Downloaded 165 times





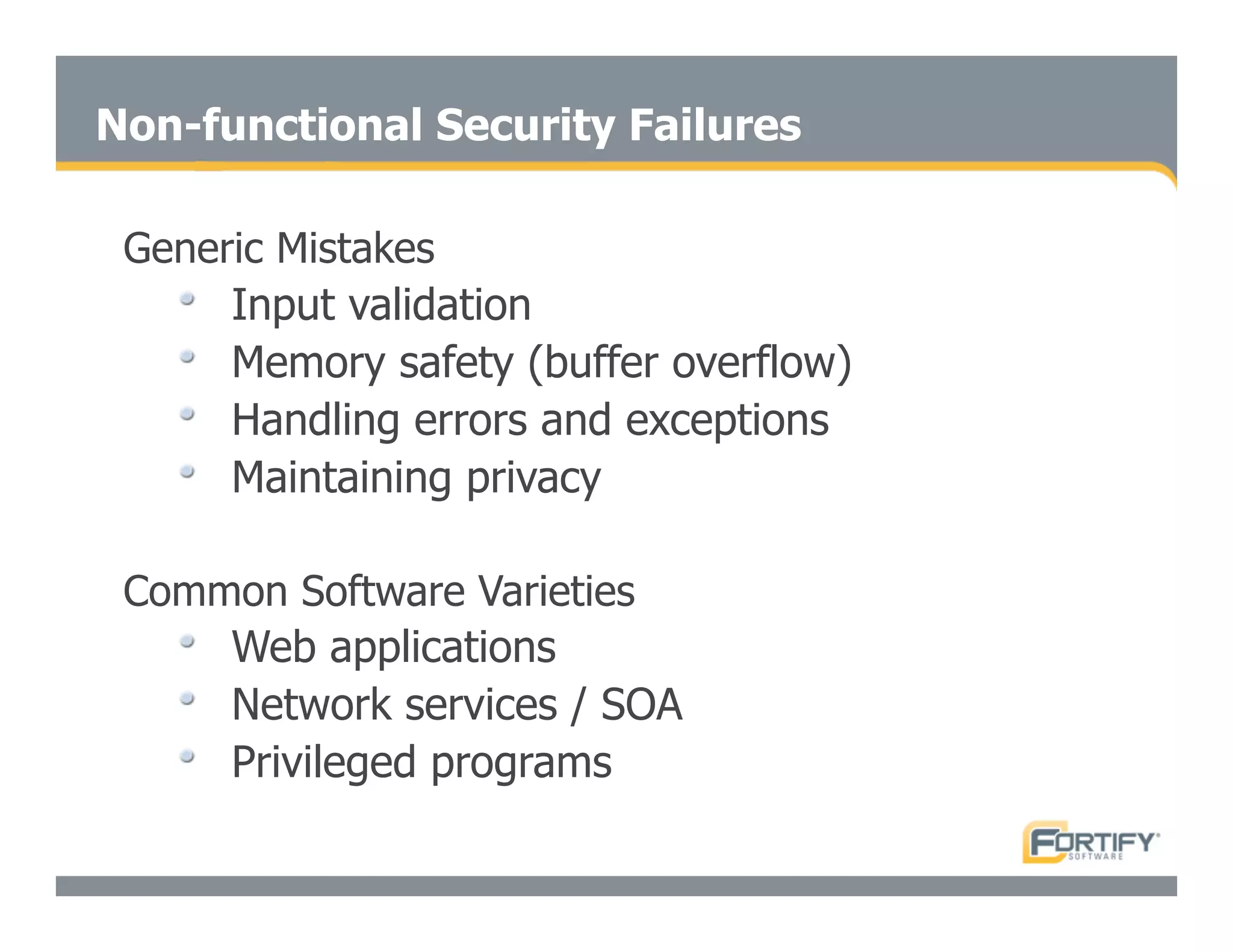
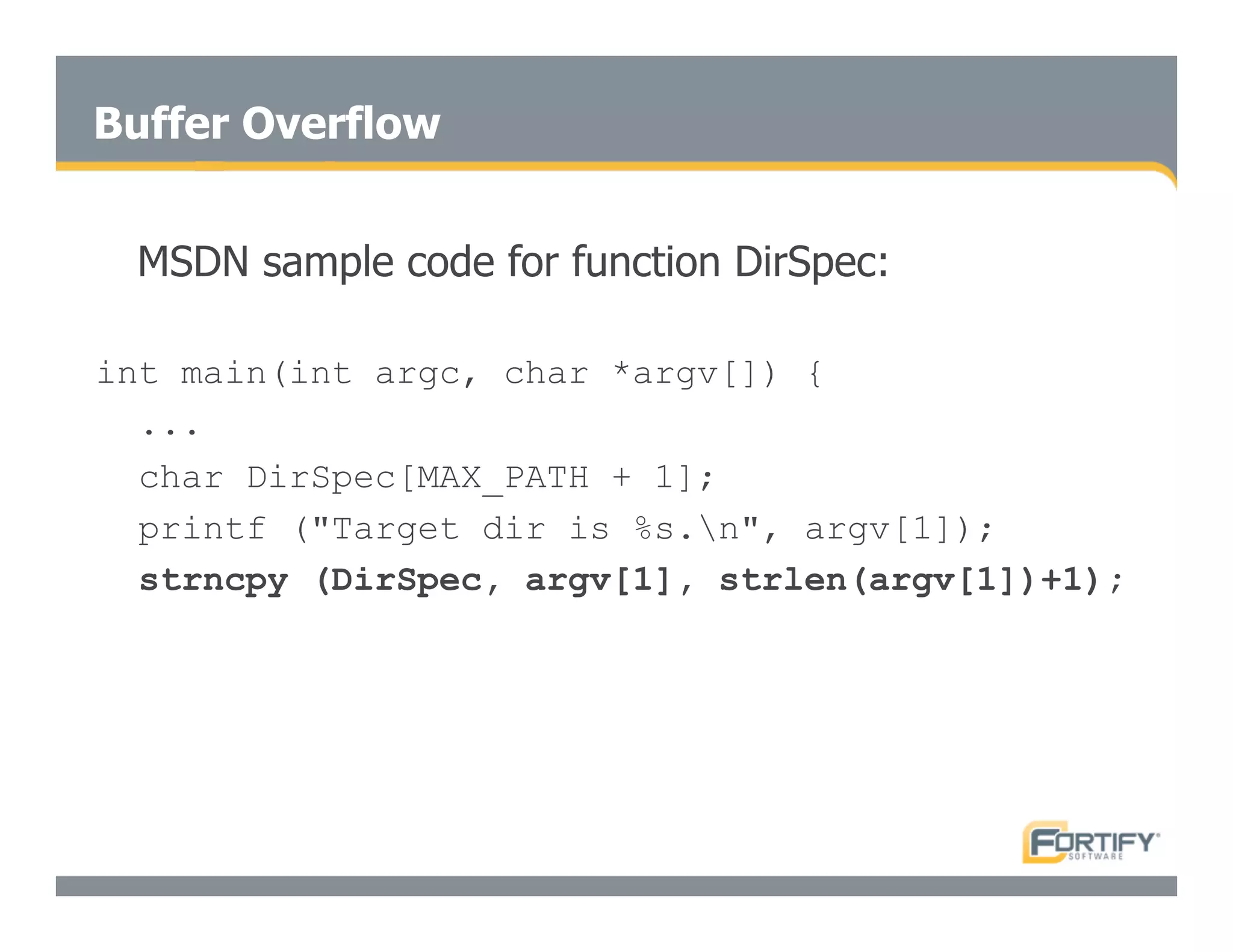
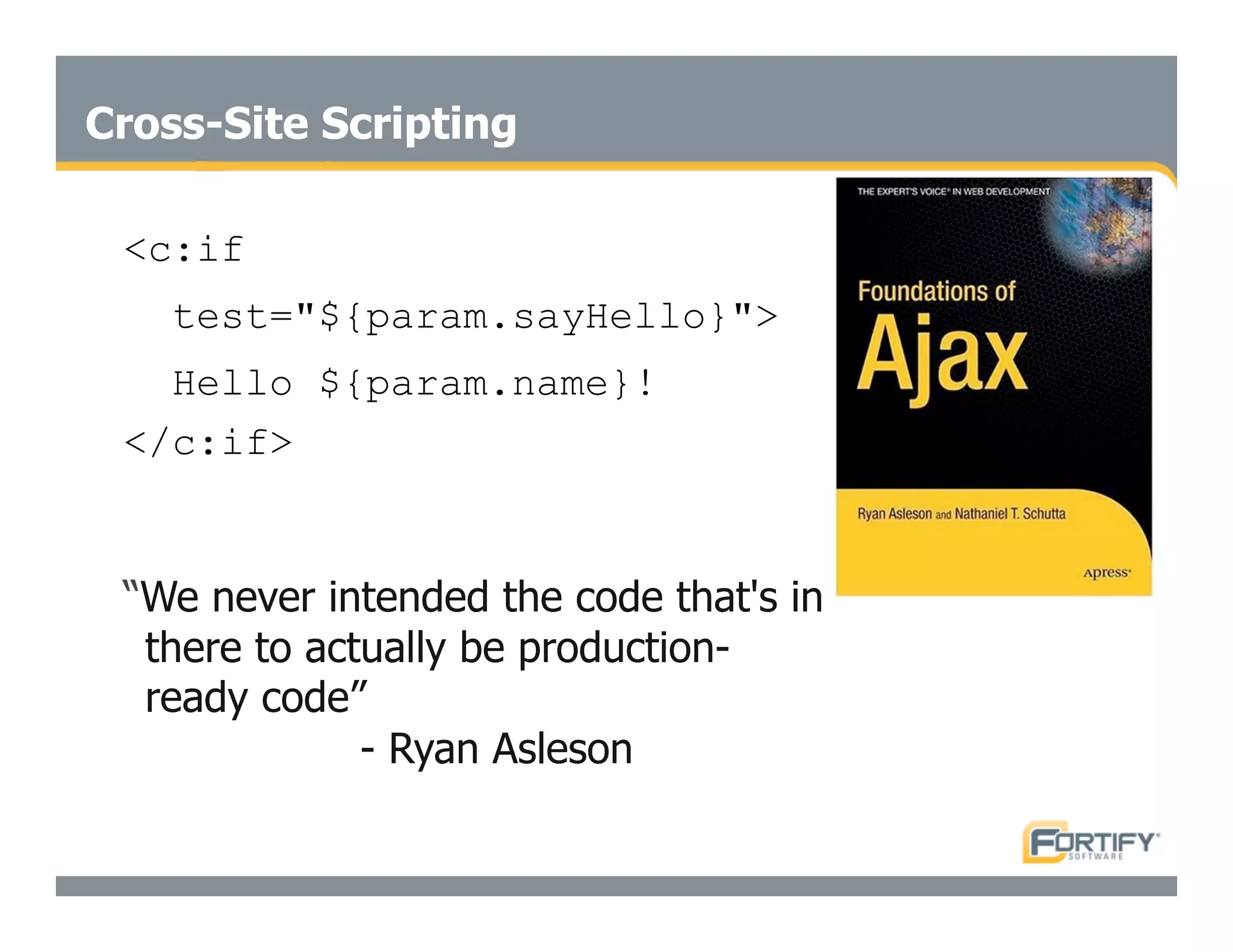
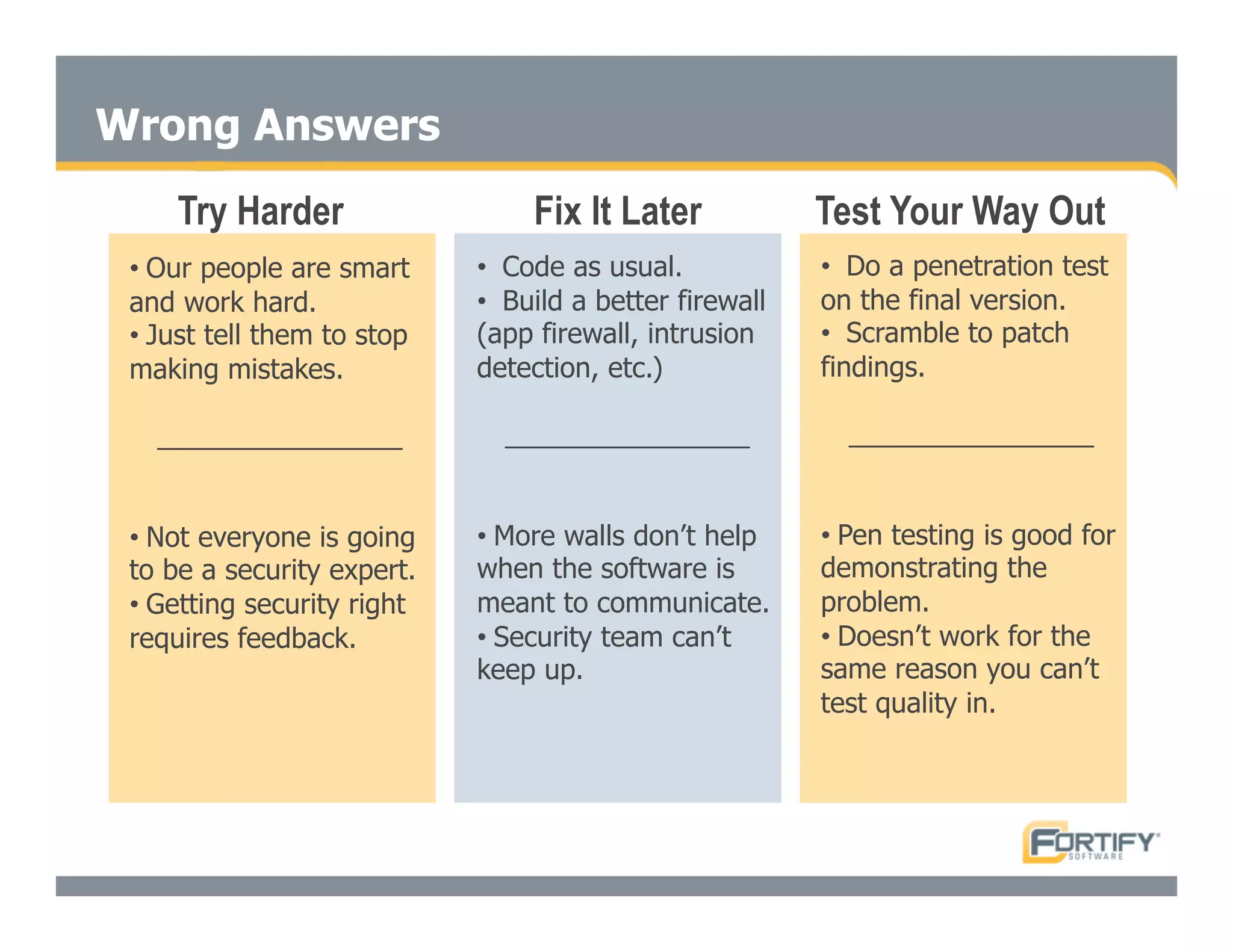
