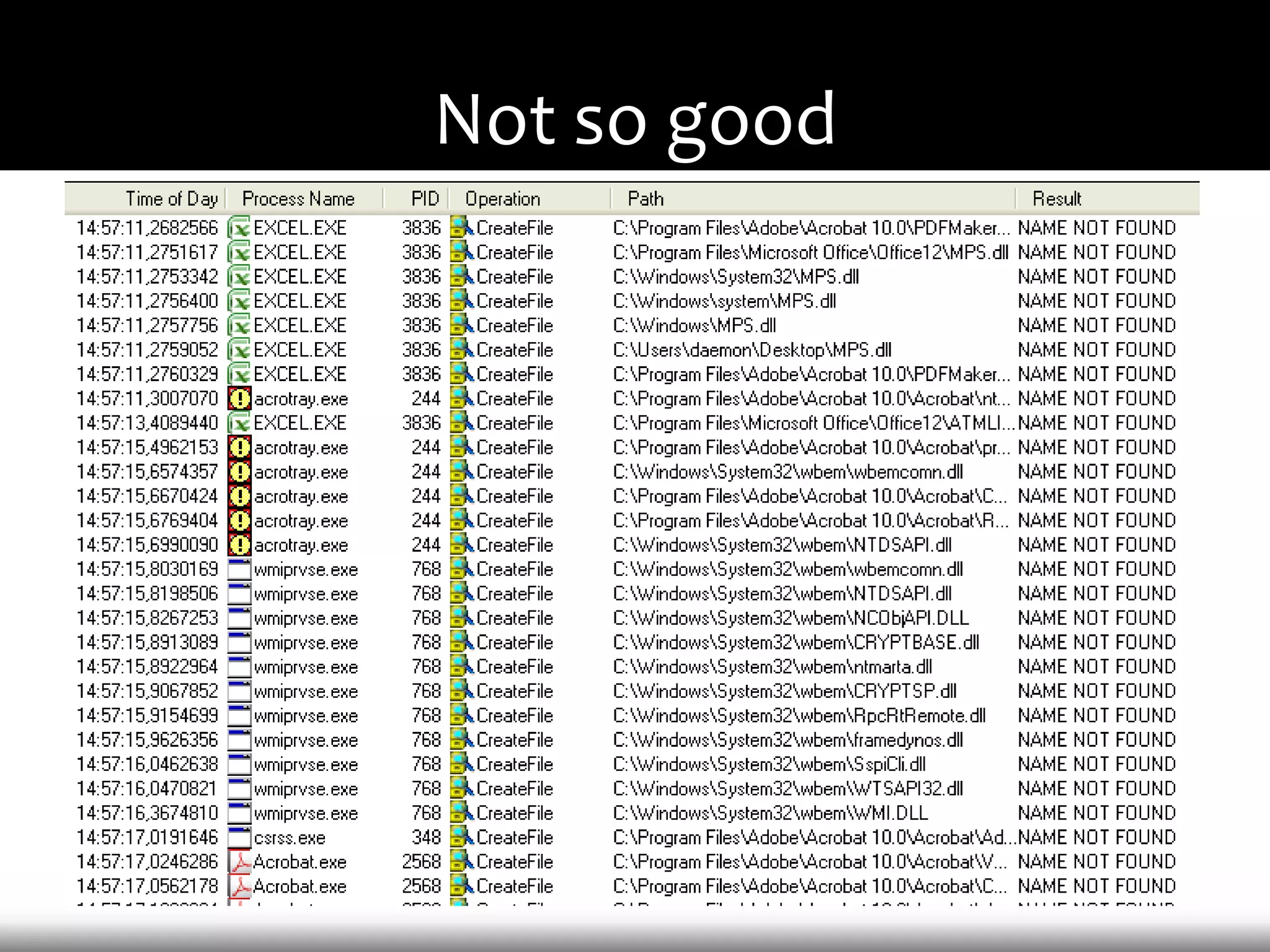
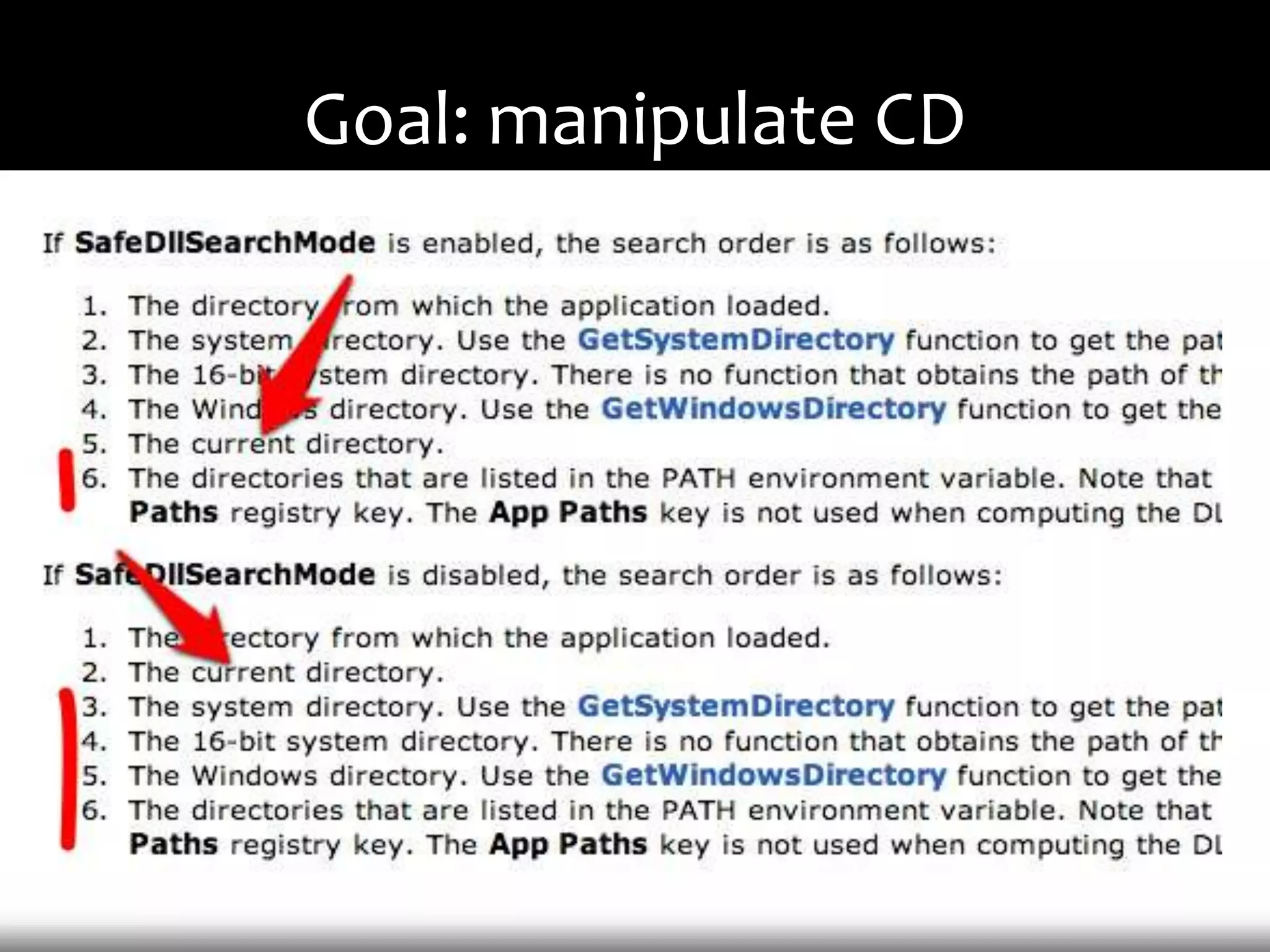
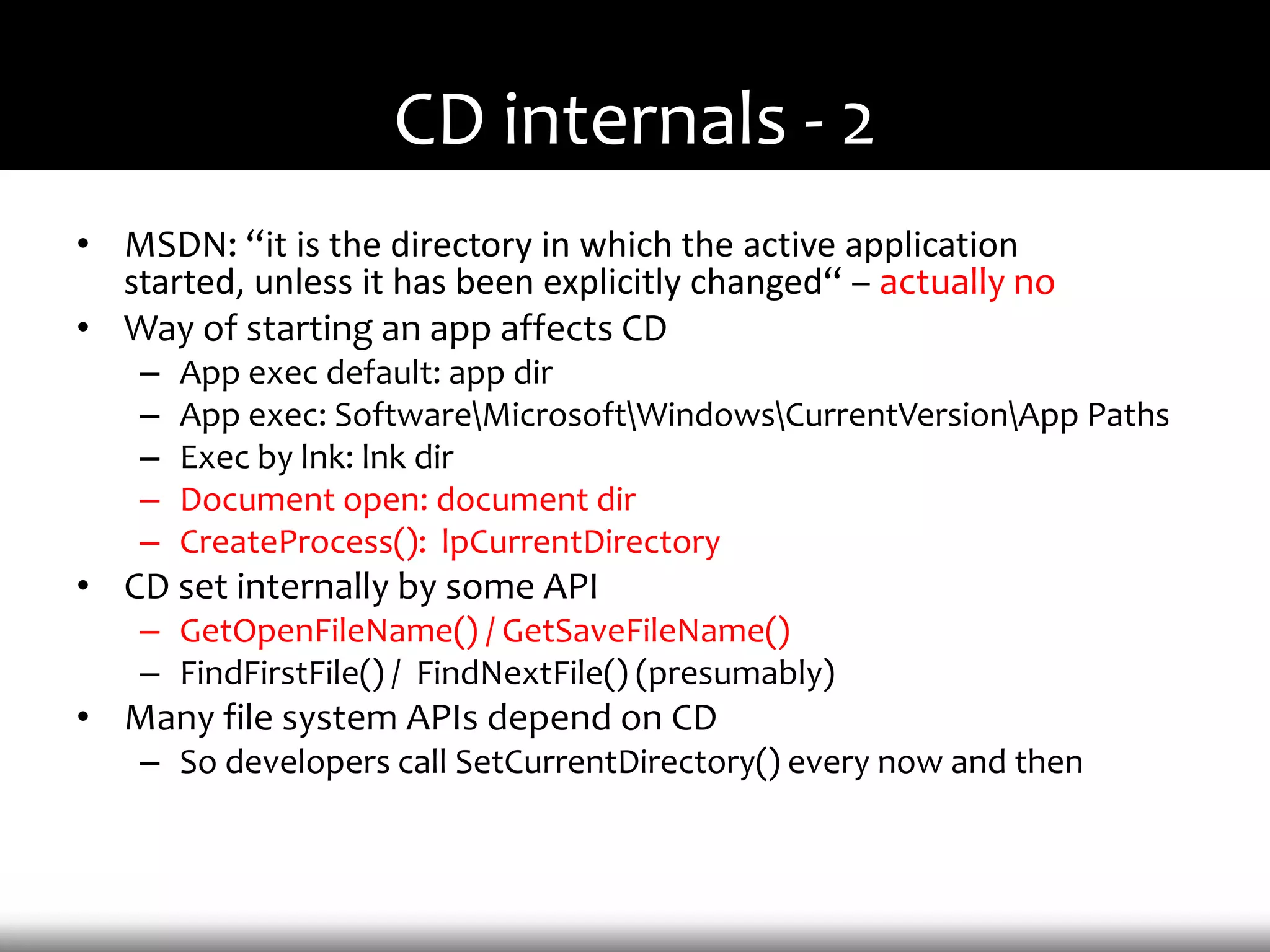
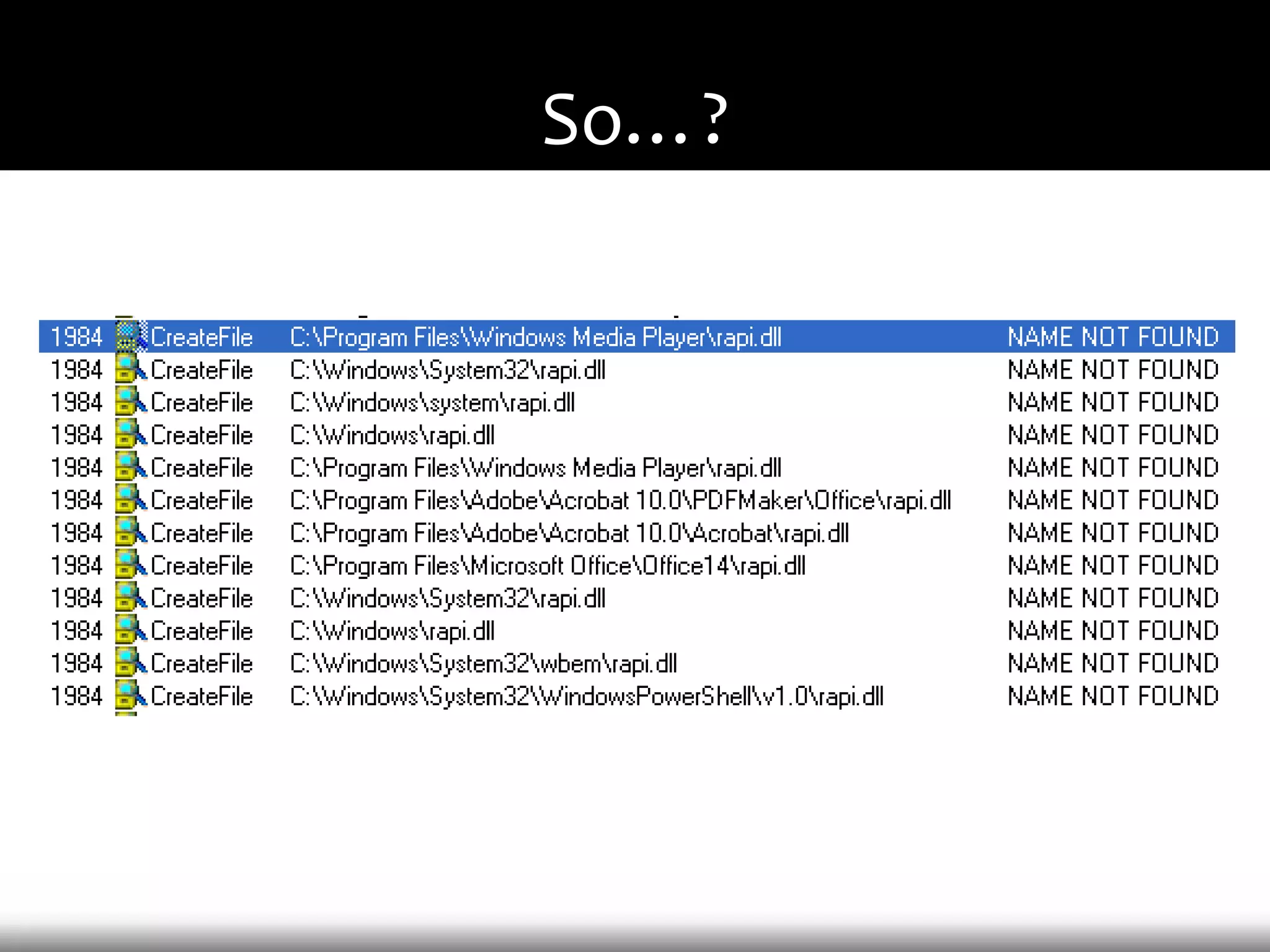
