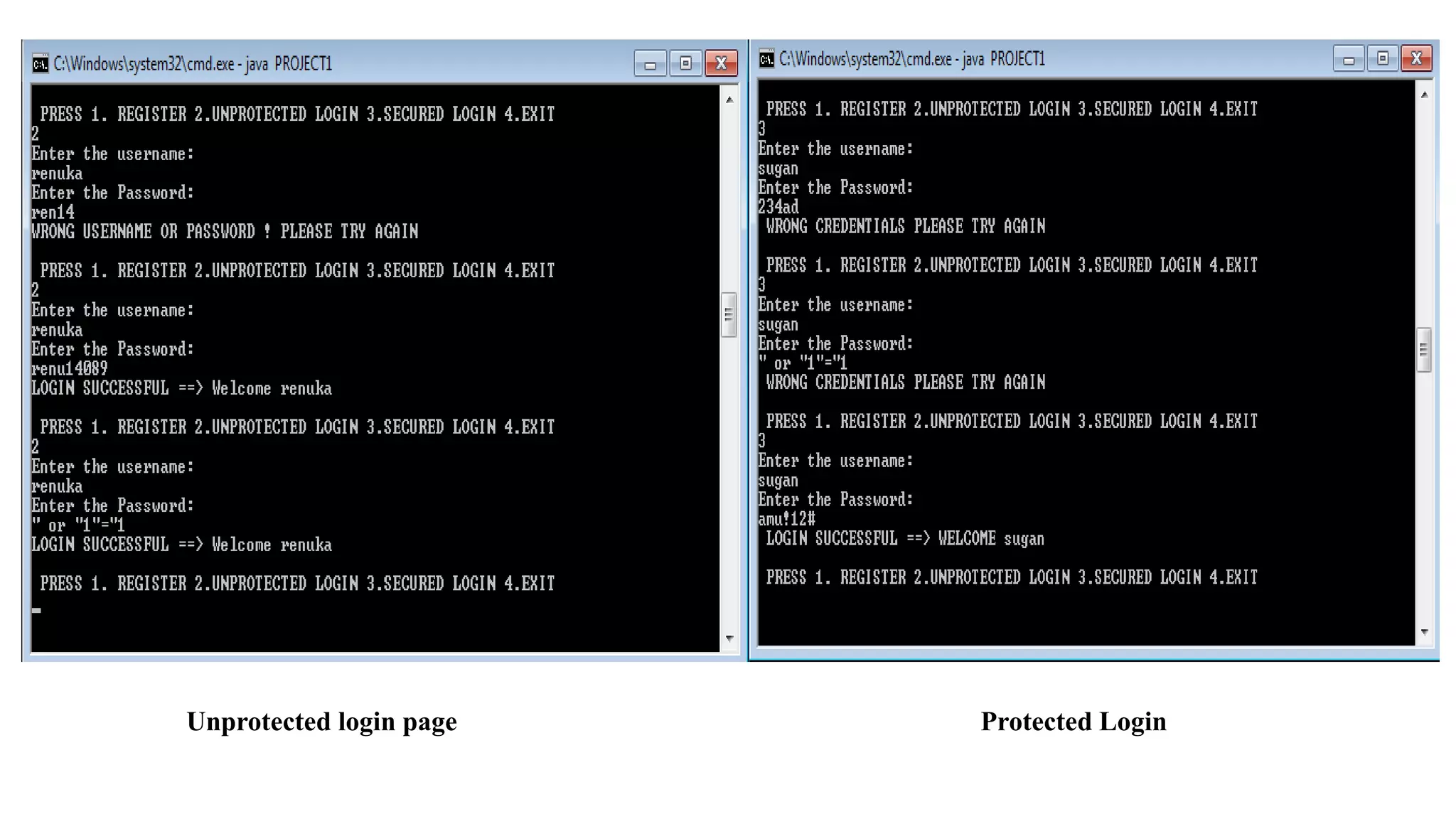
The document discusses avoiding vulnerability in web applications due to SQL injection attacks. It proposes using encryption techniques like AES encryption and secure hashing to encrypt SQL queries before sending them to the database. The proposed system architecture encrypts the username and password during registration using AES encryption, and then hashes the encrypted value for storage in the database. This makes unauthorized access and SQL injection attacks more difficult. Screenshots show the protected login page working to help prevent SQL injection attacks.
![LOYOLA – ICAM
COLLEGE OF ENGINEERING AND TECHNOLOGY (LICET)
Loyola College Campus, Nungambakkam , Chennai – 34
AVOIDING VULNERABILITY IN DATAADMITTANCE OF WEB APPLICATIONS
BASED ON ENCRYPTION TECHNIQUES
Done by
Guide
L.DIVYA [32810104013] Mr L REMEGIUS PRAVEEN SAHAYARAJ
V.PAVITHRA [32810104042]
P.SHANTHI PRIYA [32810104054]
Area Of Reasearch: Database Security](https://image.slidesharecdn.com/sqlinjectionattacks-220812034803-b5408f41/75/SQL-INJECTION-ATTACKS-pptx-1-2048.jpg)












![REFERENCES
[1] Priyanka, Vijay Kumar Bohat, (April 2013) ’Detection of SQL Injection Attack and Various Prevention Strategies’, International
Journaand Advanced Technology (IJEAT) ISSN: 2249 – 8958, Volume-2, Issue-4.
[2] Sonam Panda, 1 Ramani S2,(Jan-Feb.2013),’Protection of Web Application against Sql Injection Attacks ‘, International Journal of
Modern Engineering Research (IJMER) Vol.3, Issue.1, pp-166-168 ISSN: 2249-6645.
[3] Mihir Gandhi, JwalantBaria,( January 2013)’SQL INJECTION Attacks in Web Application’International Journal of Soft Computing
and Engineering (IJSCE) ISSN: 2231-2307, Volume-2, Issue-6.
[4] By Mayank Namdev*, Fehreen Hasan, Gaurav Shrivastav(July 2012) ‘Review of SQL Injection Attack and Proposed Method for
Detection and Prevention of SQLIA”Volume 2, Issue 7.
[5] Shubham Srivastava1, Rajeev Ranjan Kumar Tripathi, ‘Attacks Dueto SQL Injection & Their Prevention Method for Web-Application
(IJCSIT) International Journal of Computer Science and InformationTechnologies, Vol. 3 (2) , 2012,3615-3618.
[6] Indrani Balasundaram, E.Ramaraj,’An Authentication Scheme forPreventing SQL injection Attack using Hybrid Encryption’ (ISSN
1450-216,2011, Vol.53,pp.359-368.
[7] AtefehTajpour et al. ‘Evaluation of SQL Injection Detetion andPrevention Techniques’ Second International Conference
onComputational Intelligence, 2010.
[8] Shaukat Ali, Azhar Rauf, Huma Javed,’SQLIPA: An Authentication Mechanism Against SQL Injection’, European Journal of
Scientific
Research ISSN 1450-216X Vol.38 No.4 (2009), pp 604-611.
[9] Sayyed Mohammad Sadegh Sajjadi and Bahare Tajalli Pour,( September 2013) ‘Study of SQL Injection Attacks and
Countermeasures’, International Journal of Computer and Communication Engineering, Vol. 2, No. 5.
[10] W. G. Halfond, J. Viegas, and A. Orso , ‘A Classification of SQLInjection Attacks and Countermeasures,’ in Proc. the International
Symposium on Secure Software Engineering 2006.](https://image.slidesharecdn.com/sqlinjectionattacks-220812034803-b5408f41/75/SQL-INJECTION-ATTACKS-pptx-17-2048.jpg)