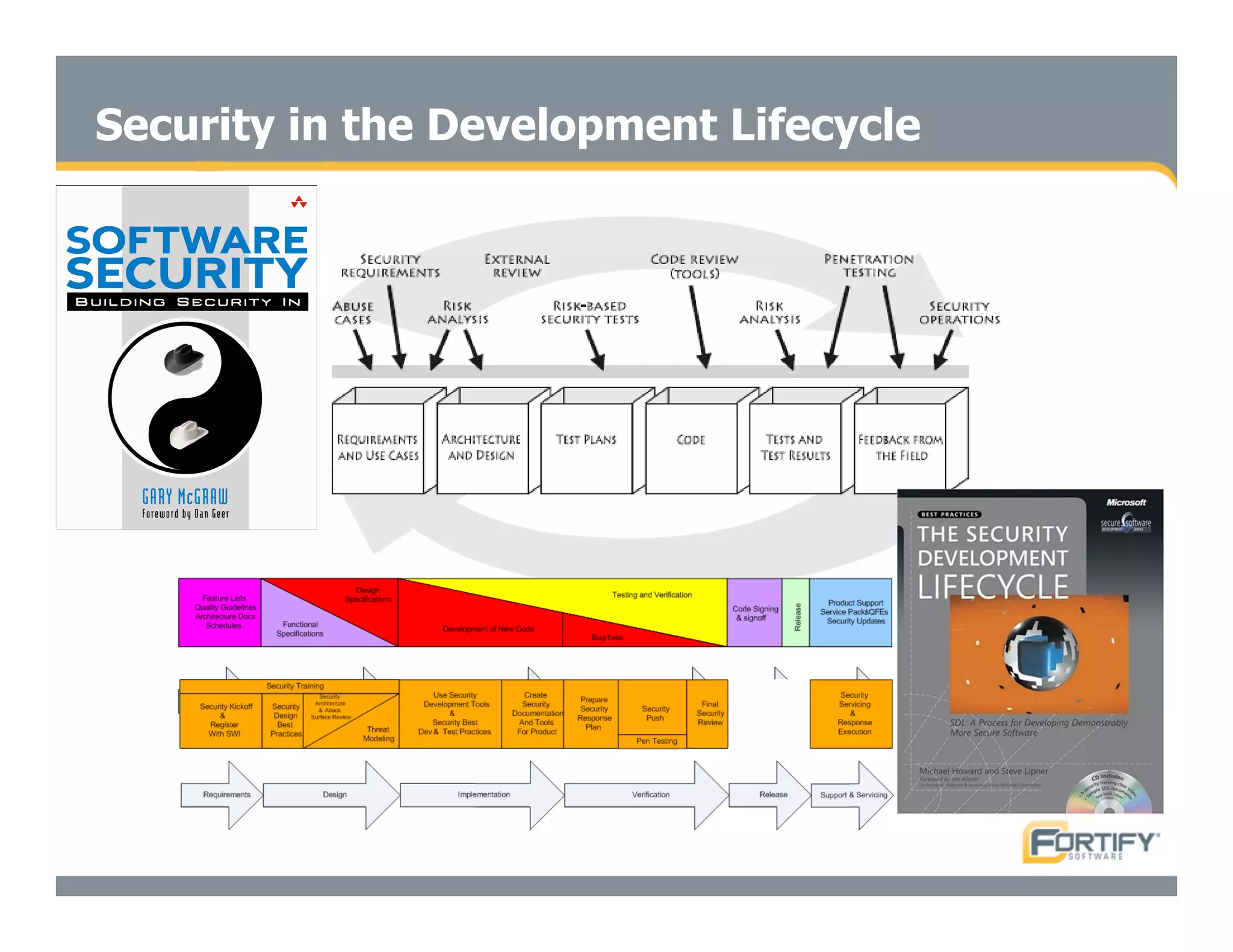
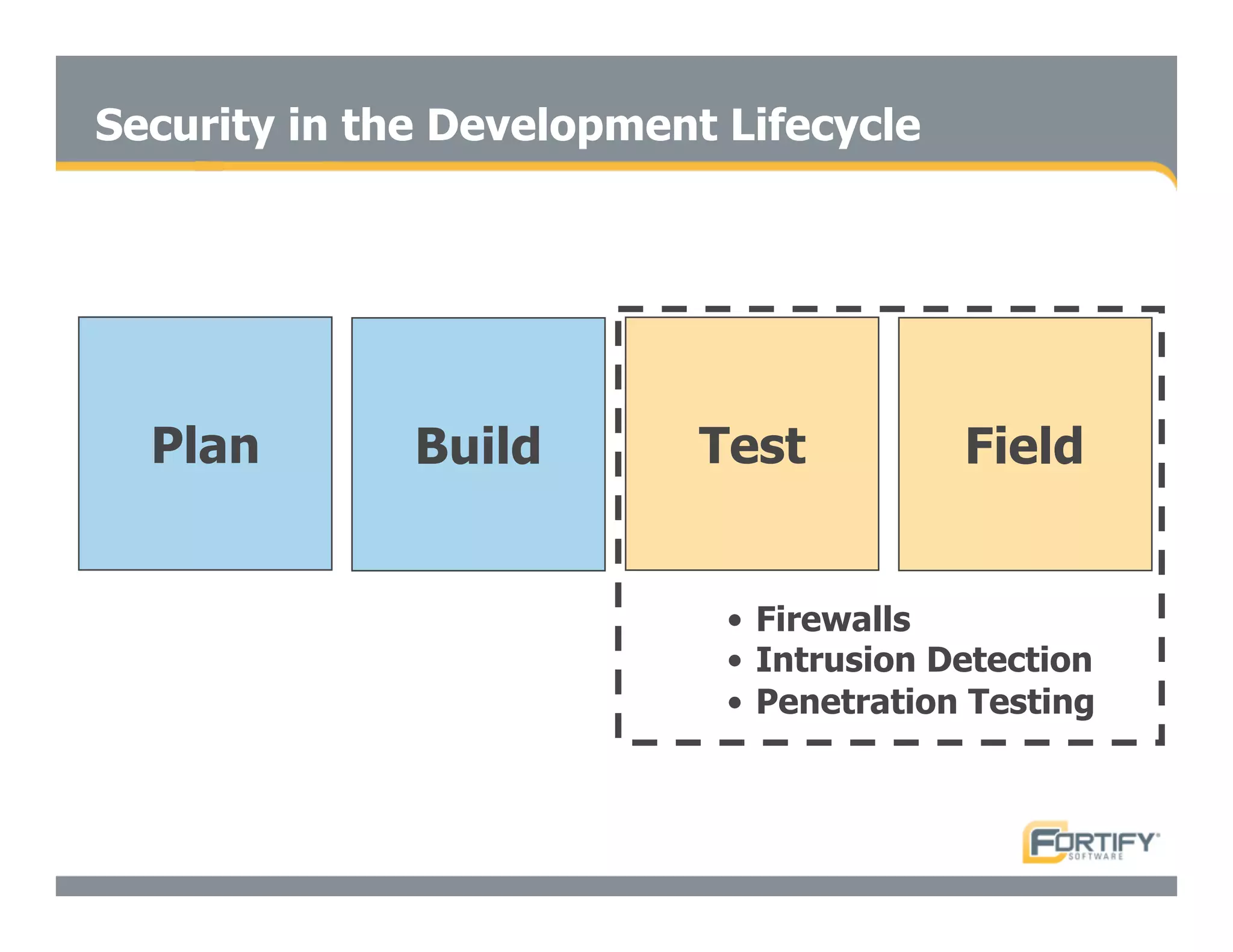
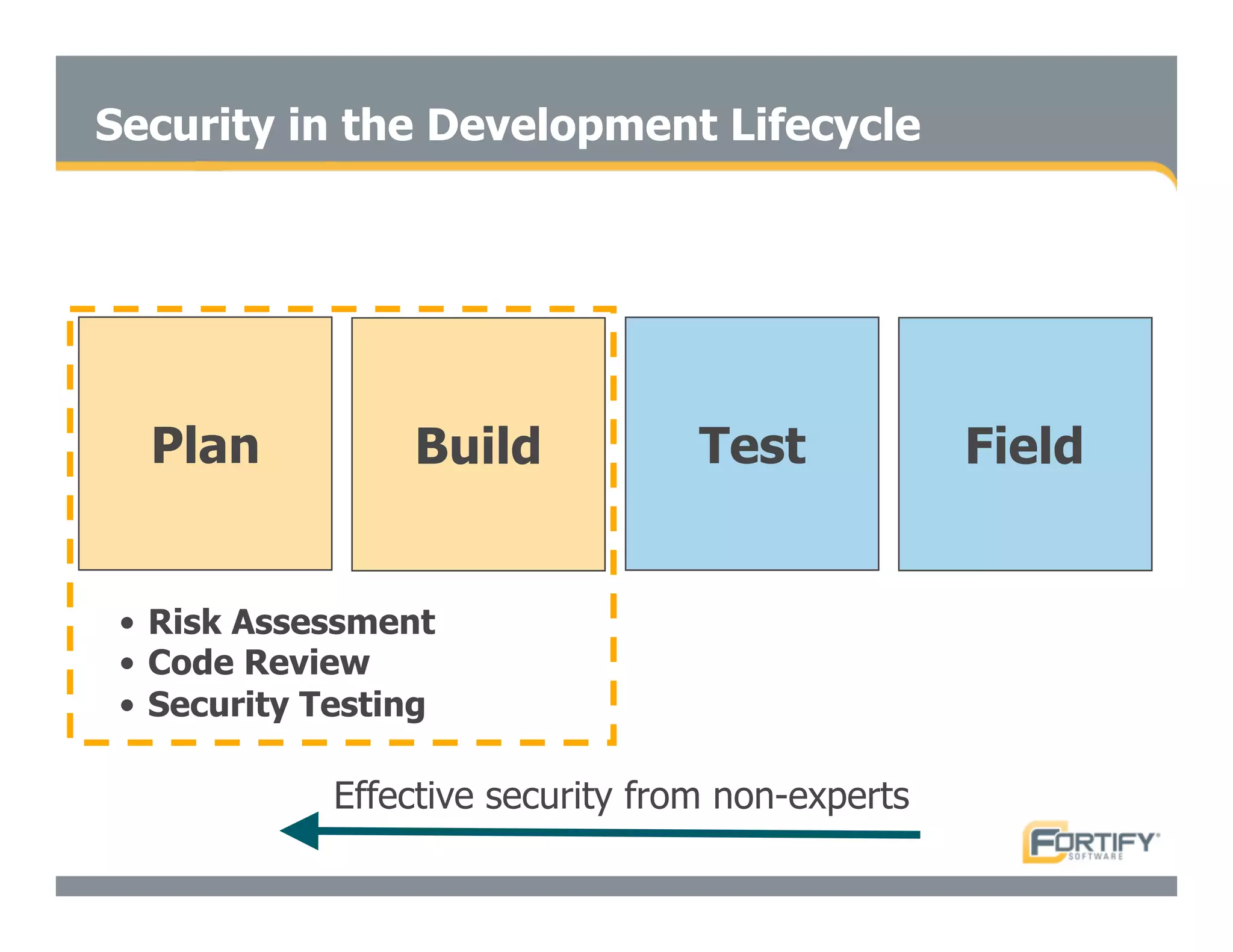


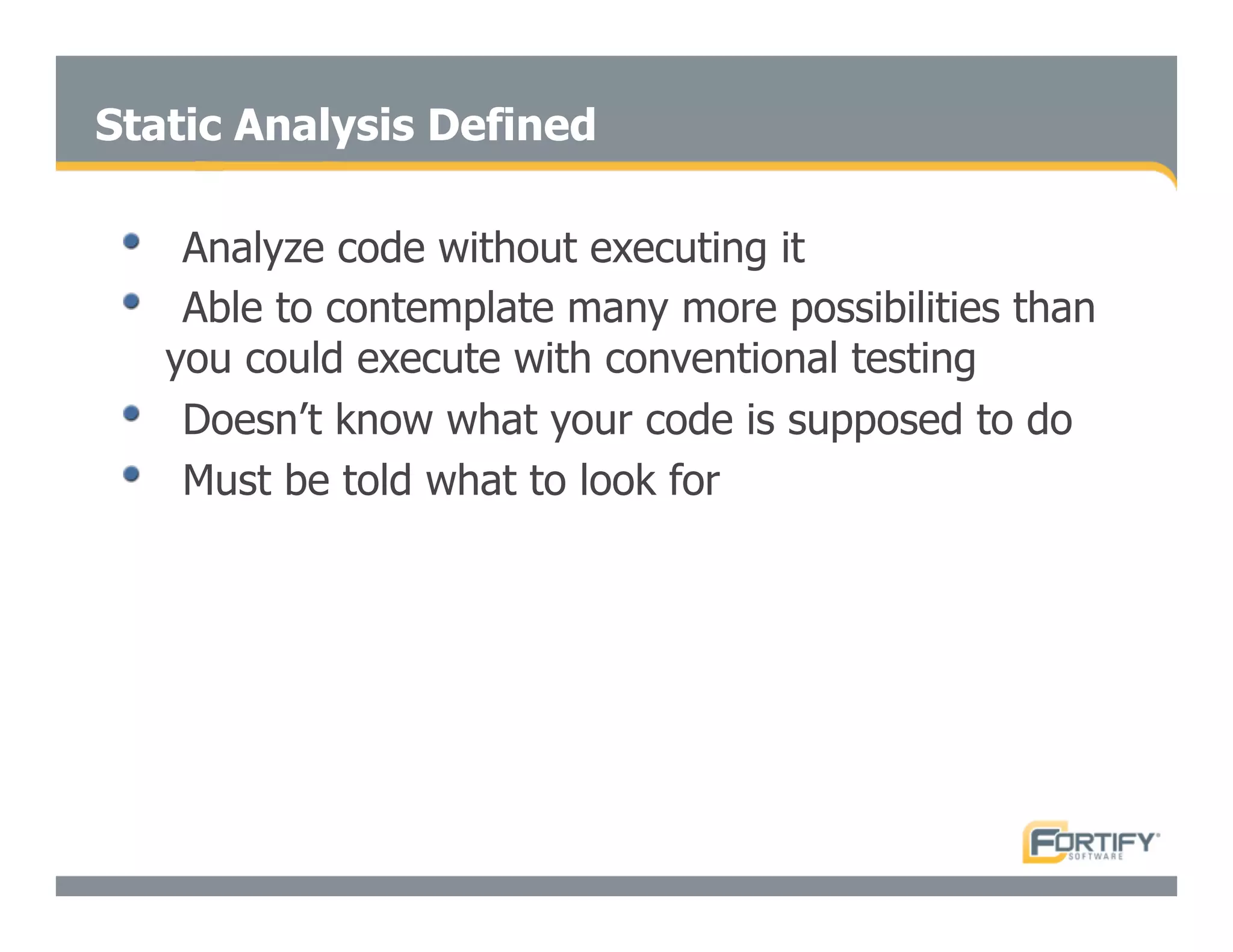


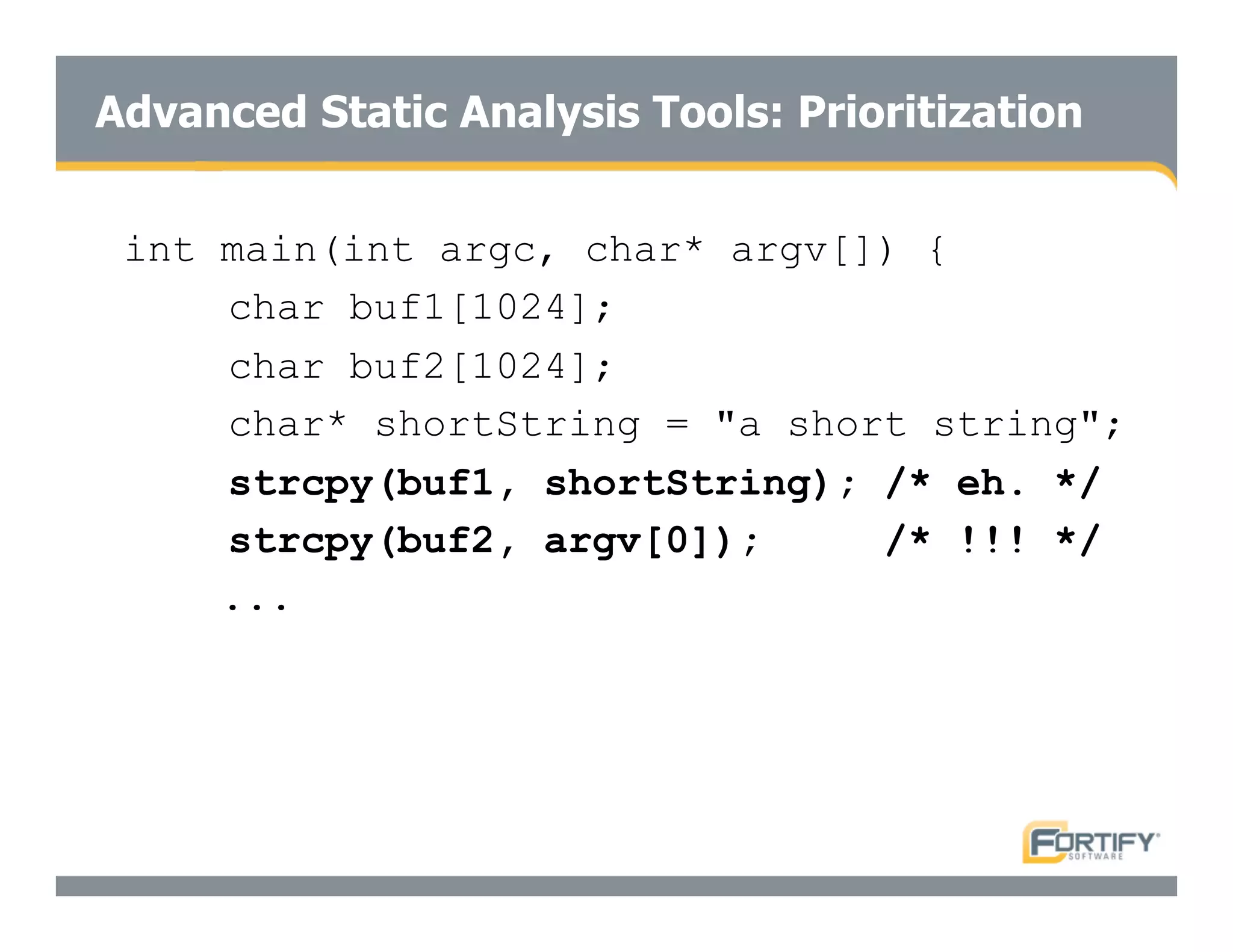