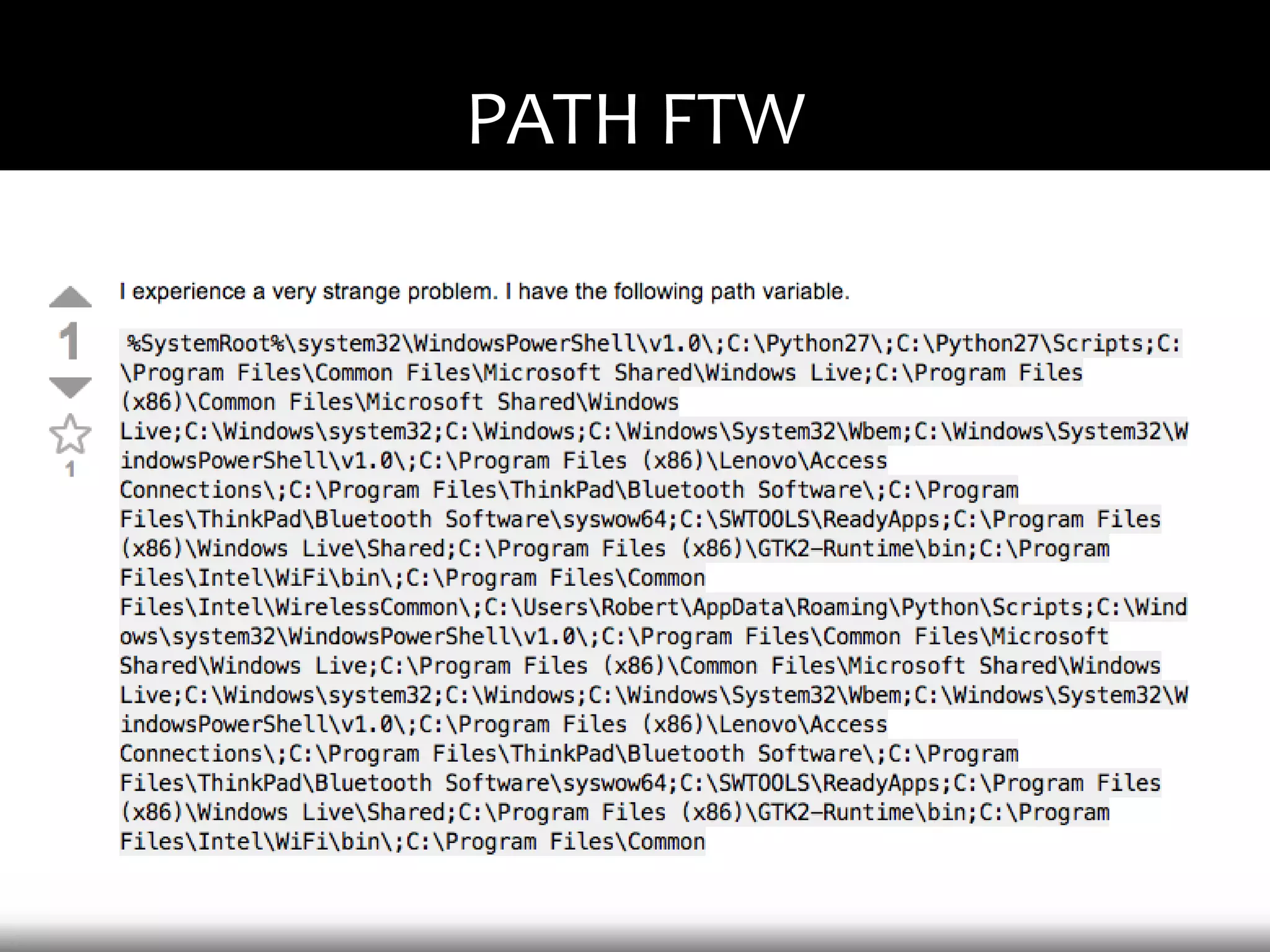
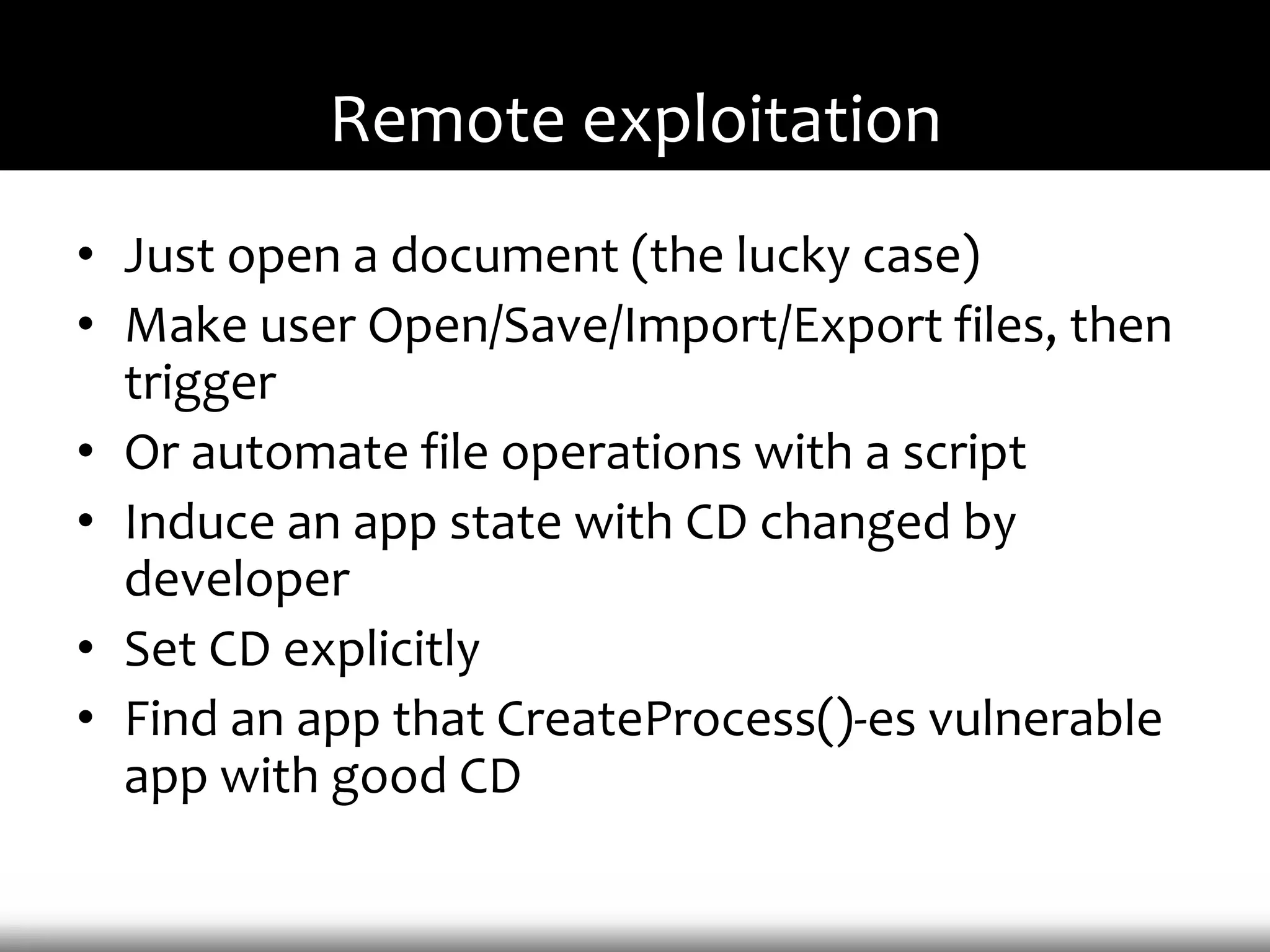
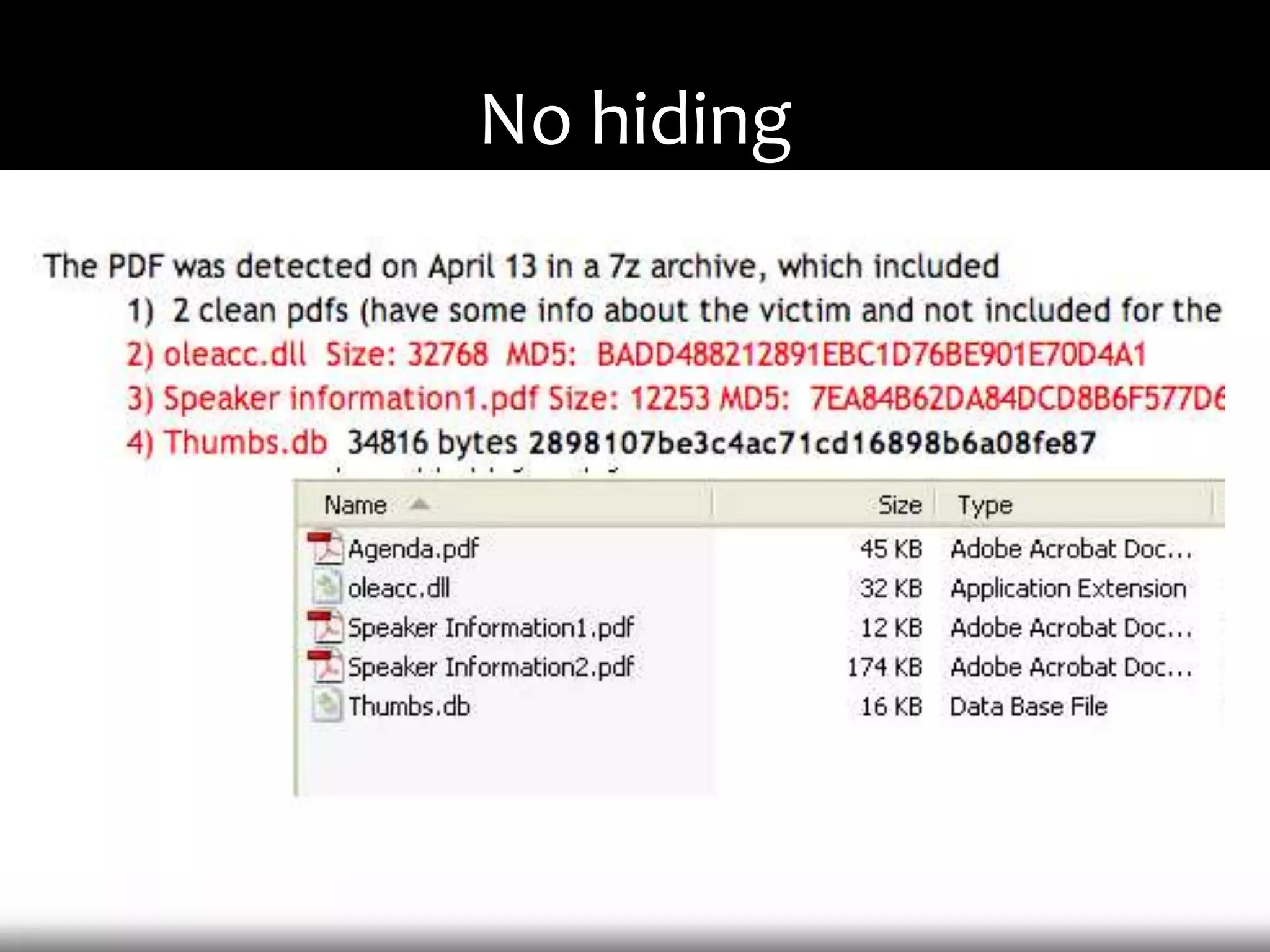
