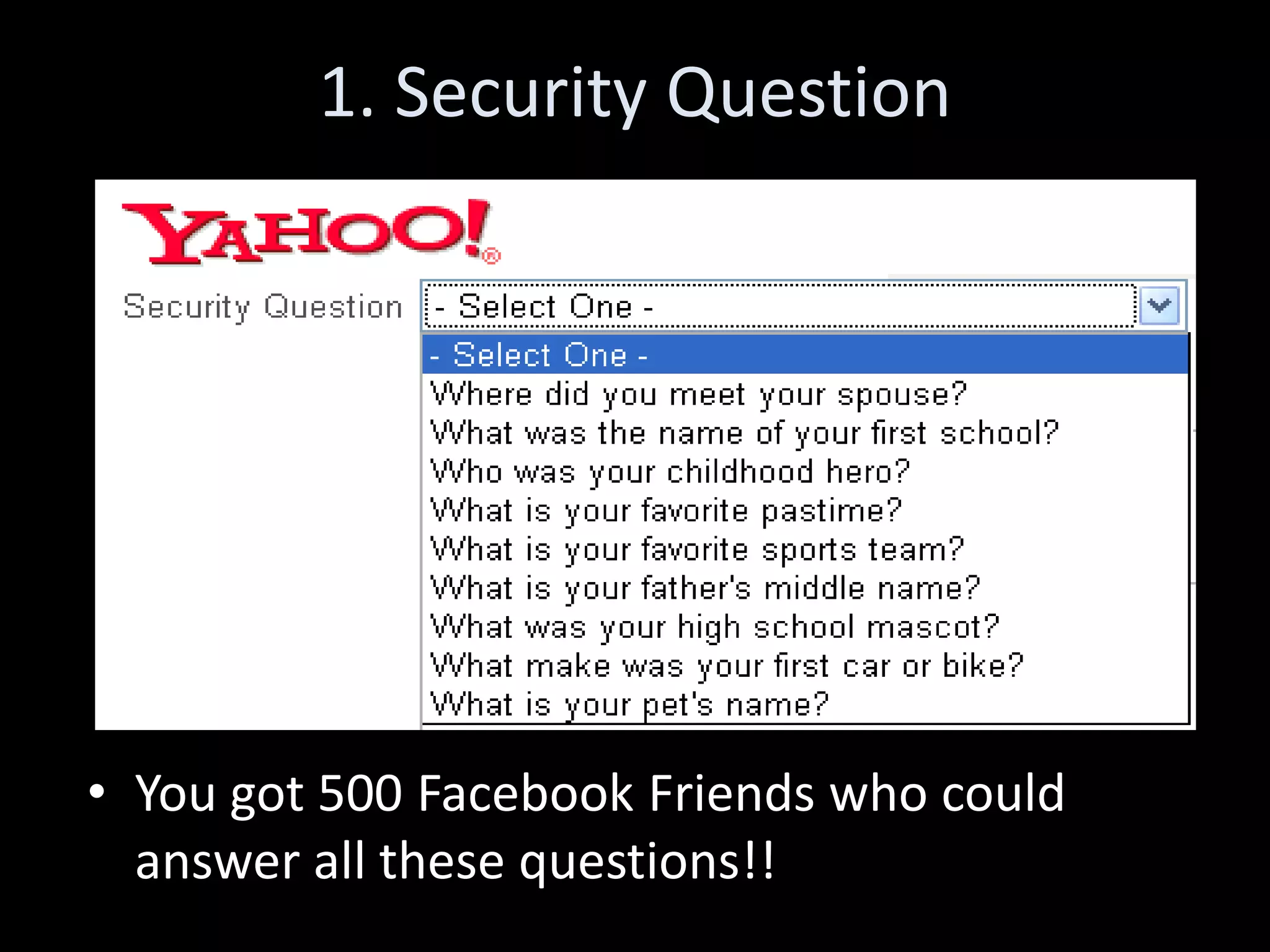
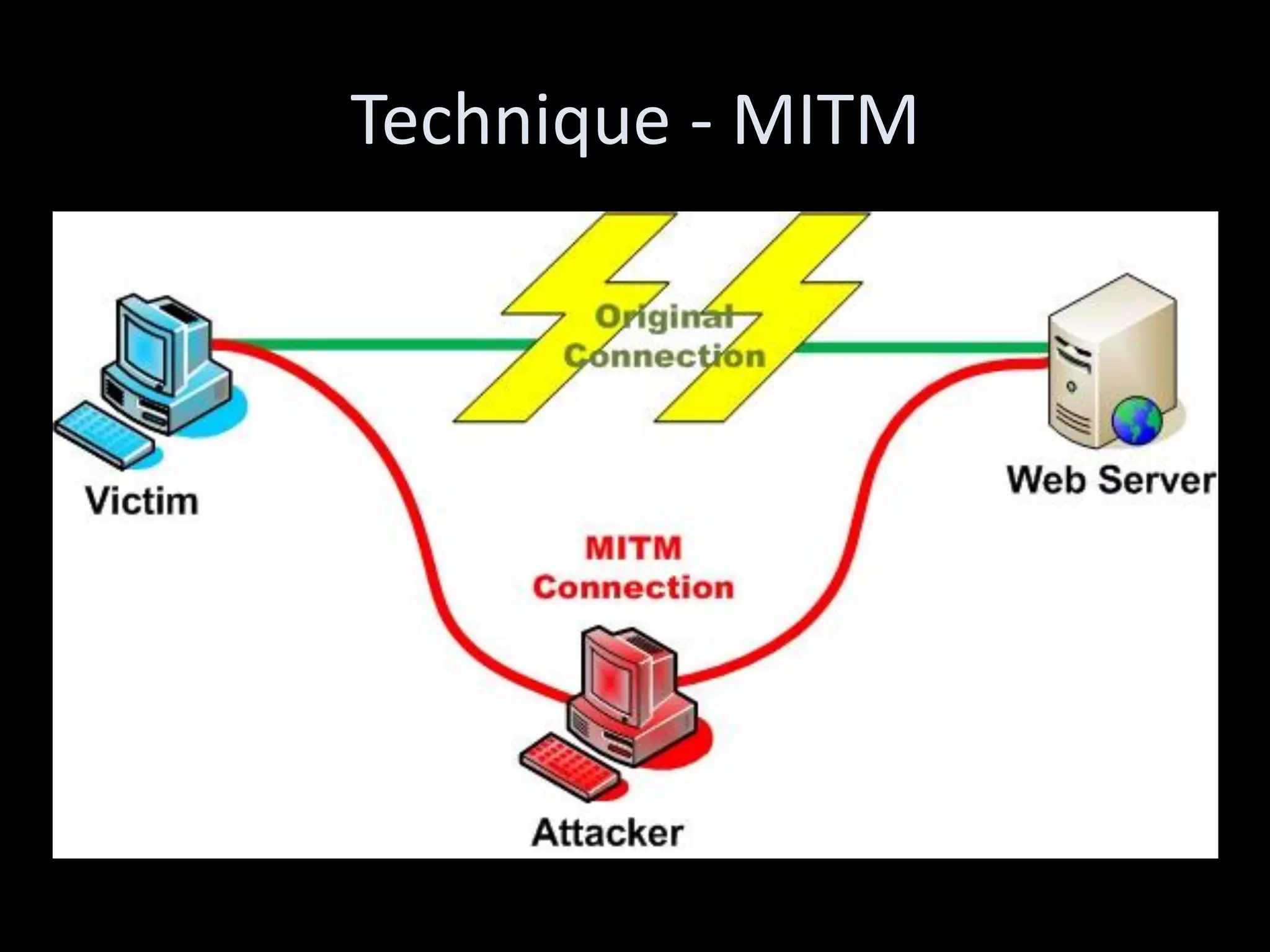
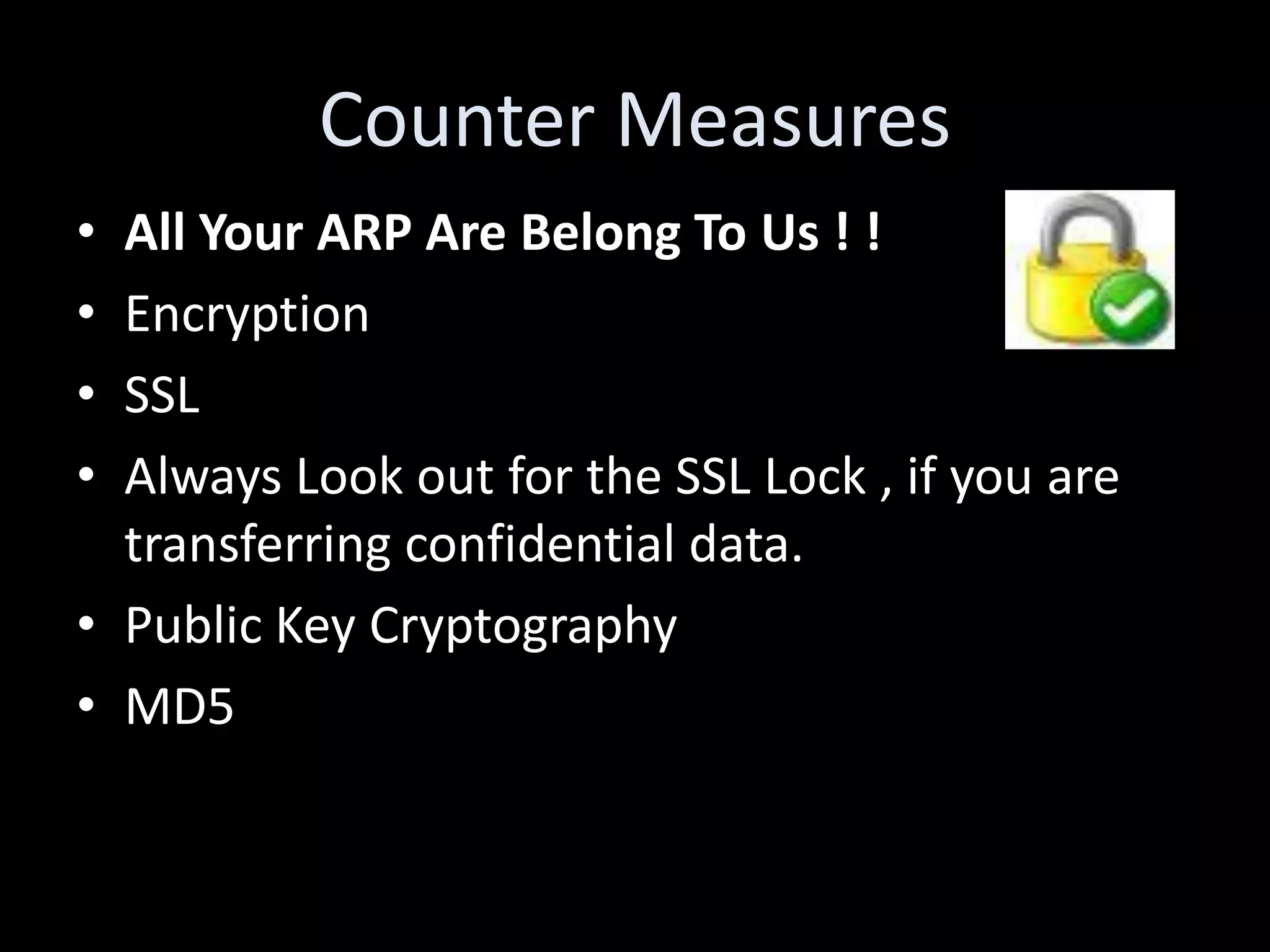
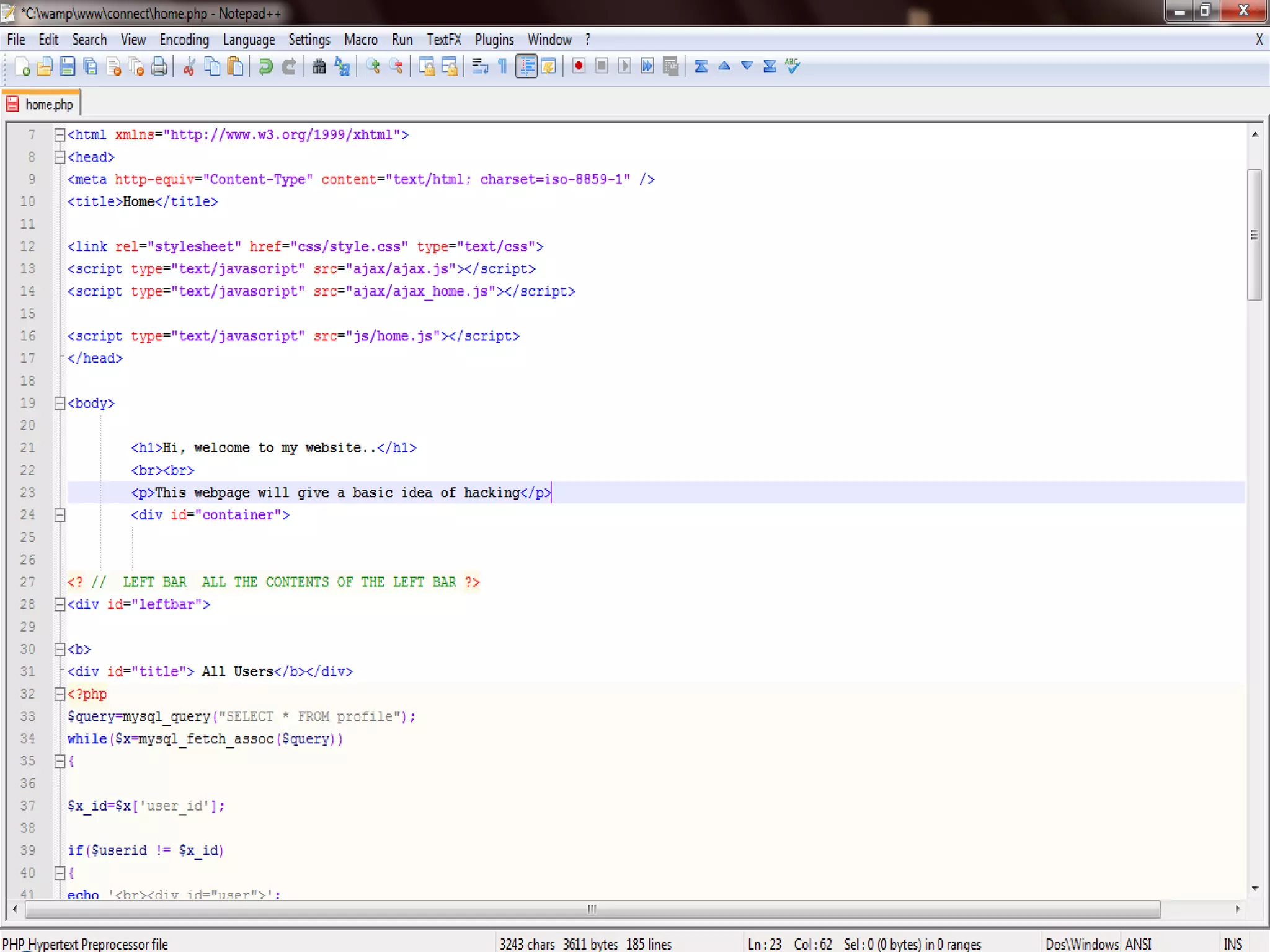
