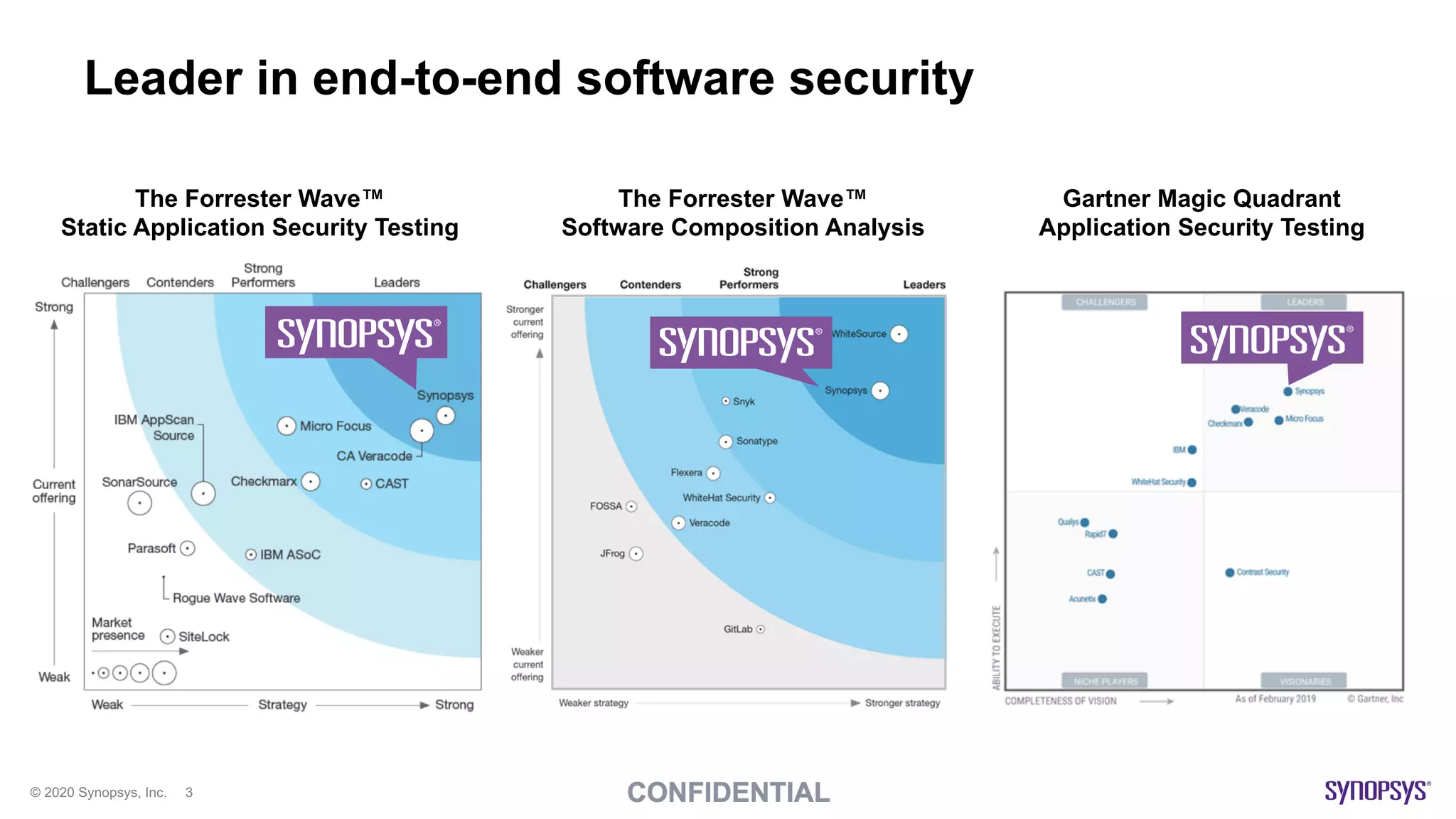
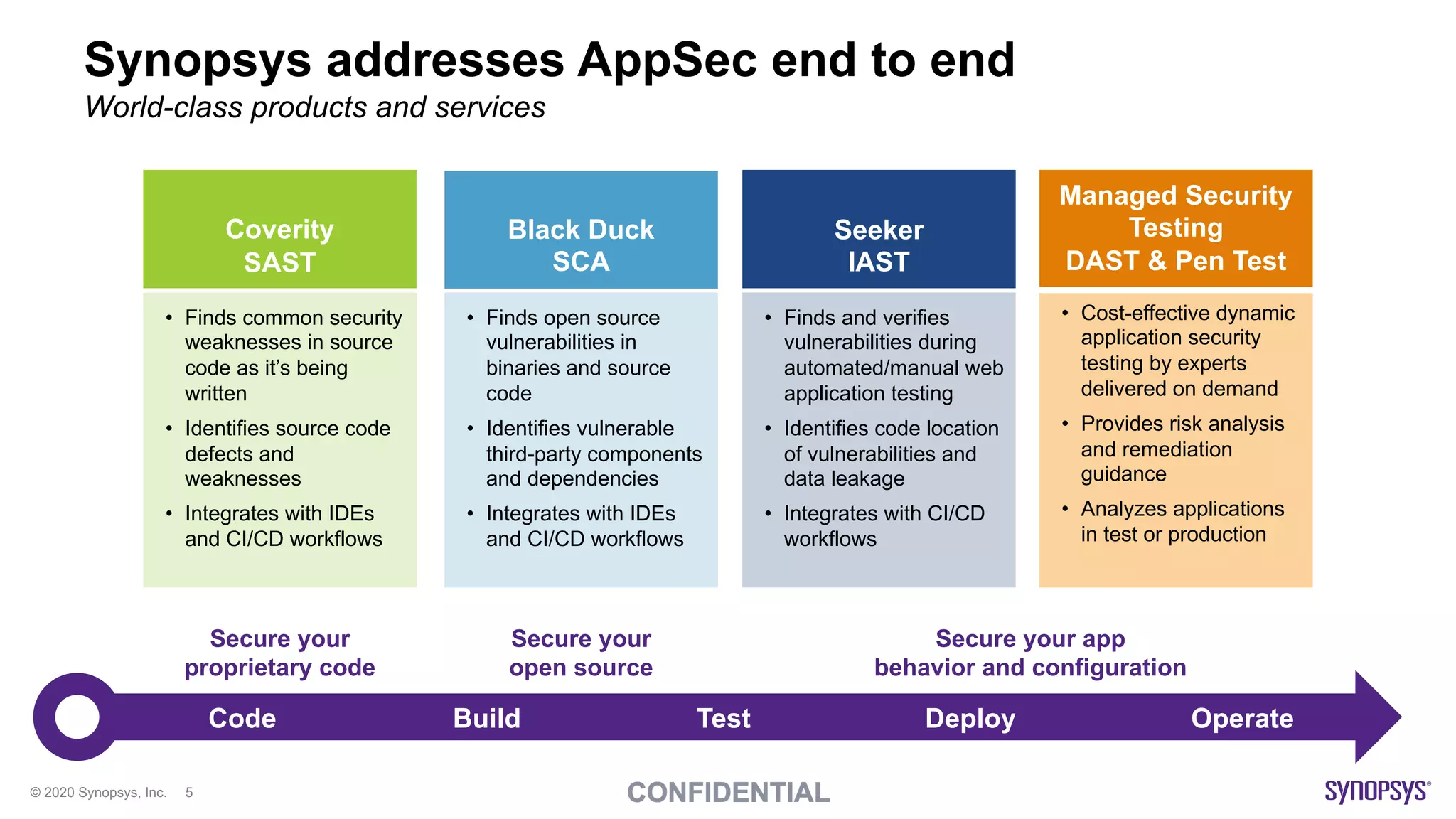
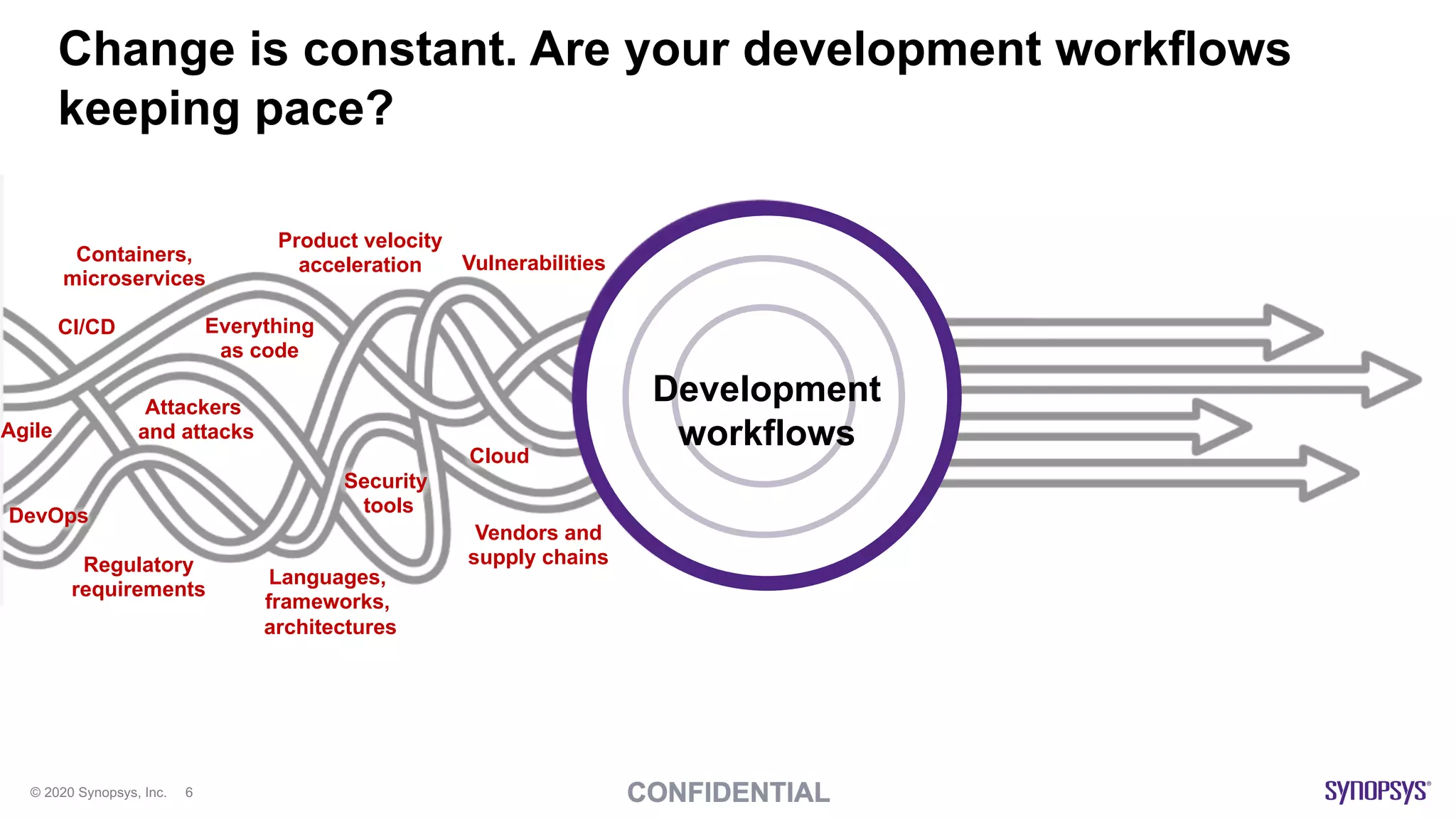