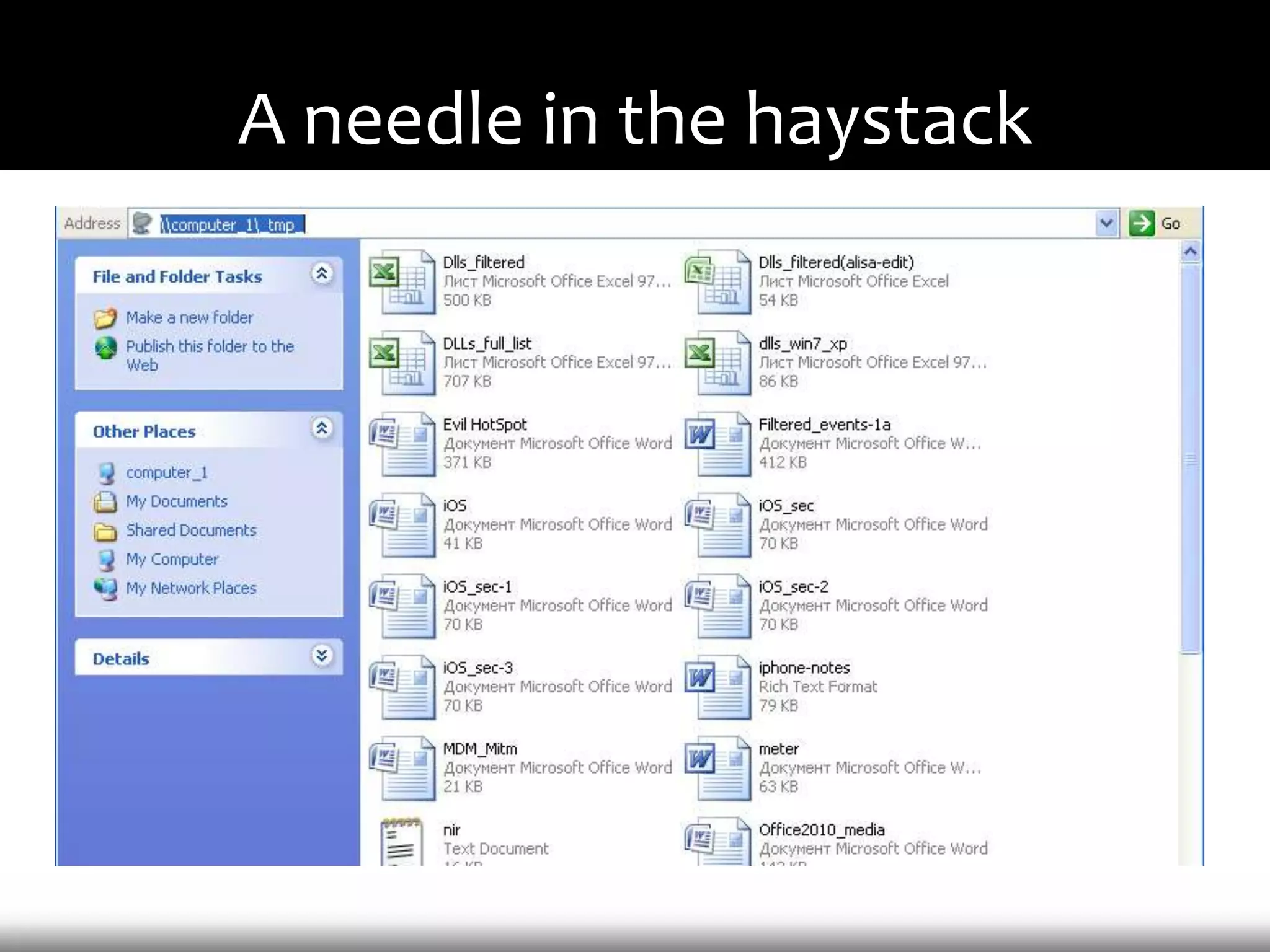
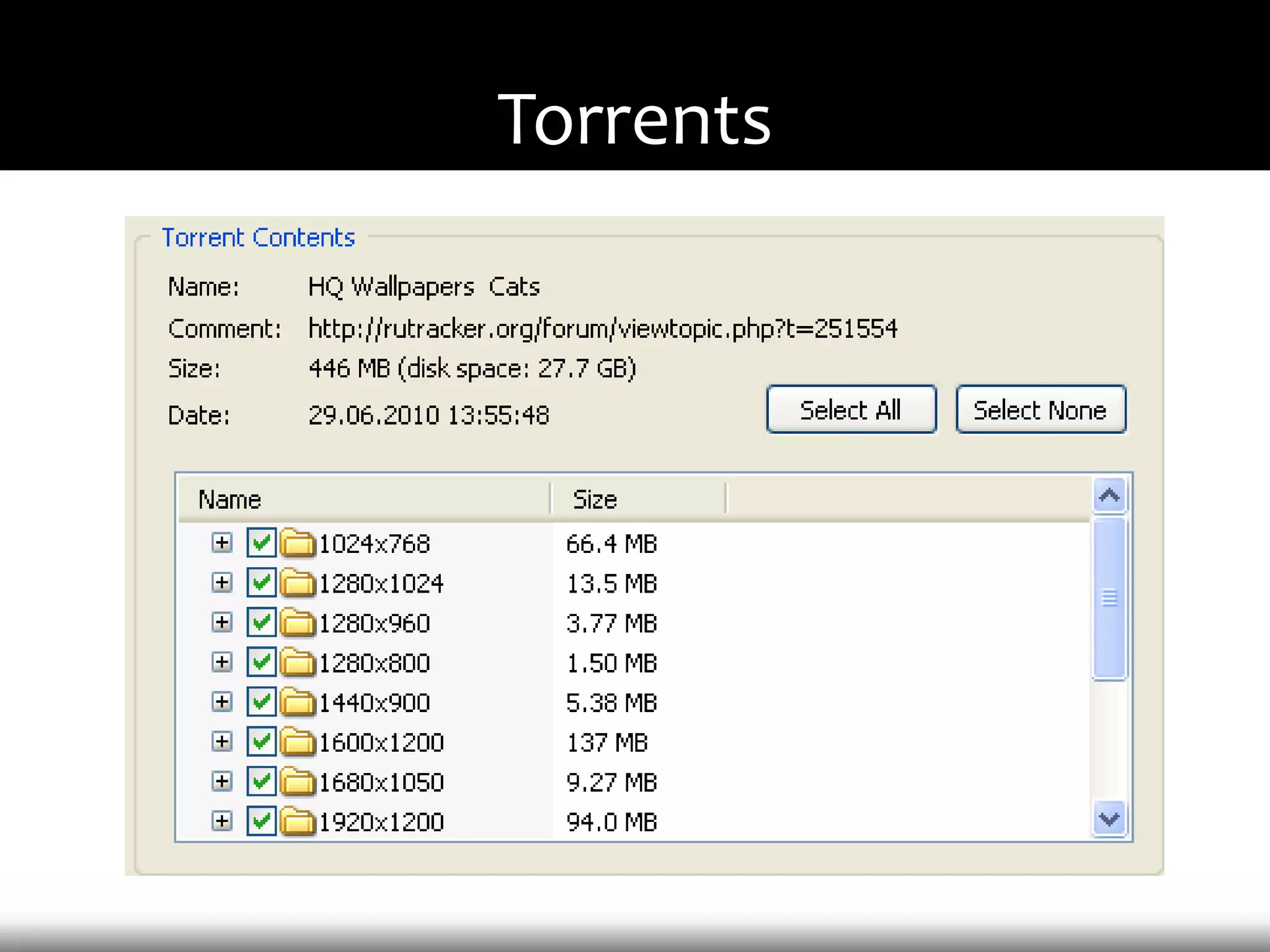
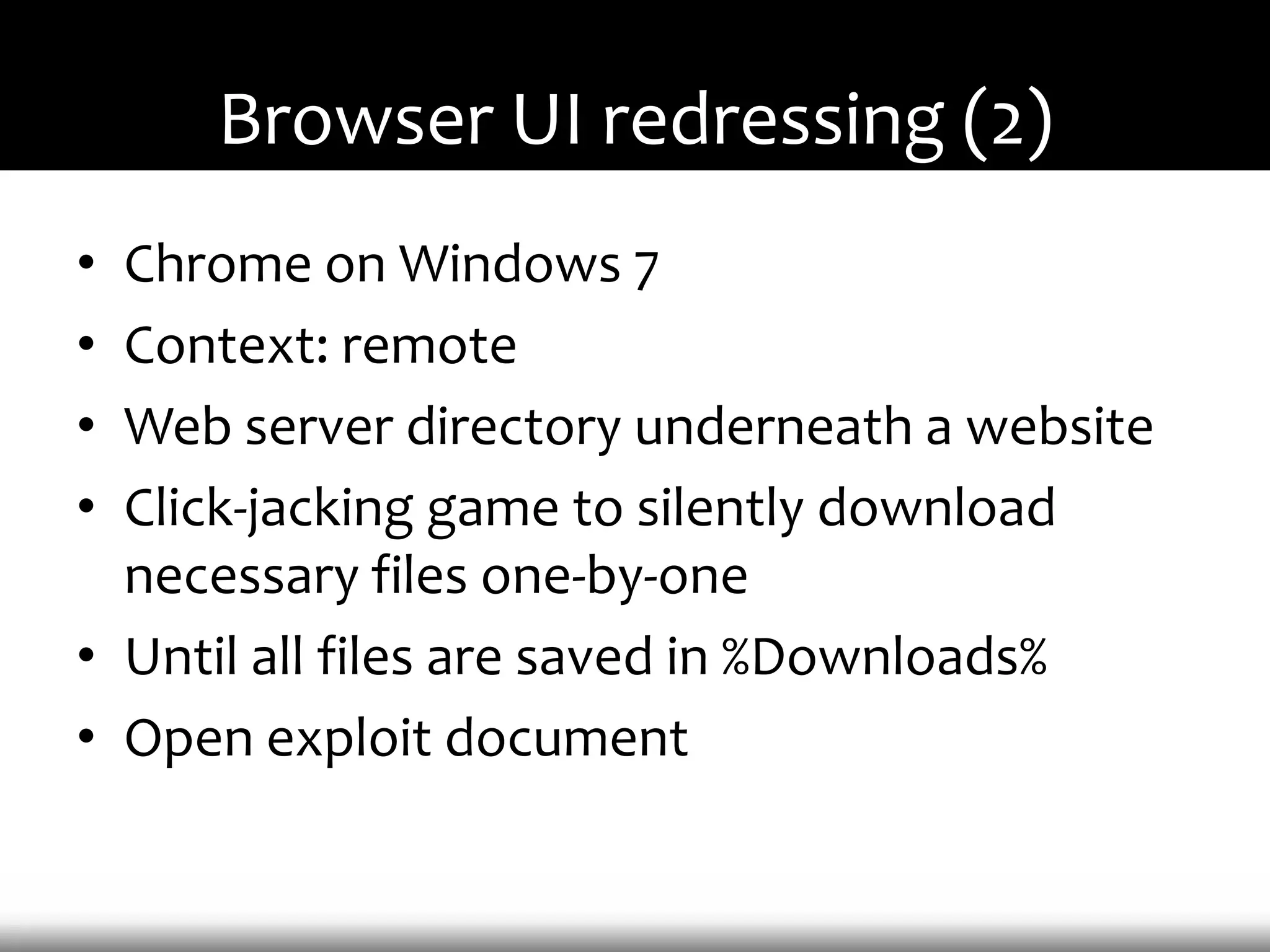
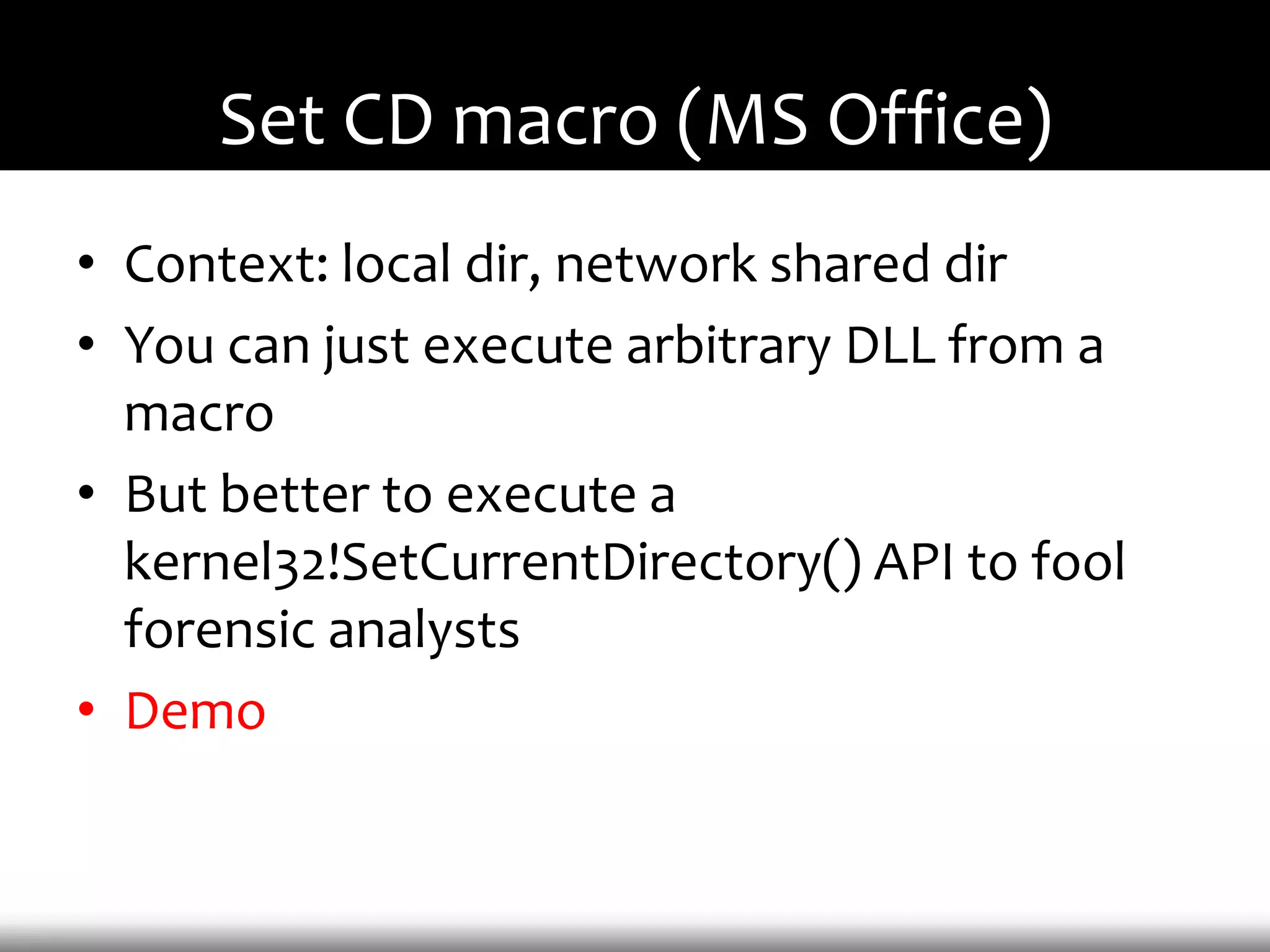
