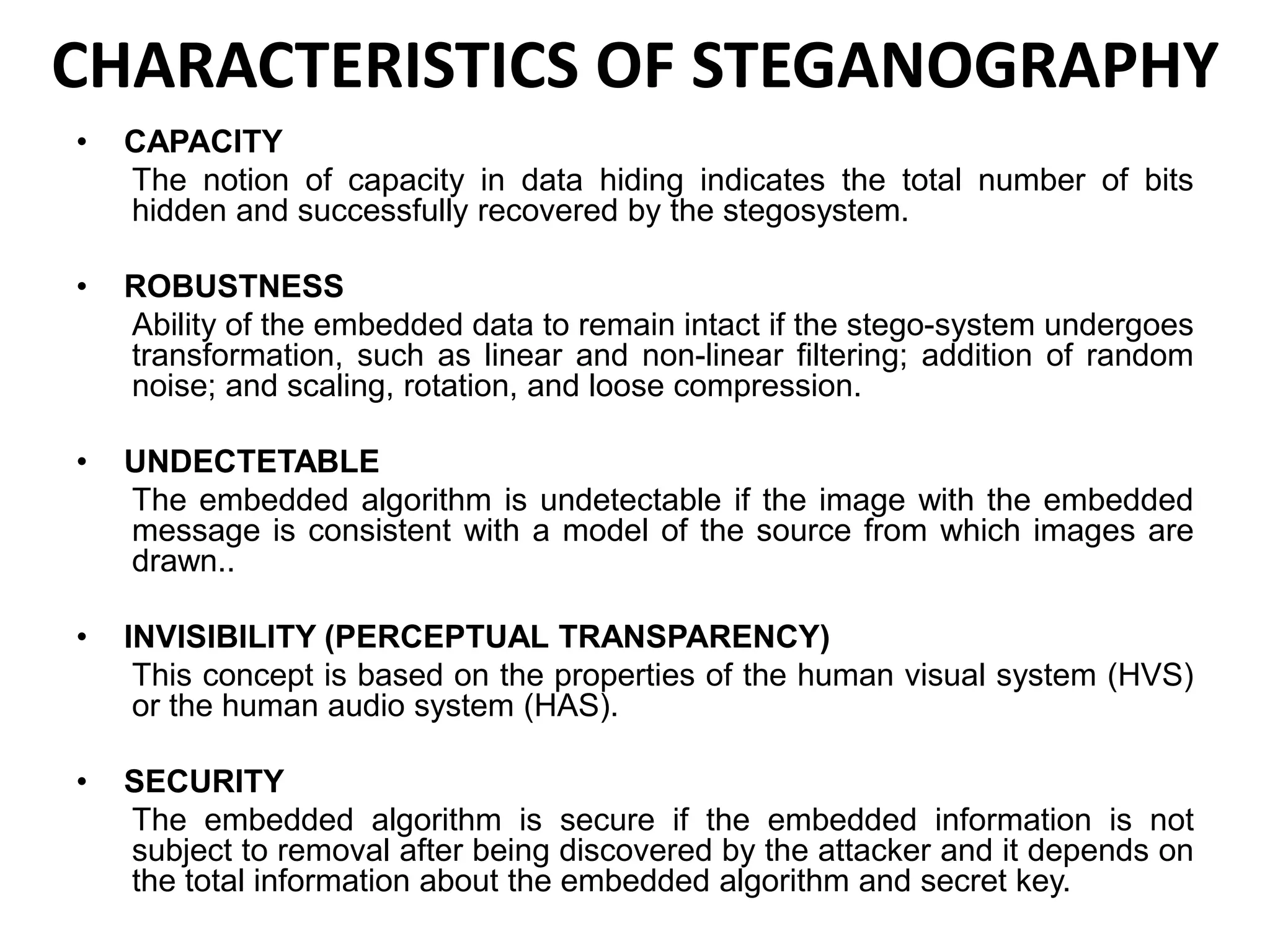
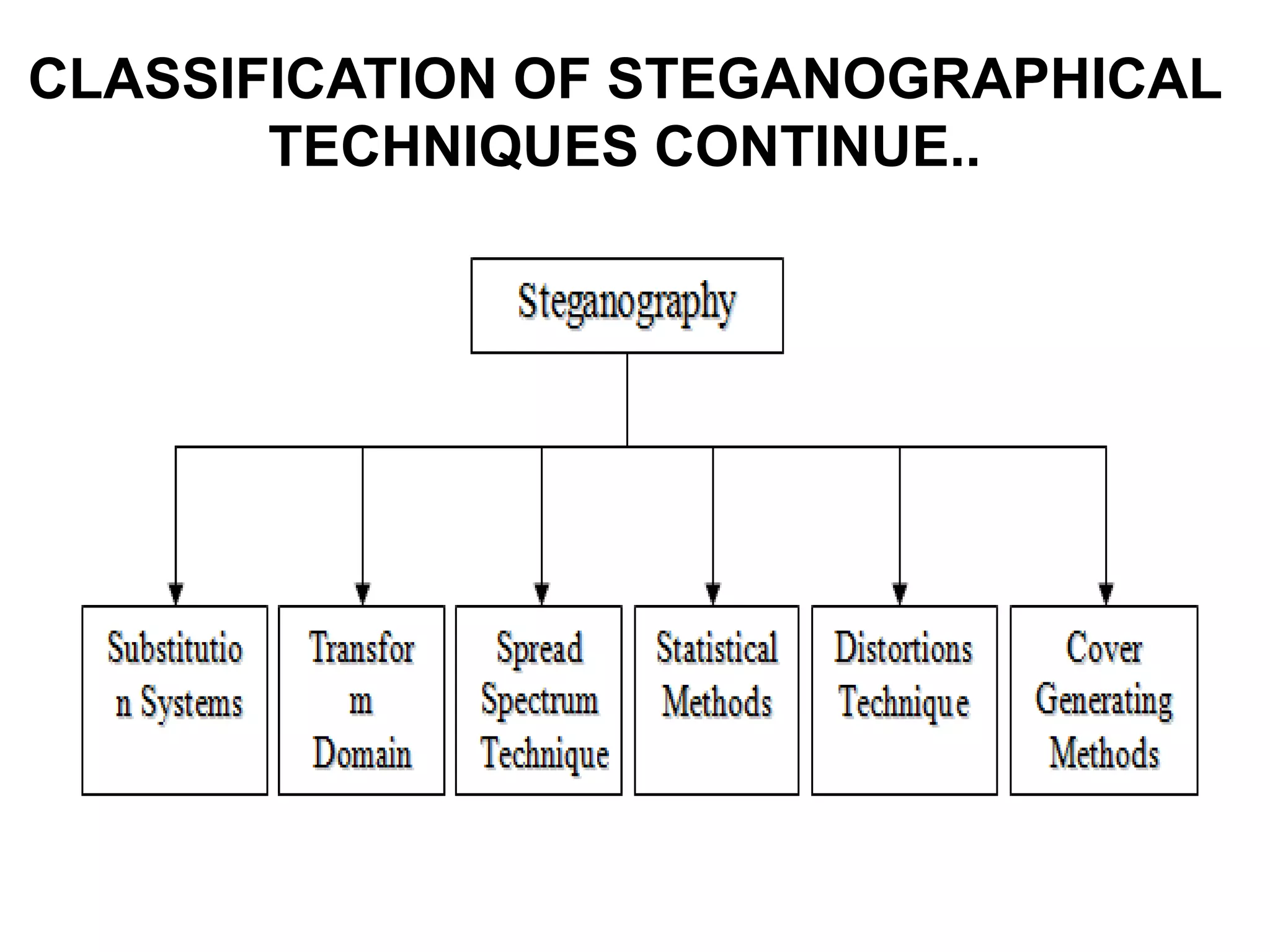
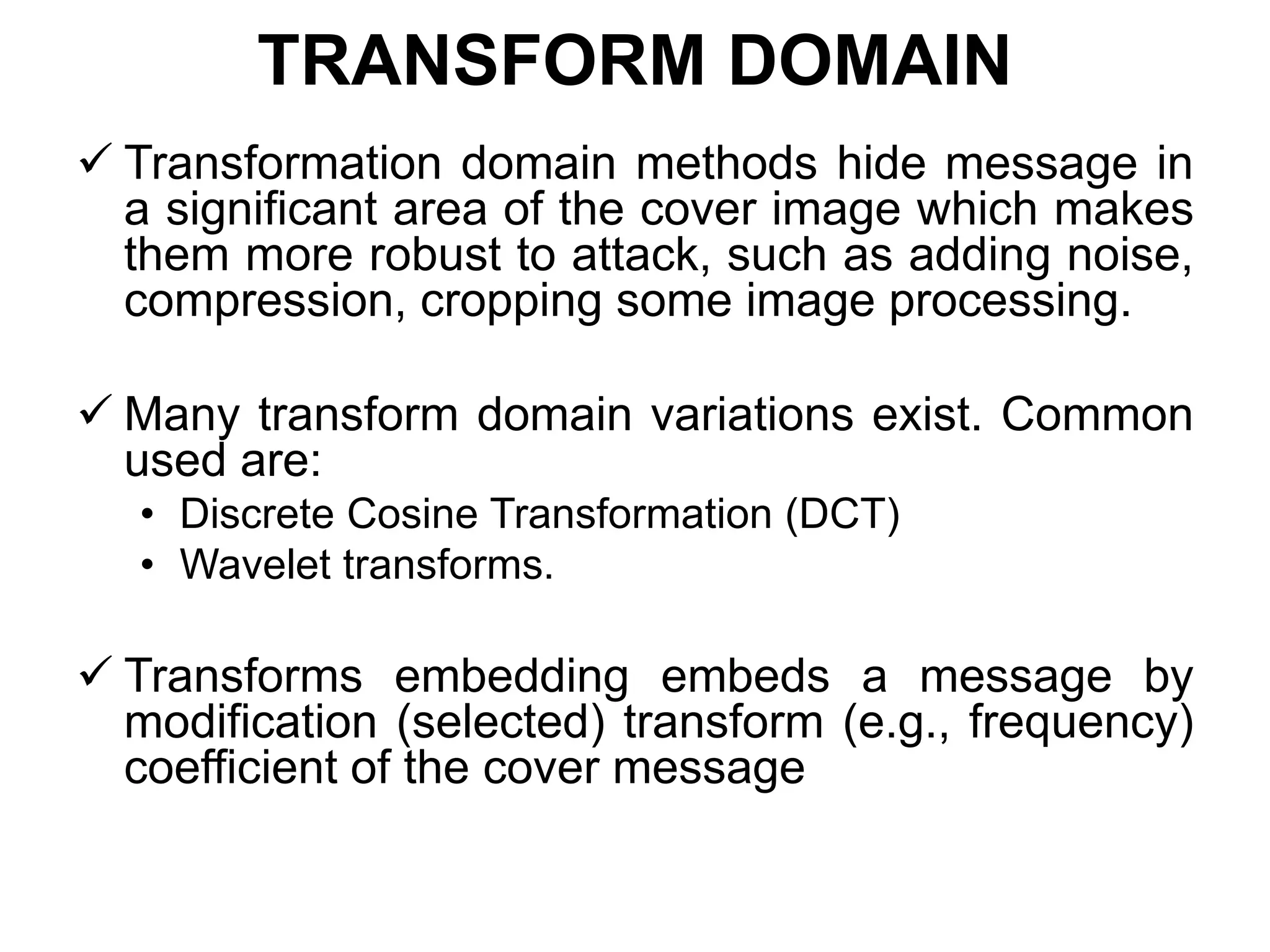