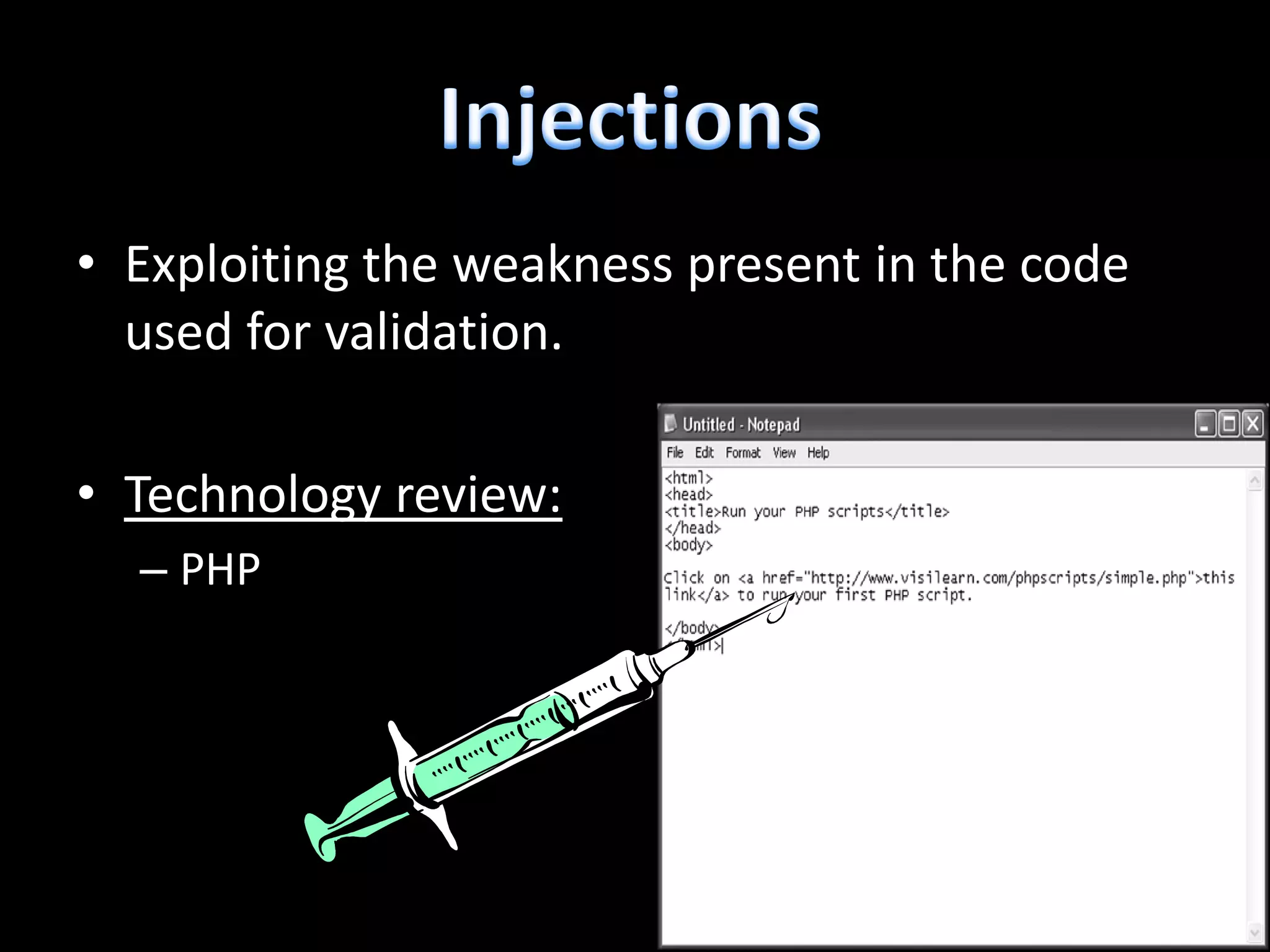
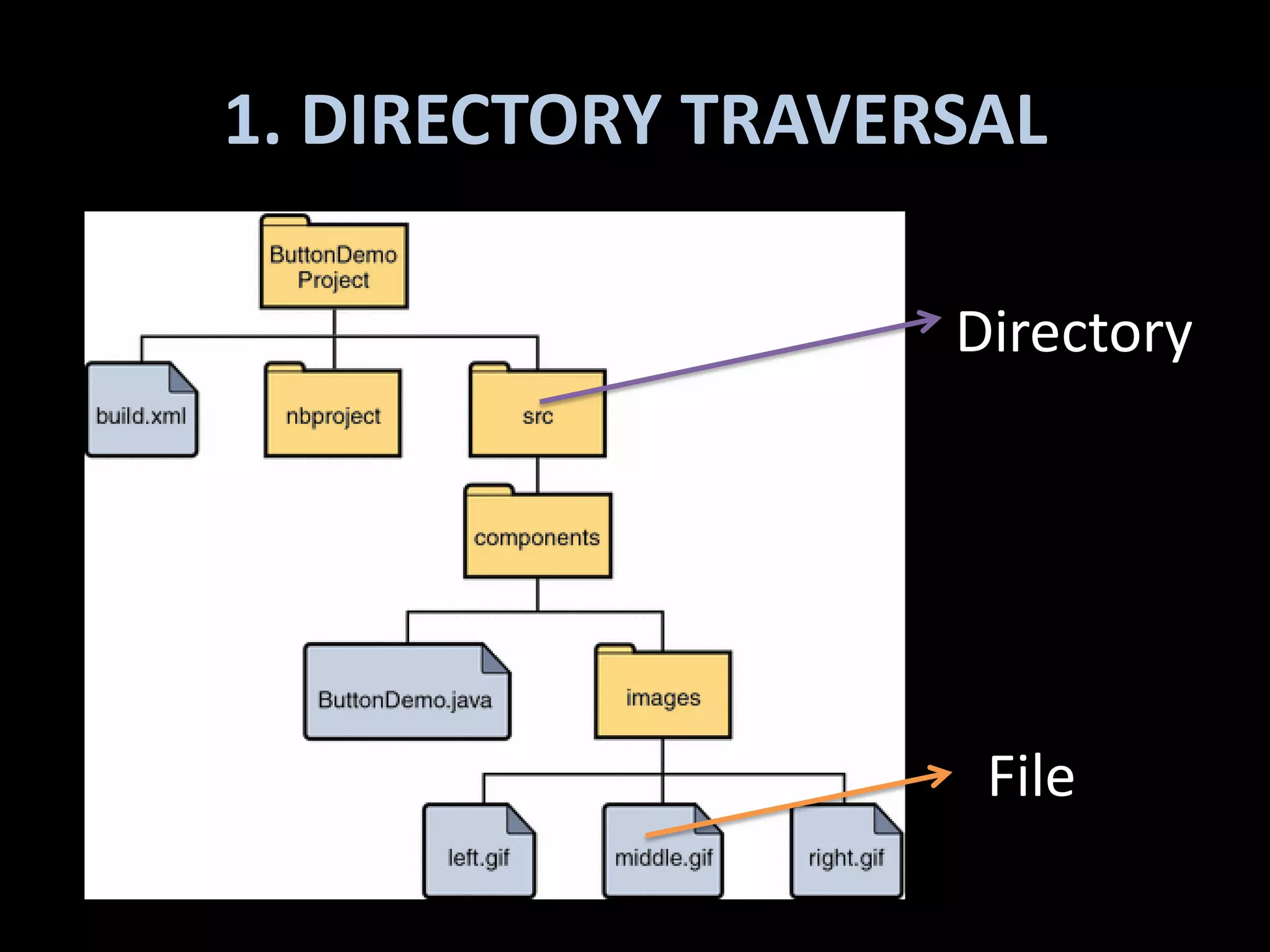
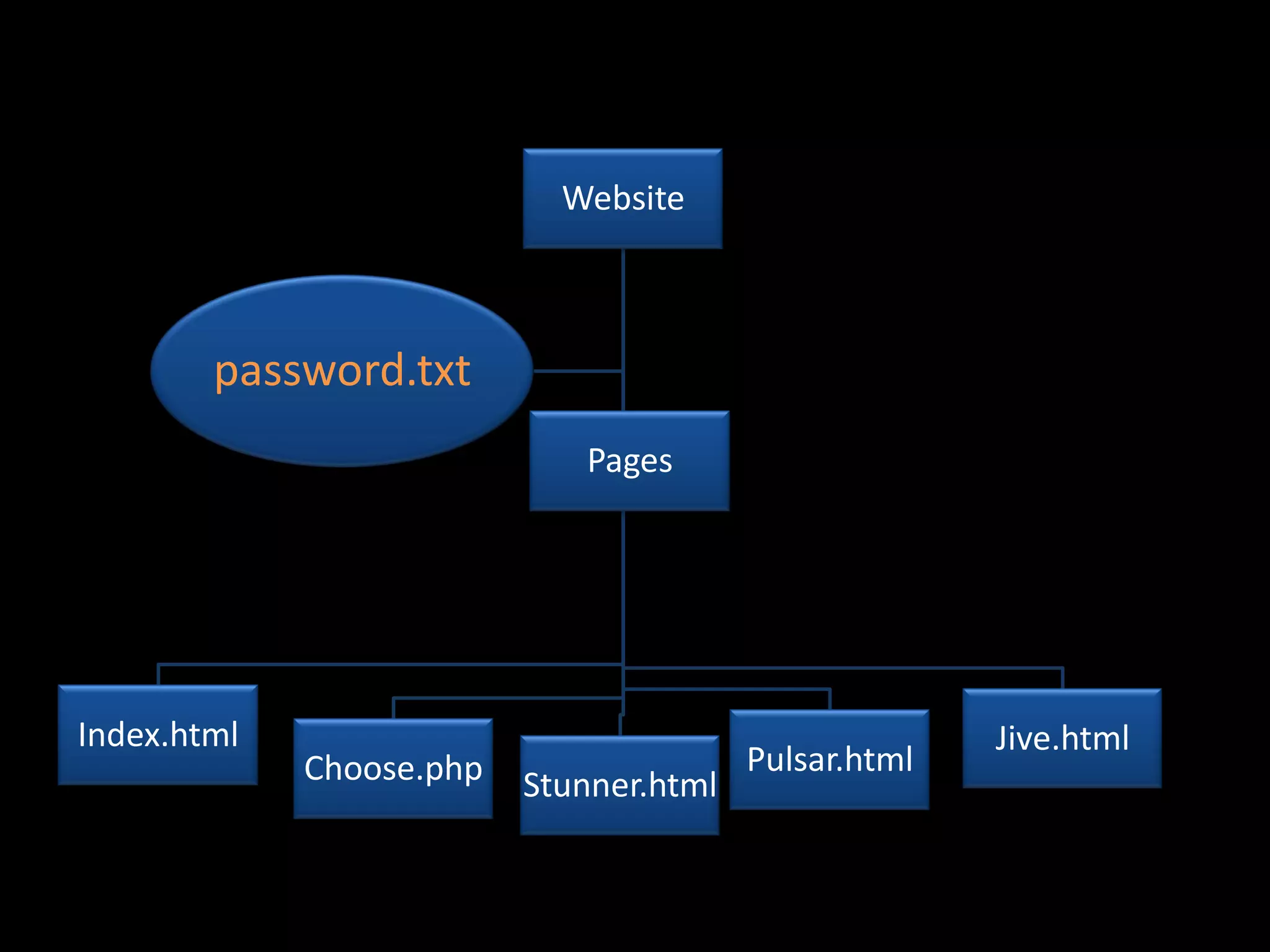
