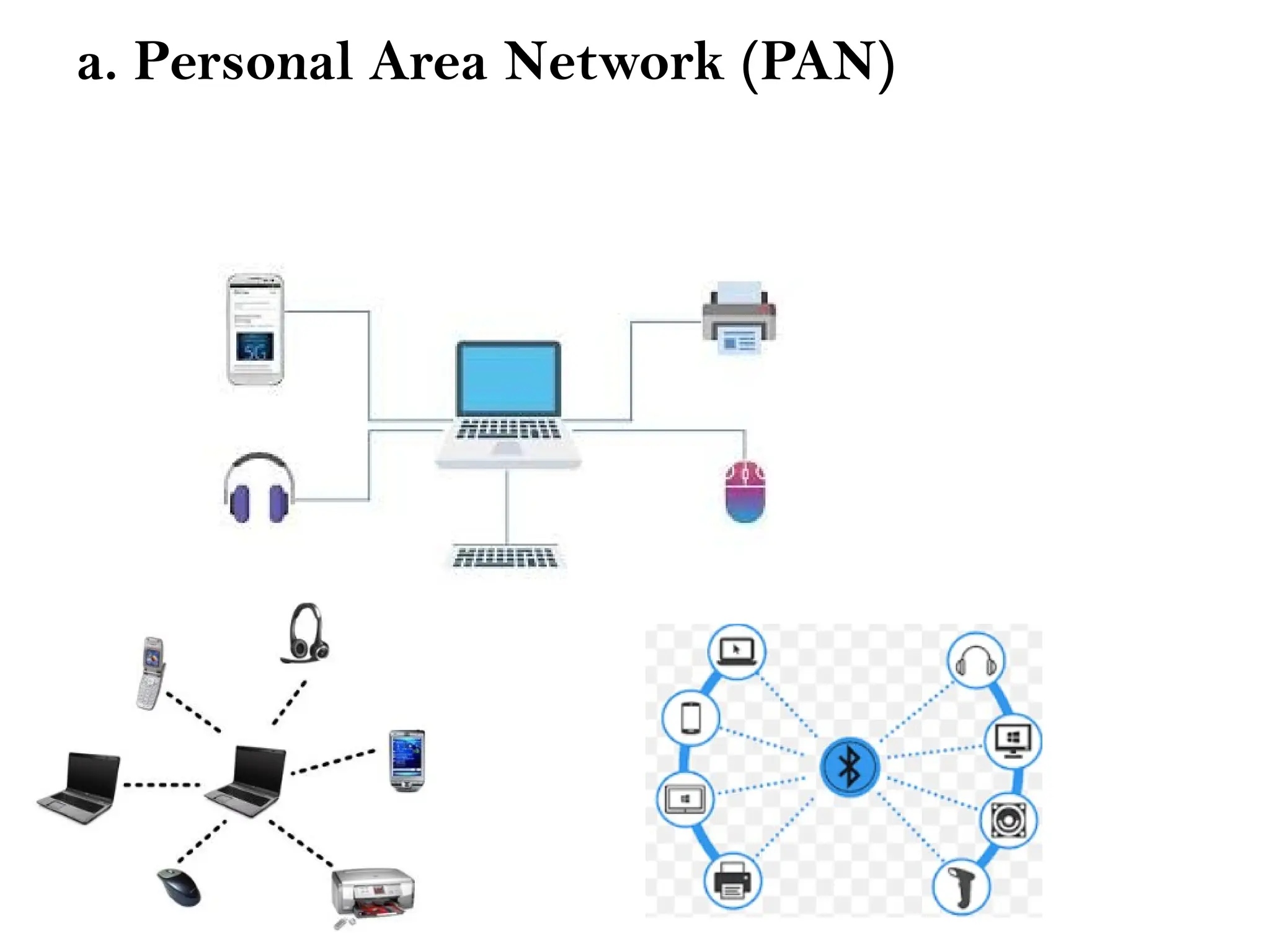
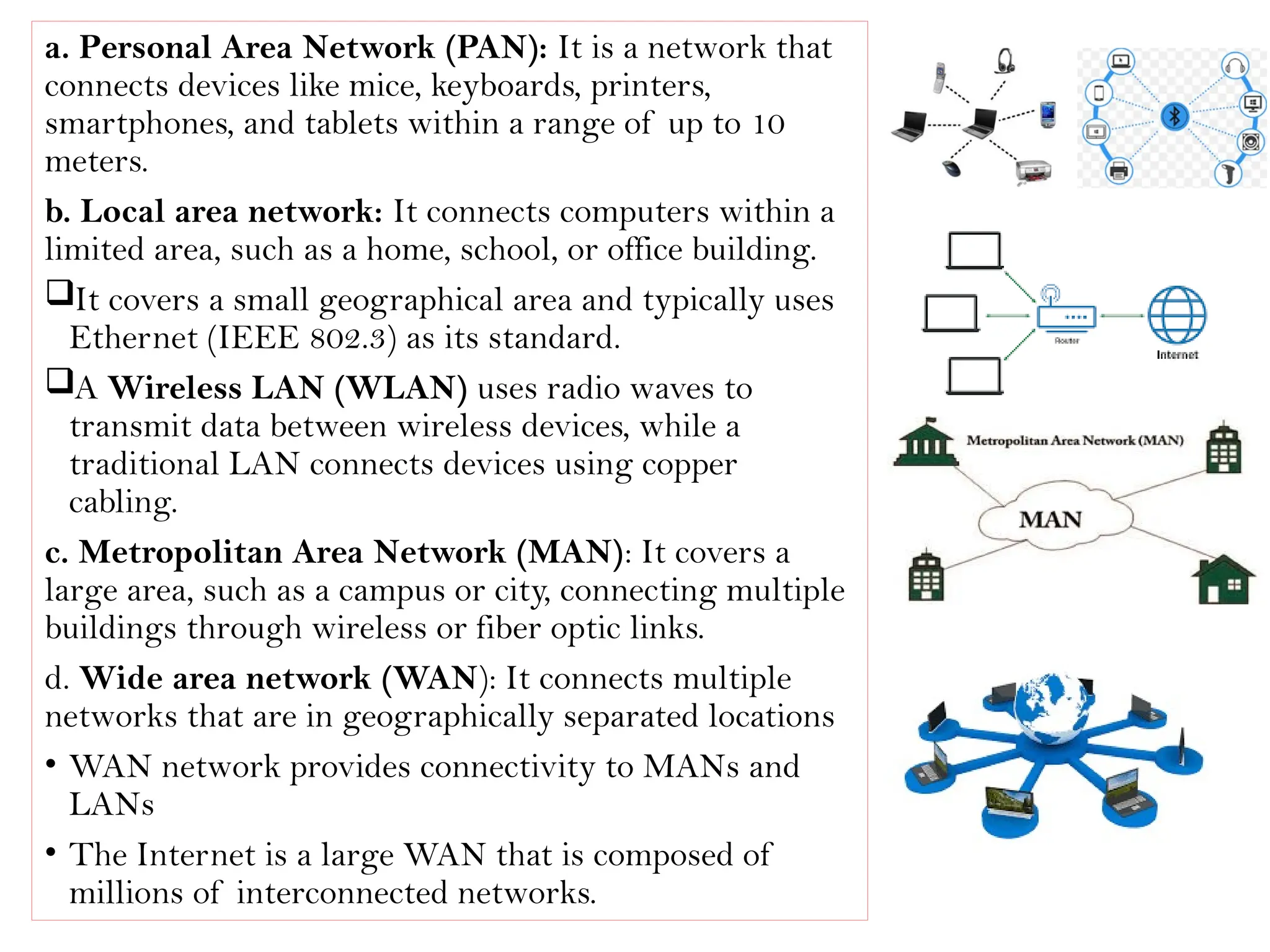
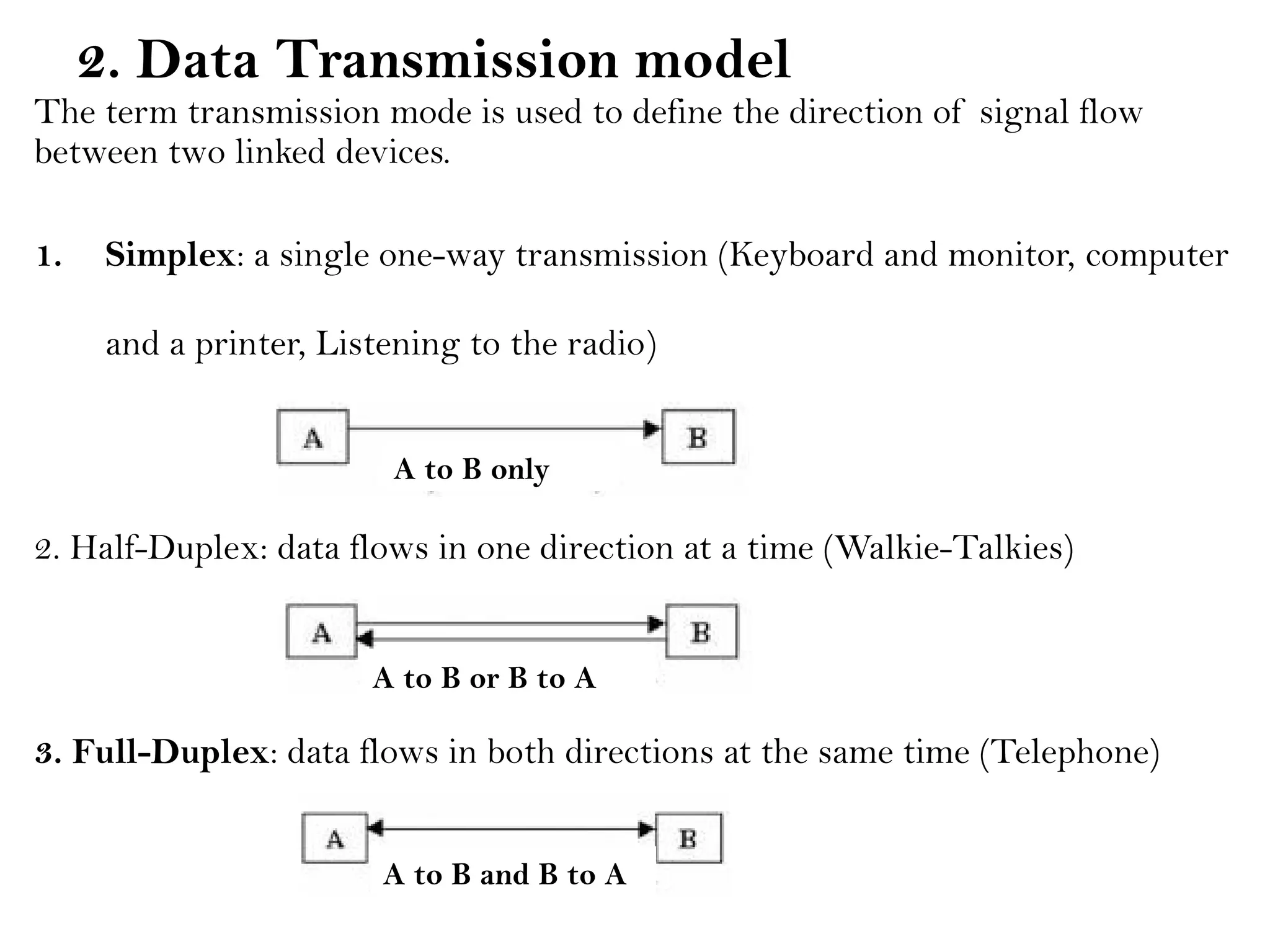
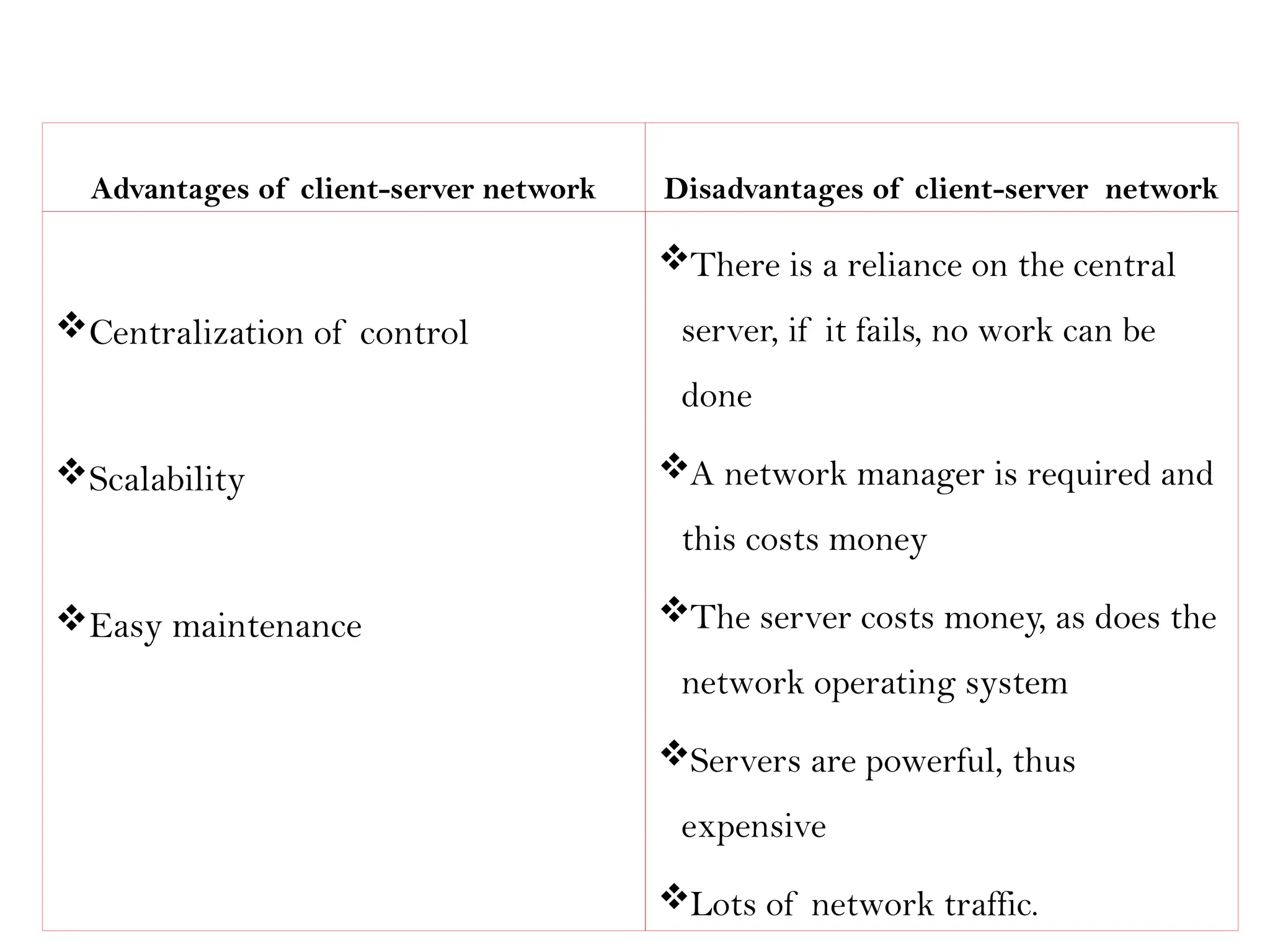
