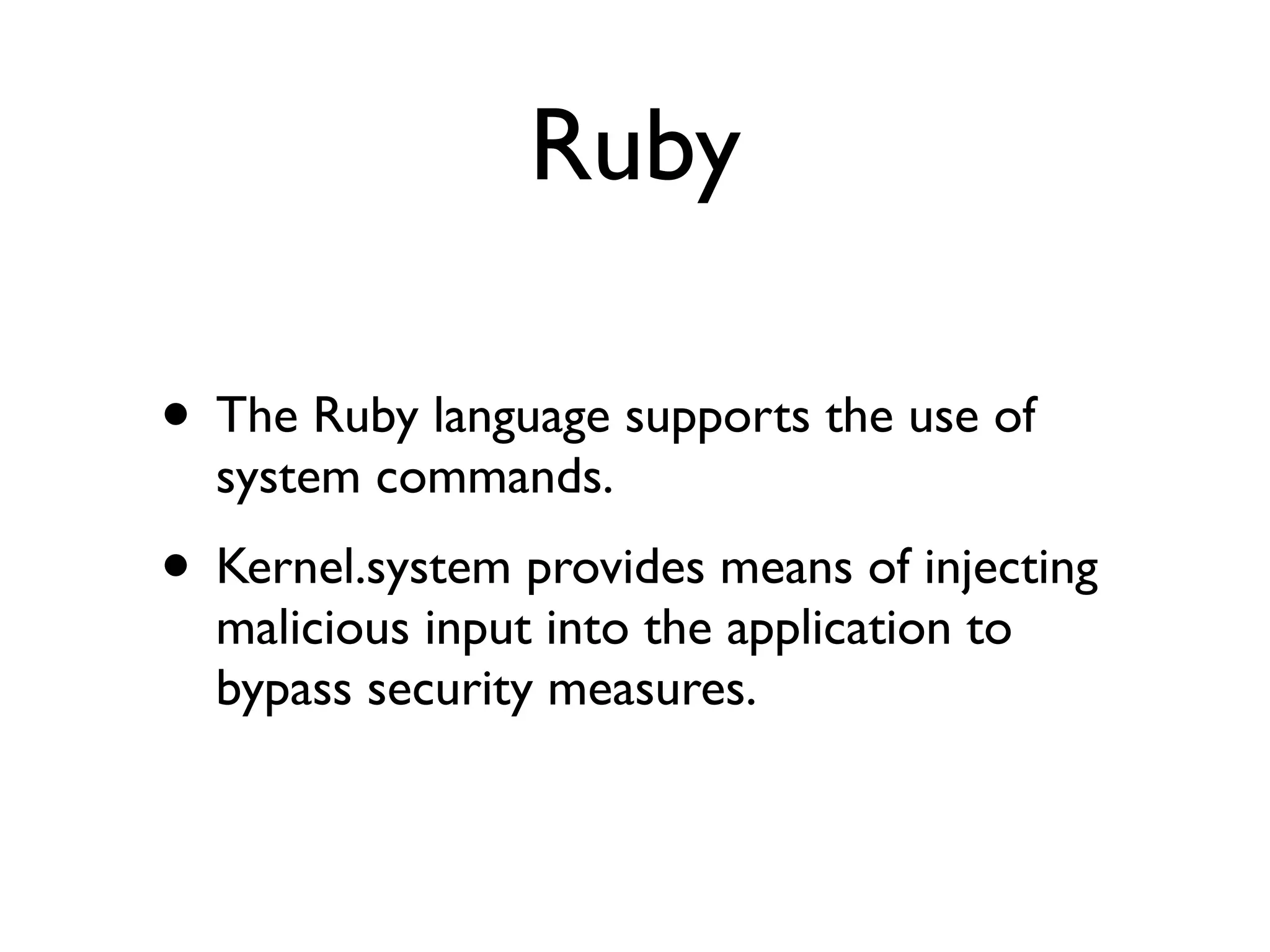
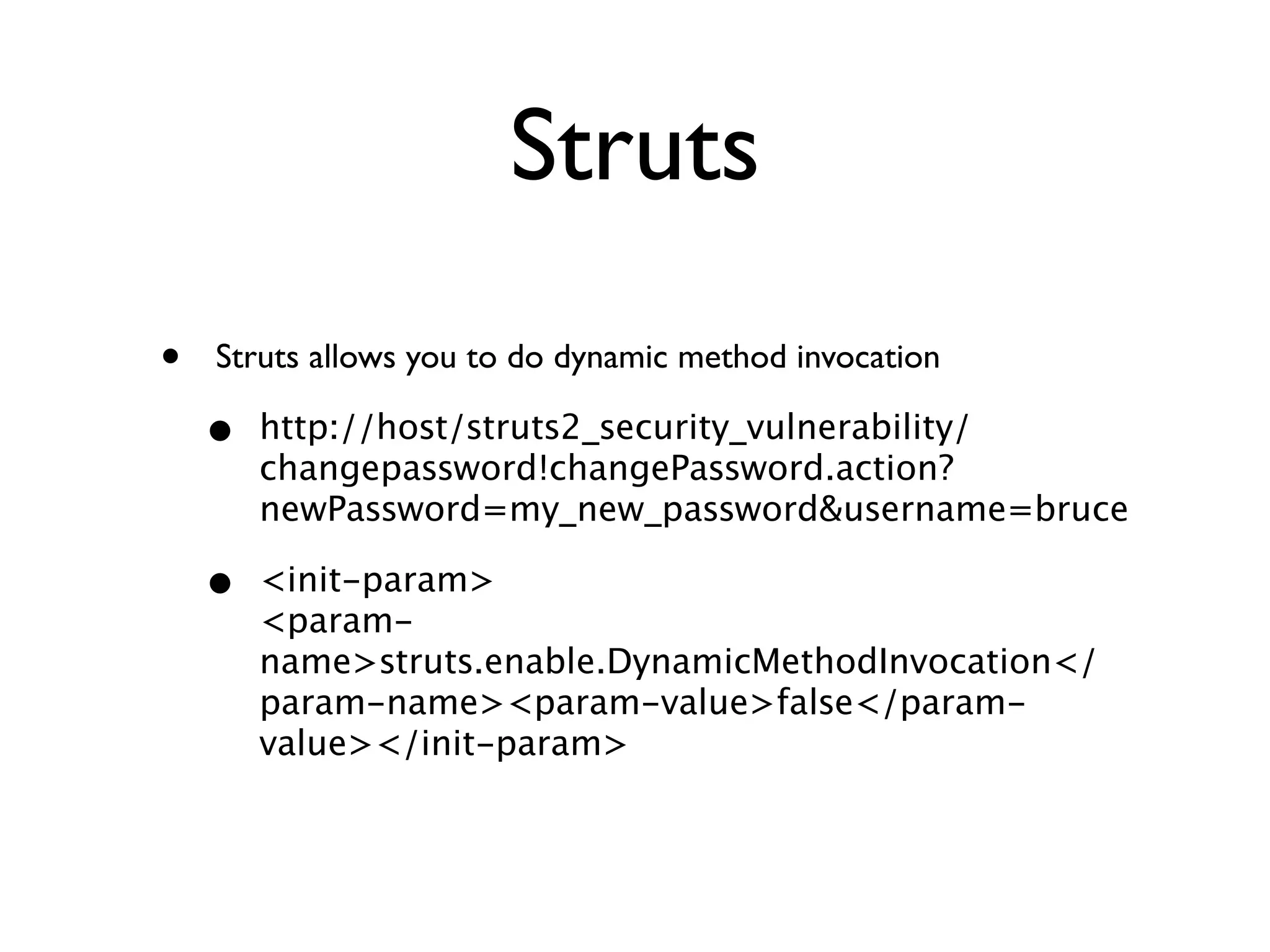
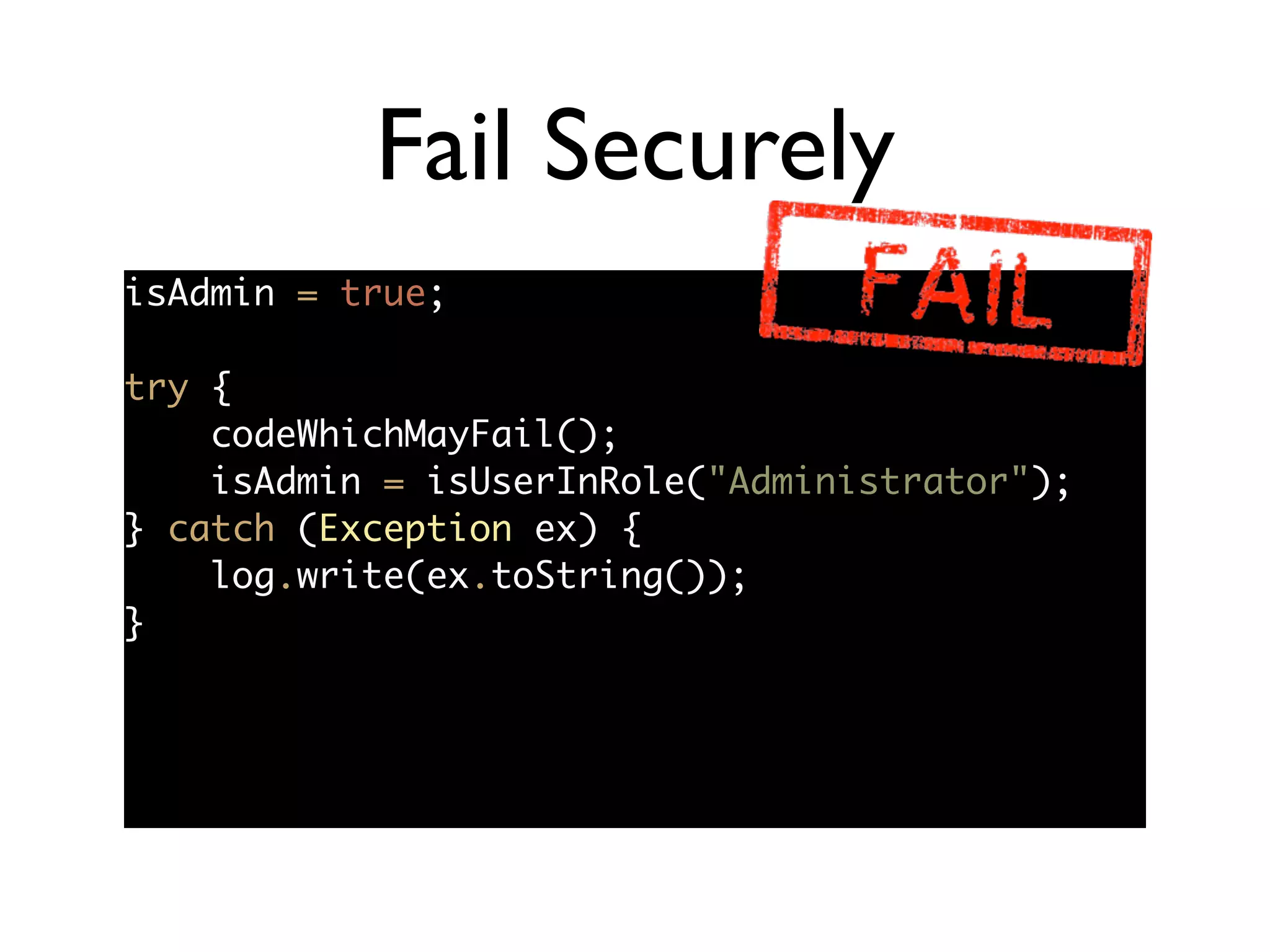
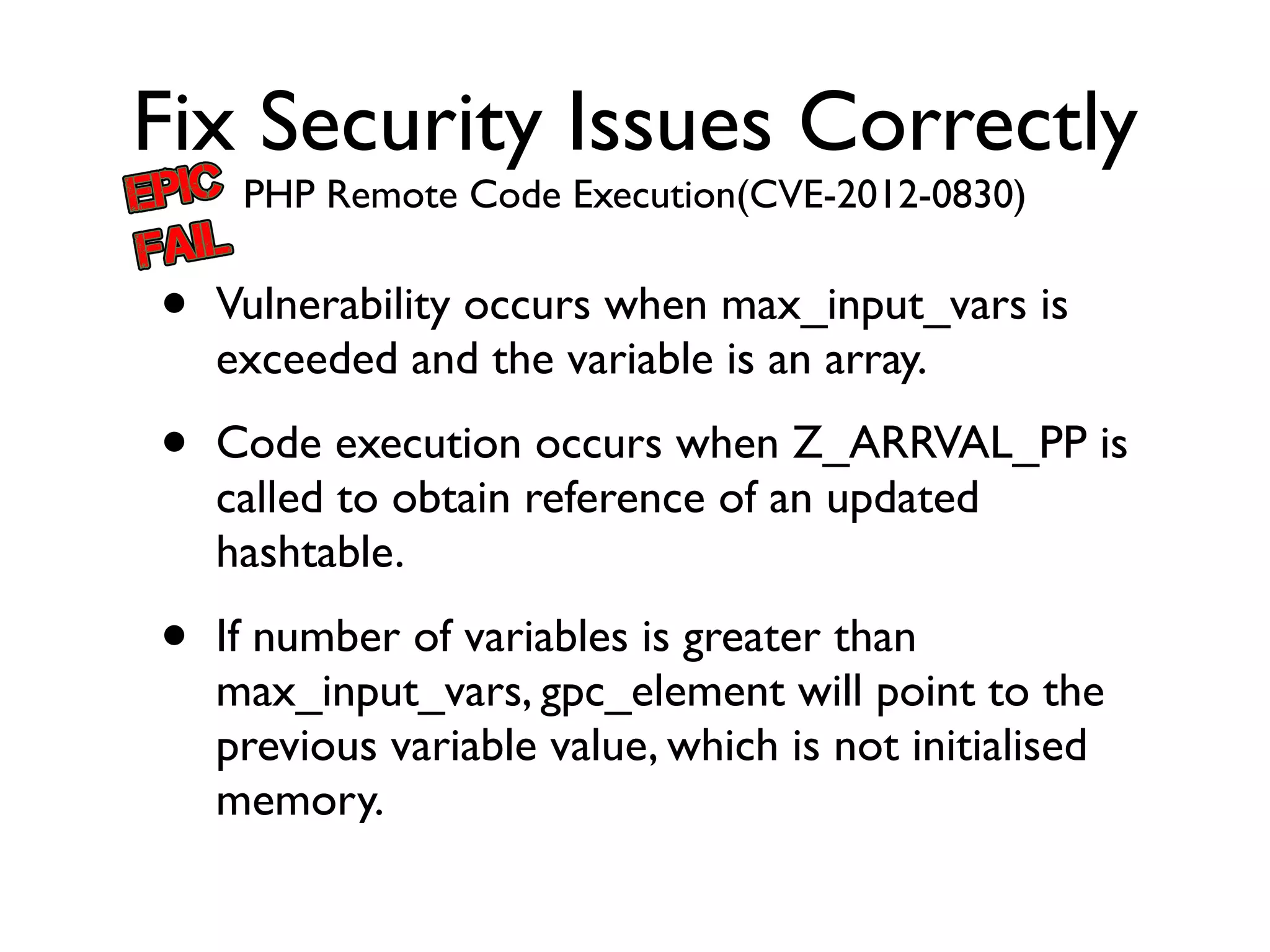
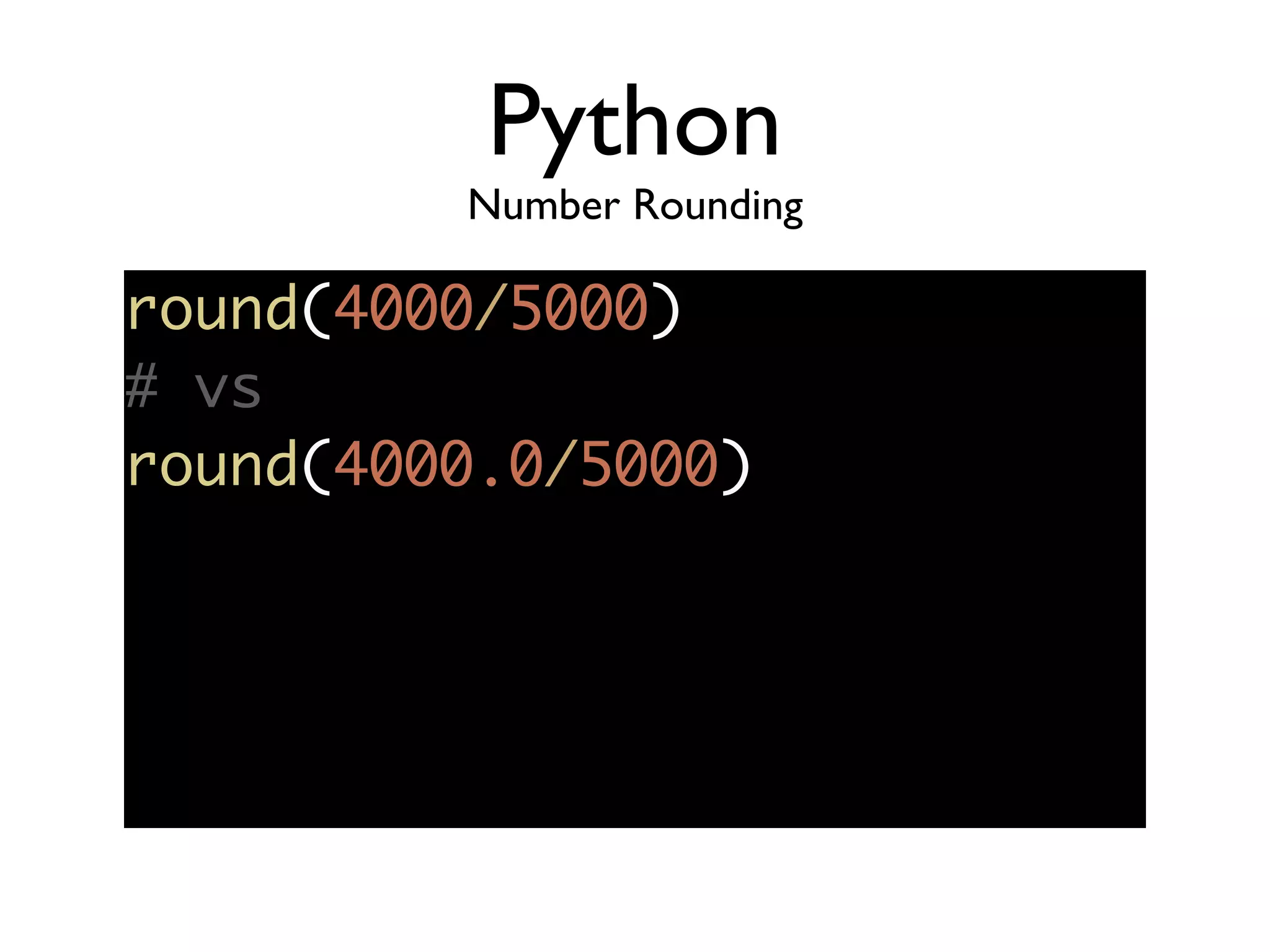
The document discusses secure coding principles and vulnerabilities in different programming languages. It provides examples of vulnerabilities in