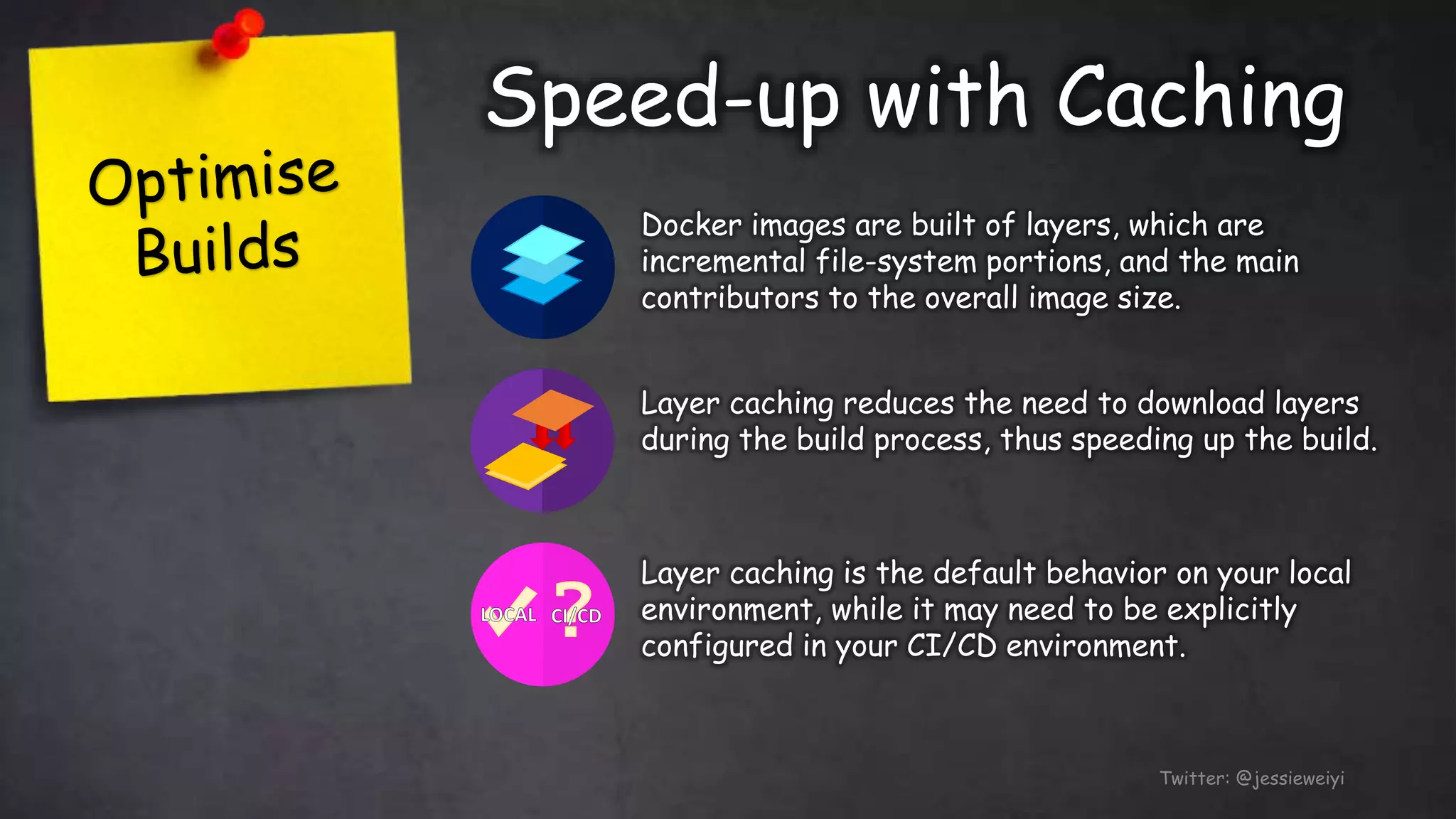
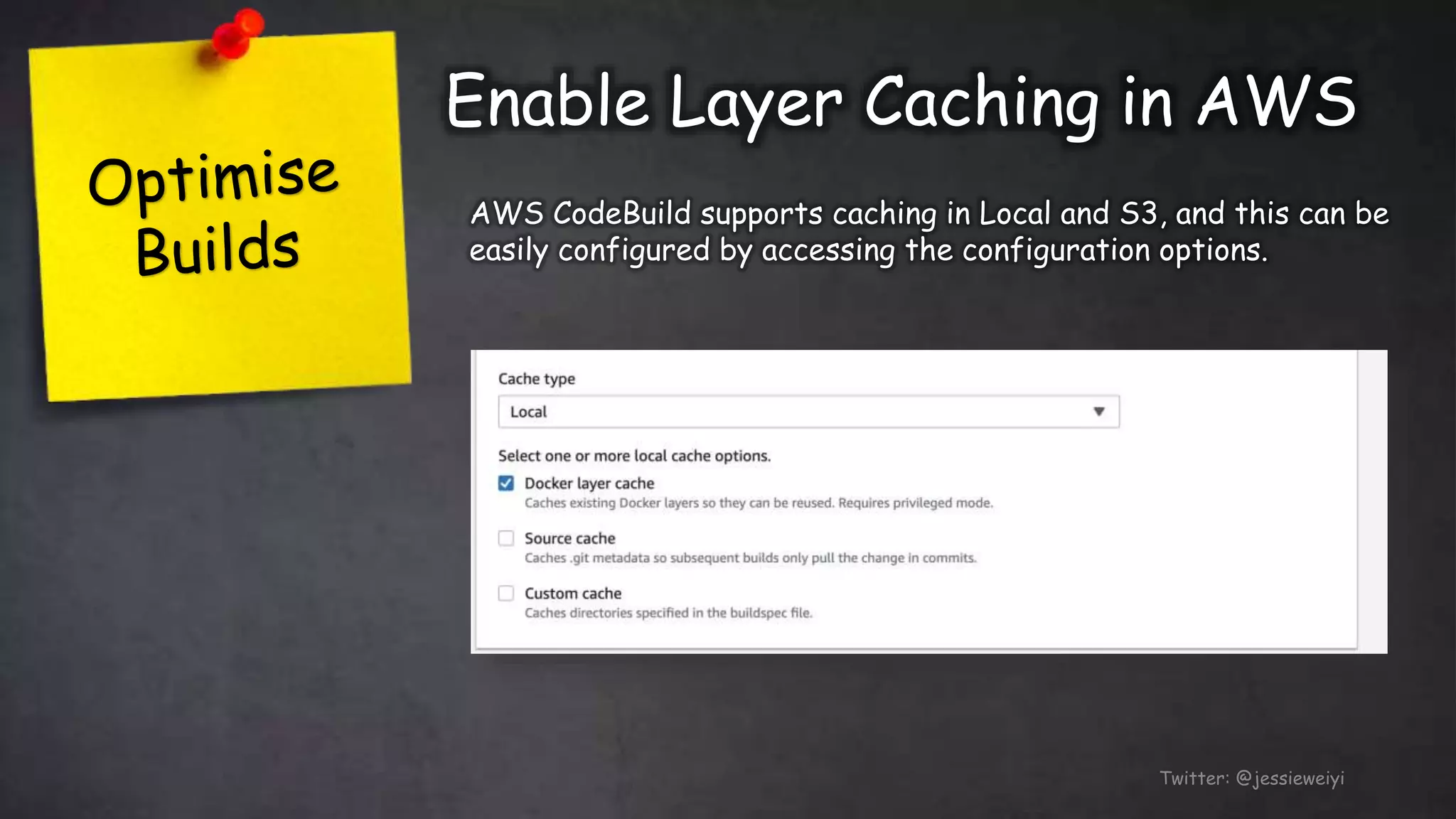
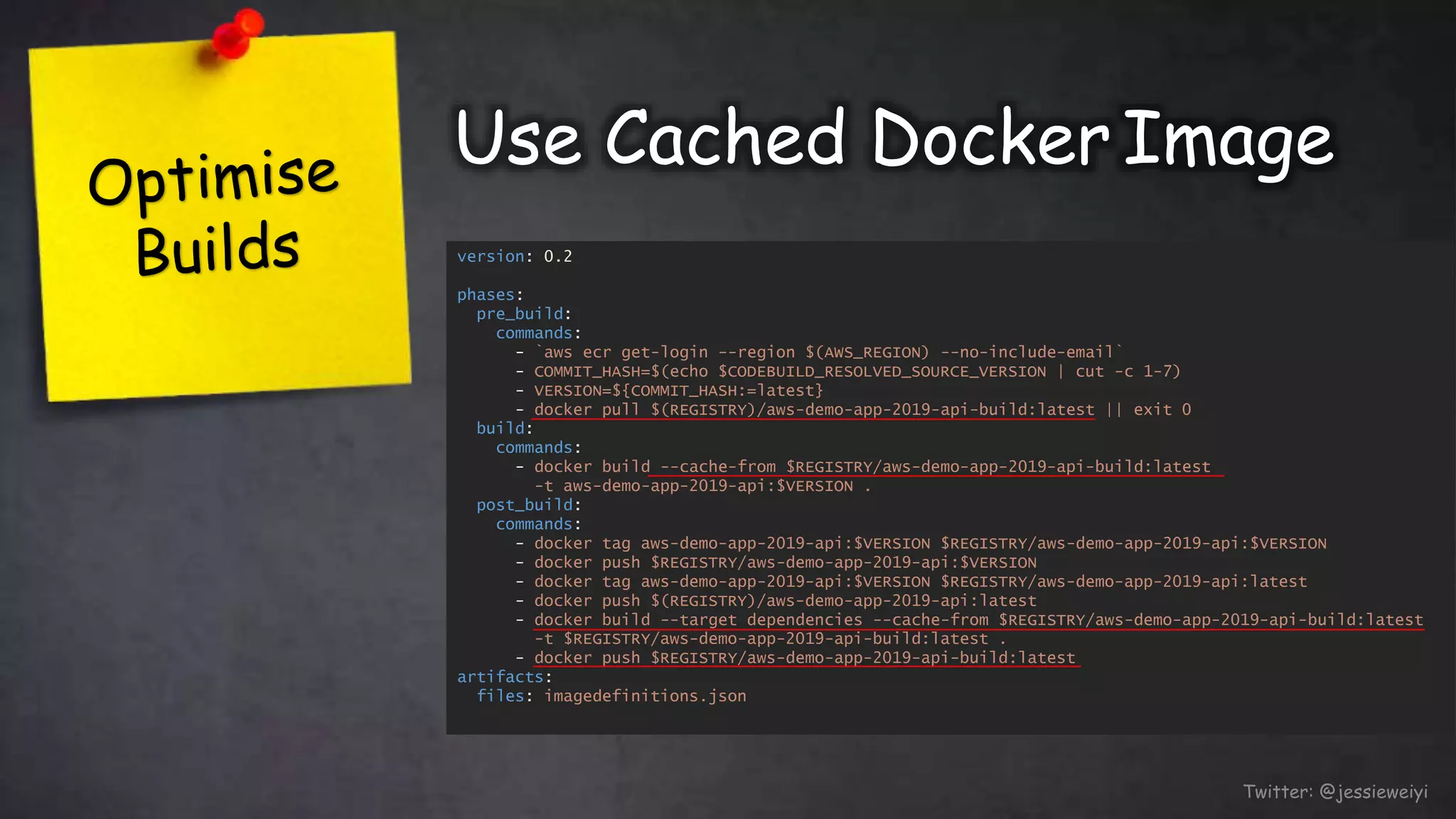
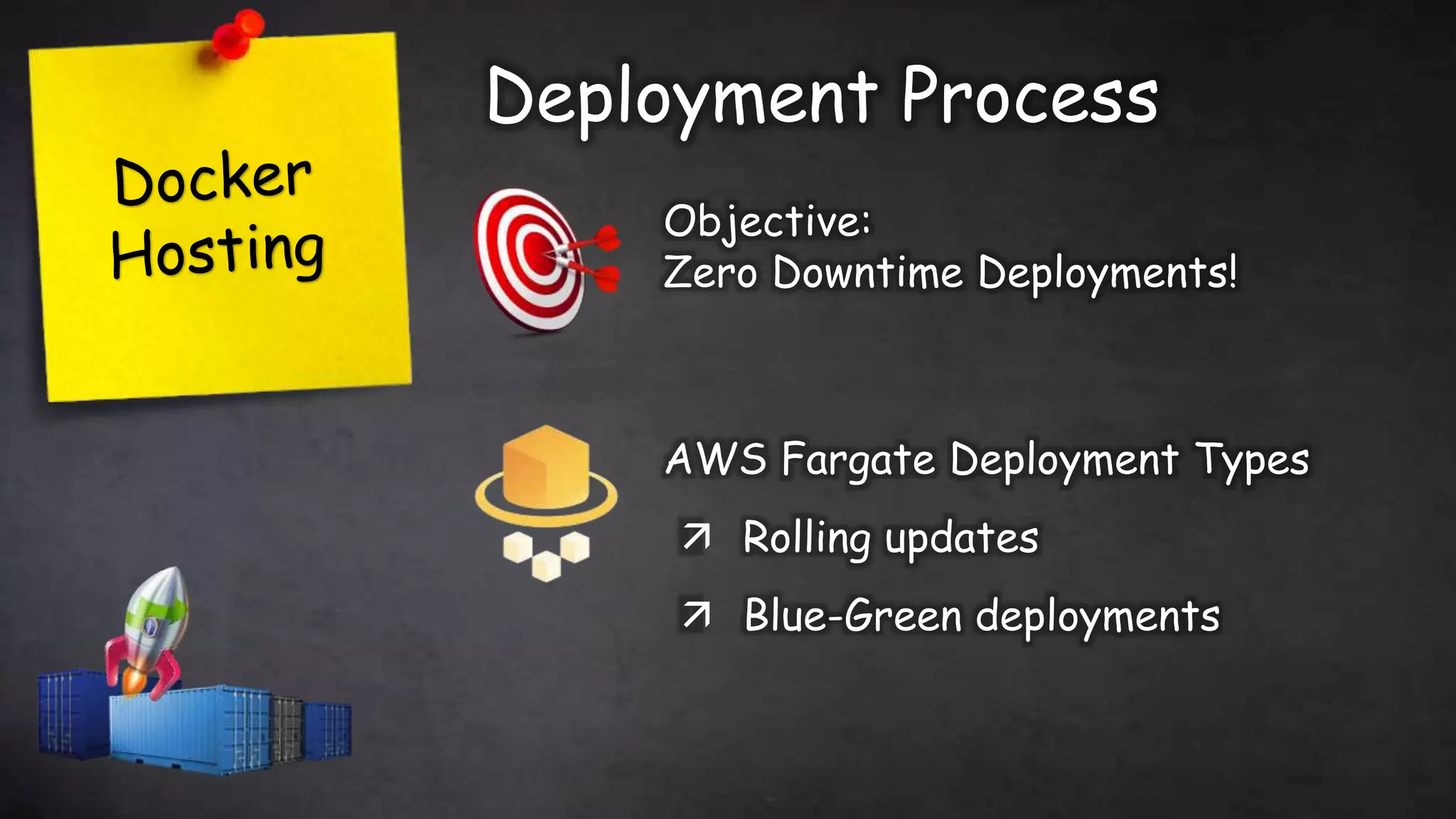