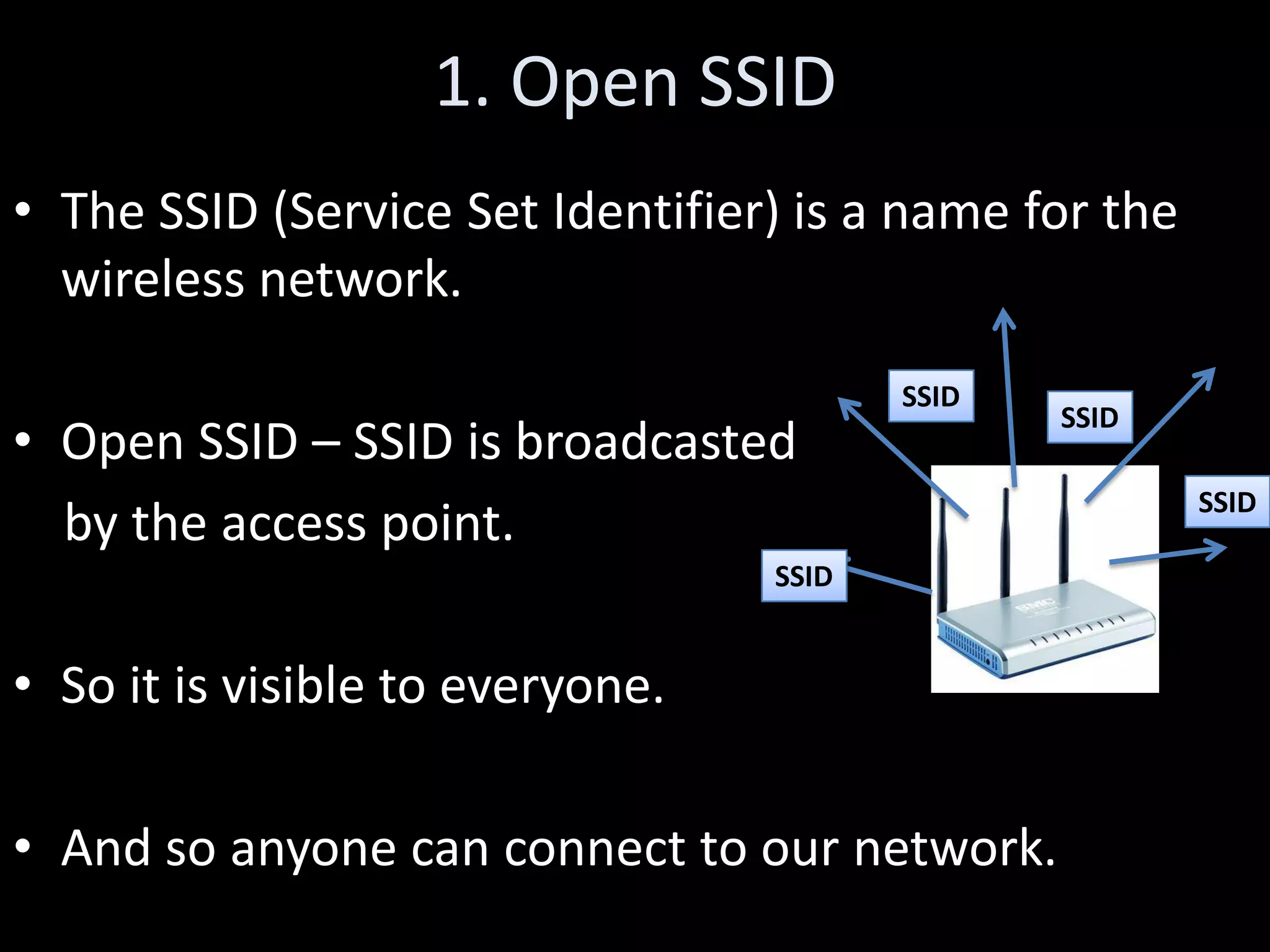
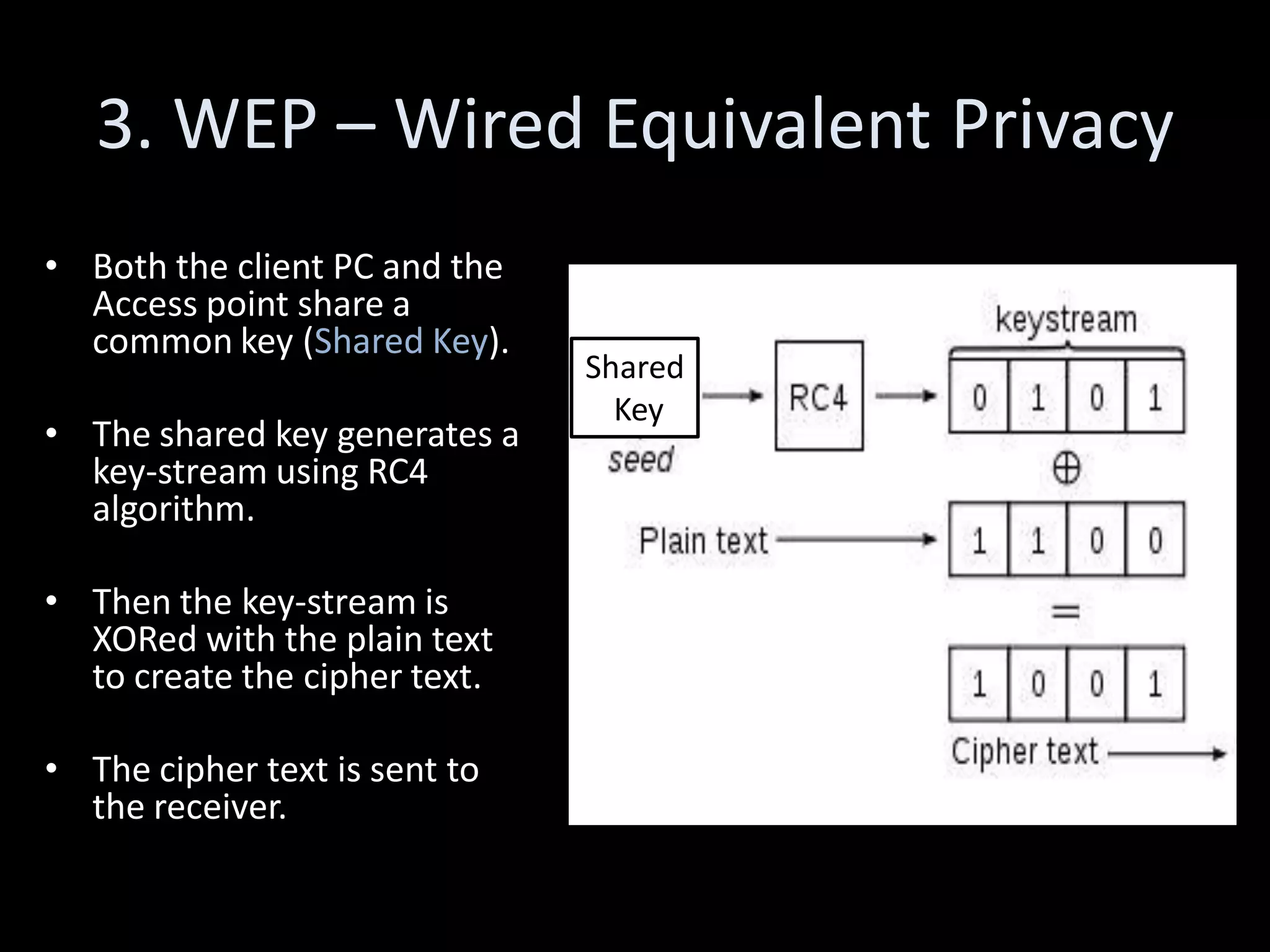
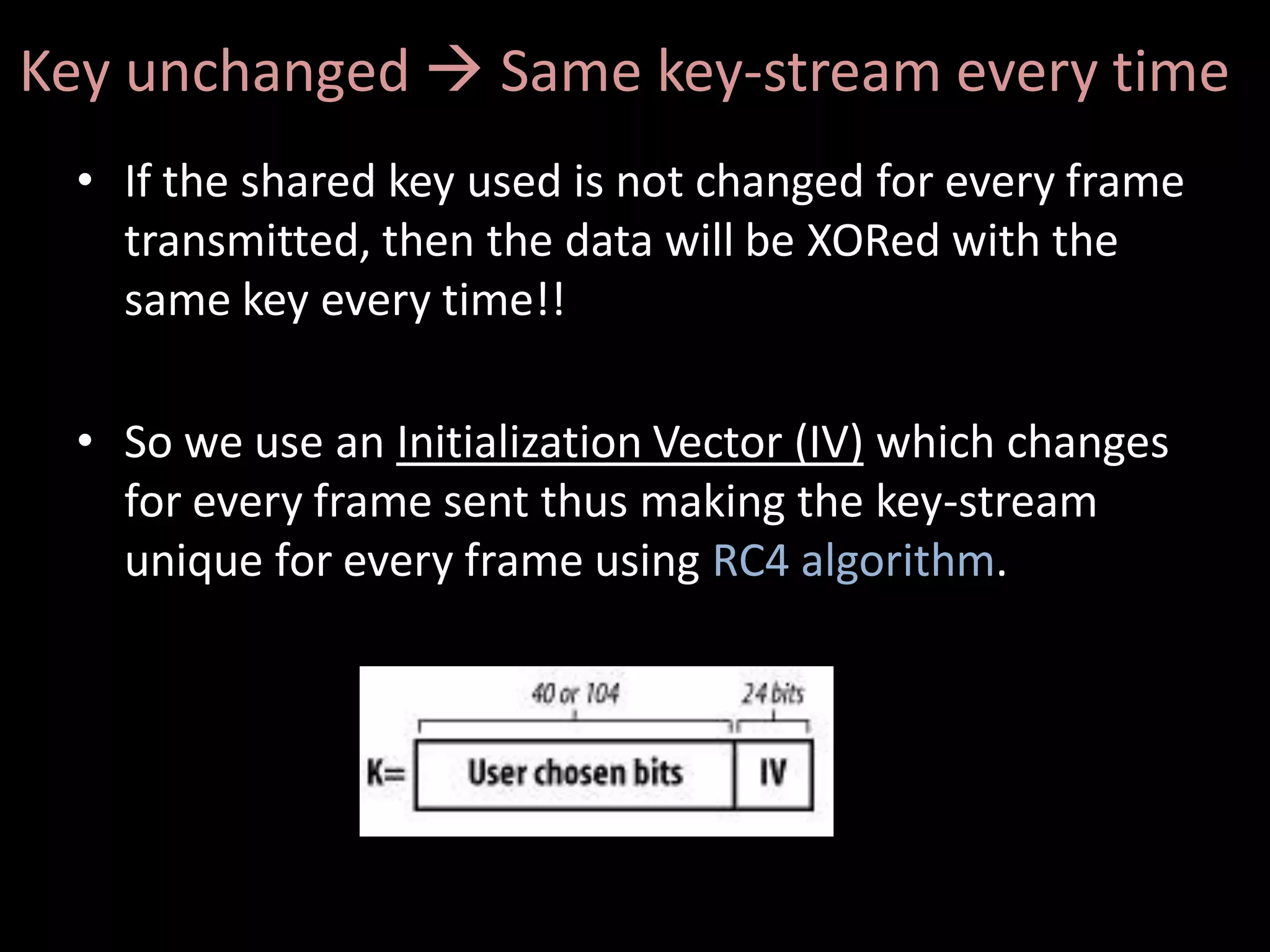
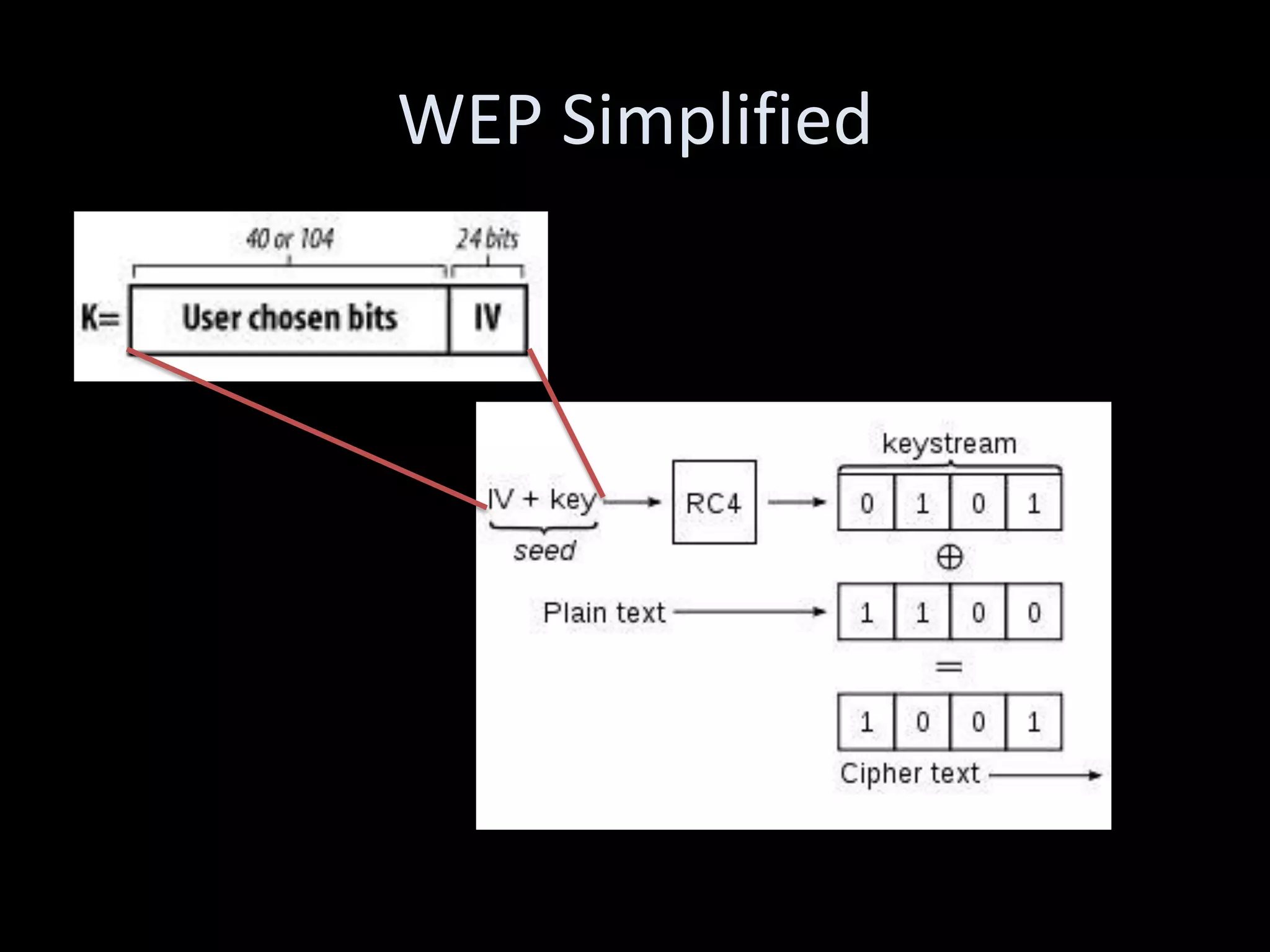