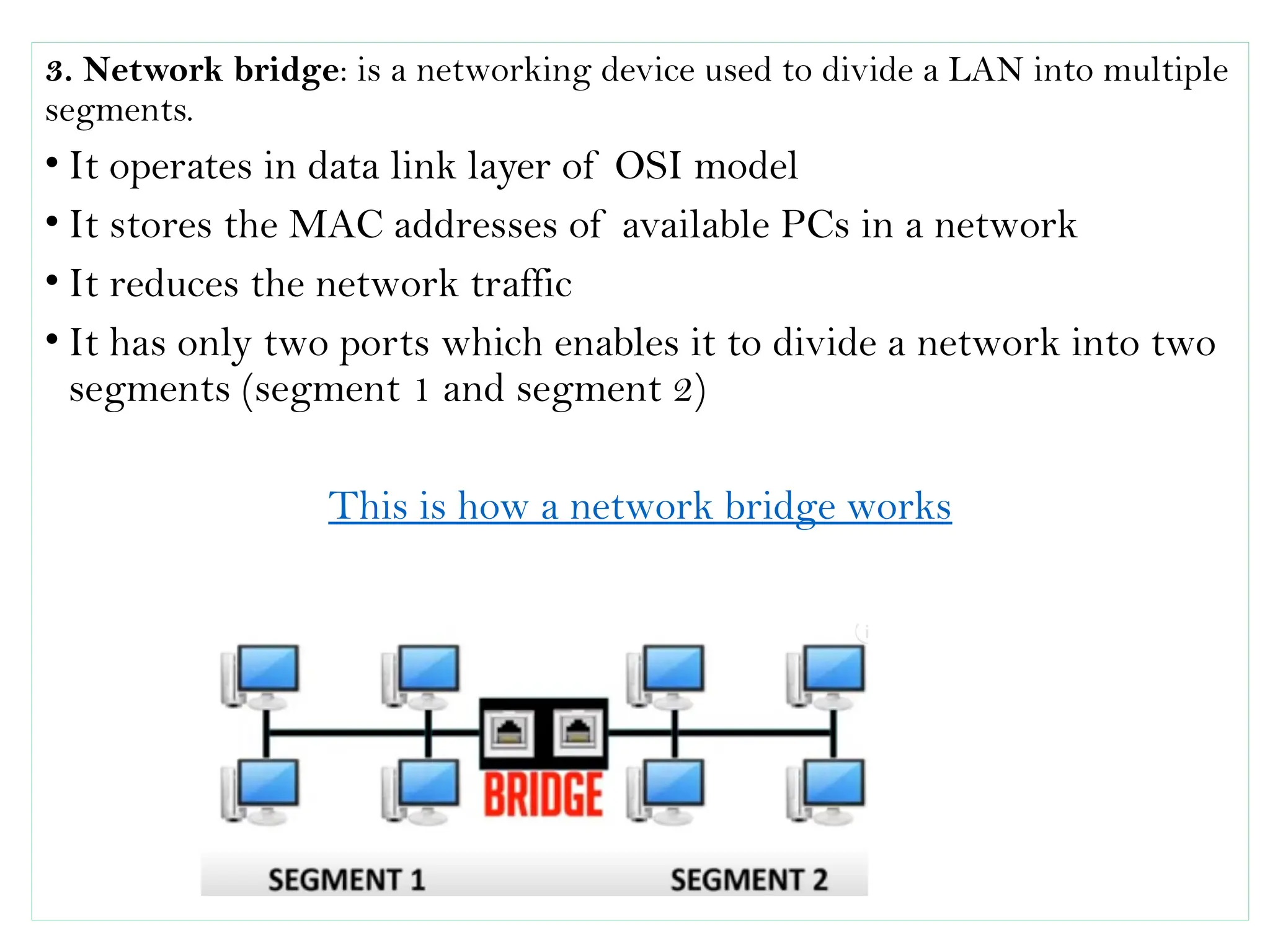
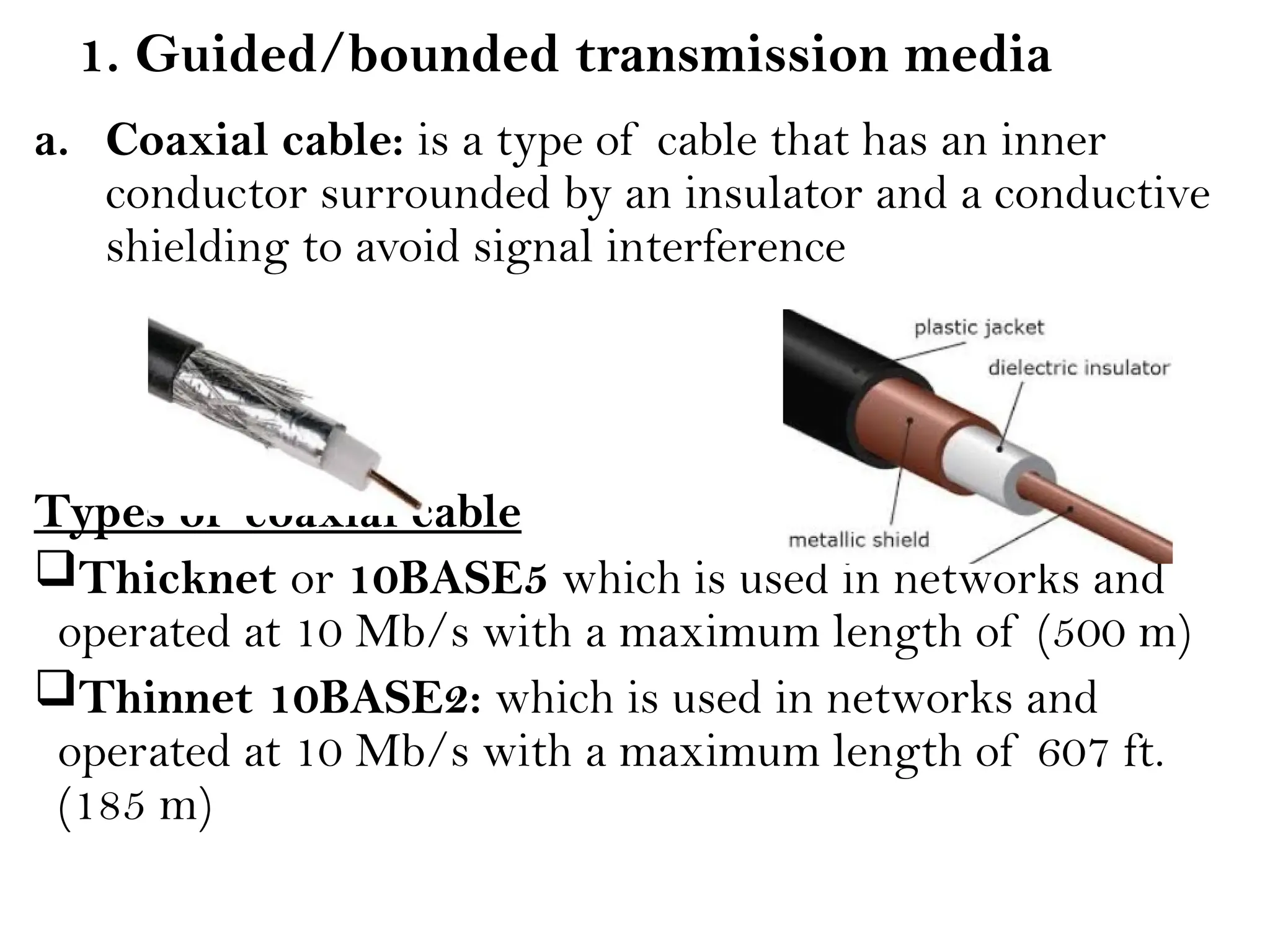
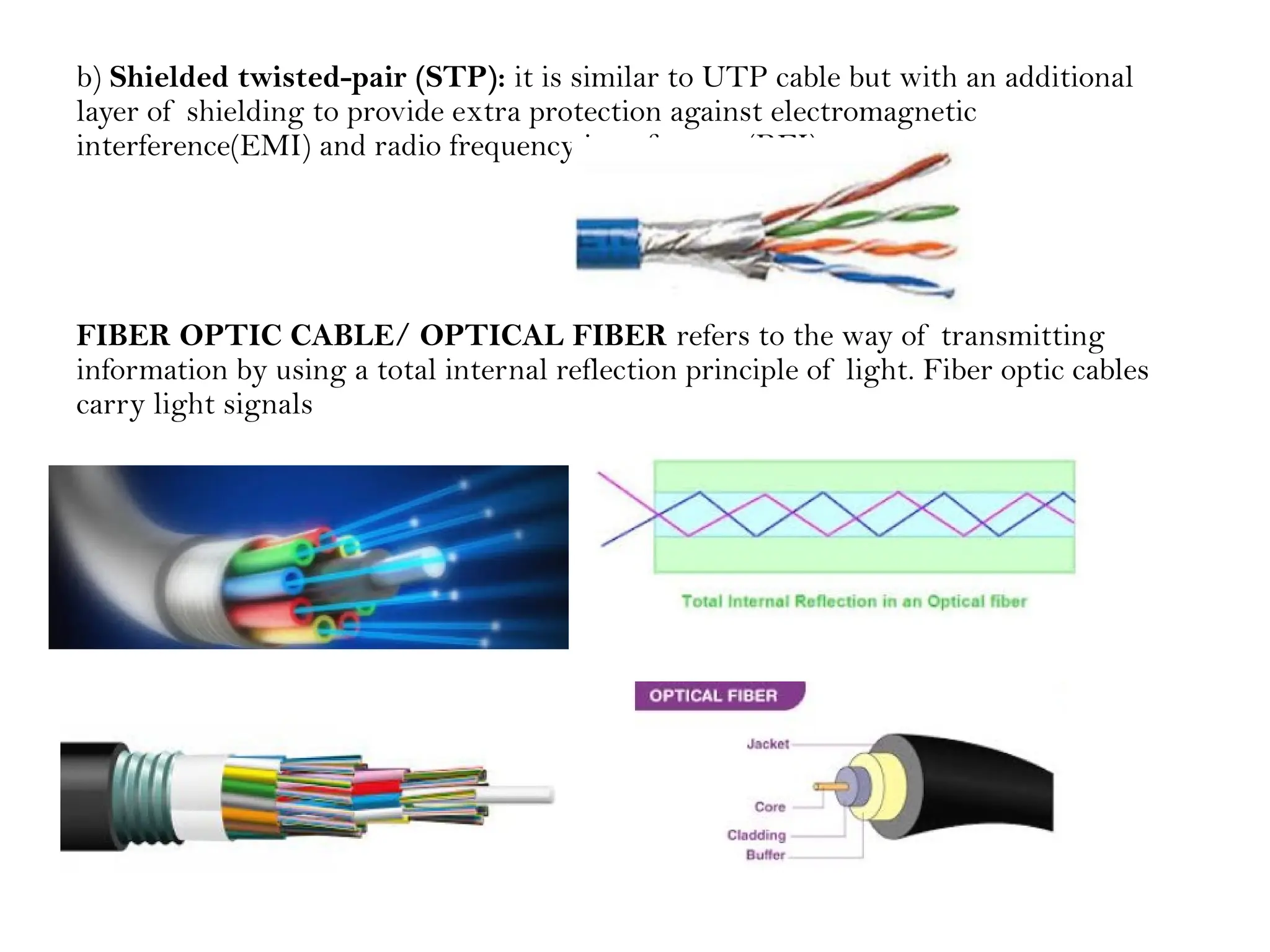