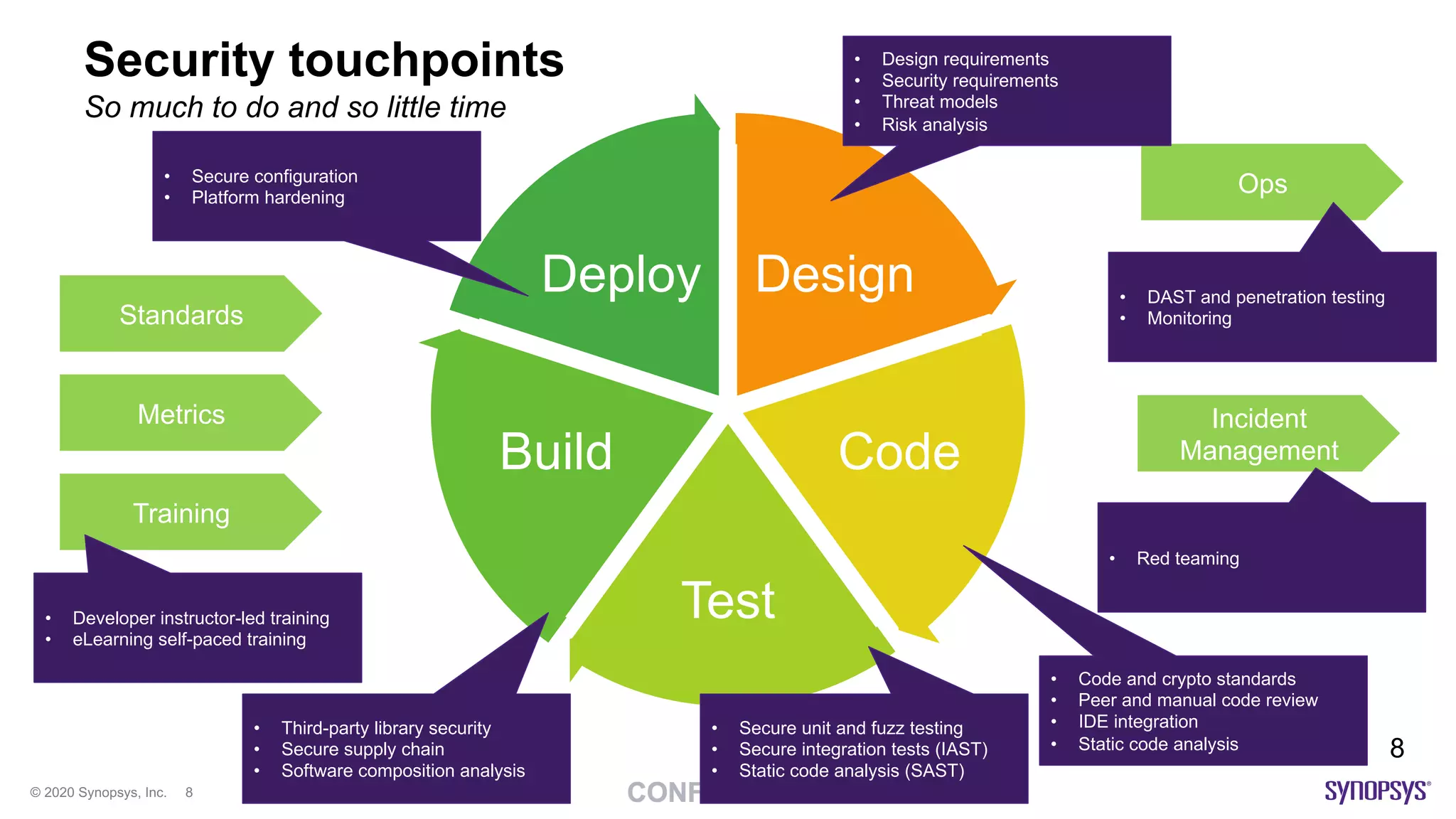
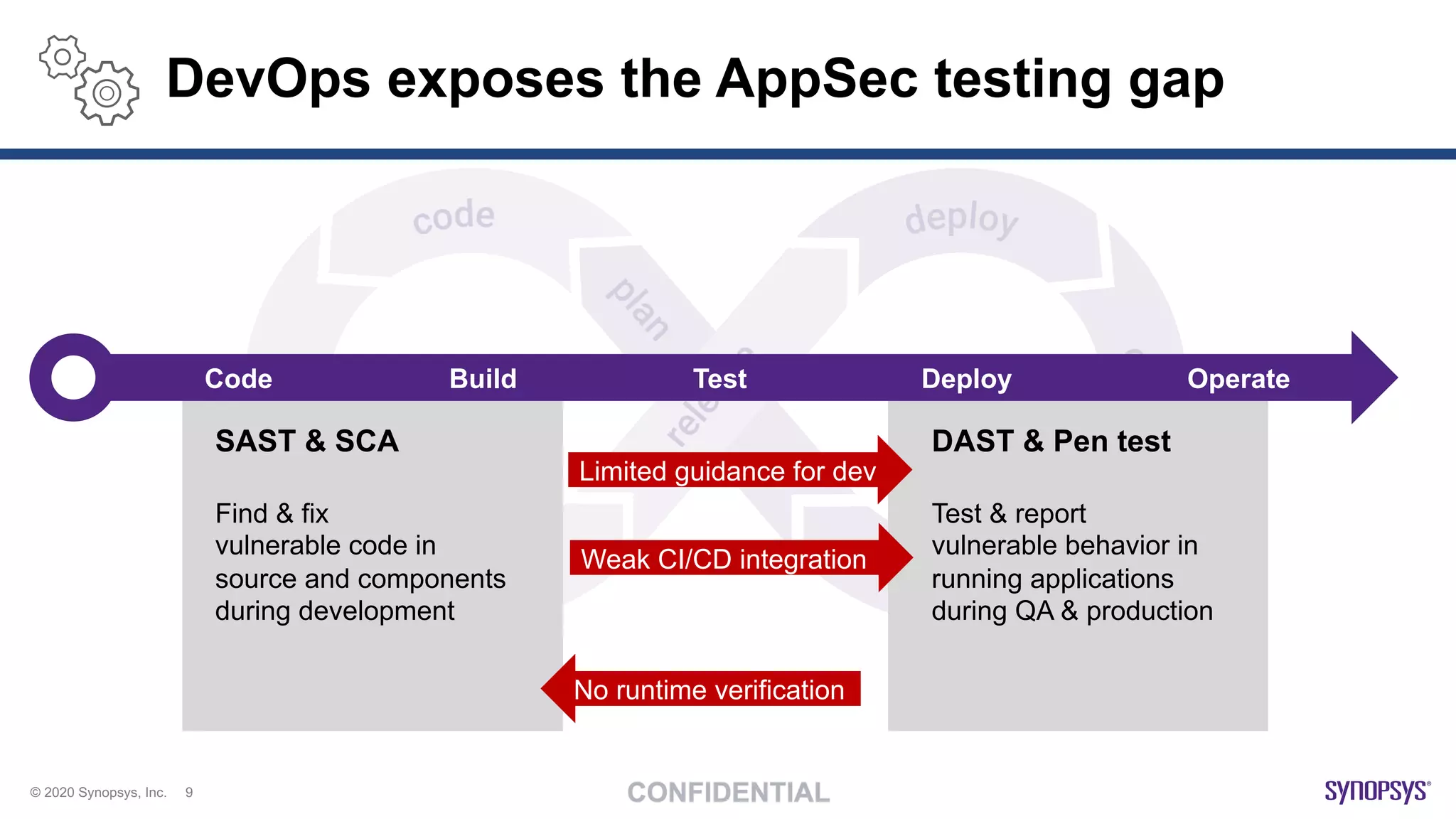
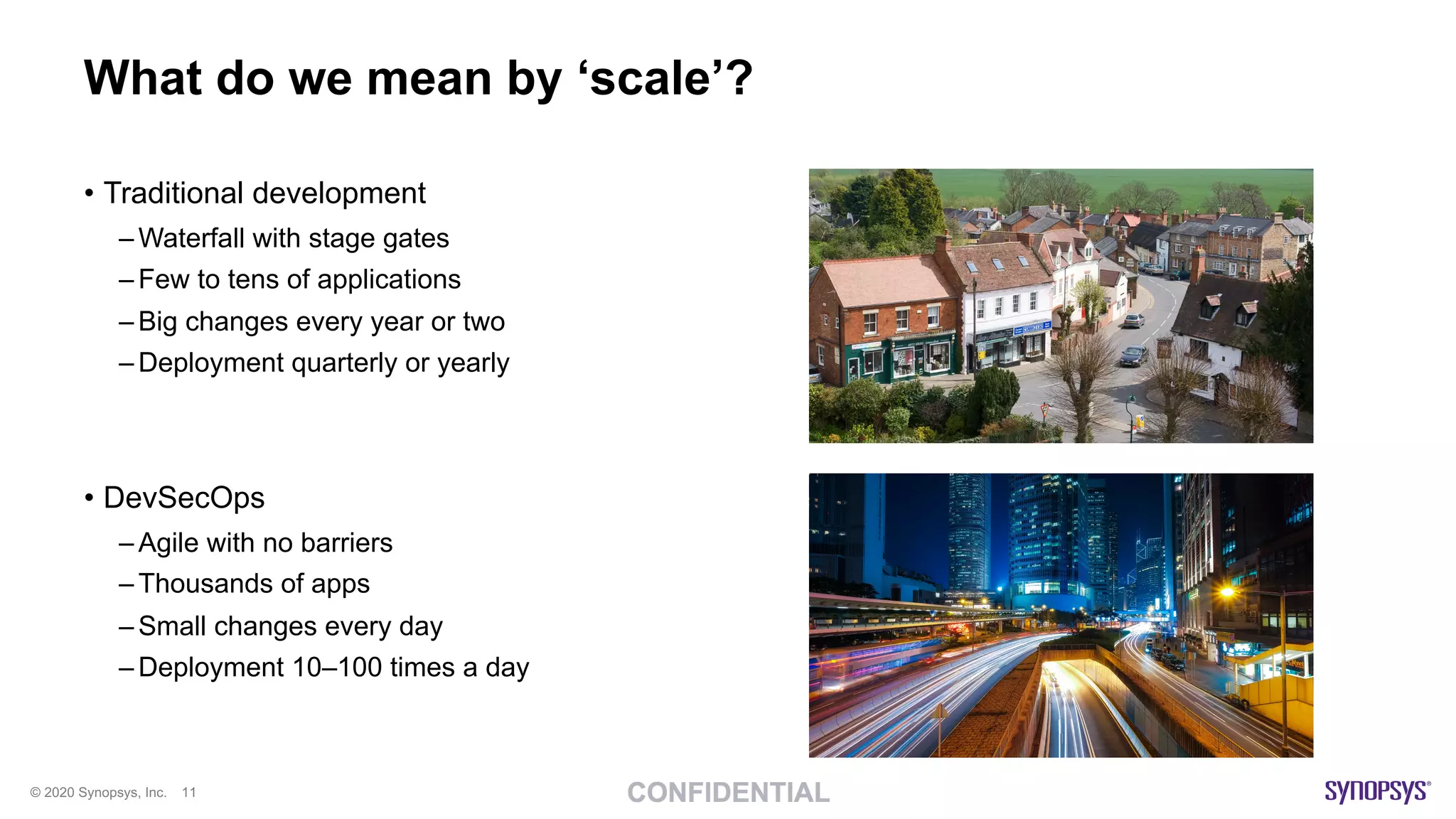