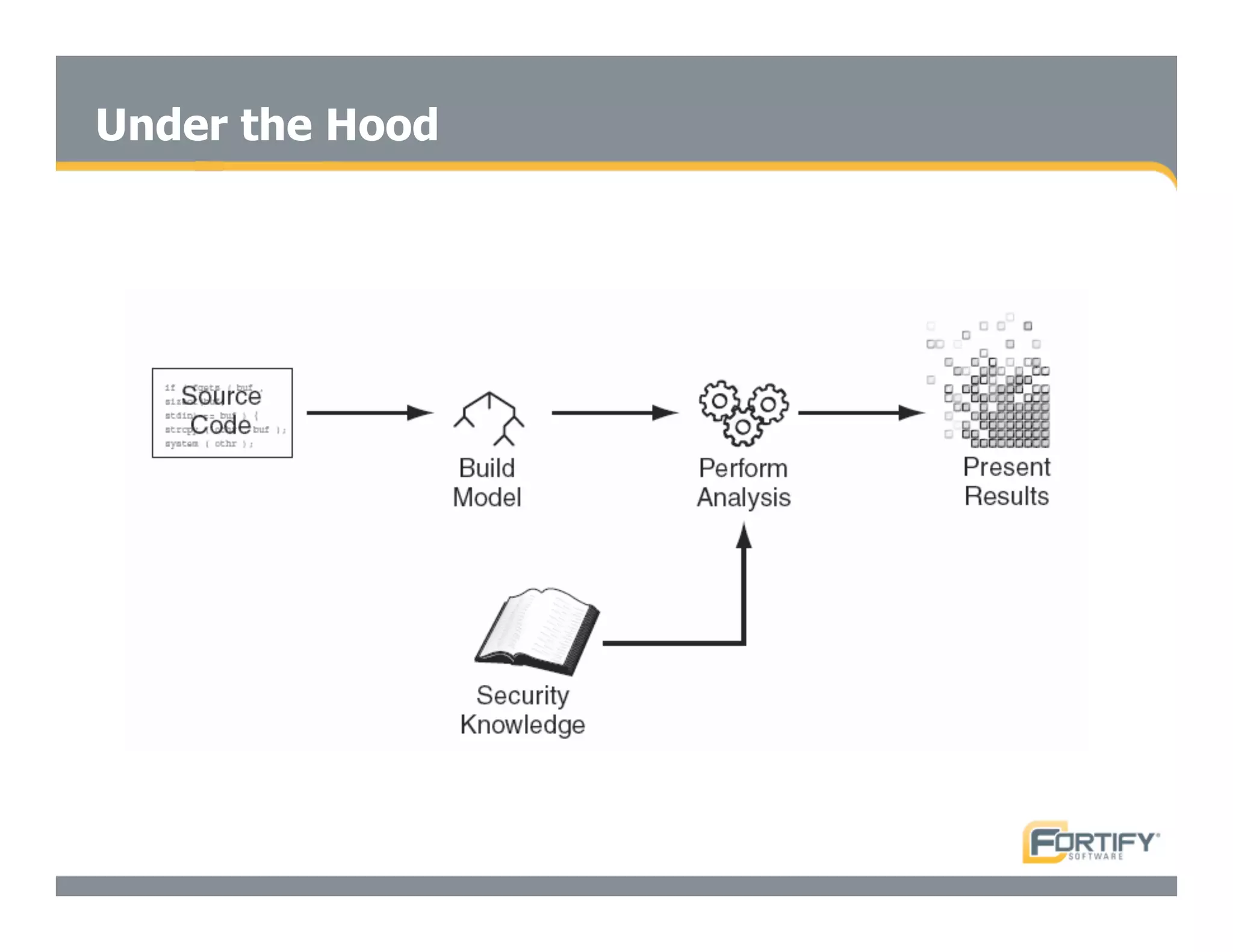
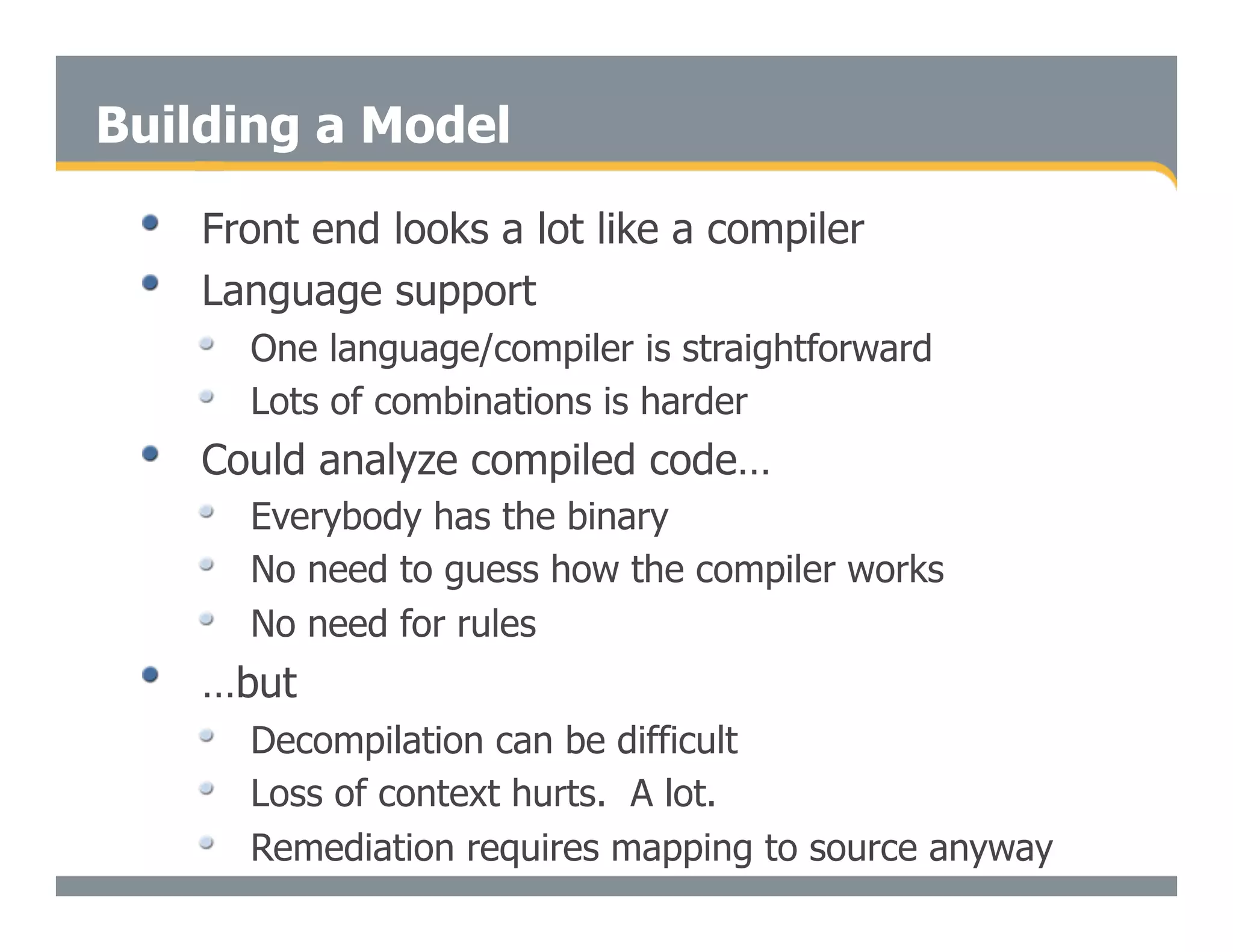
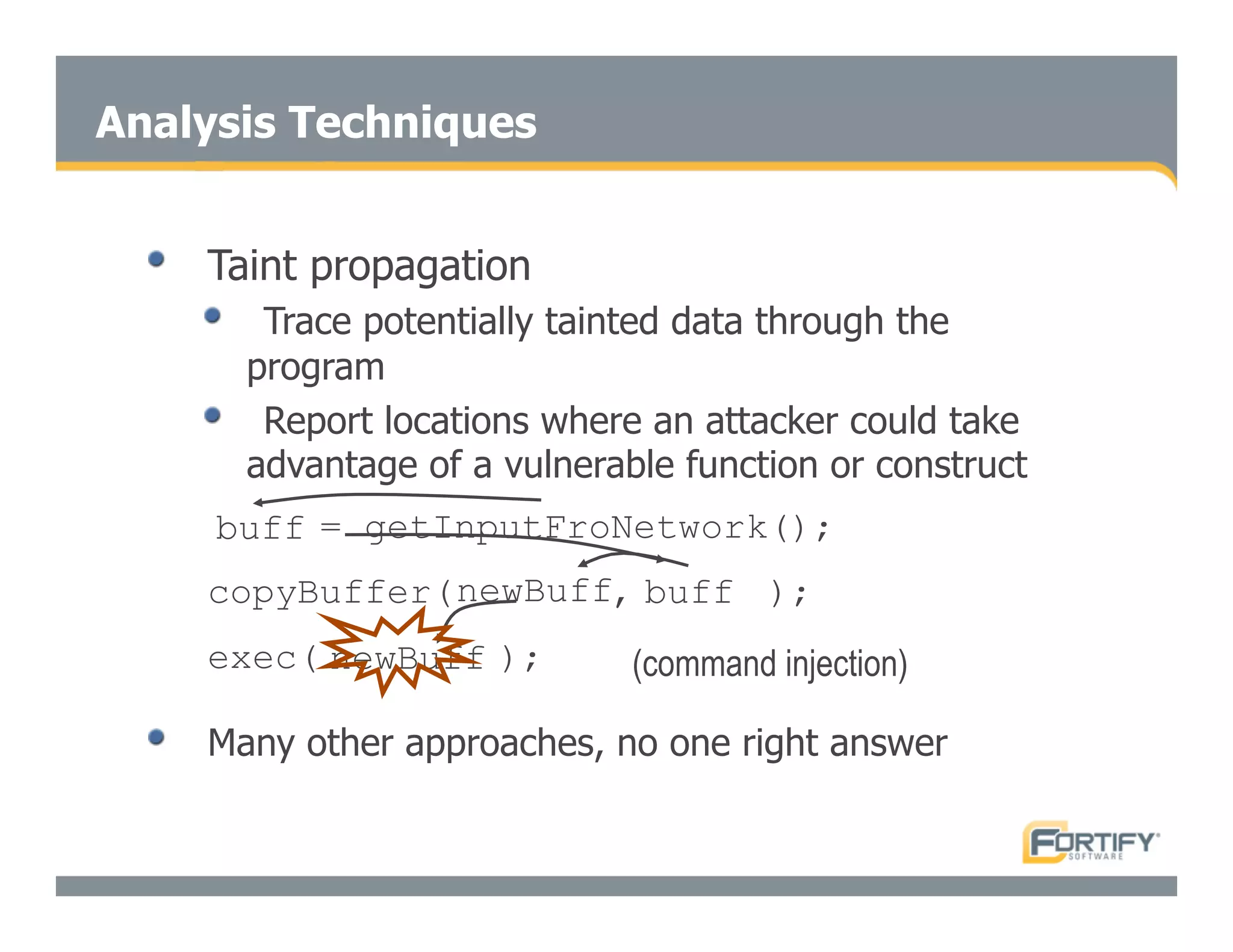
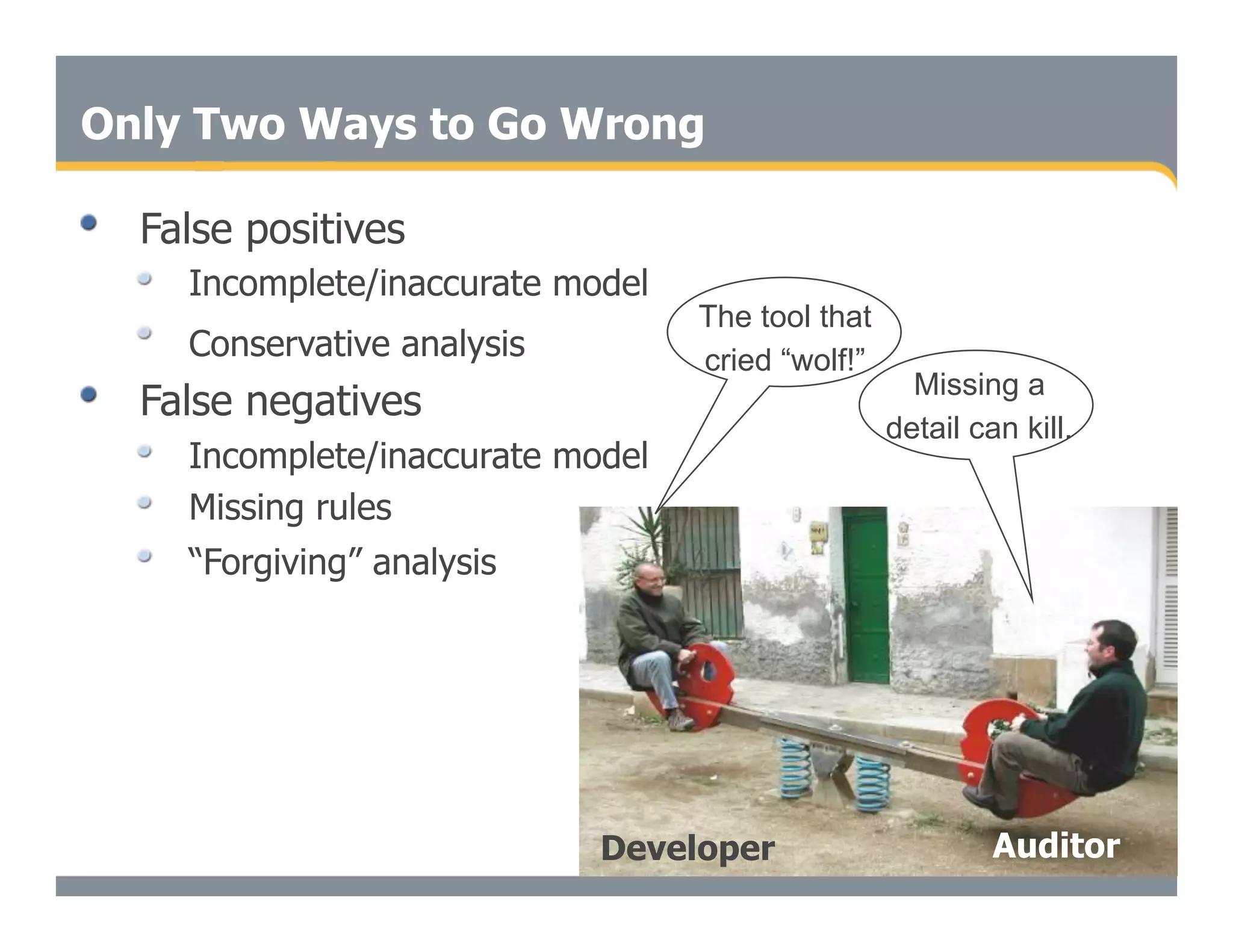
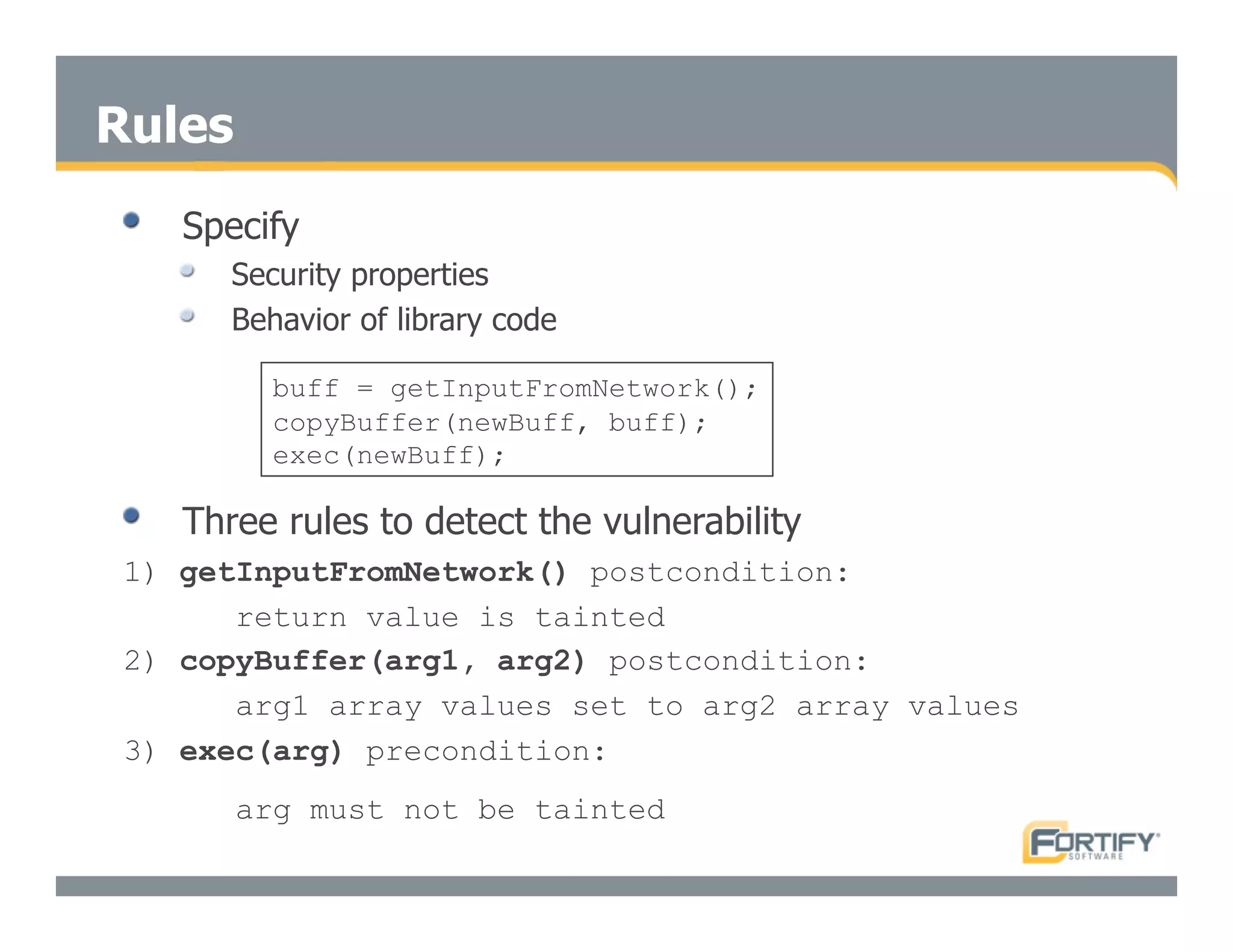