PHP, JavaScript, Ruby, Struts, and C. Key secure coding principles discussed include minimizing the attack surface, establishing secure defaults, least privilege, defense in depth, and failing securely. Specific vulnerabilities addressed include PHP hash collisions, PHP remote code execution, JavaScript type issues, Ruby system commands, and Struts dynamic method invocation.




















![JavaScript
Types Differences
{} + {} = NaN
{} + [] = 0
[] + {} = "[object Object]"
[] + [] = ""
{} - 1 = -1
[] - 1 = -1
-1 + {} = "-1[object Object]"
-1 + [] = "-1"](https://image.slidesharecdn.com/sc3-140725125400-phpapp02/75/Secure-Coding-Web-Application-Security-Vulnerabilities-and-Best-Practices-32-2048.jpg)
![JavaScript
Obfuscation
$=~[];$={___:++$,$$$$:(![]+"")[$],__$:++$,$_$_:(![]+"")
[$],_$_:++$,$_$$:({}+"")[$],$$_$:($[$]+"")[$],_$$:++$,$$
$_:(!""+"")[$],$__:++$,$_$:++$,$$__:({}+"")[$],$$_:++$,$$
$:++$,$___:++$,$__$:++$};$.$_=($.$_=$+"")[$.$_$]+($._$=$.
$_[$.__$])+($.$$=($.$+"")[$.__$])+((!$)+"")[$._$$]+($.__=
$.$_[$.$$_])+($.$=(!""+"")[$.__$])+($._=(!""+"")[$._$_])+
$.$_[$.$_$]+$.__+$._$+$.$;$.$$=$.$+(!""+"")[$._$$]+$.__+
$._+$.$+$.$$;$.$=($.___)[$.$_][$.$_];$.$($.$($.$$+"""+$.
$_$_+(![]+"")[$._$_]+$.$$$_+""+$.__$+$.$$_+$._$_+$.__
+"("+$.__$+""+$.$__+$.___+")"+""")())();
!
// equal to
!
alert(1);](https://image.slidesharecdn.com/sc3-140725125400-phpapp02/75/Secure-Coding-Web-Application-Security-Vulnerabilities-and-Best-Practices-33-2048.jpg)