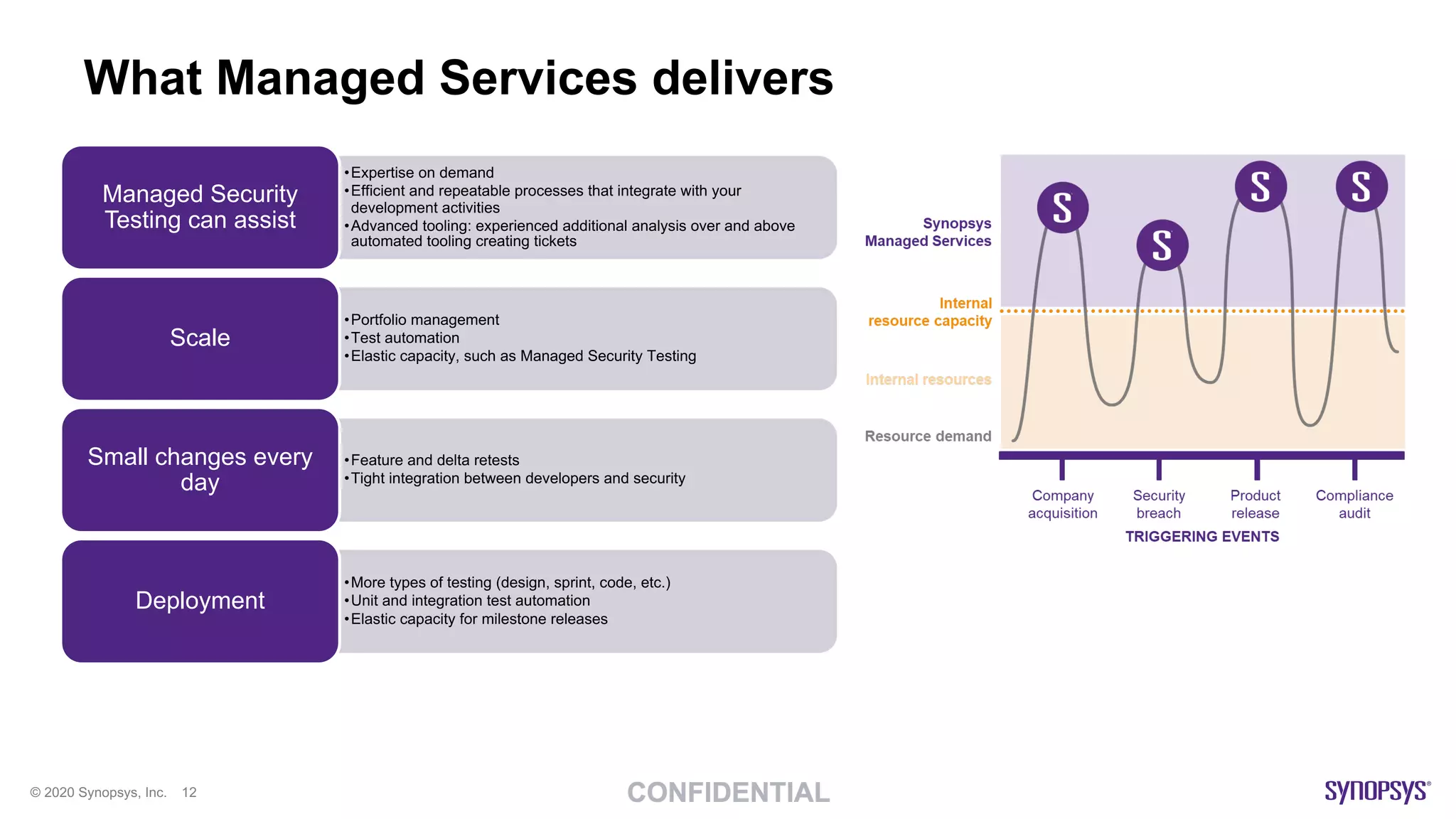
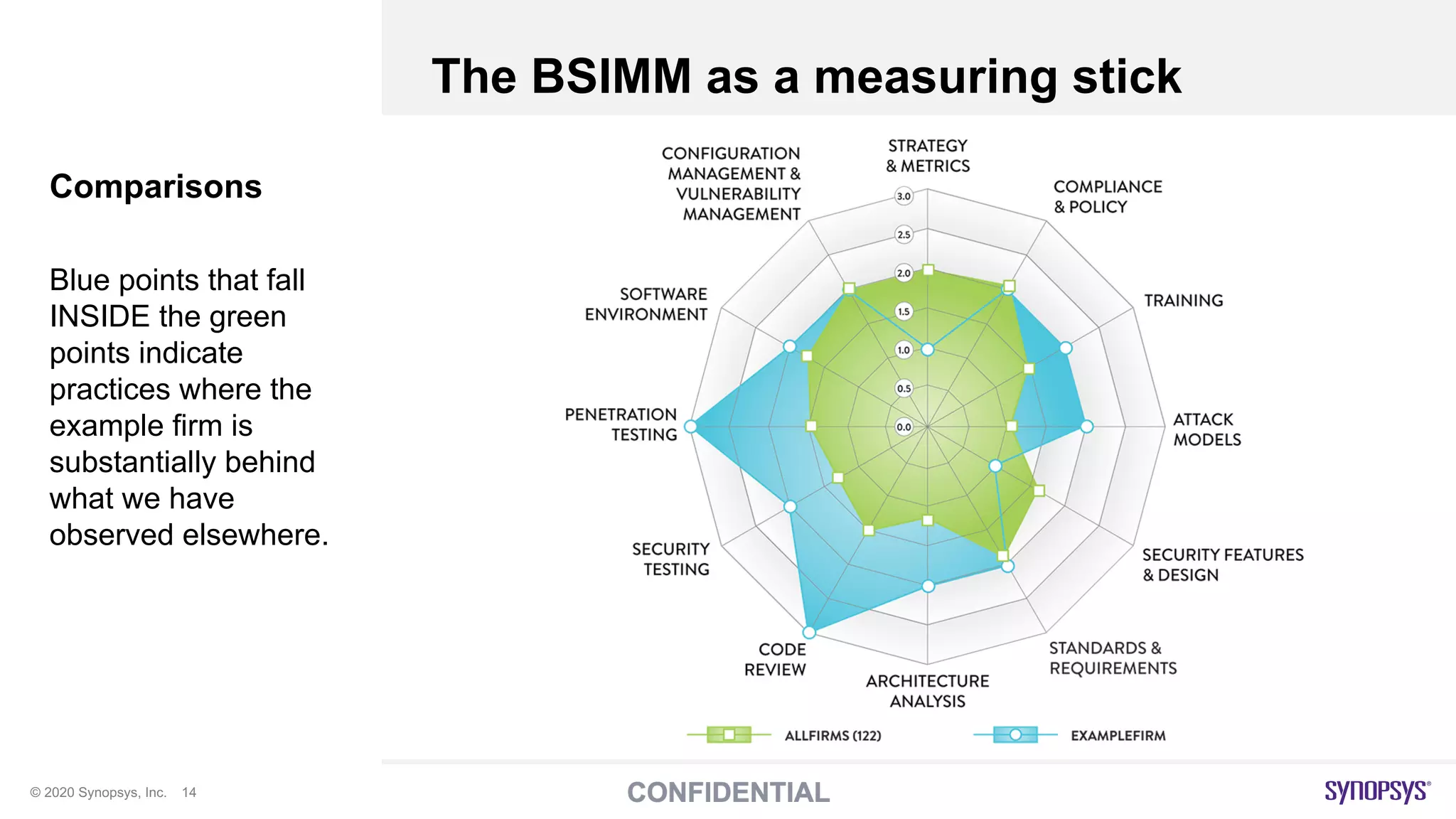
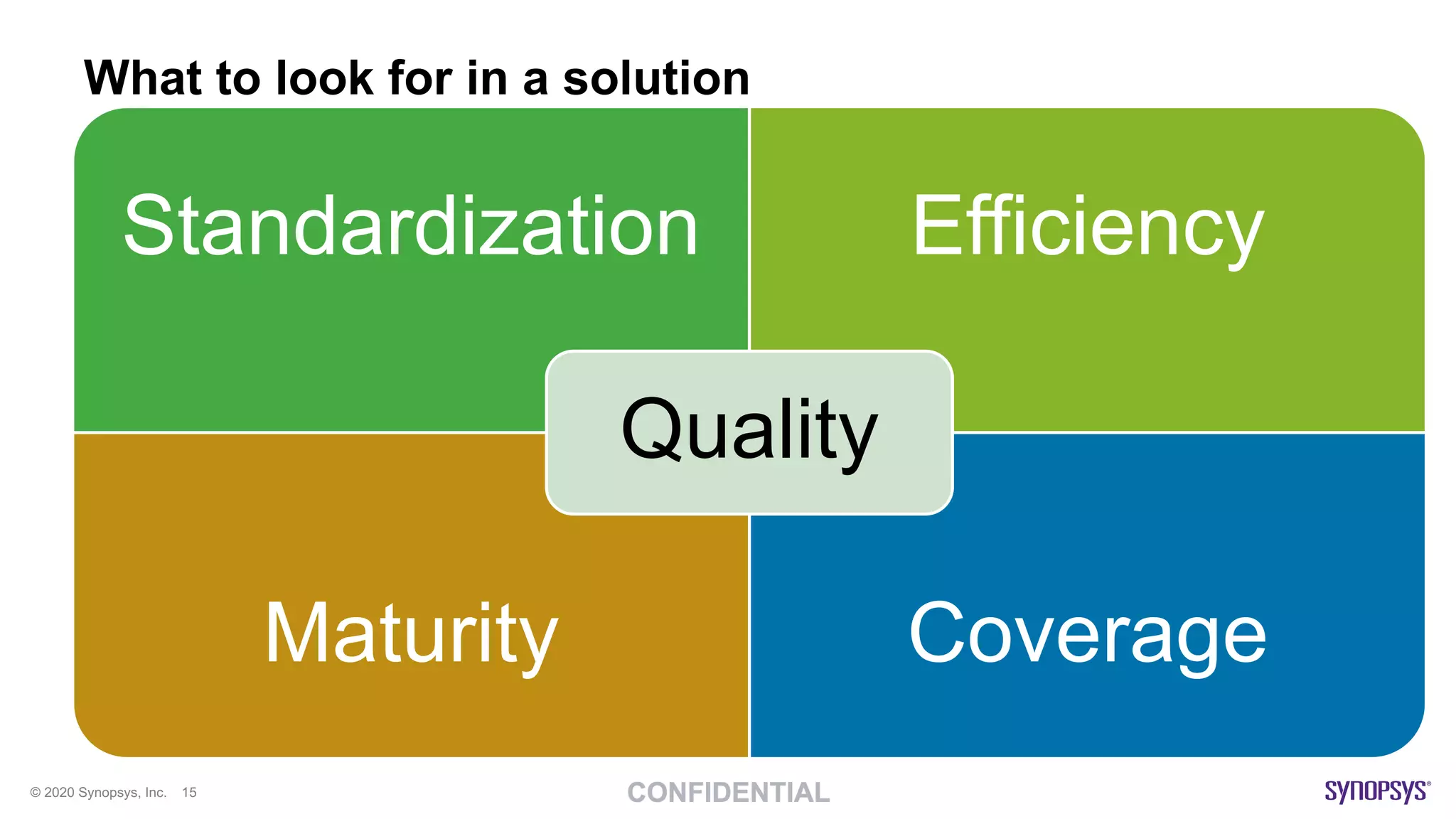