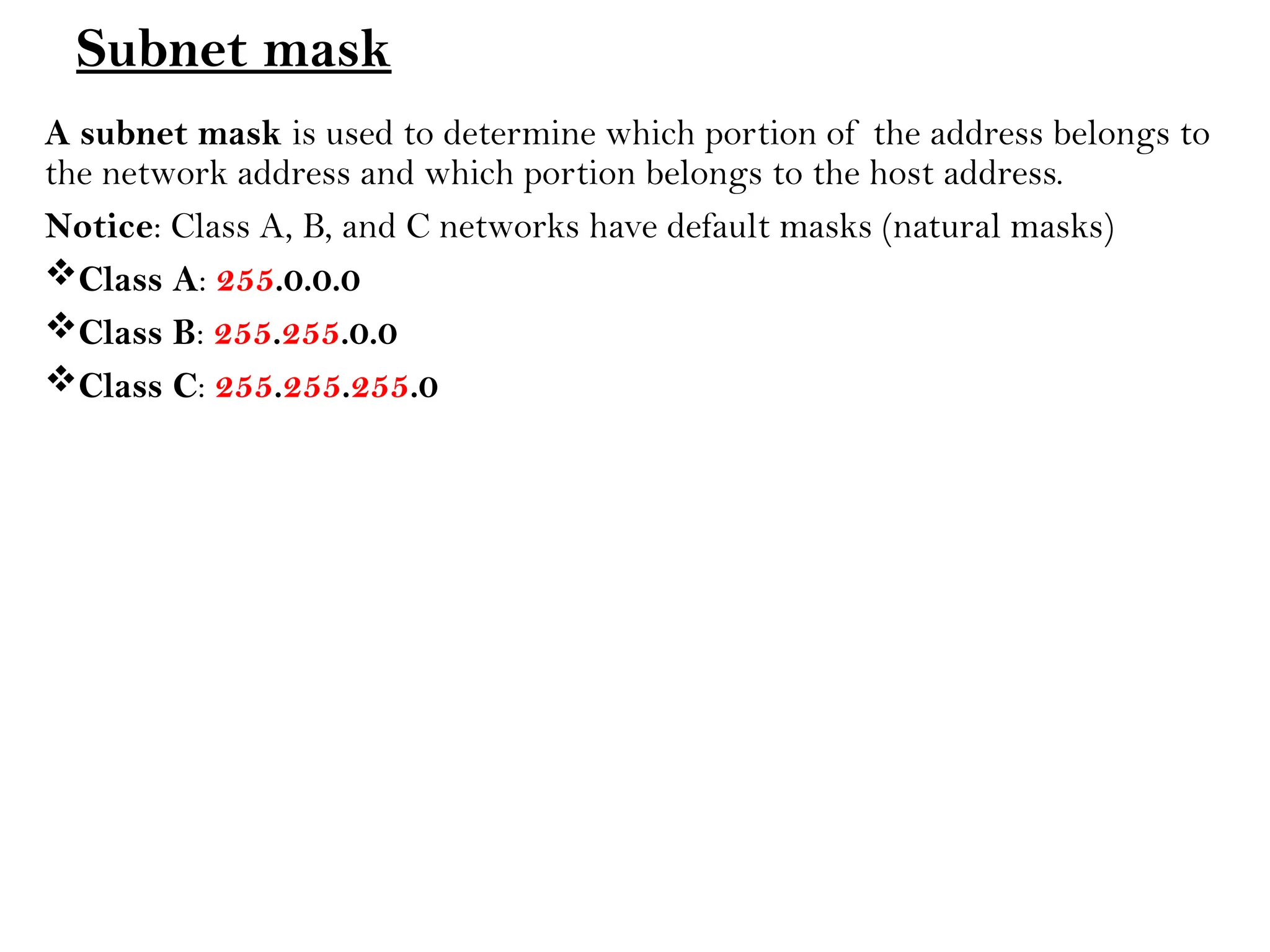
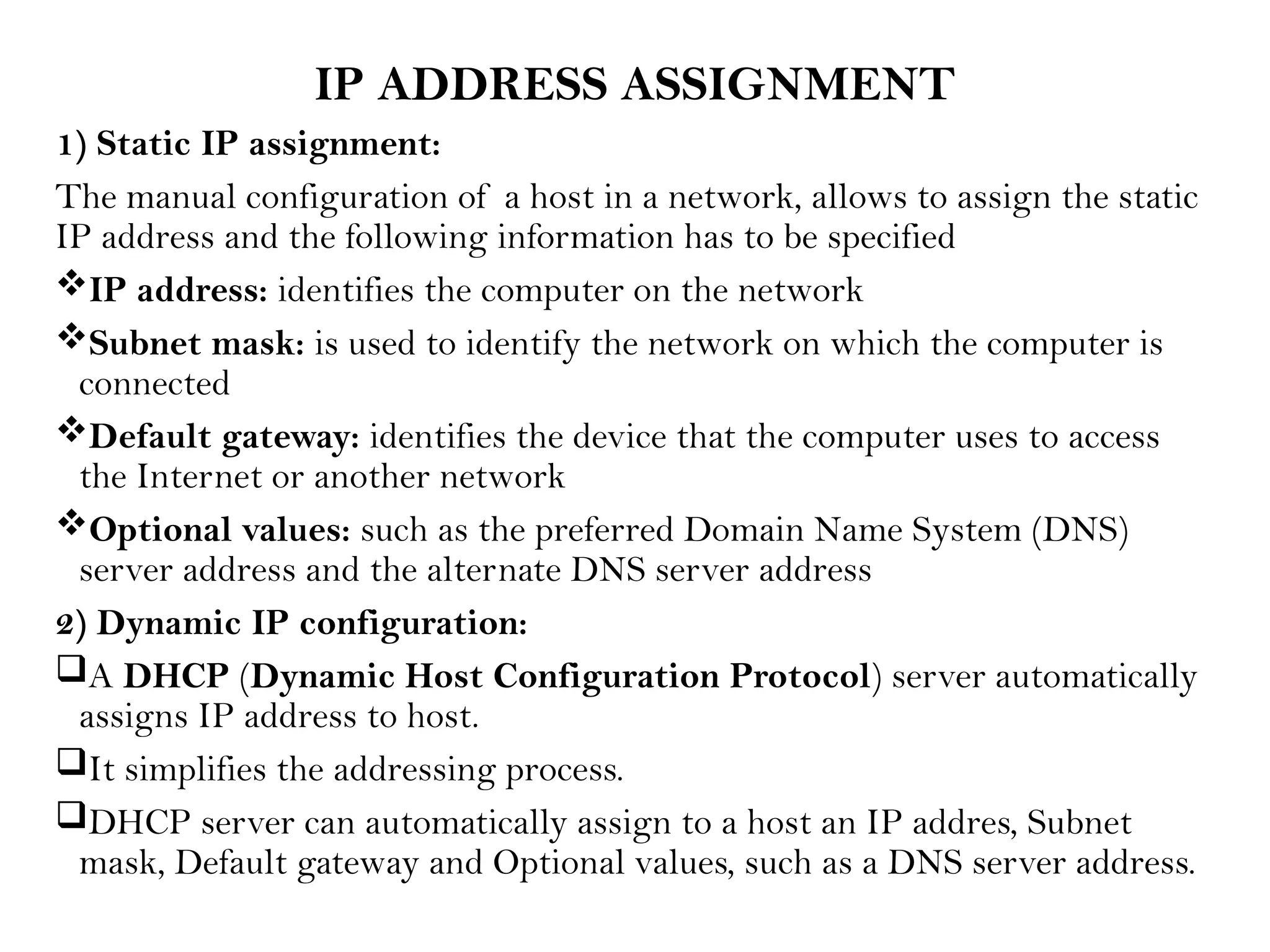
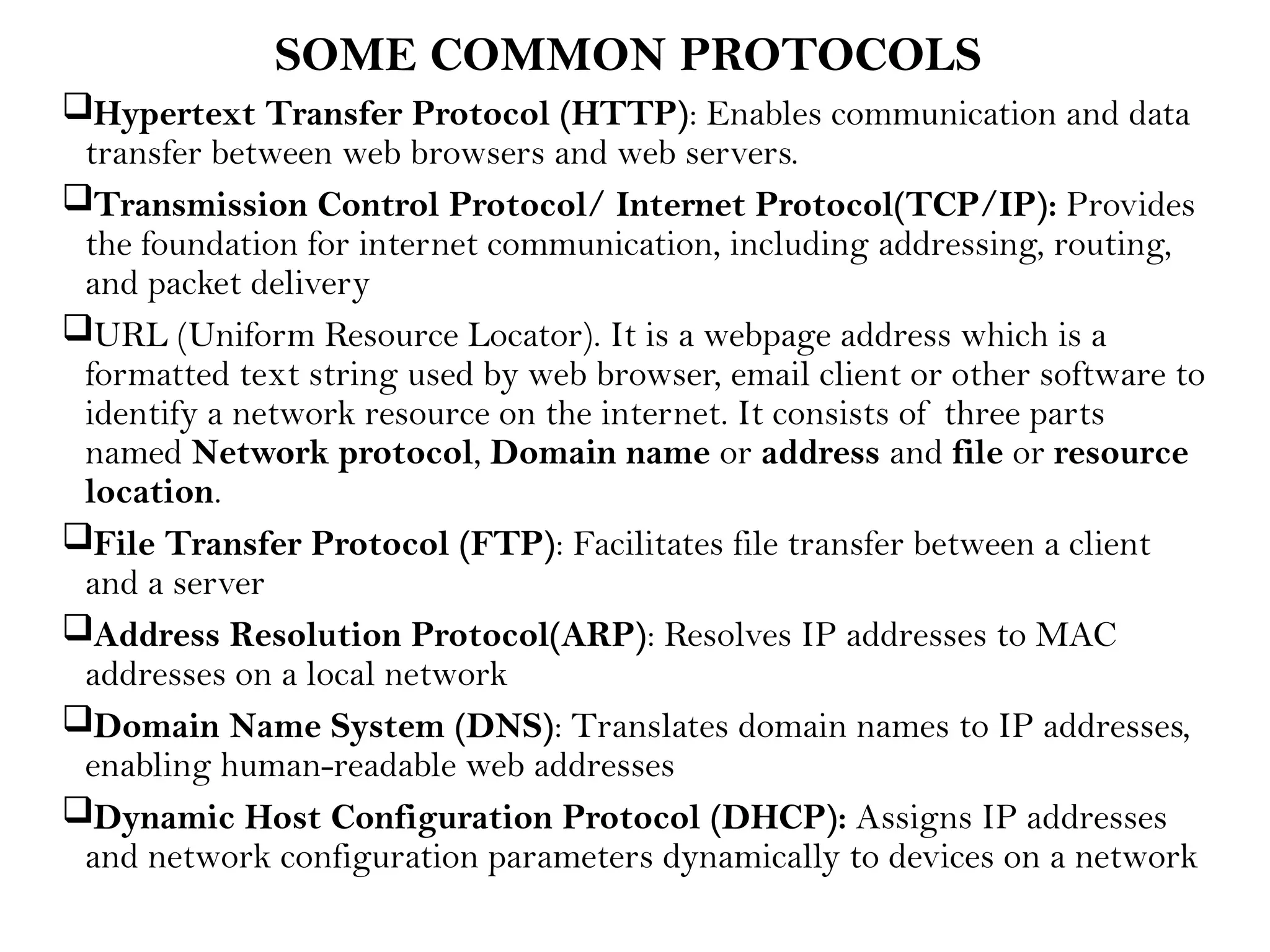
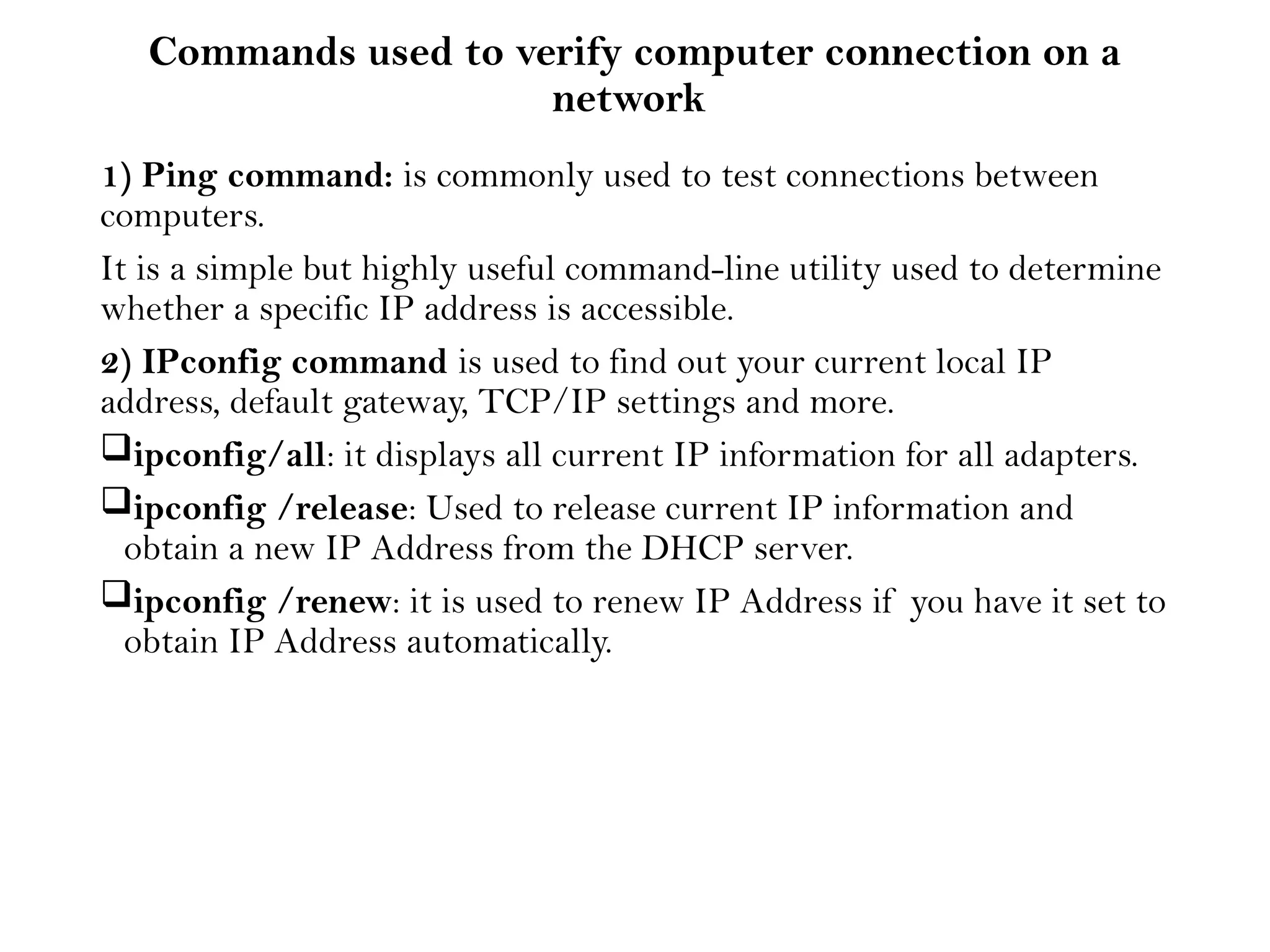