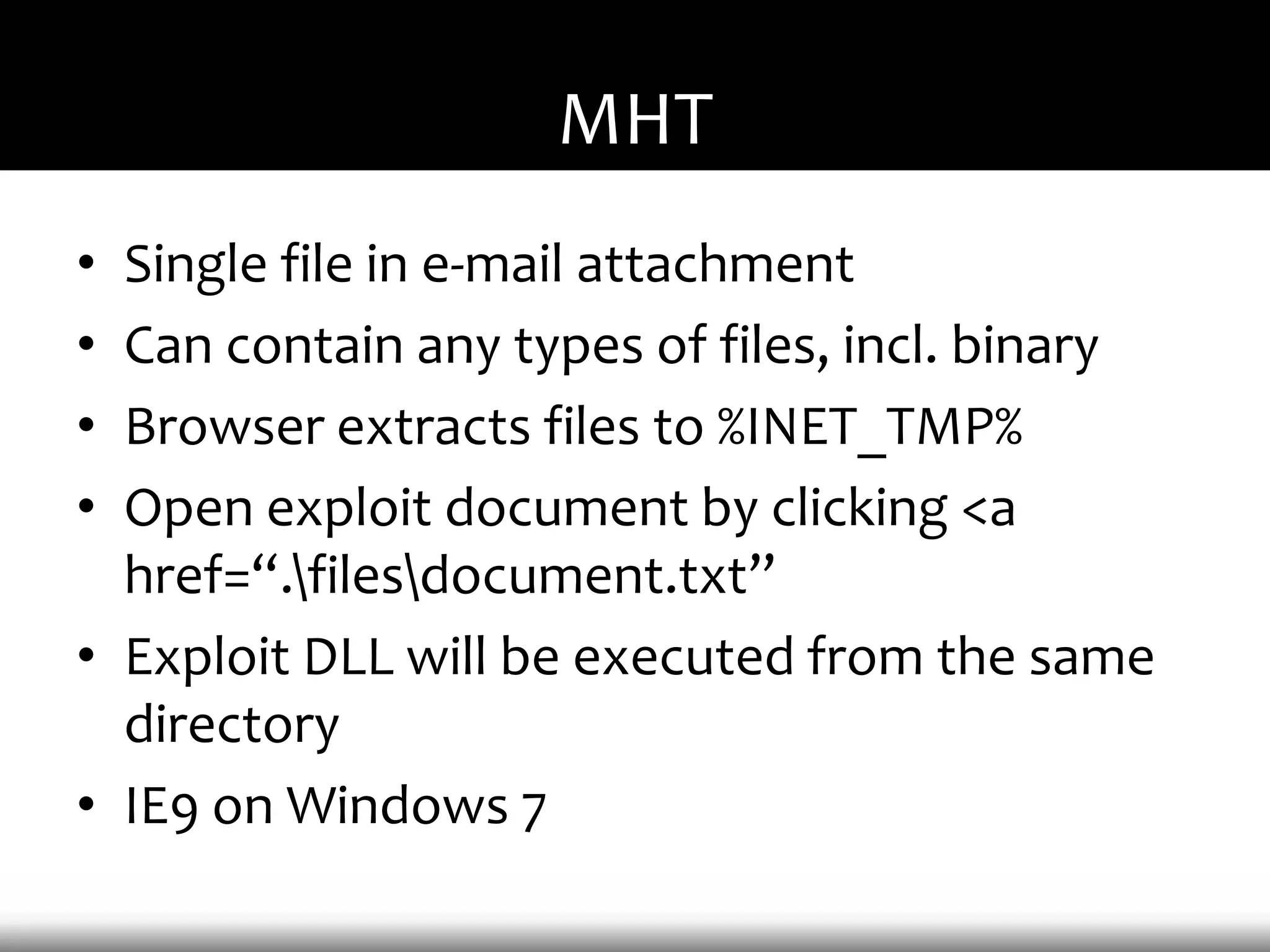
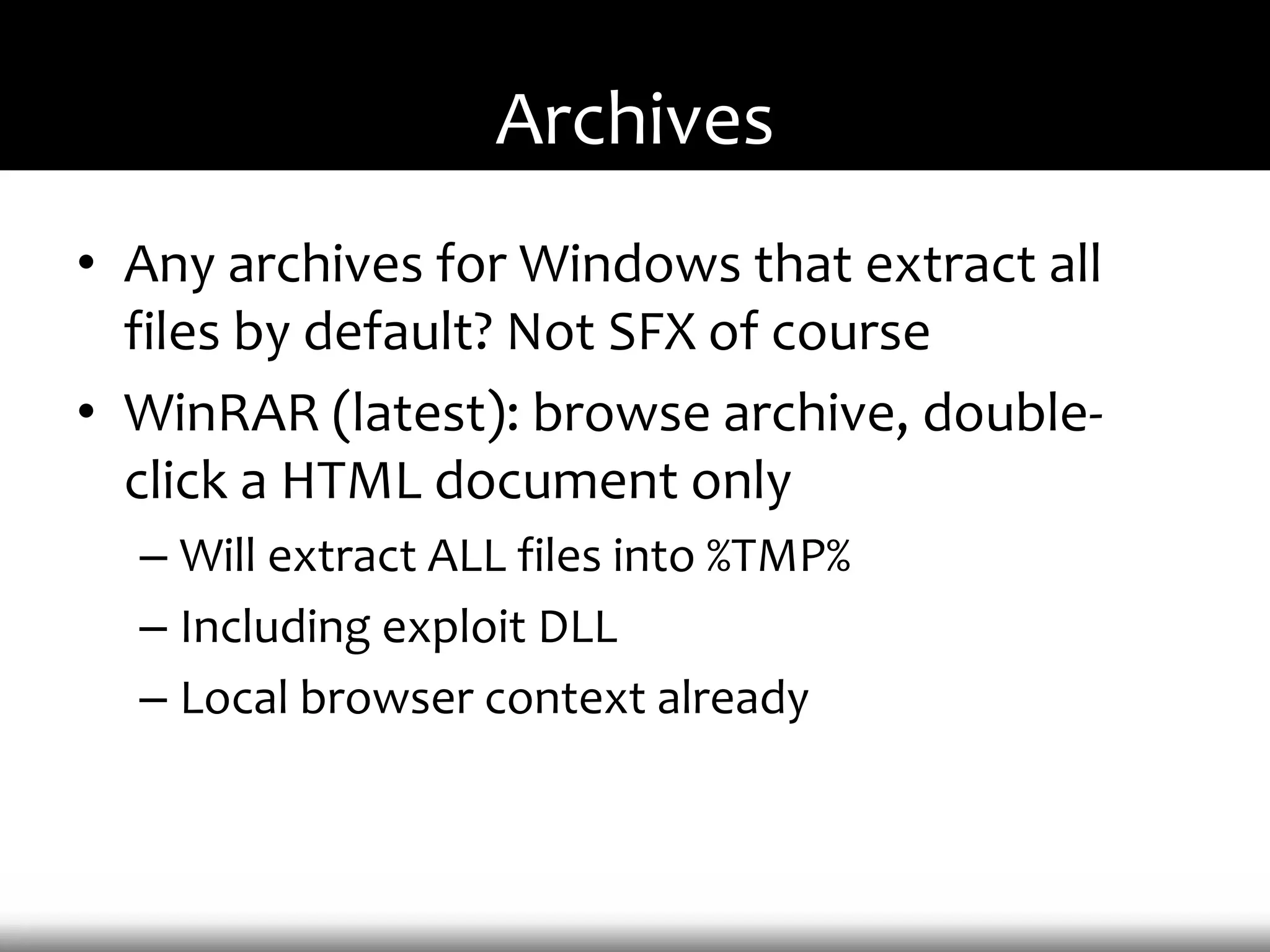
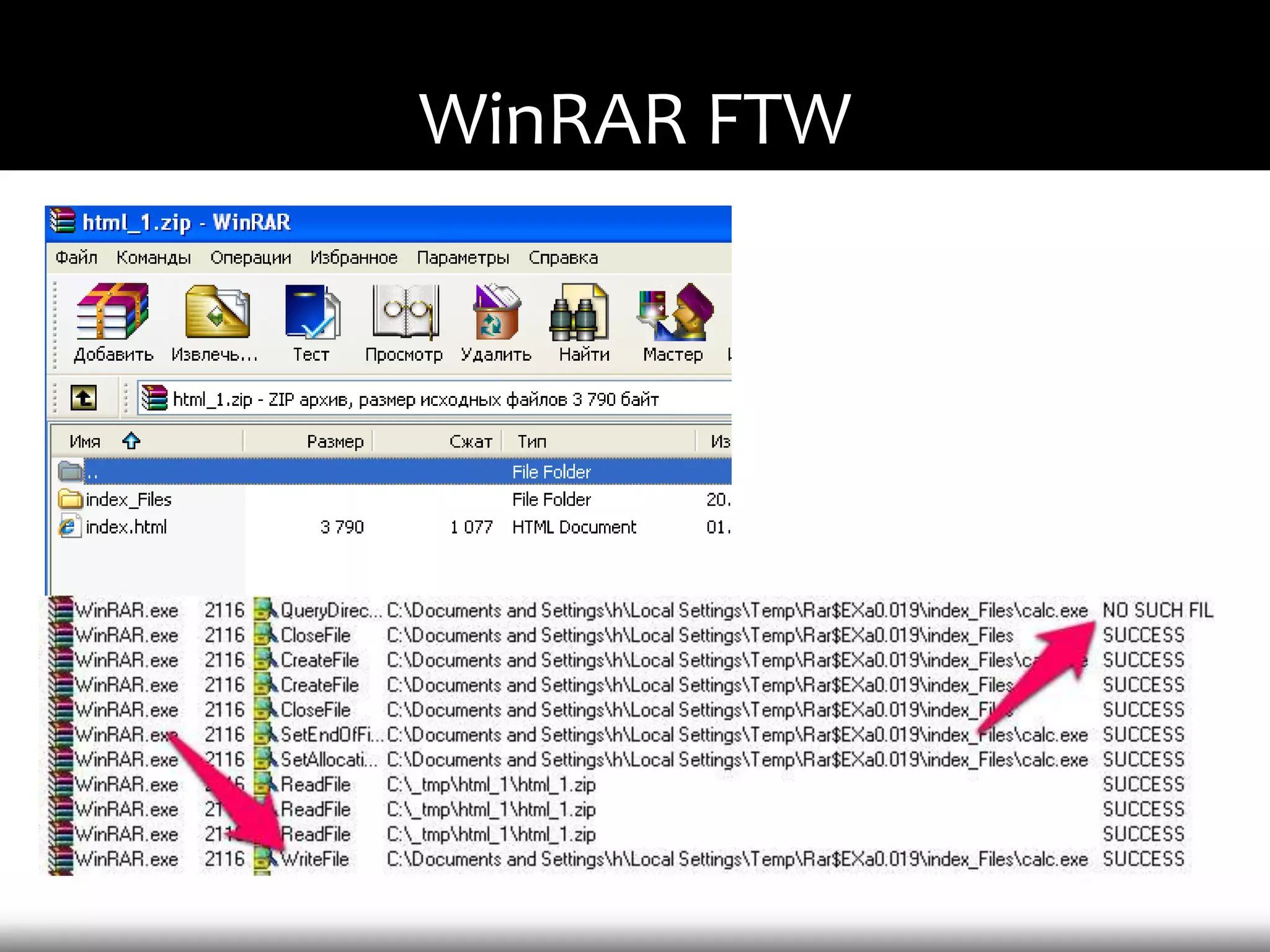