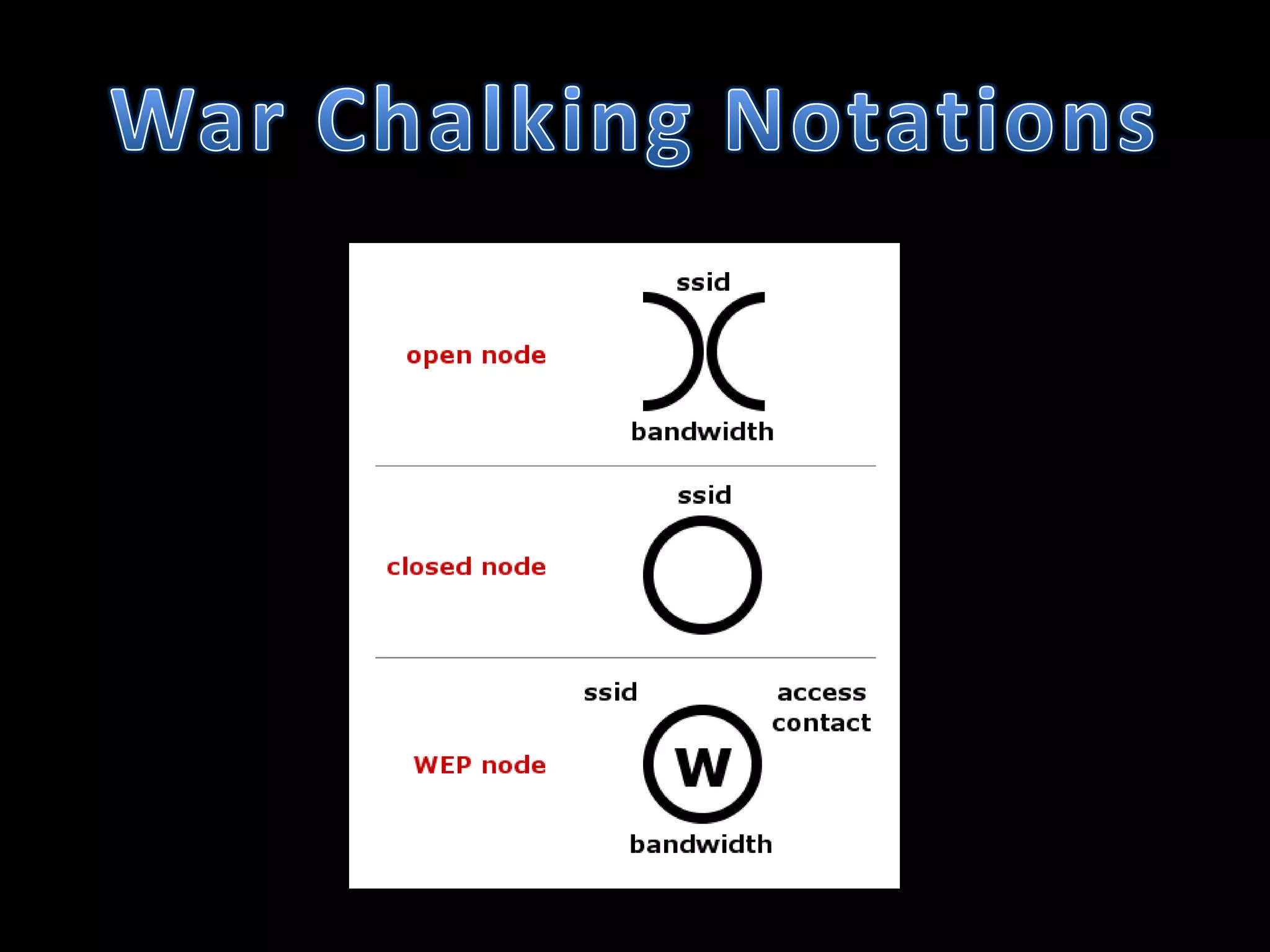
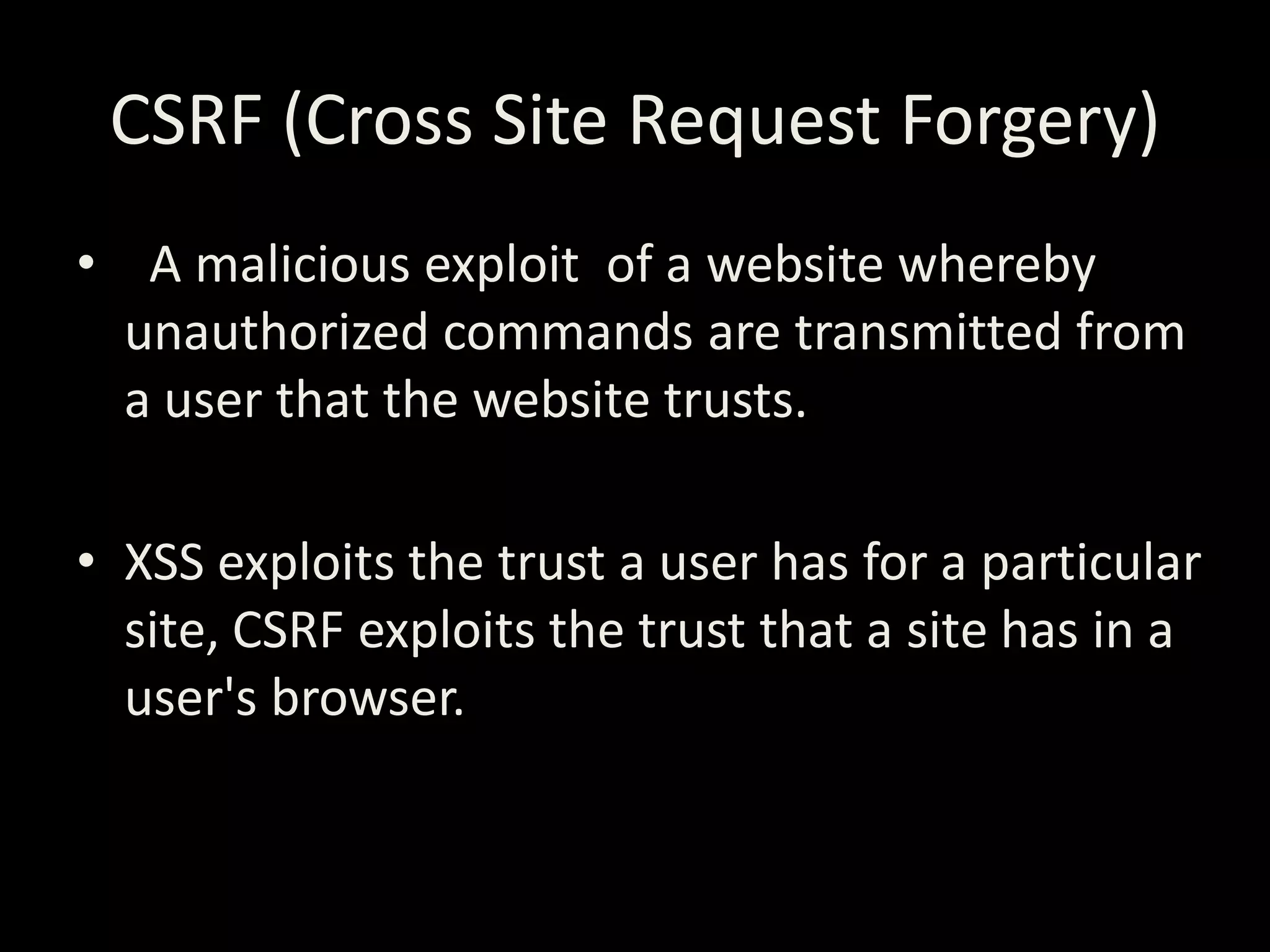
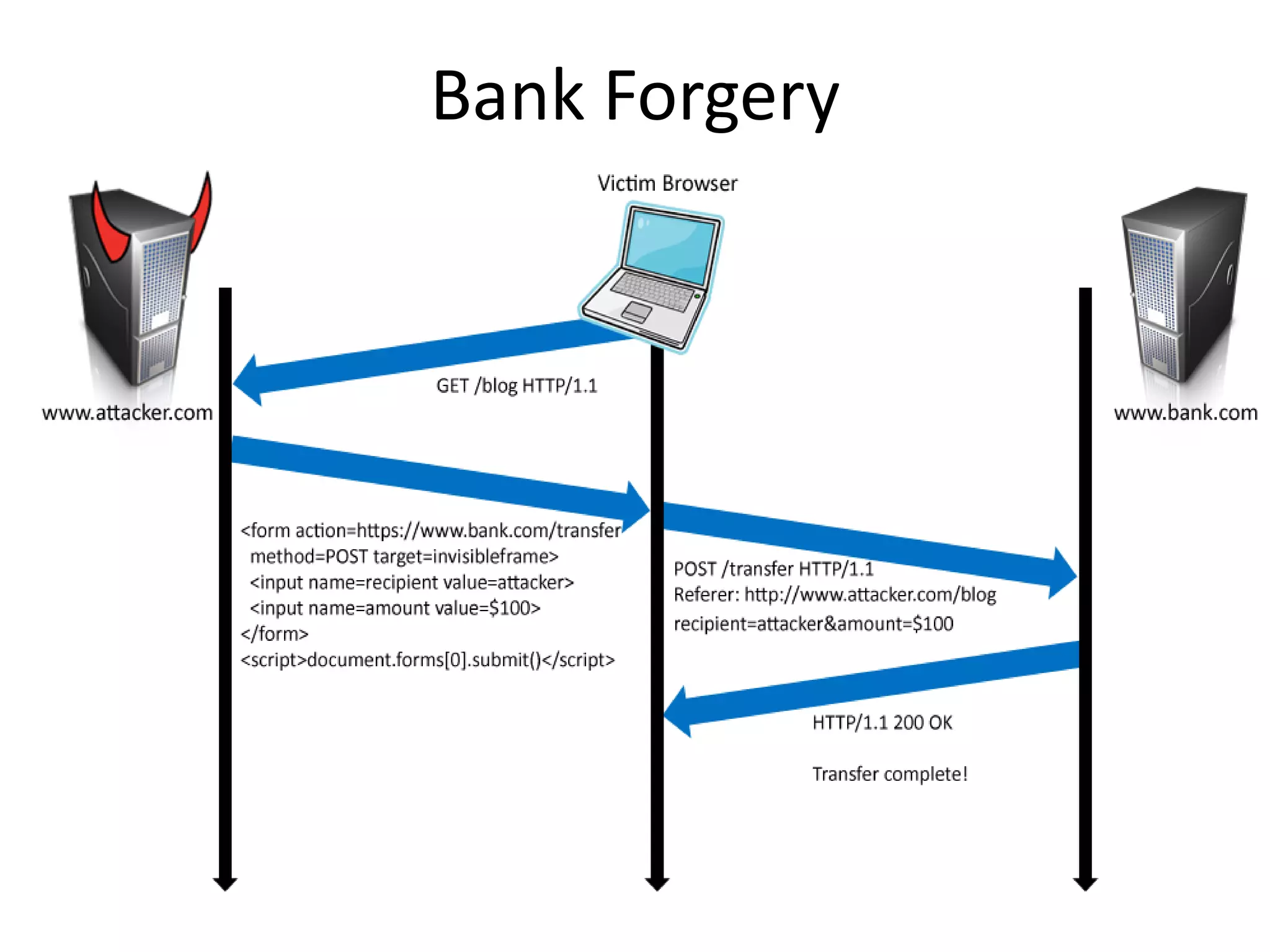