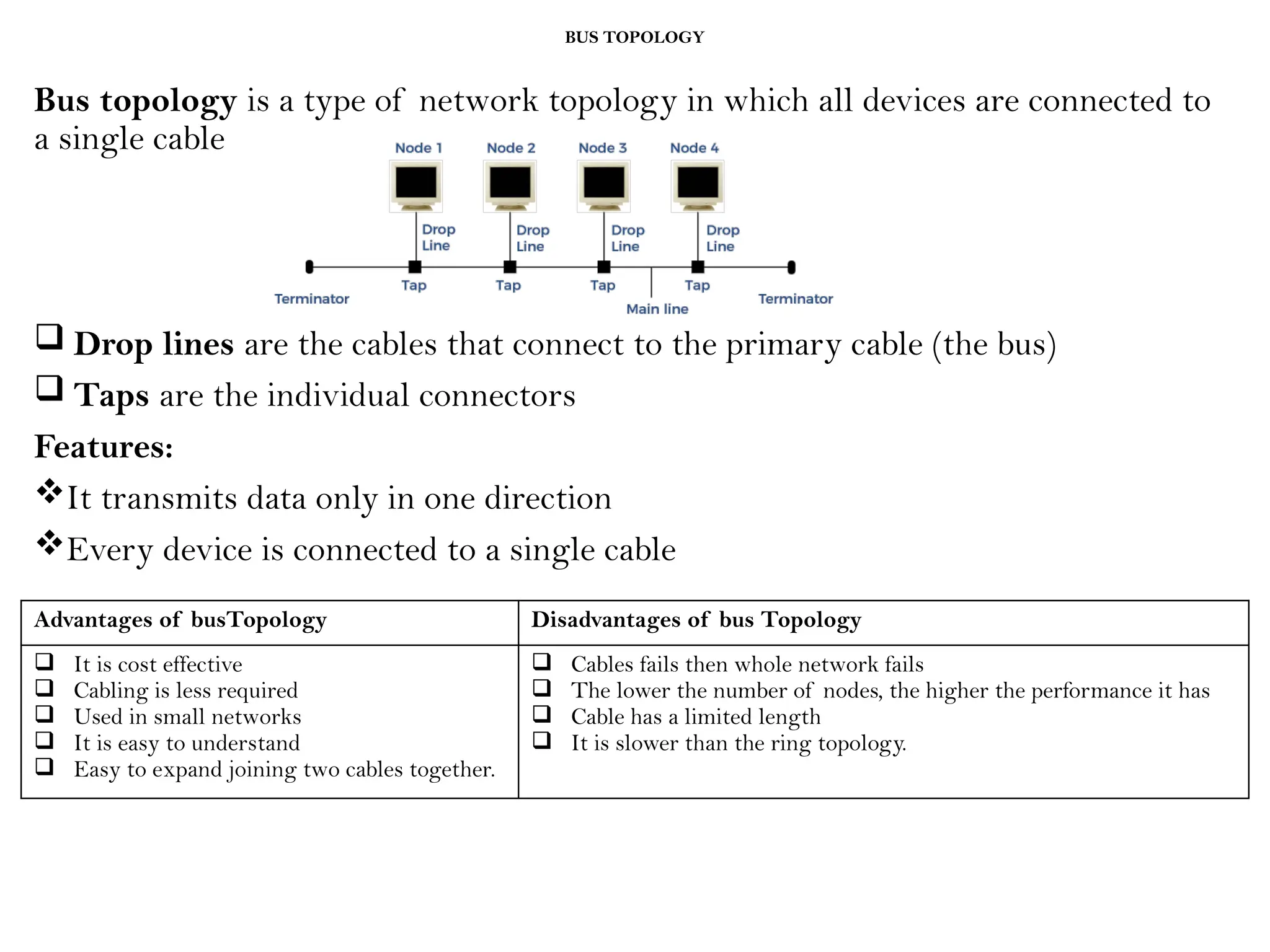
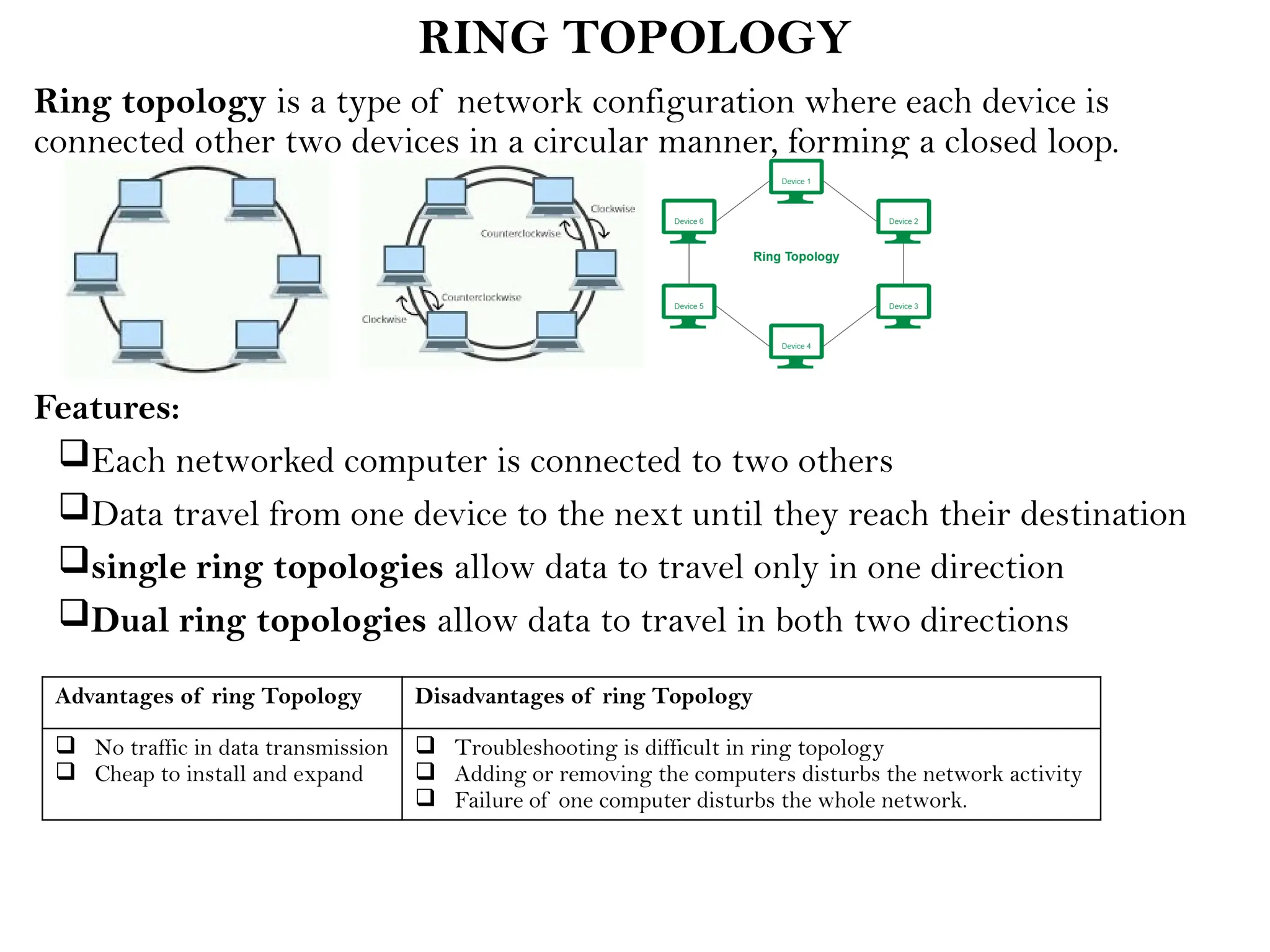
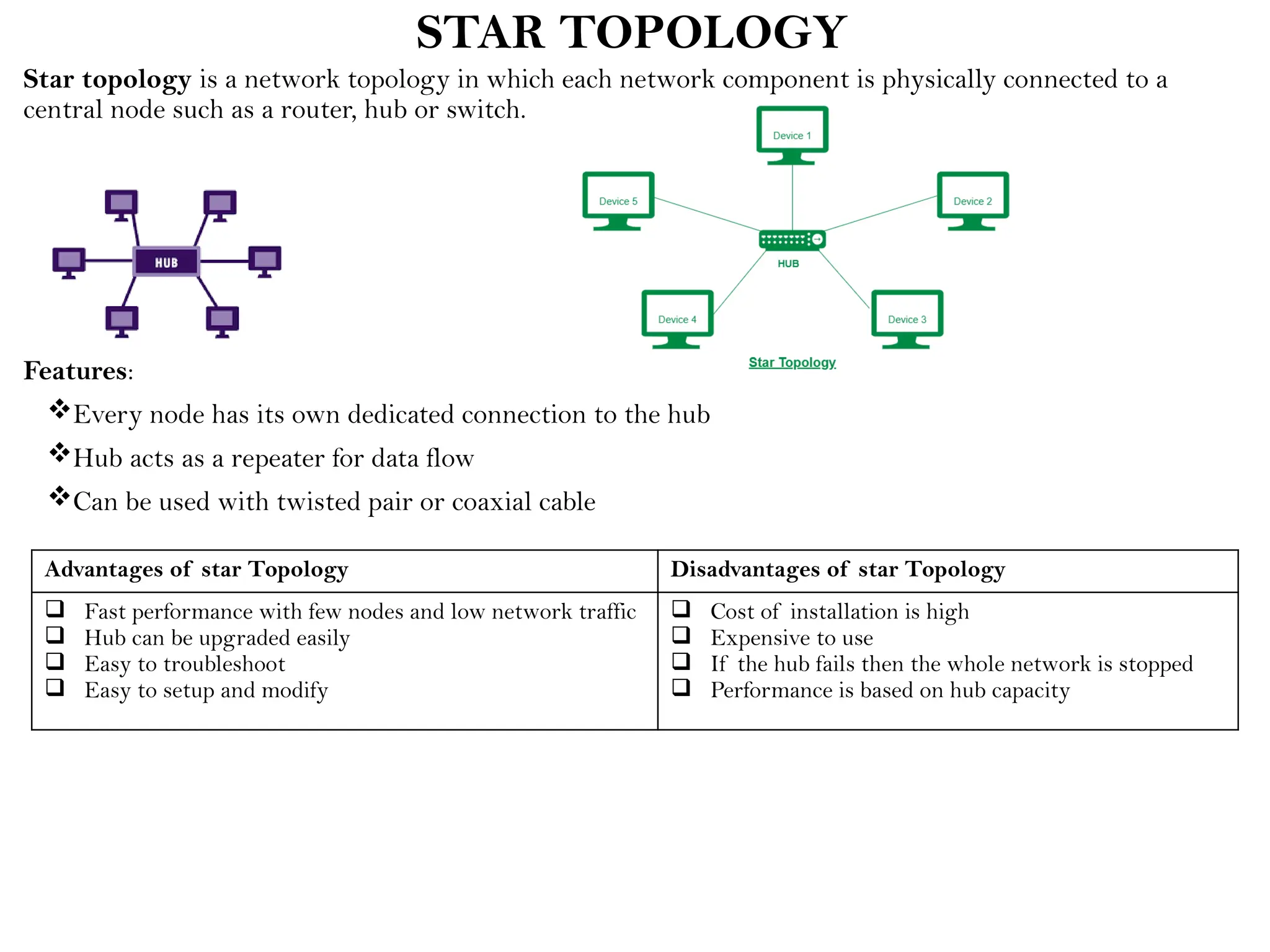