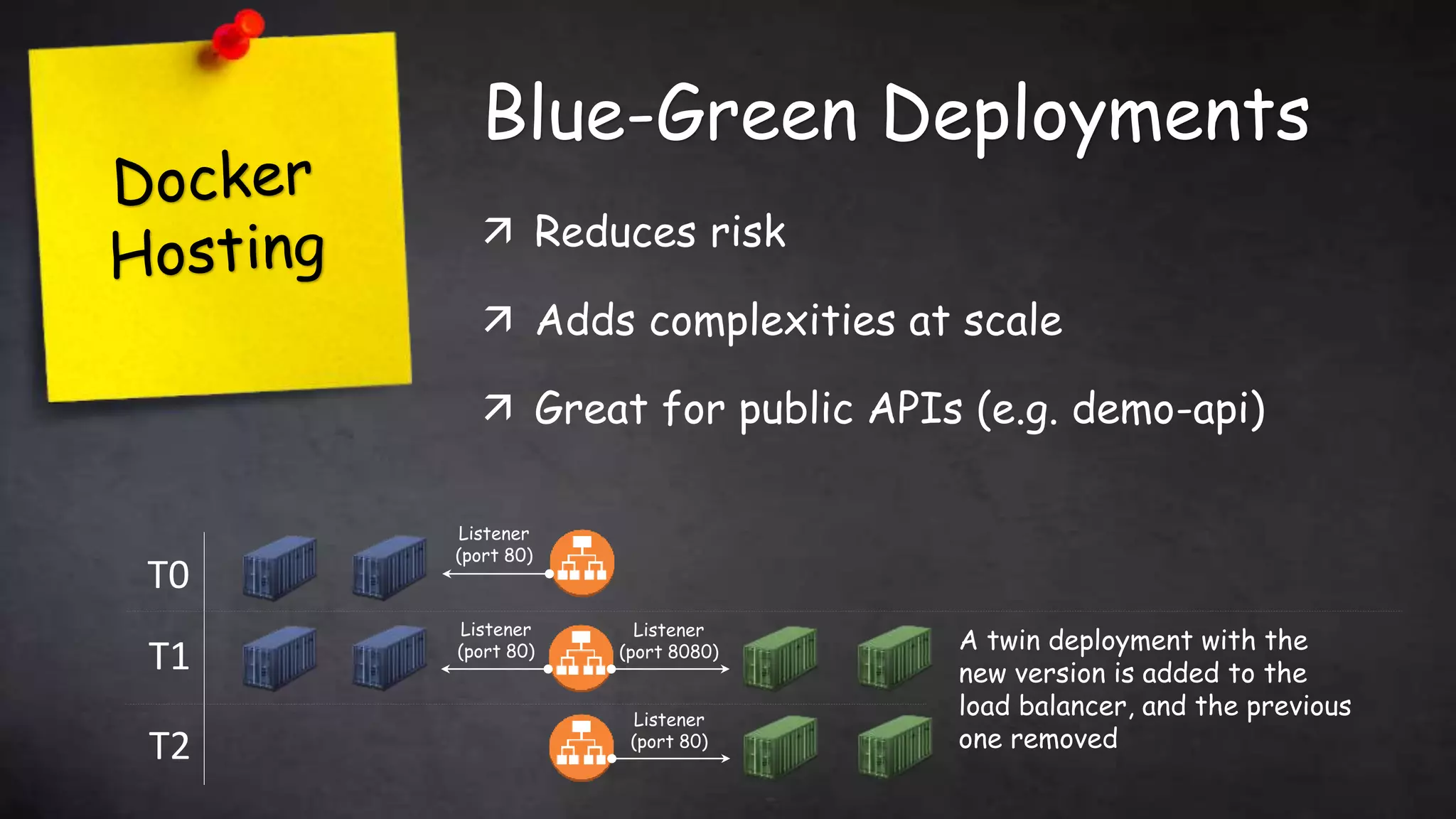
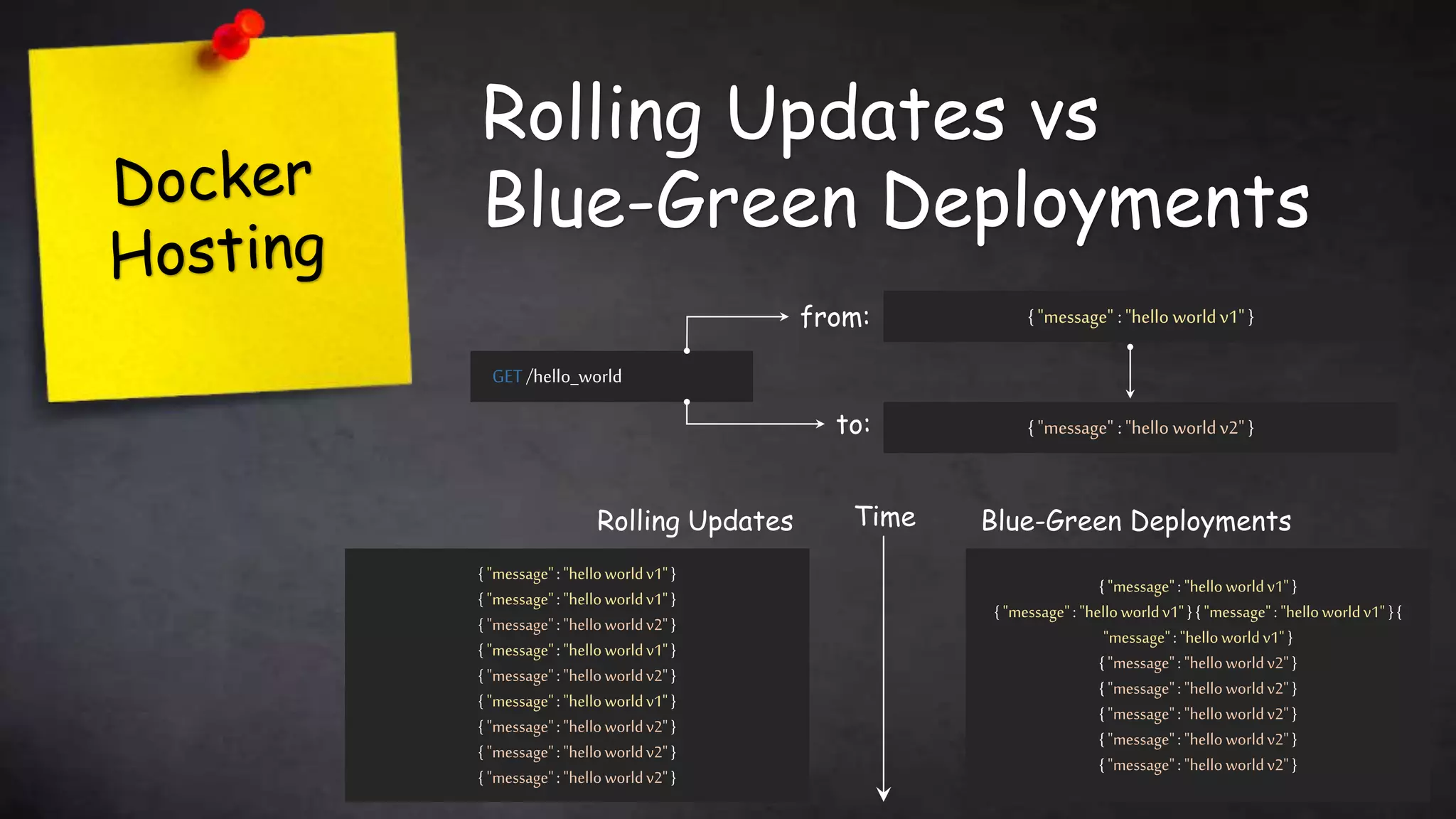
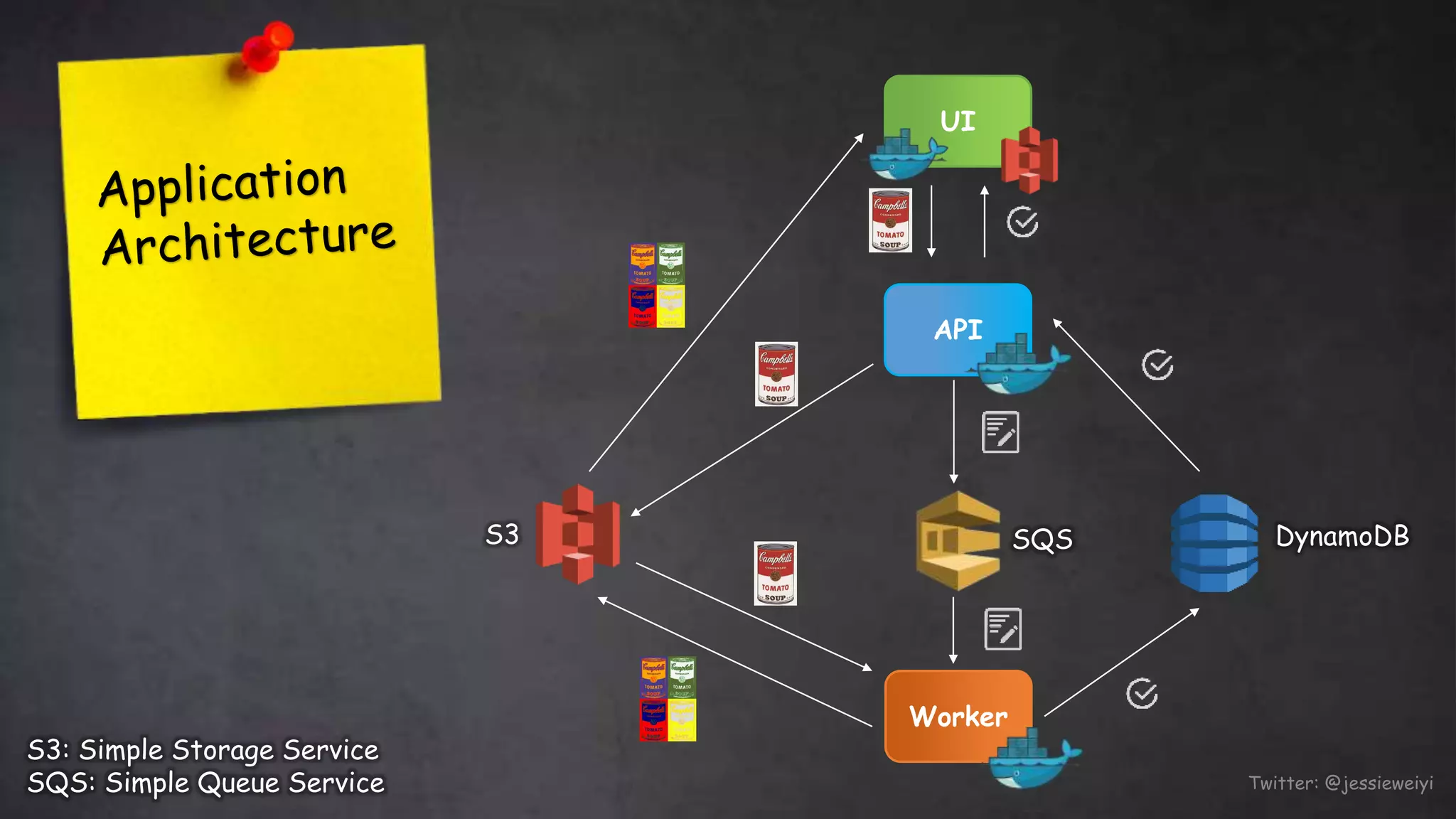
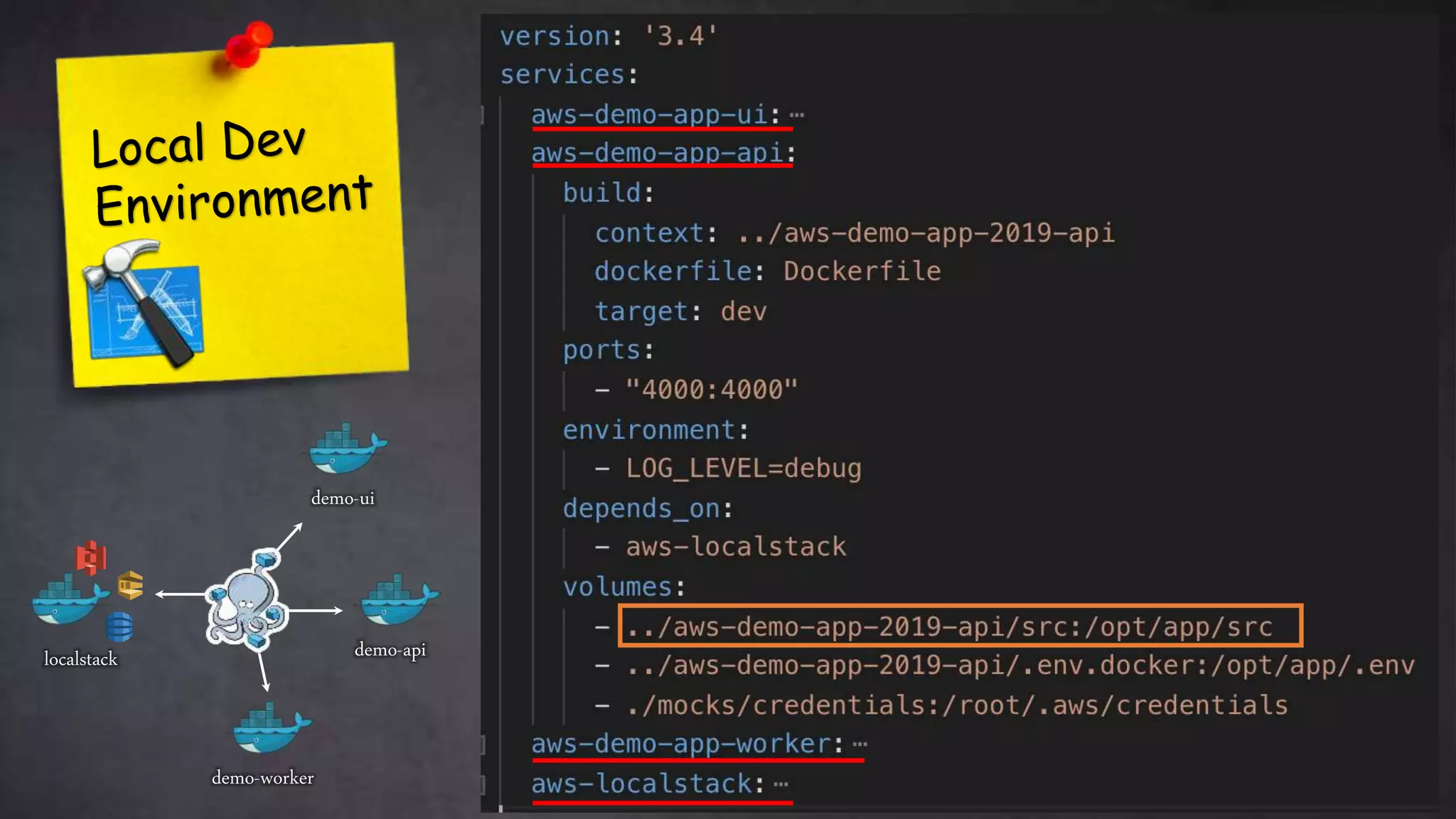
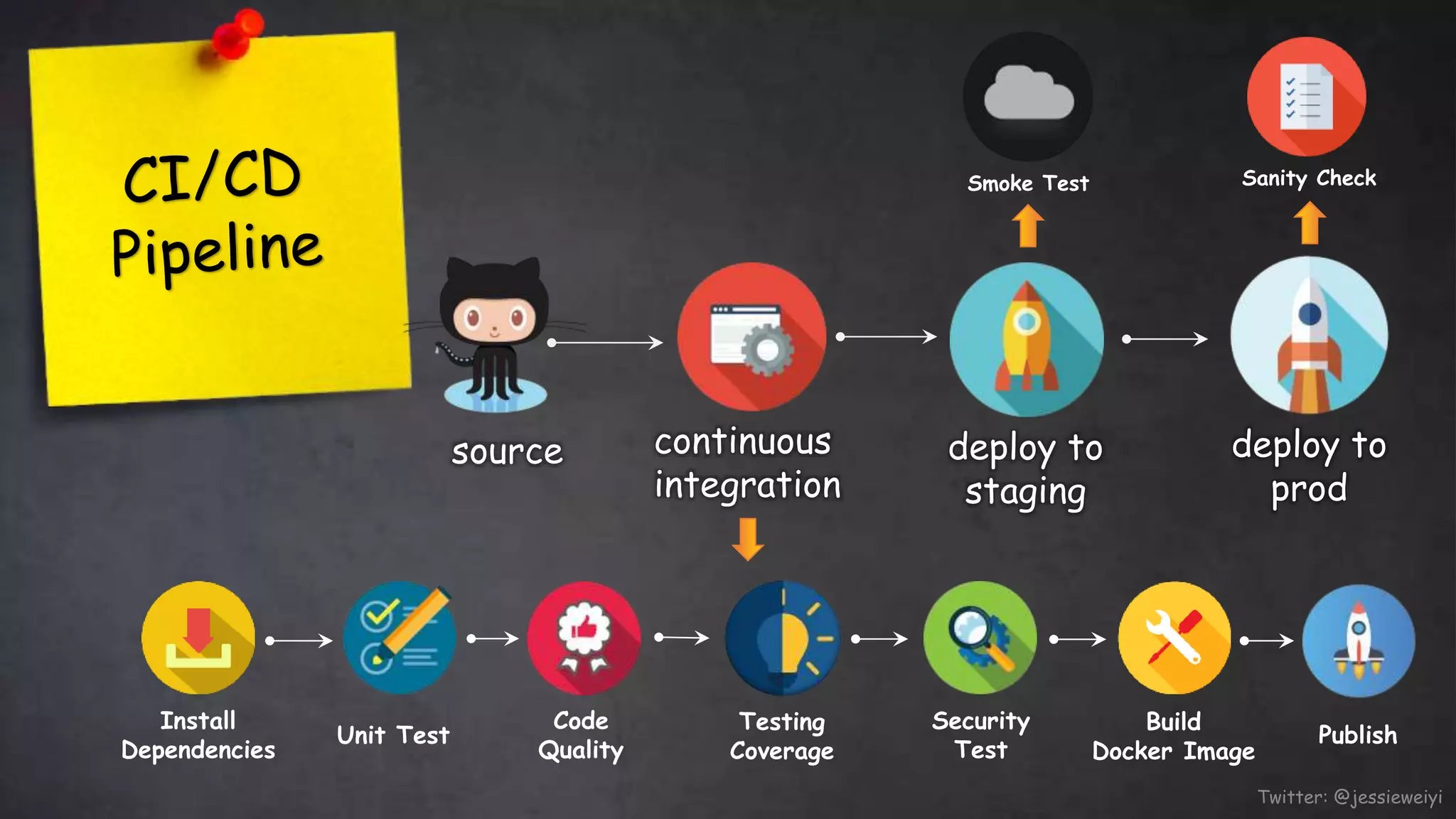