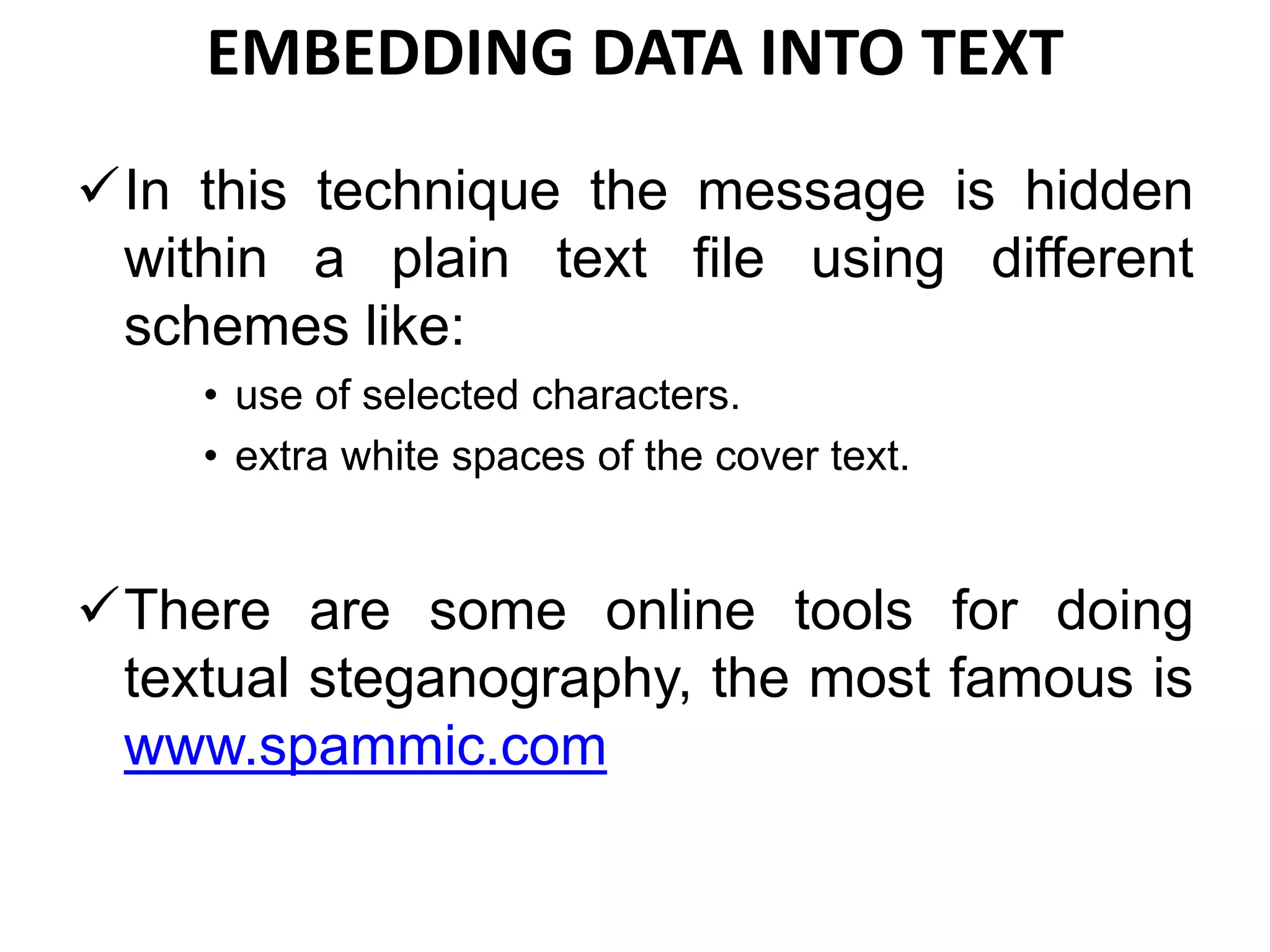
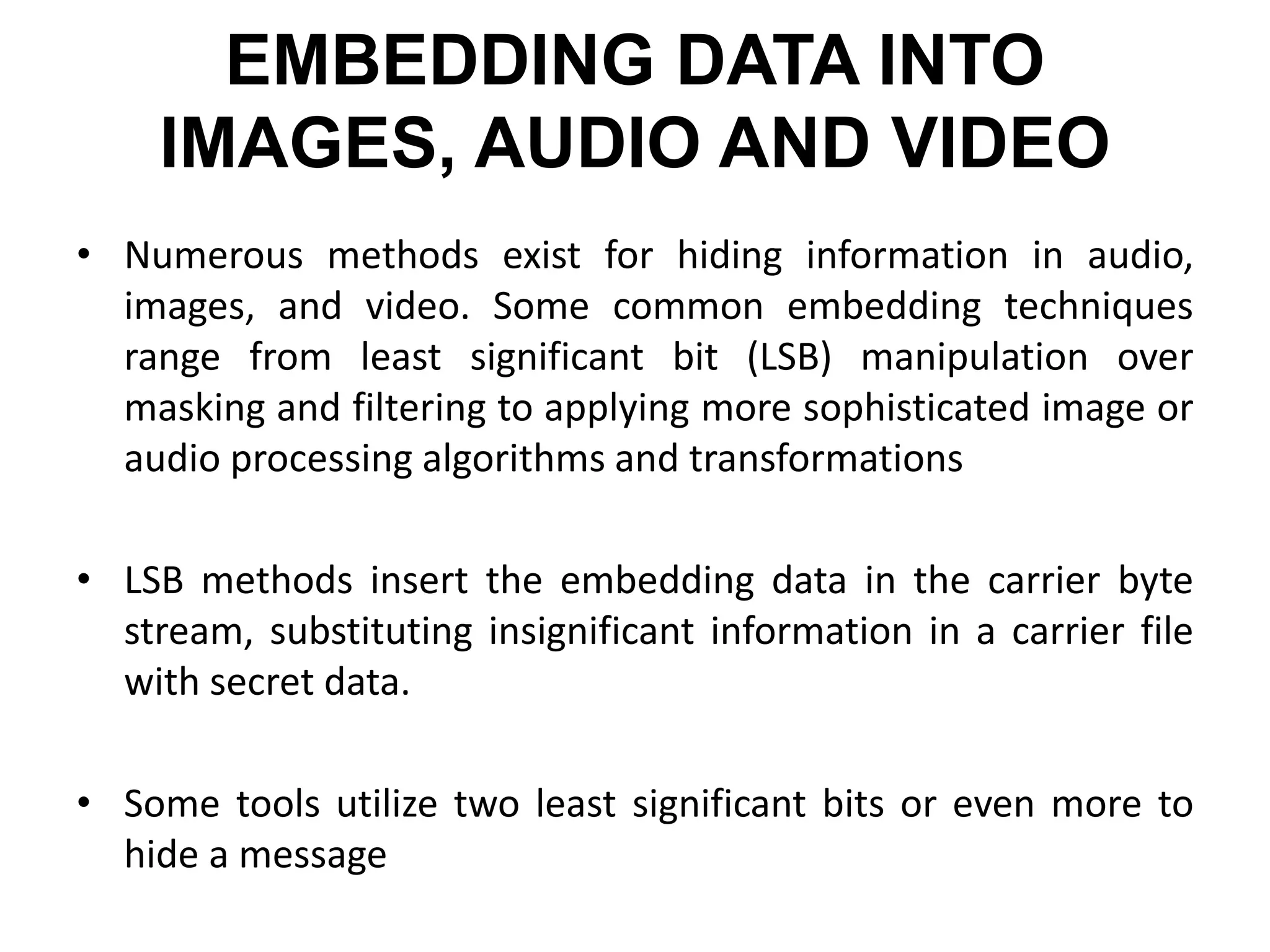