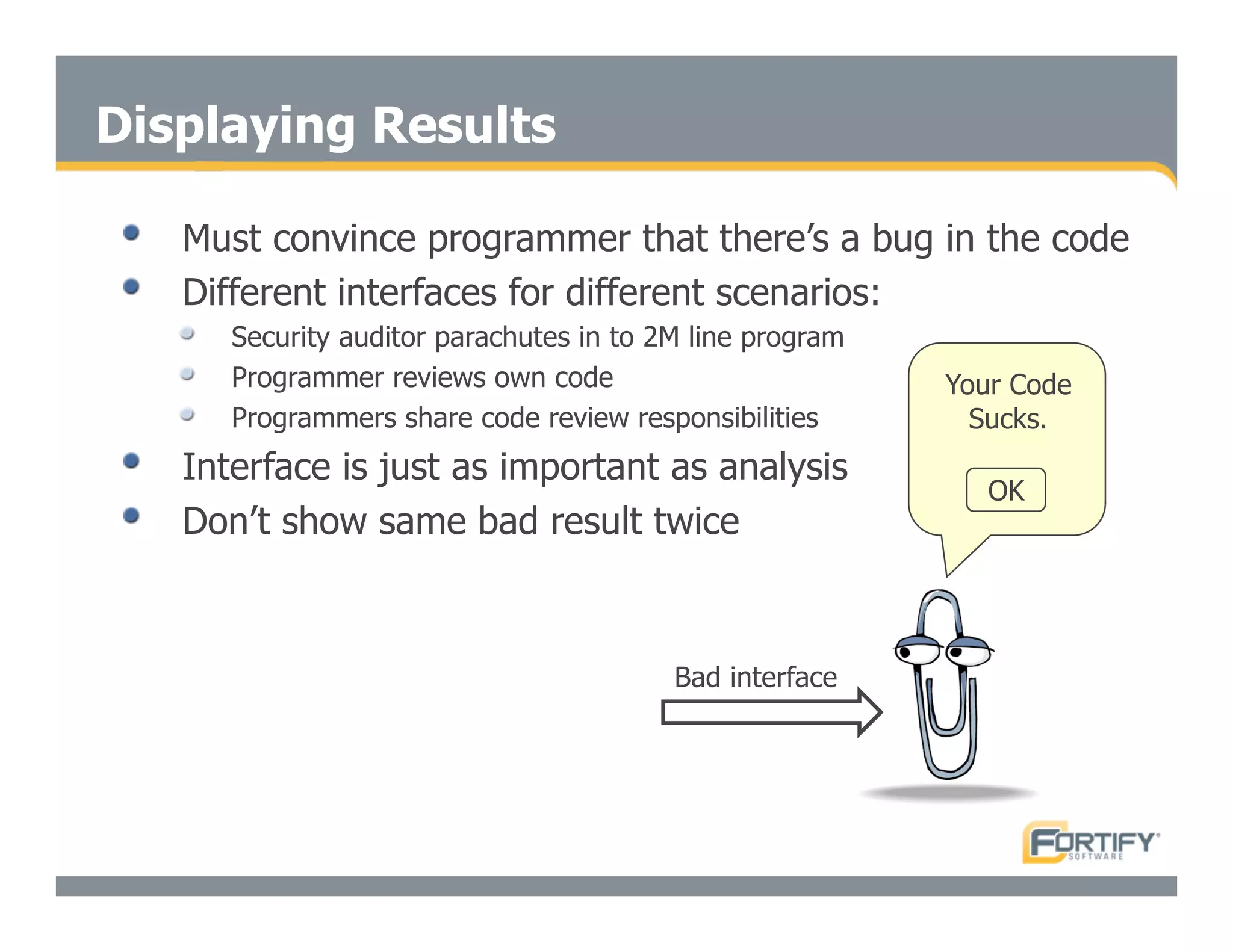



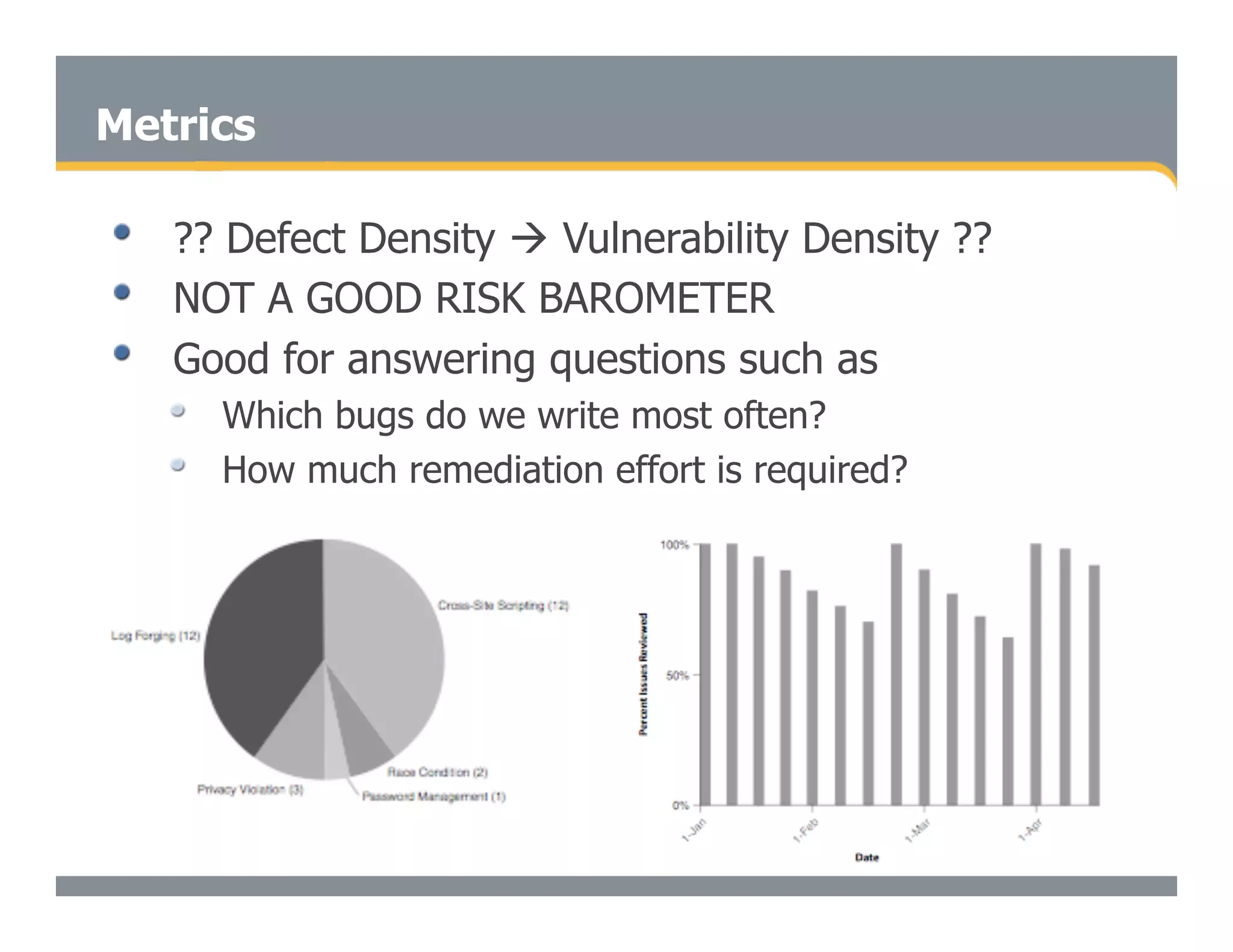
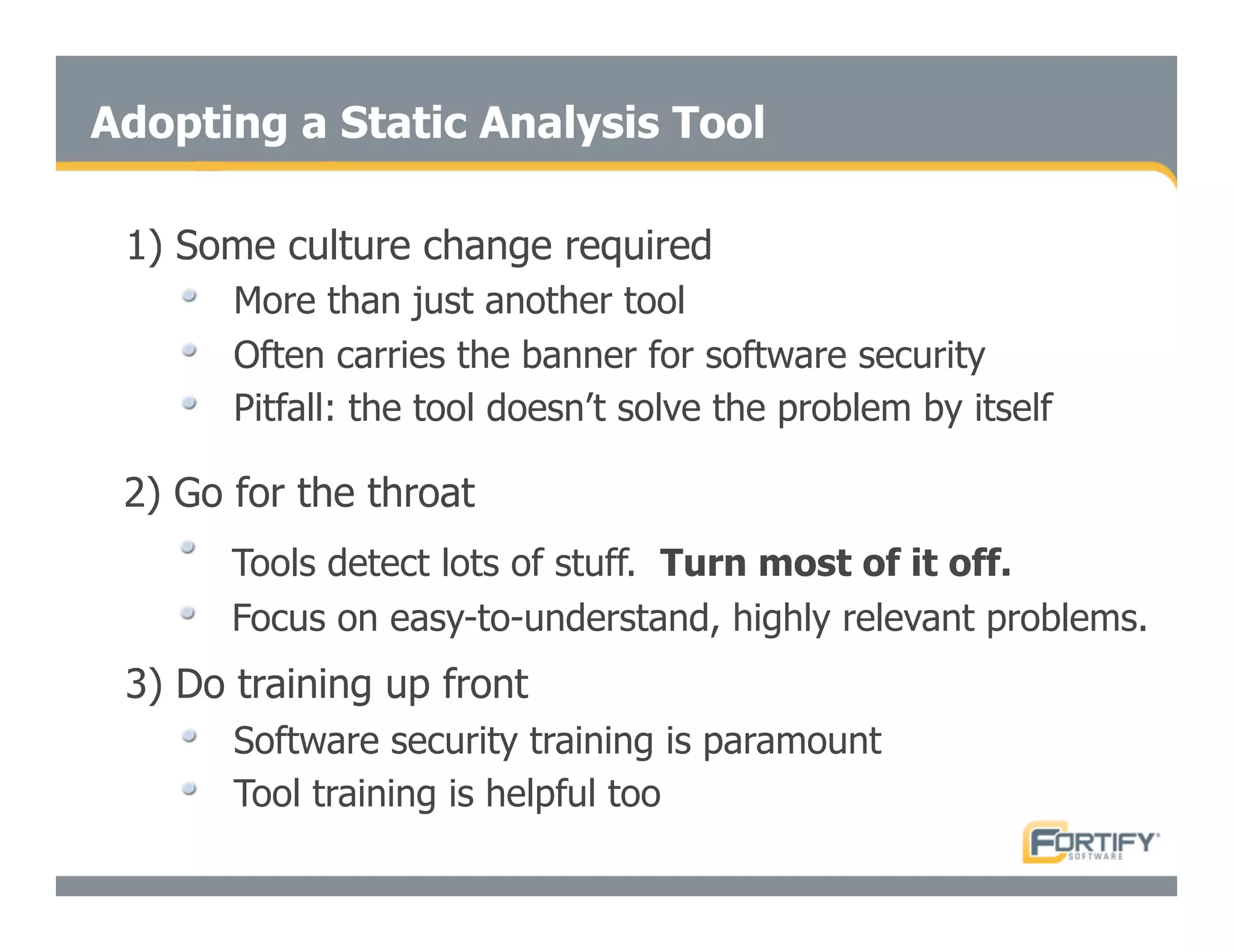
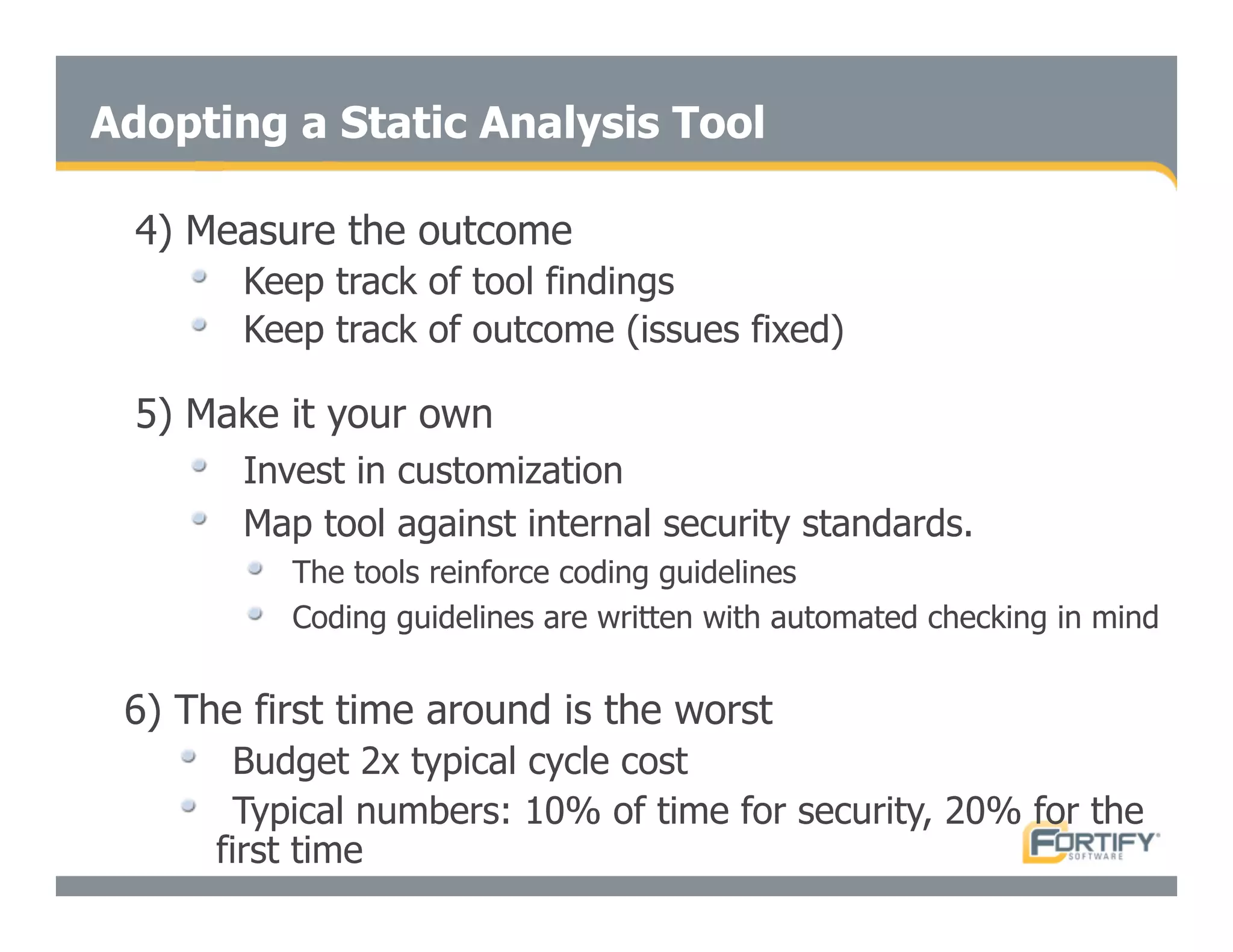



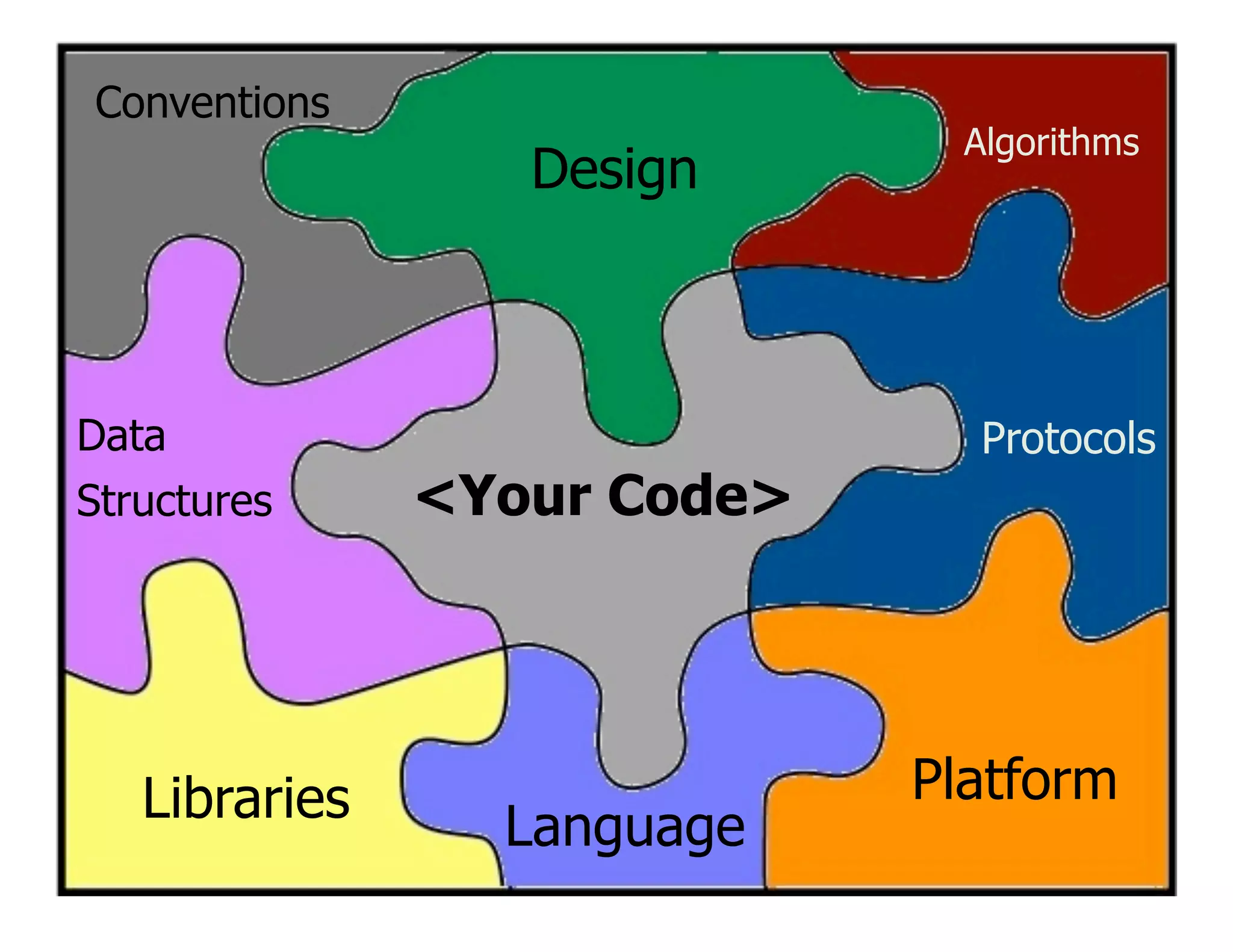