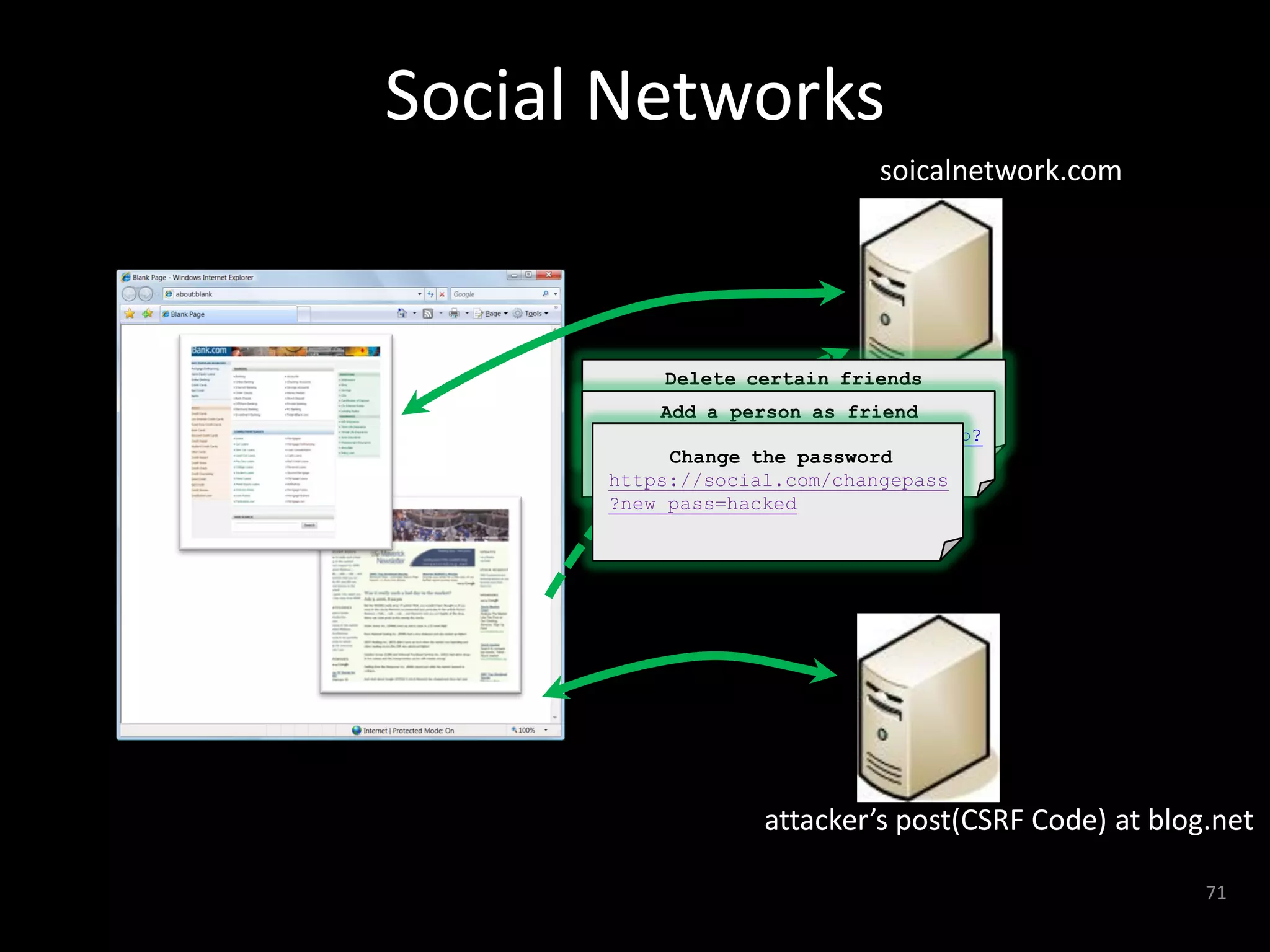
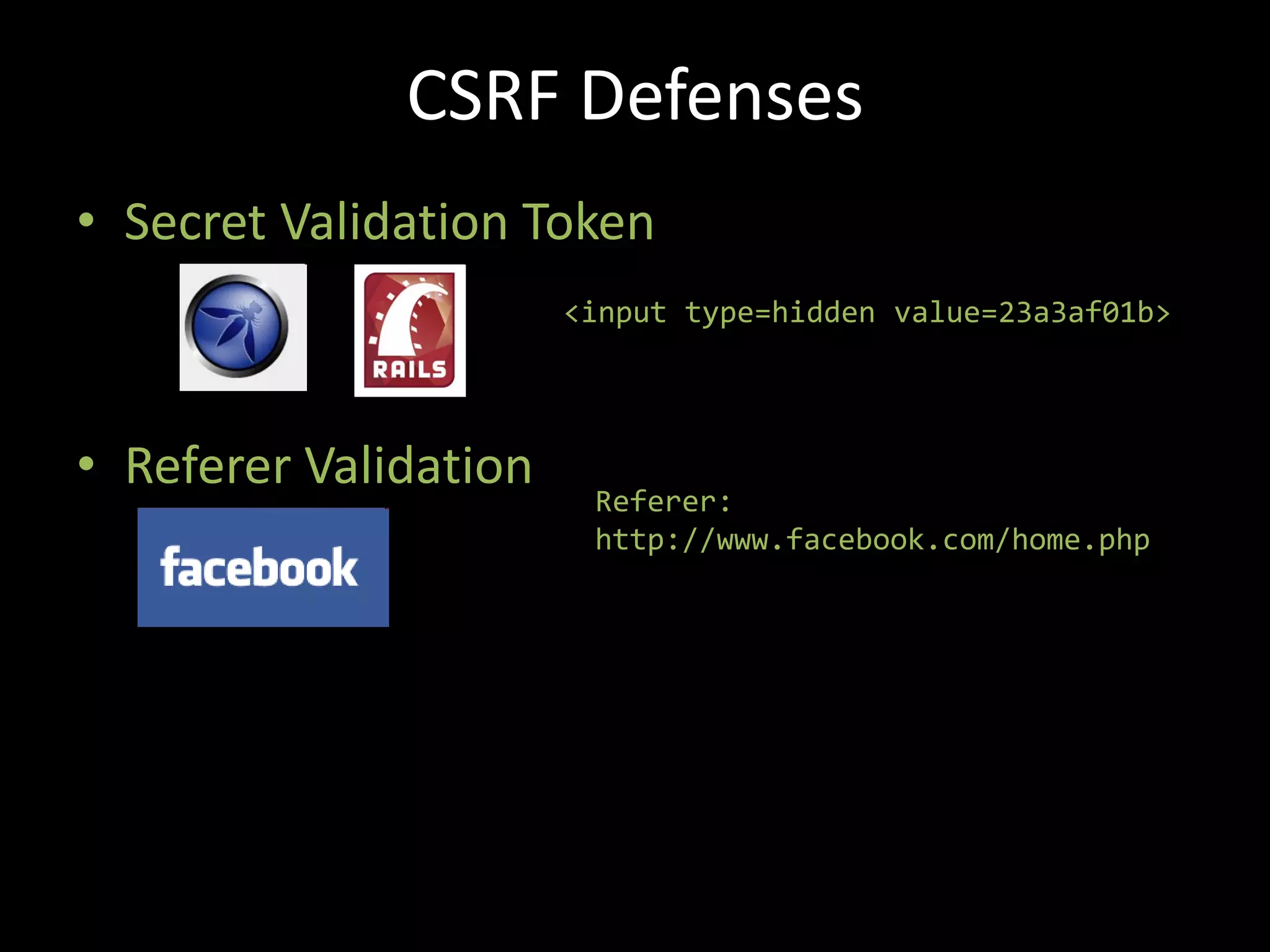
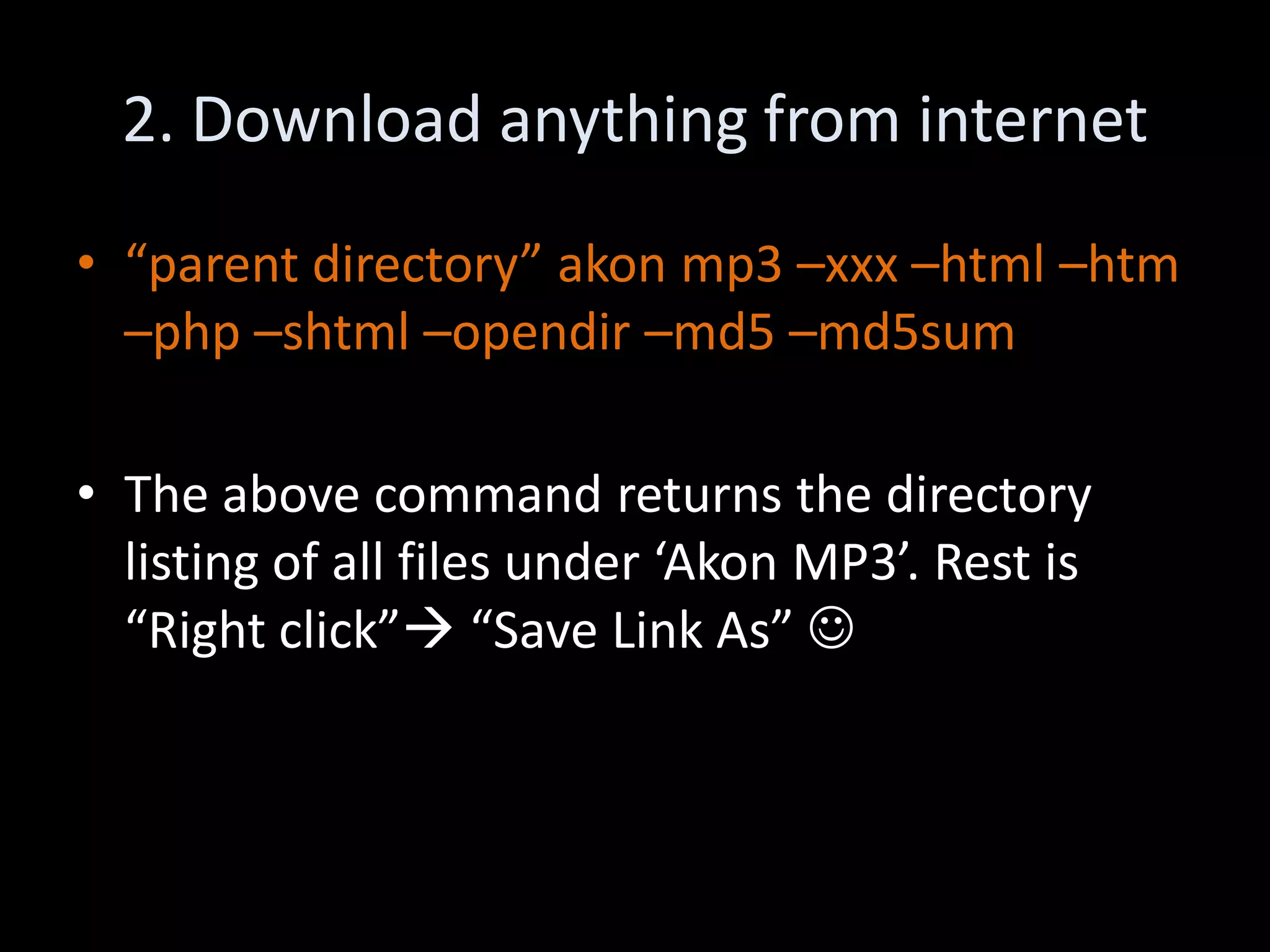
The document discusses various hacking techniques and their implications on security, such as social engineering, ARP poisoning, SQL injection, and cross-site scripting. It emphasizes the need for robust security measures including password complexity, input validation, and awareness of vulnerabilities in web applications and wireless networks. Additionally, it outlines protective mechanisms and specific countermeasures to safeguard against these cyber threats.