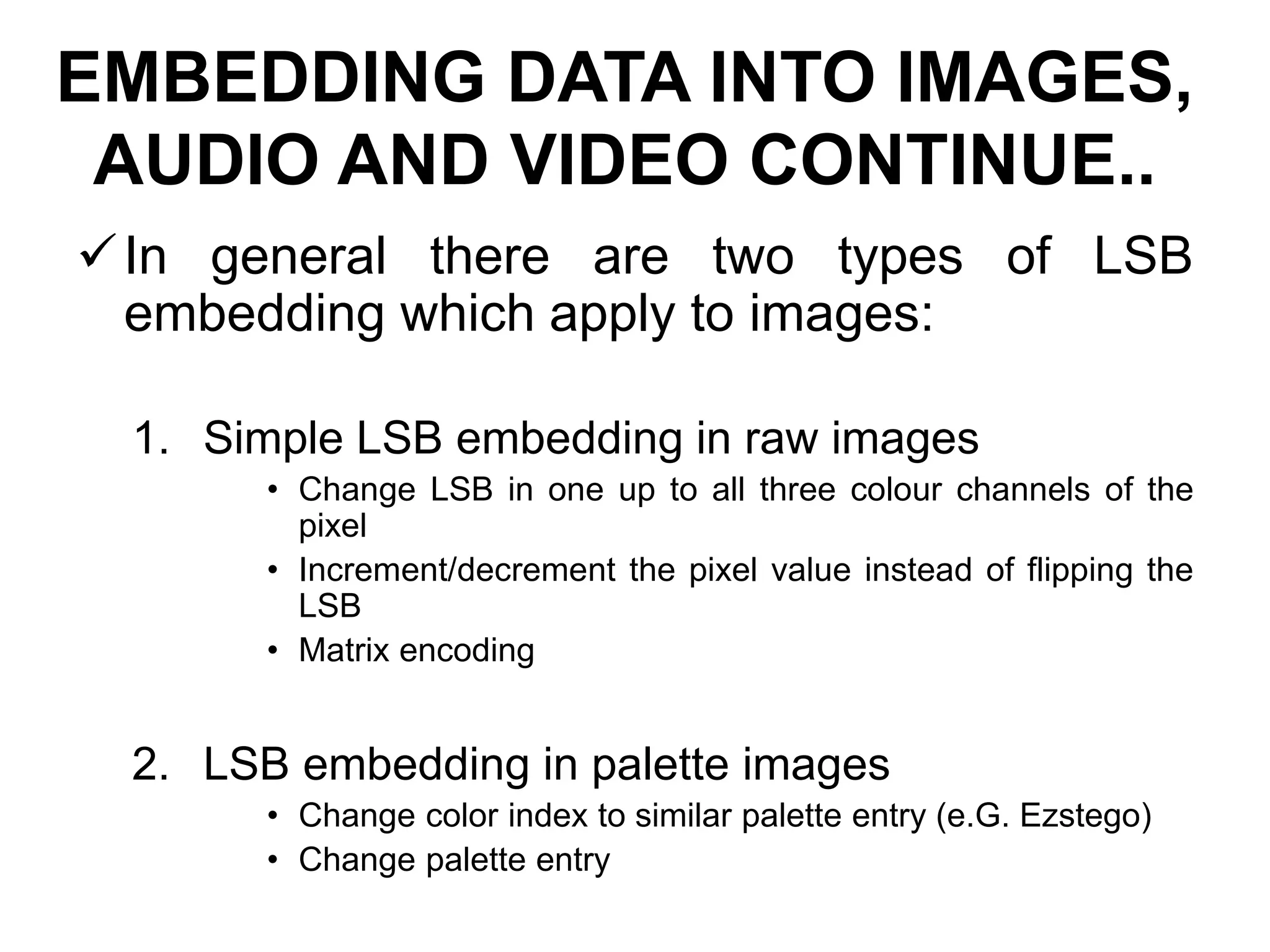
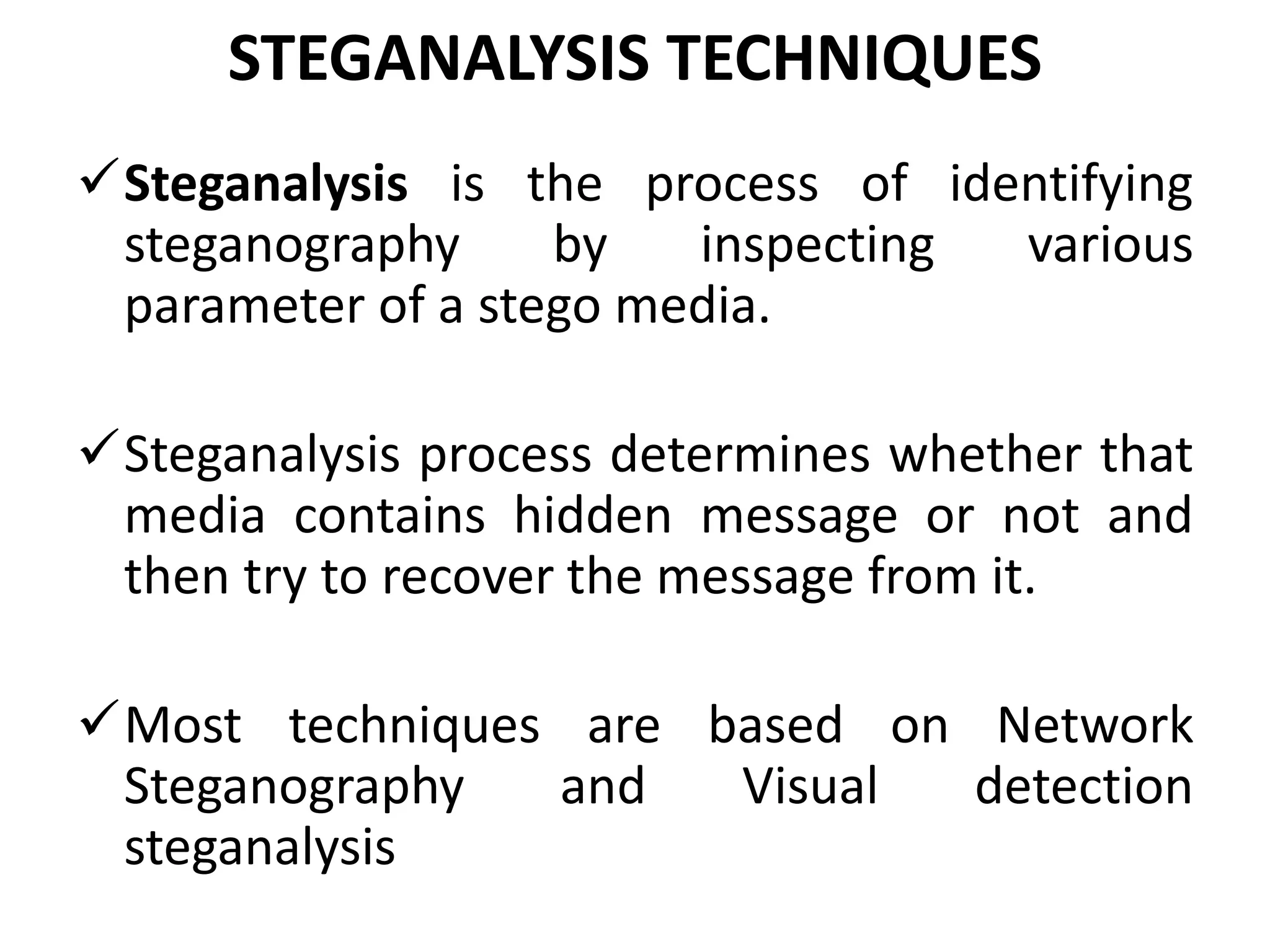
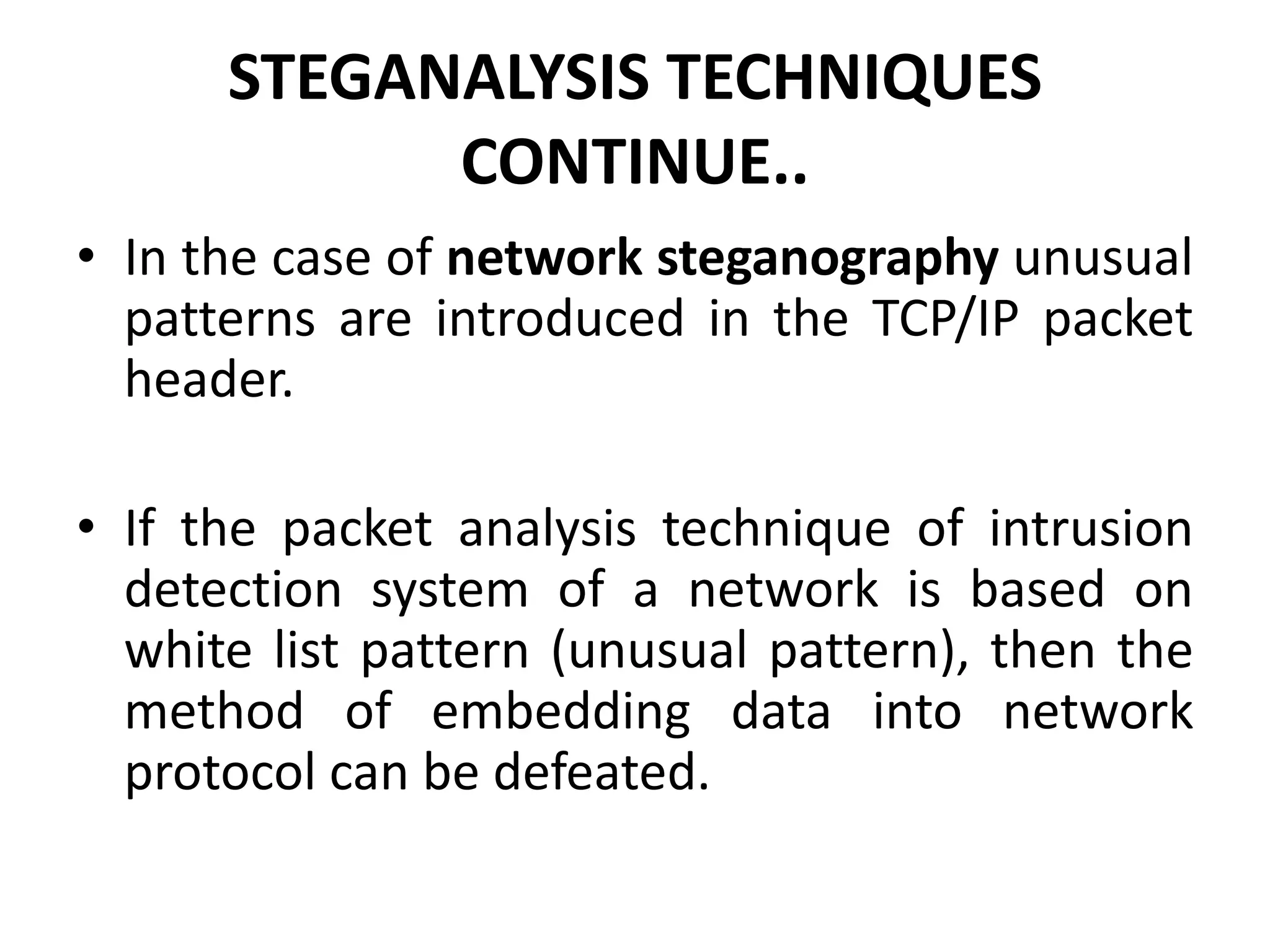
This document provides an overview of steganography presented by four students. It defines steganography as hiding secret communications such that others do not know of the message's existence. The document outlines the history of steganography, modern applications, types of techniques including LSB substitution and transform domains, characteristics, classifications, uses in text, images, and networks, and challenges around detection. It concludes that steganography allows covert transmission of secrets but also poses challenges for network monitoring.