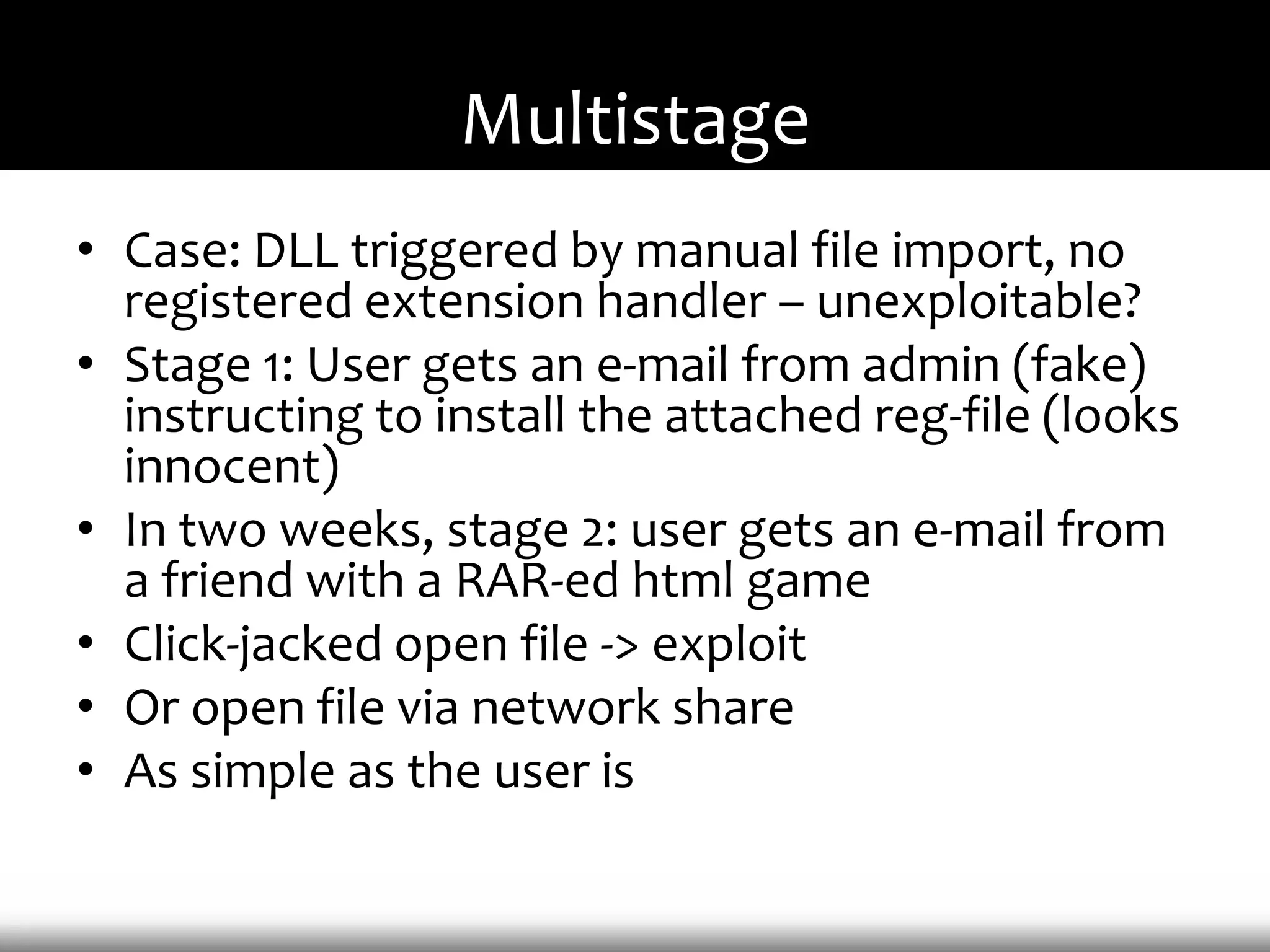
This document discusses techniques for exploiting DLL hijacking vulnerabilities remotely through user interaction. It argues that DLL hijacking is still a viable attack vector despite protections like DEP and ASLR. It proposes manipulating the current directory to execute exploits and hiding DLLs in archives, email attachments, and browser redressing to trigger exploits without appearing suspicious. While not suitable for mass attacks, it concludes DLL hijacking enables rapid targeted attacks by abusing existing vulnerabilities.