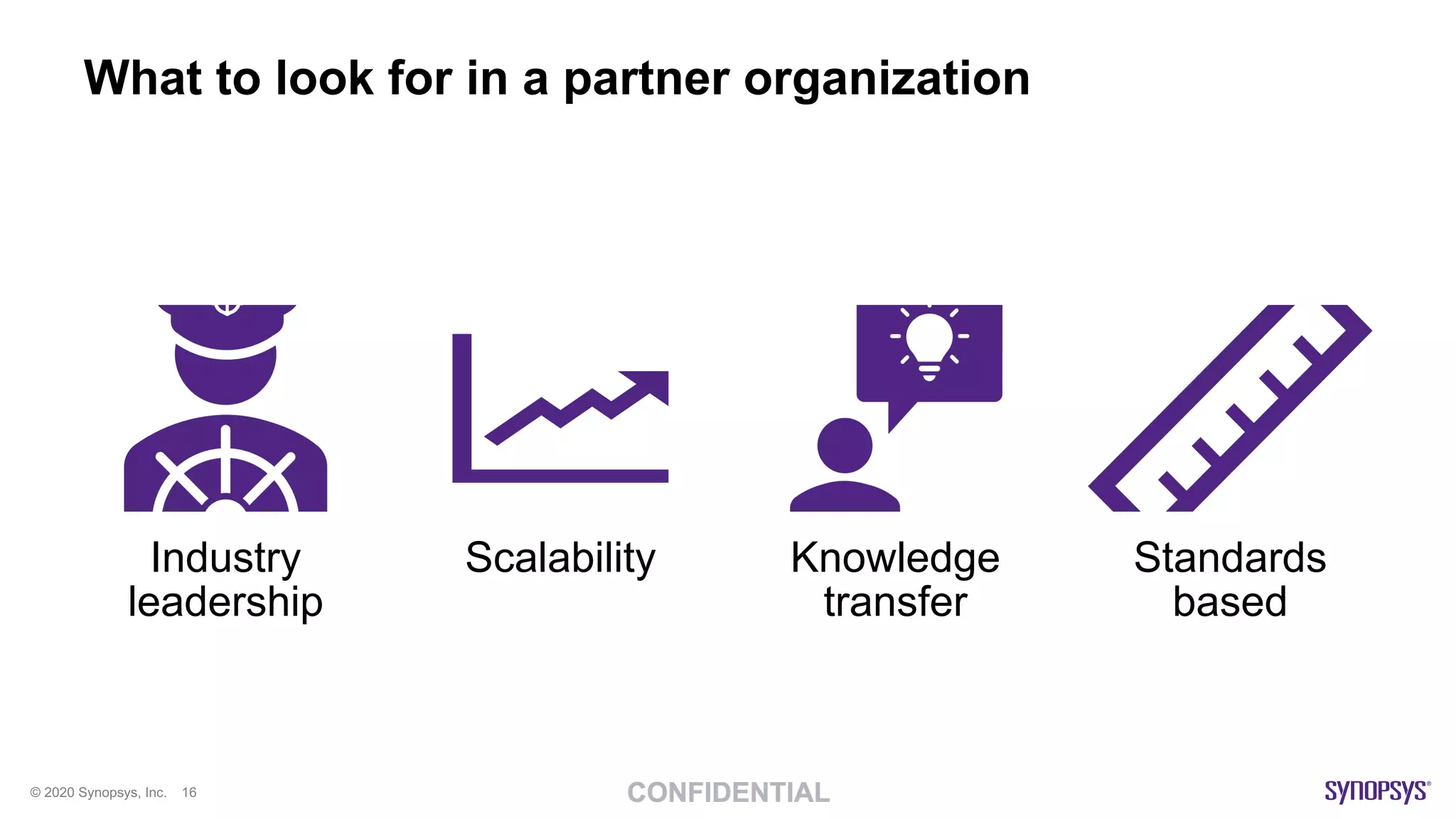
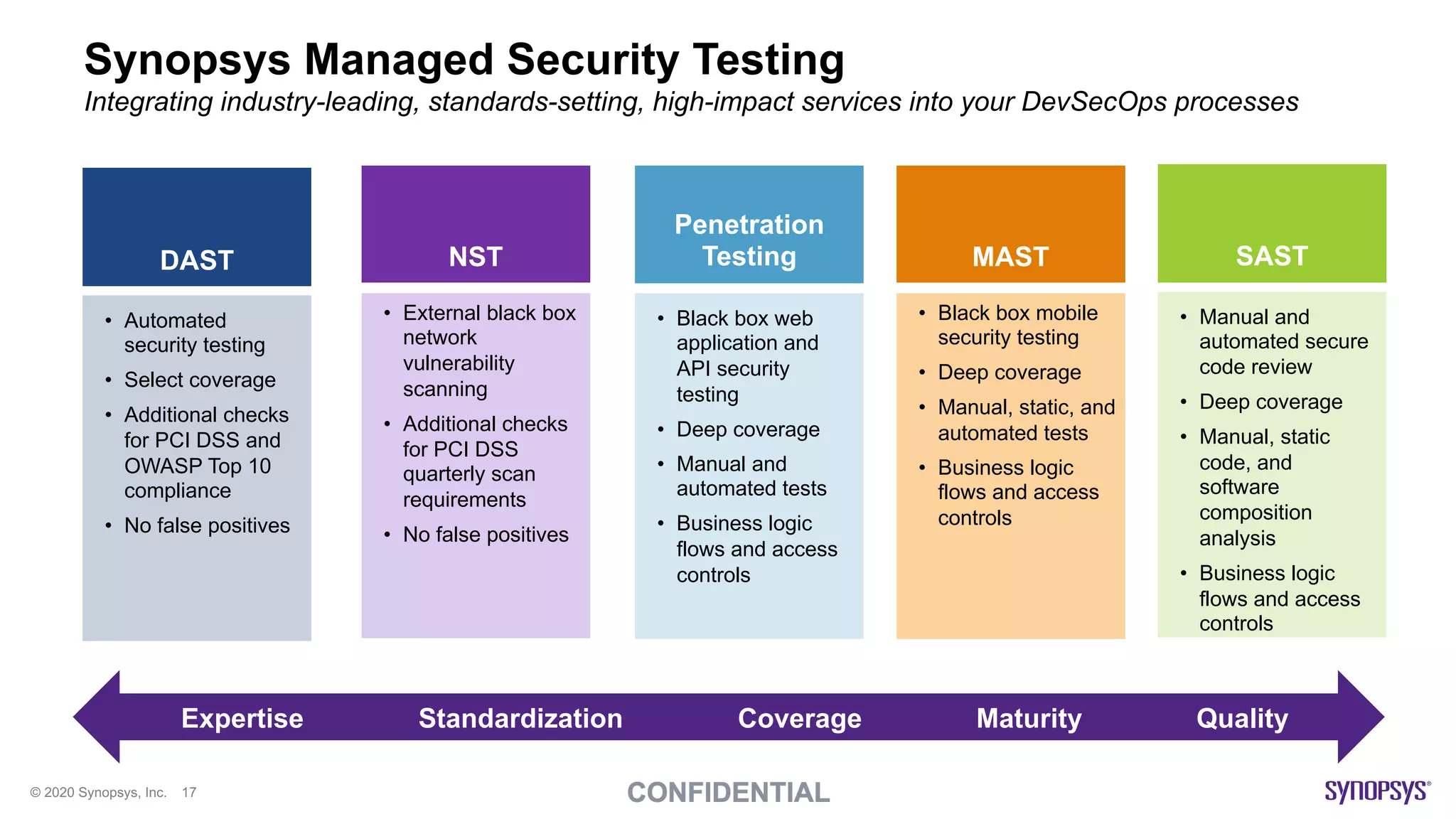
The document outlines best practices for implementing DevSecOps at scale, emphasizing the integration of security into agile development processes without hindering speed. It highlights various tools and methodologies for vulnerability detection across different stages of the software development lifecycle, including static and dynamic application security testing. A strong DevSecOps culture is positioned as a key differentiator for organizations seeking to lead in security, with recommendations for utilizing managed security services to enhance application security efforts.