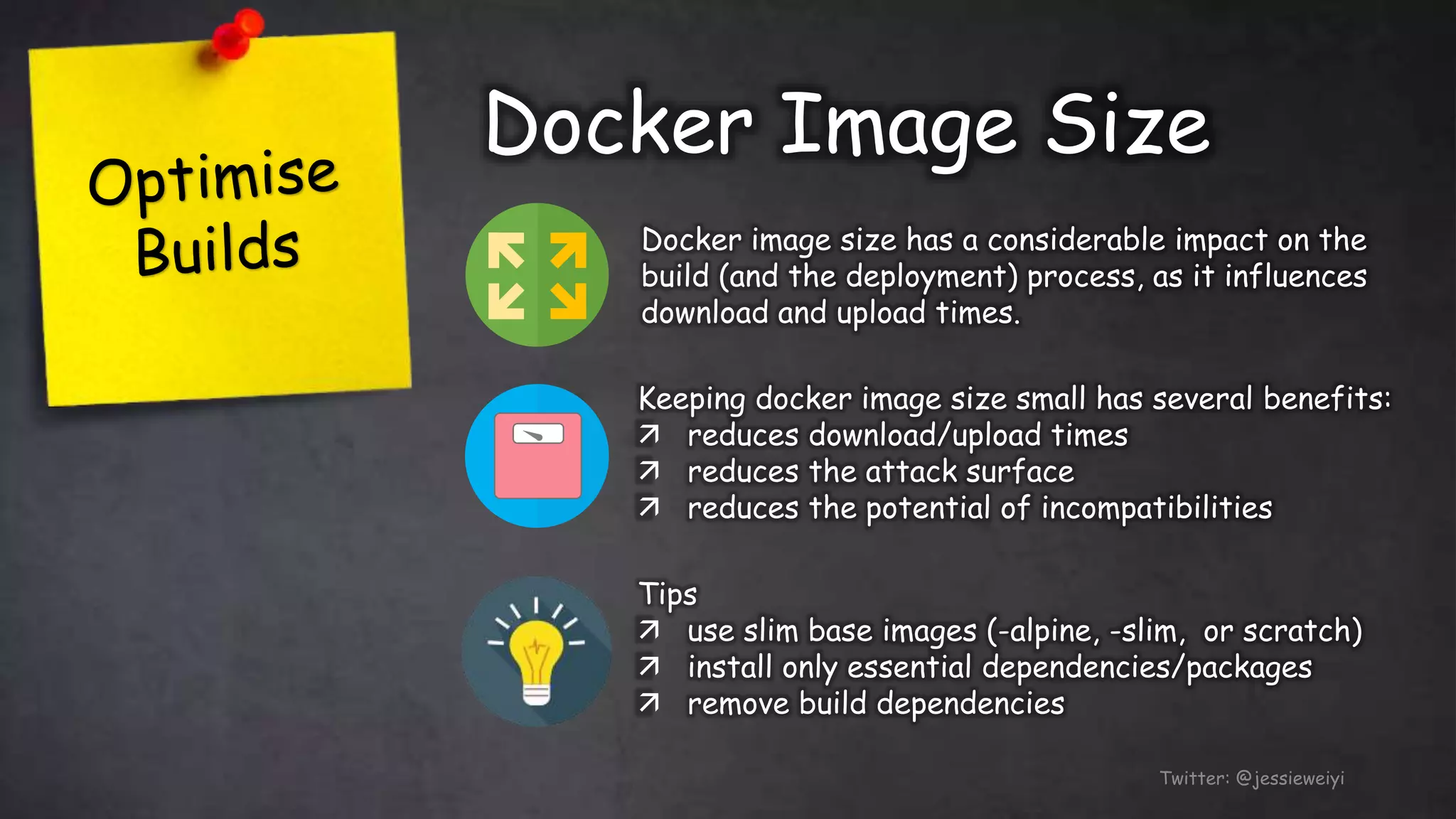
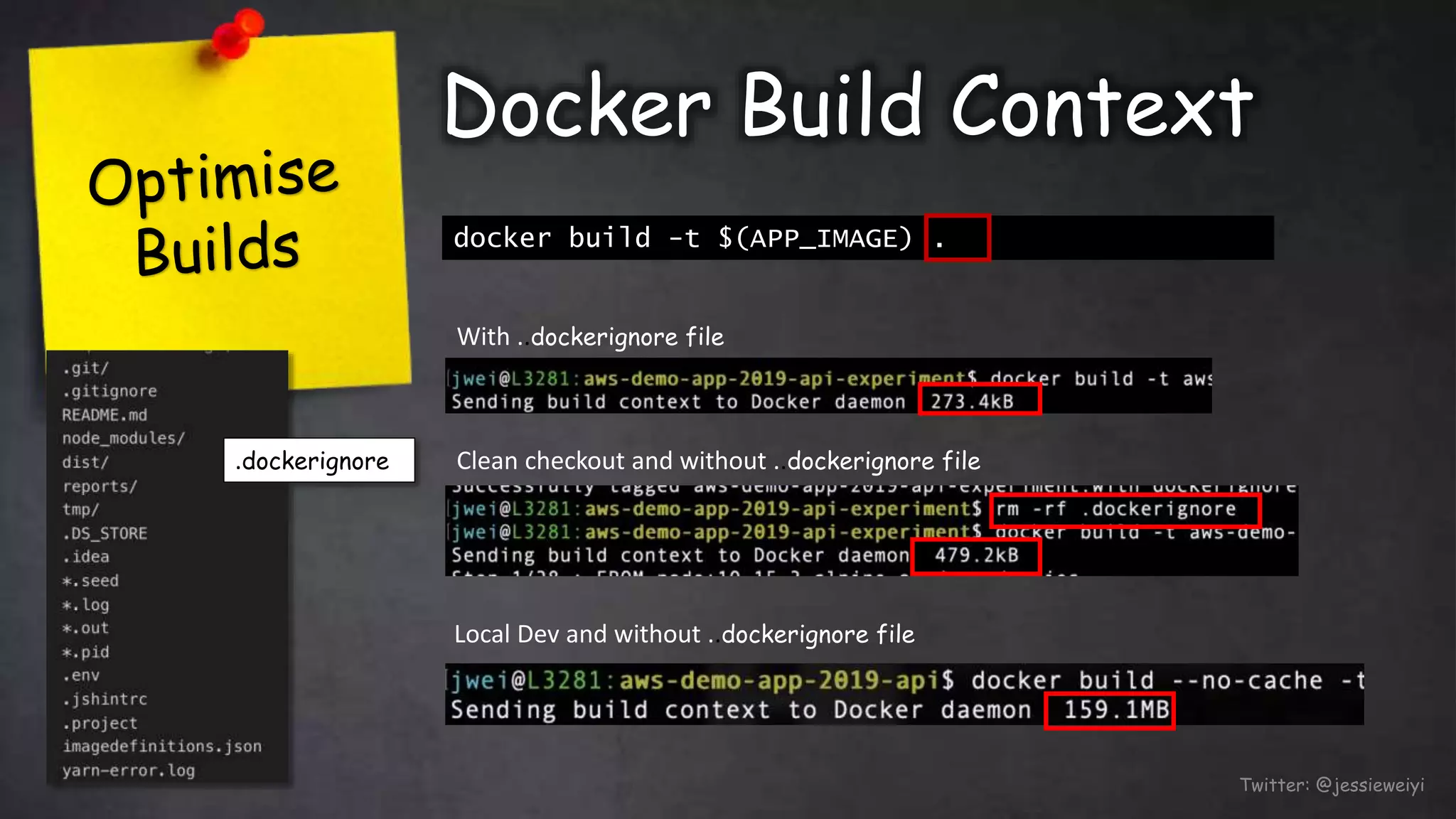
This document discusses taking Docker containers to production on AWS. It demonstrates setting up a local development environment using LocalStack to emulate AWS services like S3 and SQS. It also covers optimizing builds through techniques like multi-stage builds and caching. Finally, it provides an overview of AWS offerings for running containers like ECS and Fargate, and zero-downtime deployment strategies like rolling updates and blue-green deployments.






![Multi-Stage Build
Twitter: @jessieweiyi
FROM node:10.15.3-alpine
ENV usernode
WORKDIR /opt/app
COPY ./package.json/opt/app/package.json
COPY ./yarn.lock /opt/app/yarn.lock
RUN chown $user–R /opt/app
USER $user
RUN yarn
COPY ./ /opt/app
RUN yarnbuild
ENTRYPOINT ["yarn"]
CMD["start"]
Without Multi-Stage Builds
With
Multi-Stage
Builds
378MB
161MB](https://image.slidesharecdn.com/takingdockertodancingcontinuousdeliveryonawsslidesonly-190512120139/75/Taking-Docker-to-Dance-Continuous-Delivery-on-AWS-13-2048.jpg)