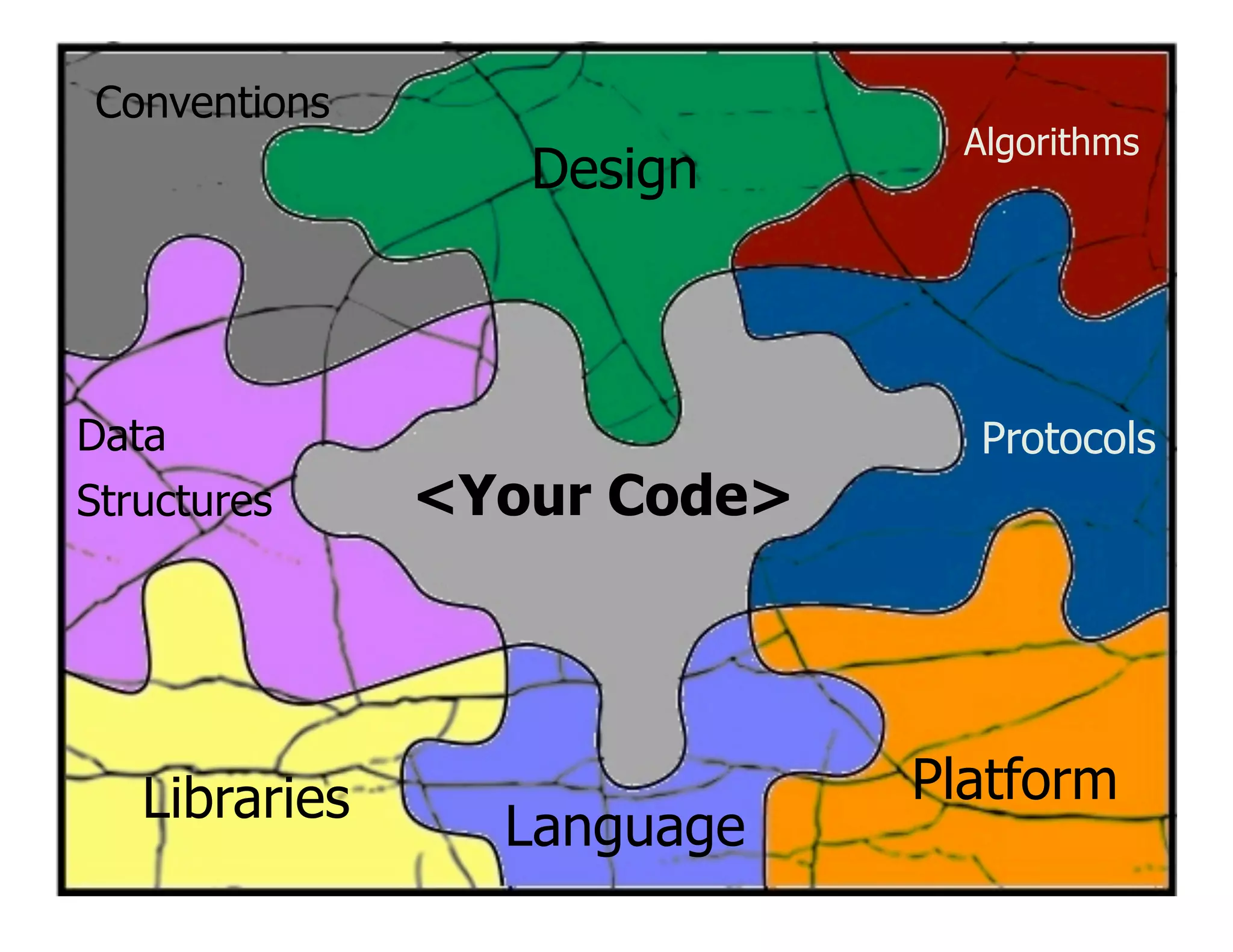
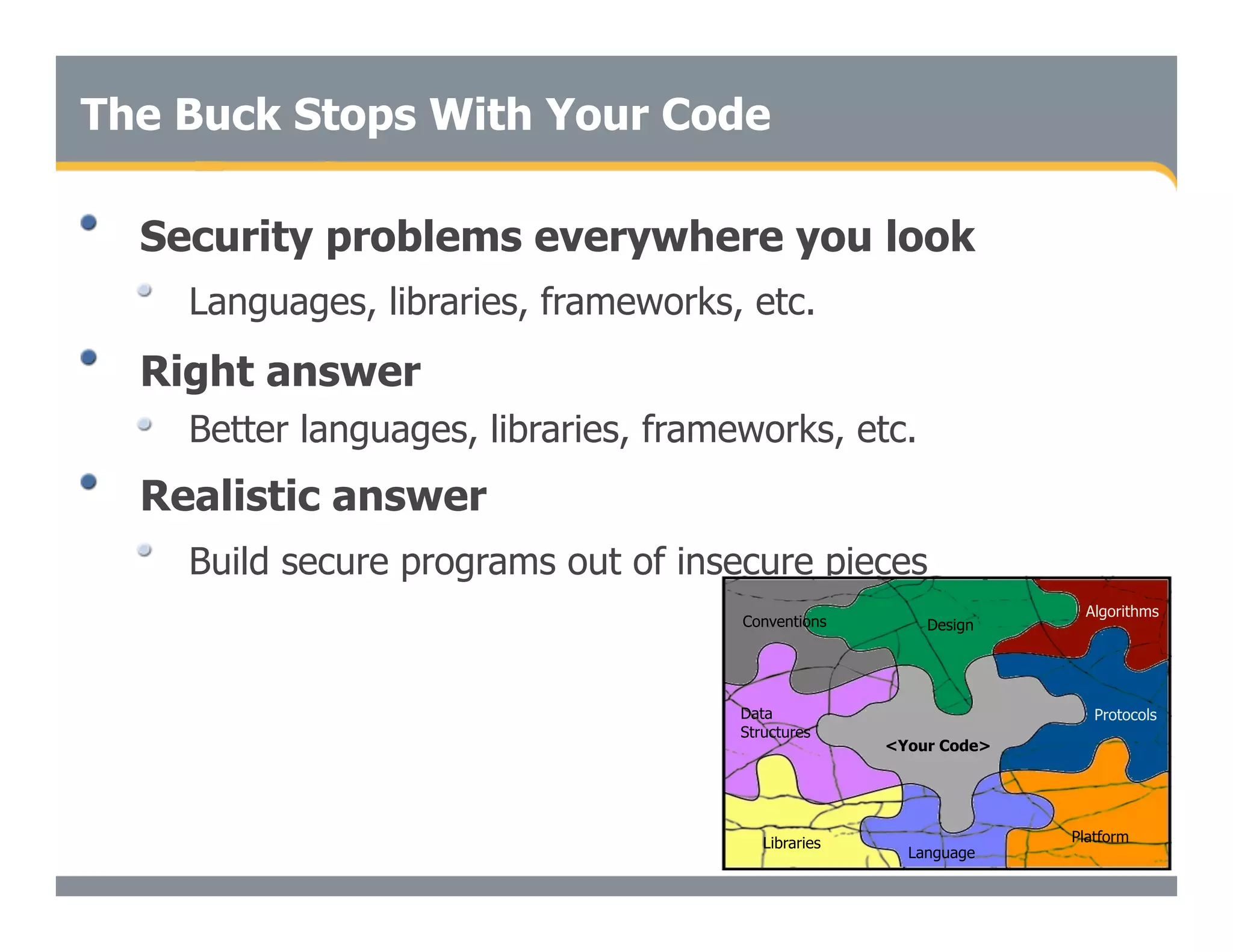


This document discusses the importance of static analysis for secure programming. It describes how static analysis tools work by analyzing code without executing it to find security vulnerabilities based on predefined rules. Good tools prioritize results by risk and provide easy-to-understand interfaces for programmers to review issues. The document recommends adopting static analysis by running tools regularly during development, focusing on high priority issues, and measuring outcomes to improve security over time. Static analysis is presented as a way to bring security expertise to all programmers and make code reviews more efficient.















