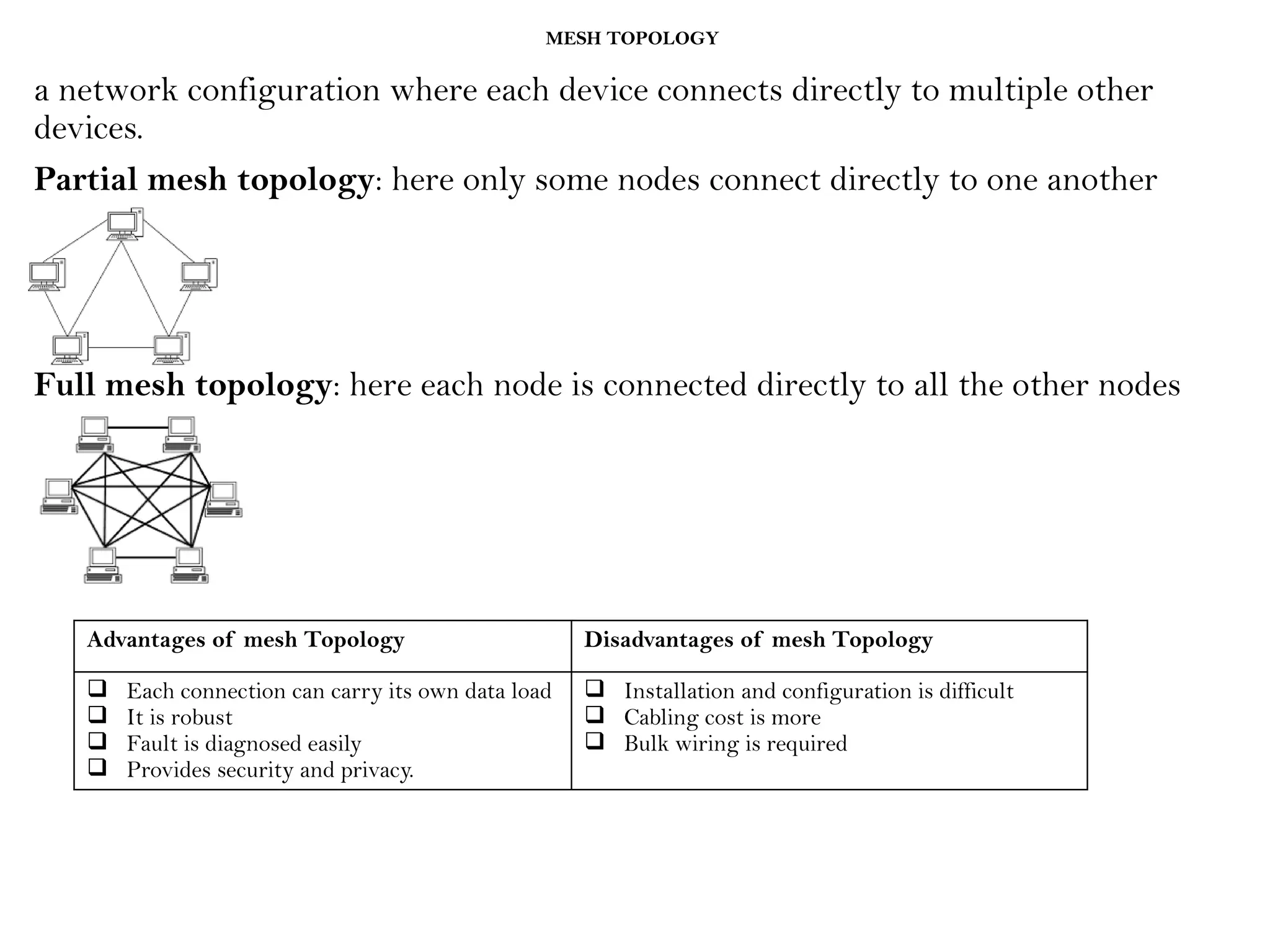
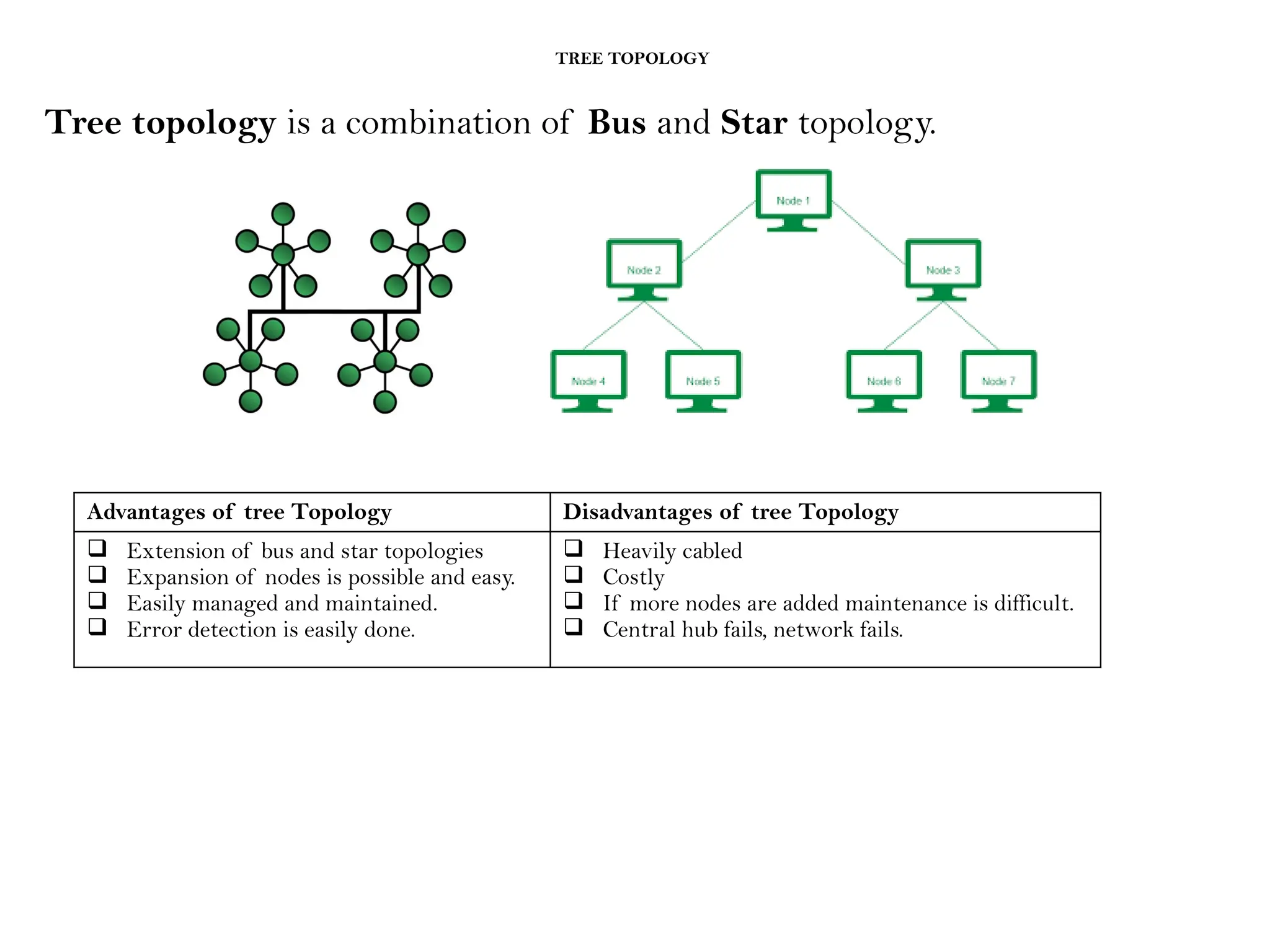
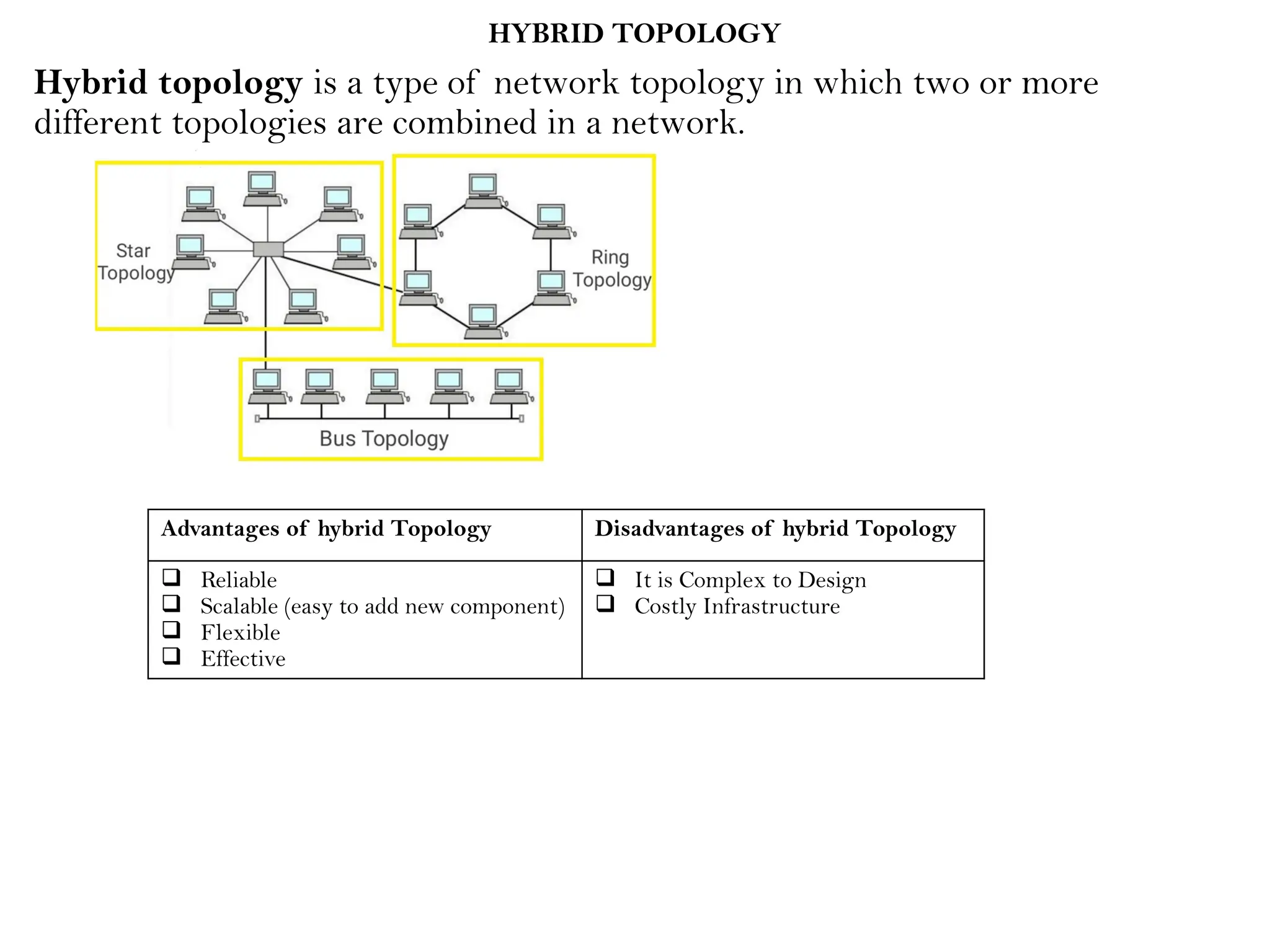
This document provides an overview of computer networks, detailing their types, properties, advantages, and disadvantages. It explains various components such as network devices, transmission media, and data transmission models, alongside discussing key technologies like Wi-Fi, Bluetooth, and cellular networks across different generations. Additionally, it touches on network metrics and the various types of networks including personal, local, metropolitan, and wide area networks.